Design of large-scale dynamic multicasting security system framework
A security system and large-scale technology, applied to key distribution, can solve the problems of high security processing cost, group members are not sure which member the data comes from, and increase the cost of multicast group deployment, so as to reduce the overall cost and expand flexibly Mechanism, the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical scheme of the present invention will be described in detail below in conjunction with the accompanying drawings.
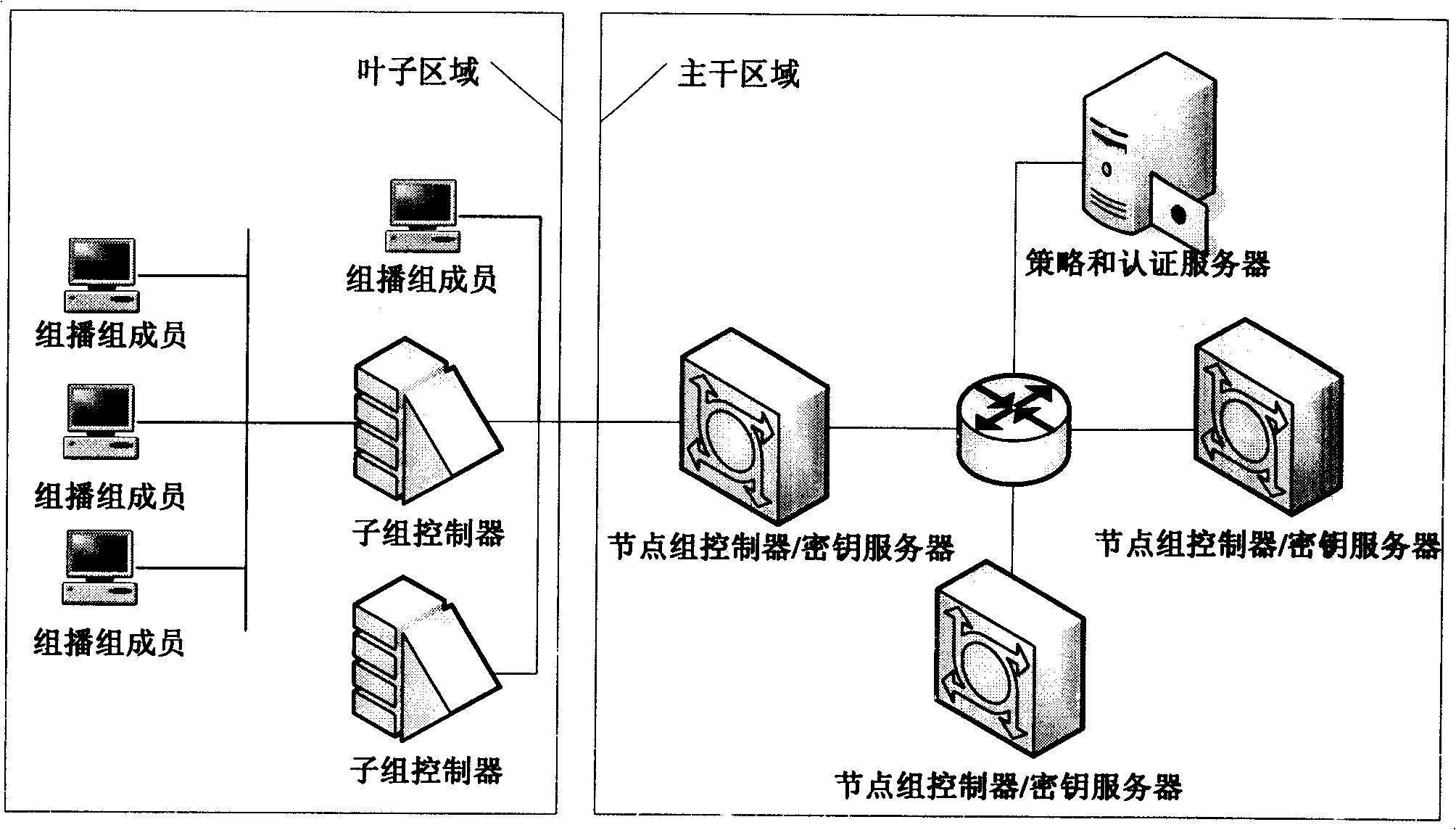
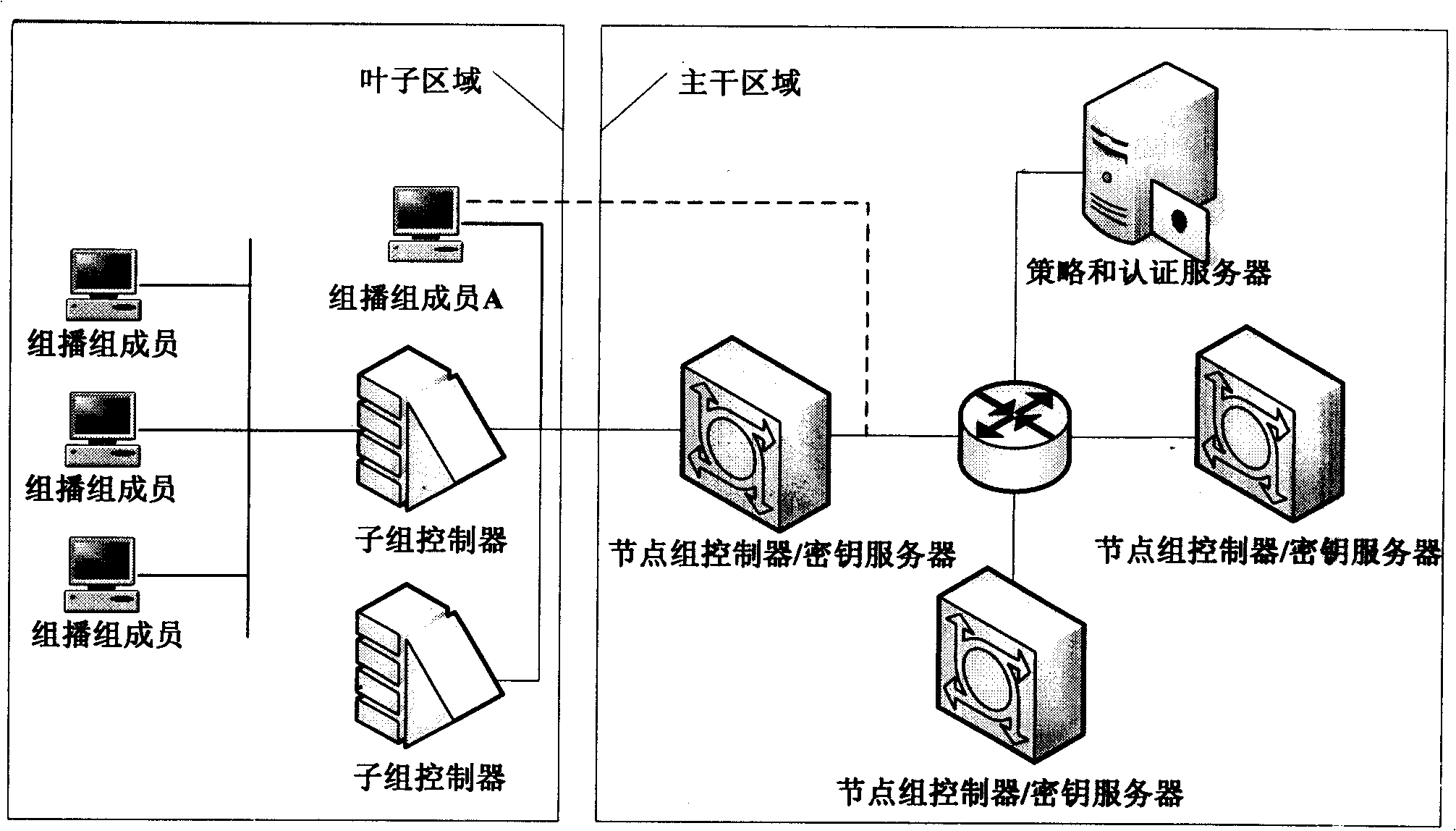
[0029] Figure 4 A schematic diagram of dynamic multicast operation under this framework is shown:
[0030] After the group owner or creator (GO) interacts with the policy server (PS) (through steps 1 and 2) to obtain the policy token (PT), it applies to a certain group of controllers and key servers (GCKS) on the backbone domain for creation A multicast group instance (step 3). The GCKS is called an initial GCKS (I-GCKS), and the I-GCKS publishes secure multicast content with the group key in the backbone domain in the backbone domain.
[0031] The group member (GM) who needs to join the multicast group sends a join request (RTJ) message to the GCKS that manages the leaf domain (steps 7 and 8), or submits a join application to the GCKS through the S-GCKS that manages the subgroup (steps 5 and 8). 6, 9, 10).
[0032] The GM that exits the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com