Security association storage and recovery in group key management
a technology of group key management and security association, applied in the security field, can solve the problems of reducing the performance of multicast applications, sa, data sa, etc., and achieve the effect of minimizing the performance loss of re-establishing the secure group
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
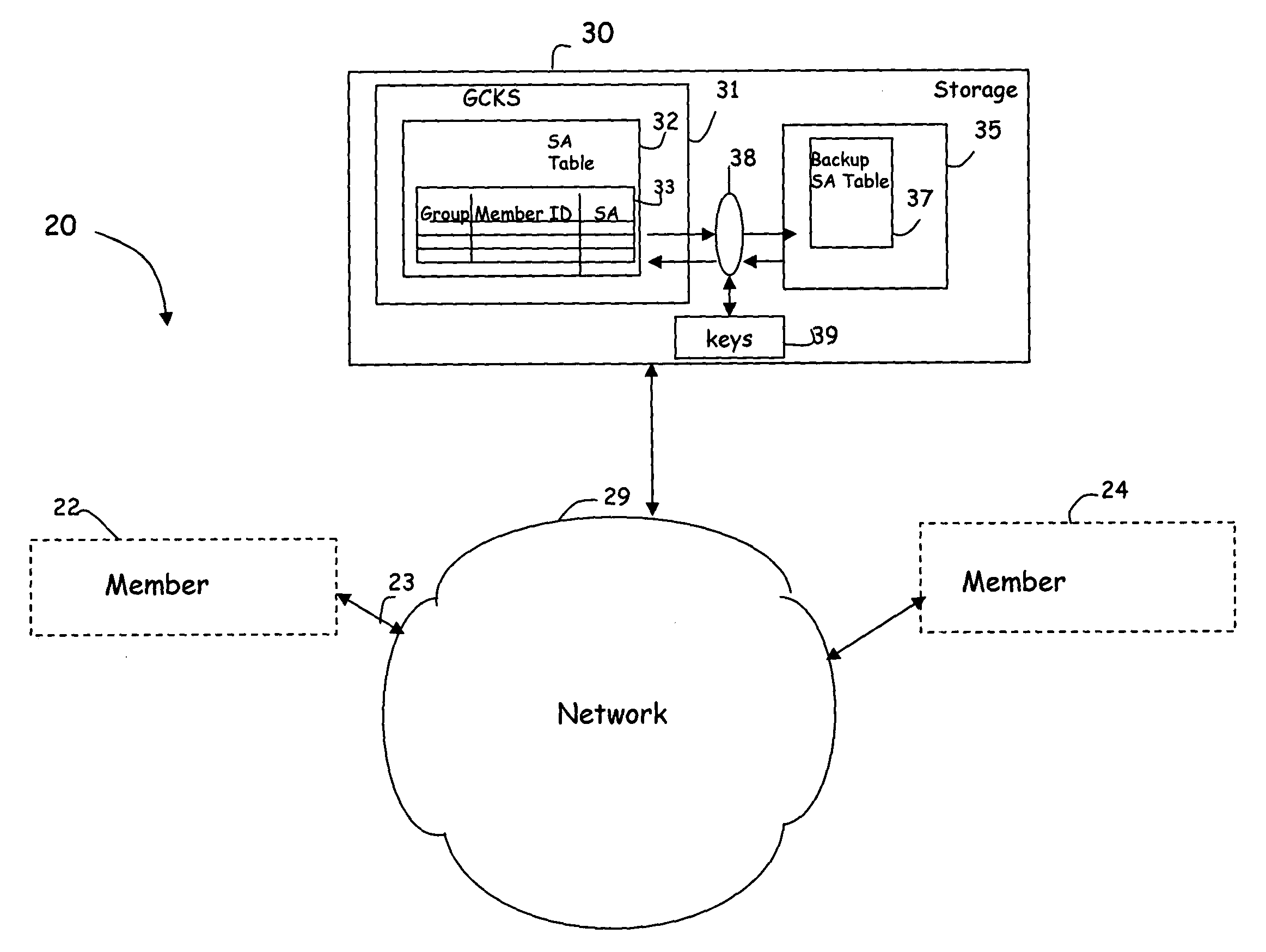
[0011]FIG. 1 illustrates a system 20 illustrating a number of members 22 and 24 coupled to a server 30 via a communications network 29. The system of FIG. 1 is a generic system, and the members may be any type of device that is capable of receiving controlled data content, including a television, computer, wire-less device, etc. Thus, the network 29 may be any type of network, whether it is cable based, ISDN based, wireless or some combination thereof operating according to any communication protocol. Exemplary members include, for example, members of a private computer network who share a private network, or a cable consumers who receive content via a pre-paid service arrangement, such as pay-per-view, etc.
[0012]The server 30 is shown to include a Group Controller / Key Server (GCKS) 31 and storage 35. The server 30 that includes the GCKS 31 functionality is illustrated as a distinct entity. However, the present invention is not limited to any particular implementation or placement o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com