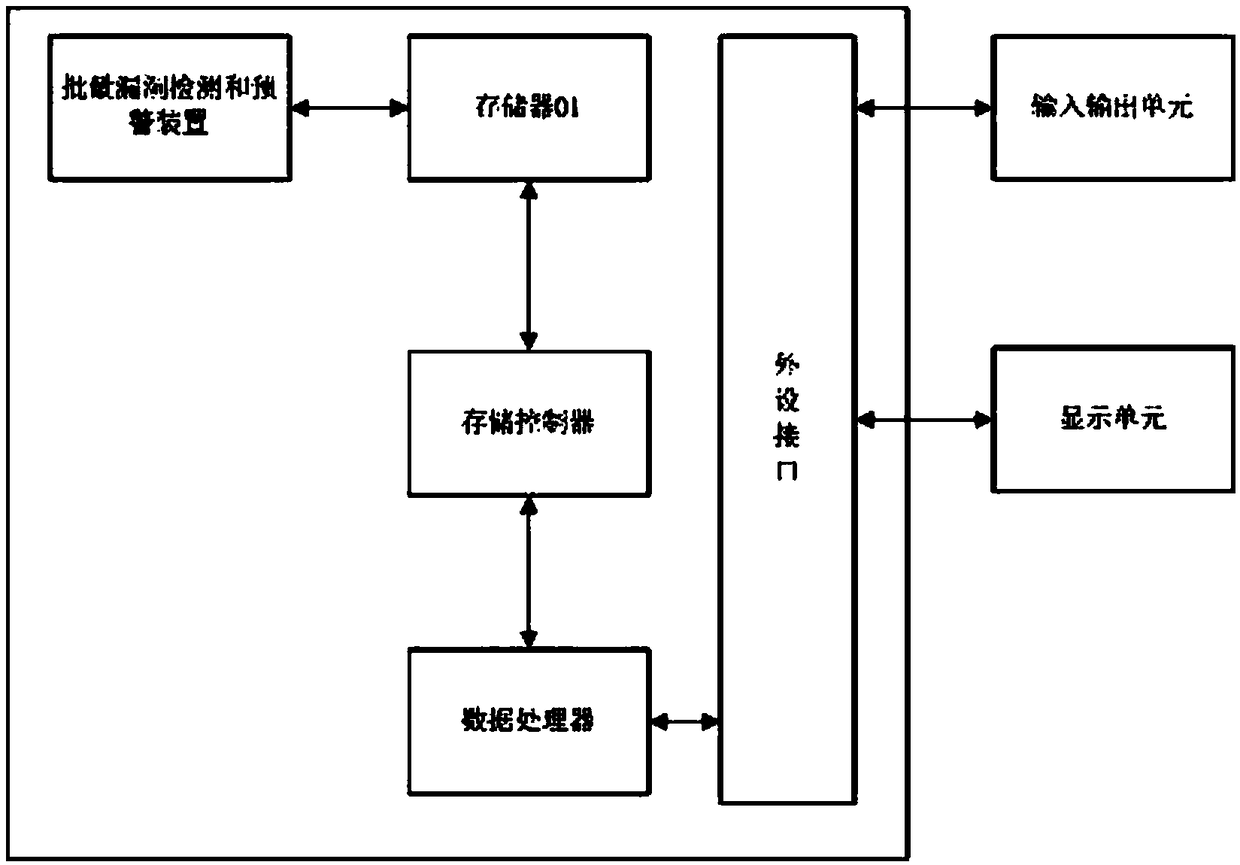
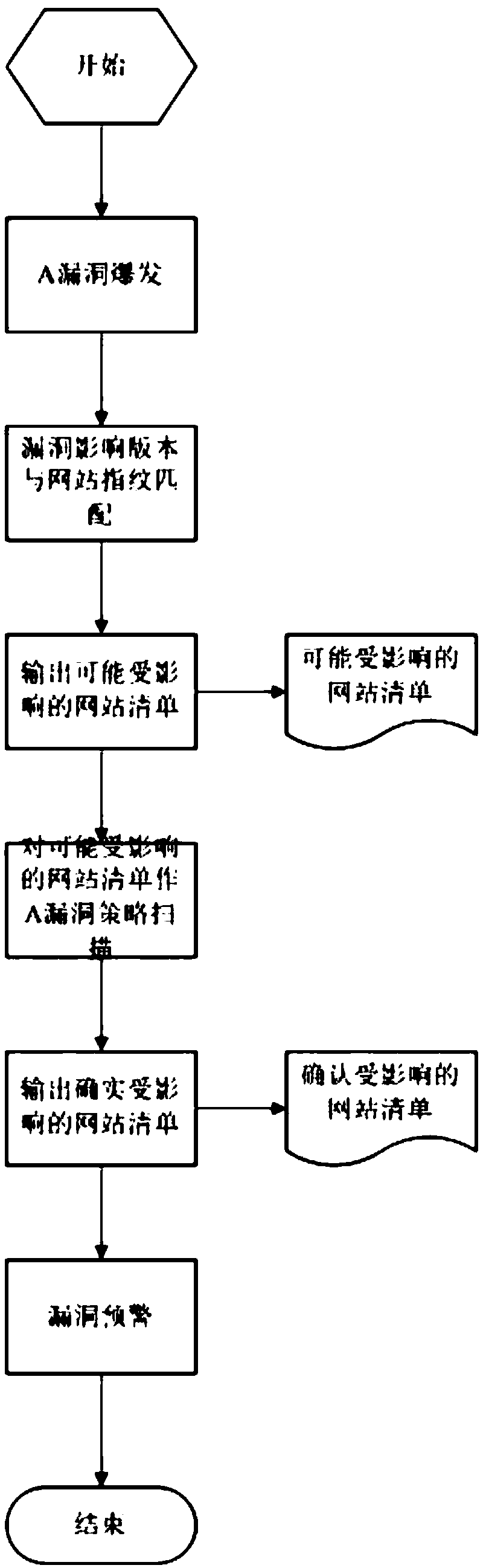
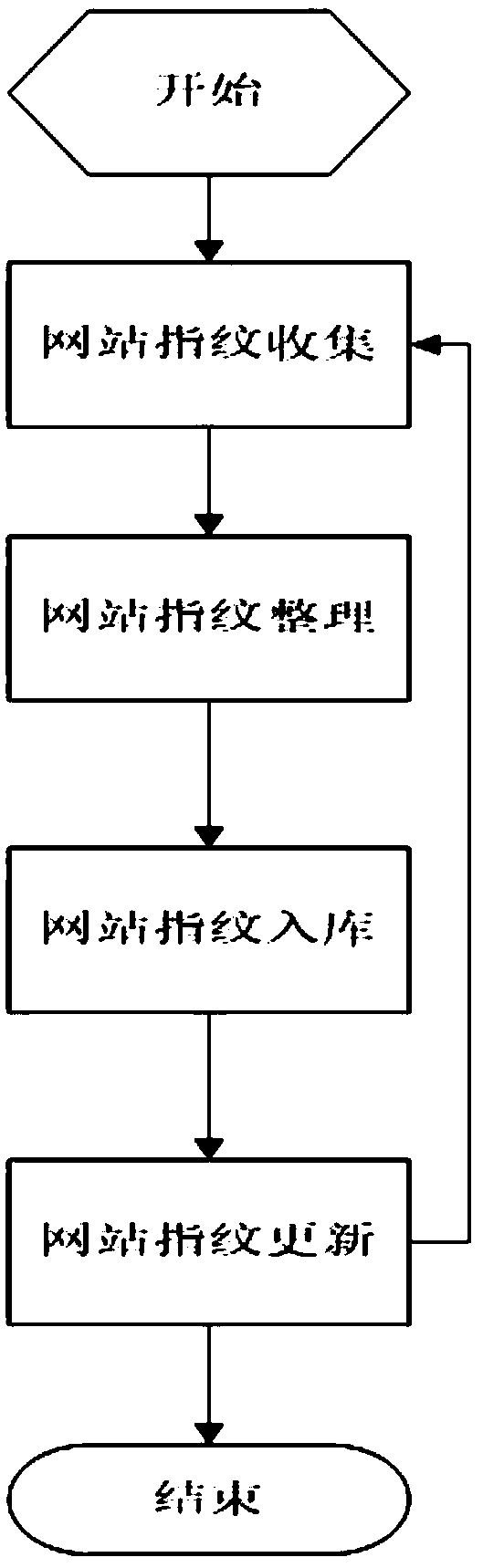
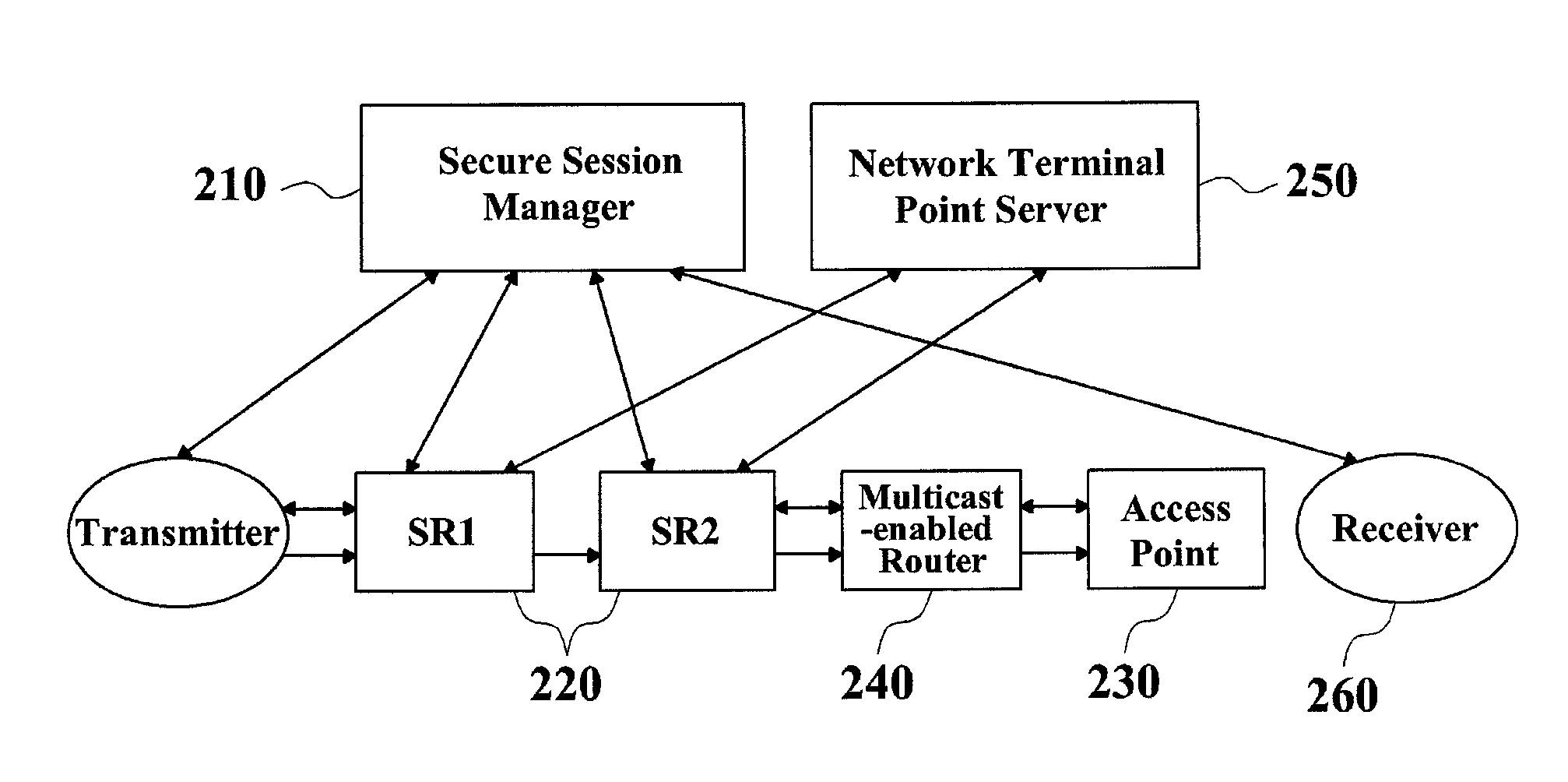
Patents
Literature
33results about How to "Address security threats" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
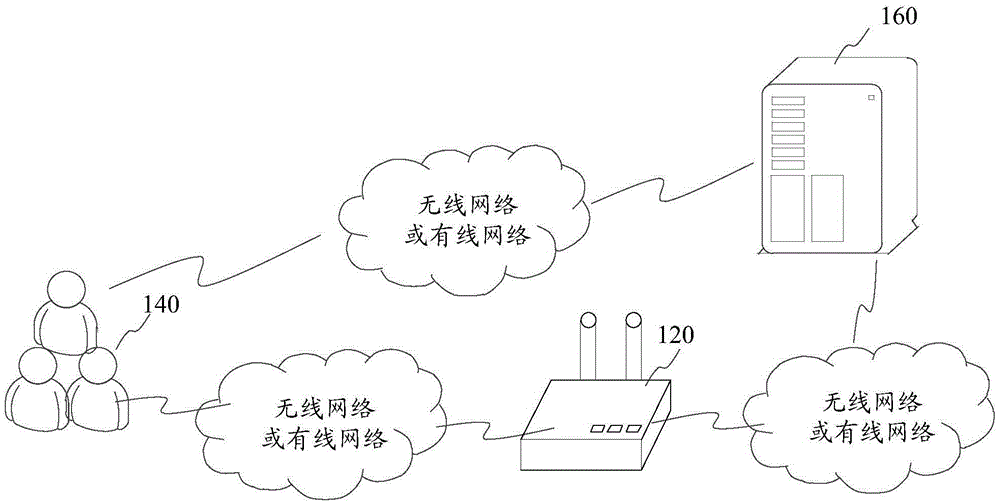
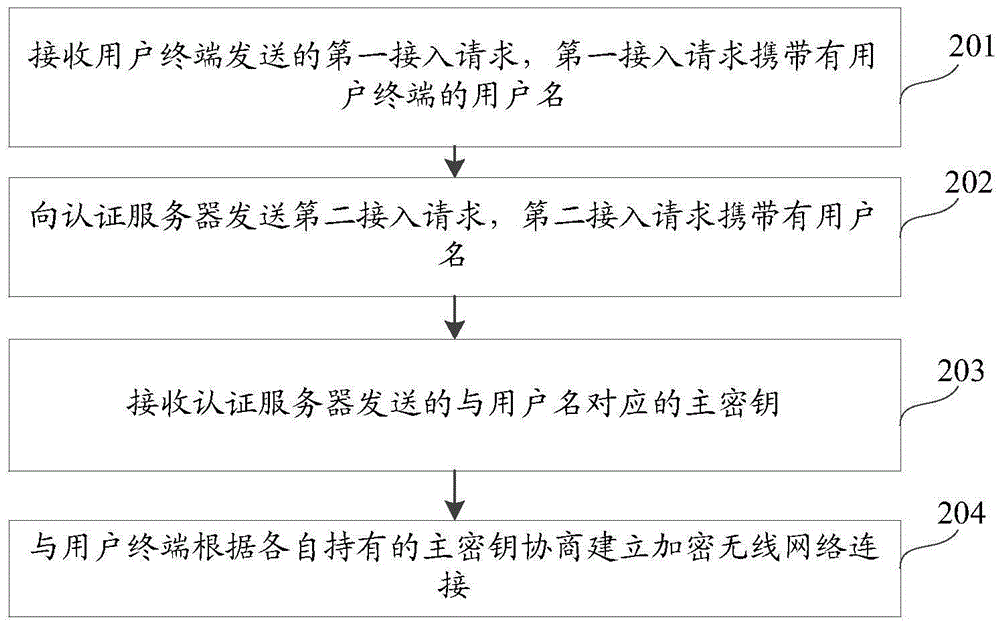
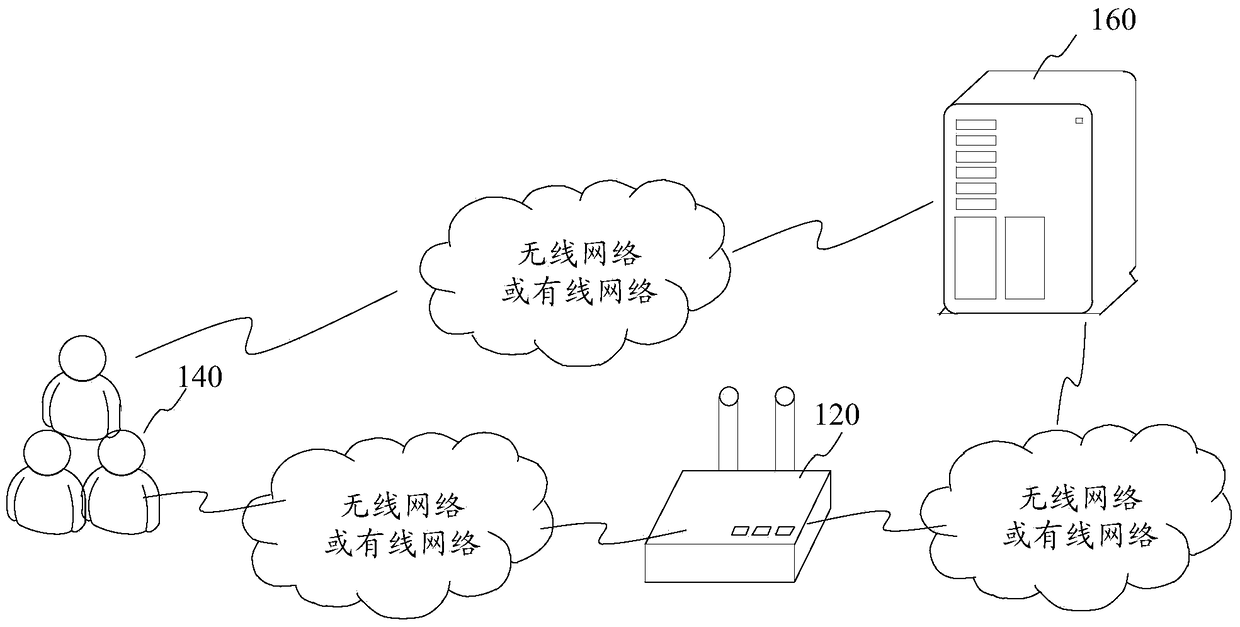
Wireless network connecting method, device and system
ActiveCN105554747AAddress security threatsImprove data securityConnection managementTransmissionWi-FiNetwork connection
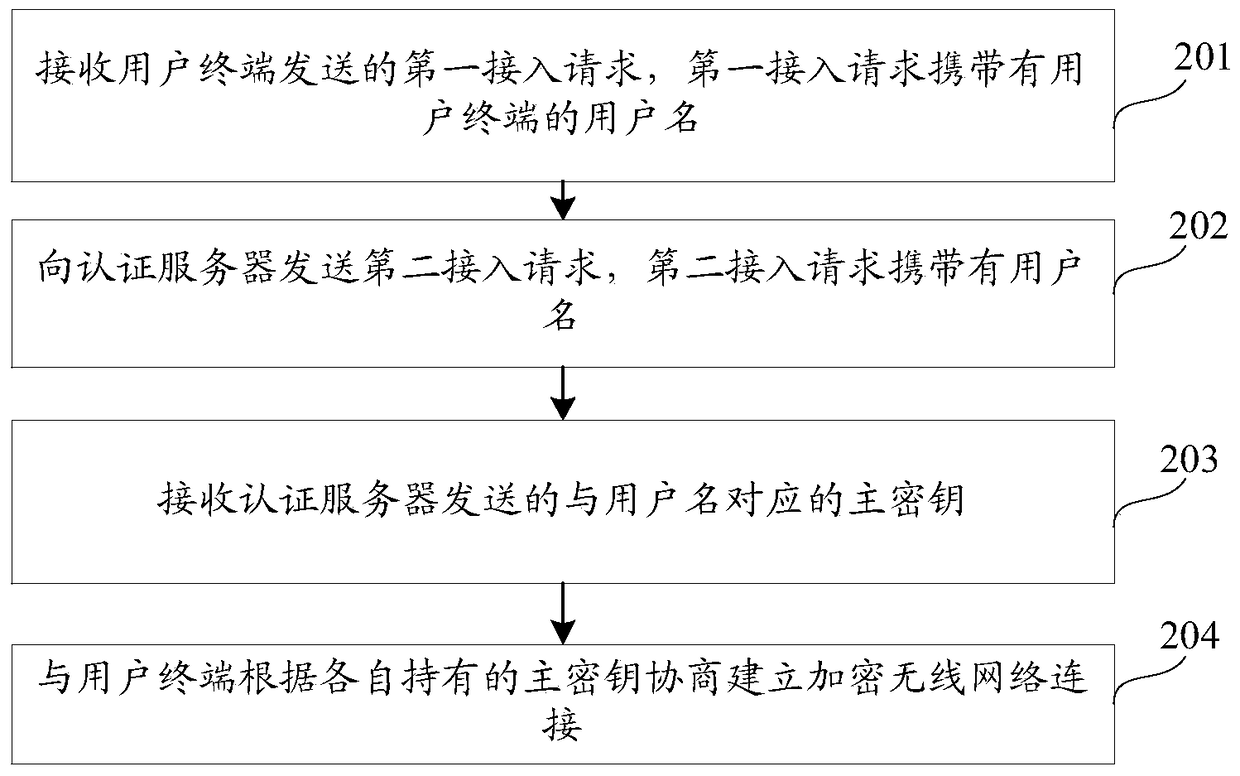
The embodiment of the invention discloses a wireless network connecting method, device and system belonging to the network security field. According to the invention, a first access request is sent to a wireless access point; an authentication server sends a second access request; whether the wireless access point belongs to a trust wireless access point is authenticated, when the wireless access point belongs to the trust wireless access point, first identity authentication is carried out with a user terminal, a main secrete key is generated through negotiating with the user terminal; the main secrete key corresponding to a user name is sent to the wireless access point; an encrypted wireless network connection is built by negotiating with the user terminal according to the main secrete key; the problems that the data transmitted to the counterfeit public Wi-Fi by the user terminal and the data in the user terminal are in security threat are solved; only the trust wireless access point can obtain the secrete key corresponding to the user name; therefore, the encrypted wireless network connection is built by negotiating with the user terminal according to the main secrete key; the data security of the data transmitted by the user terminal and the data in the user terminal is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
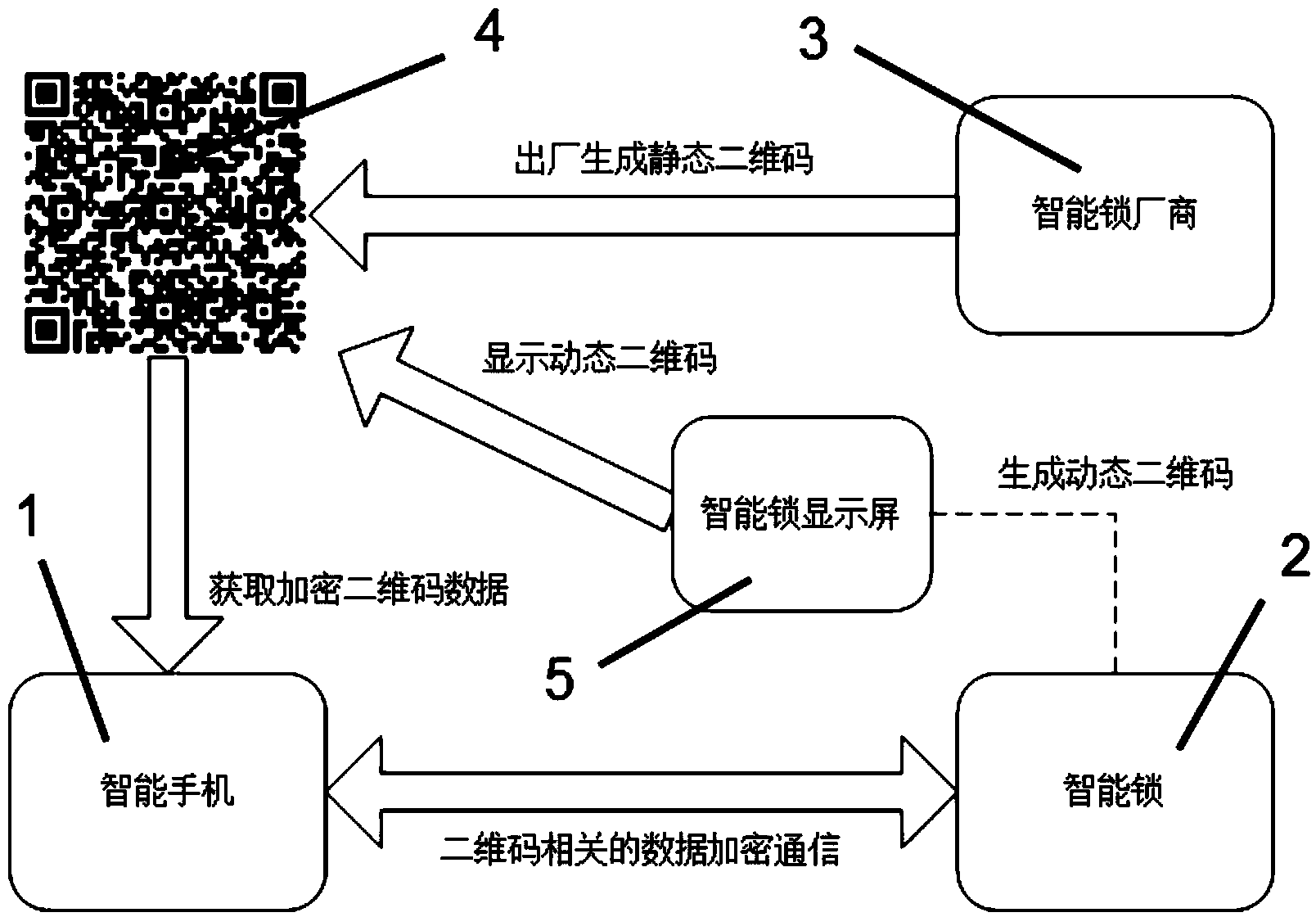
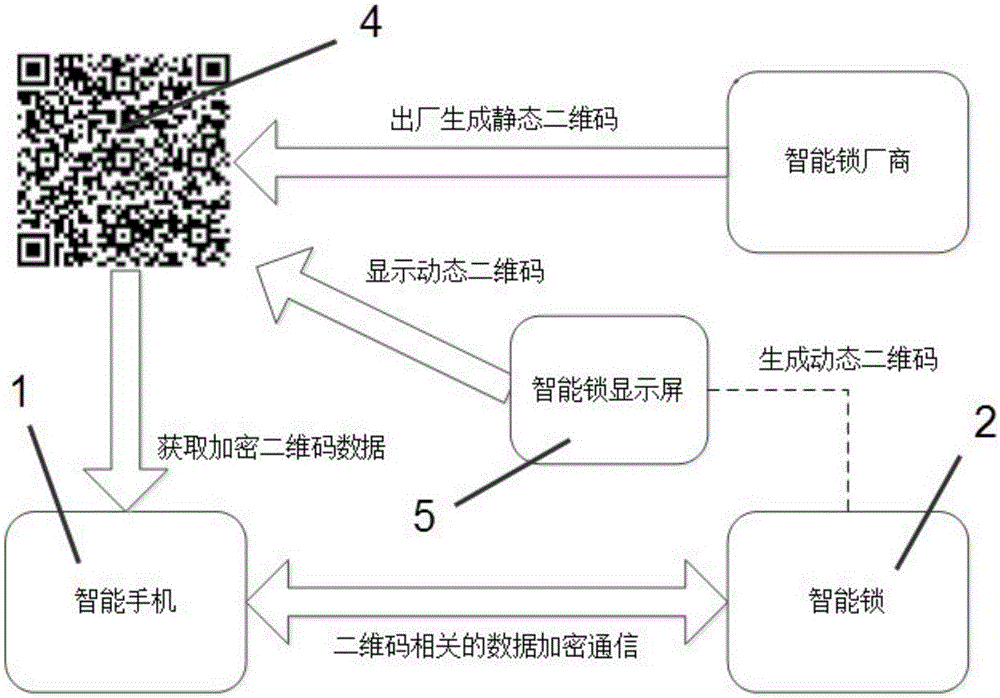
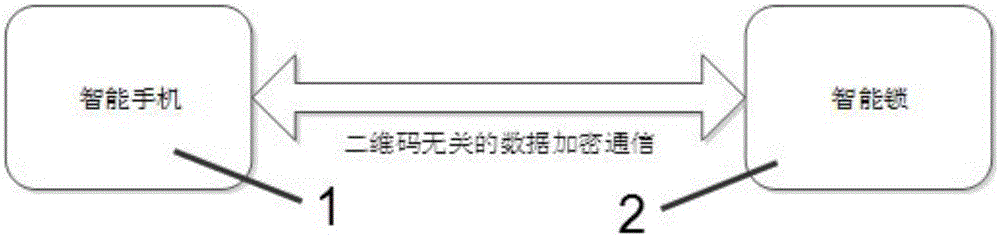
Intelligent lock device and usage method thereof as well as configuration method for electronic keys
ActiveCN103646455AFix security issuesSecurity issues do not existIndividual entry/exit registersComputer hardwareSecure transmission
The invention discloses an intelligent lock device and a usage method thereof as well as a configuration method for electronic keys. The configuration method for the electronic keys comprises the following steps: I, generating two-dimensional codes corresponding to a specific intelligent lock, wherein the two-dimensional codes comprise basic configuration parameters and enciphered messages of communication corresponding to the specific intelligent lock; II, scanning the two-dimensional codes by a mobile client side, decrypting and reading data in the two-dimensional codes; III, establishing a first security channel by the mobile client side through using the analyzed two-dimensional data and the intelligent lock; IV, mutually sending the key information and secrete key information, configured in the first security transmission channel, through the mobile client side and the intelligent lock, and storing the key information and secrete key information as electronic keys. The intelligent lock device has standard safety and is simple to use and convenient to operate.
Owner:深圳市诺赛特系统有限公司
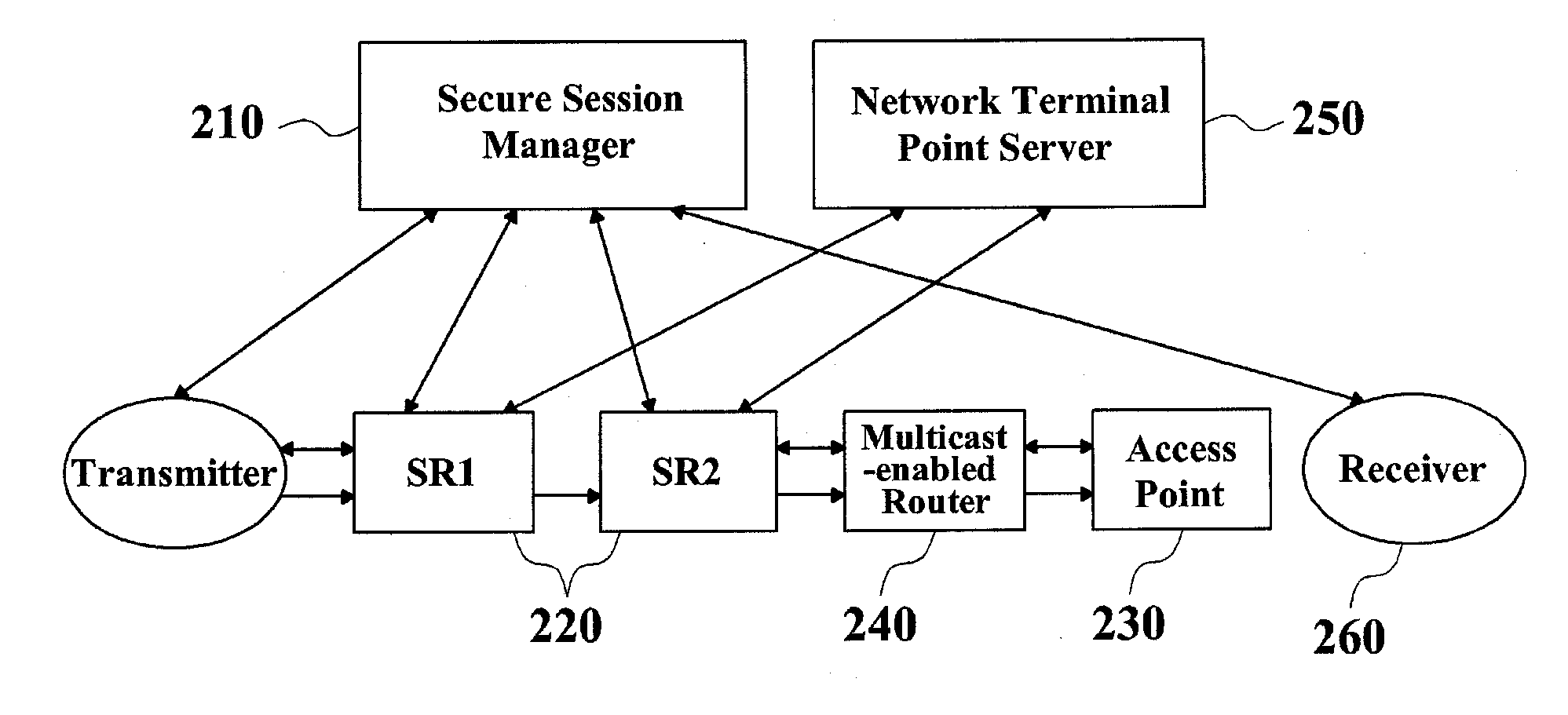
Method of Managing a Mobile Multicast Key Using a Foreign Group Key
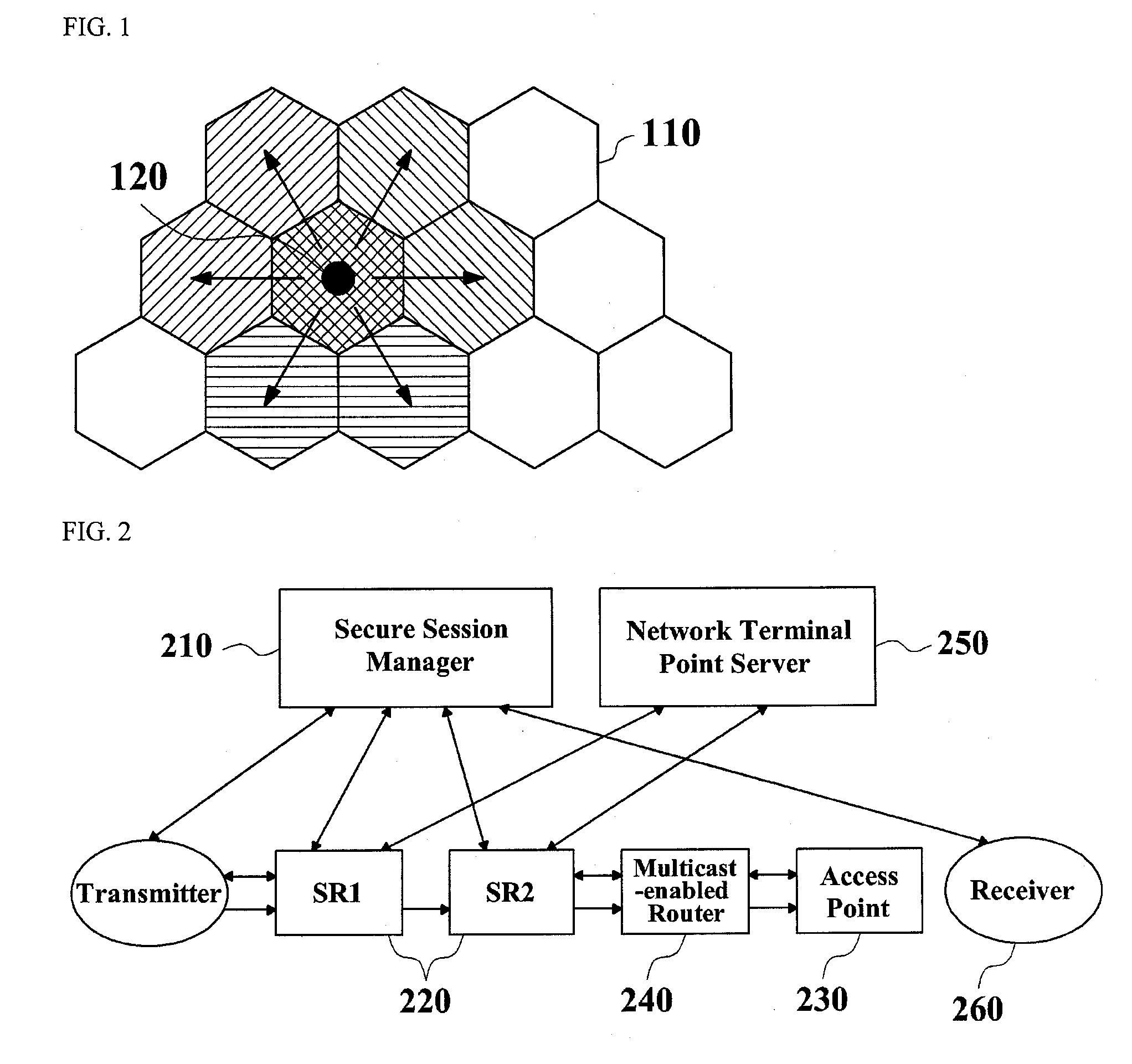
InactiveUS20080123856A1Address security threatsSecurity arrangementSecuring communicationSecure communicationMicrowave
The present invention relates to a method of managing a mobile multicast key using a foreign key. More specifically, the present invention relates to a method of managing a mobile multicast key using a foreign key for secure communication between a mobile terminal and a secure relay server in the region where microwaves from plural access points overlap.A method of managing a mobile multicast key using a foreign key according to the present invention has an advantage that multicast secure relay servers perform delegated authentication in advance in a region where microwaves overlap, thus reducing a delay time for authentication in a mobile terminal.And it has an advantage that it can minimize an effect from changes in group keys that user's movement make, by using a primary group key and a foreign key. This results in a reduction of an overhead from update of a group key while moving, and accordingly a reduction of a delay time.In addition, it has an advantage that it centralizes functions of key management to a secure relay server, thus overcoming the limitations on processing ability or network bandwidth of a mobile terminal.
Owner:KOREA INTERNET & SECURITY AGENCY
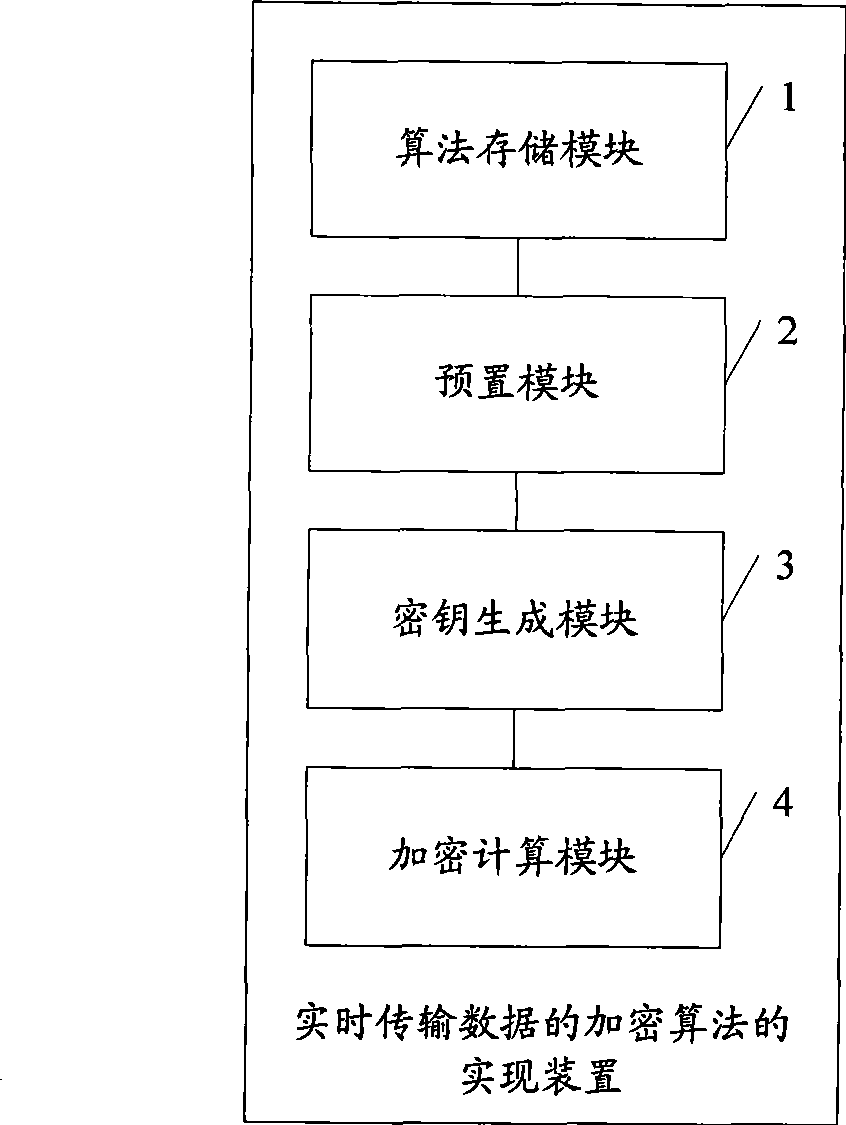
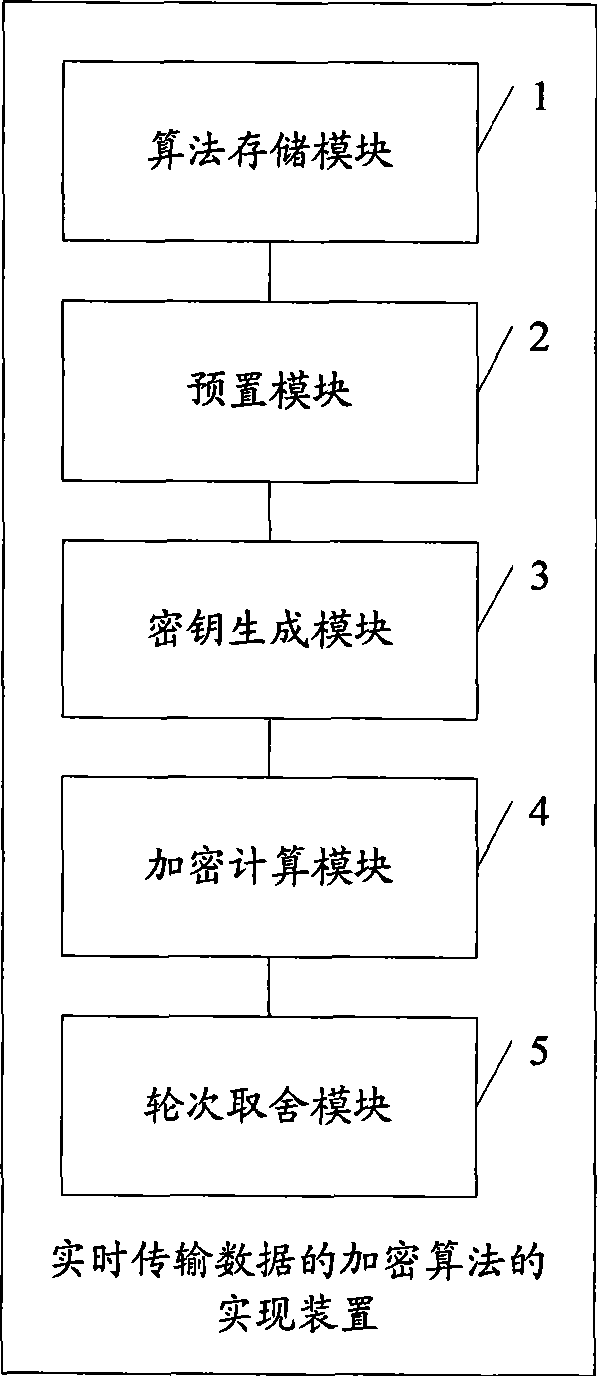
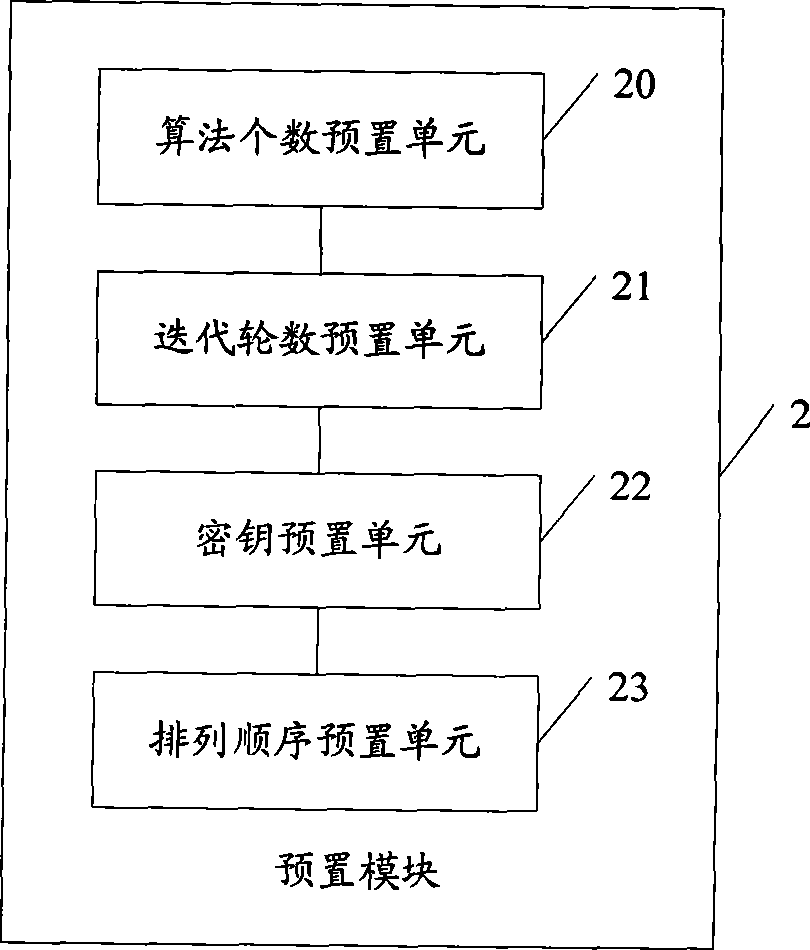
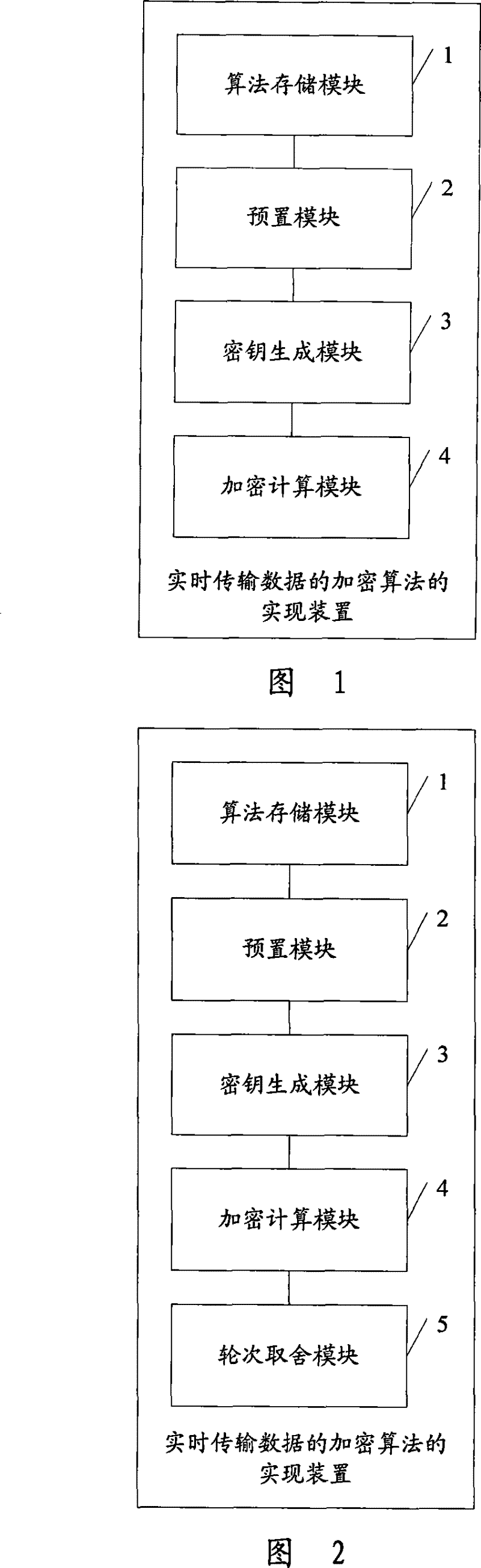
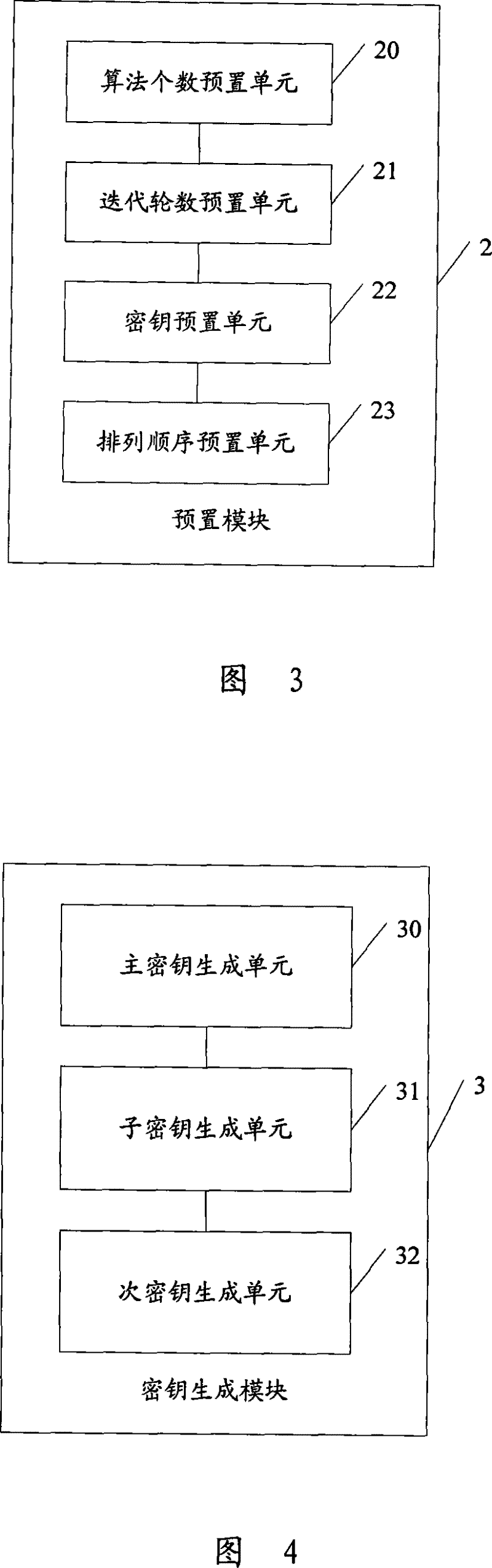
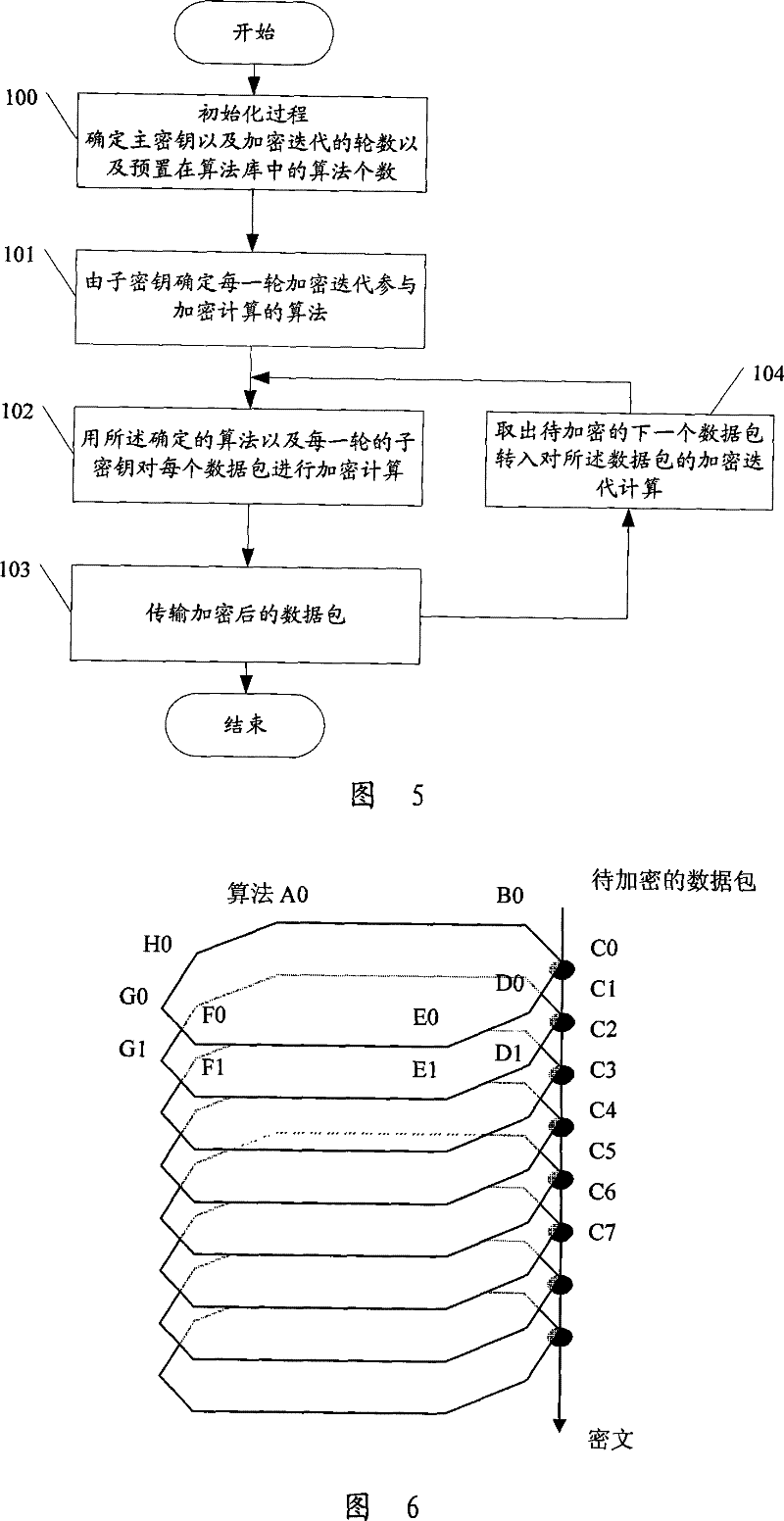
Implementation method and device for real-time transmission data encryption algorithm
InactiveCN101459510AAddress security threatsOvercoming the problem of low safety factorInterconnection arrangementsSecuring communicationComputer hardwareNetwork packet
The invention discloses a realization method for an encryption algorithm of real-time transmission data, which comprises determining the iterative rounds used to conduct the encryption algorithm for the real-time transmission data, selecting one of a plurality of algorithms in an algorithms library according to a key when in each round of encryption iteration, and conducting the encryption algorithm for real-time transmission data using the data pack as a unit by combining the key. The invention further discloses a realization device for the encryption algorithm of real-time transmission data. The method is adopted to overcome the problems of low security coefficient brought by the encryption and complexity of strong encryption, and realize the security encryption effect for the real-time transmission data, thereby solving various security threat problems faced by real-timely transmitted VoIP data.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
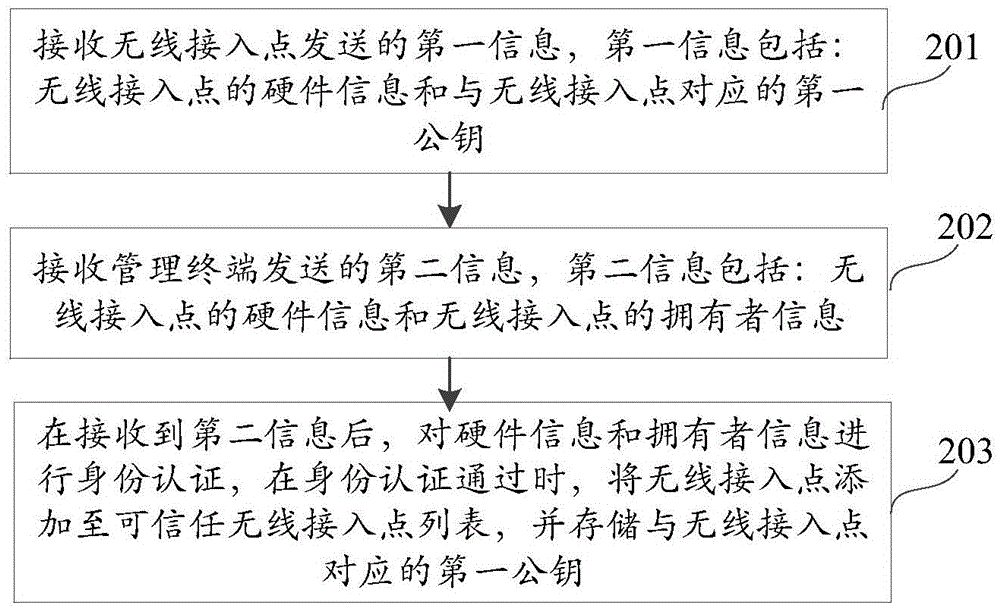
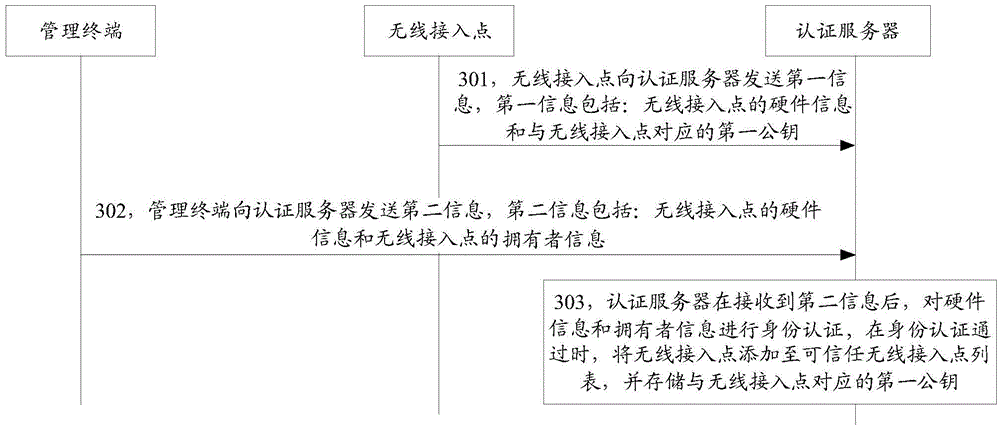
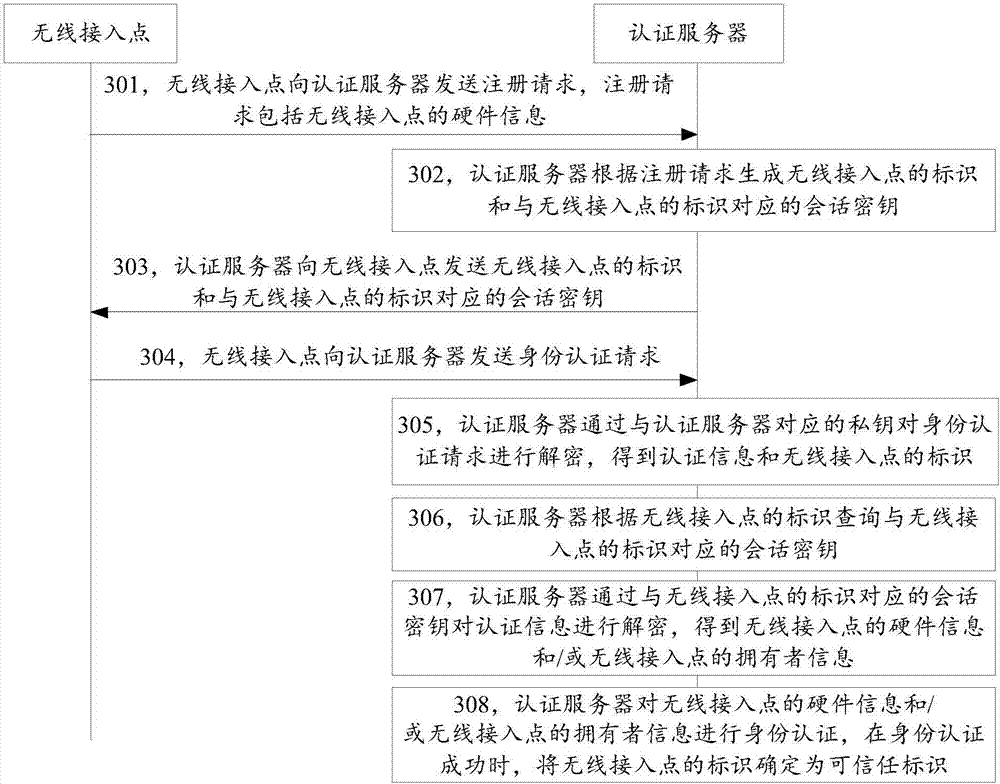
Wireless access point authentication method, device and system
ActiveCN105554760AAddress security threatsImprove data securityAssess restrictionSecurity arrangementWi-FiAuthentication server
The invention discloses a wireless access point authentication method, device and system belonging to the network security field. According to the invention, first information is sent to an authentication server through a wireless access point; a management terminal sends second information to the authentication server; after the authentication server receives the second information, the authentication server carries out identity authentication to hardware information and owner information, when the identity authentication is successful, the wireless access point is added in a trust wireless access point list; the problems that the existing authentication method and authentication server add the counterfeit public Wi-Fi as default trust public Wi-Fi, the data transmitted to the counterfeit public Wi-Fi by the user terminal and the data in the user terminal are in security threat are solved; the identity authentication is carried out to the wireless access point by the authentication server; therefore, only the actual wireless access point can pass through the identity authentication of the authentication server; the data security of the data transmitted by the user terminal and the data in the user terminal is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
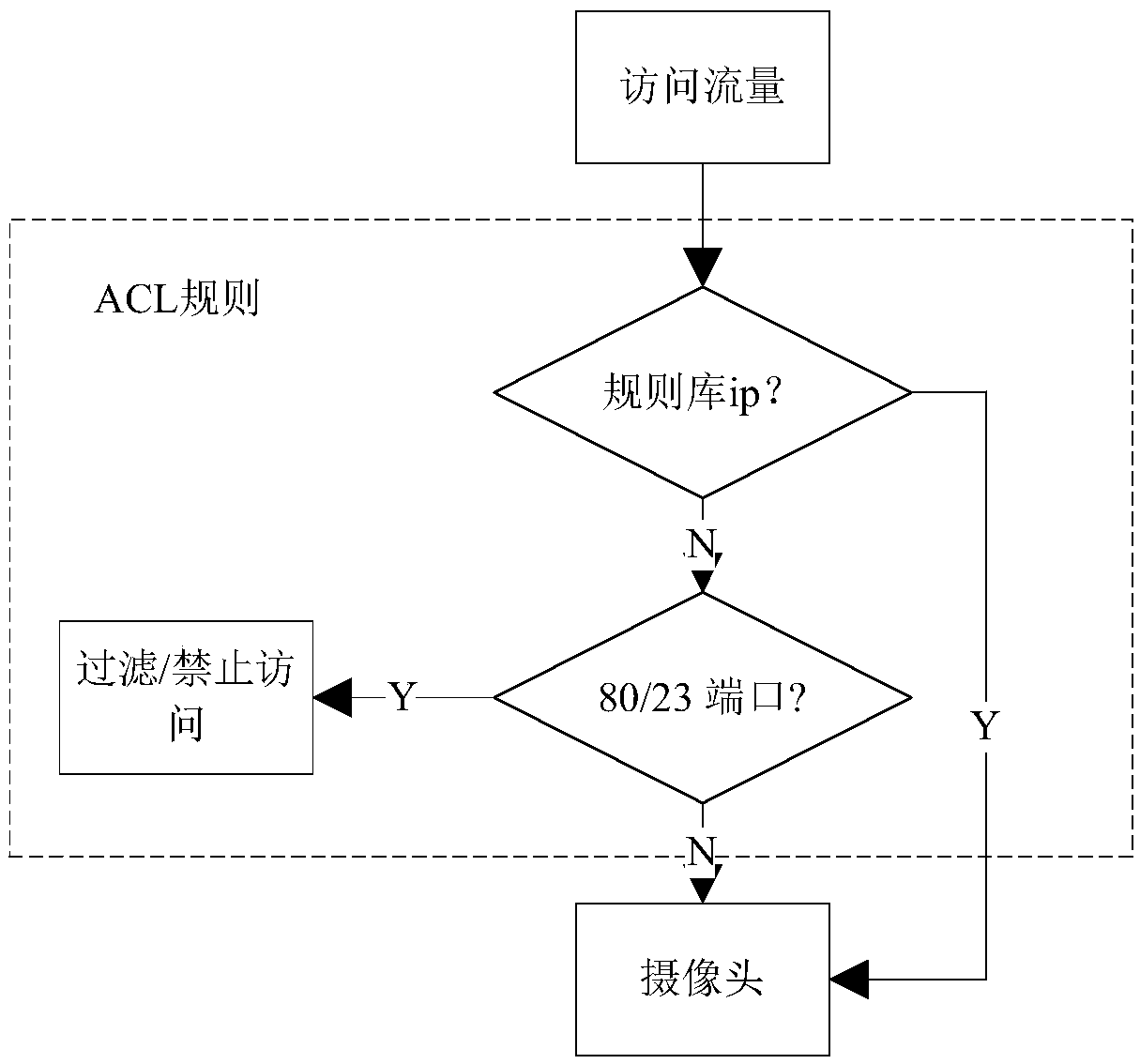
Defense method for configuring weak password vulnerability of internal and external network camera
The invention discloses a defense method for configuring weak password vulnerabilities of internal and external network cameras. A honeypot is arranged at a network end of the camera, and a public network end of the camera is accessed to the rear of a router to configure an access control list for the router. In an internal environment, ports 23 and 80 of the camera are exposed through the honeypot, and a scanned traffic packet is obtained, the source IP address of the scanned traffic packet is analyzed, and an intranet attack host is obtained through the honeypot when a camera vulnerability scan attack occurs. In an external network environment, all traffic accessing the camera is uniformly filtered by the router, and the IP address allowed to be accessed is released, otherwise prohibiting. According to the defense method for configuring weak password vulnerabilities of the internal and external network cameras, illegal requests of the external network are filtered by using a router ACL, and all external networks accesses do not need to be forbidden, thereby guaranteeing the functionality of the camera; and a Cowrie honeypot is used for internal network deployment, so that low false alarm rate is achieved, and intrusion method and flow of an attacker can be more clearly understood.
Owner:NANJING UNIV OF POSTS & TELECOMM
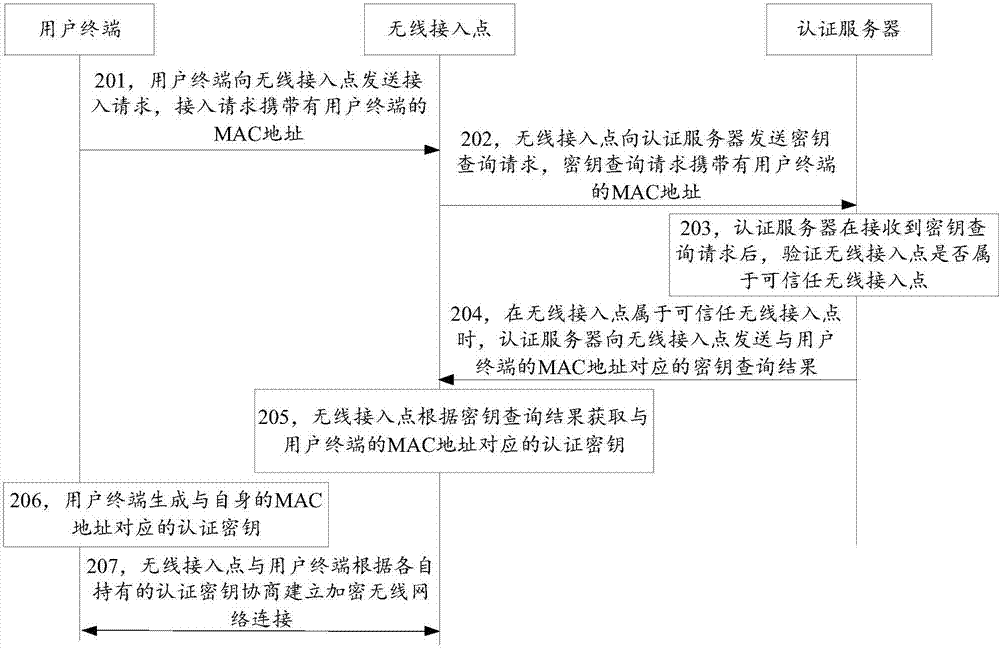
Wireless network connection method, device and system
ActiveCN107040922AAddress security threatsImprove data securityConnection managementTransmissionWi-FiComputer terminal
The invention discloses a wireless network connection method, device and system, belonging to the field of network security. The method comprises the following steps: a user terminal sends an access request to a wireless access point; the wireless access point sends a key query request to an authentication server; the authentication server sends a corresponding key query result to the wireless access point when the wireless access point belongs to a trusted wireless access point; the wireless access point acquires a corresponding authentication key; the user terminal generates an authentication key corresponding to the own MAC address; and the wireless access point and the user terminal negotiate to establish an encrypted wireless network connection according to the separately-owned authentication keys. According to the wireless network connection method, device and system disclosed by the invention, the problem that both the data transmitted to the fake public Wi-Fi by the user terminal and the internal data of the user terminal are subject to security threats can be solved; and only the trusted wireless access point can acquire the authentication key to establish the encrypted wireless network connection with the user terminal, and the effect of improving the security of the data transmitted by the user terminal and the internal data of the user terminal can be achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A method and a system for fast detection of bulk site vulnerabilities based on web fingerprints
InactiveCN109190380ARealize risk detectionEarly warningPlatform integrity maintainanceTransmissionData miningFingerprint
The invention relates to network security and provides a method and a system for rapid detection of bulk site vulnerabilities based on web fingerprints. The method for quickly detecting bulk site security vulnerabilities based on web fingerprints comprises the following steps: collecting and classifying target group fingerprints; matching vulnerabilities and the fingerprints, and screening out thesites which may have current vulnerabilities in the target site group; conducting site vulnerability detection to confirm the existence of the vulnerabilities. The method firstly quickly matches thecomponents and versions that are affected by the vulnerability and then carries out targeted vulnerability strategy scanning on the batch of possibly affected sites, thereby rapidly realizing site vulnerability risk detection, realizing site vulnerability early warning and safety response, and reducing the safety risk caused by site vulnerabilities.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Method of managing a mobile multicast key using a foreign group key
InactiveUS7864961B2Address security threatsSecurity arrangementSecuring communicationSecure communicationMicrowave
The present invention relates to a method of managing a mobile multicast key using a foreign key. More specifically, the present invention relates to a method of managing a mobile multicast key using a foreign key for secure communication between a mobile terminal and a secure relay server in the region where microwaves from plural access points overlap. A method of managing a mobile multicast key using a foreign key according to the present invention has an advantage that multicast secure relay servers perform delegated authentication in advance in a region where microwaves overlap, thus reducing a delay time for authentication in a mobile terminal and it has an advantage that it can minimize an effect from changes in group keys that user's movement make, by using a primary group key and a foreign key. This results in a reduction of an overhead from update of a group key while moving, and accordingly a reduction of a delay time. In addition, it has an advantage that it centralizes functions of key management to a secure relay server, thus overcoming the limitations on processing ability or network bandwidth of a mobile terminal.
Owner:KOREA INTERNET & SECURITY AGENCY
Content self-adaptive screen watermark display method
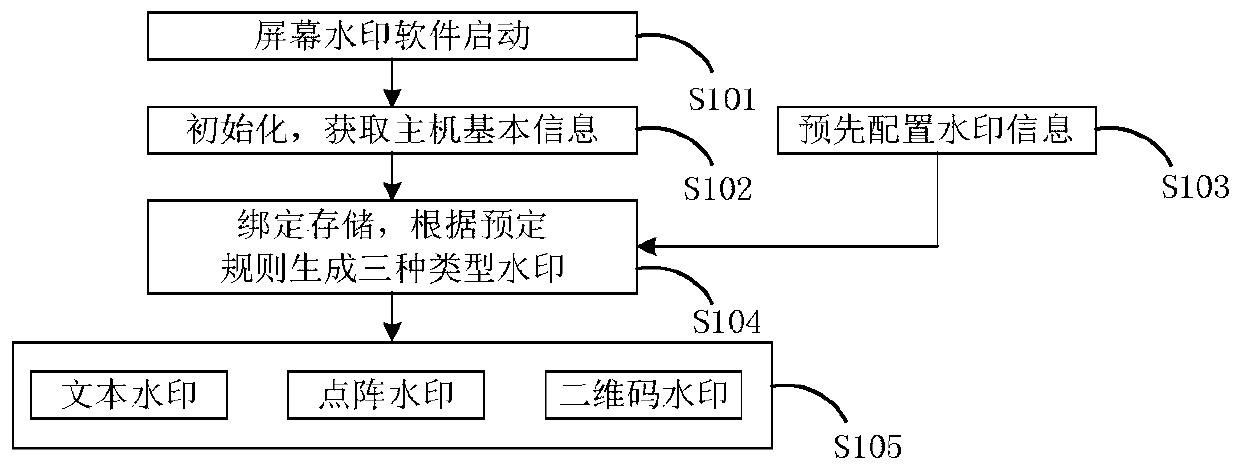
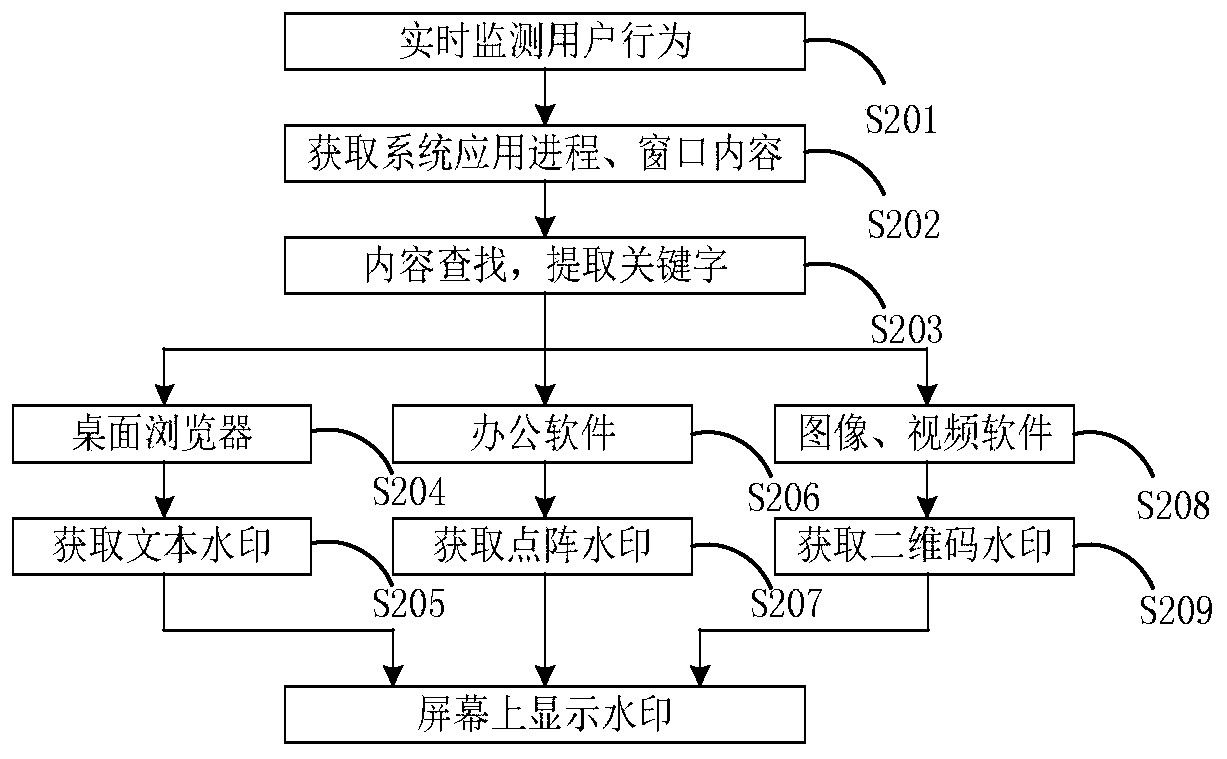
InactiveCN110362971AMonitor behavior in real timeReduce the impactImage data processing detailsProgram/content distribution protectionDot matrixContent Model
The invention discloses a content self-adaptive screen watermark display method. The method comprises: a screen watermark program monitoring computer operation behaviors of a user in real time; acquiring a current running program of the system and related contents in a program display window; searching the key content obtained by the operations, and extracting keywords / characters contained in thecontent; the screen watermarking program further determining the current running program and the attribute to which the related content in the display window belongs according to the contained keyword / word information; when the computer is in a system desktop or runs a browser program, displaying text watermarking on the screen; when the computer runs office software, displaying dot matrix watermarks on a screen; when the computer opens the picture or plays the video, displaying the two-dimensional code watermark on the screen. According to the method, the software running safety is improved,the influence of the screen watermark on the display content can be reduced, and the visual experience of a user is improved.
Owner:HANGZHOU DIANZI UNIV
Method and device for safety judgment based on consistency of expanded name and file format
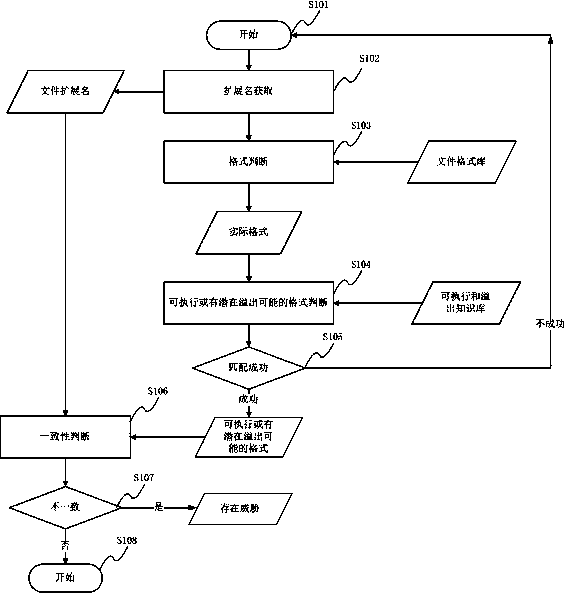
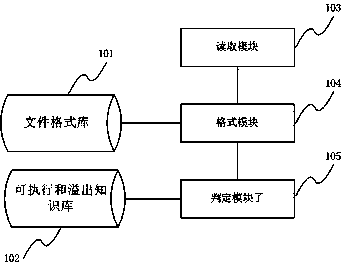
InactiveCN103544437AAddress security threatsImprove the detection ratePlatform integrity maintainanceAnti virusDocument security
The invention discloses a method and device for safety judgment based on the consistency of an expanded name and a file format. The method for safety judgment based on the consistency of the expanded name and the file format comprises the following steps that a format of an expanded name of an object file to be detected is obtained; the characteristics of the object file to be detected are extracted, matching is conducted on the characteristics of the object file to be detected and characteristics in a file format base, and if matching is successful, an actual format of the object file to be detected is recorded; comparison is conducted on the actual format of the object file to be detected and executable formats of an overflowing knowledge base, if comparison is successful, whether the actual format and the format of the expanded name are consistent is judged, and if the actual format and the format of the expanded name are not consistent, it is determined that a threat to the object file to be detected exists. By the adoption of the method and device for safety judgment based on the consistency of the expanded name and the file format, the defect that traditional anti-virus software cannot cope with the situation that detection is eluded through change of an expanded name is overcome, the method for safety judgment based on the consistency of the expanded name and the file format is put forward innovatively, the problem of a safety threat caused by change of the expanded name is effectively solved, and the detection rate of the anti-virus software is improved.
Owner:HARBIN ANTIY TECH
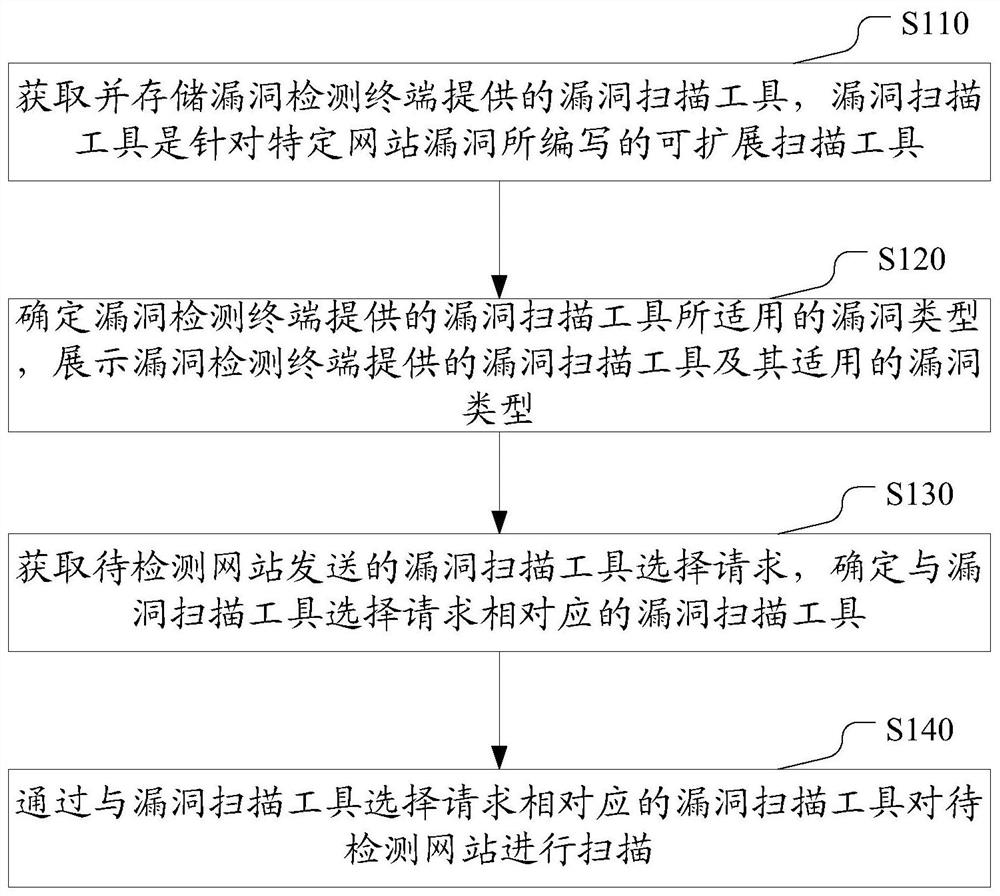
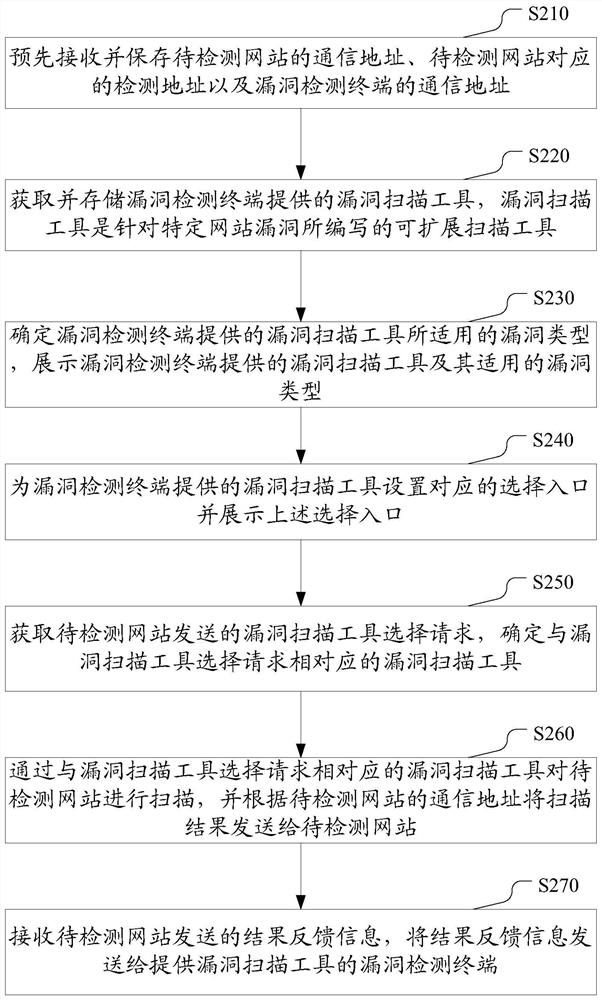
WEB vulnerability scanning method, apparatus and system
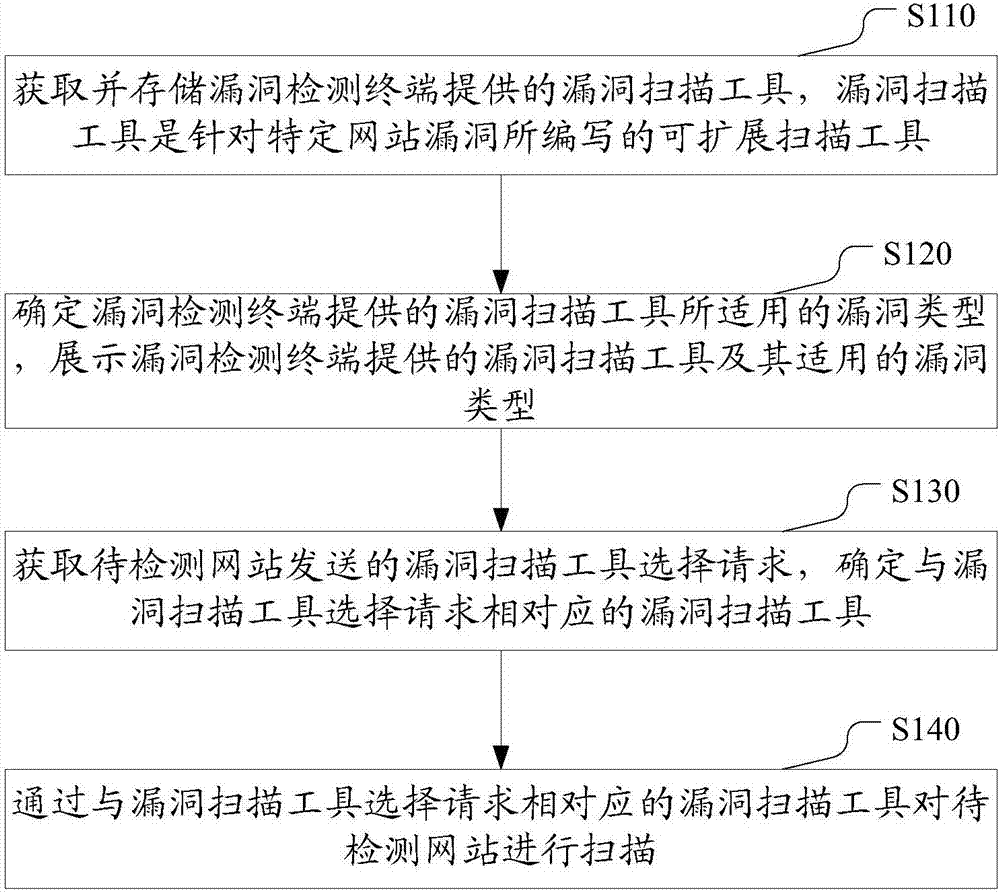
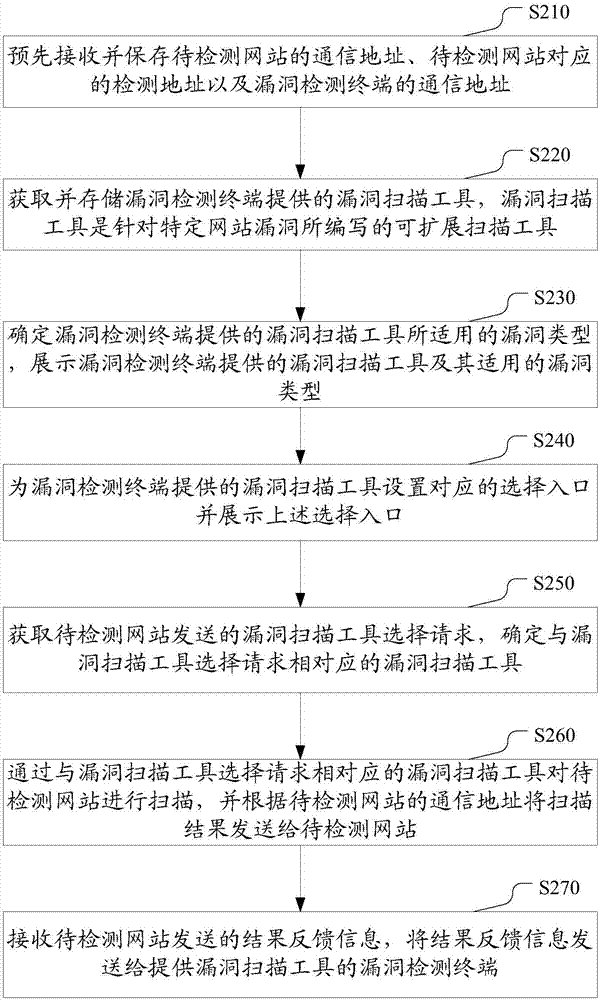
ActiveCN107046527AAddress security threatsMaintain securityTransmissionInternet usersComputer terminal
The invention discloses a WEB vulnerability scanning method, apparatus and system for at least solving the problem that the network information security of internet users is threatened due to the overlong interval time between the discovery and identification of vulnerabilities in the prior art. The WEB vulnerability scanning method comprises the following steps: obtaining and storing a vulnerability scanning tool provided by a vulnerability detection terminal, wherein the vulnerability scanning tool is an extensible scanning tool programmed for a specific website vulnerability; determining the applicable vulnerability type of the vulnerability scanning tool provided by the vulnerability detection terminal, and displaying the vulnerability scanning tool provided by the vulnerability detection terminal and the applicable vulnerability type; obtaining a vulnerability scanning tool selection request sent by a to-be-detected website, and determining the vulnerability scanning tool corresponding to the vulnerability scanning tool selection request; and scanning the to-be-detected website through the vulnerability scanning tool corresponding to the vulnerability scanning tool selection request.
Owner:BEIJING QIHOO TECH CO LTD +1
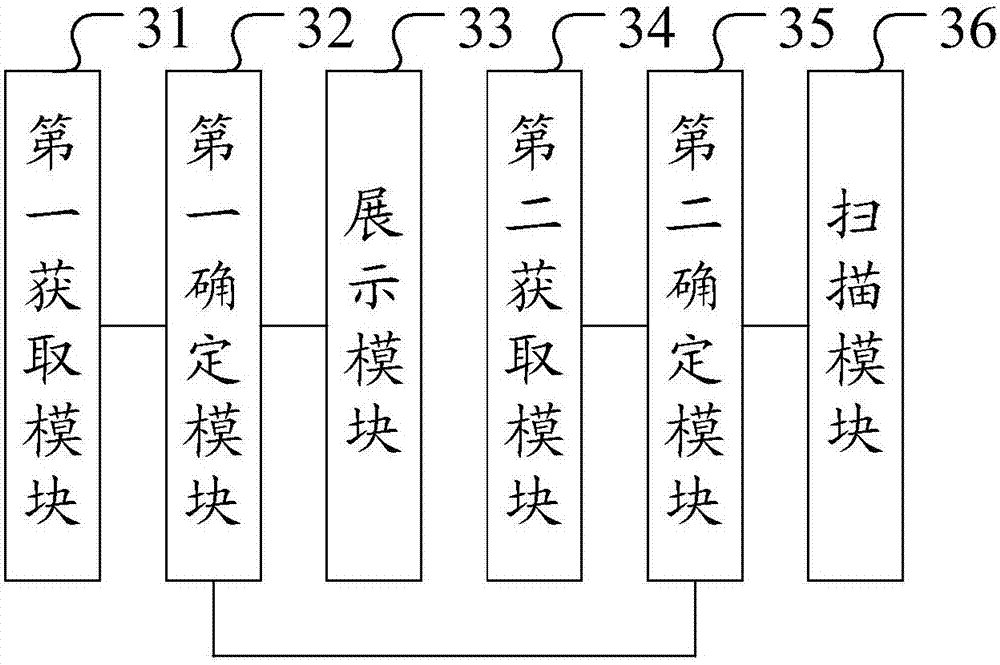
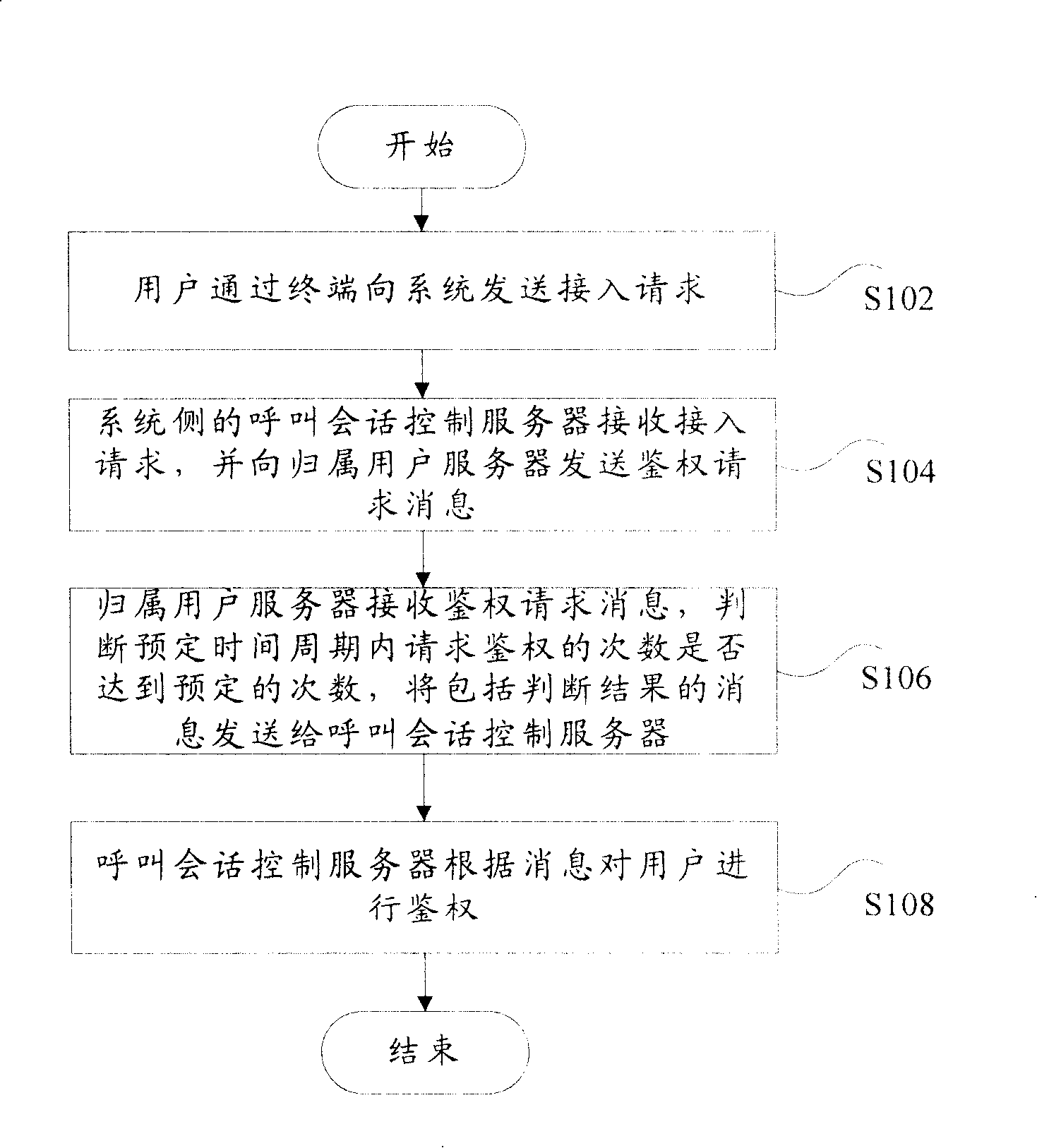
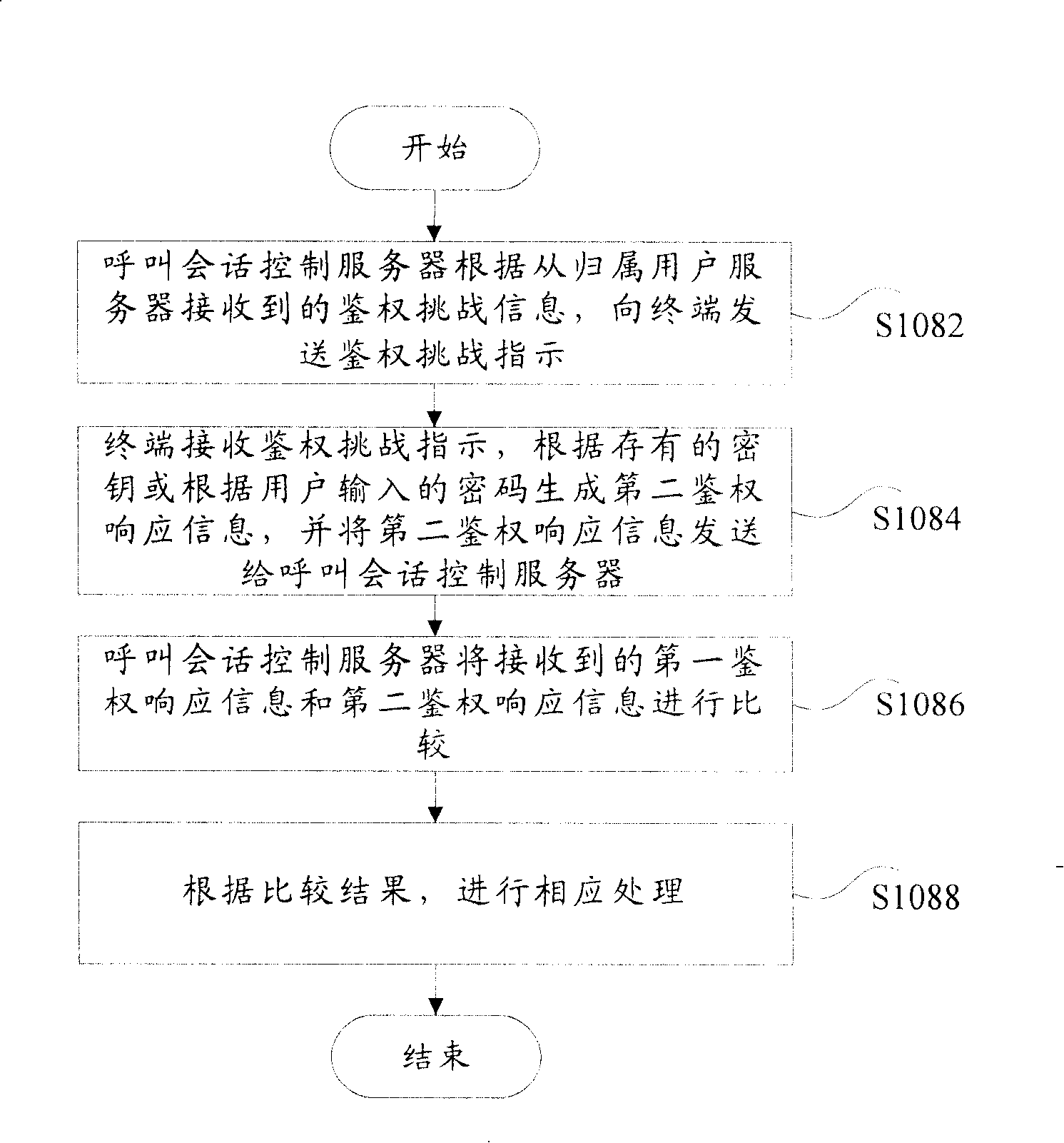
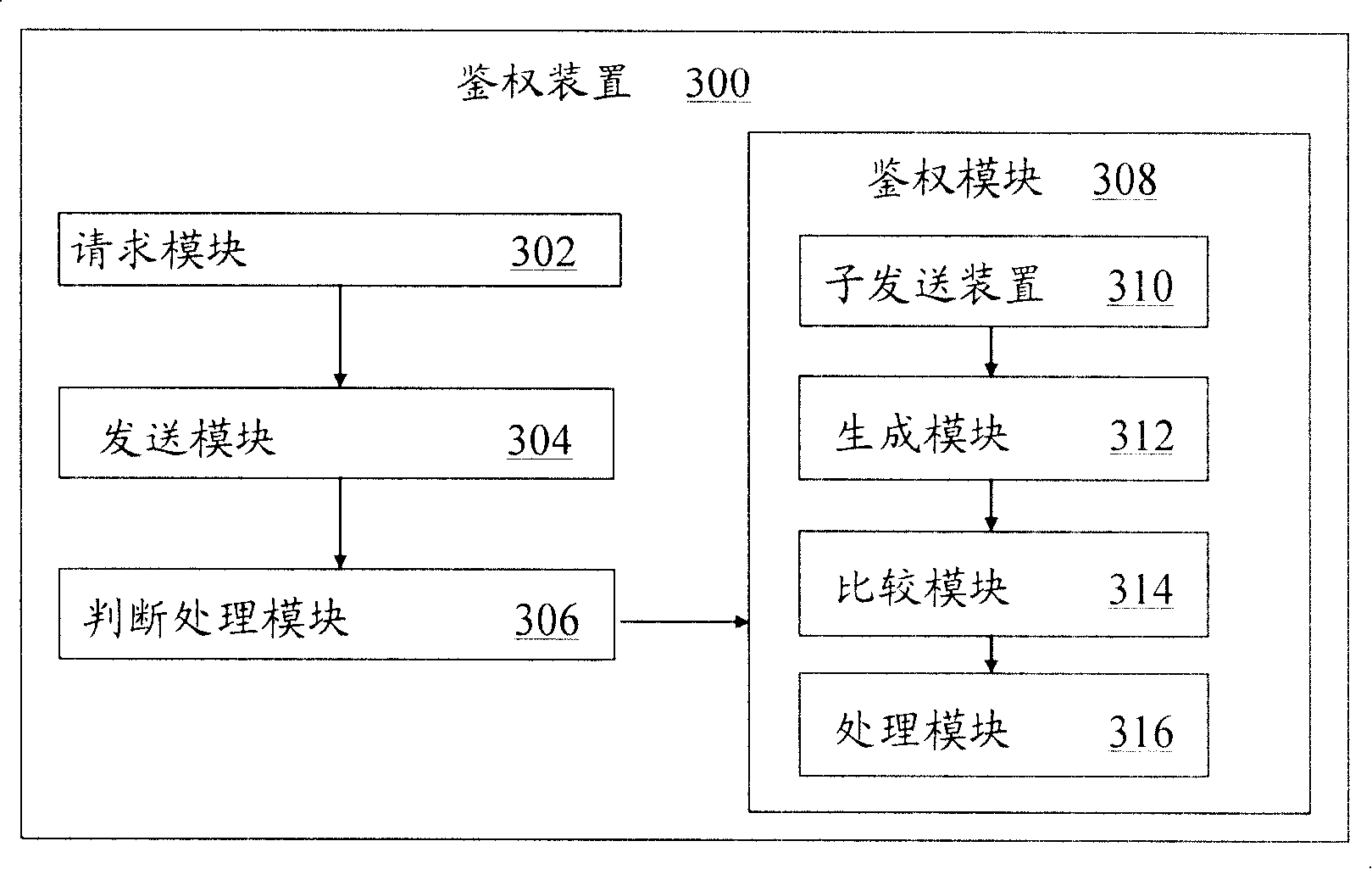
Authentication device in communication system
InactiveCN101197672AMaintenance rightsMaintain securityUser identity/authority verificationRadio/inductive link selection arrangementsCommunications systemSession control
The invention discloses an authentification method of a communication system. The device comprises a request module, a transmitter module, an identifying and processing module and an authentification module, wherein, the request module is used for the user to send an access request to a system through the terminal; the transmitter module is used for a call session control server on the system side to receive the access request and to send an authentification request message to an HSS; the identifying and processing module is used for the HSS to receive the authentification request message and to judge whether the times of the authentification request in a presetting time period are up to the presetting times as well as sending the message including the judged result to the call session control server; the authentification module is used for the call session control server to authenticate the user according to the message. The invention can maintain the authority and the security of a legal user and can have good compatibility.
Owner:ZTE CORP
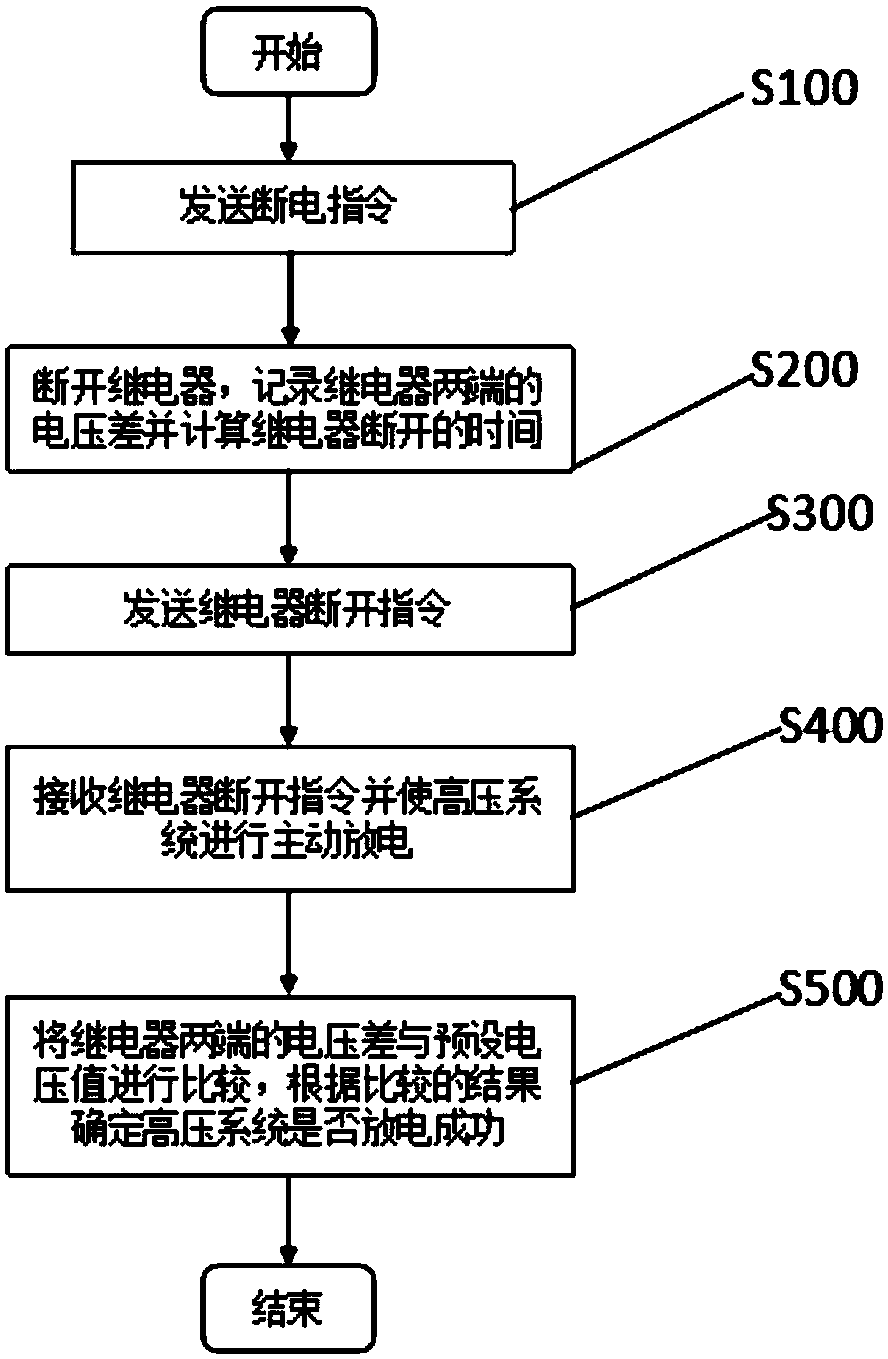
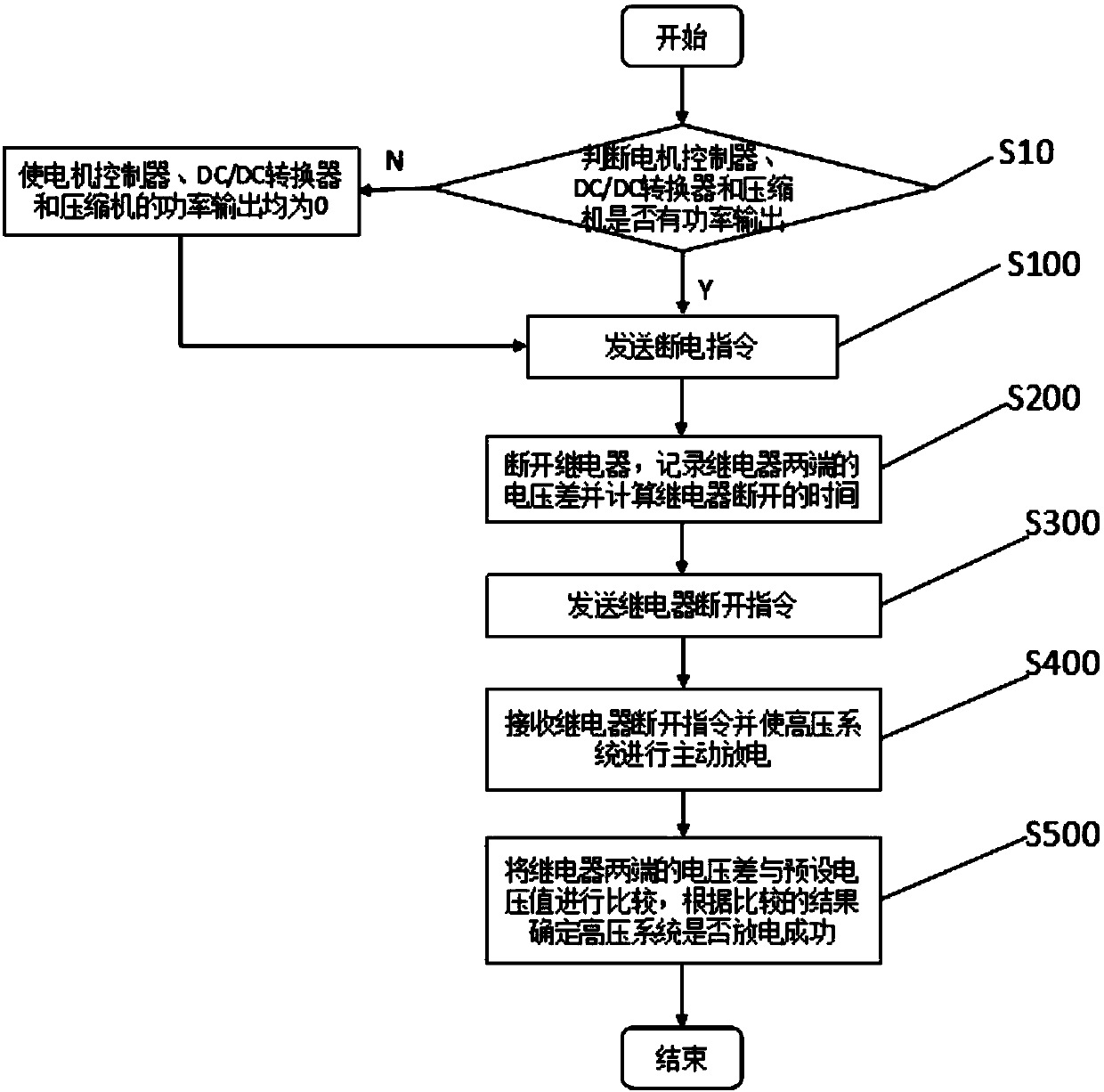
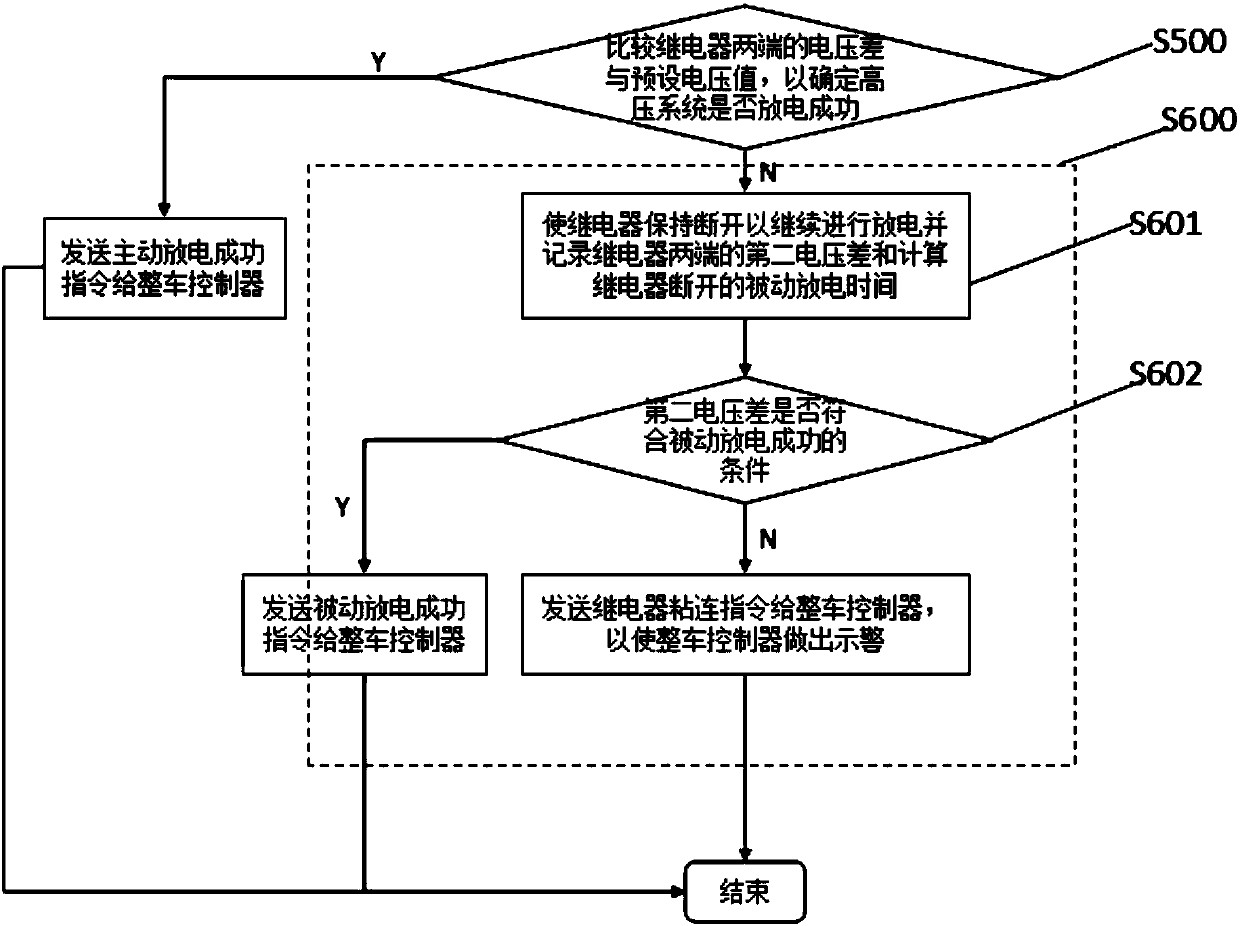
Control method and system for discharging of vehicle high-voltage system
InactiveCN108016298AAchieve reliefAddress security threatsSpeed controllerElectric devicesEngineeringHigh pressure
The invention provides a control method and system for discharging of a vehicle high-voltage system, and relates to the control field. The control method is used for achieving discharging of energy ofthe vehicle high-voltage system, and comprises the steps of sending a power outage instruction, disconnecting a relay according to the power outage instruction, recording the voltage difference of the two ends of the relay and calculating the disconnecting time of the relay, sending the disconnecting instruction of the relay, receiving the disconnecting instruction of the relay and enabling the high-voltage system to actively discharge, and comparing the discharging difference of the two ends of the relay with a preset voltage value to determine whether the high-voltage system discharges successfully or not. The control system comprises a vehicle controller, a battery management system and a motor controller. The control method and system for discharging of the vehicle high-voltage systemsolve the energy discharging problem of the vehicle high-voltage system.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
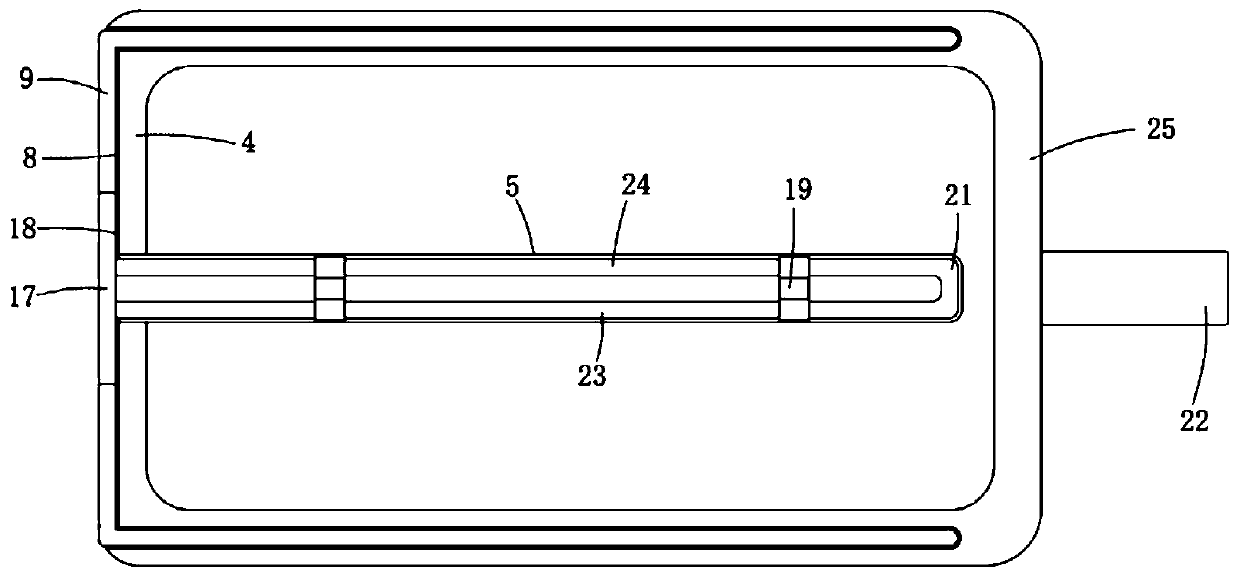
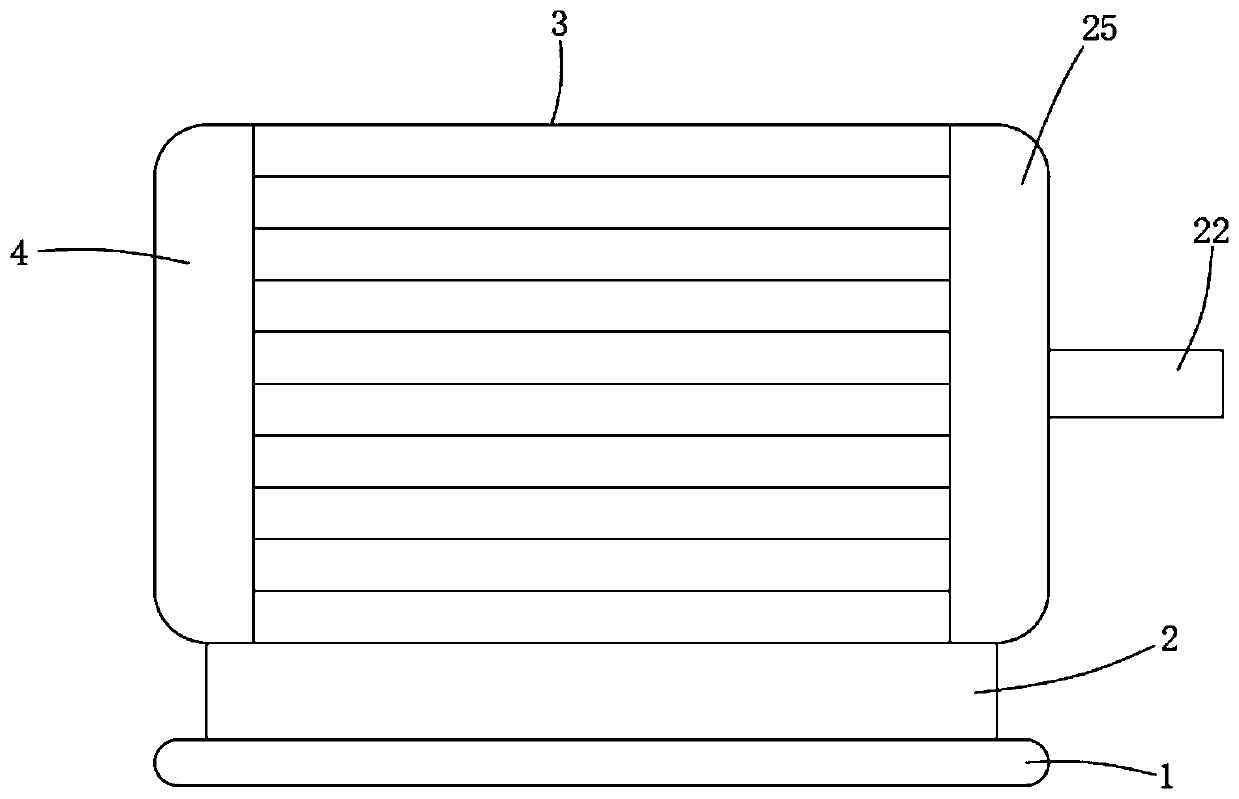
Explosion-proof three-phase asynchronous motor
ActiveCN110165833AAvoid damageAddress security threatsCooling/ventillation arrangementDrive shaftThree phase asynchronous motor
The invention belongs to the technical field of motors, and particularly relates to an explosion-proof three-phase asynchronous motor. The explosion-proof three-phase asynchronous motor comprises a motor casing, wherein the lower part of the motor casing is provided with supporting blocks, one side of the motor casing is provided with a front end cover, the front end cover is internally equipped with a driving shaft, the motor casing is provided with a back end cover at the side away from the driving shaft, the back end cover is provided with a first installation groove, the first installationgroove is internally equipped with an installation plate, the installation plate is equipped with a cooling device, the cooling device includes multiple sets of cooling pipes and a miniature circulating water pump, the installation plate is provided with a second installation groove, the miniature circulating water pump is installed in the second installation groove, and each cooling pipe includes a first cooling part and a second cooling part which are parallel to each other. In the invention, even if the cooling pipes are accidentally broken, the outflow cooling liquid will not flow into the inner part of the motor and much less touch the electric power components inside the motor, so that the normal use of the electric power components is guaranteed.
Owner:徐州亚泰电机有限公司
Web vulnerability scanning method, device and system
The invention discloses a WEB vulnerability scanning method, apparatus and system for at least solving the problem that the network information security of internet users is threatened due to the overlong interval time between the discovery and identification of vulnerabilities in the prior art. The WEB vulnerability scanning method comprises the following steps: obtaining and storing a vulnerability scanning tool provided by a vulnerability detection terminal, wherein the vulnerability scanning tool is an extensible scanning tool programmed for a specific website vulnerability; determining the applicable vulnerability type of the vulnerability scanning tool provided by the vulnerability detection terminal, and displaying the vulnerability scanning tool provided by the vulnerability detection terminal and the applicable vulnerability type; obtaining a vulnerability scanning tool selection request sent by a to-be-detected website, and determining the vulnerability scanning tool corresponding to the vulnerability scanning tool selection request; and scanning the to-be-detected website through the vulnerability scanning tool corresponding to the vulnerability scanning tool selection request.
Owner:BEIJING QIHOO TECH CO LTD +1
Adjustable soil shovel conveyor
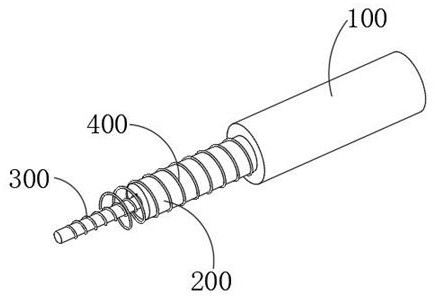
InactiveCN111926870AAddress security threatsAvoid deepMechanical machines/dredgersSoil scienceDrive wheel
The invention discloses an adjustable soil shovel conveyor which structurally includes a machine frame, a push rod arm, a driving wheel, a shovel bucket, and soil loosening mechanisms. The front end of the machine frame is connected with the push rod arm, and the driving wheel is arranged at and is connected with the bottom of the machine frame. The shovel bucket is located at one end of the pushrod arm, and the soil loosening mechanisms are arranged on the two sides of the shovel bucket. The adjustable soil shovel conveyor has the beneficial effects that first, a drill ring in the mechanismis used to be in contact with sandy soil during high-speed rotation and rub against with the sandy soil to destroy the stacking state of the sandy soil so as to enable the sandy soil to turn into a loose state; and second, a squeeze cone is used to break the pressure tension of an air pressure ball to trigger the high-pressure ejection of internal air to disperse the sandy soil covering parts, thesandy soil slide down naturally through the cooperation the air and the parts, the conveyor is prevented from going deep into a sandy soil coverage area, and the risk of being buried is minimized.
Owner:刘培泉
Distributed power station
InactiveCN106385223AGuarantee the safety of useAddress security threatsPhotovoltaic supportsPhotovoltaic energy generationArchitectural engineeringDistributed power
The invention discloses a distributed power station. The distributed power station comprises a house body and a photovoltaic assembly. The distributed power station is characterized by comprising a first support device, a second support device and an installation seat for installing the photovoltaic assembly; the bottom ends of the first support device and the second support device are abutted against the ground; the first support device and the second support device are arranged on the left side and the right side of the house body; the installation seat is arranged on the upper side of a roof of the house body, and the left end and the right end of the installation seat are fixedly connected to the first support device and the second support device; on the distributed power station, because the first support device and the second support device are arranged on the left side and the right side of the house body, the load bearing of the roof can be effectively reduced through the support of the first support device and the second support device and the safety of the house body can be guaranteed. Meanwhile, the front side and the back side of the house body can be effectively avoided and lighting inside the house body can be ensured. As a result, the distributed power station can effectively solve the safety threatening problem of the distributed power station house body in the prior art.
Owner:晶科电力科技股份有限公司
Wireless network connection method, device and system
ActiveCN105554747BAddress security threatsImprove data securityConnection managementTransmissionInternet privacyNetwork connection
Owner:TENCENT TECH (SHENZHEN) CO LTD
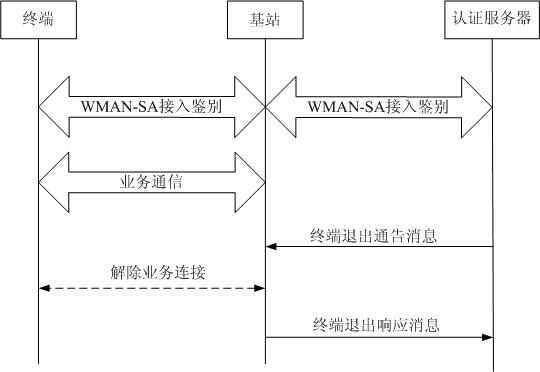
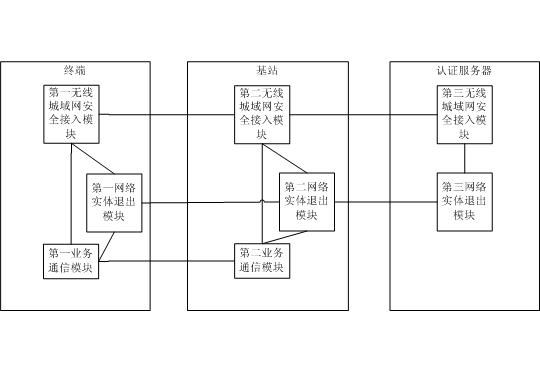
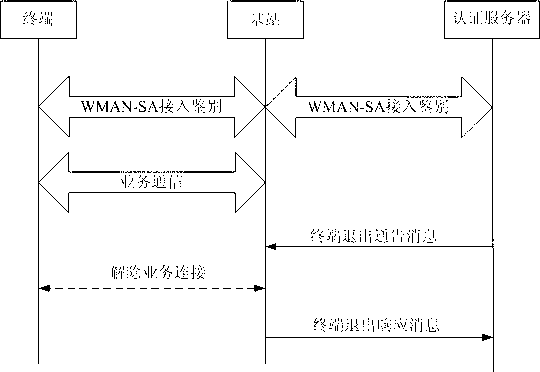
Method and system for WMAN (wireless metropolitan area network) entity exiting from network
InactiveCN101917718AAddress security threatsConnection managementSecurity arrangementWireless metropolitan area networkAuthentication server
The invention relates to the technical fields of wireless communication network and network security, in particular to a method and a system for a WMAN (wireless metropolitan area network) entity exiting from a network. The method of the invention comprises the following steps that: a terminal accesses a base station on the network side after passing the identification of an authentication server, and the authentication server records the IDs of the terminal and the base station and corresponding relationship thereof; a service communication is carried out between the base station and the terminal; the authentication server revokes the certificate of the terminal; the authentication server sends a 'notice information for terminal exit' according to the recorded local IDs of the terminal and the connected base station and corresponding relationships thereof; the base station removes the service connection with the terminal to be exited from the network, and interrupts the service communication; and the base station sends a 'response information for terminal exit' to the authentication server. In the invention, when the ID of some terminal of the wireless metropolitan area network fails, or some terminal is set as an illegal user by a manager, the method and the system of the invention can make the terminal timely exit from the communication network so as to ensure the safety ofthe communication network.
Owner:GCI SCI & TECH
Control method, control module and automobile
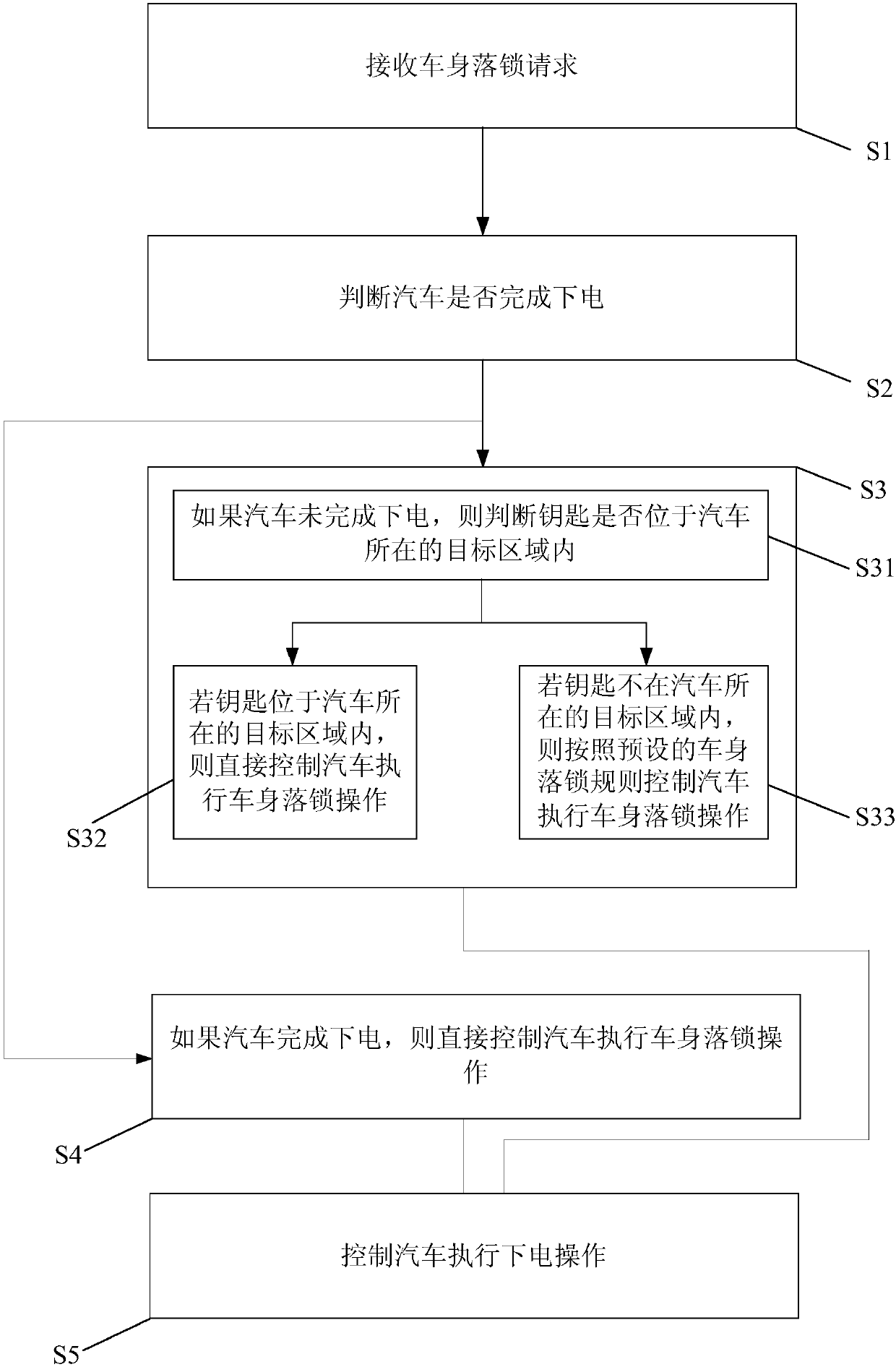
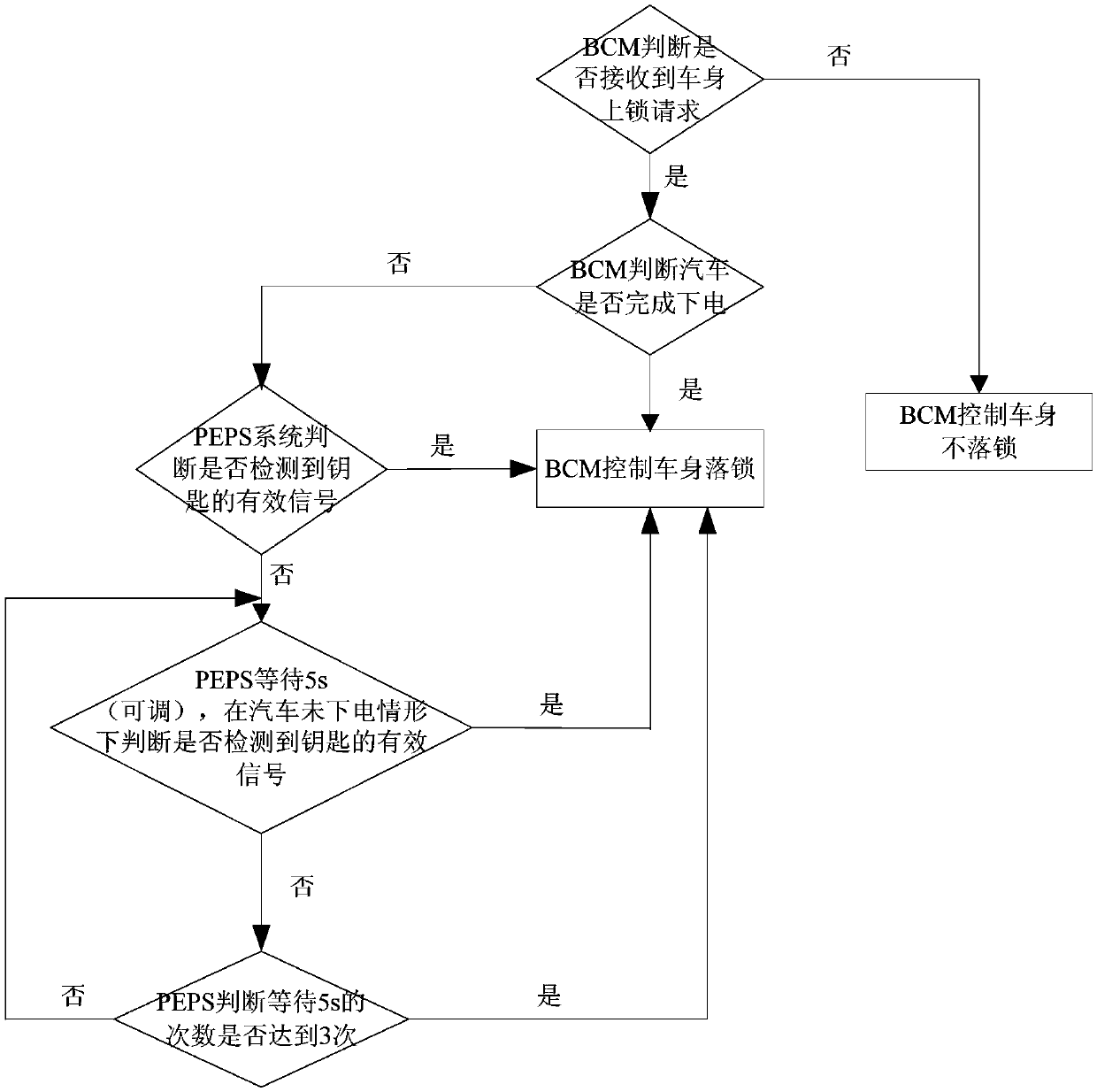
InactiveCN110316150AEnsure safetyAddress security threatsAnti-theft devicesElectricityAutomotive engineering
Owner:GREAT WALL MOTOR CO LTD
A Remote Security Meter Reading Method Based on Improved ibooe Algorithm
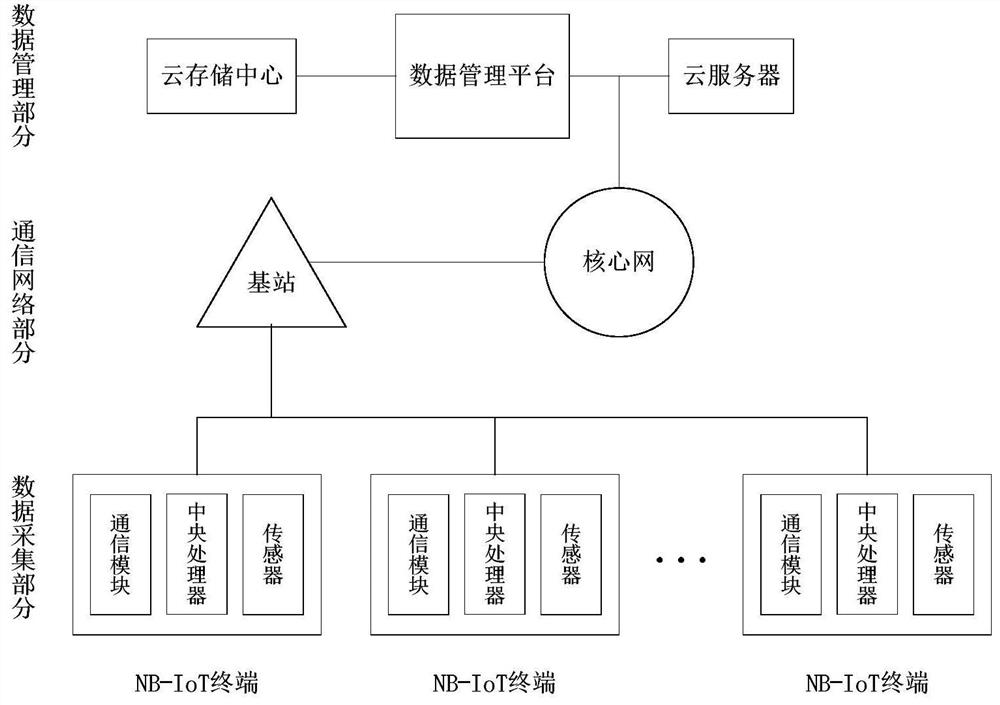
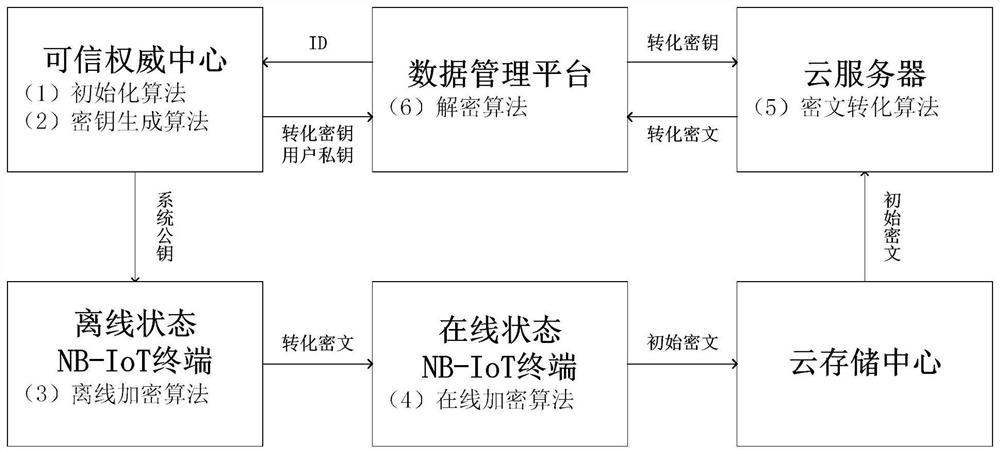
ActiveCN110299993BProtection against copy attacksDefense against capture attacksKey distribution for secure communicationUtility meters data arrangementsData acquisitionEngineering
The invention discloses a remote safe meter reading method based on an improved IBOOE algorithm, which is mainly aimed at a remote meter reading system whose application scenario is a residential area and is deployed on an NB-IoT network. The improved IBOOE algorithm is used to encrypt the transmitted data. After uploading to the secure cloud storage platform, the data management platform initiates a request to the secure cloud server to obtain the converted encrypted data, and finally decrypts and reads the information on the data management platform to solve the problem that the data acquisition part of the remote meter reading system may exist. Most of the security problems, the improved IBOOE algorithm adopted in the present invention is an identity-based online and offline encryption scheme that can be outsourced and decrypted. The algorithm is extended to ensure the security of the remote meter reading system.
Owner:NANJING UNIV OF POSTS & TELECOMM
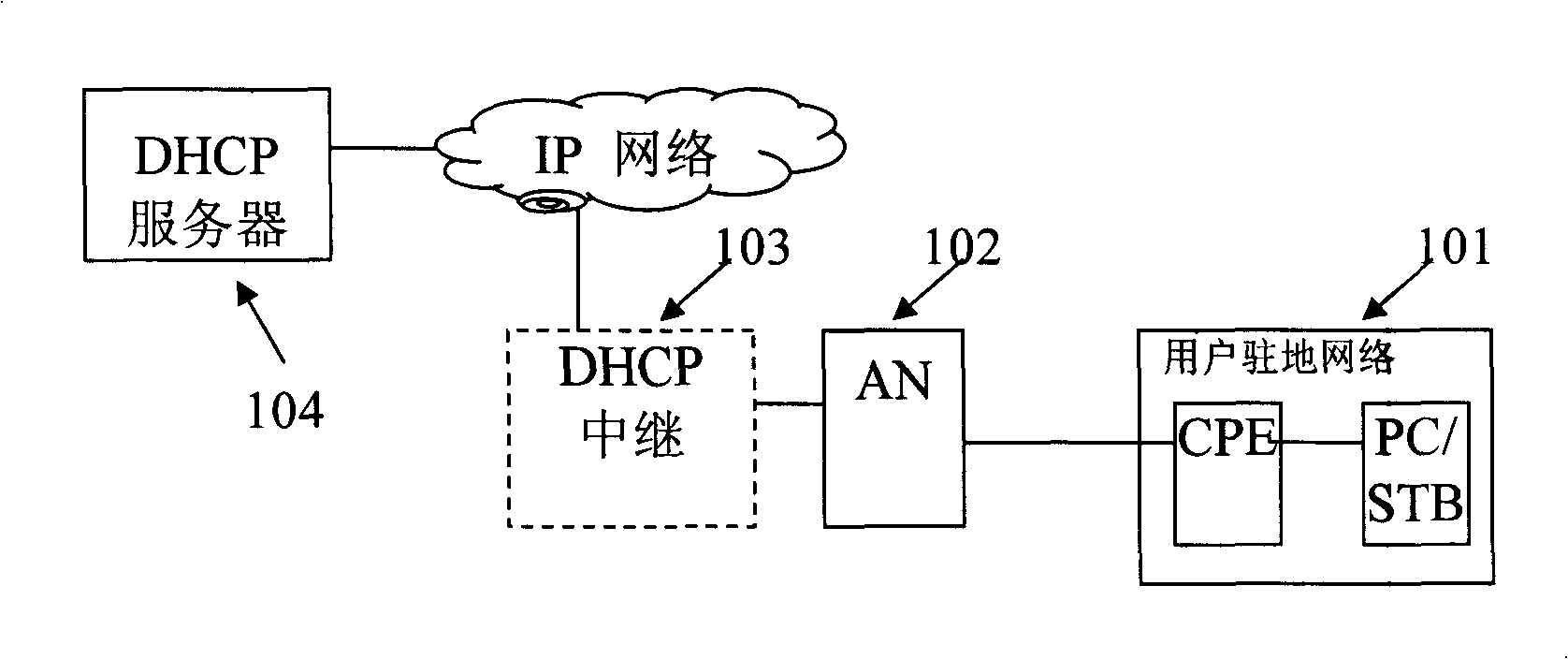
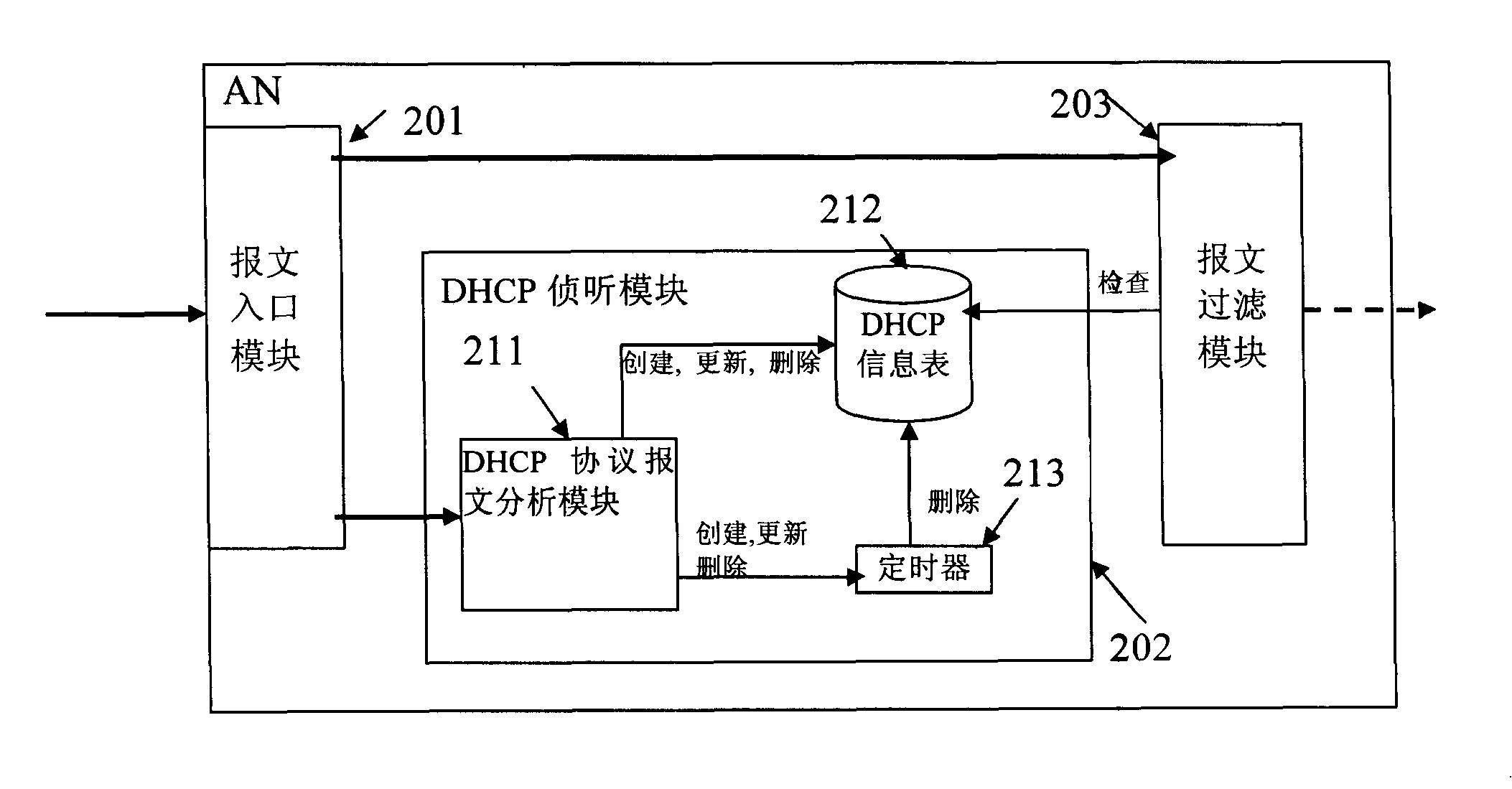
Devices for implementing anti-spurious IP address on AN and methods therefor
InactiveCN101098290BAddress security threatsSecure Multimedia Service OperationUser identity/authority verificationData switching networksInternet privacyIp address
Owner:ZTE CORP
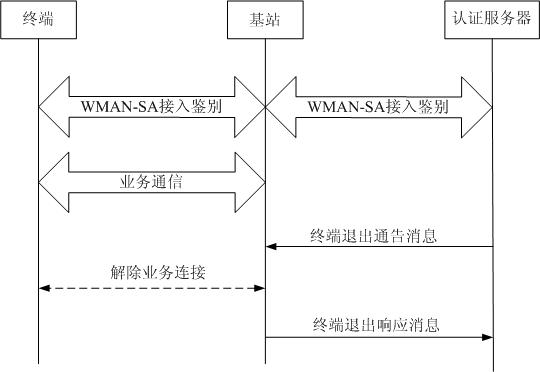
Method and system for WMAN (wireless metropolitan area network) entity exiting from network
InactiveCN101917718BAddress security threatsConnection managementSecurity arrangementWireless metropolitan area networkAuthentication server
The invention relates to the technical fields of wireless communication network and network security, in particular to a method and a system for a WMAN (wireless metropolitan area network) entity exiting from a network. The method of the invention comprises the following steps that: a terminal accesses a base station on the network side after passing the identification of an authentication server, and the authentication server records the IDs of the terminal and the base station and corresponding relationship thereof; a service communication is carried out between the base station and the terminal; the authentication server revokes the certificate of the terminal; the authentication server sends a 'notice information for terminal exit' according to the recorded local IDs of the terminal and the connected base station and corresponding relationships thereof; the base station removes the service connection with the terminal to be exited from the network, and interrupts the service communication; and the base station sends a 'response information for terminal exit' to the authentication server. In the invention, when the ID of some terminal of the wireless metropolitan area network fails, or some terminal is set as an illegal user by a manager, the method and the system of the invention can make the terminal timely exit from the communication network so as to ensure the safety ofthe communication network.
Owner:GCI SCI & TECH
Video conference data security sharing method
ActiveCN113411186AAddress security threatsImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey generationData security
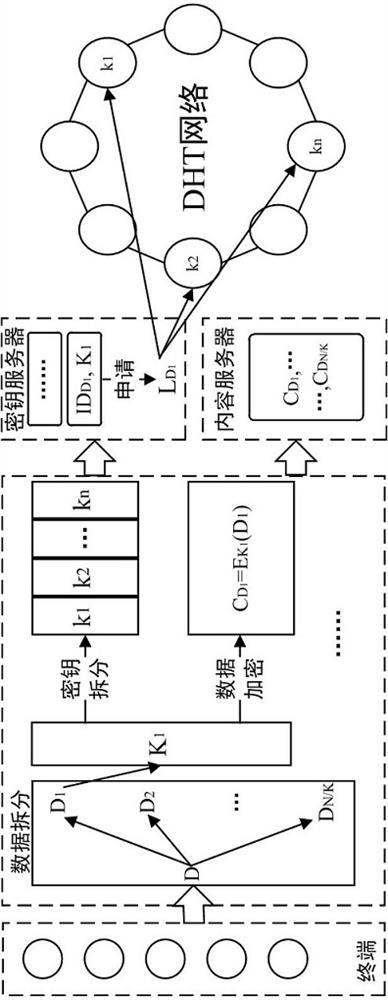
The invention relates to a video conference data security sharing method. The method comprises the following steps: determining a k value through a privacy disclosure threshold value and a data quality threshold value; performing k-anonymization operation on the terminal data set by using the determined k value to obtain a k-anonymized data set; randomly selecting a tuple from each anonymous group of the k-anonymized data set to form a recombined data set; encrypting each data subset in the recombined data set by using a randomly selected key, storing the encrypted recombined data set in a content server, and splitting the randomly selected key into n sub-keys; generating a mapping position of each sub-key in the DHT network; and when the application applies for data to be shared to the sharing party, accessing the mapping position of each sub-key in the DHT network according to the applied access key, determining the key of each data subset corresponding to the data to be shared, and obtaining corresponding shared data. According to the invention, the security of shared data is improved.
Owner:北京电信易通信息技术股份有限公司
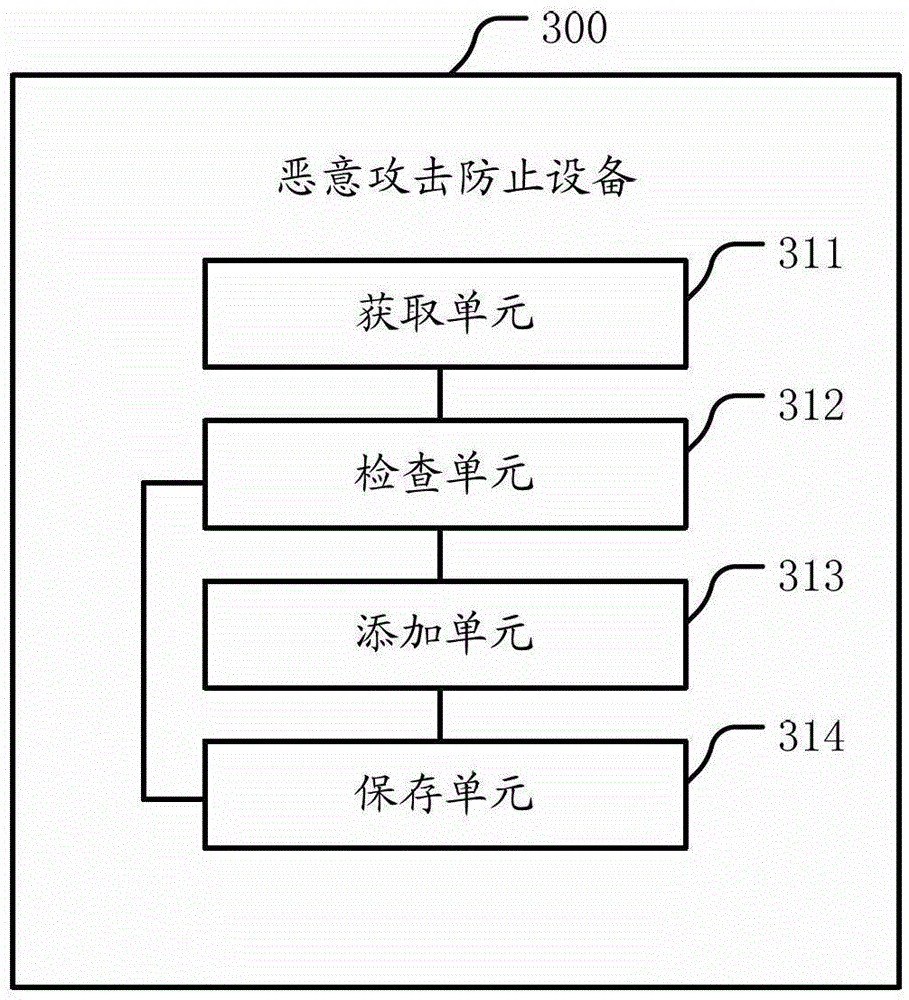
Malicious attack prevention method and browser
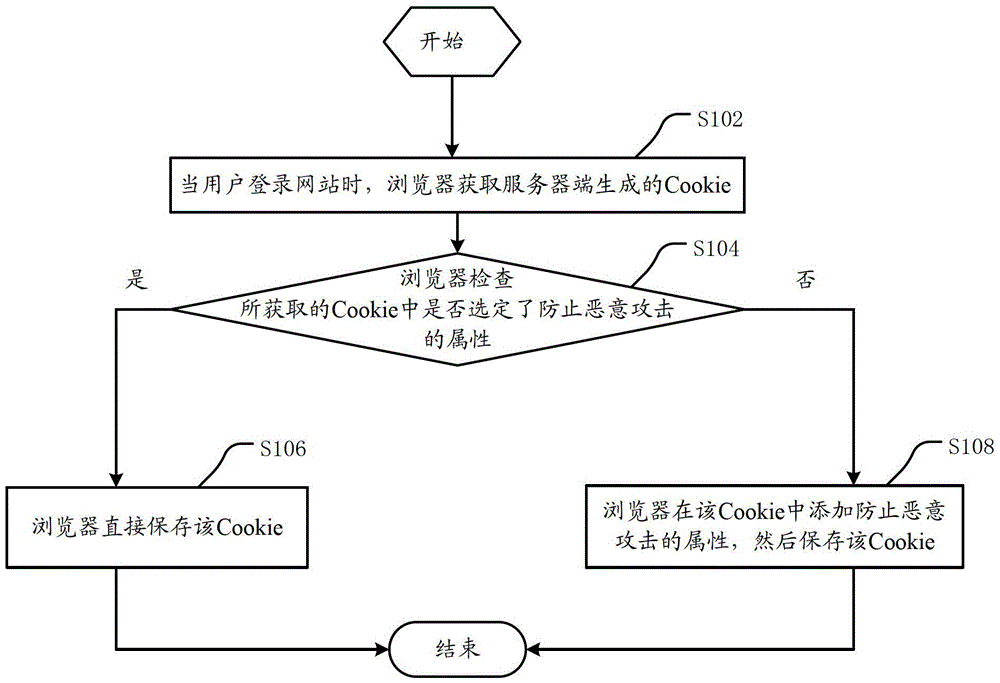
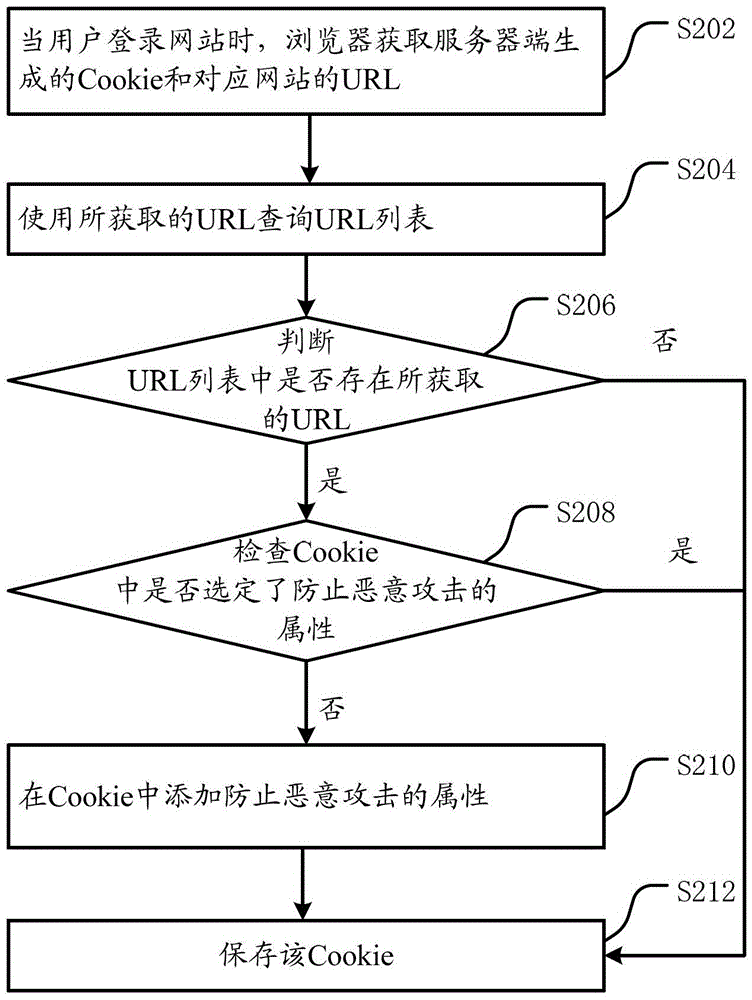
The invention discloses a malicious attack prevention method and a browser, and relates to the technical field of Internet. The browser comprises malicious attack prevention equipment, wherein the malicious attack prevention equipment comprises an acquisition unit, a checking unit, an adding unit and a storage unit; the acquisition unit is suitable for acquiring Cookie generated by a server when a user logs into a website and sending the Cookie to the checking unit; the checking unit is used for checking whether an attribute for preventing a malicious attack is selected in the Cookie, and if the attribute for preventing the malicious attack is not selected in the Cookie, sending the Cookie to the adding unit; the adding unit is used for adding the attribute for preventing the malicious attack into the Cookie and sending the Cookie to the storage unit; and the storage unit is used for storing the received Cookie. By the technical scheme, the malicious attack launched by using the Cookie can be prevented on the browser side; and therefore, the problem that the user security is threatened because information in the user Cookie is probably stolen or modified when the server of the website accessed by the user is low in security relative to cross-site scripting is solved.
Owner:BEIJING QIHOO TECH CO LTD
Roadway repairing machine for coal mine
ActiveCN113859998ARealize the function of deliveryProblems affecting work efficiencyConveyorsLoading/unloadingTransmission beltElectric machinery
The invention discloses a roadway repairing machine for a coal mine, and relates to the technical field of roadway repair. The roadway repairing machine comprises a roadway repairing machine body, the top of the roadway repairing machine body is provided with a cockpit, the left side of the cockpit is provided with a repair mechanical arm, the bottom of the cockpit is provided with a coal mine conveying mechanism, a top protection mechanism is arranged on the top of the cockpit, and the coal mine conveying mechanism comprises a lifting hopper and a transmission channel. The coal mine can be moved into an inner cavity of the lifting hopper by controlling the roadway repairing machine body to move forwards, the coal mine can be moved to the top of a transmission belt through a through groove through a centrifugal conveying mechanism by controlling a first driving motor to operate, and the function of conveying the coal mine can be achieved by controlling a second driving motor to operate; and the problem that the maintenance work is influenced by accumulation of the coal mine is solved, the problem that the working efficiency of workers is influenced when the workers control external equipment to convey the coal mine is solved, and the convenience of the device is improved.
Owner:赤峰西拉沐沦(集团)公格营子煤业有限公司
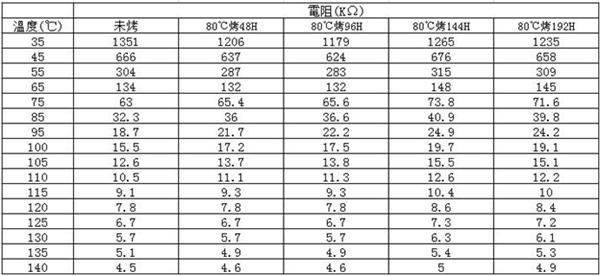
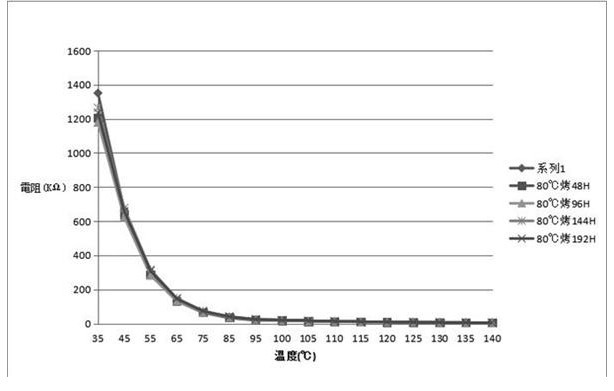
A kind of preparation method, device and application of modified PVC material with NTC effect
The invention provides a preparation method, device and application of a modified PVC material with NTC effect. The raw materials are placed in a vertical mixing tank, and the raw materials are mixed and stirred by the vertical mixing tank until they are plasticized to obtain a semi-finished product; step (3), the semi-finished product is put into an extruder, and the extruder is used to Extrusion granulation is carried out to obtain a modified PVC material with NTC effect. The invention is convenient for people to quickly replace different die heads, so as to switch to produce plastic particles of different sizes, and after changing the die head, the die head and the connecting channel are pressed tightly, thereby increasing the sealing performance, preventing the raw material from overflowing, and improving the stability Higher and easier to clean.
Owner:惠州市大义塑胶新材料有限公司
A kind of intelligent lock device and its use method, preparation method of electronic key
ActiveCN103646455BFix security issuesSecurity issues do not existIndividual entry/exit registersComputer hardwareSecure transmission
The invention discloses an intelligent lock device and a usage method thereof as well as a configuration method for electronic keys. The configuration method for the electronic keys comprises the following steps: I, generating two-dimensional codes corresponding to a specific intelligent lock, wherein the two-dimensional codes comprise basic configuration parameters and enciphered messages of communication corresponding to the specific intelligent lock; II, scanning the two-dimensional codes by a mobile client side, decrypting and reading data in the two-dimensional codes; III, establishing a first security channel by the mobile client side through using the analyzed two-dimensional data and the intelligent lock; IV, mutually sending the key information and secrete key information, configured in the first security transmission channel, through the mobile client side and the intelligent lock, and storing the key information and secrete key information as electronic keys. The intelligent lock device has standard safety and is simple to use and convenient to operate.
Owner:深圳市诺赛特系统有限公司
Implementation method and device for real-time transmission data encryption algorithm
InactiveCN101459510BAddress security threatsOvercoming the problem of low safety factorInterconnection arrangementsSecuring communicationComputer hardwareNetwork packet
The invention discloses a realization method for an encryption algorithm of real-time transmission data, which comprises determining the iterative rounds used to conduct the encryption algorithm for the real-time transmission data, selecting one of a plurality of algorithms in an algorithms library according to a key when in each round of encryption iteration, and conducting the encryption algorithm for real-time transmission data using the data pack as a unit by combining the key. The invention further discloses a realization device for the encryption algorithm of real-time transmission data. The method is adopted to overcome the problems of low security coefficient brought by the encryption and complexity of strong encryption, and realize the security encryption effect for the real-timetransmission data, thereby solving various security threat problems faced by real-timely transmitted VoIP data.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com