Implementation method and device for real-time transmission data encryption algorithm
A technology of real-time transmission and encryption algorithm, applied in transmission systems, interconnection devices, digital transmission systems, etc., can solve the problems of inability to achieve security protection, weak encryption strength, and easy to be analyzed and broken, so as to solve the problem of security threats, Overcome the effect of low security factor and secure encryption effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
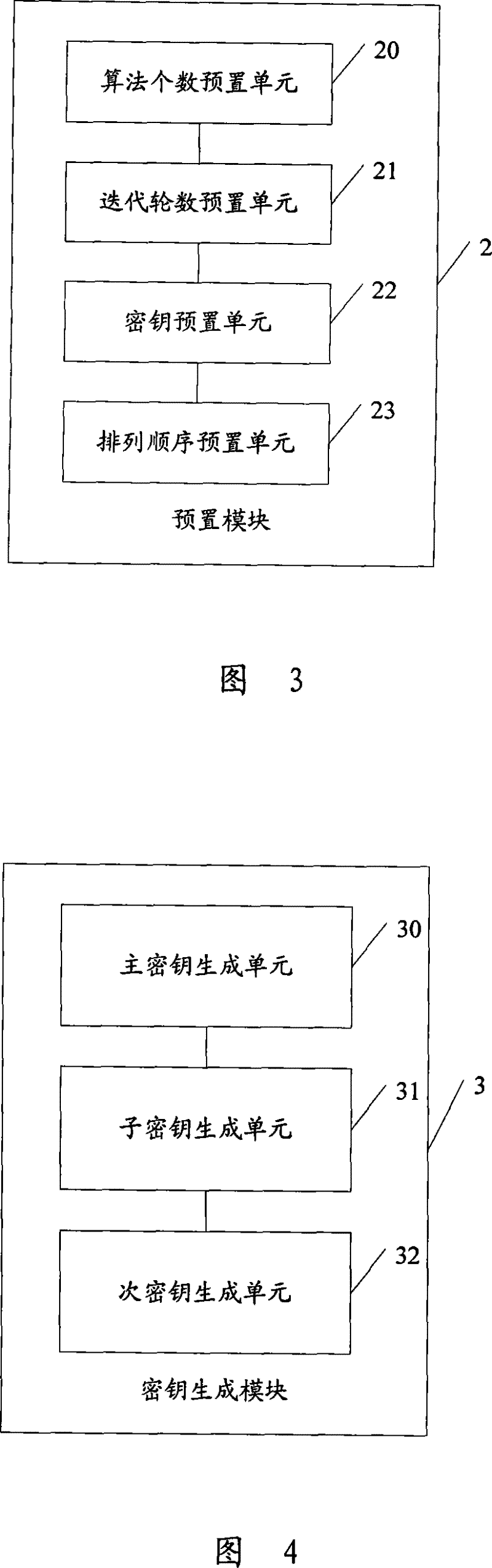
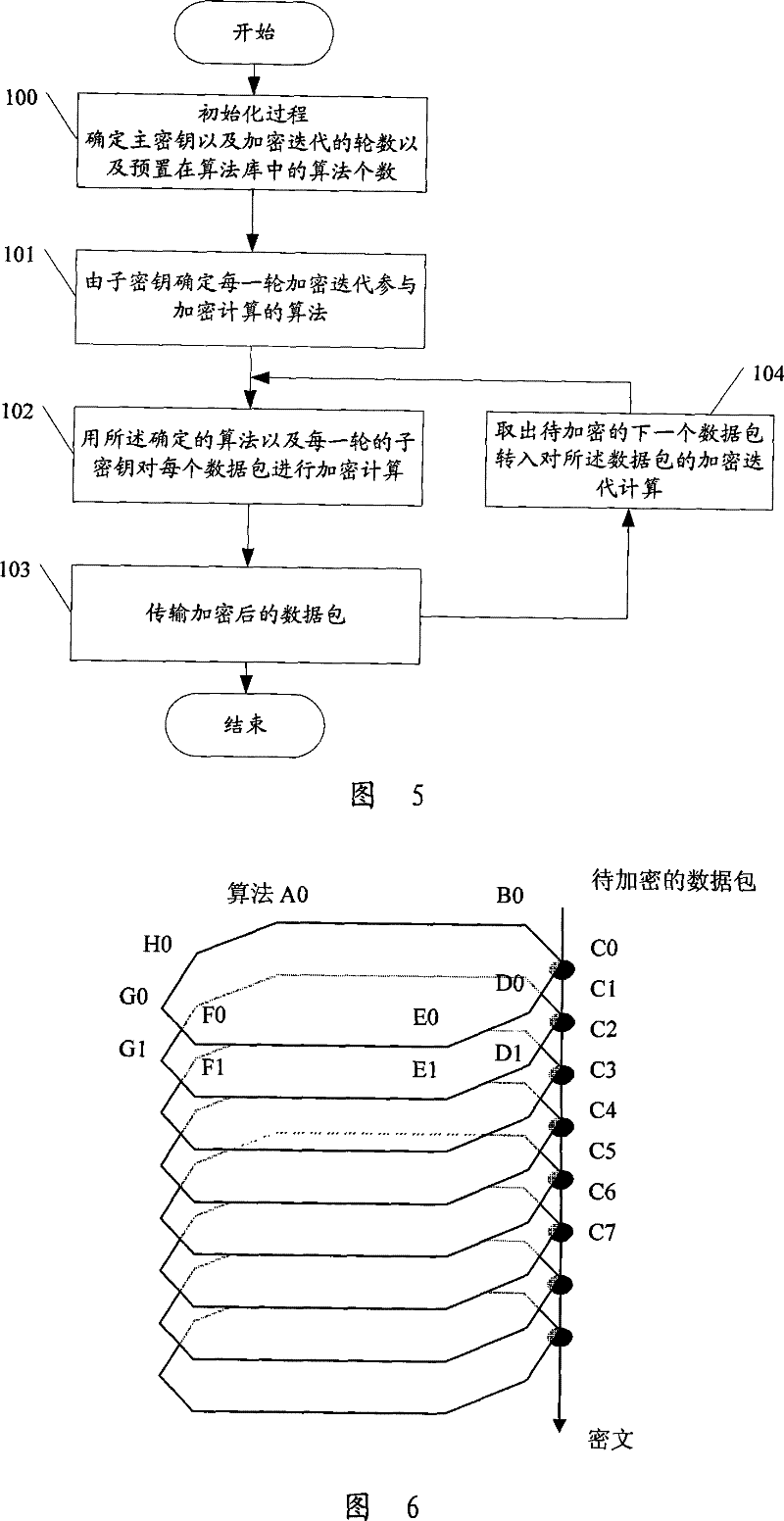
[0027] The implementation method and device of the encryption algorithm for real-time transmission data provided by the present invention use the constantly changing characteristics of the algorithm to replace the complexity of the algorithm, and perform multiple rounds of encryption iterations on the real-time transmission data to be encrypted to overcome the security brought by simple encryption The problem of low coefficient can achieve a safe encryption effect, thereby solving various security threats faced by real-time transmitted VoIP data.
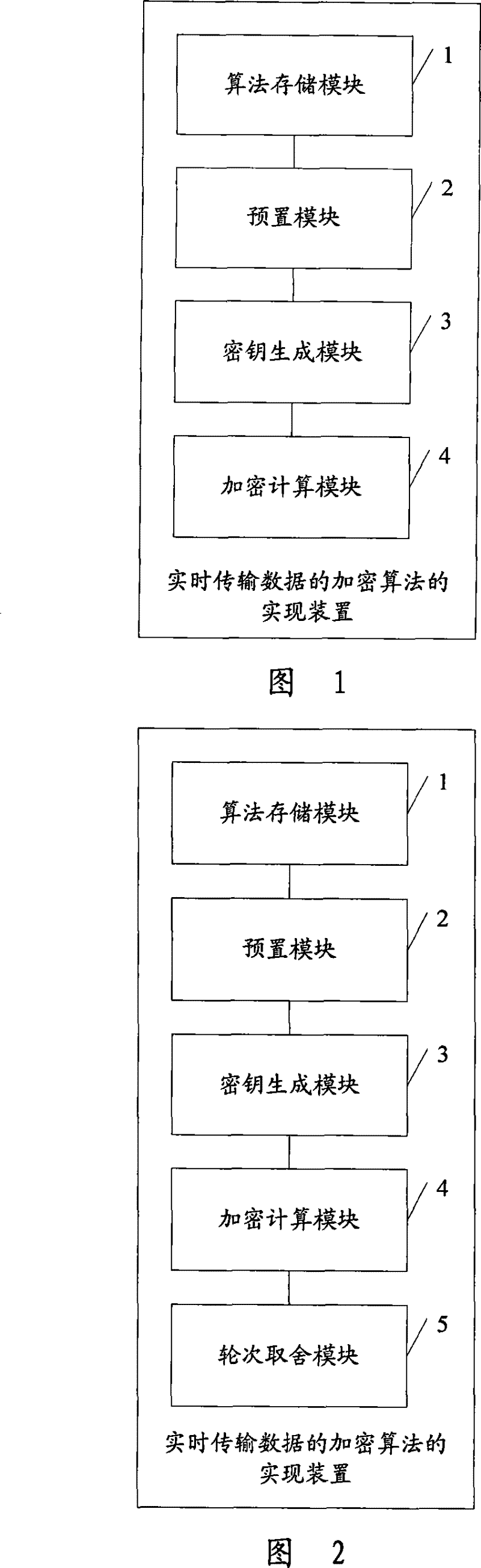
[0028] see figure 1 It is a schematic structural diagram of the first embodiment of the device for implementing an encryption algorithm for real-time data transmission in an embodiment of the present invention;
[0029] The realization device of the encryption algorithm of described real-time transmission data comprises:
[0030] The algorithm storage module 1 is used to store an algorithm library with multiple algorithms; the stor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com