Patents
Literature
33results about How to "Prevent security attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
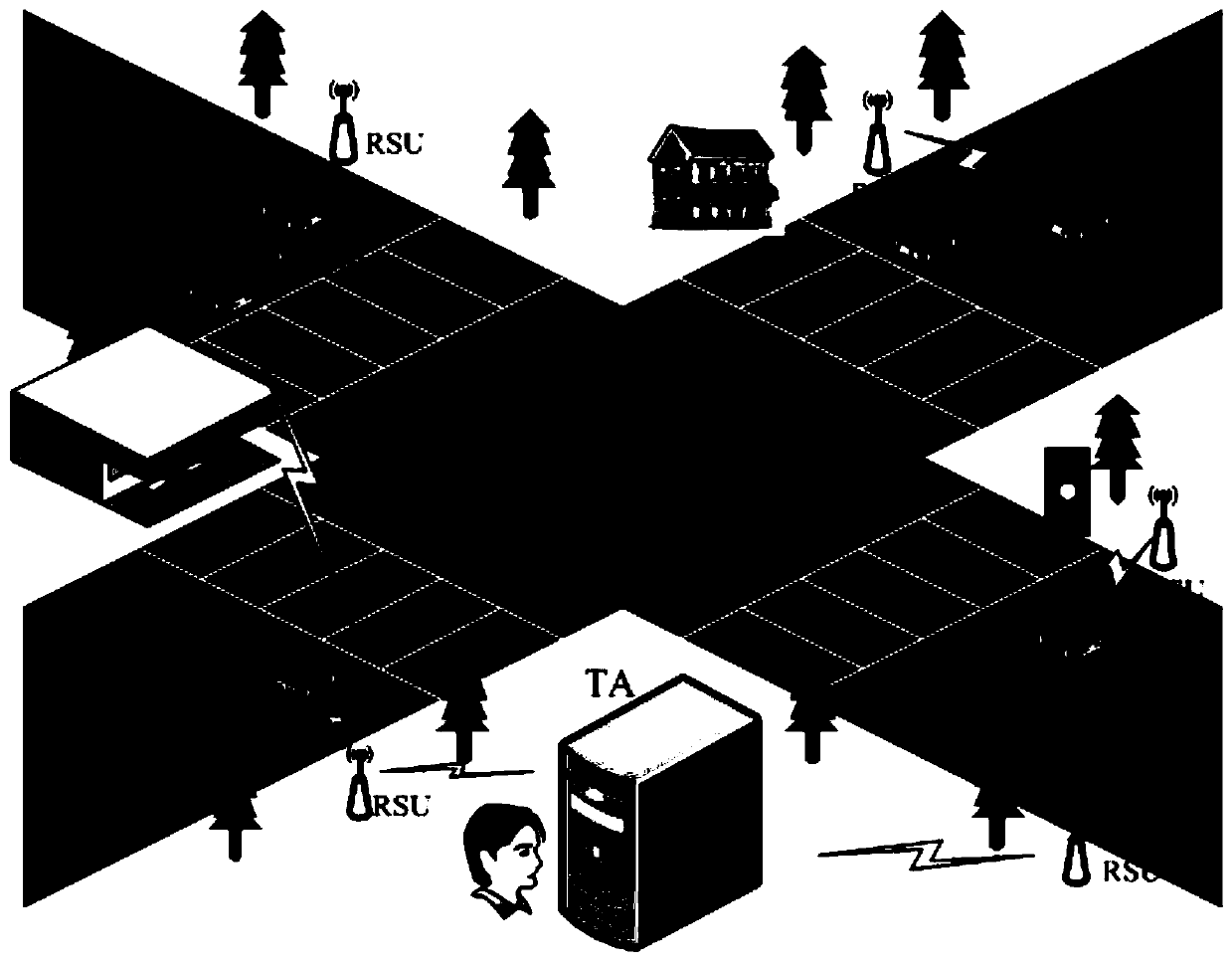
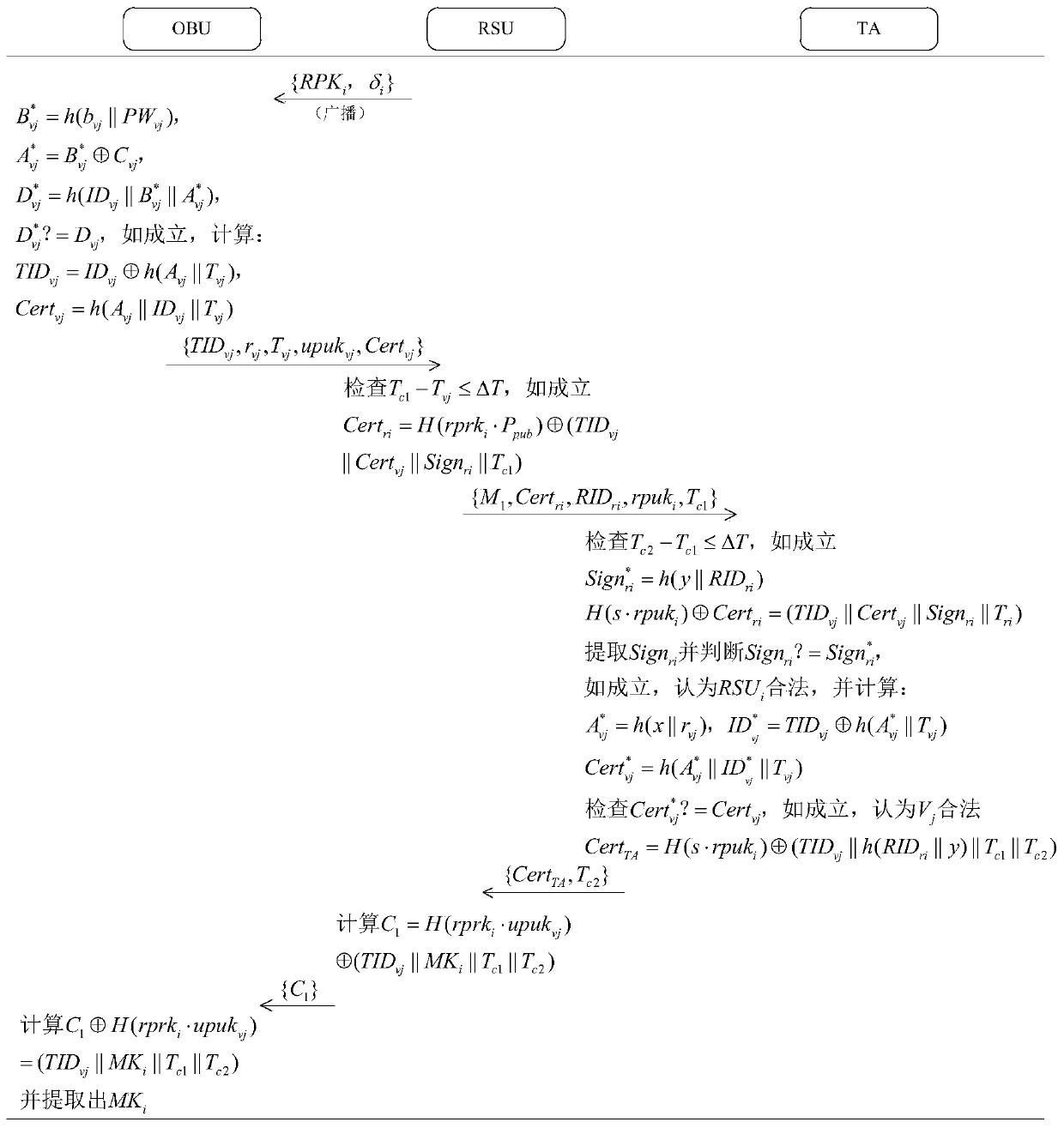
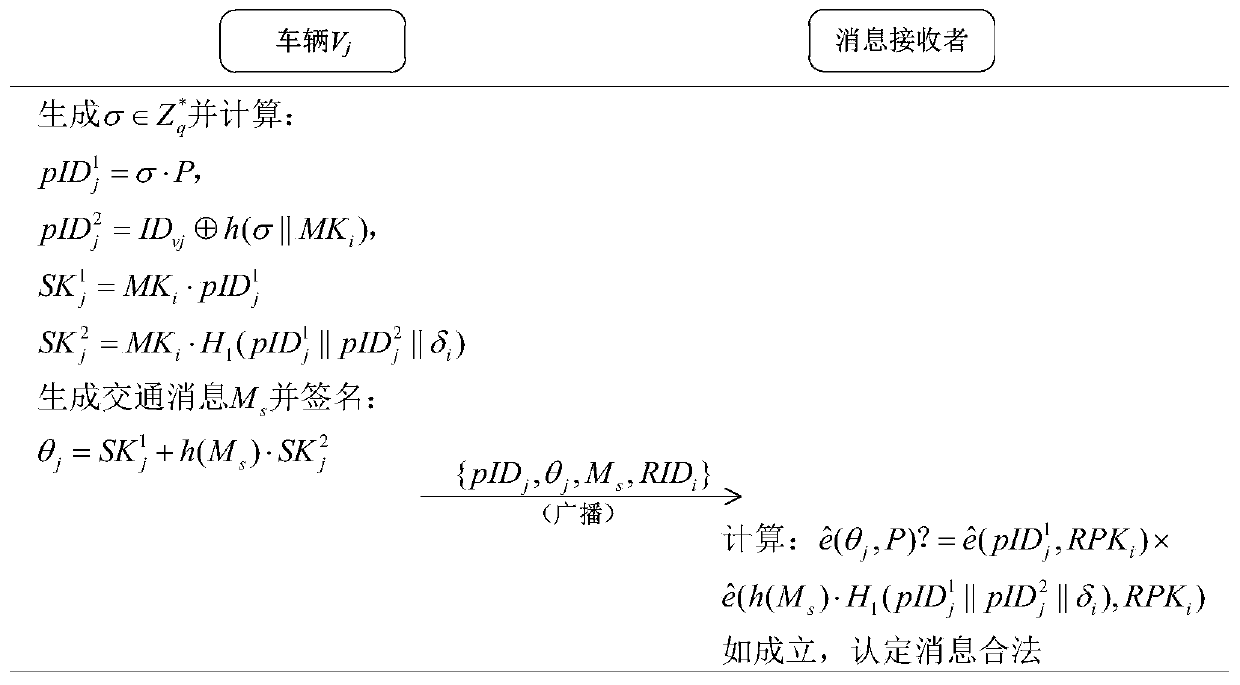
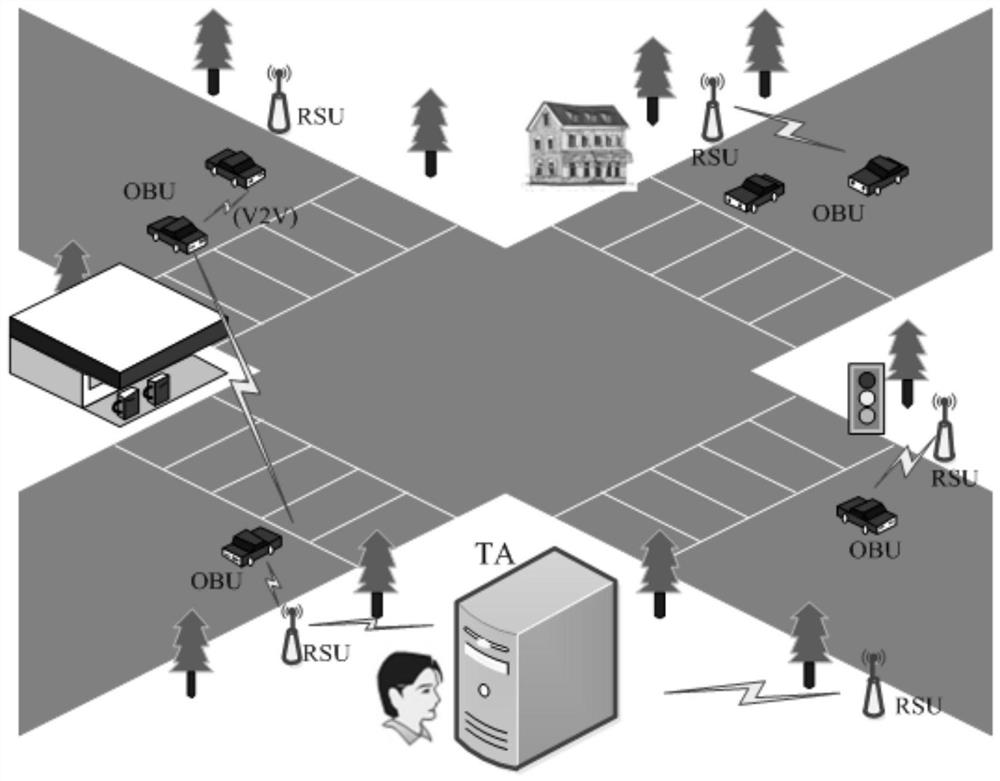
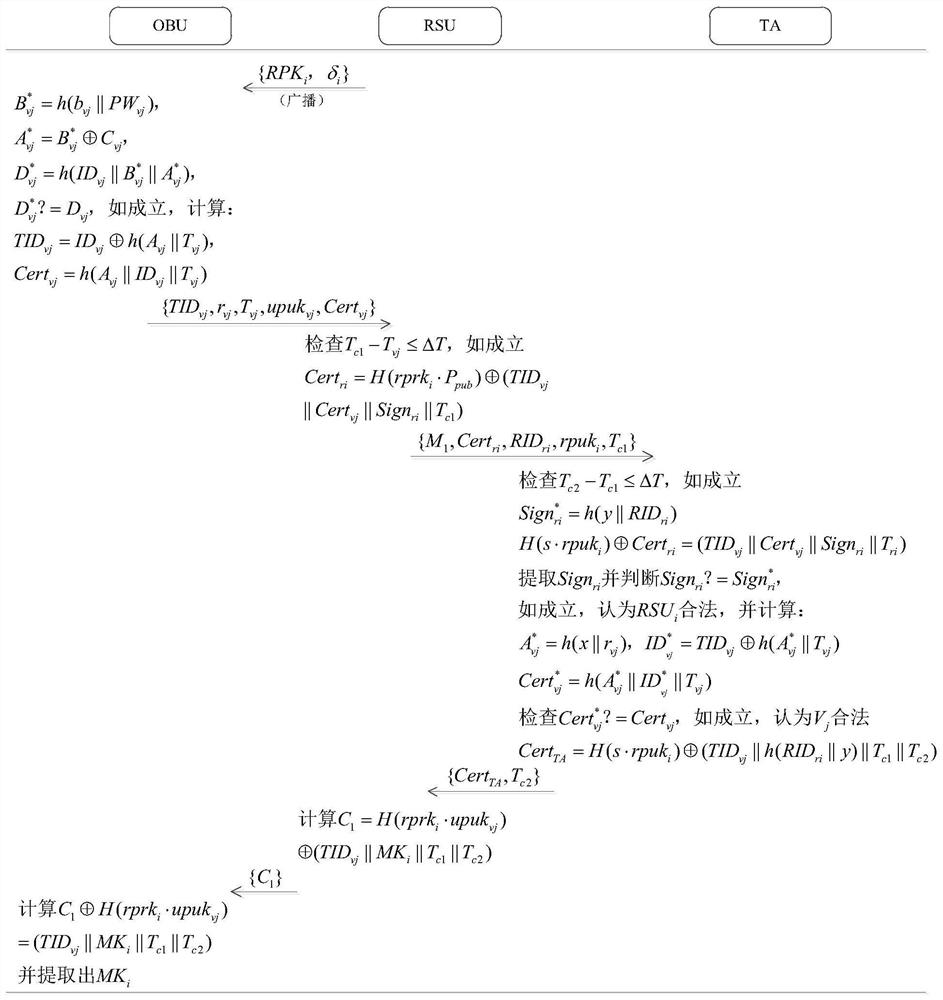
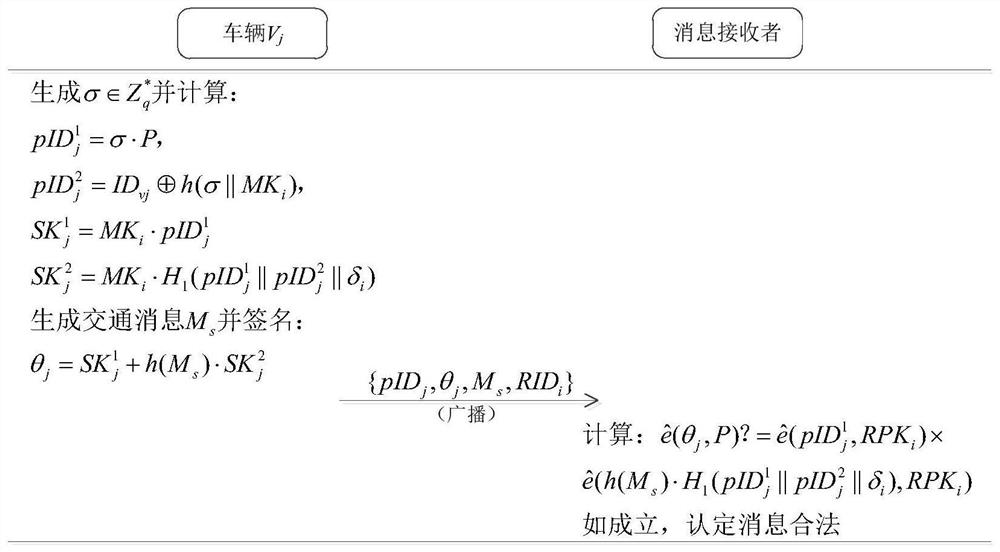
A vehicle authentication and message verification method in a vehicle-mounted network environment
ActiveCN109922475AGuaranteed privacyPrivacy protectionPublic key for secure communicationParticular environment based servicesDigital signatureValidation methods
The invention provides a vehicle authentication and message verification method in a vehicle-mounted network environment. The vehicle authentication and message verification method comprises the stepsthat a trust mechanism initializes a system; the vehicle-mounted unit is registered, and the roadside unit is registered; a temporary key of the roadside unit is released; a vehicle authentication stage; the trust mechanism verifies the legality of the roadside unit through the digital signature, extracts the message and verifies the legality of the automobile, the trust mechanism sends the identity identifier of the automobile to the roadside unit, the roadside unit sends the private key and the temporary main key to the automobile, and the automobile extracts the temporary main key; the automobile calculates a temporary identifier and a temporary private key, generates a traffic message and signs and broadcasts the traffic message; and when other automobiles receive the automobile broadcast message, verifying the effectiveness of the broadcast message through bilinear mapping. According to the method, the vehicle access safety in the Internet of Vehicles environment can be ensured,the safety of traffic information sent by legal vehicles is also ensured, and the method has a relatively high application value in an application environment in the mobile vehicular network environment.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Key digital identification method using once variable quantity
InactiveCN1980124AImprove integrityAchieve freshnessUser identity/authority verificationComputer hardwareMessage authentication code
Using message authentication code (MAC) to authenticate message, the invention uses one-off variable. The method includes steps: before using one-off variable, saving range and use state of one-off variable; it must carry out operation for one-off variable and message together to calculate MAC; in authenticating MAC, must authenticate one-off variable, and its state; after using one-off variable, must mark and save use state; for certain cipher key and authentication function, one-off variable is only use for once to authenticate message effectively. Using one-off variable can realize integrality and freshness of authenticating message. Advantages are: synchronous use one-off variable to prevent security attack in many ways, and simple method for realizing complicated authentication application.
Owner:刘金宏
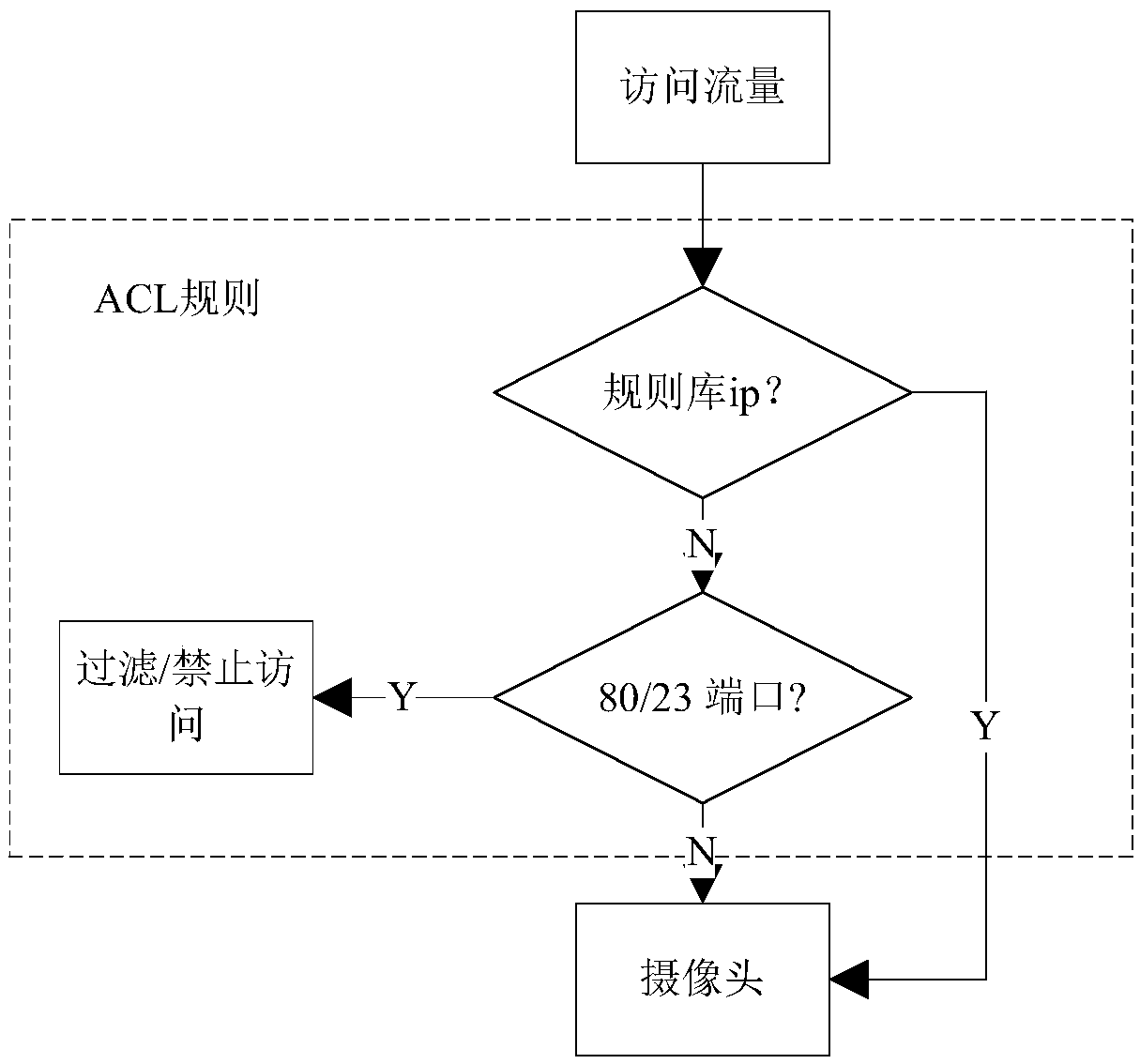
Defense method for configuring weak password vulnerability of internal and external network camera
The invention discloses a defense method for configuring weak password vulnerabilities of internal and external network cameras. A honeypot is arranged at a network end of the camera, and a public network end of the camera is accessed to the rear of a router to configure an access control list for the router. In an internal environment, ports 23 and 80 of the camera are exposed through the honeypot, and a scanned traffic packet is obtained, the source IP address of the scanned traffic packet is analyzed, and an intranet attack host is obtained through the honeypot when a camera vulnerability scan attack occurs. In an external network environment, all traffic accessing the camera is uniformly filtered by the router, and the IP address allowed to be accessed is released, otherwise prohibiting. According to the defense method for configuring weak password vulnerabilities of the internal and external network cameras, illegal requests of the external network are filtered by using a router ACL, and all external networks accesses do not need to be forbidden, thereby guaranteeing the functionality of the camera; and a Cowrie honeypot is used for internal network deployment, so that low false alarm rate is achieved, and intrusion method and flow of an attacker can be more clearly understood.
Owner:NANJING UNIV OF POSTS & TELECOMM
Ad hoc network security routing method based on trust model
InactiveCN103347011AEnsure safetyReduce overheadTransmissionSecurity arrangementSafe operationEnergy consumption
The invention provides an Ad hoc network security routing method based on the trust model and relates to the technical field of communication. The method comprises the steps of defining trust, obtaining properties involved with the trust, and quantizing and evaluating the properties; acquiring overall credibility of nodes comprehensively, wherein the overall credibility is the composition of the quantized properties; monitoring the state and the behavior of each node in a network, recording the state and the behavior in the network, and providing information of the nodes and the network; monitoring the current state of a neighbor node and judging whether the node is capable of participating in the routing; acquiring, calculating and updating trust values of the nodes; providing the message format, the routing strategy and the routing process inside a routing protocol; analyzing and verifying the security and performance of the routing. According to the Ad hoc network security routing method based on the trust model, energy consumption of the nodes in the network is effectively reduced, network performance is improved, security attack in the network can be resisted, and safe operation of the network routing protocol is guaranteed.
Owner:山东政信大数据科技有限责任公司
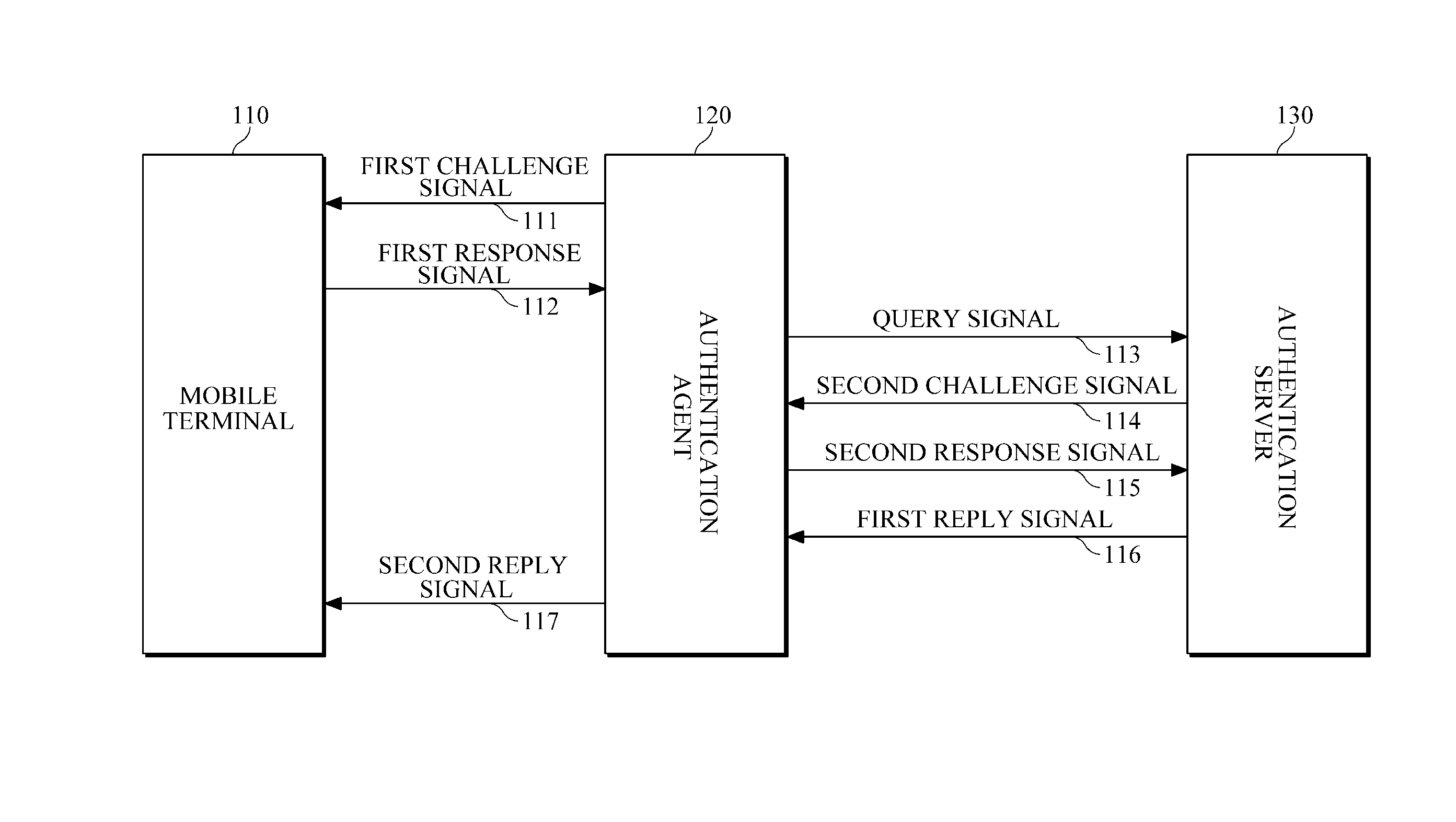
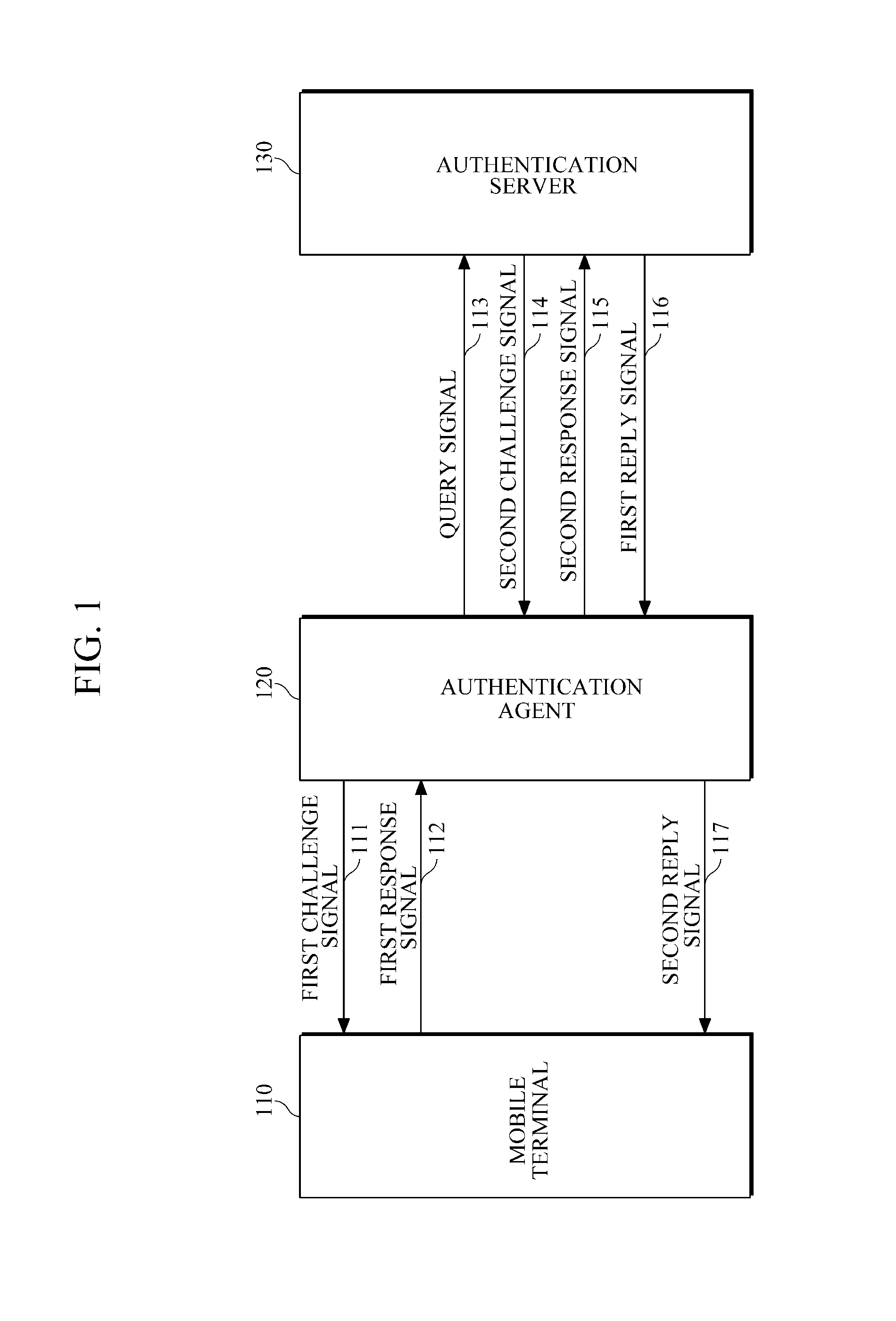
Mutual authentication system and method for mobile terminals
InactiveUS20120166801A1Avoid data breachesEfficient updateDigital data processing detailsUser identity/authority verificationAuthentication systemMutual authentication
Provided is a technique for mutual authentication between different kinds of objects (devices, apparatuses, users, etc.) by expanding the kinds of objects that are subject to authentication, such as authentication between users, authentication between users and an apparatuses (devices, equipment, terminals, etc.), and authentication between apparatuses (devices, equipment, terminals, etc.).
Owner:ELECTRONICS & TELECOMM RES INST
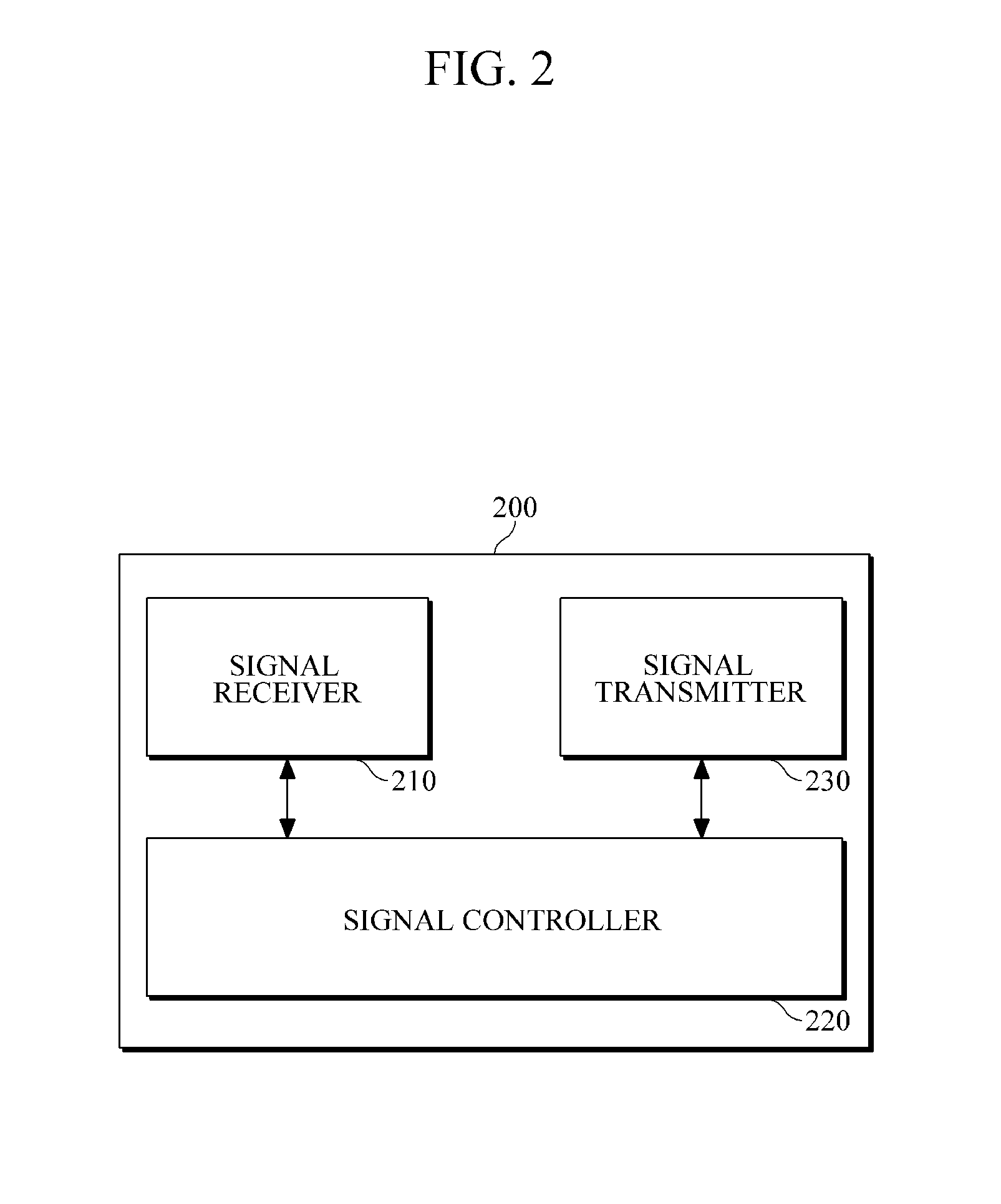
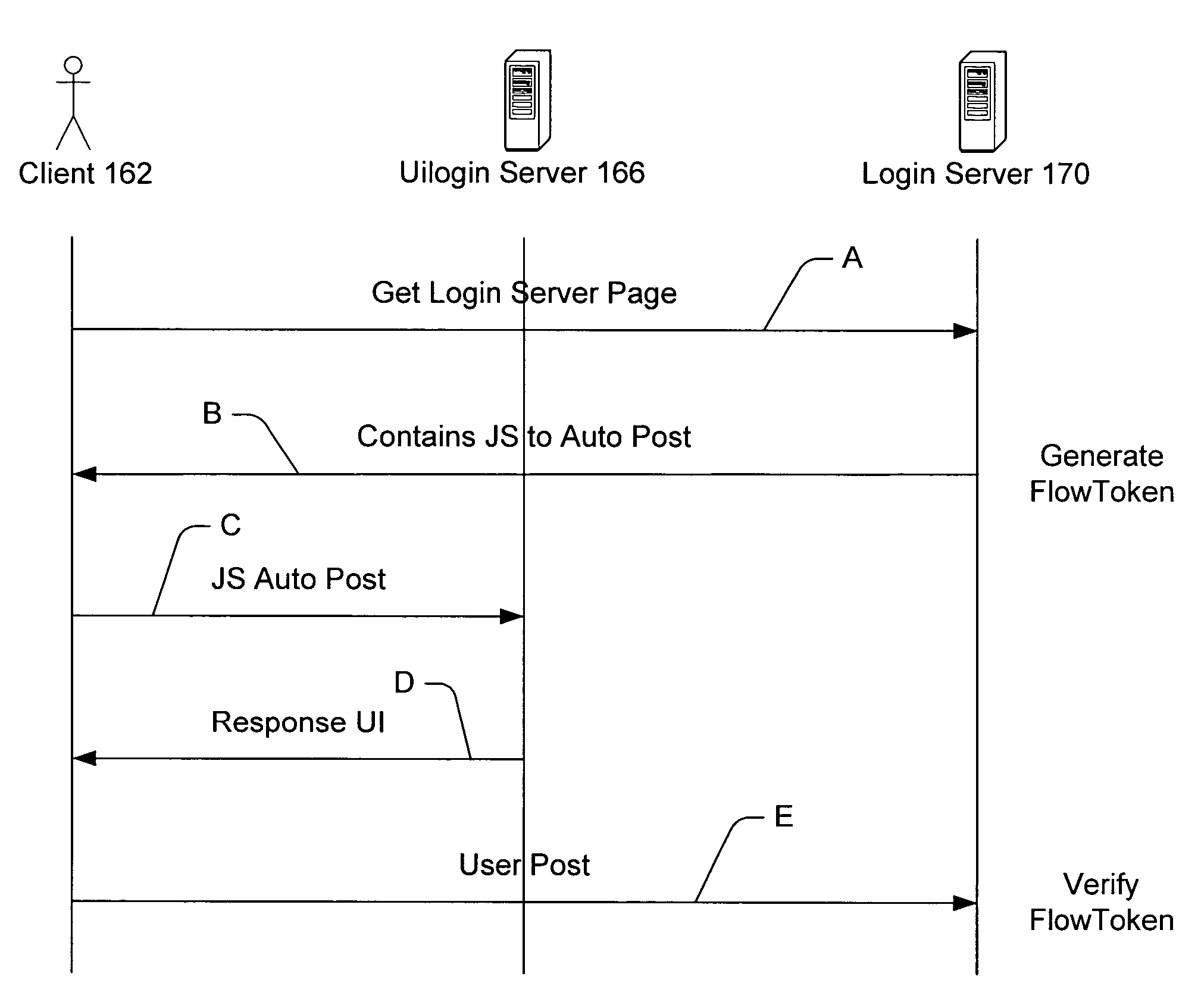
Flow token
ActiveUS7565538B2Easy to managePrevent security attacksDigital data processing detailsUser identity/authority verificationClient-sideNetwork service
Managing and securing process flow. A network server receives user data and retrieves secured flow data from the user data. A user interface is rendered at the client in response to the user data. The flow data is based on a web request from the client and identifies the process flow and a position within the process flow. The request initiates the process flow on a data communication network and the user interface has a hidden form field that contains the retrieved flow data. The client posts user-supplied information in addition to the flow data via the user interface for verifying the web request.
Owner:MICROSOFT TECH LICENSING LLC
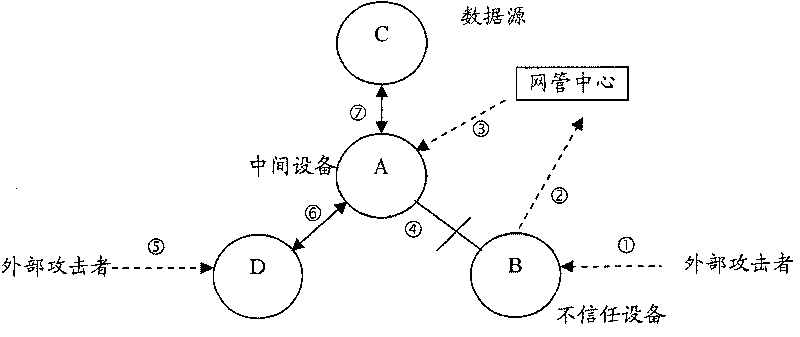
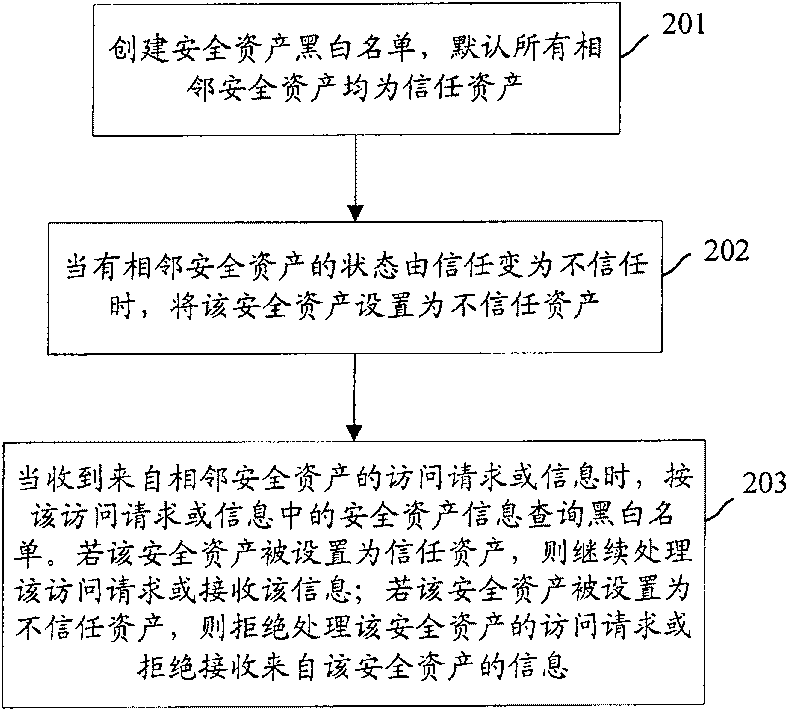
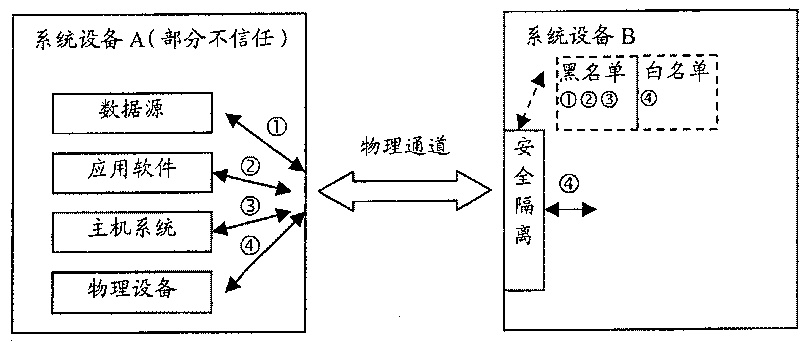
Assets safety management method, system and network element equipment of telecom network
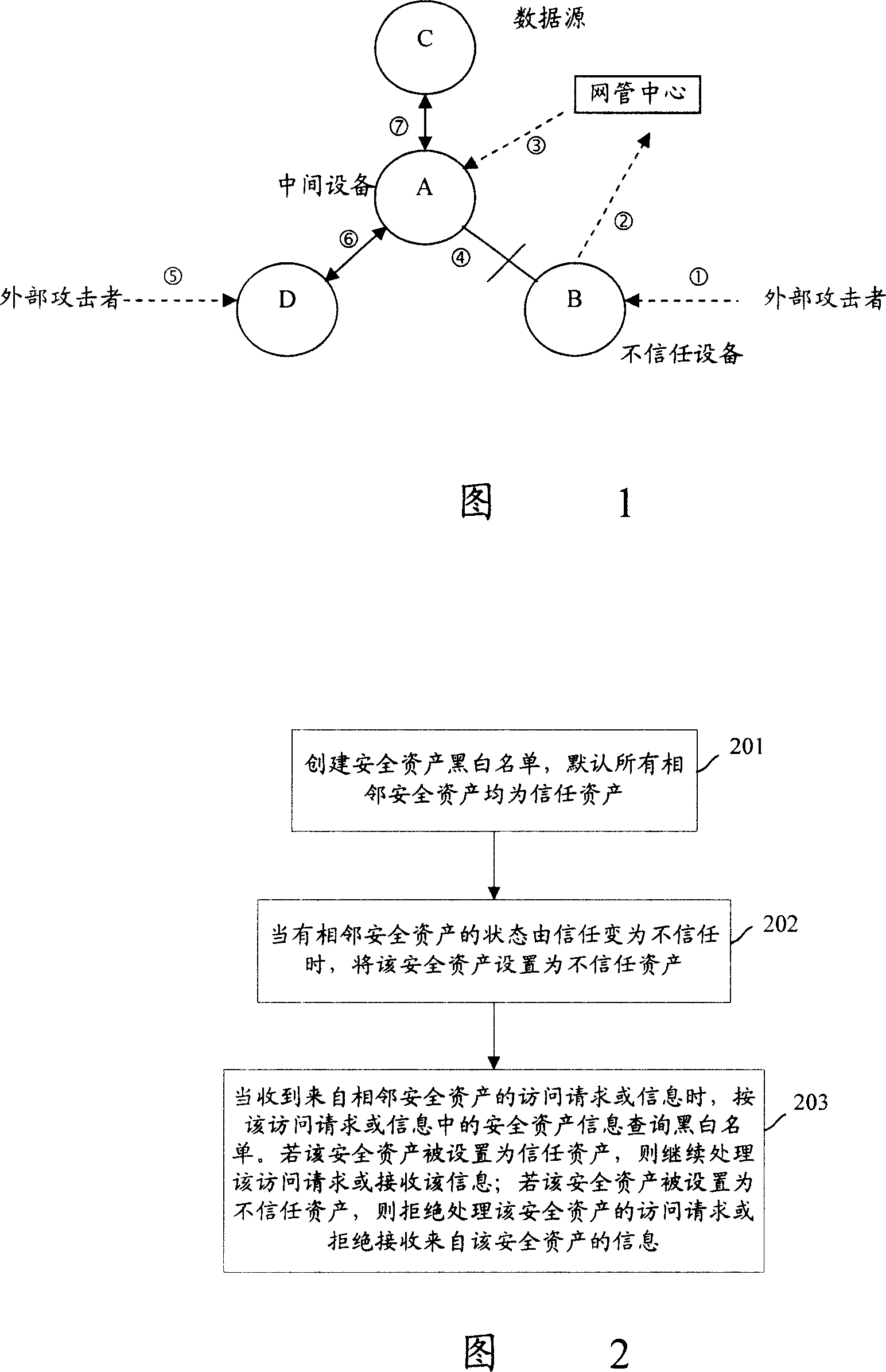
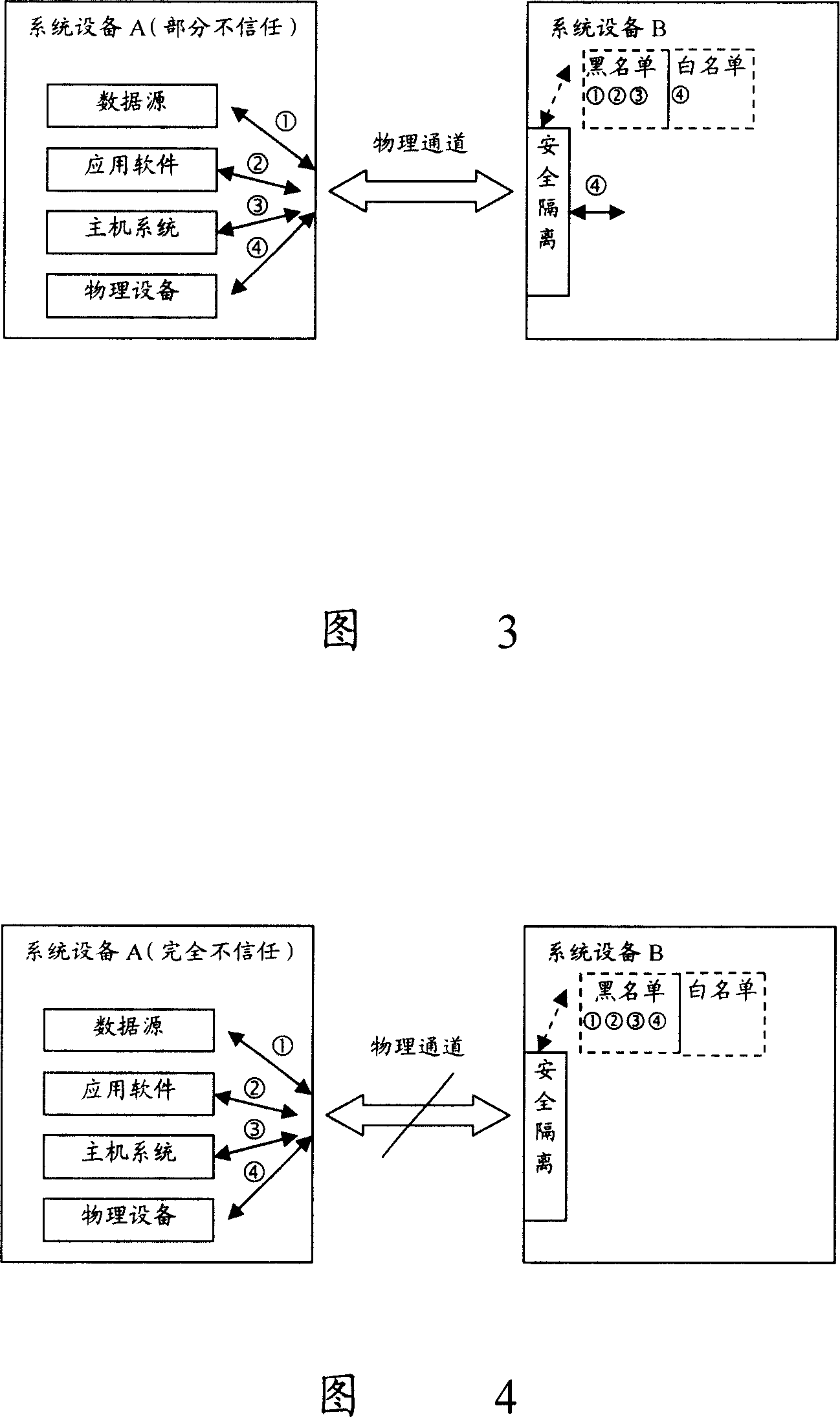
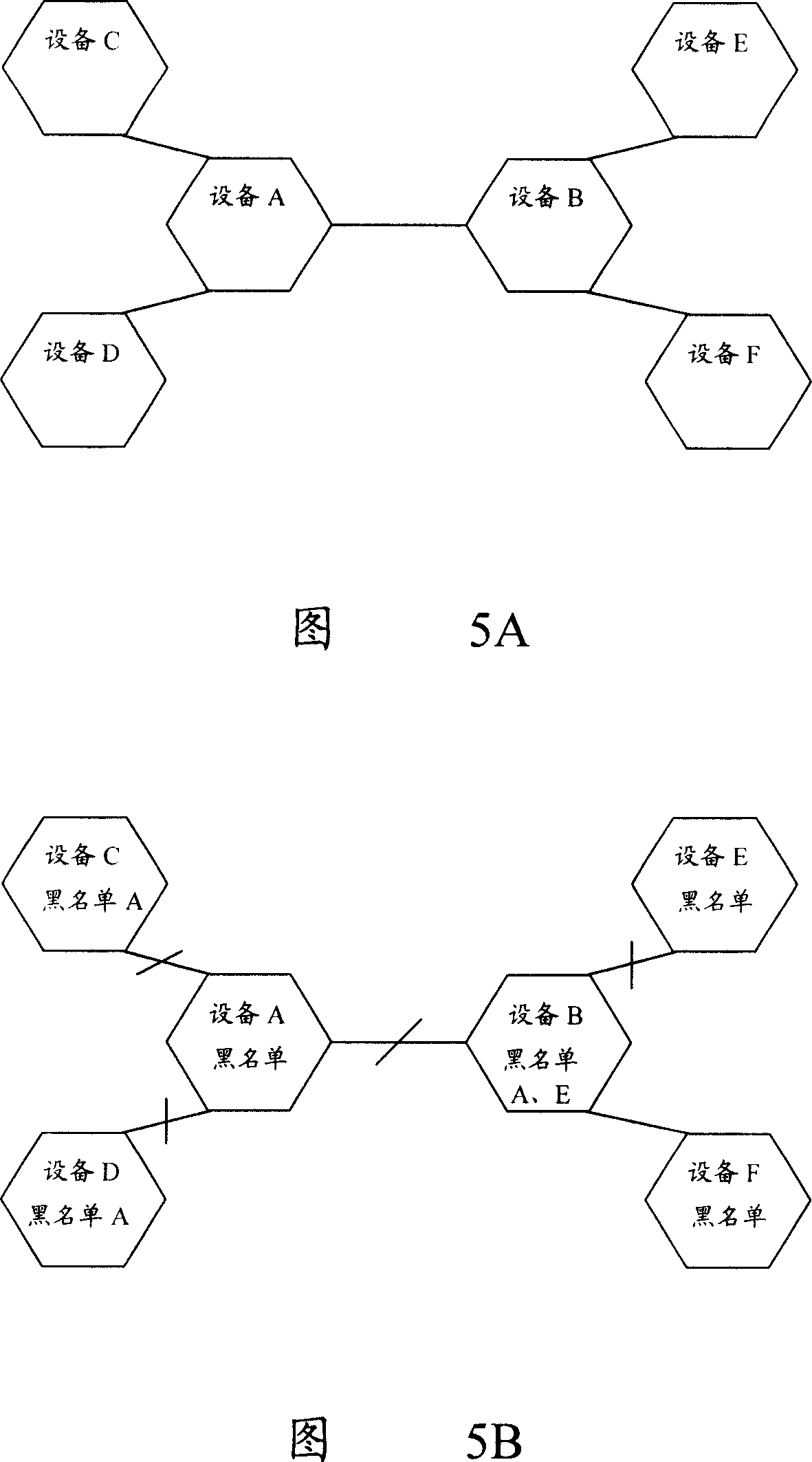
ActiveCN101136767APrevent security attacksData switching networksTelecommunications networkSecure state
The method is applicable to telecomm network including at least one device of net element. In the method, device of net element takes charge of tracking safe state of asset for each asset included in adjacent device of net element, and manages safety of asset according to safe state of asset. The invention also discloses the system and device of net element corresponding to the method as well as technique for carrying out safety management for peripheral assets based on individual device.
Owner:HUAWEI TECH CO LTD
Public key cryptographic methods and systems with preprocessing
InactiveUS20060251248A1Improve computing efficiencyIncrease capacityCryptographic attack countermeasuresPlaintextSecure communication
A system and method for public key cryptosystem for secure communication of messages including at least one message encrypted by standard RSA methods; and a predetermined number of prime factors used for the generation key(s) for decryption including a modulus N and an exponent e, wherein a proper subset of the prime factors of the modulus N, along with the exponent e, are required to decrypt messages encrypted using the public exponent e and the public modulus N, N is generated using RSA methods, and encryption occurs using RSA methods, wherein the exponents d and e are generated such that e*d=1 mod (N−1) and gcd(e,d)=1, and further including additional method steps for preprocessing plaintext messages to prevent potential security attacks within the context of superset RSA; and wherein the system is operable to decrypt encrypted messages using the key(s).
Owner:CRYPTOIP
Processing method and exchange equipment for address detected message
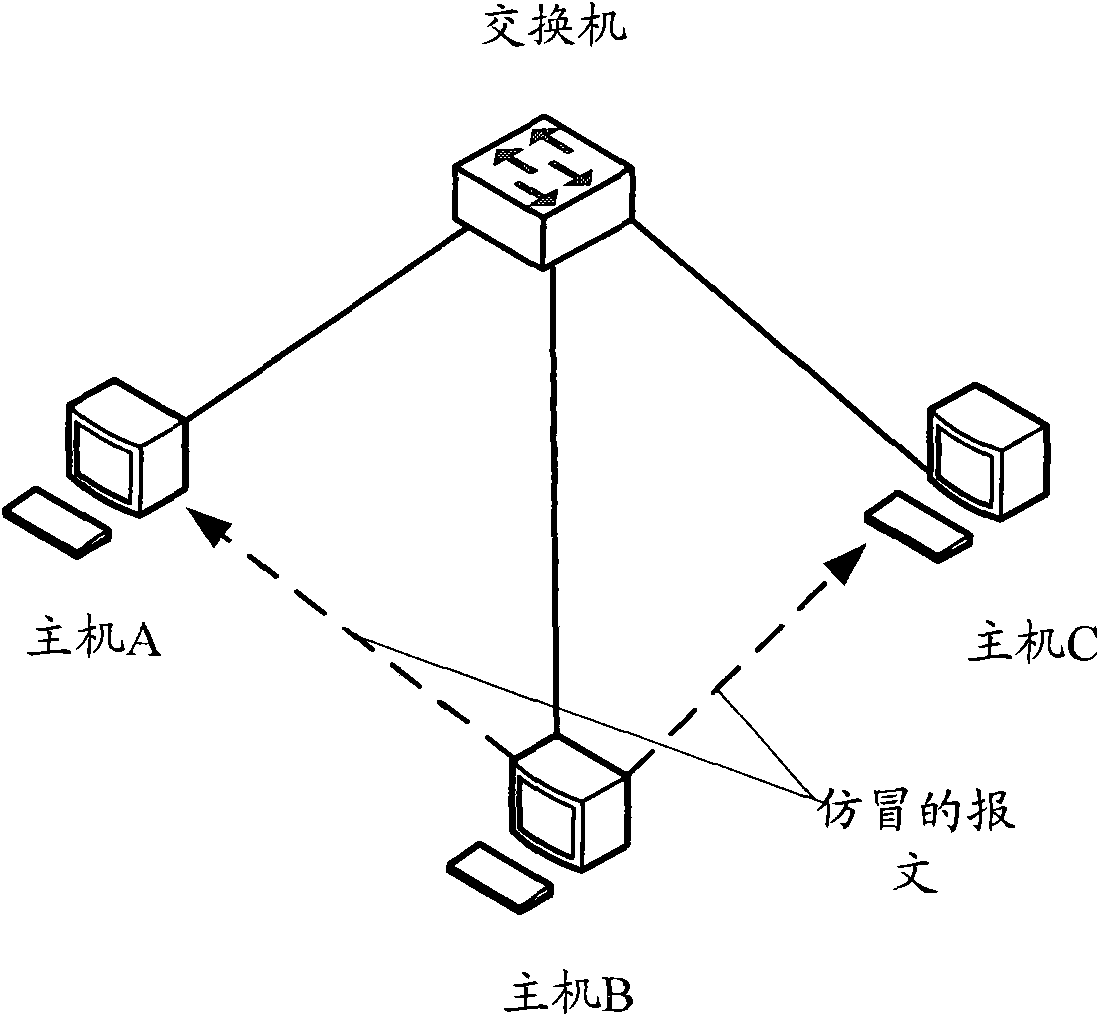
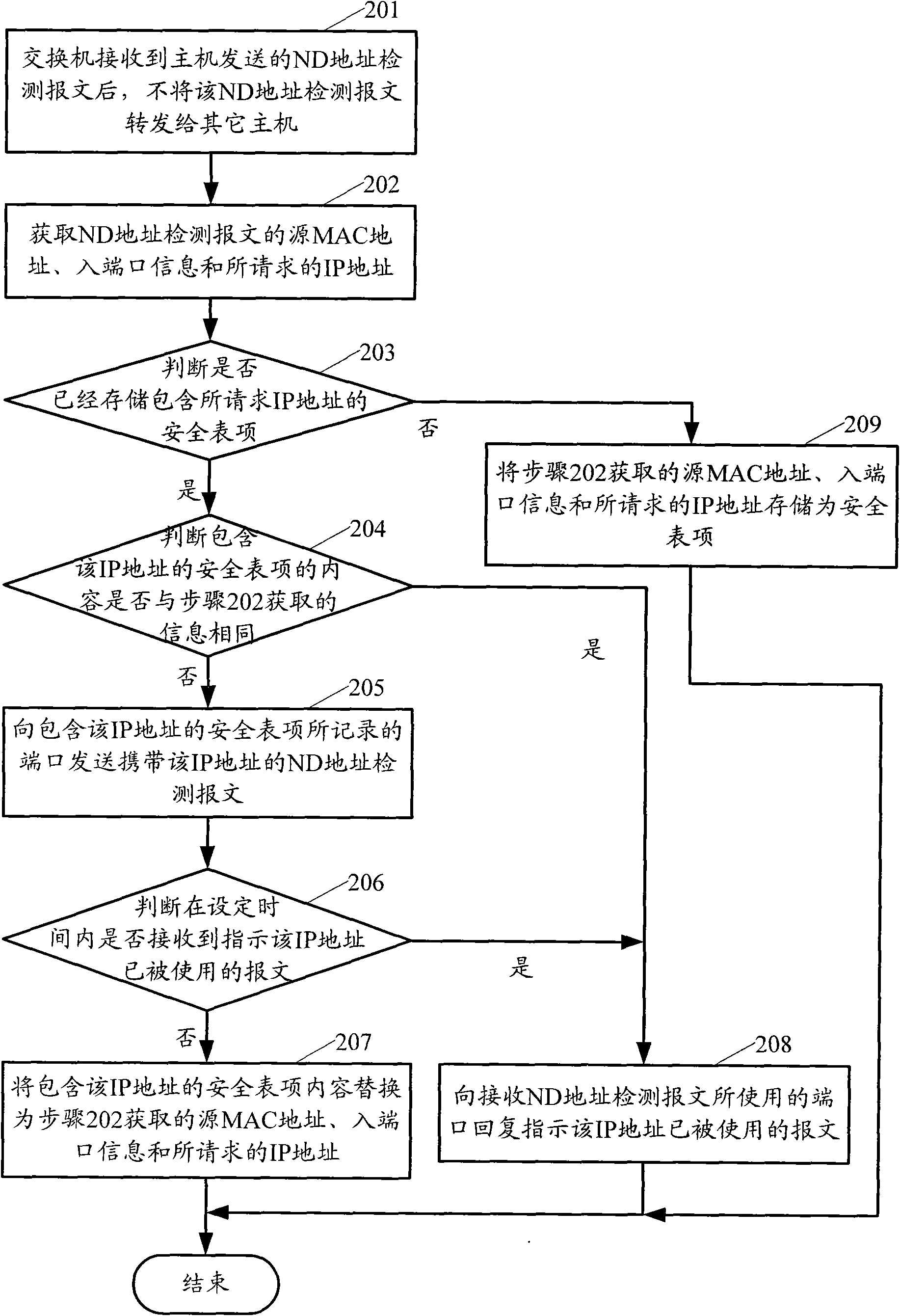
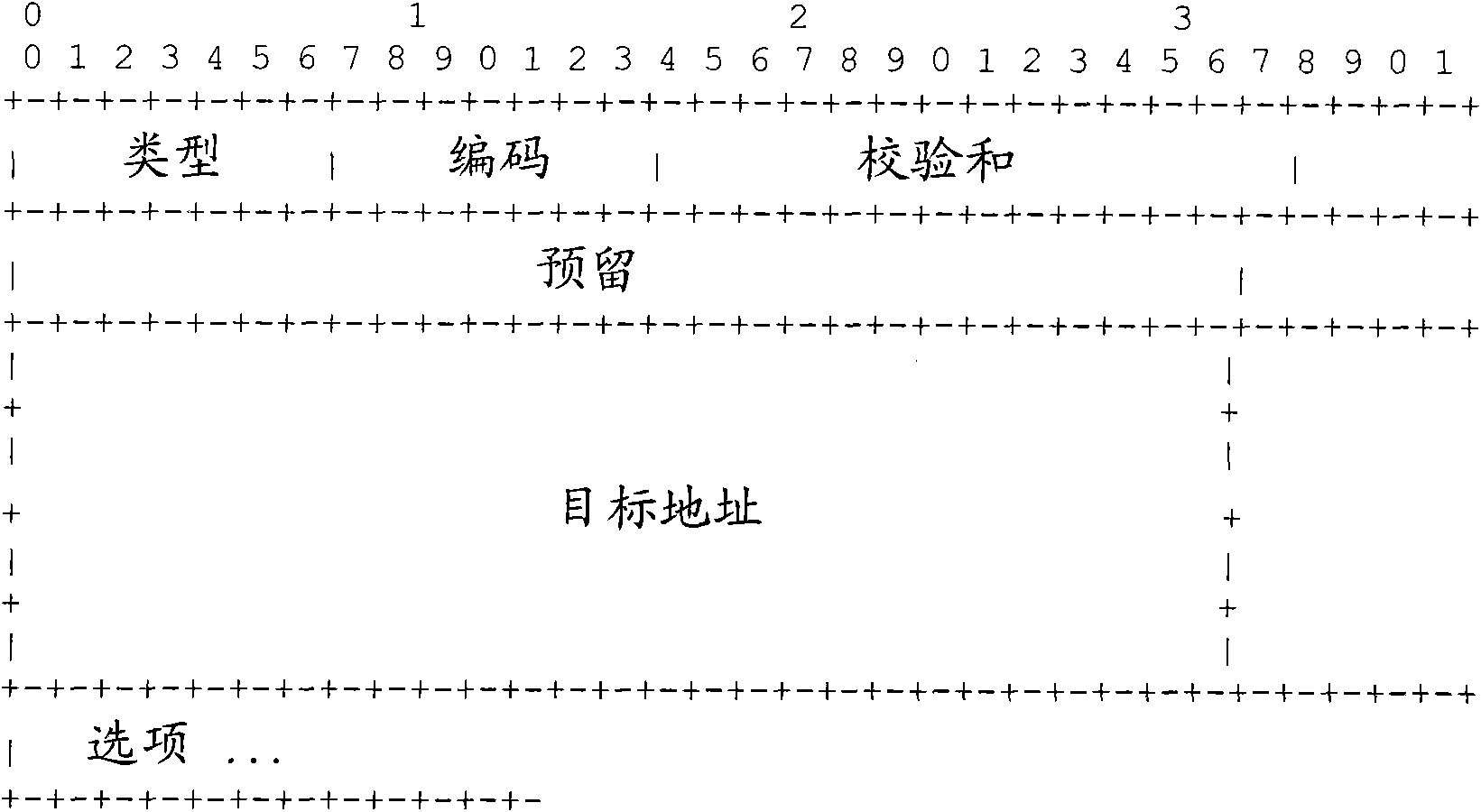
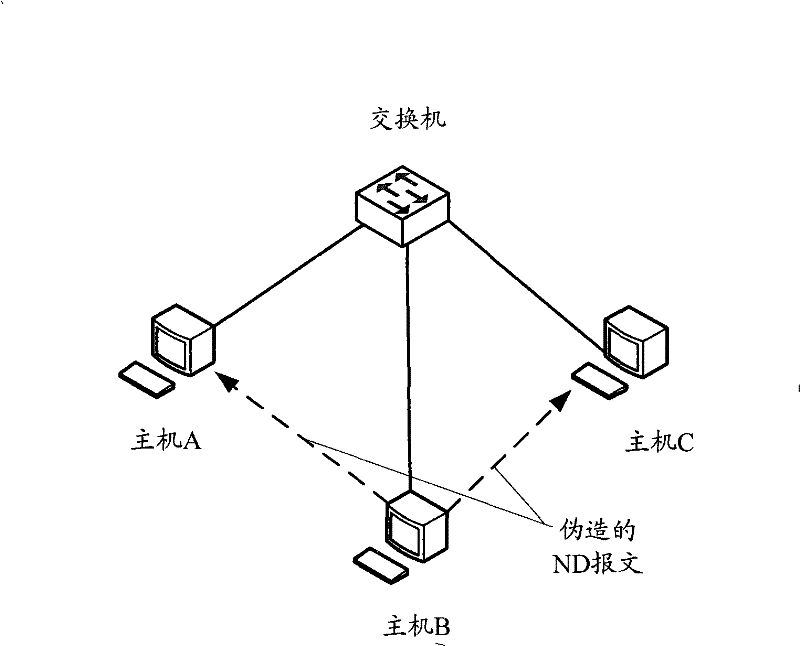
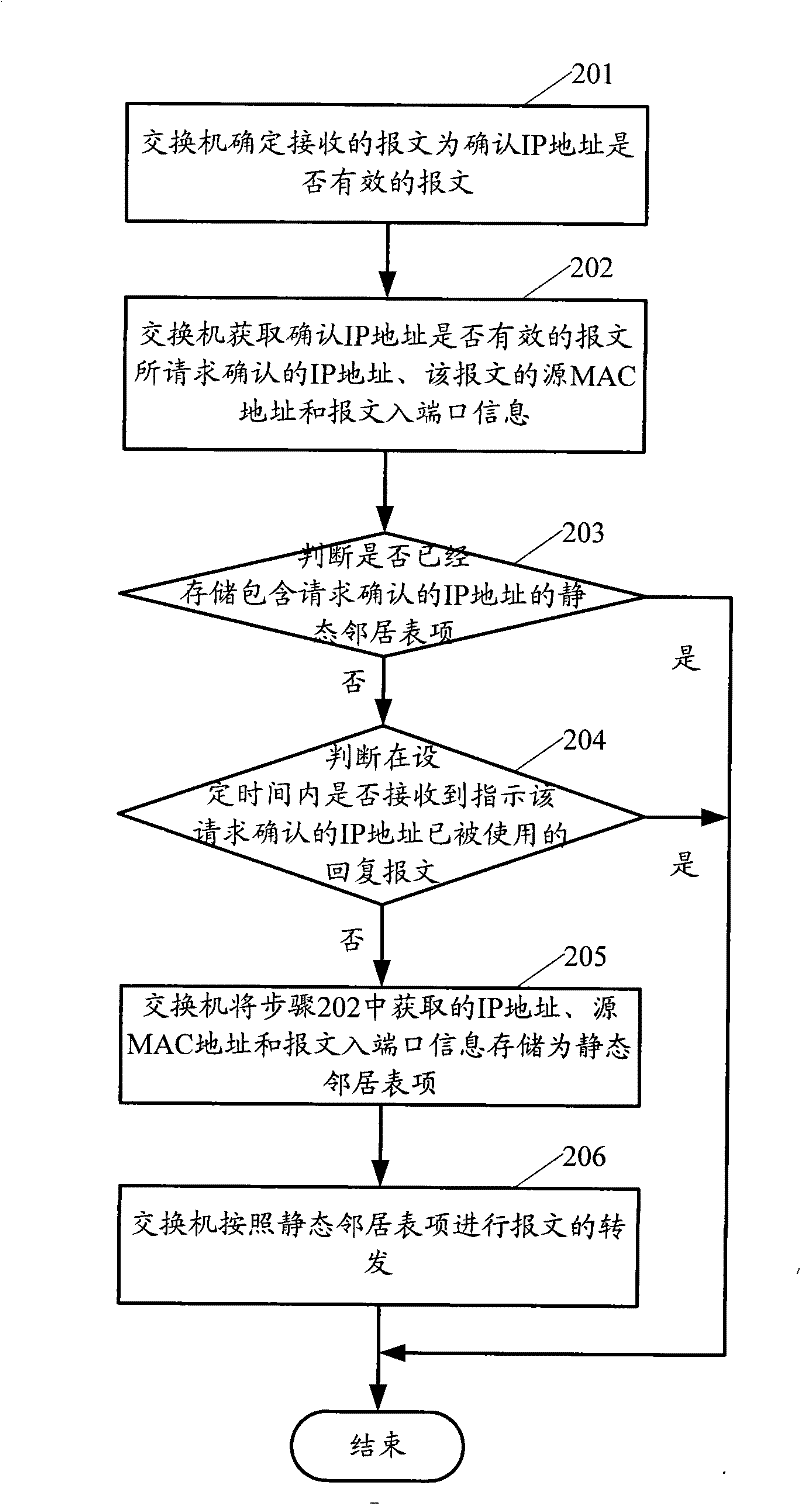
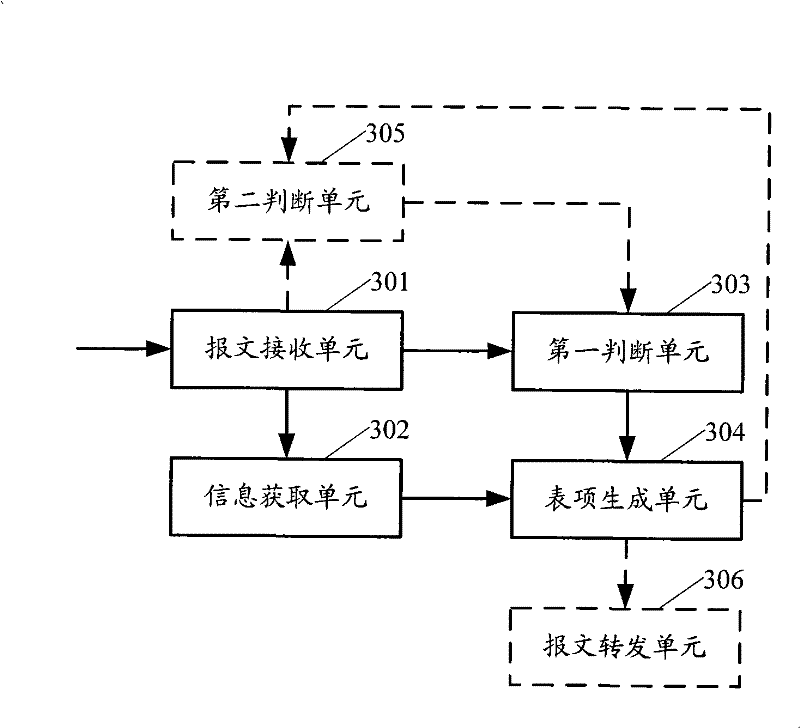
ActiveCN101552677APrevent security attacksData switching networksSecuring communicationIp addressMedia access control
The present invention provides a processing method and exchange equipment for address detected message, wherein, the method includes: when an exchange equipment receives neighbor discovery (ND) address detected message, the exchange equipment does not transmit the ND address detected message to the host computer; getting source media access control (MAC) address, ingress port information and the requested IP address of the ND detected message; judging whether the exchange equipment has stored security entry of the IP address, if yes then reply to the interface used for receiving the ND detected address message that the IP address has been used; otherwise, storing the obtained source MAC address, the ingress port message and the requested IP address as security entry. The invention can prevent security attack caused by counterfeiting message with has been used directing IP address more easily.
Owner:NEW H3C TECH CO LTD
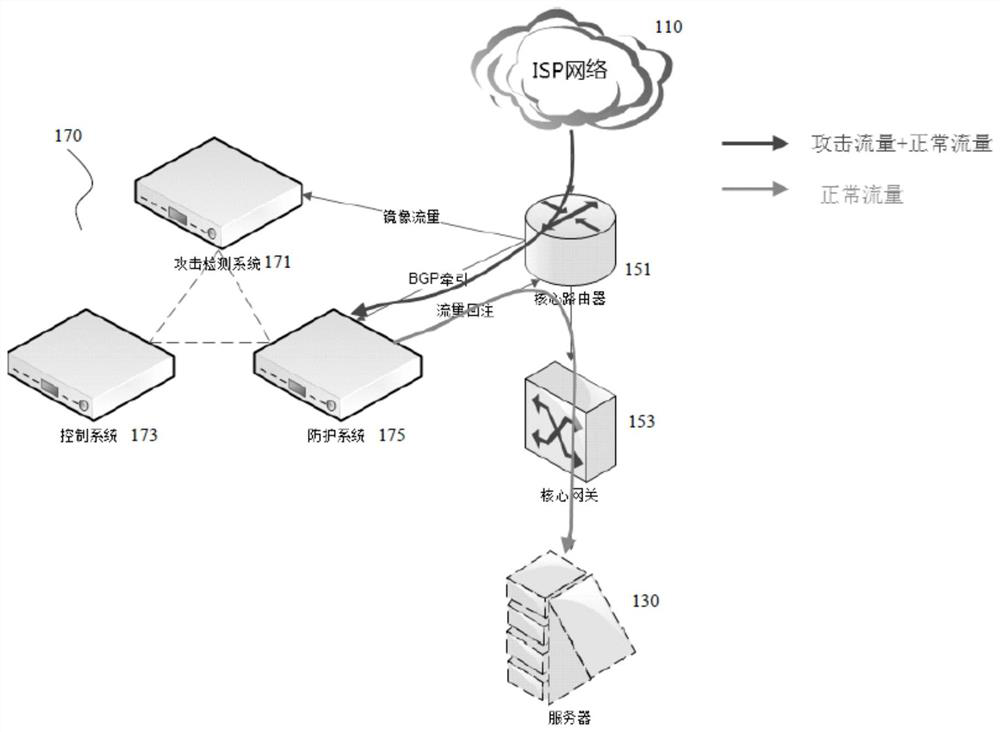
Security attack detection method and device, computer equipment and storage medium
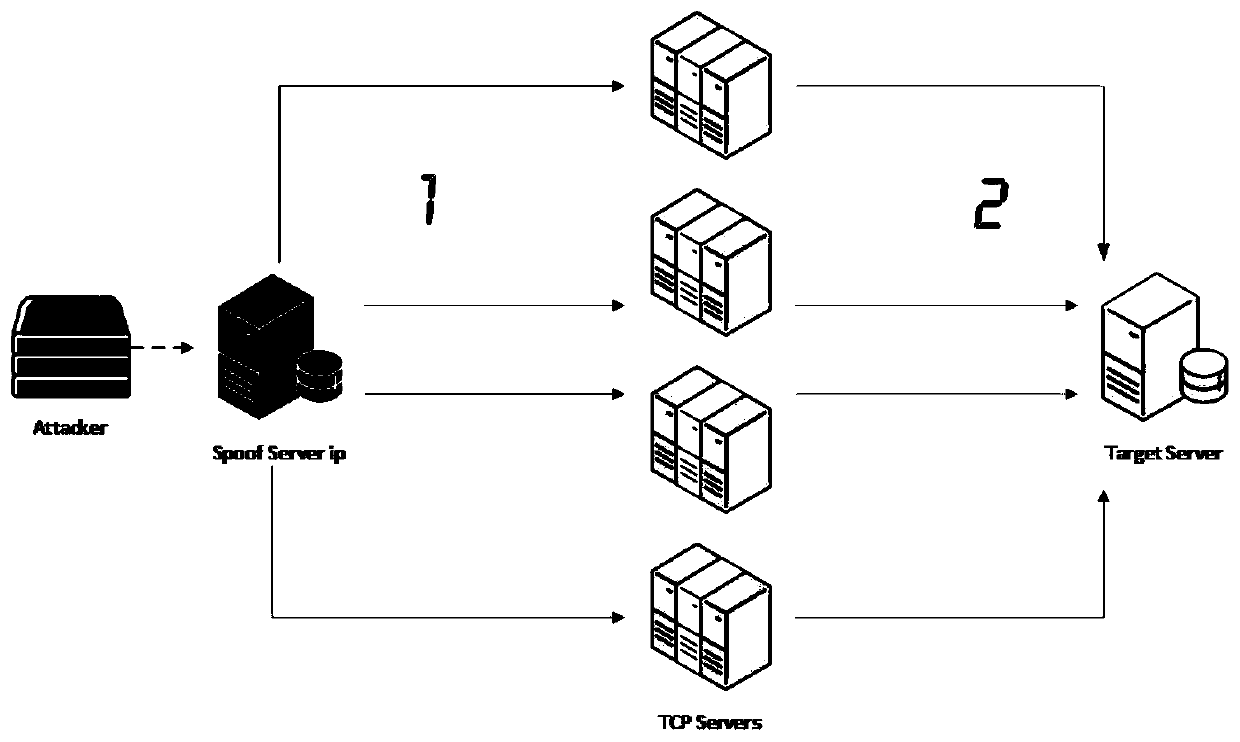
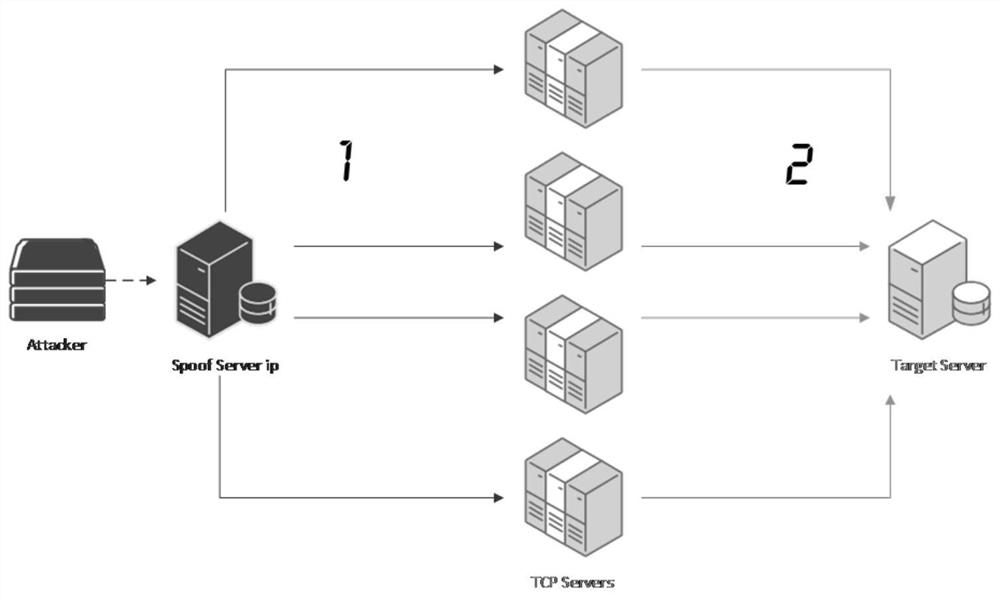
ActiveCN110266678APrevent security attacksNo manslaughterTransmissionTraffic capacityComputer network
The invention discloses a security attack detection method and device, computer equipment and a storage medium. The security attack detection method comprises the steps of acquiring mirror image flow; creating a session between the source end and the destination end according to the mirror image flow aiming at the source end which requests to be connected with the destination end; discarding a first specific message corresponding to the session in the mirror image flow, and waiting for the source end to retransmit the first specific message; forwarding the first specific message retransmitted by the source end to the destination end, and detecting whether the source end enters a connection establishment state or not by tracking the session; and if it is detected that the source end does not enter the connection establishment state, determining that the destination end is subjected to the TCP reflection attack from the source end, and intercepting the flow corresponding to the session in the flow to be transmitted to the destination end. By adopting the method and the device, the problem of high false detection rate in security attack detection in the prior art is solved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Reliable Ad hoc network security routing device
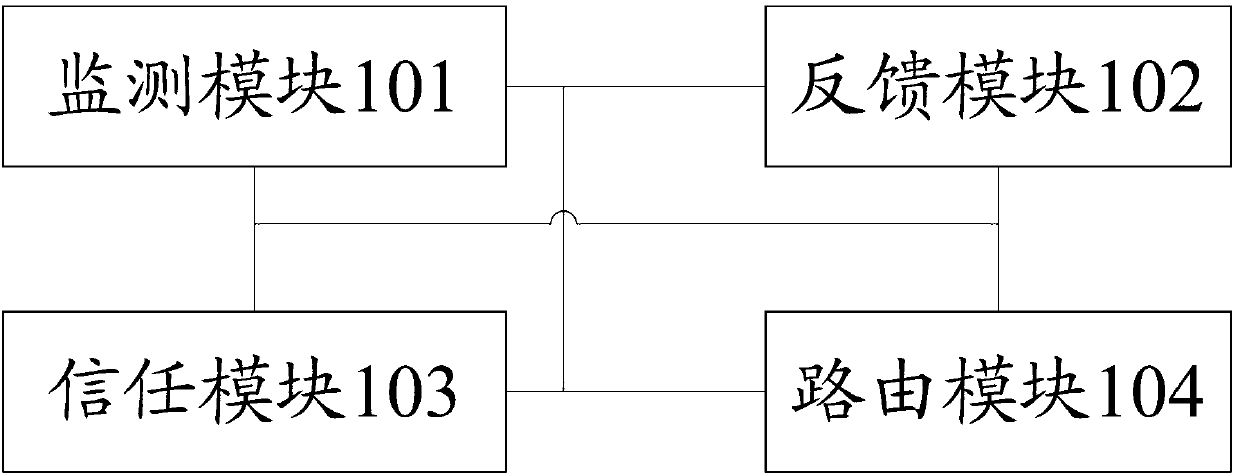
ActiveCN103347260AEnsure safetyReduce overheadPower managementSecurity arrangementData transmissionProtocol for Carrying Authentication for Network Access
The invention provides a reliable Ad hoc network security routing device and relates to the field of communication techniques. The reliable Ad hoc network security routing device comprises a monitoring module, a feedback module, a trust module and a routing module, wherein the monitoring module is used for monitoring and recording states and behaviors of all nodes in a network and providing node and network information, the feedback module can judge whether the node can participate routing according to the current states of the neighbor nodes, the trust module is used for finish acquiring, calculating and updating node trust values, and the routing module is used for providing message formats in a routing protocol, routing strategies and a routing work process. The reliable Ad hoc network security routing device can effectively improve data transmission rate, reduces energy consumption of nodes in the network, improves network performance, meanwhile can resist to security attacks in the network and can guarantee security operation of the network routing protocol.
Owner:深圳市国鸿信息技术有限公司
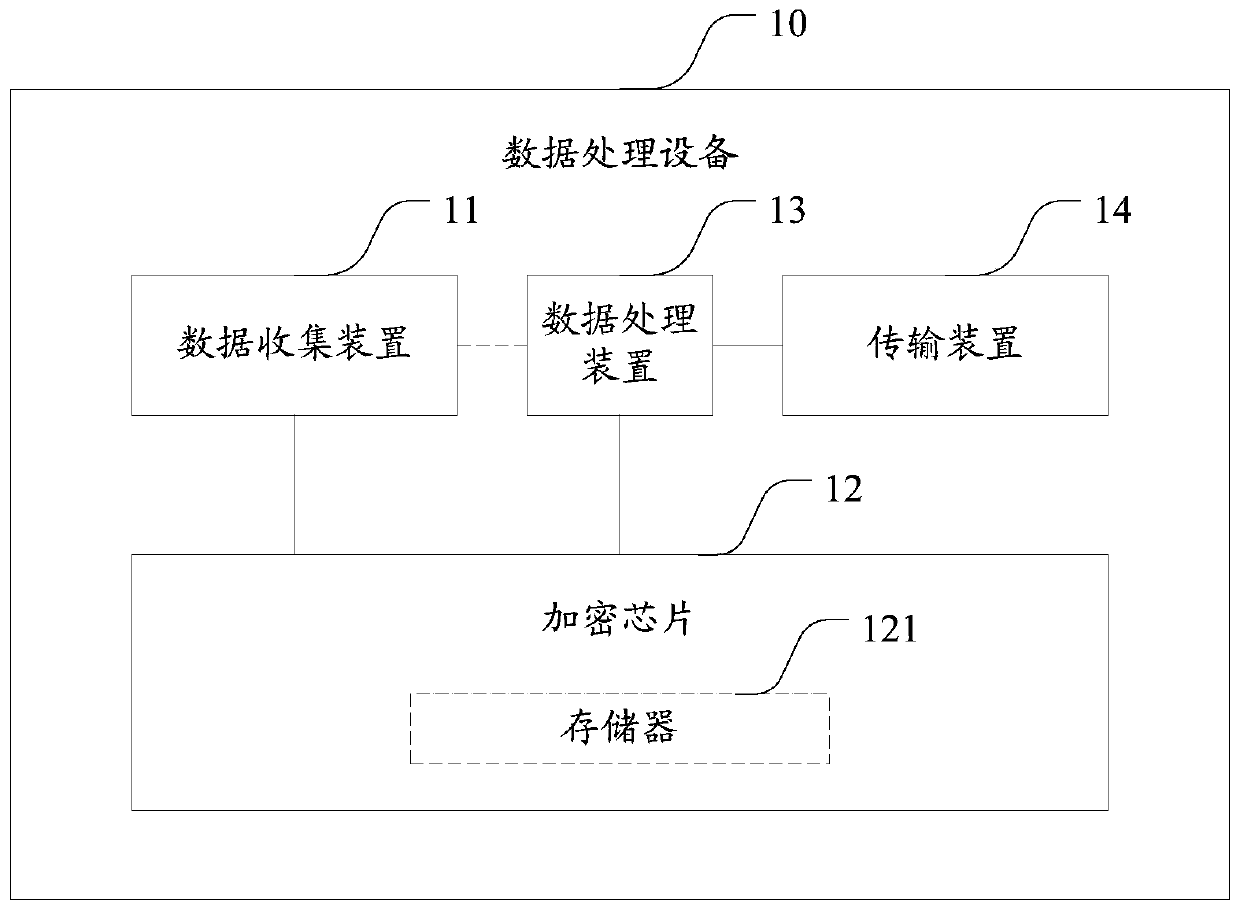
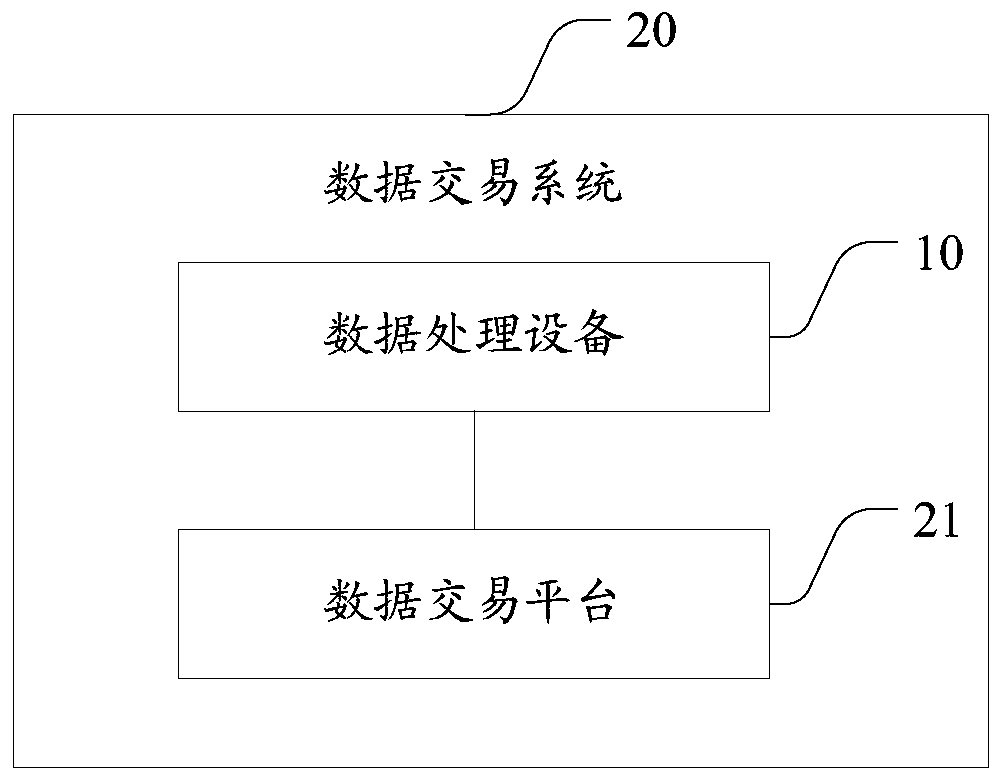
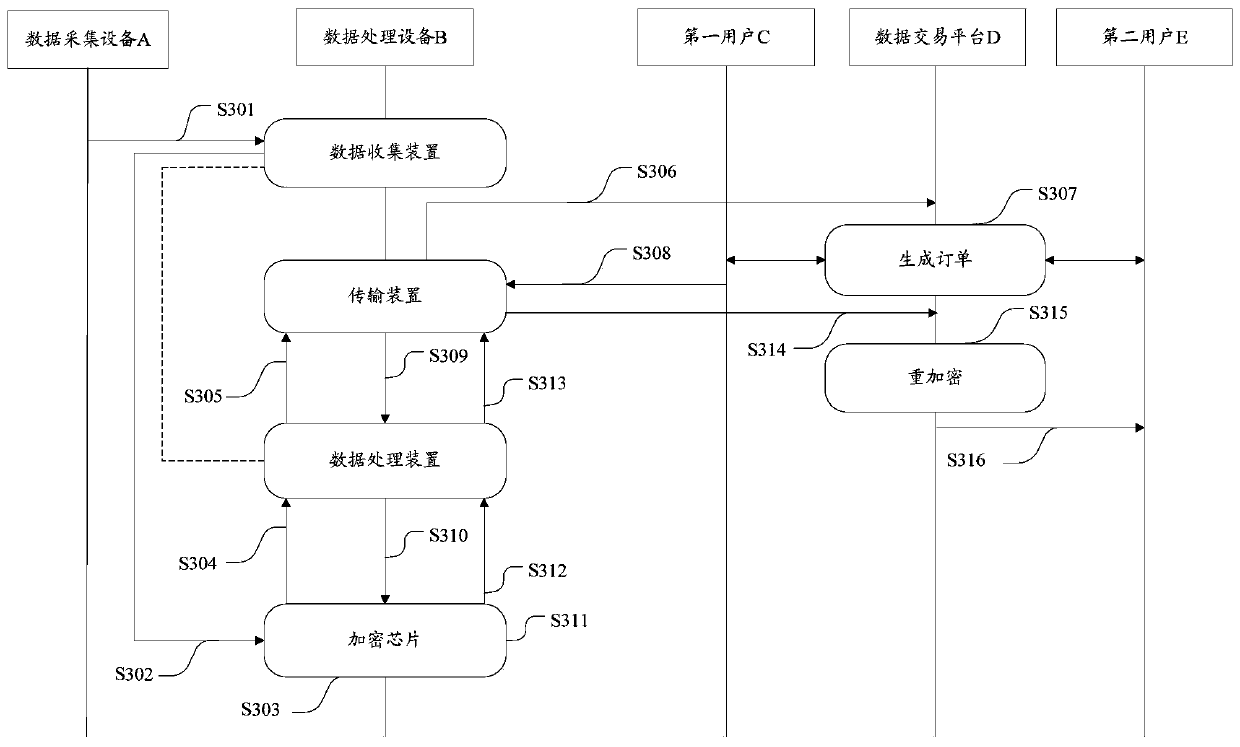
Data processing device and transaction system
The invention relates to a data processing device and a transaction system, the data processing equipment is coupled with a data acquisition device and comprises a data collection device, an encryption chip, a data processing device and a transmission device, and the data collection device is used for collecting data acquired by the data acquisition device and transmitting the data to the encryption chip; an Encryption chip, generating a public and private key pair of the first user, encrypting the collected data by adopting the public key of the first user to generate ciphertext data, transmitting the ciphertext data to the data processing device, receiving a public key of a second user from the data processing device, generating a re-encryption key by adopting the private key of the first user and the public key of the second user, and transmitting the re-encryption key to the data processing device; The data processing device receives the public key, transmitted by the transmissiondevice, of the second user, transmits the public key to the encryption chip, receives the ciphertext data and the re-encryption key and transmits the ciphertext data and the re-encryption key to the transmission device; And the transmission device is used for transmitting the ciphertext data and the re-encrypted data to a network side. By adopting the scheme, the security of data flow can be improved.
Owner:石更箭数据科技(上海)有限公司
Synchronous code encryption device and method for access control system
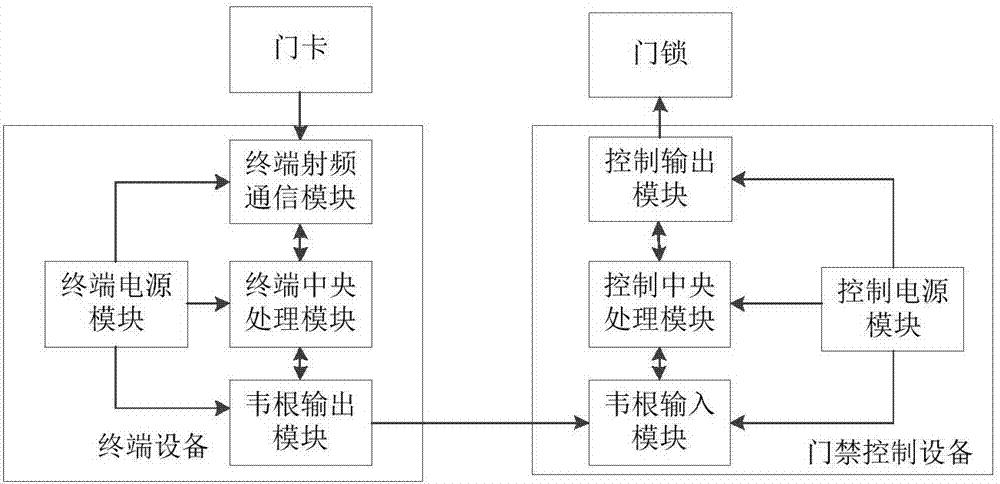
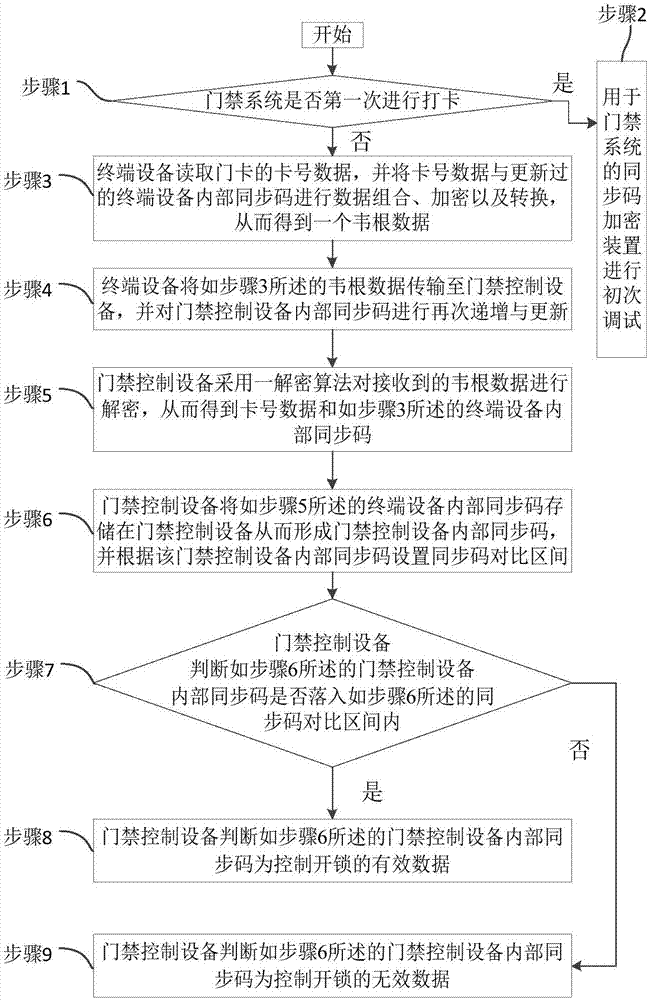
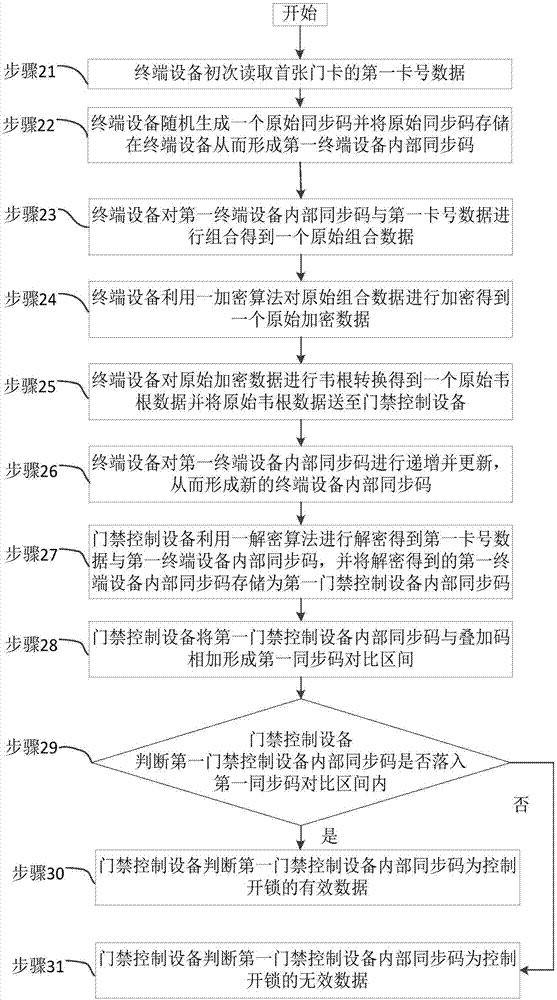
InactiveCN107170080AImprove safety and reliabilityImprove securityIndividual entry/exit registersMedia access controlData combination
The invention relates to the technical field of electronic information encryption and discloses a synchronous code encryption device for an access control system. The synchronous code encryption device comprises access control equipment and terminal equipment. The invention further discloses a synchronous code encryption method for the access control system, which comprises the following steps: step 1, judging whether to punch a card for the first time or not; step 2, performing initial debugging; step 3, reading card number data and performing data combination, encryption and conversion; step 4, transmitting Wiegand data and performing incremental update on synchronous codes inside the access control equipment; step 5, decrypting the Wiegand data; step 6, storing the synchronous codes inside the terminal equipment in the access control equipment and setting a synchronous code contrast interval; step 7, judging whether the synchronous codes inside the access control equipment fall into the synchronous code contrast interval or not; step 8, judging as effective data; step 9, judging as ineffective data. The synchronous code encryption device and method provided by the invention favorably prevent security attack in a manner of counterfeiting the effective data, so that the safety and the reliability of a door lock system are improved.
Owner:广州盛炬智能科技有限公司
Method and control chip for performing access control of memory device
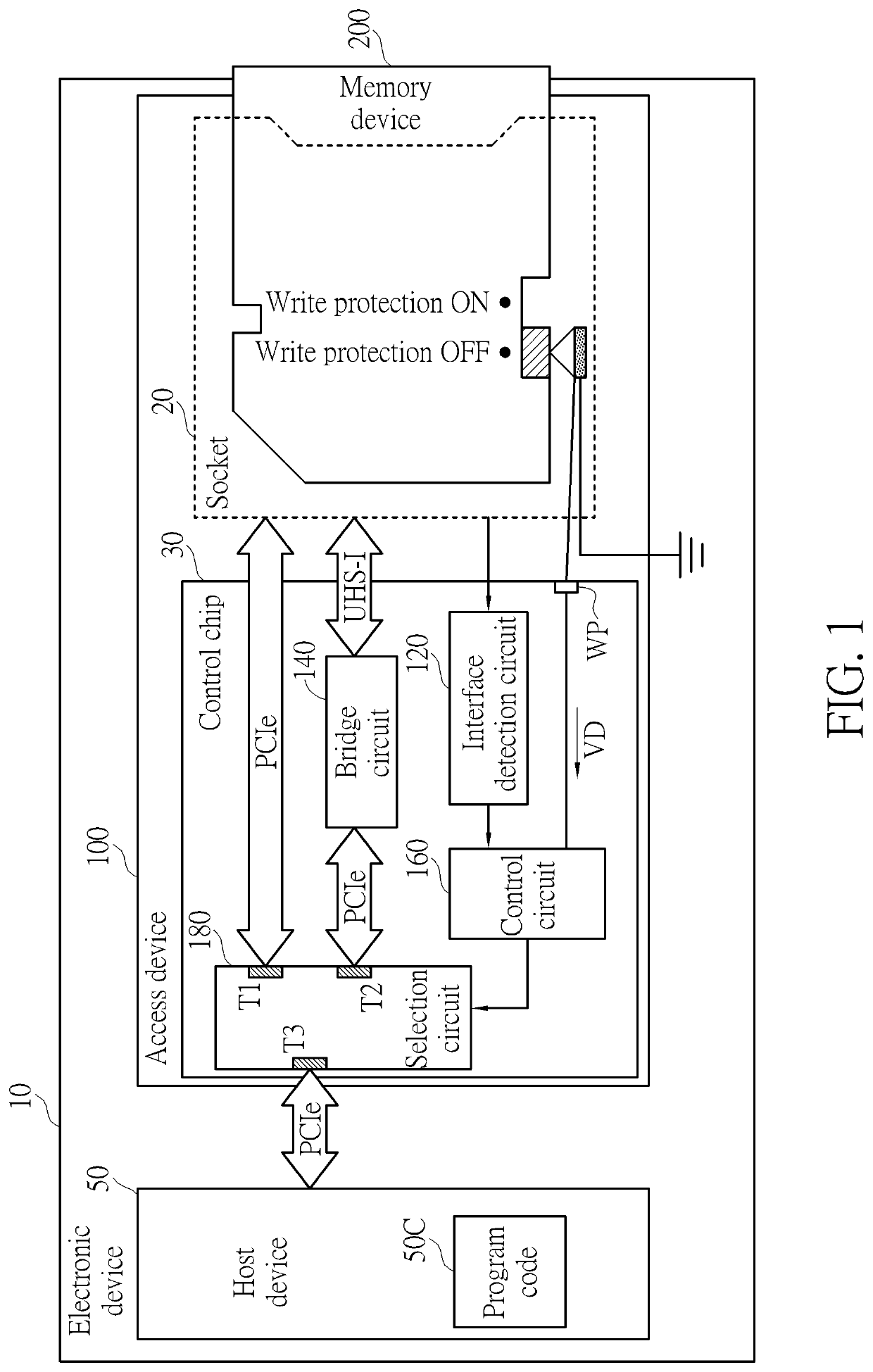
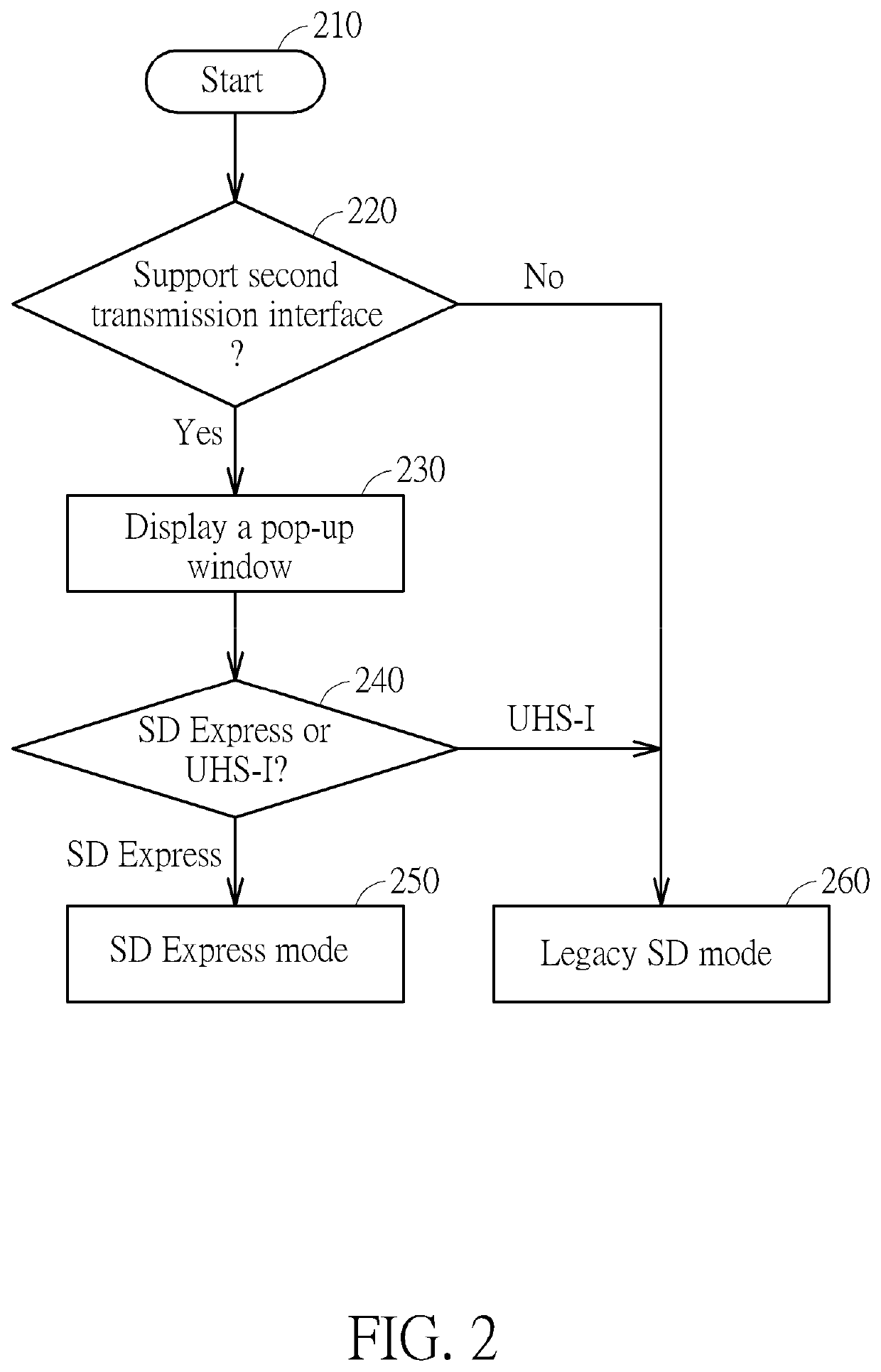
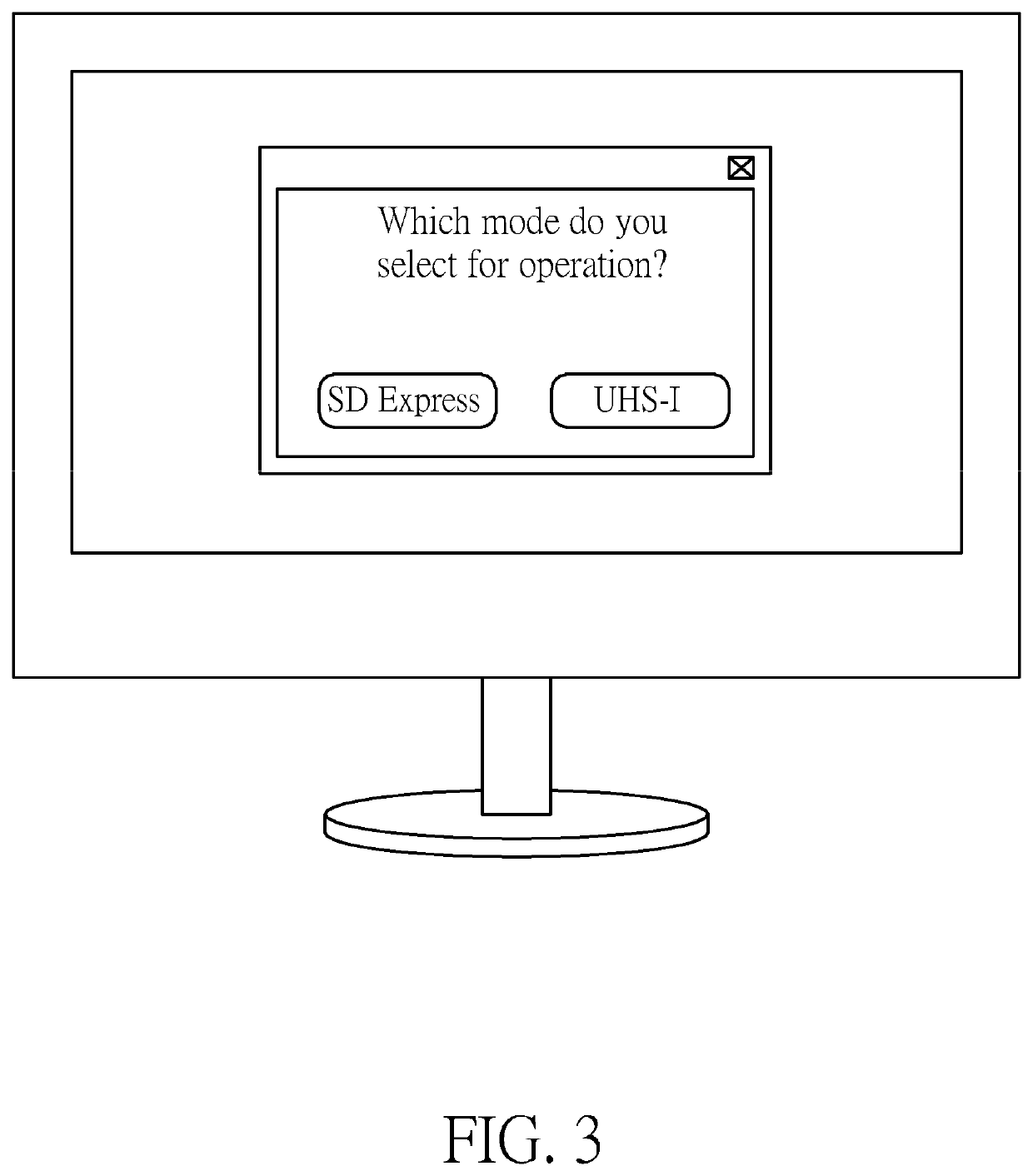
ActiveUS20210064551A1Prevent security attacksMemory architecture accessing/allocationUnauthorized memory use protectionComputer hardwareUser Privilege
A method and a control chip for performing access control of a memory device are provided, wherein the control chip is coupled to a host device. The method includes: utilizing a first transmission interface of the control chip to determine whether the memory device supports a second transmission interface different from the first transmission interface to generate a determination result; and according to user permissions of a user regarding the host device, determining whether to allow the control chip to decide whether to utilize the second transmission interface to access the memory device based on the determination result. In addition, if the user permissions satisfy a predetermined condition, a user interface of the host device may display a pop-up window in order to allow the user to decide which one of the first transmission interface and the second transmission interface to utilize for accessing the memory device.
Owner:REALTEK SEMICON CORP
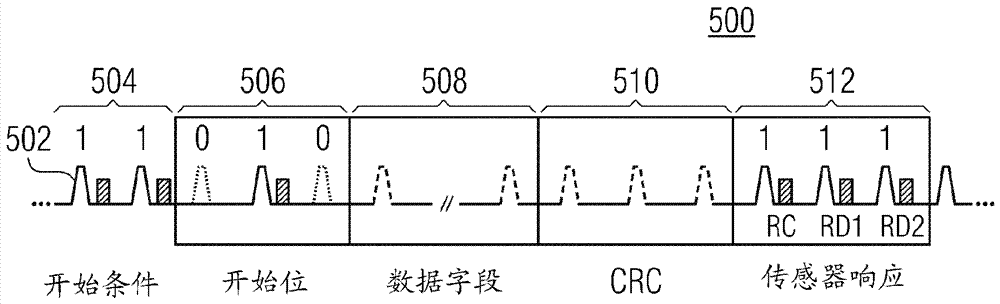
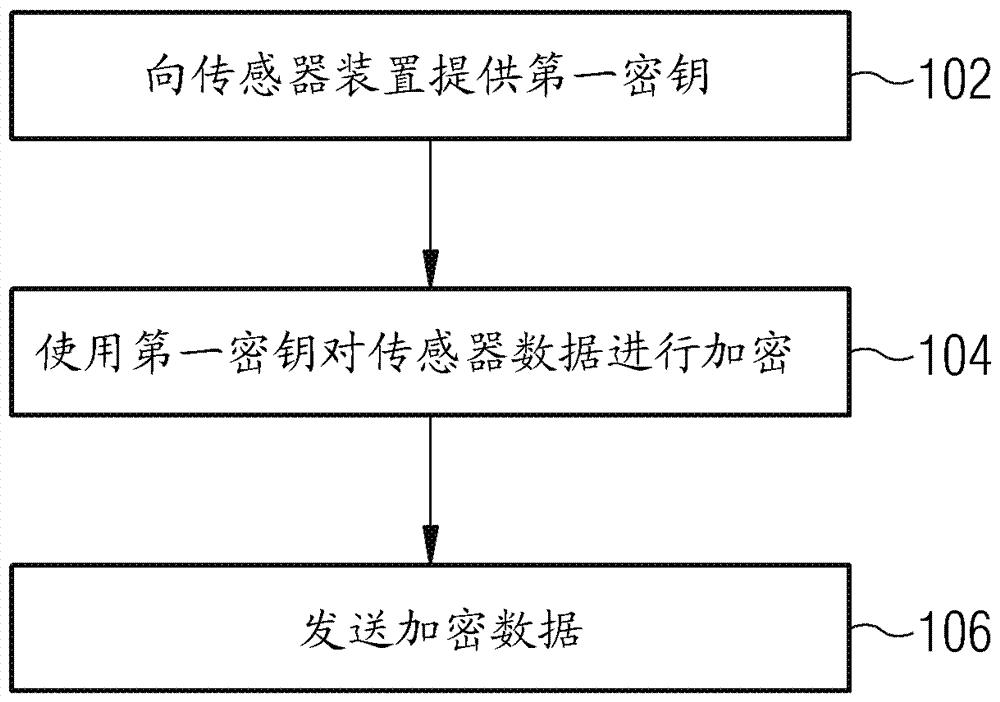
Method for communicating data from a sensor device to an electronic control unit, a sensor device and an electronic control unit
ActiveCN107135067APrevent security attacksAvoid destructionKey distribution for secure communicationMultiple keys/algorithms usageBidirectional communicationReal-time computing
The invention relates to a method for communicating data from a sensor device to an electronic control unit, a sensor device and an electronic control unit. The method for communicating data from a sensor device to an Electronic Control Unit using a single-wire bi-directional communication protocol includes providing a first key of the Electronic Control Unit to the sensor device, encrypting sensor data of the sensor device using the first key to determine encrypted data, and transmitting the encrypted data from the sensor device to the Electronic Control Unit.
Owner:INFINEON TECH AG
Access control method and communication equipment
ActiveCN113498055APrevent security attacksAssess restrictionNetwork topologiesInternet privacyEngineering
Provided are an access control method and communication equipment, the method comprising: sending first information and / or first indication information to a first target end, wherein the first information comprises at least one of the following items: index information of a second authentication server, related information of a manufacturer of first communication equipment, and address related information of the second authentication server; the first indication information is used for requesting to acquire a certificate related to a first network or indicating that the access type is limited service. In this way, information related to authentication of the communication equipment can be acquired, and authentication and configuration of the communication equipment can be further supported under the condition that the communication equipment does not acquire a certificate related to a network.
Owner:VIVO MOBILE COMM CO LTD
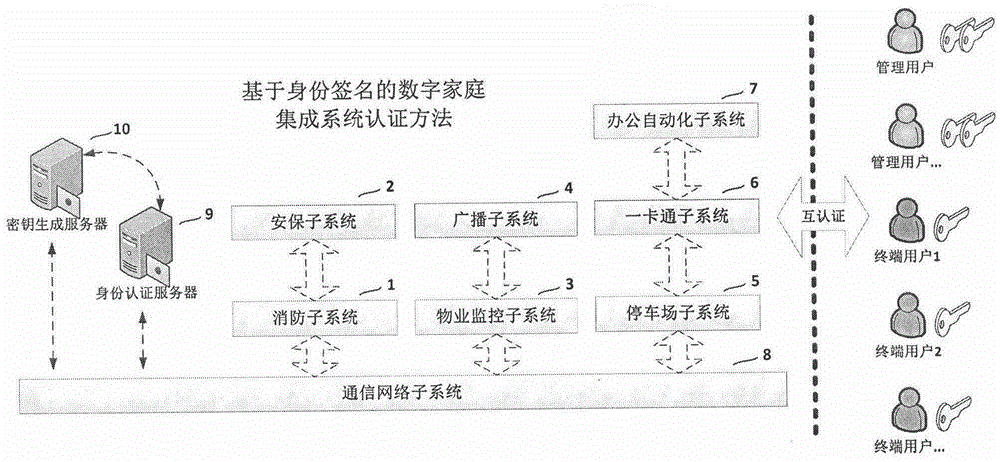
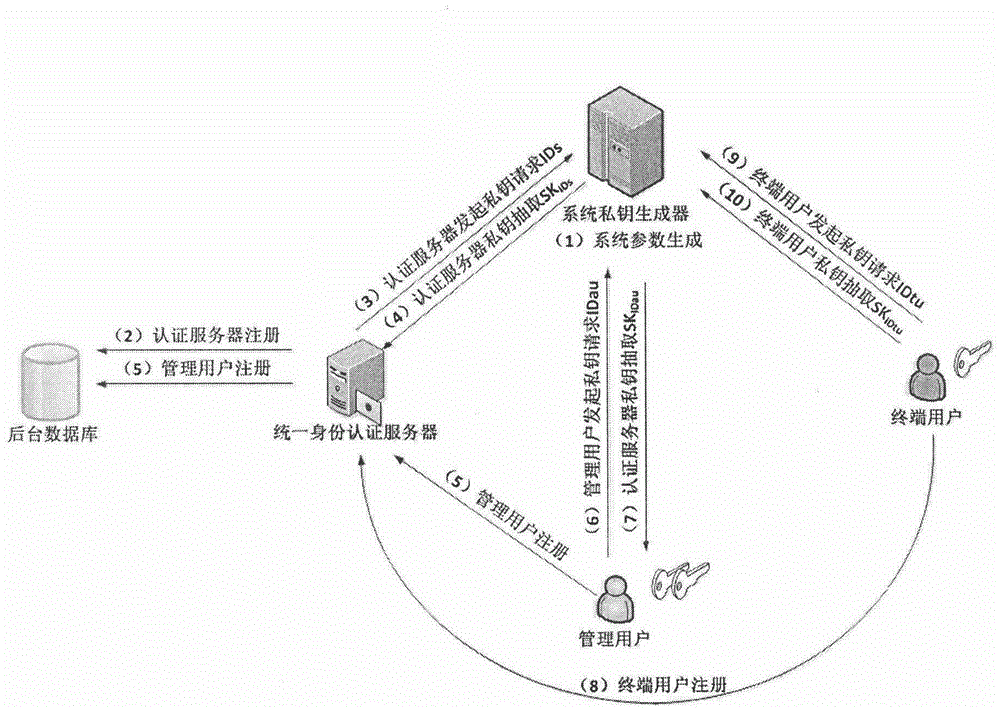
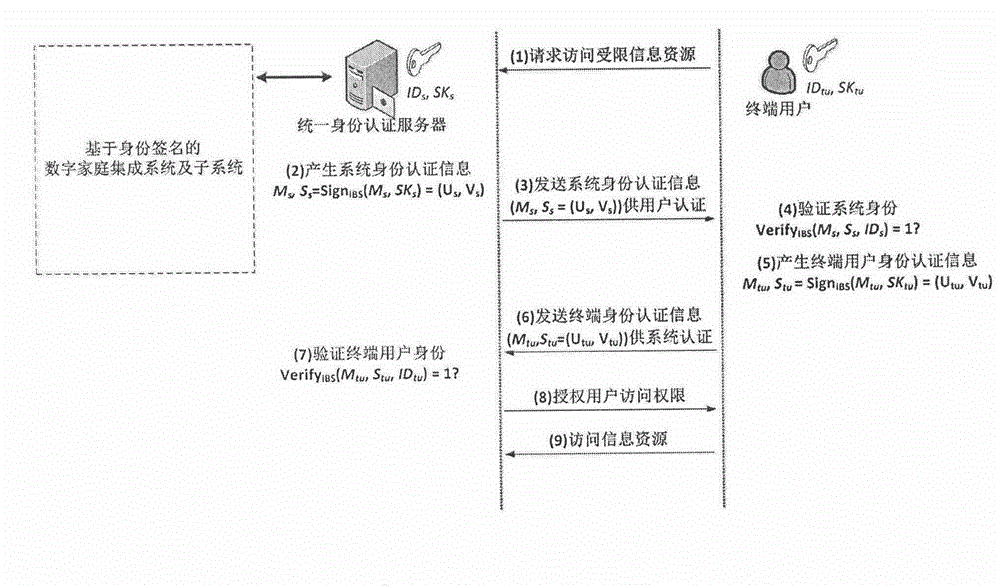
Identity-based signature authentication method for digital home integrated system
InactiveCN106209743APrevent security attacksImprove securityUser identity/authority verificationBroadcastingInformation security
The invention discloses an identity-based signature authentication method for a digital home integrated system. The system integrates multiple basic support and functional service sub-systems comprehensively applied for a digital home. The system comprises, but not limited to, a basic communication network sub-system, a fire fighting sub-system, a security sub-system, a property management sub-system, an office automation sub-system, a park sub-system, a one-card sub-system, a broadcasting sub-system and the like. According to the identity-based signature authentication method for the digital home integrated system provided by the invention, while the information safety of the system is improved and the personal privacy of users is protected, due to convenience of identity information authentication, the complexity of the digital home system in the aspect of information safety protection is reduced; the robustness and the whole performance of the system are improved; and the application environment of the system is enlarged.
Owner:GUANGZHOU XINGHAI INTELLIGENCE HOME SYST INTEGRATION +1
A security routing method for ad hoc network based on trust mechanism
The trust mechanism-based Ad hoc network security routing method provided by the present invention relates to the field of communication technology, including defining trust, obtaining attributes involved in trust, quantifying and evaluating attributes; comprehensively obtaining the total trust value of nodes; The trust value is a synthesis of quantified attribute values; monitor and record the status and behavior of each node in the network, and provide node and network information; monitor the current status of neighboring nodes, and judge whether the node is capable of participating in routing; obtain , Calculate and update the trust value of the node; provide the message format, routing strategy and routing working process inside the routing protocol; analyze and verify the security and performance of the above routing. The invention provides a trust mechanism-based Ad hoc network security routing method, which can effectively reduce the energy consumption of nodes in the network, improve network performance, resist security attacks in the network, and ensure the safe operation of network routing protocols.
Owner:山东政信大数据科技有限责任公司
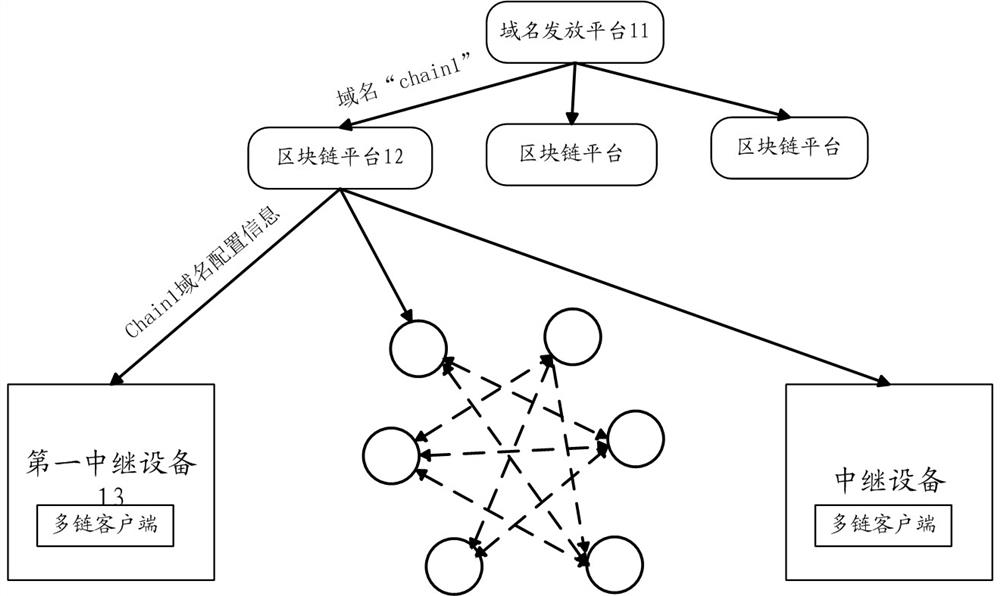
A method and device for updating blockchain domain name configuration
ActiveCN112737793BPrevent security attacksUser identity/authority verificationComputer hardwareDomain name
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD +1
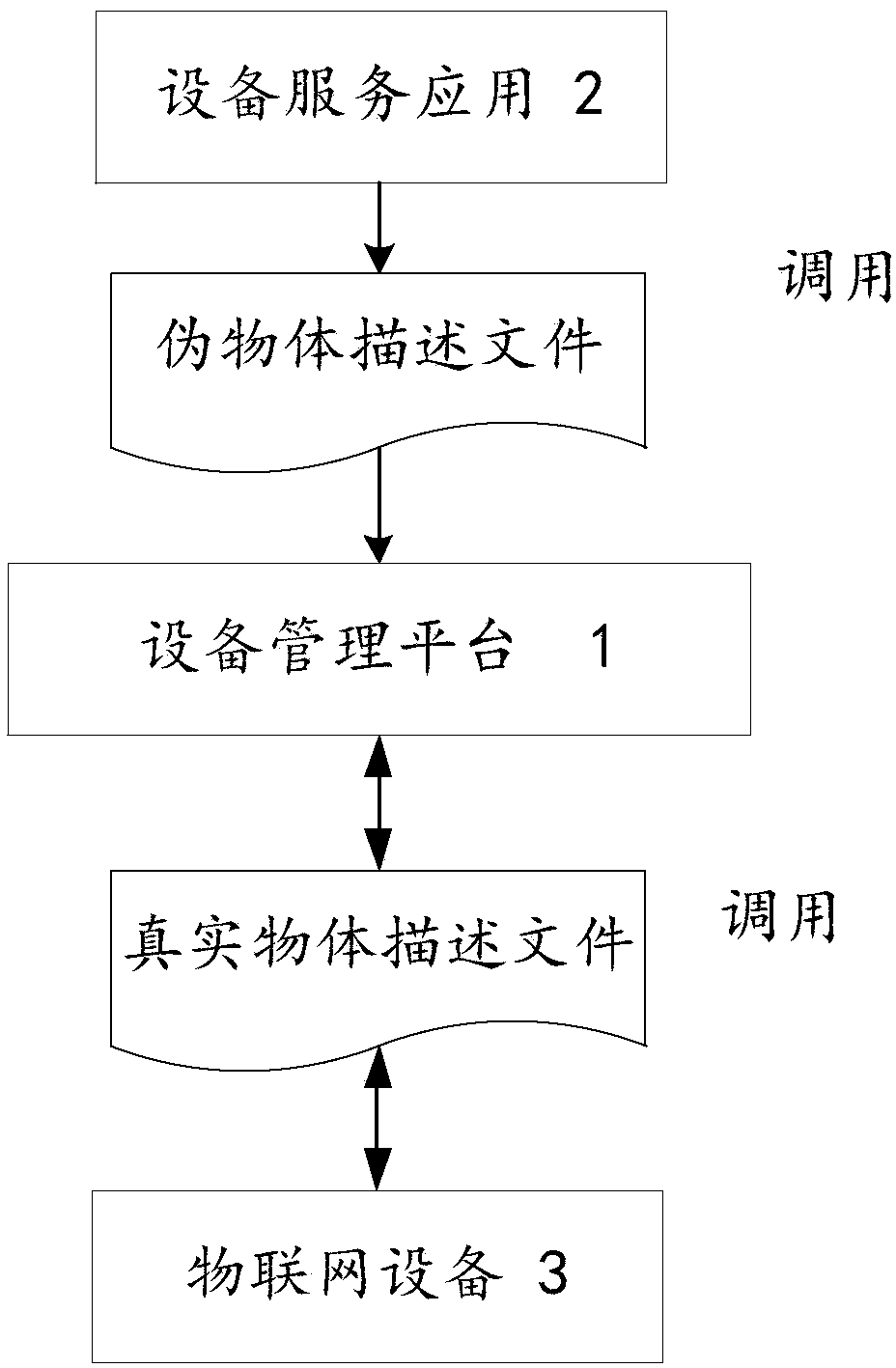
an Internet of things system with a network mask based on an object description method
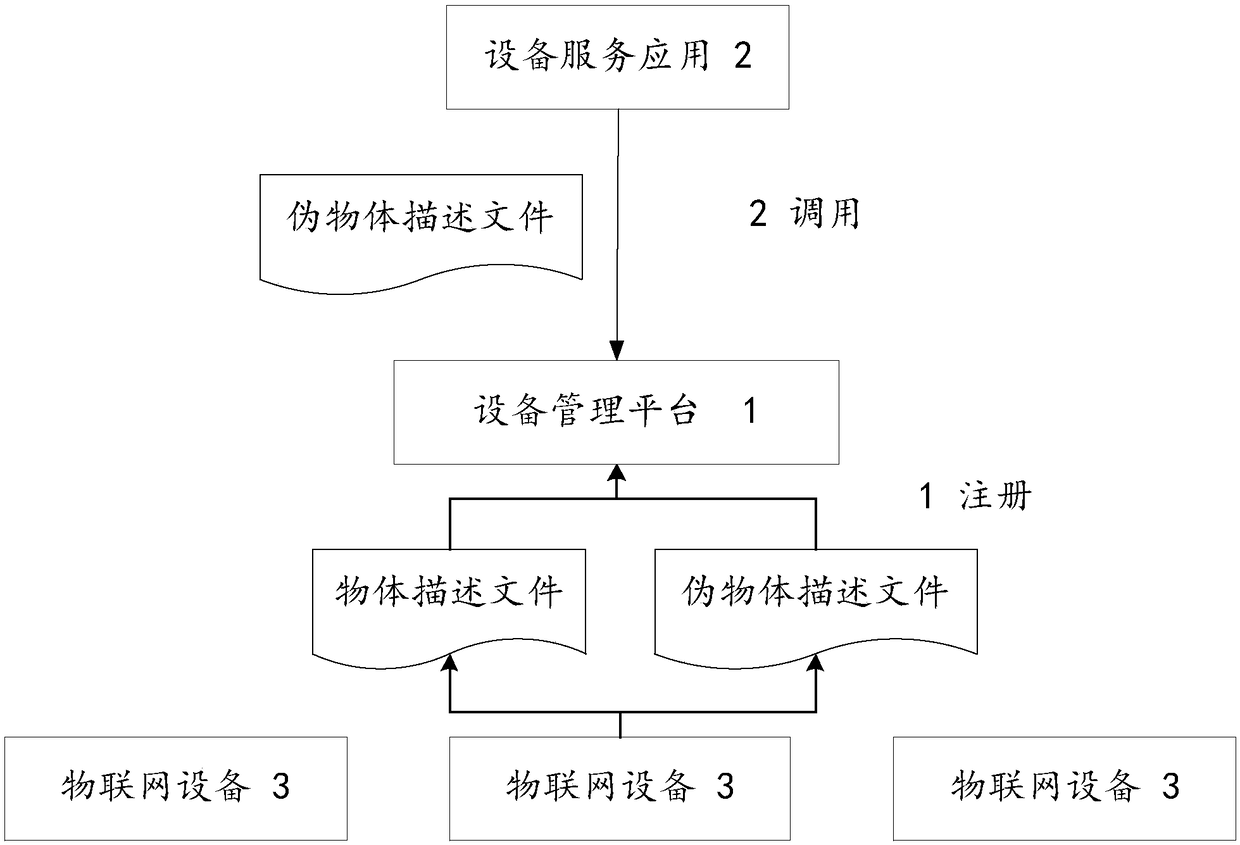
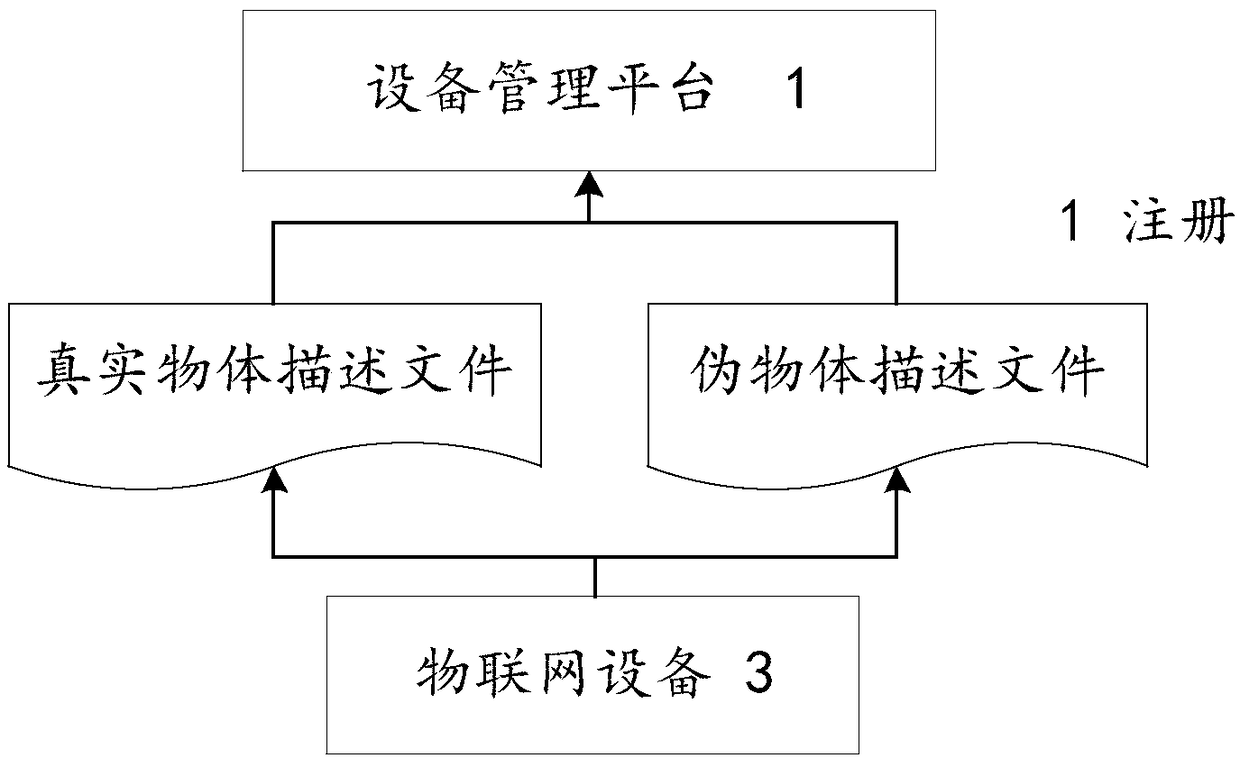
ActiveCN109040313AEnhance camouflagePrevent security attacksTransmissionInternet of ThingsObject description
An Internet of things system with a network mask based on an object description method includes a device management platform, a plurality of device service applications, and a plurality of Internet ofThings devices. Wherein the internet of things device is based on an object description template, A real object description file and a pseudo object description file are formed, an access request issent to the device management platform and the registering is performed, the calling of the device management platform is received by the object description file, wherein the interaction between the device management platform and the device discovery platform and the device service application is based on the pseudo object description file, and the invocation between the device management platformand the Internet of Things device is based on the real object description file. The object description method can be used for describing all objects in the Internet of Things, and has compatibility and universality. By using the real object description method and the pseudo object description method, the malicious attacker is prevented from launching a direct malicious attack on the device itselfbecause of obtaining the information of the device invocation.
Owner:INFORMATION SCI RES INST OF CETC
Integrated circuit with secure metadata store
InactiveUS9100684B2Area minimizationMaintain securityTelevision system detailsColor television detailsSemiconductorDatabase
A semiconductor integrated circuit for processing content data by encrypting or decrypting the data has one or more inputs to received content and metadata. A metadata store comprises two portions, a first portion for storing metadata itself and a second portion for storing an address of locations of bitfields of metadata. This arrangement allows for efficient storage of the metadata but requires certain rules to ensure that bitfields of metadata cannot be stored and used with anything other than the content with which the metadata is associated.
Owner:STMICROELECTRONICS (RES & DEV) LTD
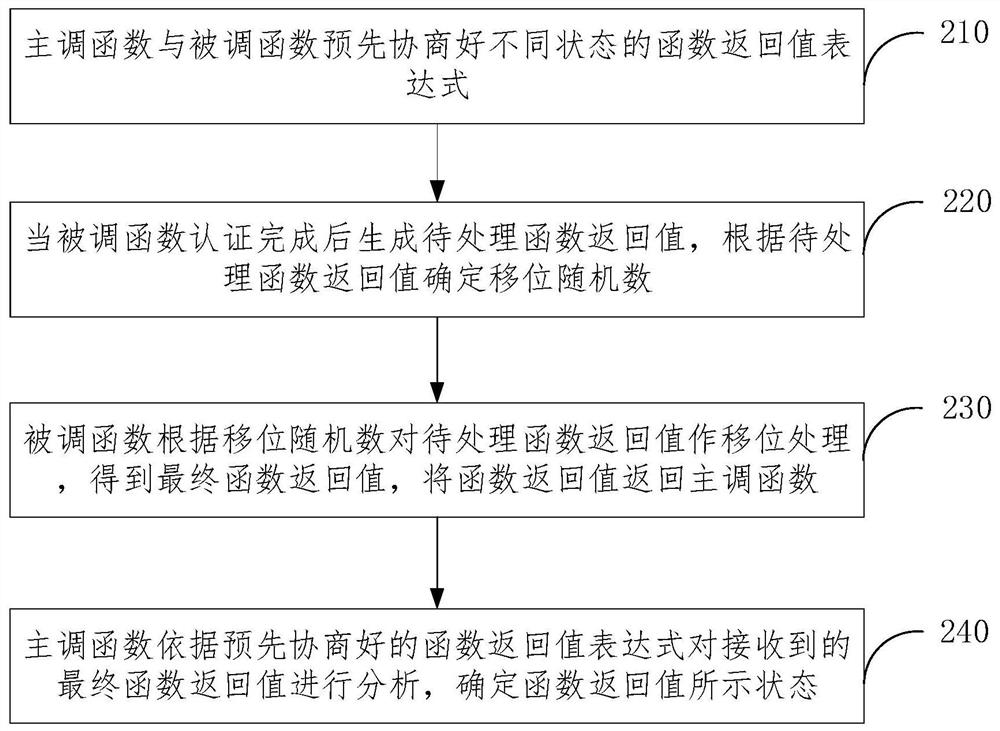
Implementation method and application of security authentication function return value
ActiveCN111104668BReduce tamperingEnsure safetyPlatform integrity maintainanceSecure authenticationComputer science
The application discloses a method for realizing a return value of a security authentication function and an application thereof. The method includes that the calling function and the called function pre-negotiate function return value expressions in different states; when the called function executes security authentication, it generates the return value of the function to be processed, and determines the shift random number according to the return value of the function to be processed ;The called function performs shift processing on the return value of the function to be processed according to the shift random number, obtains the final function return value, and returns the function return value to the calling function; The final function return value is analyzed to determine the state indicated by the function return value. The application method is used to realize a certain degree of interaction between the calling function and the called function during the calling operation, and the processed function return value cannot be easily identified, which ensures the safety of the function execution result and reduces the function return. Potential for the value to be tampered with on return.
Owner:HENGBAO
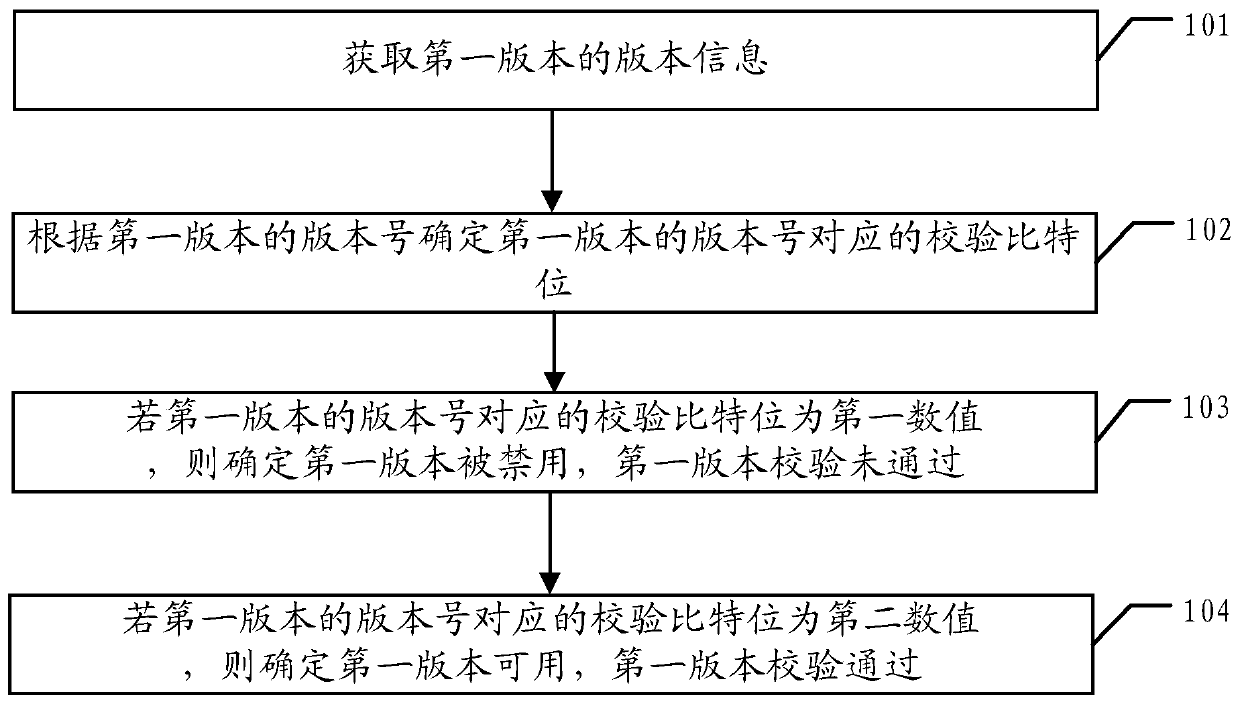
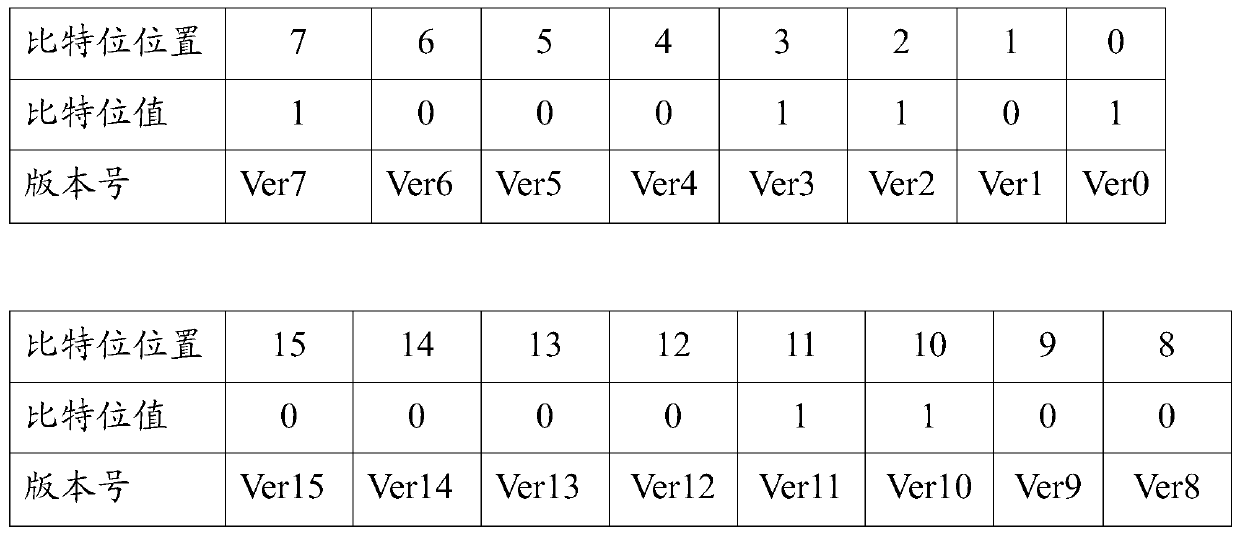
A version verification method, device and terminal equipment
ActiveCN106650460BPrevent security attacksPlatform integrity maintainanceTerminal equipmentSecurity check
A version check method, apparatus and terminal device, used for preventing an attacker from using versions having security vulnerabilities to carry out security attacks so as to improve system security. In the method, a version number of each version has a corresponding check bit, and forbidden information and available information of a version are indicated by means of the bits; when acquiring a first version, a check bit corresponding to a version number is first determined according to the version number of the version; if the check bit corresponding to the version number of the version is a first numerical value, the version is determined to be forbidden and the check has not passed; and if the check bit corresponding to the version number of the version is a second numerical value, then the version is determined to be available and the check has passed. By means of said method, a security check may be conducted on the versions, and versions which do not pass the check may not be used, thus an attacker may be prevented from using versions having security vulnerabilities to carry out security attacks.
Owner:SHANGHAI HUAWEI TECH CO LTD
Assets safety management method, system and network element equipment of telecom network
ActiveCN101136767BPrevent security attacksData switching networksTelecommunications networkSecure state
The method is applicable to telecomm network including at least one device of net element. In the method, device of net element takes charge of tracking safe state of asset for each asset included inadjacent device of net element, and manages safety of asset according to safe state of asset. The invention also discloses the system and device of net element corresponding to the method as well as technique for carrying out safety management for peripheral assets based on individual device.
Owner:HUAWEI TECH CO LTD
Generation method and apparatus for neighbor table items
The present invention provides generation method and apparatus for neighbor table items, exchange equipment receives message of affirming the IP address whether effective or not, judging whether receive reversion message of indicating the requested affirming IP address is used or not in setting time, if not, restore the source medium access control (MAC) address, ingress port message of the message and the requested affirming IP address as static neighbor table item. The invention can prevent the IP address from copy and modification at the same time of assuring the requested IP address effective, effectively preventing security attack.
Owner:NEW H3C TECH CO LTD
Security attack detection method, device, computer equipment and storage medium
ActiveCN110266678BPrevent security attacksNo manslaughterSecuring communicationComputer networkAttack
The invention discloses a security attack detection method, device, computer equipment and storage medium. The security attack detection method includes: acquiring mirrored traffic; and creating the source according to the mirrored traffic for a source terminal requesting to connect to the destination terminal. The session between the end and the destination end; discarding the first specific message corresponding to the session in the mirrored traffic, waiting for the source end to retransmit the first specific message; The first specific message retransmitted by the source end is forwarded to the destination end, and by tracking the session, it is detected whether the source end has entered the connection establishment state; if it is detected that the source end has not entered the If the above connection establishment status is established, it is confirmed that the destination end is subjected to a TCP reflection attack from the source end, and the flow corresponding to the session in the flow to be transmitted to the destination end is intercepted. The invention solves the problem of high false detection rate in security attack detection in the prior art.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Vehicle authentication and message verification method in vehicle network environment
ActiveCN109922475BGuaranteed privacyPrivacy protectionPublic key for secure communicationParticular environment based servicesMobile vehicleIn vehicle
The present invention proposes a method of vehicle certification and message verification in the car network environment. The steps are: the trust agency initializes the system; the vehicle unit registers, the roadside unit is registered; the temporary key to the roadside unit is released; the vehicle certification stage; Trust agencies verify the legitimacy of roadside units through digital signatures, trust agencies to extract messages and verify the legitimacy of the car.Send to the car, the car extraction of the temporary main key key; the car calculates the temporary identifier and the temporary private key to generate traffic messages to sign and broadcast it; when other cars receive the information of the car broadcast, the effectiveness of the broadcast message is verified by dual -line -based mapping.The present invention can ensure the safety of vehicles in the vehicle network of vehicle network, and also ensure the safety of traffic information issued by legal vehicles, and has greater application value in the application environment in the mobile vehicle network environment.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Integrated circuit with secure metadata store
InactiveUS20080044020A1Area minimizationMaintain securityTelevision system detailsColor television detailsComputer scienceDatabase
A semiconductor integrated circuit for processing content data by encrypting or decrypting the data has one or more inputs to received content and metadata. A metadata store comprises two portions, a first portion for storing metadata itself and a second portion for storing an address of locations of bitfields of metadata. This arrangement allows for efficient storage of the metadata but requires certain rules to ensure that bitfields of metadata cannot be stored and used with anything other than the content with which the metadata is associated.
Owner:STMICROELECTRONICS (RES & DEV) LTD
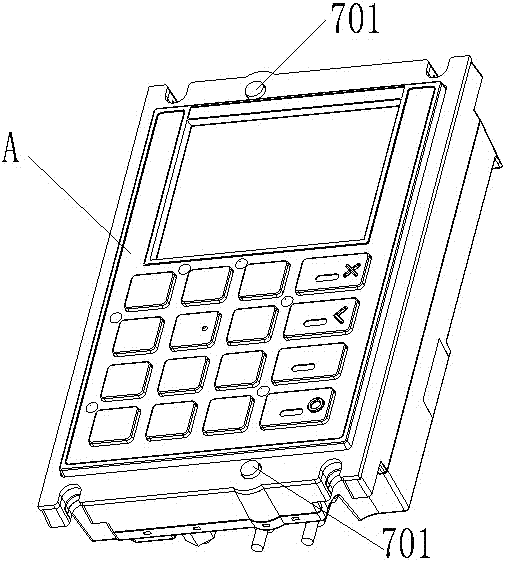
Metal keyboard with anti-tamper contacts and installation method thereof
ActiveCN105304386BPrevent security attacksElectric switchesEmergency protective devicesKey pressingSilica gel
The invention relates to a metal keyboard with an anti-disassembly contact, and an installation method thereof. The metal keyboard comprises a keyboard body and is characterized in that the keyboard body comprises a plastic case face frame and metal buttons arranged in the plastic case face frame, the rear side of the metal buttons as a whole is successively provided with a silica gel keypad body and a keypad, the surface of the silica gel keypad body is provided with silica gel protruding buttons, the back surface of the silica gel keypad body is provided with a conductor, and the conductor is connected with a circuit switch on the keypad when the silica gel protruding buttons are extruded to the side of the keypad. According to the invention, when the keyboard is artificially dismounted from an external device, the silica gel protruding buttons rebound to a normal state from an extruded state, as a result, the conductor below the silica gel protruding buttons is disconnected from the keypad, and thus a security attack is prevented.
Owner:FUJIAN NEWLAND PAYMENT TECH
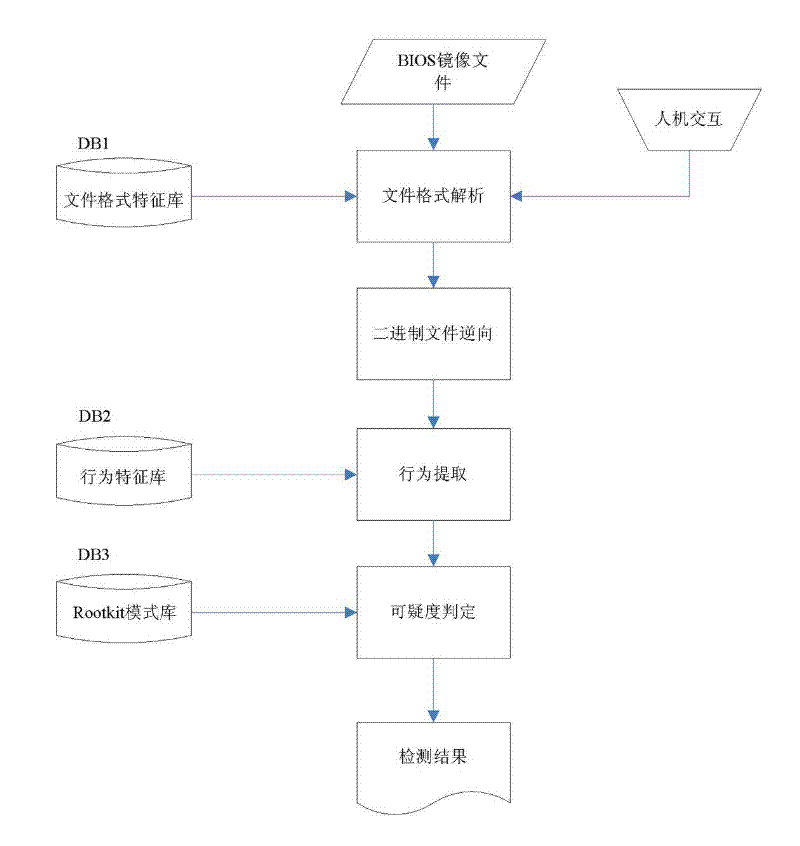
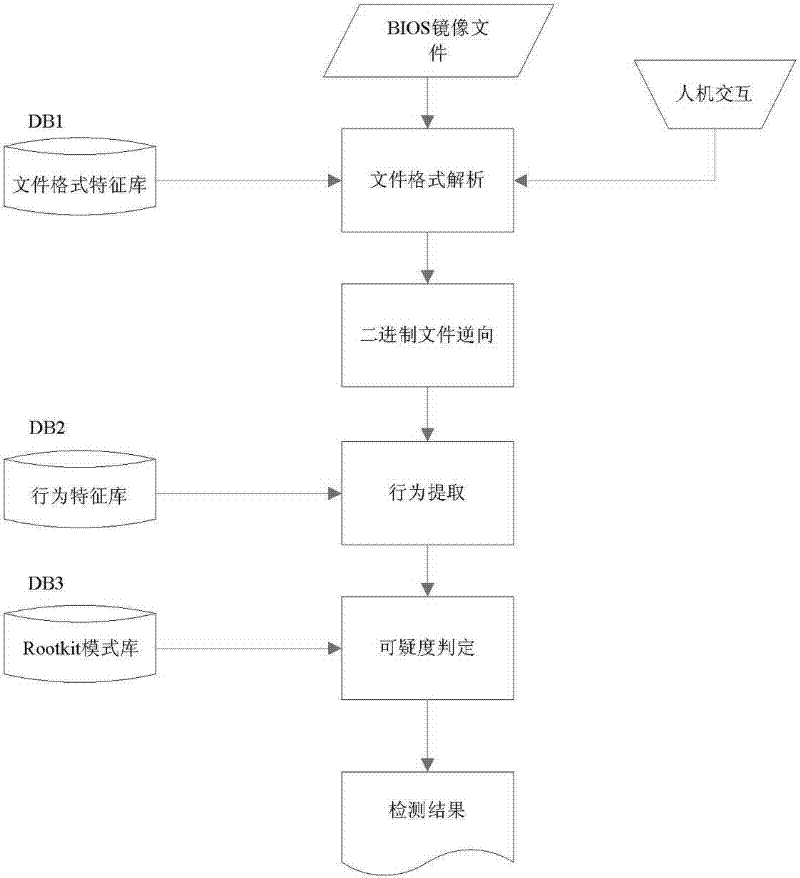
BIOS firmware Rootkit detection method based on behaviour characteristic
InactiveCN101976319BProtection securityPrevent security attacksPlatform integrity maintainanceControl flowSemantics
The invention relates to a detection method which aims at computer BIOS firmware Rootkit on the basis of a program behaviour characteristic, belonging to the technical field of computer safety. The detection method is mainly used for replying attack realized by BIOS and possible BIOSRootkit. The BIOSRootkit detection method based on the behaviour characteristic comprises the following steps: a. analyzing a binary system BIOS image file to be analyzed; b. carrying out reversal to a code in the mode of static control flow for an analyzed binary file, equivalently mapping instruction semantics in a code segment to intermediate representation, and building the control flow graph (CFG) of a program; c. simplifying the intermediate representation, extracting the behaviour characteristic according to suspicious BIOSRootkit behaviour stored in a characteristic repository DB2, extracting a candidate behaviour set according to a behaviour template in the behaviour characteristic repository, andadopting a stepwise selection mode to extract the behaviour characteristic; and d. judging the suspicious degree of the malicious behaviour, and outputting a detection result.
Owner:张平
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com