Generation method and apparatus for neighbor table items
A technology of neighbor tables and messages, which is applied in the field of network communication, can solve the problems of high complexity in use, and achieve the effects of preventing security attacks, simple function feature settings, and simple configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
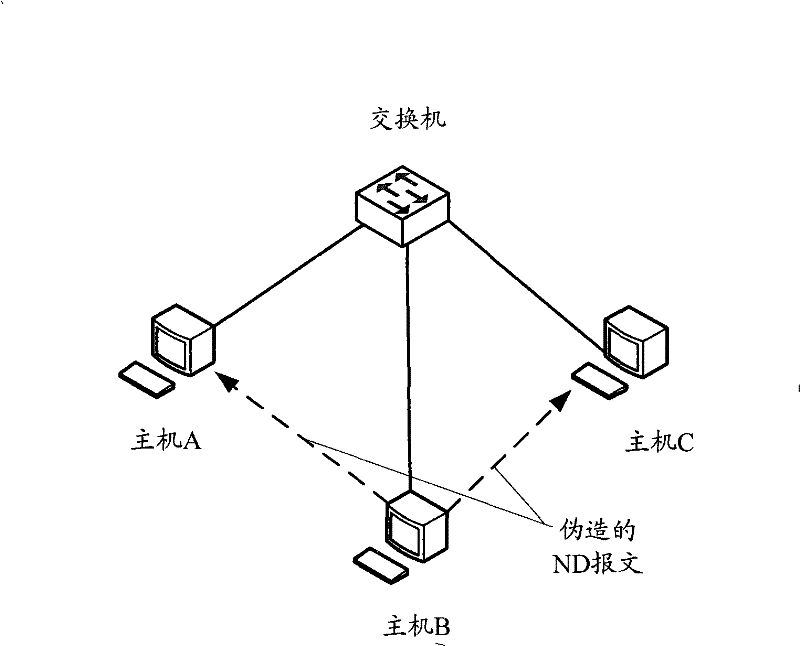
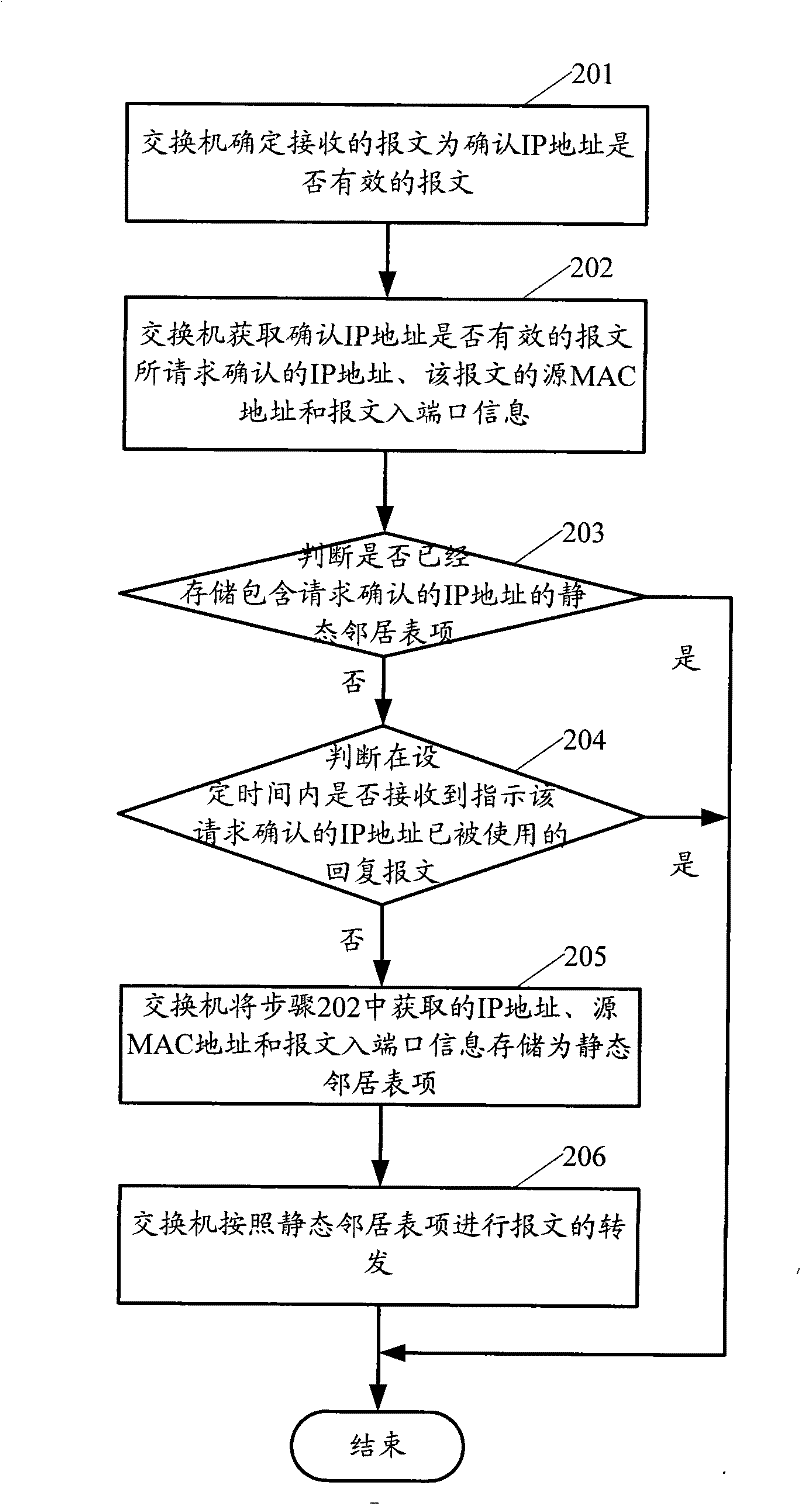
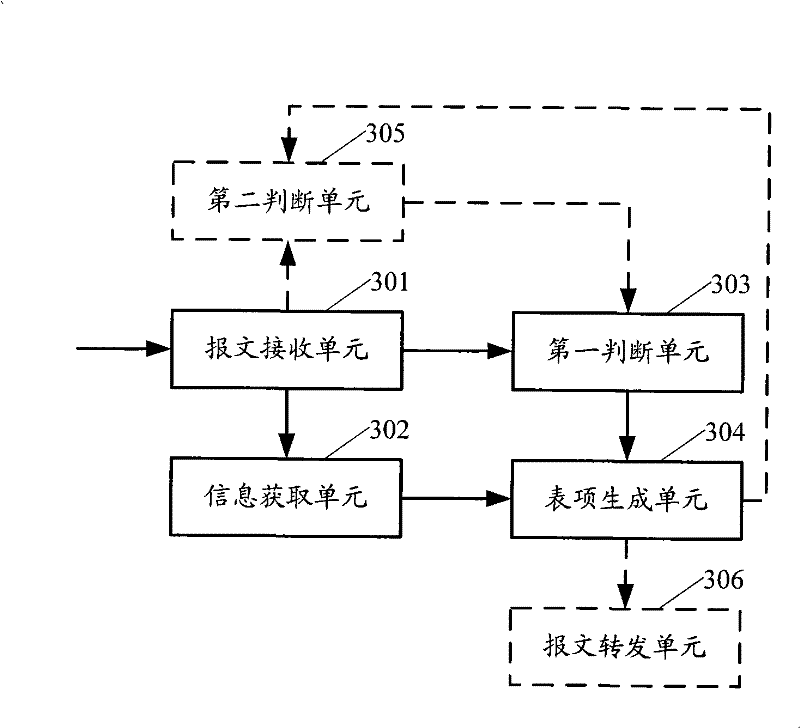
[0019] The method provided by the present invention mainly includes: after the switching device receives the message confirming whether the IP address is valid, if it does not receive the reply message that the IP address requested by the message has been used within the set time, then Store the source MAC address, inbound port information, and IP address of the packet as a static neighbor entry.
[0020] Wherein, the aforementioned switching device may be a Layer 3 forwarding device such as a switch or a router.
[0021] The foregoing message for confirming whether the IP address is valid may be an ND address detection message, a Dynamic Host Configuration Protocol detection protocol version 6 (DHCPv6) message, and the like.
[0022] The above m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com