Synchronous code encryption device and method for access control system
An access control system and synchronous code technology, applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve the problems of security performance, security damage of access control system, data easy to be intercepted, cracked and counterfeited, etc. problems, to achieve the effect of improving safety and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
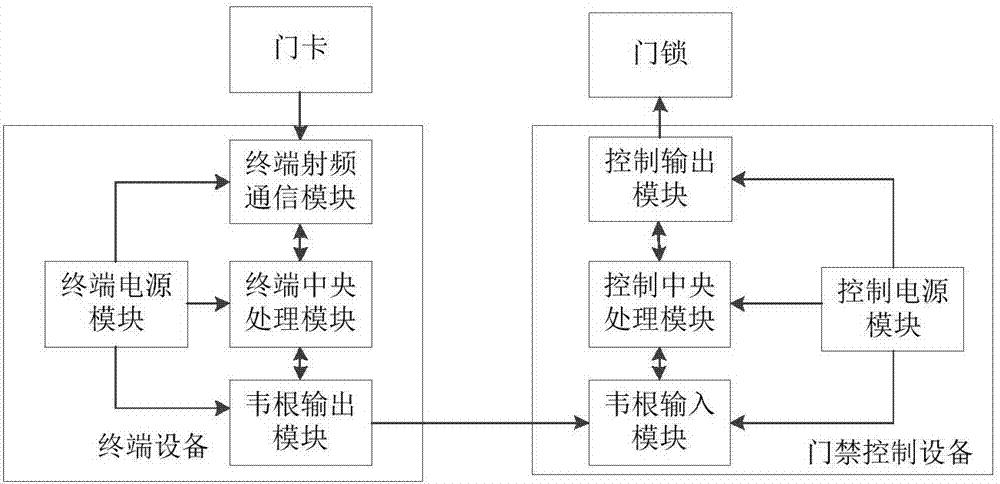
[0069] like figure 1 As shown, a synchronous code encryption device for an access control system is applied to an access control system including a door card and a door lock, including an access control device and a terminal device;
[0070] The terminal equipment includes a terminal power supply module, a terminal central processing module, a Wiegand output module, and a terminal radio frequency communication module, which are used to read the card number data of the door card and perform dynamic encryption of the synchronization code, and transmit the encrypted data to the access control device;
[0071] The terminal power supply module is respectively electrically connected to the terminal central processing module, the Wiegand output module, and the terminal radio frequency communication module, and is used to provide DC power to the connected modules;
[0072] The terminal central processing module communicates with the Wiegand output module and the terminal radio frequen...
Embodiment 2
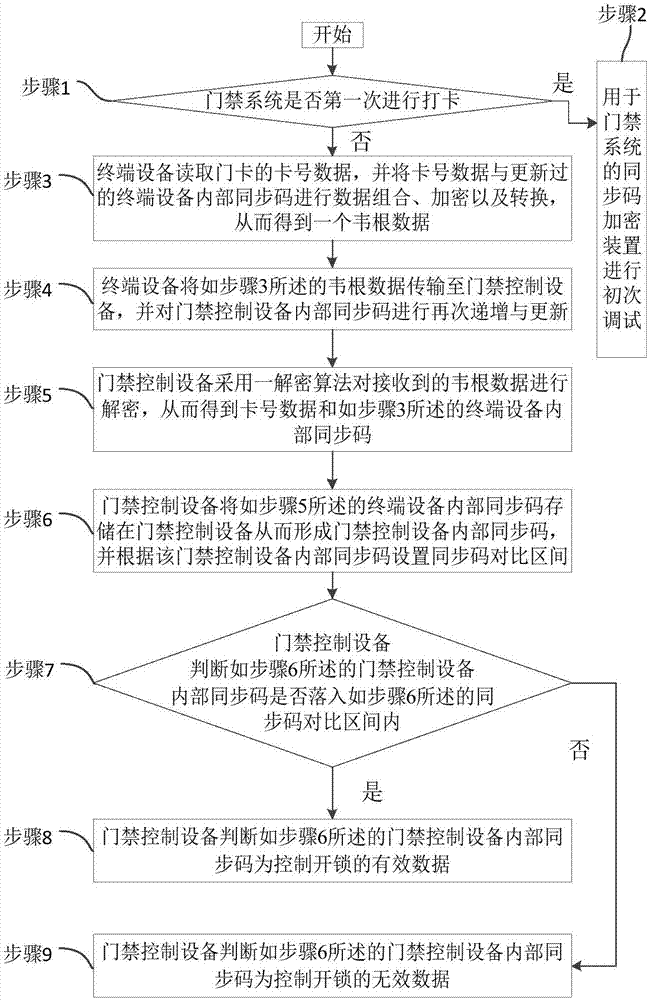
[0123] A synchronous code encryption method for access control system can realize that the signal waveform of the same valid data transmitted on the Wiegand data line is different every time, and the access control controller will automatically synchronize the communication and receive the data correctly and then parse out the correct data, and then perform subsequent operations. For example: access control card reader (that is, the terminal device swipes the card, the card number is 0x11223344, the access control card reader will add the dynamic synchronization code to the card number data and encrypt the data and then convert it into Wiegand data output, so after the first card swiping, the Weigan The actual output data of the root output module will be processed as 0x8564127845986534, the actual output data of the Wiegand output module will be processed as 0x7468534145687526 after the second card swiping, and the actual output data of the Wiegand output module will be proces...
Embodiment 3
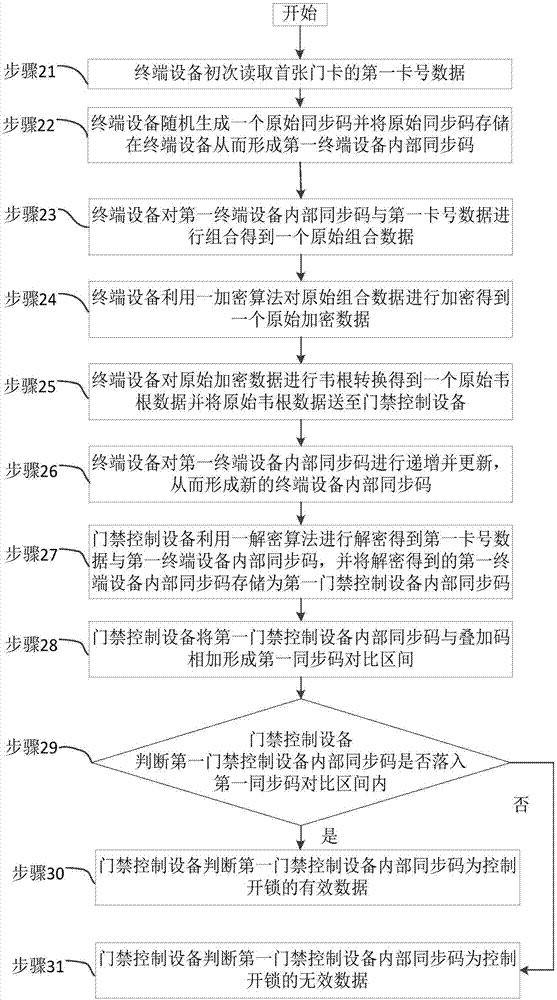
[0125] A kind of concrete implementation process of the synchronous code encryption method that is used for access control system comprises the following steps:
[0126] S1, the terminal device is powered on, and a random number is internally generated as the most original synchronization code, for example, this data is 0x11223344;
[0127] S2, the terminal device reads the card number data, and the card number is 0xAABBCCDD;
[0128] S3, the terminal device combines the two data into 0x11223344AABBCCDDEE;
[0129] S4, the terminal device encrypts the combined data to generate a piece of ciphertext, the encryption algorithm is RC5 (you can also use a custom encryption algorithm or other public algorithms), for example, the ciphertext data is 0x18584A4C51E22C8A;
[0130] S5, the terminal device updates the internal synchronization code, for example: the update rule is the synchronization code +1, then the new synchronization code is 0x11223345 (the synchronization code change ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com