Data encryption mobile storage management method based on virtual disk
A virtual disk and mobile storage technology, applied in software simulation/interpretation/simulation, internal/peripheral computer component protection, program control devices, etc., can solve problems such as slow speed, data leakage, easy password cracking, etc., to prevent card Pause or wait, simple and convenient to use, high safety and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The specific implementation of the technical solution of the present invention will be described below by taking a USB flash drive as an example of a mobile storage device.
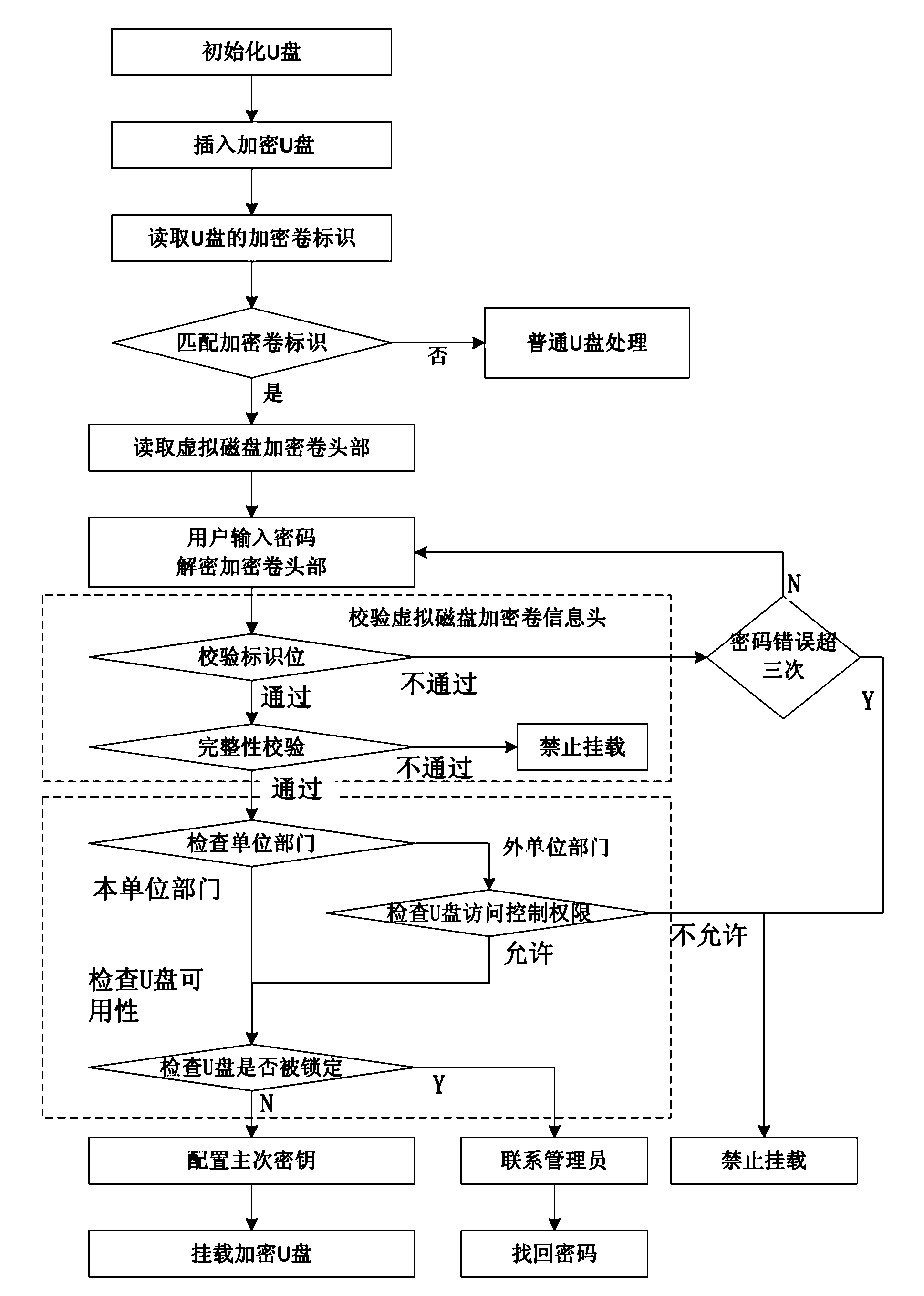
[0044] Such as figure 1 As shown, the implementation steps of the data encryption mobile storage management method based on the virtual disk in this embodiment are as follows:
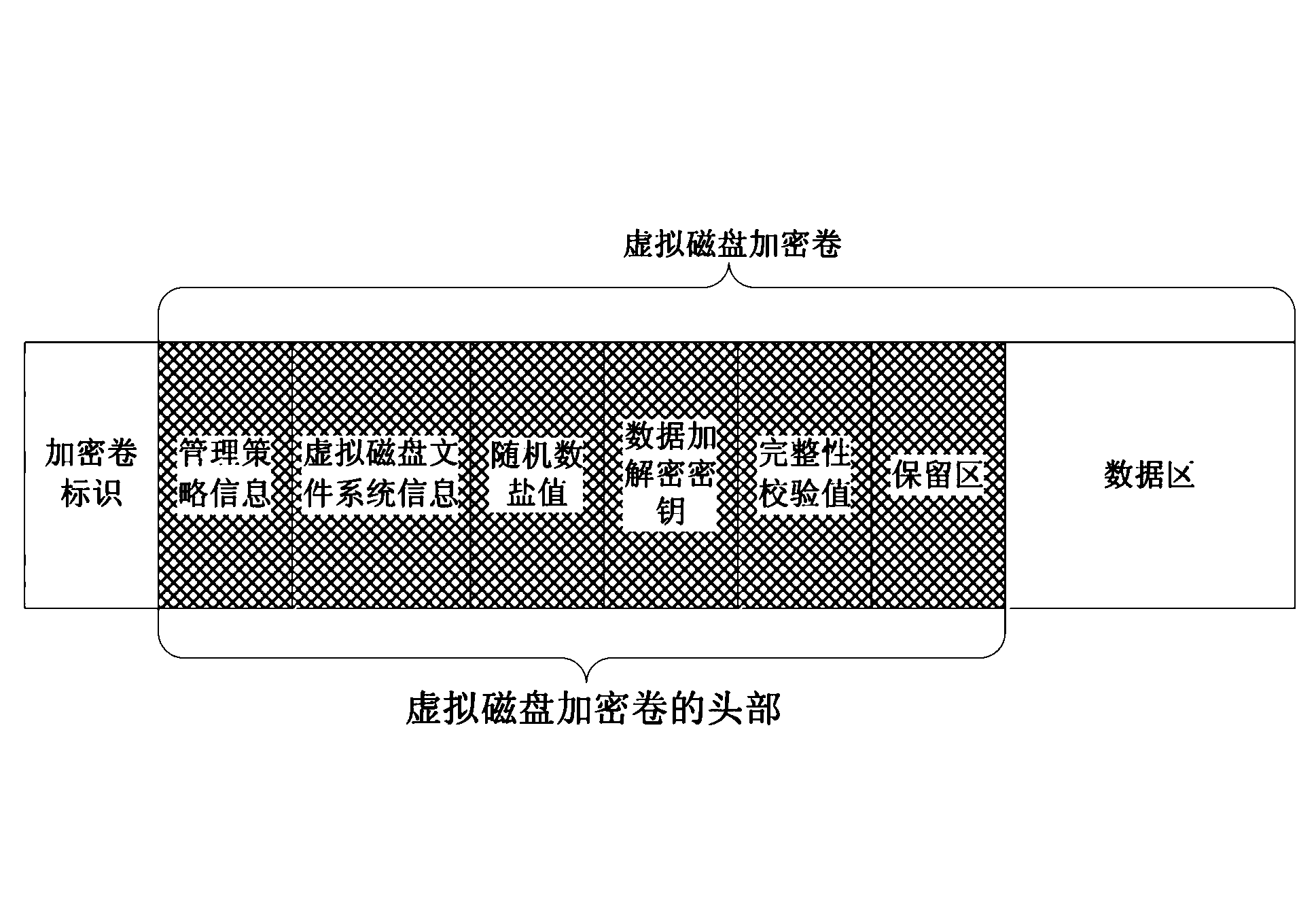
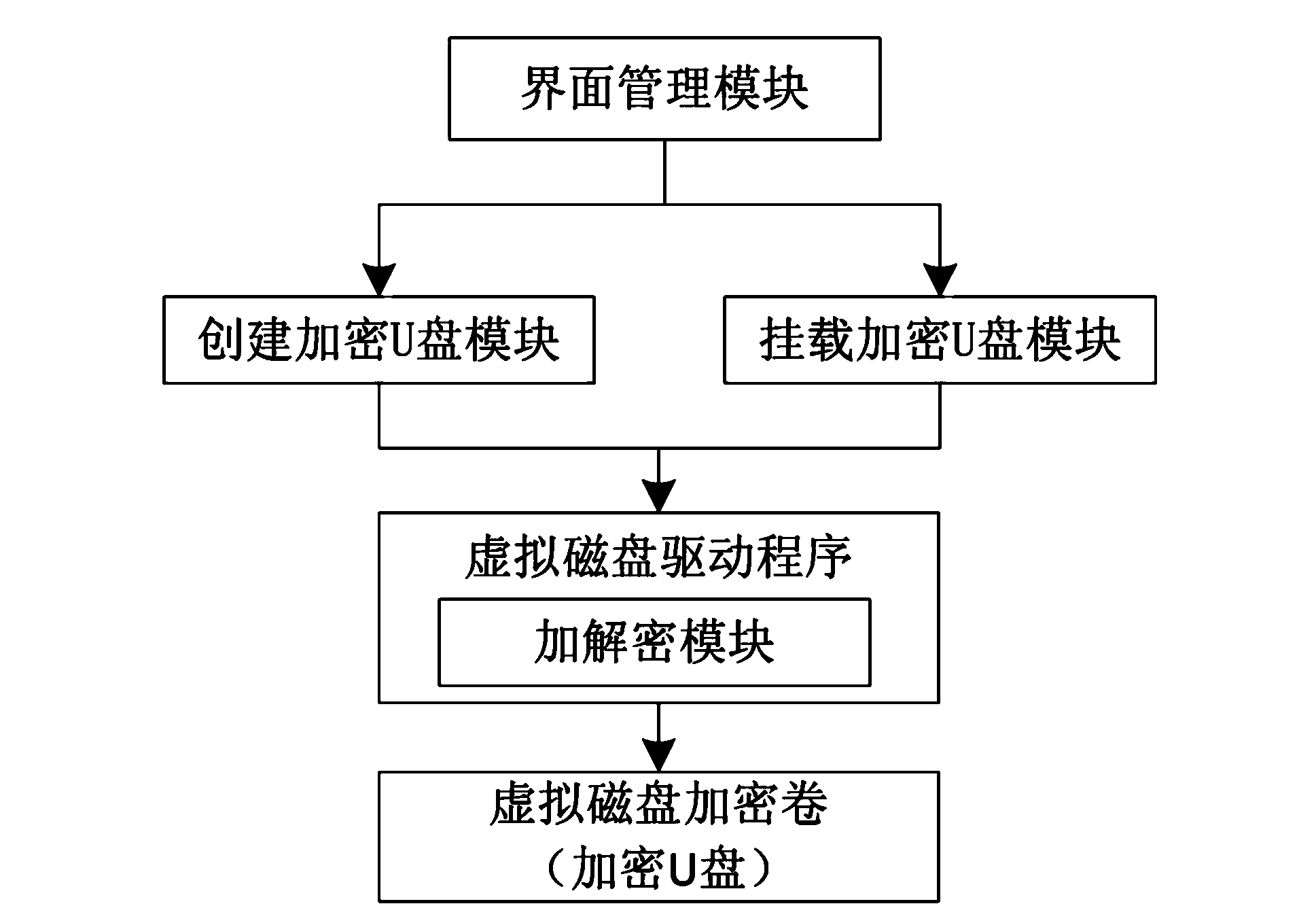
[0045] 1) Write the encrypted volume logo in the head of the ordinary U disk and create a virtual disk encrypted volume to obtain an encrypted U disk, set the head of the virtual disk encrypted volume to encrypt the virtual disk encrypted volume information header according to the mount password entered by the user , the virtual disk encryption volume information header contains data encryption and decryption keys, management policy information and virtual disk file system information;
[0046] 2) When the U disk is inserted into the specified computer, check whether the encrypted volume ID of the U disk is correct. If the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com