Defense method for configuring weak password vulnerability of internal and external network camera
A camera and weak password technology, applied in the defense field of weak password vulnerability configuration for internal and external network cameras, can solve the problem of unable to fundamentally eliminate camera monitoring, unable to prevent secondary infection, difficult to determine whether it is infected, etc., to prevent weak passwords. Password scanning, resolving security threats, reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be further described below in conjunction with the accompanying drawings.
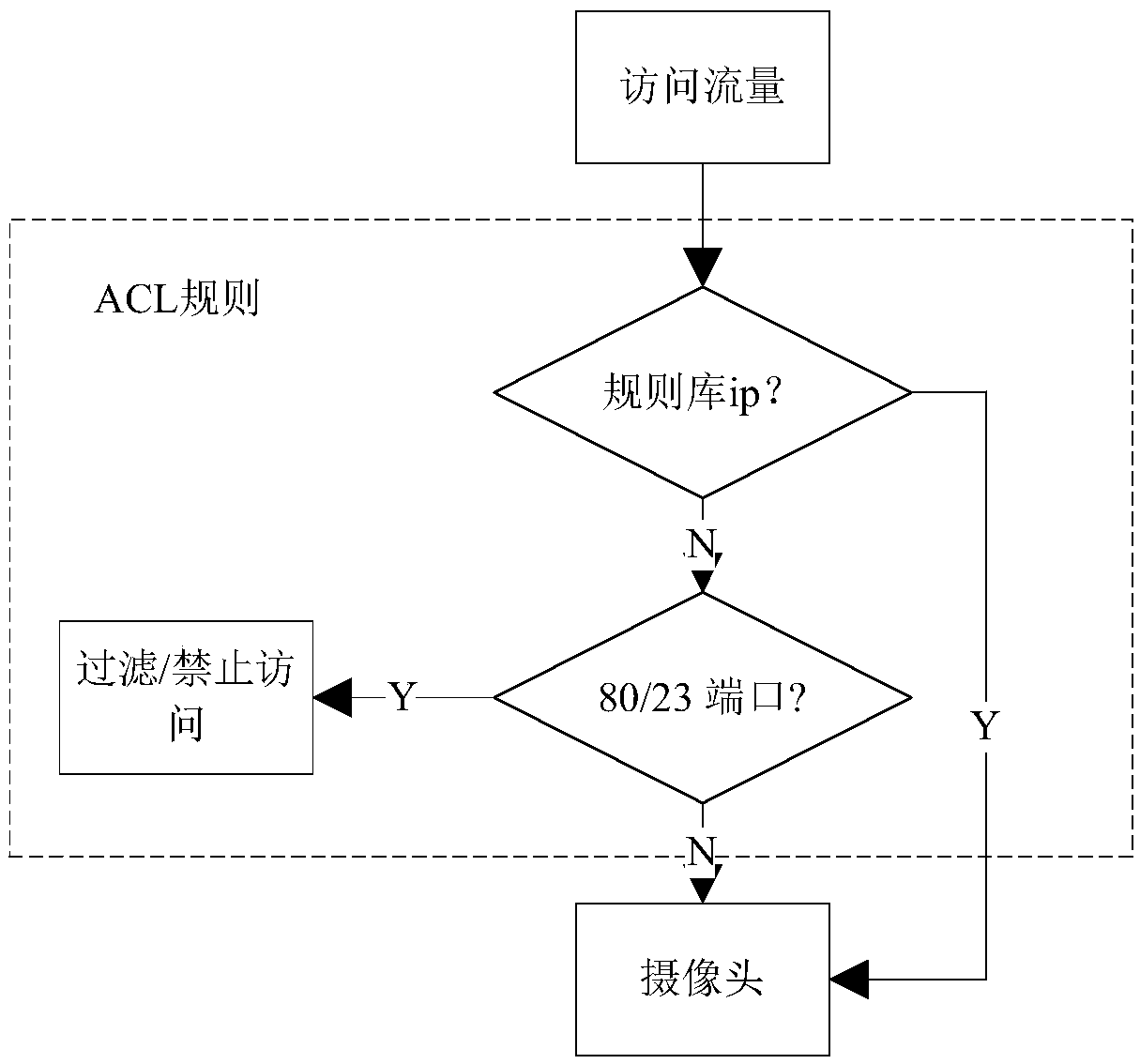
[0017] ACL technology is widely used in routers. It is a flow control technology based on packet filtering. The control list uses the source address, destination address and port number as the basic elements of data packet inspection, and can specify whether the qualified data packets are Allowed to pass.
[0018] Honeypot technology is essentially a technology to deceive the attacker. By arranging some hosts, network services or information as bait, the attacker is induced to attack them. Since the honeypot cannot execute the corresponding malicious code, the attack information It will be well preserved, so that the attack behavior can be captured and analyzed, the tools and methods used by the attacker can be understood, and the attack intention and motivation can be speculated, so that the defender can clearly understand the security threats it faces, and through T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com