Patents
Literature
51results about How to "Ensure access security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Wi-fi access method, access point and wi-fi access system
InactiveUS20120036557A1Lower upgradeLow costDigital data processing detailsComputer security arrangementsWi-FiAccess method
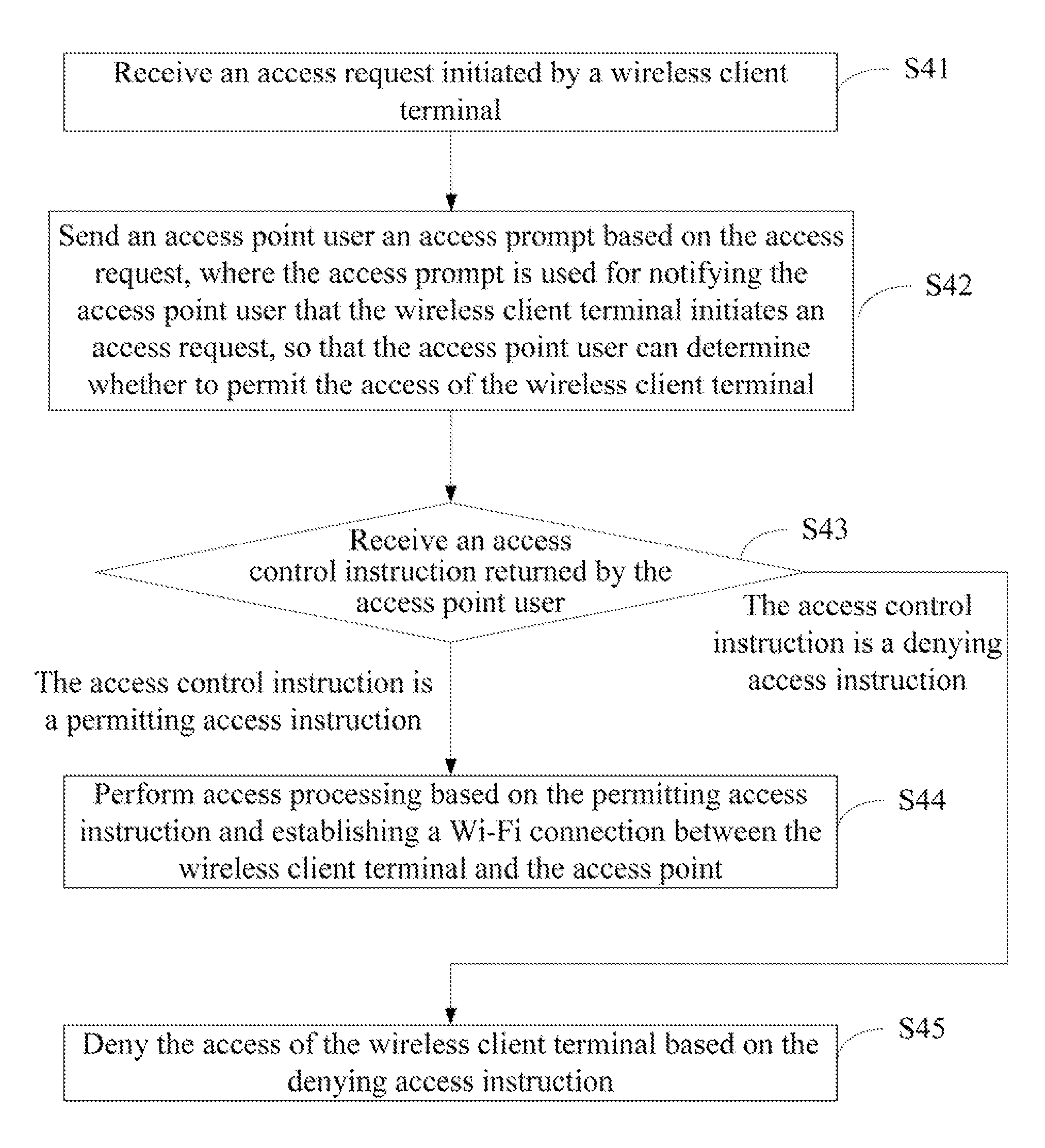
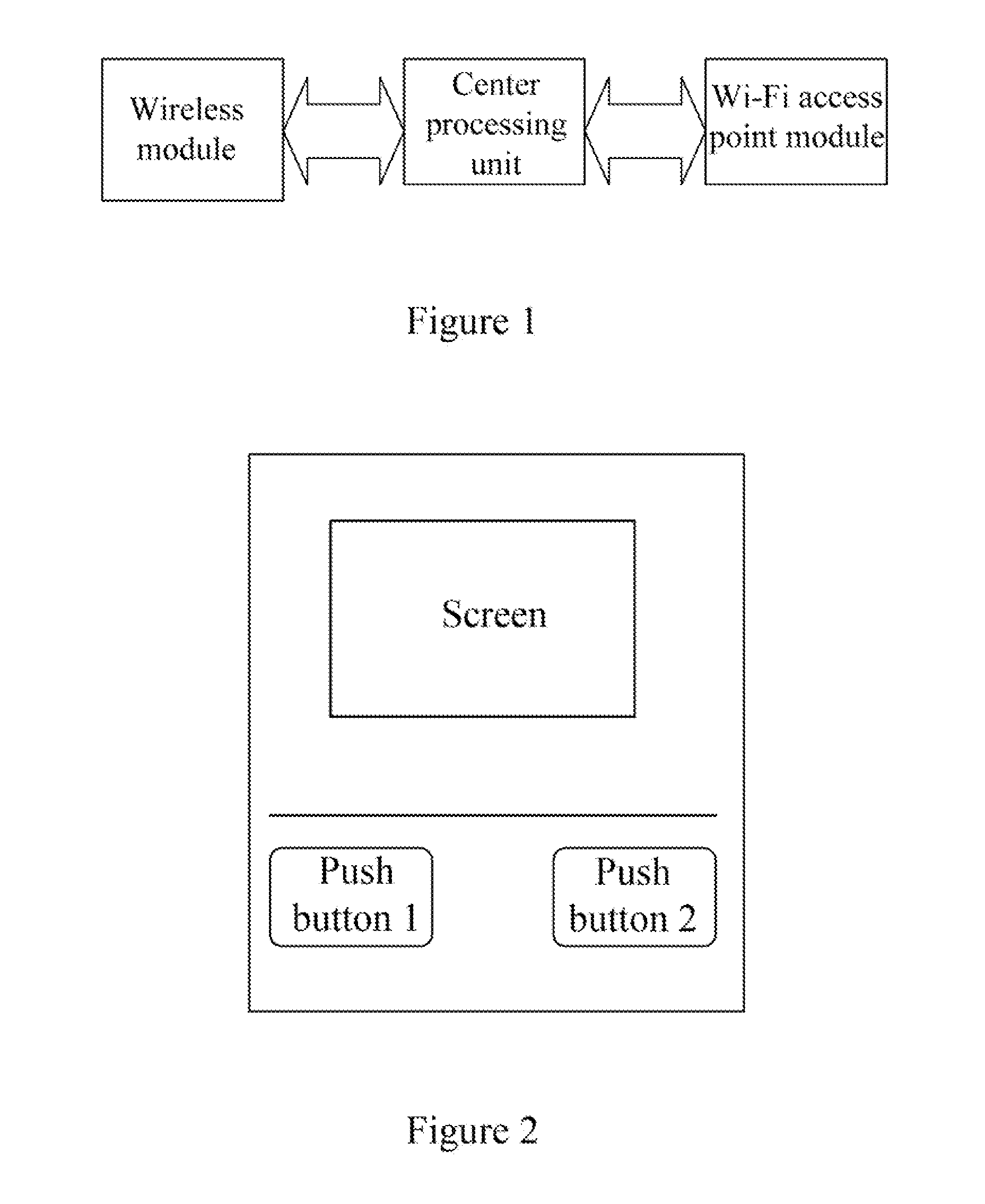
The present invention discloses a Wi-Fi access method, access point and a Wi-Fi access system. It is related to the field of communication technology and is devised for realizing the security access of a Wi-Fi device with relatively low costs. The Wi-Fi access method comprises: receiving an access request initiated by a wireless client terminal; sending an access prompt to an access point user based on the access request; receiving an access control instruction returned by the access point user; when the received access control instruction is a permitting access instruction sent by the access point user, performing access processing and establishing a Wi-Fi connection between the wireless connection terminal and the access point based on the permitting access instruction; or denying the access of the wireless client terminal based on a denying access control when the received access control instruction is the denying access instruction sent by the access point user. The present invention may cause a Wi-Fi device to access an access point (AP).
Owner:HUAWEI DEVICE CO LTD
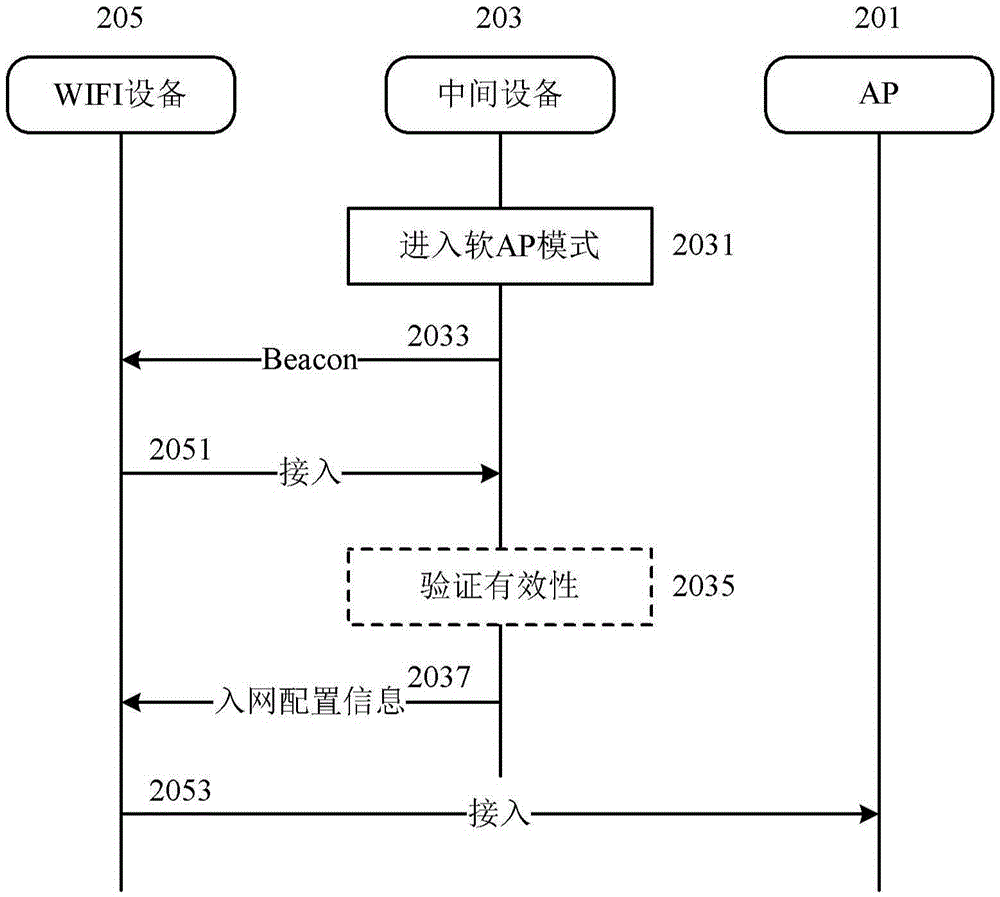
WIFI equipment, electronic device and method for assisting WIFI equipment access to network
The invention discloses WIFI equipment, an electronic device and a method for assisting the WIFI equipment access to a network. According to the embodiment, the electronic device may comprise a WIFI unit which is configured to establish WIFI connection with other devices, wherein the WIFI unit has a soft AP (Access Point) mode, sends a beacon when the WIFI unit is in the soft AP mode, and sends configuration information used for the AP to the accessed WIFI equipment when the WIFI device accessing the WIFI unit exists.
Owner:BEIJING JINGDONG CENTURY TRADING CO LTD
Network security management and control system for accessing social video networks to video private network
InactiveCN106027358ARealize security management and controlSafe and reliable connectionClosed circuit television systemsNetworks interconnectionDigital videoData stream
The invention discloses a network security management and control system for accessing social video networks to a video private network. The network security management and control system comprises the video private network, multiple social video networks and multiple access equipment arranged among the video private network and the social video networks; and an integrated management platform is arranged on the video private network. According to the network security management and control system disclosed by the invention, security management and control of a network is realized through the access equipment and the integrated management platform; an illegal data flow and access of an illegal user are intercepted in a physical isolation manner from a bottom protocol level of a network data packet while real-time transmission requirements of digital video information are ensured; and thus, the access security from the social video networks to the video private network is ensured.
Owner:SHANGHAI HORIZON INFORMATION TECH
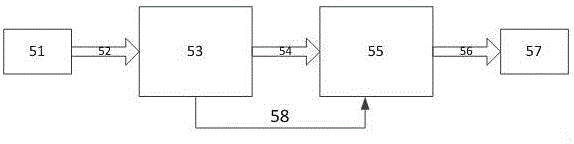
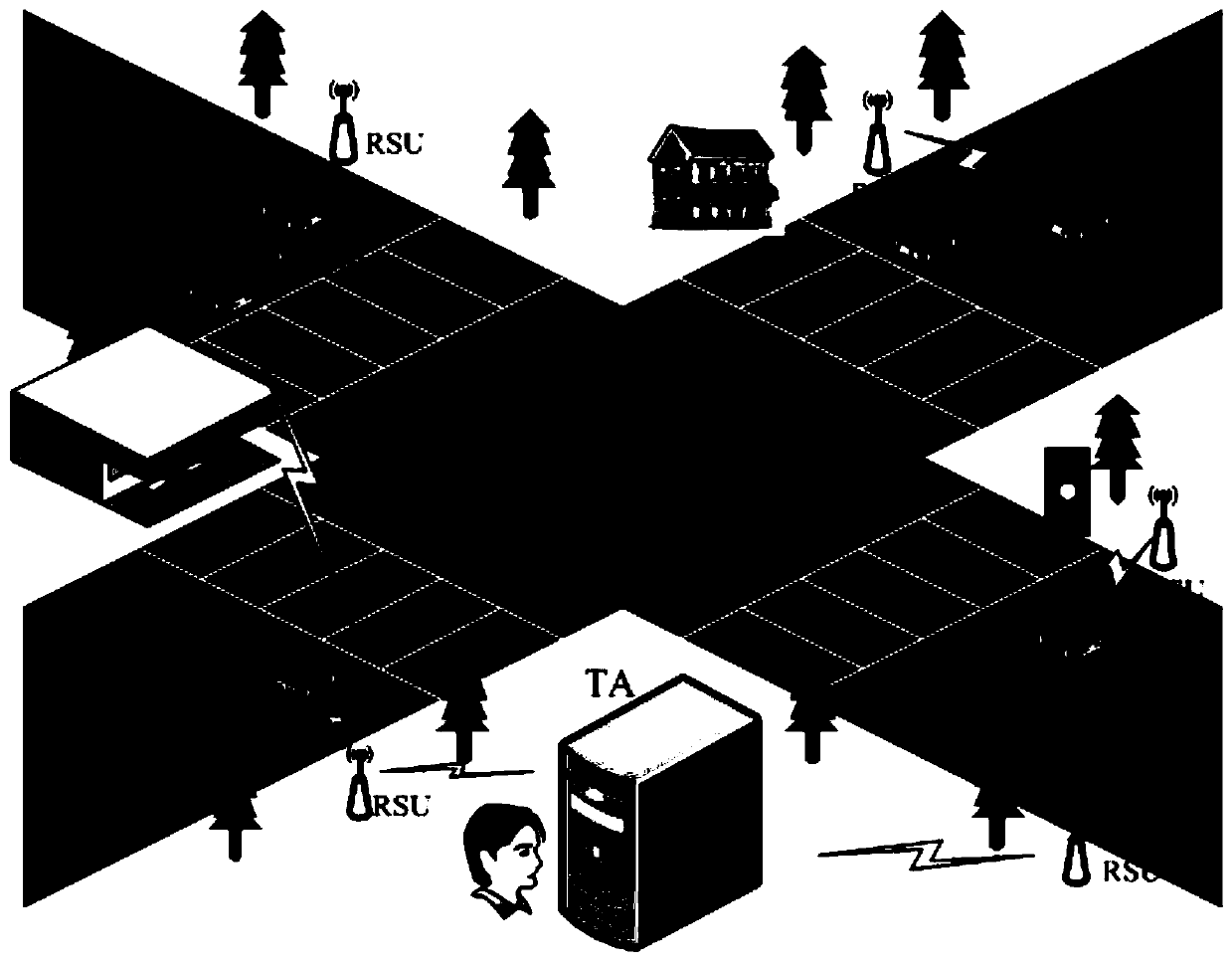
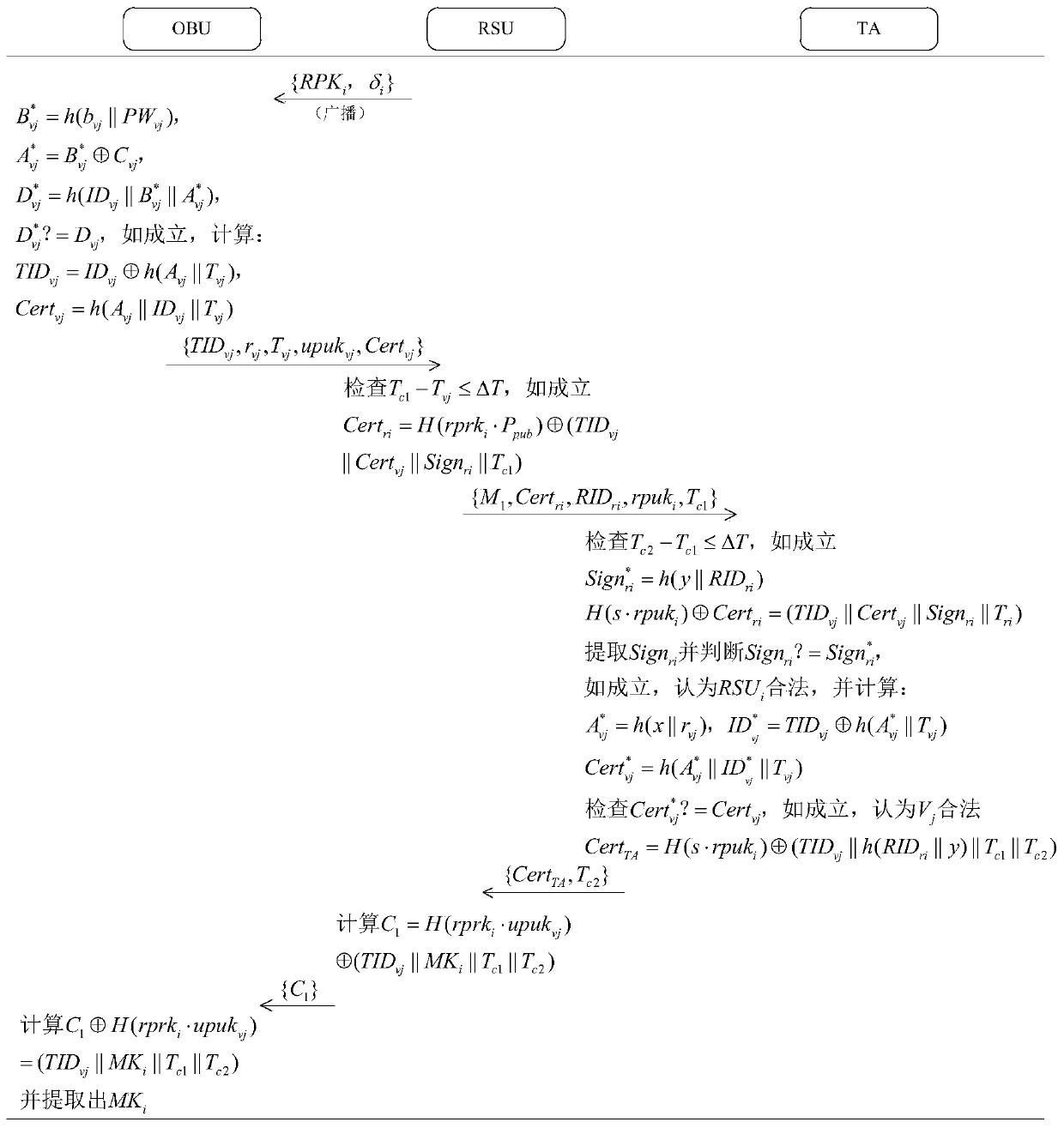
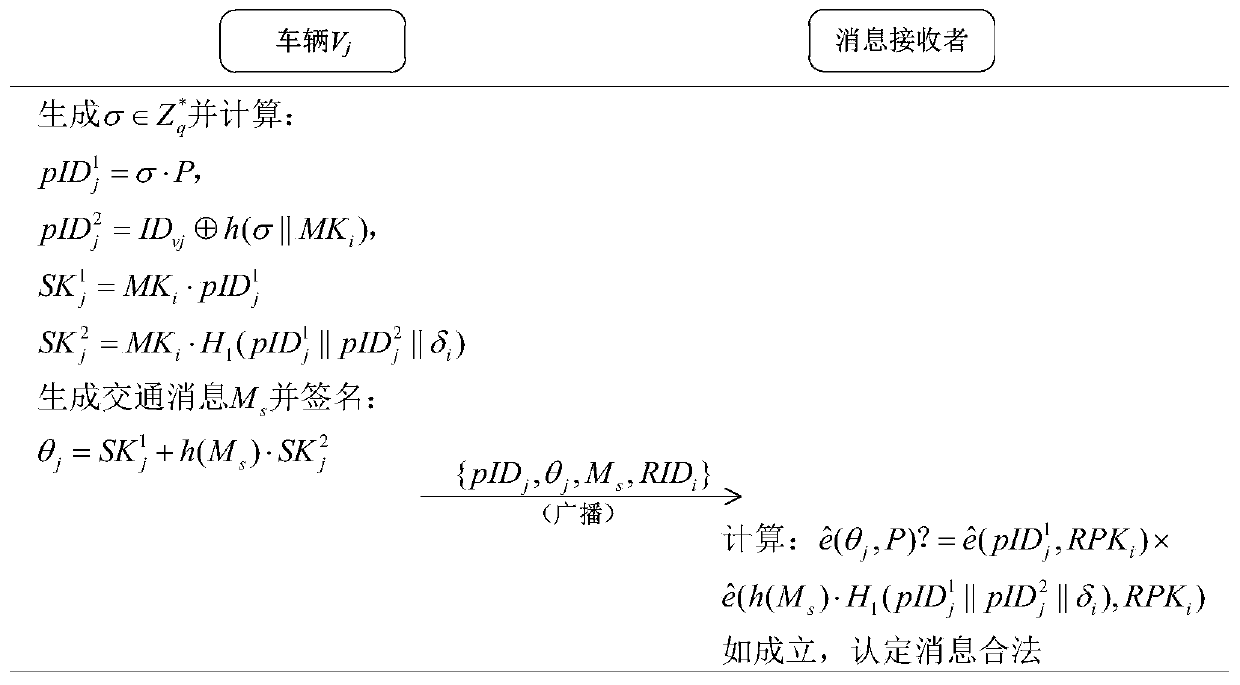
A vehicle authentication and message verification method in a vehicle-mounted network environment
ActiveCN109922475AGuaranteed privacyPrivacy protectionPublic key for secure communicationParticular environment based servicesDigital signatureValidation methods
The invention provides a vehicle authentication and message verification method in a vehicle-mounted network environment. The vehicle authentication and message verification method comprises the stepsthat a trust mechanism initializes a system; the vehicle-mounted unit is registered, and the roadside unit is registered; a temporary key of the roadside unit is released; a vehicle authentication stage; the trust mechanism verifies the legality of the roadside unit through the digital signature, extracts the message and verifies the legality of the automobile, the trust mechanism sends the identity identifier of the automobile to the roadside unit, the roadside unit sends the private key and the temporary main key to the automobile, and the automobile extracts the temporary main key; the automobile calculates a temporary identifier and a temporary private key, generates a traffic message and signs and broadcasts the traffic message; and when other automobiles receive the automobile broadcast message, verifying the effectiveness of the broadcast message through bilinear mapping. According to the method, the vehicle access safety in the Internet of Vehicles environment can be ensured,the safety of traffic information sent by legal vehicles is also ensured, and the method has a relatively high application value in an application environment in the mobile vehicular network environment.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
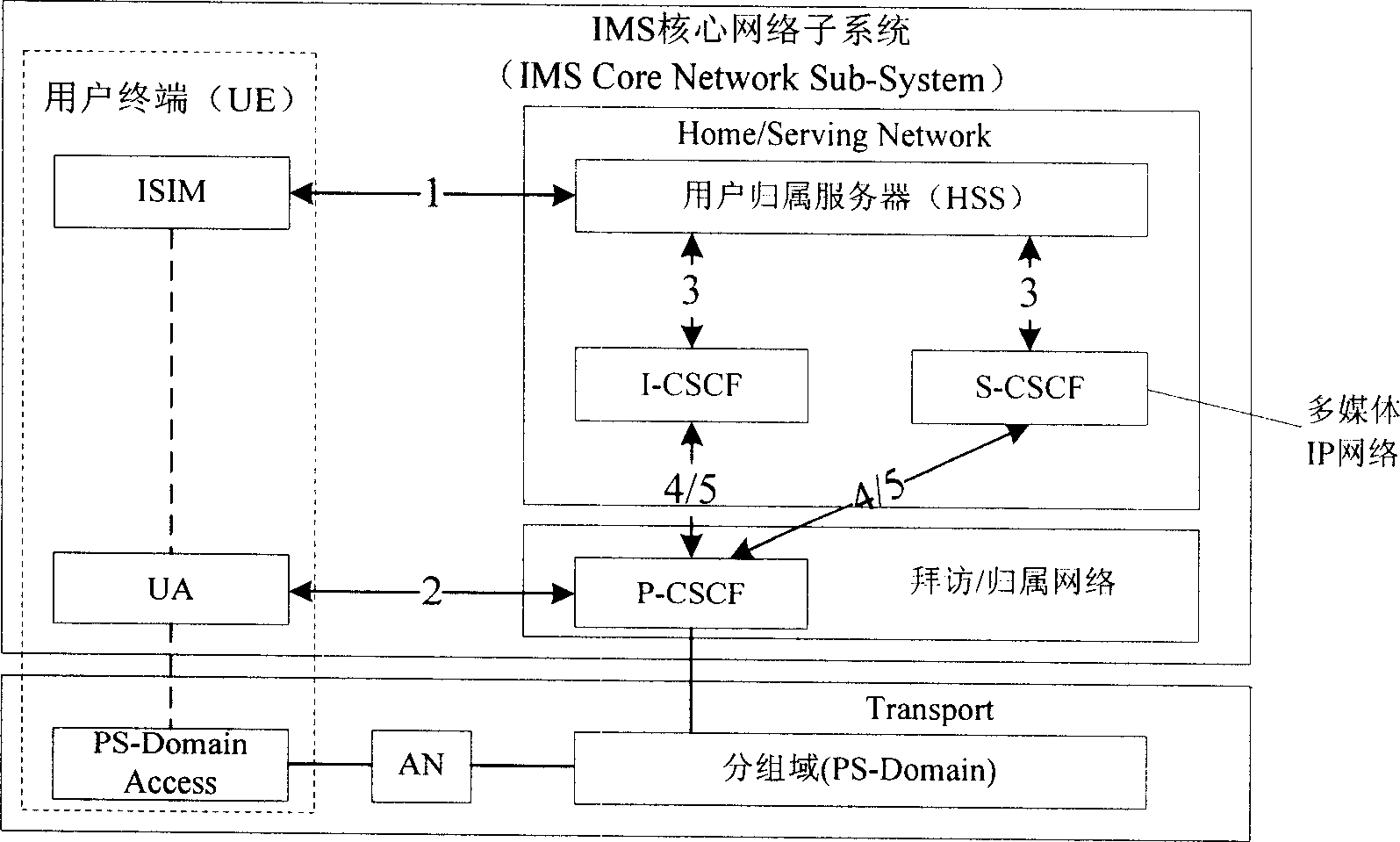
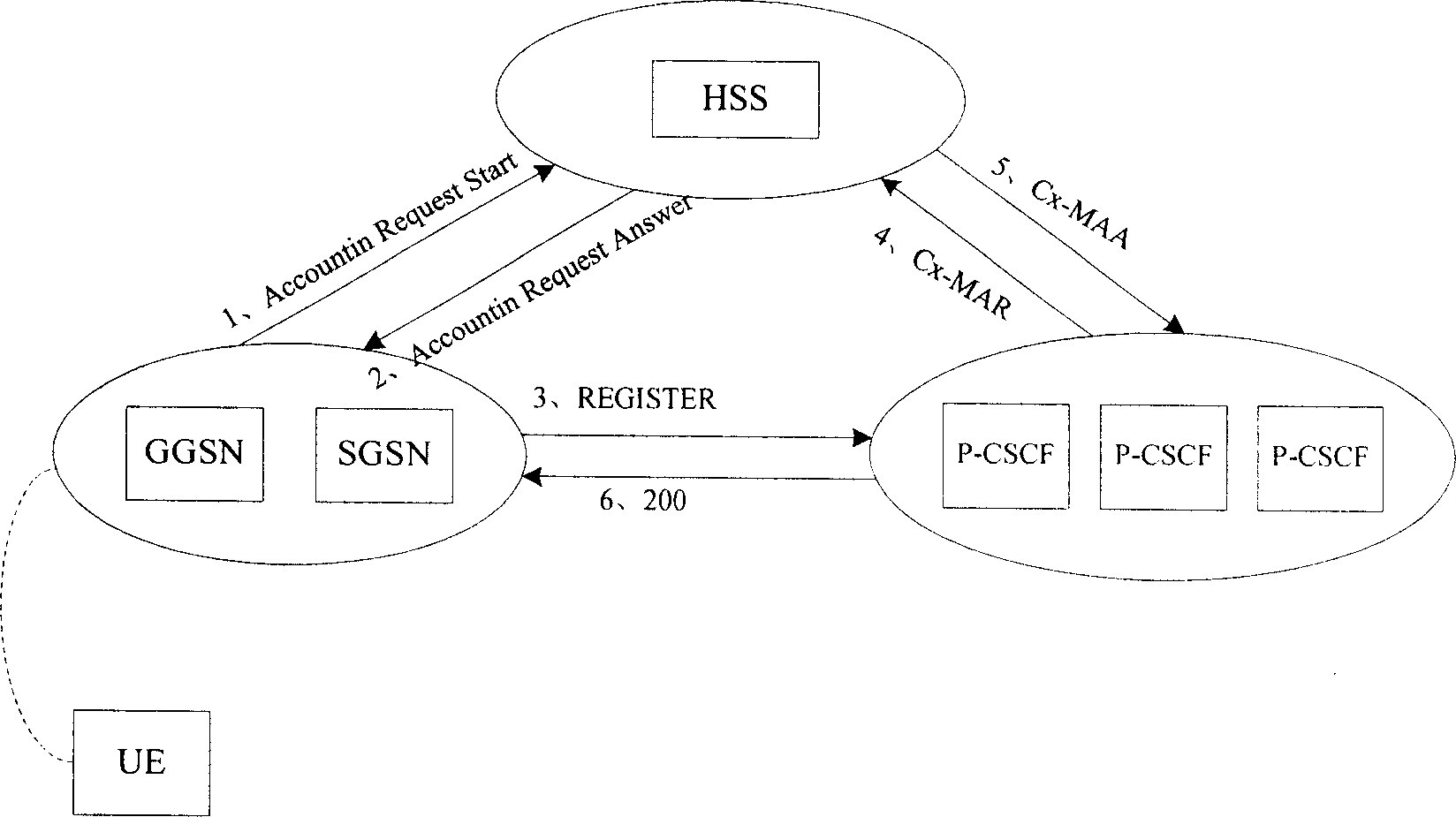
Method for selecting safety mechanism of IP multimedia subsystem acess field
InactiveCN1870812AEnsure access securityImprove scalabilityRadio/inductive link selection arrangementsTransmissionIP Multimedia SubsystemSelection method
The invention discloses a unified method for accessing IP Multimedia Subsystem (IMS), which distributes one or more domain access securities for the network access or / and user IDs at network equipments of IMS network; the Network equipments choose one domain access security from the distributed ones based on the above requested information of user terminal, and the network equipments of access security handle referred request information with the chosen security.
Owner:INVT SPE LLC
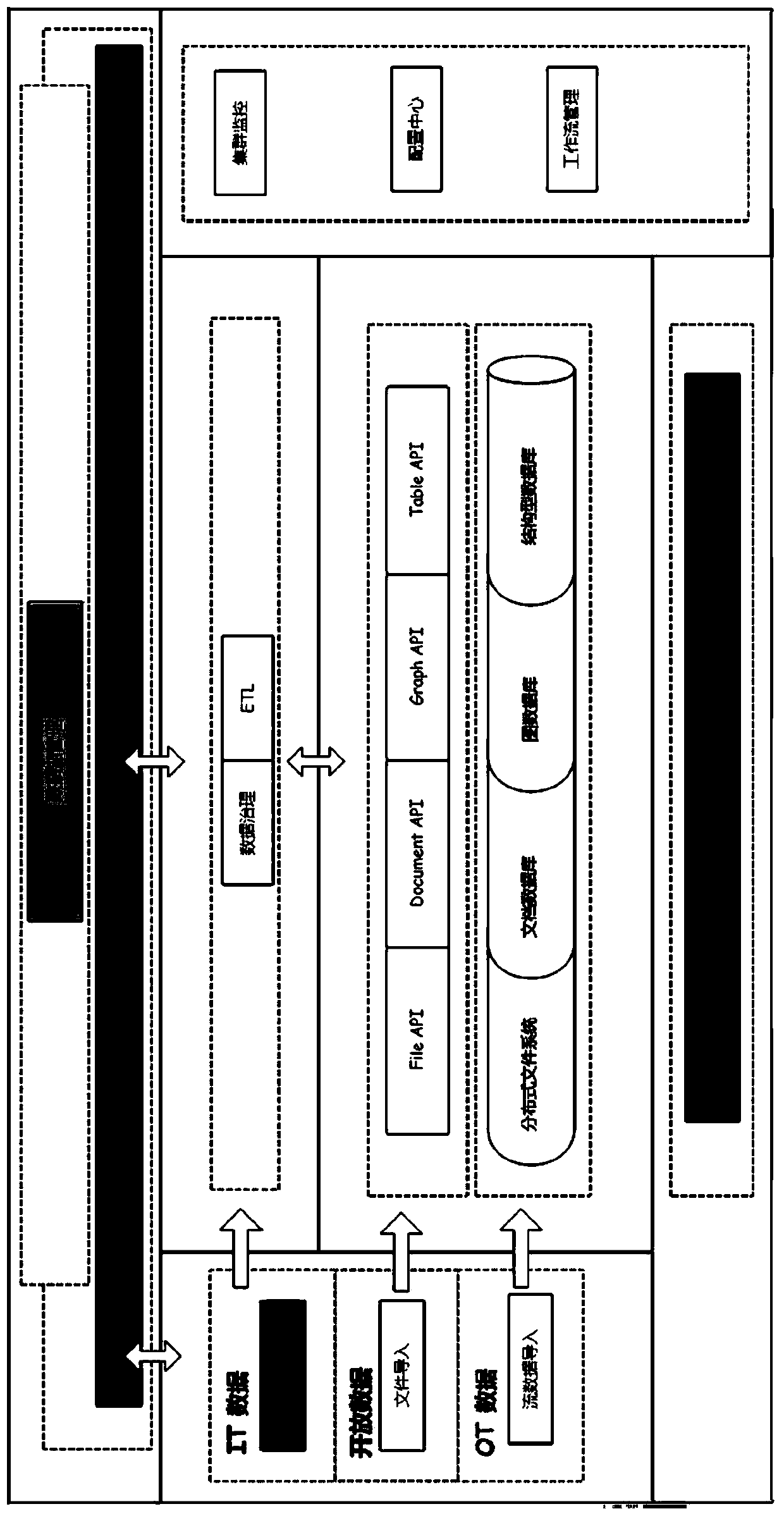
Method for importing multi-source heterogeneous data into data lake
PendingCN111221791AEasy to collectEasy to manageFile/folder operationsSpecial data processing applicationsData transformationRelational database
The invention discloses a method for importing multi-source heterogeneous data into a data lake, which comprises the following steps of: obtaining an access interface address of external file type data, importing the file type data and storing the file type data into a distributed file system of a local data lake server; or obtaining access interface information of an external data source, connecting the access interface information with a local data lake server; importing data of an external data source and storing the data in a distributed file system in a data file form; or converting the non-relational data of the external data source into relational data and then storing the relational data in a relational database, or directly importing the relational data of the external data sourceand storing the relational data in the relational database, or importing the non-relational data of the external data source and storing the non-relational data in a document database. According to the method, the problem of multivariate isomerism of the to-be-stored data can be solved, collection, management, application and expansion of the multi-source isomerism data are facilitated, various requirements of an organizational structure are met, and the data access security and the data import flexibility are ensured.
Owner:中云开源数据技术(上海)有限公司
Safety verification method and device, terminal and server
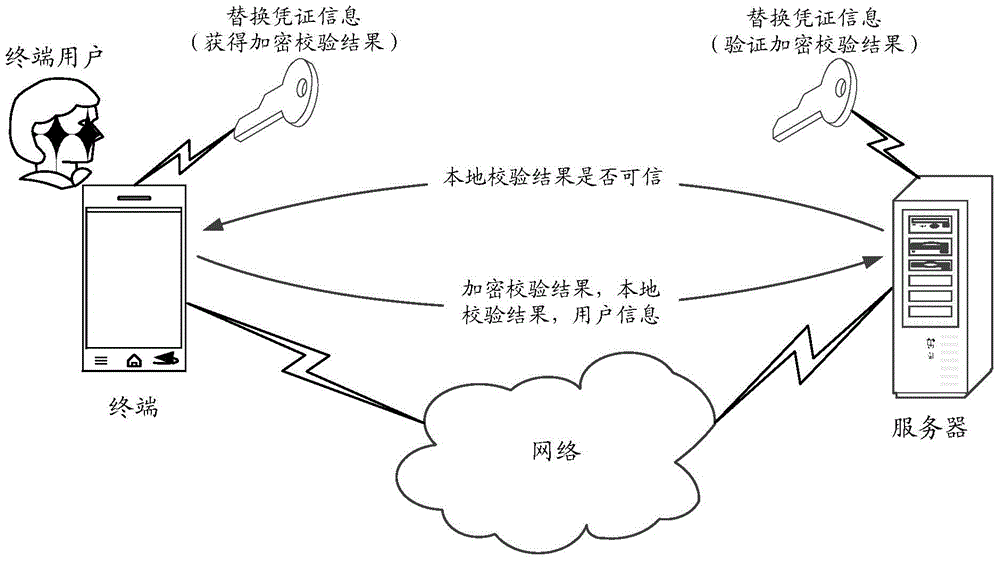
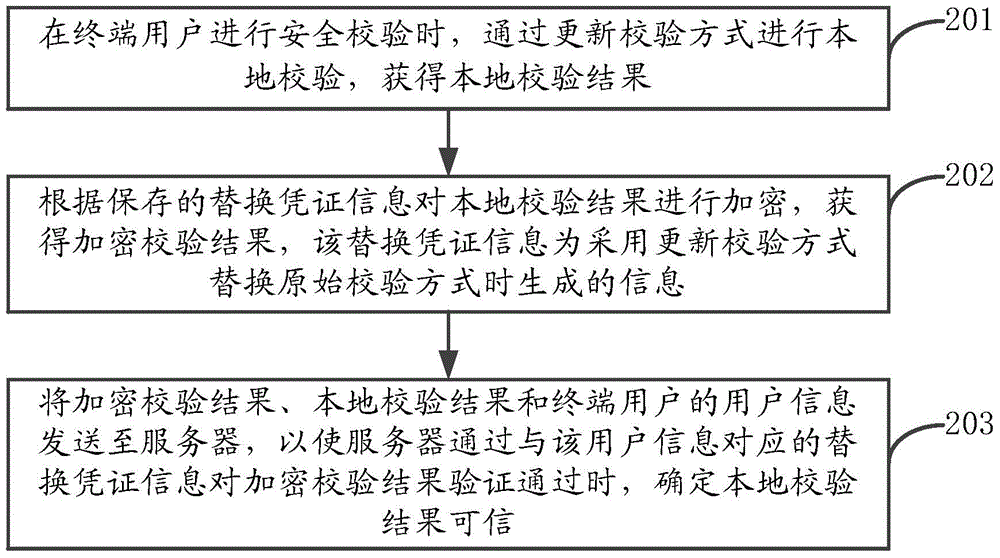
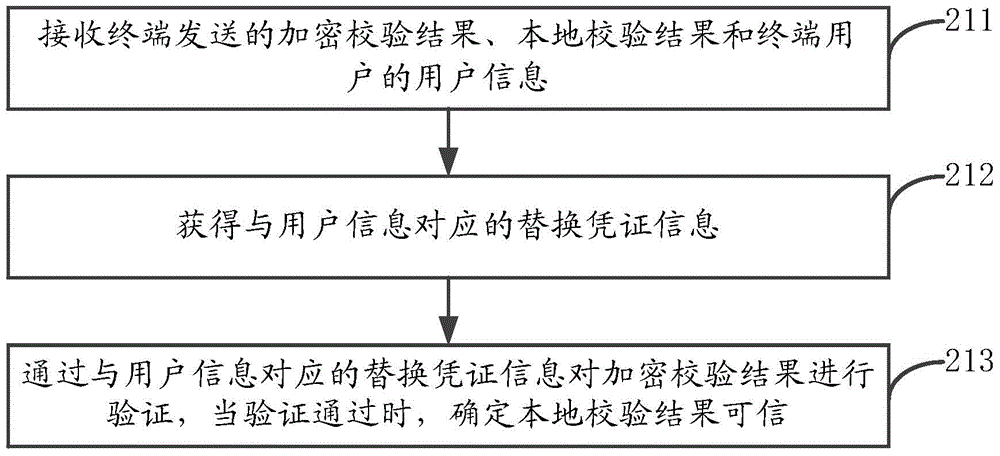
ActiveCN105490997ALocal verification results are credibleImprove reliabilityMultiple keys/algorithms usagePublic key for secure communicationThird partyDependability
The application discloses a safety verification method and device, a terminal and a server. The method comprises the following steps of: when a terminal user performs safety verification, performing local verification through updating of a verification manner, and acquiring a local verification result; encrypting the local verification result according to stored replacement credential information and acquiring an encrypted verification result; and sending the encrypted verification result, the local verification result and user information of the terminal user to the server to enable the server to determine that the local verification result is credible when the verification of the encrypted verification result through the replacement credential information corresponding to the user information is successful. Through adoption of the method and the device, a malicious third party cannot acquire the replacement credential information, and even if the malicious third party acquires the local verification result, safety verification cannot be completed, so that the safety verification reliability is improved, and the access security of network applications is ensured.
Owner:ADVANCED NEW TECH CO LTD
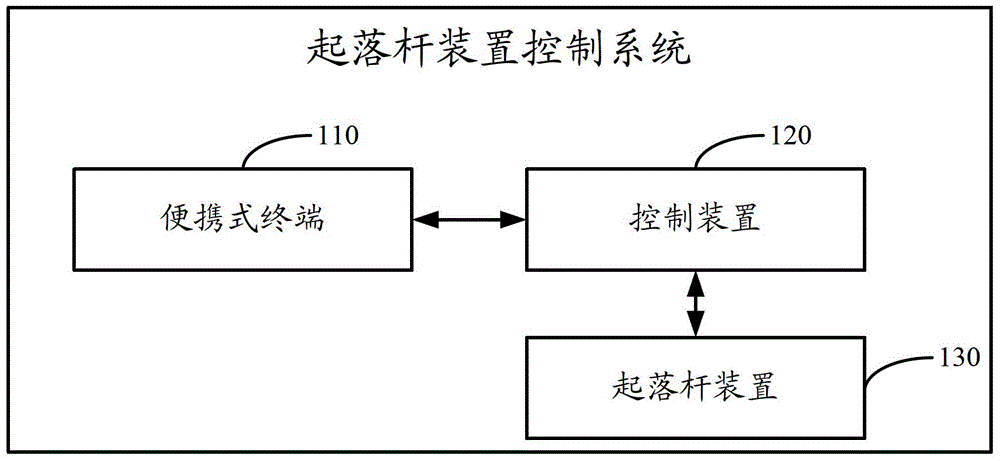
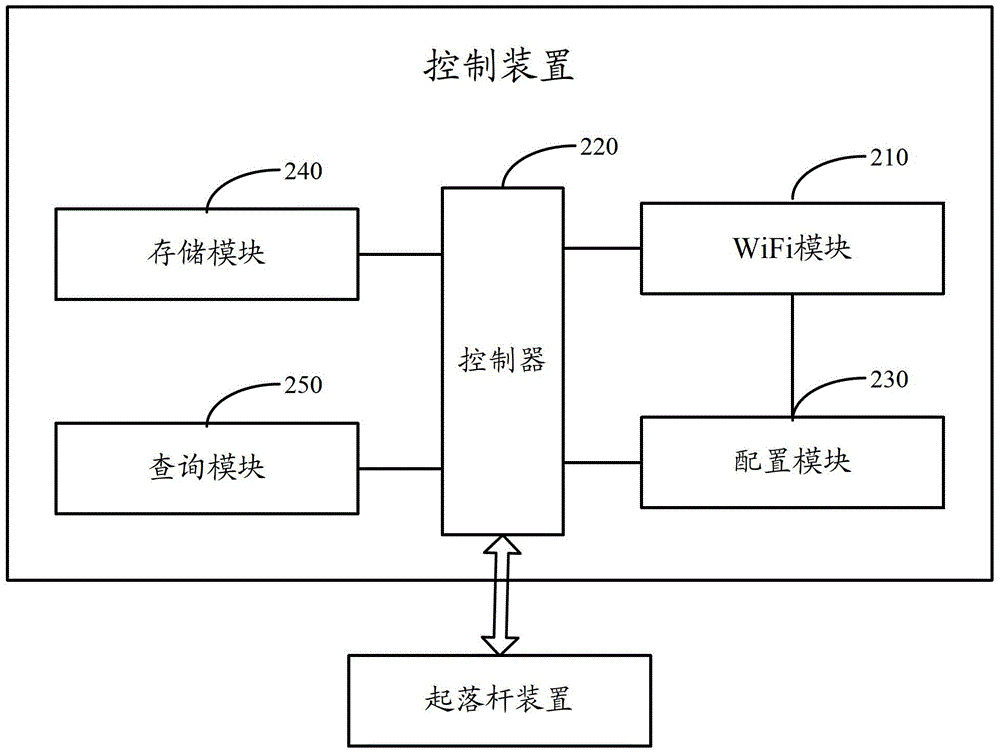
Control device and lifting-falling lever device control system
InactiveCN104424780AEnsure access securityLower control costsTransmission systemsNetwork topologiesControl systemWifi network
A control apparatus, and a control system for a rod lifting apparatus. The system comprises: a portable terminal (110), a control apparatus (120), and a rod lifting apparatus (130) connected to the control apparatus (120). The portable terminal (110) obtains, through searching, a WiFi network provided by the control apparatus (120), and sends a WiFi connection request to the control apparatus (120). The control apparatus (120) establishes a WiFi connection based on the WiFi connection request, sends a rod lift-up instruction to the rod lifting apparatus (130), and when the WiFi connection is broken, sends a rod lift-down instruction to the rod lifting apparatus (130). The system applies the WiFi technology to the control system for the rod lifting apparatus, so that in a case of no customization, a user can successfully control lift-up and lift-down of the rod by carrying the portable terminal in a car, thereby improving car park access efficiency.
Owner:ZTE CORP
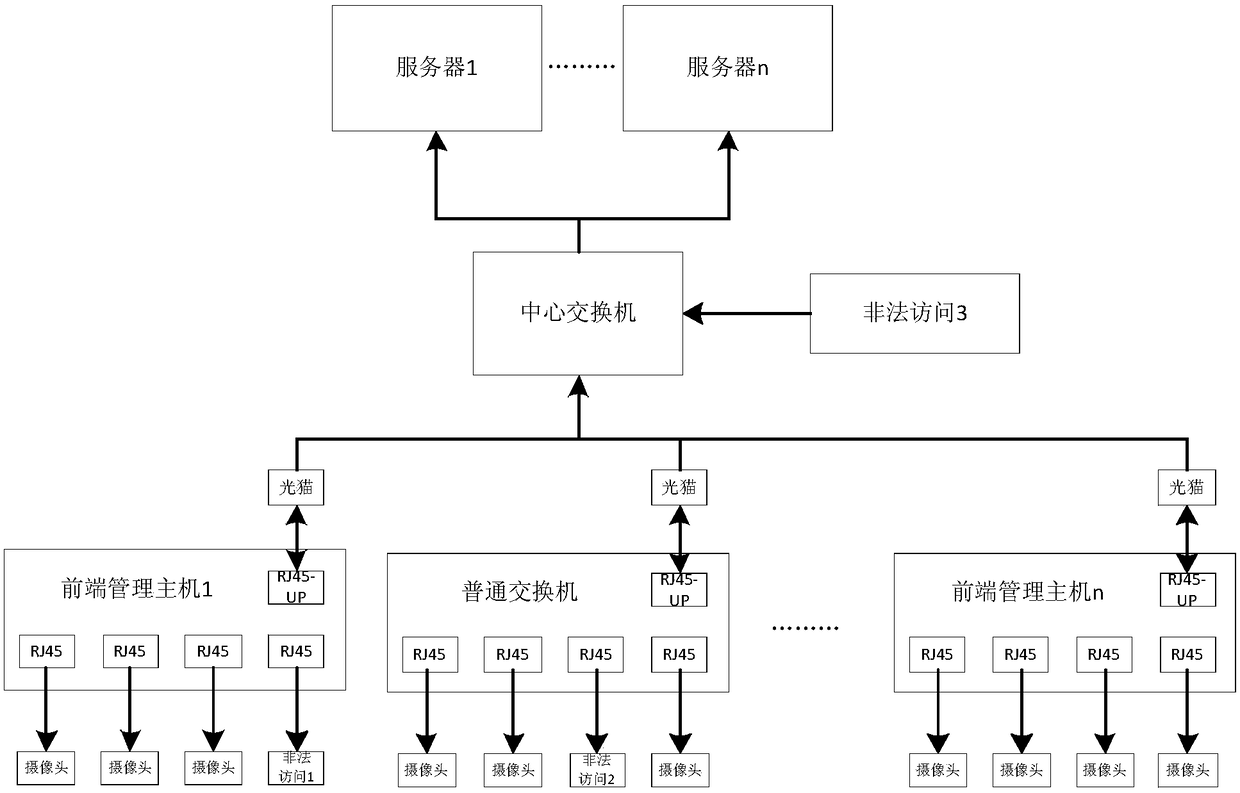
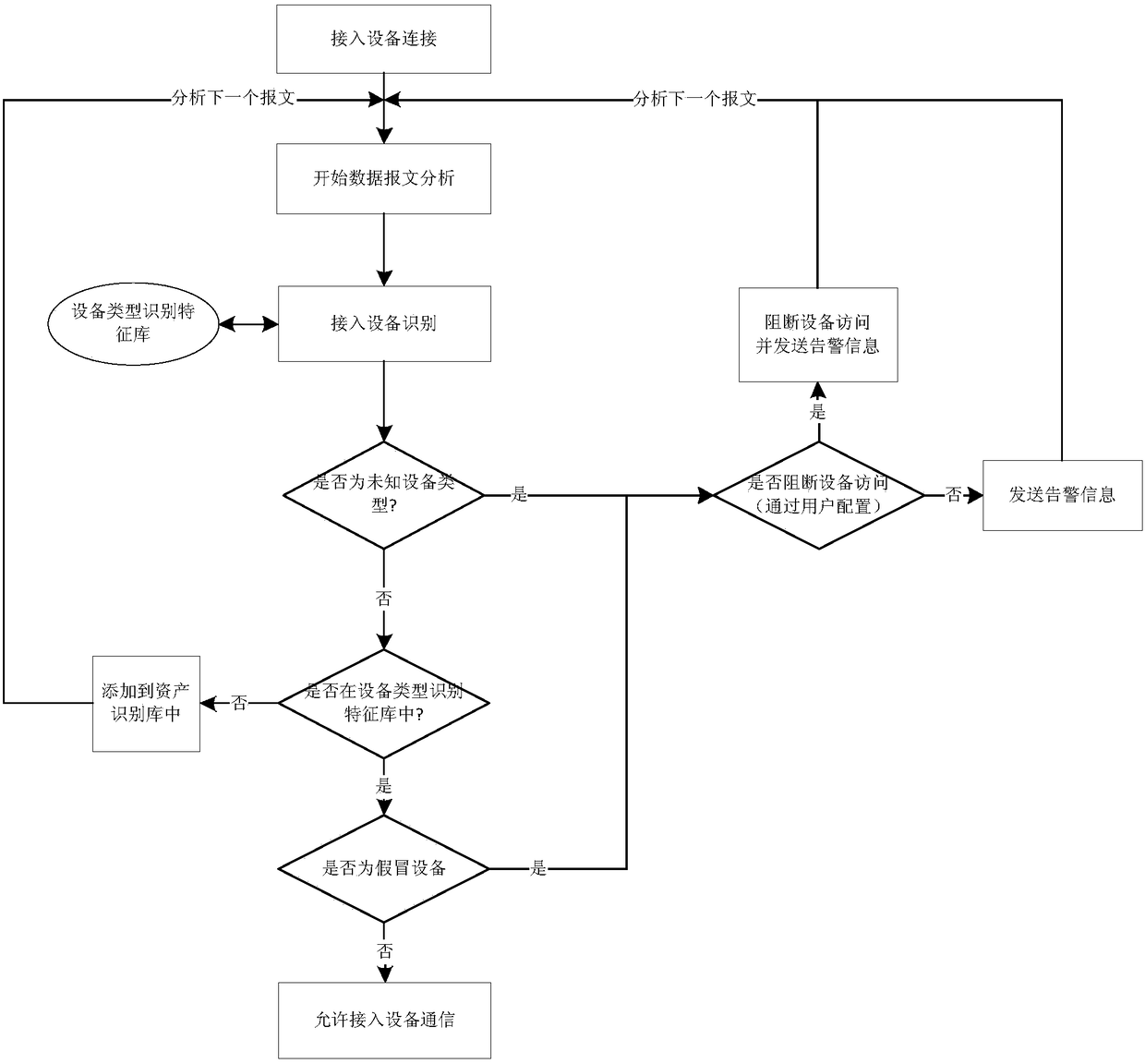
Video monitoring security access method based on equipment feature recognition
InactiveCN108494737ARealize illegal accessAutomatic quick identificationClosed circuit television systemsTransmissionVideo monitoringDevice type
The invention discloses a video monitoring security access method based on equipment feature recognition. The method is based on front-end management hosts connected with access equipment; the front-end management hosts, like common switches, are connected with the server via a central switch; a CPU with illegal access and illegal access detection and control functions is arranged in each front-end management host, a plurality of external ports connected with the access equipment are arranged on the front-end management host, and each external port is connected with the CPU of the front-end management host; and the server can distribute an equipment type recognition feature library to each front-end management host via the central switch. According to the method provided by the invention,the front-end management host is used for performing port mirroring, message analysis, equipment feature recognition and other functions on the access equipment to achieve illegal access, equipment counterfeit and detection and control of the illegal access; and the communication of the access equipment is automatically blocked and / or the treatment of only sending warning information is performedaccording to user configuration.
Owner:浙江远望通信技术有限公司
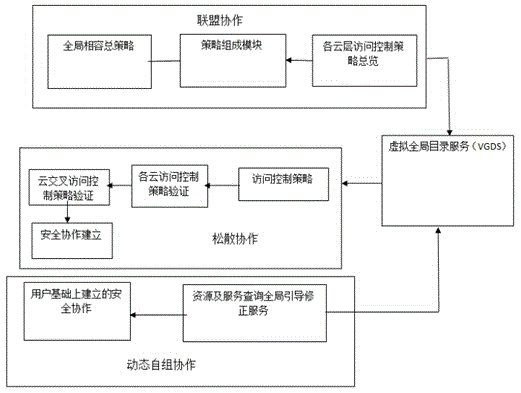
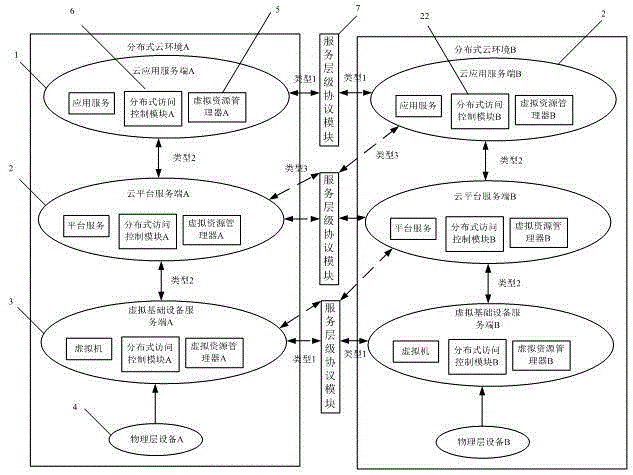
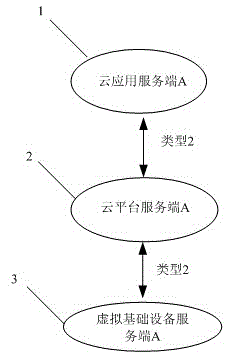
Security access control framework under distributed cloud environment and access method thereof
InactiveCN105049409AEnsure interoperabilitySuitable for access management needsTransmissionPolicy decisionApplication server
The invention relates to a security access control framework under a distributed cloud environment and an access method thereof, which solves a defect of unavailability in allusion to a distributed multi-cloud system access control framework. The security access control framework under the distributed cloud environment comprises virtual resource manager A and a distributed access control module A, wherein the virtual resource manager A is used for providing and configuring virtual resources and maintaining a virtual demand resource table associated with the configuration thereof, and the virtual demand resource table comprises local and remote resources in the whole virtual global catalog service library; the distributed access control module A is used for strengthening an access control policy, and comprises a policy decision point, a policy strengthening point and a policy library; and a cloud application server A, a cloud platform server A and a virtual infrastructure server A are all provided with the virtual resource manager A and the distributed access control module A. Provided by the invention is a method for preventing channel attack and no interference in a multi-tenant or resource virtual environment, and a safe and reliable distributed cloud computing infrastructure is established.
Owner:HEFEI CITY COULD DATA CENT
Identity authentication method and device
PendingCN112533202ACalculation speedReduce attackKey distribution for secure communicationUser identity/authority verificationAccess networkTerminal equipment
The invention provides an identity authentication method and device, and belongs to the technical field of communication. According to the scheme provided by the invention, the terminal equipment sends the network access request carrying the temporary privacy identity identifier to the network equipment when having the network access requirement, and performs message interaction and verification with the network equipment according to the verification key corresponding to the temporary privacy identity identifier, and therefore the identity authentication process is completed. The network device can identify the anonymous identity of the user without maintaining an identity database, it can be guaranteed that privacy of the user is not leaked, meanwhile, due to the fact that the network device can filter out false request packets on the front side of the identity management server in the identity identification process, and the processing pressure of the network device is greatly reduced. In this way, a large number of processing resources are prevented from being occupied, processing of normal request packets is not affected, and normal operation of network services can be guaranteed.
Owner:HUAWEI TECH CO LTD
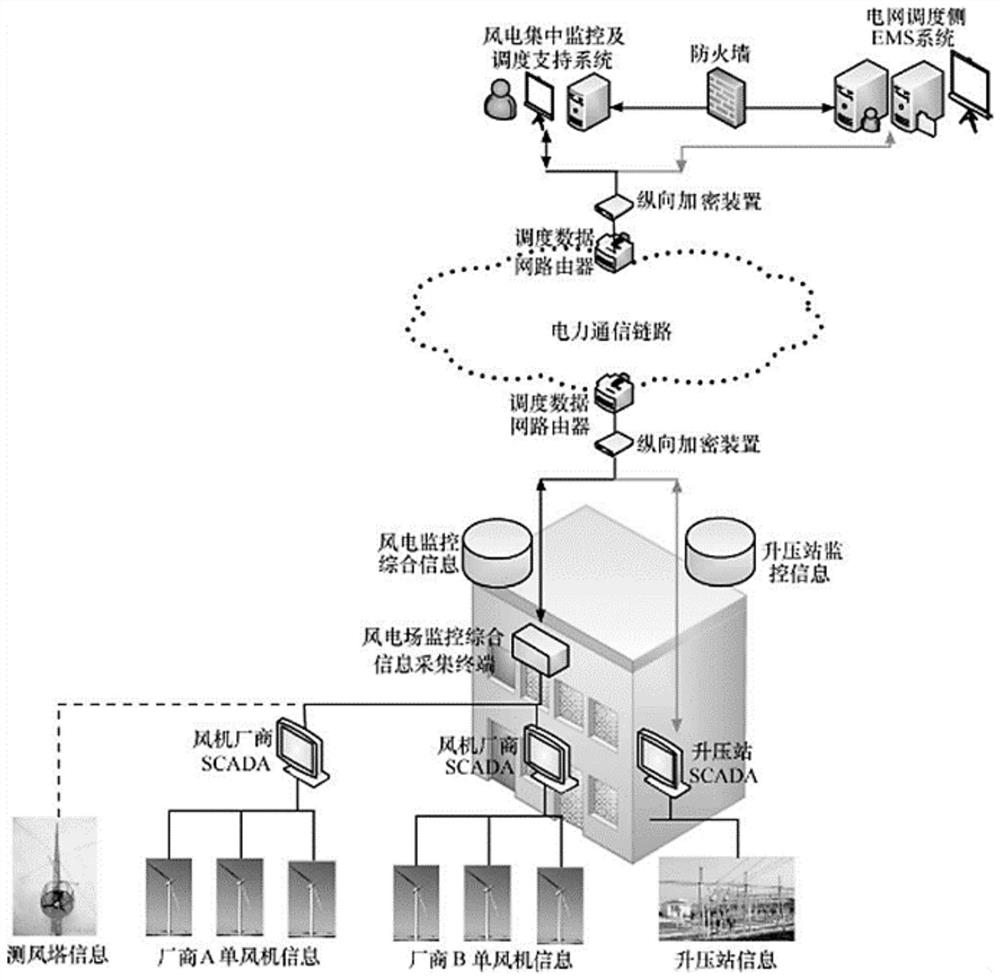
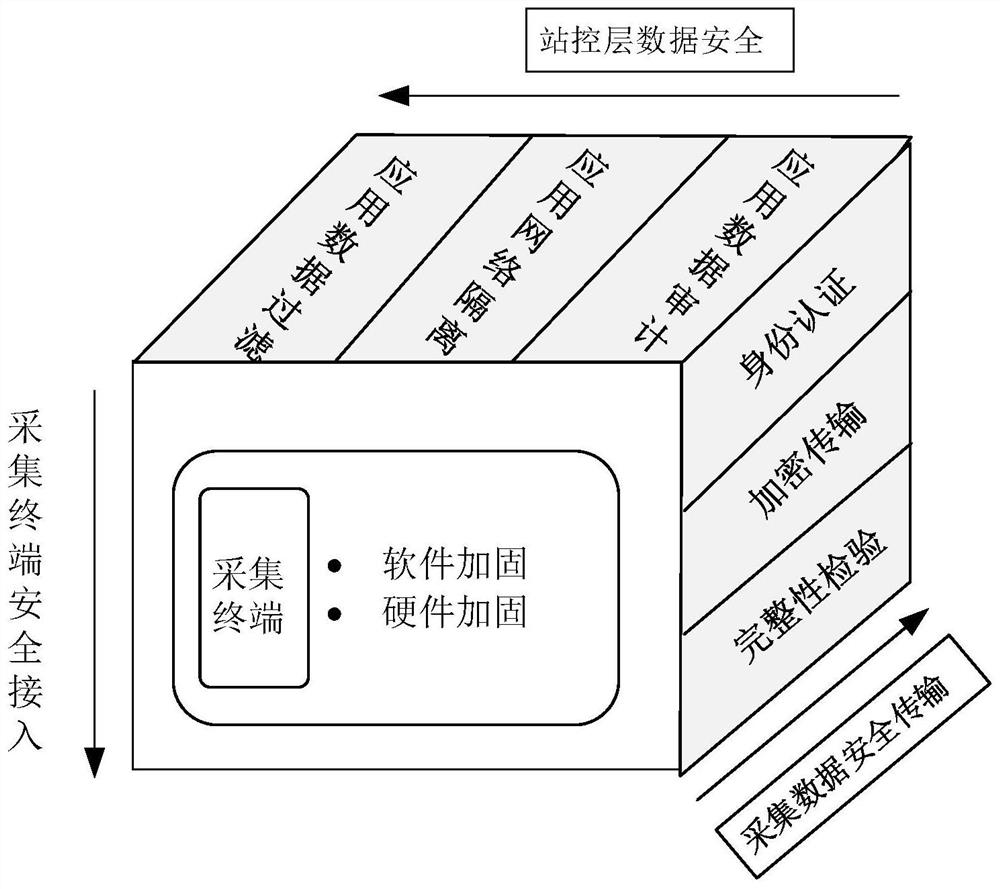
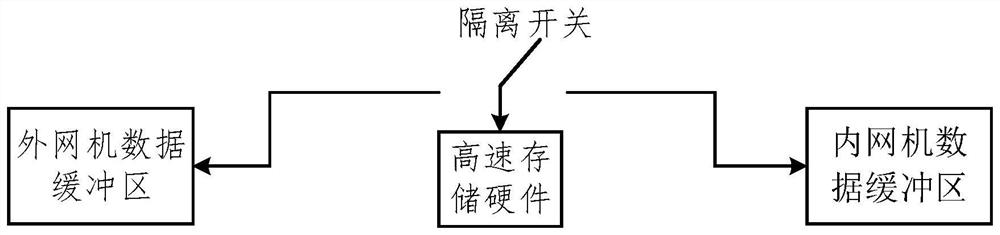
New energy plant station power generation unit acquisition terminal data safety guarantee method and system
The invention provides a new energy plant station power generation unit acquisition terminal data safety guarantee method and system. Mainly from the three aspects of acquisition terminal access safety, acquisition data safety transmission and station control layer data safety use, safety protection measures are added for the three links of data acquisition, transmission and use, data safety is guaranteed, and a complete set of method and system is formed. According to the invention, software and hardware security reinforcement is carried out on an acquisition terminal to ensure terminal security access; the two-way identity authentication technology based on the digital certificate technology and the ECDH security key exchange protocol based on SM2 are reasonably utilized to ensure the security transmission of data. And meanwhile, the data security of a station control layer is realized by utilizing a data filtering technology and a network isolation technology, so that a set of complete method and system for realizing the data acquisition security of the power generation unit of the new energy plant station are formed, and the method and system have universality for the protection of the data security of the new energy plant station and have wide application prospects.
Owner:CHINA ELECTRIC POWER RES INST +1
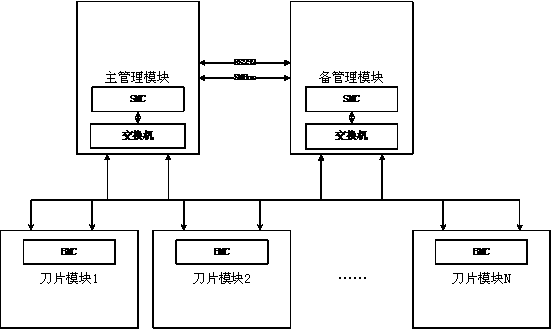
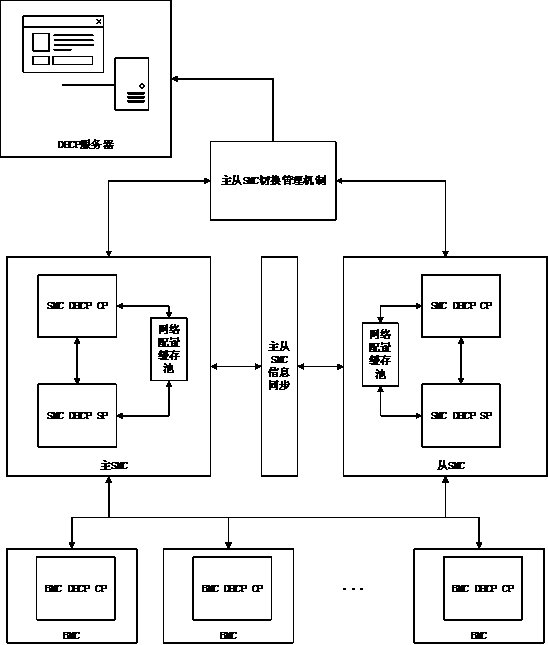
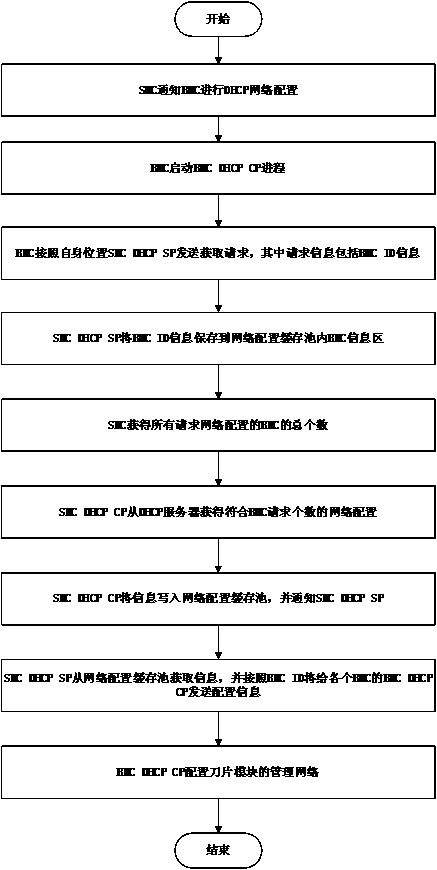
Blade server management network driving DHCP allocating method
ActiveCN103916280AEnsure access securityImprove configuration securityData switching networksDistribution methodConnection form
The invention provides a blade server management network driving DHCP allocating method. Firstly, the network of a blade server management module is configured through a superior DHCP server; secondly, the networks of blade modules apply to the superior DHCP server and are configured through the management module. The allocating method mainly comprises the steps related to a blade server managerial grid external access mode, preconditions of management module or blade module driving type DHCP allocation and network driving DHCP configuration managing. By means of the allocating method, excessive modules can be prevented from being exposed to the external network, the safety performance of traditional server managerial grid DHCP configuration is improved, and the allocating method can be conveniently achieved under the Ethernet connection form, the large blade server cluster management network can be configured fast, and the network running, managing and maintaining cost caused in the large-scale cluster arranging process can be reduced.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
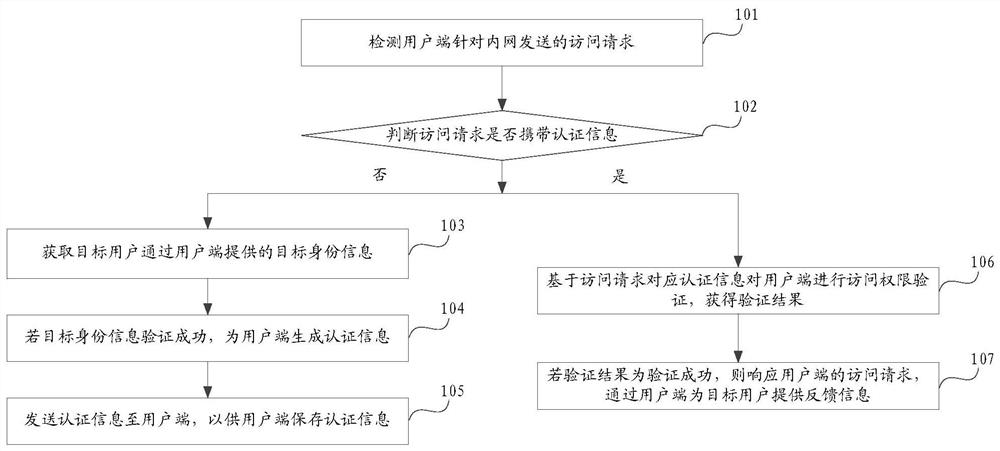
Information processing method and device, and server
PendingCN112836202AEnsure access securityImplement automatic authenticationDigital data protectionDigital data authenticationInformation processingInternet privacy
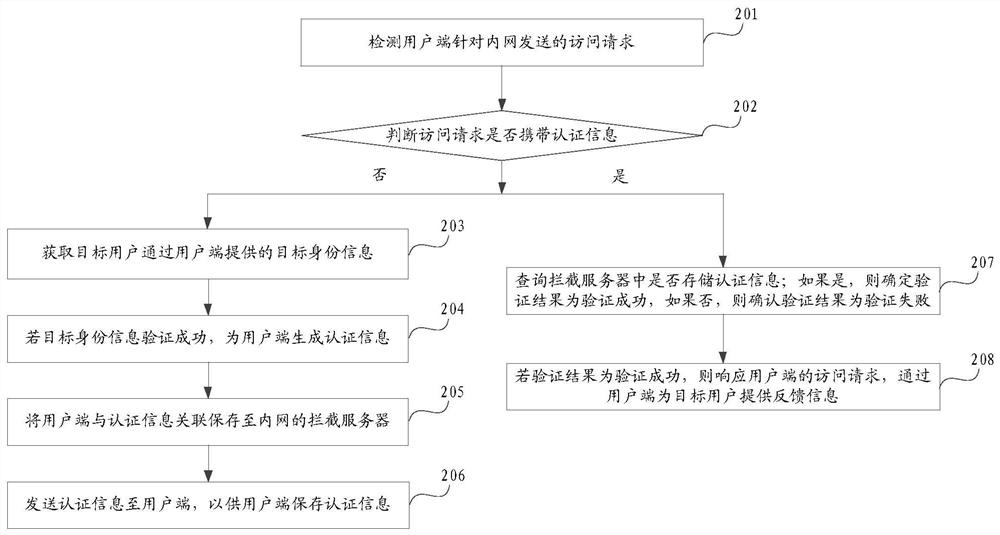
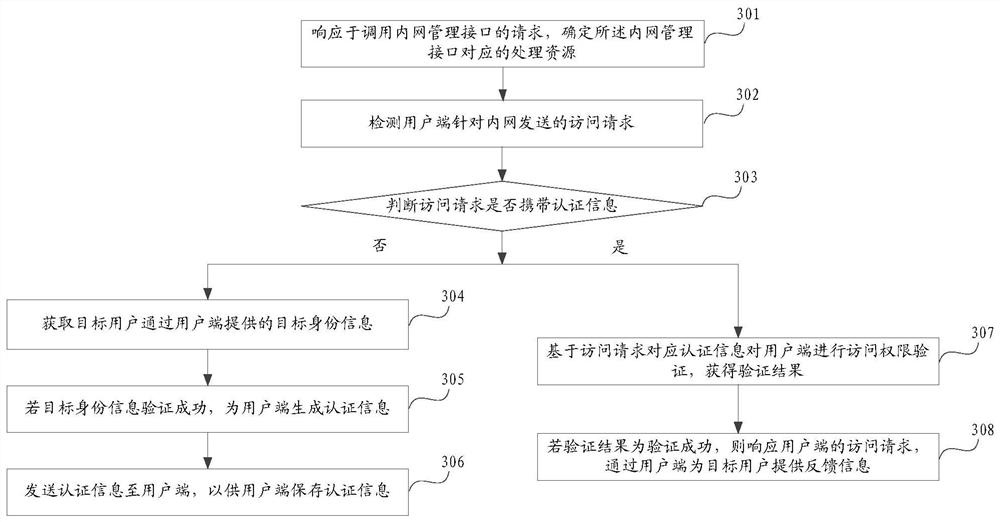
Embodiments of the invention provide an information processing method and device, and a server. The method comprises the steps of detecting an access request sent by a user terminal for an intranet; wherein the access request is triggered by a target user; judging whether the access request carries authentication information; if not, obtaining target identity information provided by the target user through the user terminal; if the target identity information is successfully verified, generating authentication information for the user terminal; sending the authentication information to the user terminal so that the user side can store the authentication information; wherein the authentication information and the re-initiated access request are provided at the same time; if yes, performing access permission verification on the user terminal based on authentication information carried by the access request, and obtaining a verification result; and if the verification result is successful verification, responding to the access request of the user terminal, and providing feedback information for the target user through the user terminal. According to the method of the invention, the intranet access efficiency is improved.
Owner:长沙市到家悠享网络科技有限公司
IMS-based intelligent operation and maintenance fault diagnosis management method
PendingCN112804106AImprove securityImprove transmission securityNatural language data processingResourcesEngineeringDiagnosis management
The invention discloses an IMS-based intelligent operation and maintenance fault diagnosis management method, which comprises the following steps: S1, collecting working environment data and network environment data for fault analysis; S2, displaying the collected environment data and network data to a client; S3, performing analysis through big data, and positioning a fault point accurately; S4, analyzing the cause of the fault, and judging whether an automatic solution mode or a manual solution mode is adopted or not; S5, fault solving: solving fault points solved by adopting automatic processing, automatically sending an order, and giving responsibilities to people; and S6, automatically counting a data report through IMS intelligent operation and maintenance faults for a manager to examine. By adopting the IMS intelligent operation and maintenance fault diagnosis management system, on one hand, the equipment state can be effectively monitored, the fault reason can be analyzed, the fault problem can be remotely solved, and one-key data statistics can be realized; and on the other hand, network access security and transmission security can be improved, the intelligent management level of security and protection equipment is improved, industrial upgrading is promoted, and smart city and smart traffic construction is improved.
Owner:辽宁科电交通科技有限公司
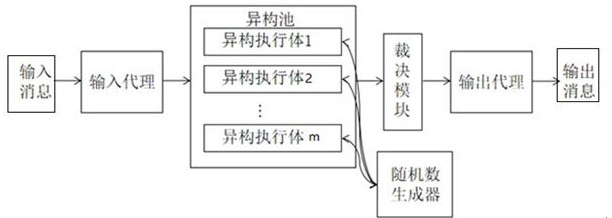
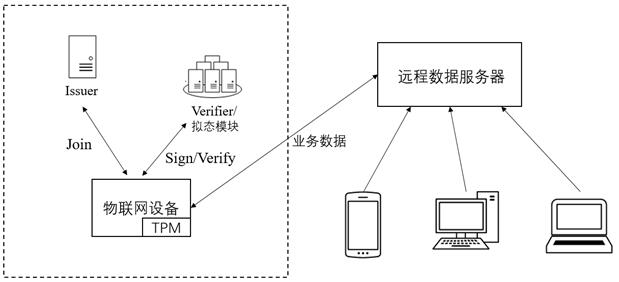
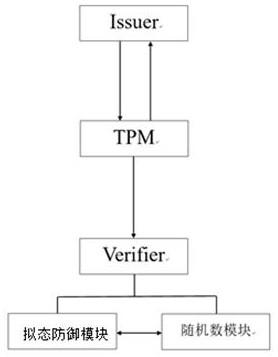
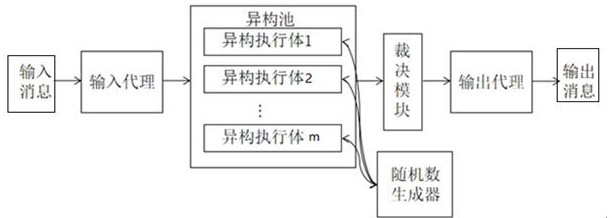
Bidirectional anonymous authentication system and method based on mimicry defense principle
ActiveCN111741008AEnsure access securityEnsure safetyUser identity/authority verificationThe InternetHigh availability
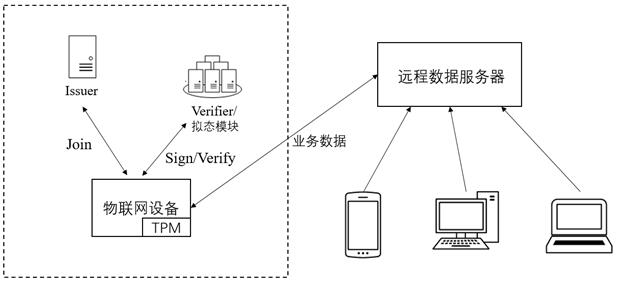
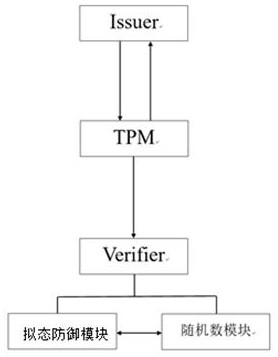
The invention discloses a bidirectional anonymous authentication system and method based on a mimicry defense principle, and is applied to the technical field of information security. The method comprises the steps that a certificate issuer is initialized; a Join sub-protocol runs between a platform and the certificate publisher; the platform operates a Sign sub-protocol between the TPM and the Host; and a signature detection party operates the Verify sub-protocol through a heterogeneous executive body. According to the invention, a DAA bidirectional anonymous authentication technology is adopted; a mimicry module is added in the signature detection party; while remote anonymous authentication of the underlying equipment accessing the Internet of Things network is realized, the endogenoussecurity function of the mimicry module can effectively resist any security threat implemented by using a known and unknown software and hardware vulnerability back door in a target system, so that the access security of the Internet of Things equipment is ensured at the technical architecture level, the three-in-one attribute of high reliability, high credibility and high availability is achieved, and the security of the Internet of Things system is ensured.
Owner:NANJING REDMATRIX NETWORK SECURITY TECH R & D INST
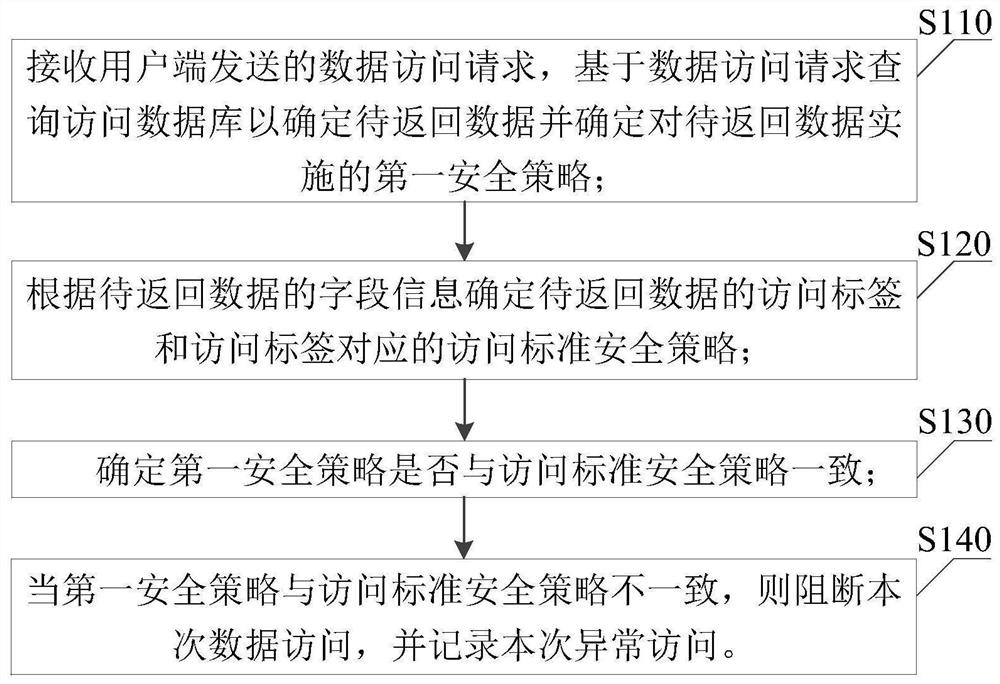
Data management method and device, electronic equipment and storage medium
PendingCN114021184AEnsure access securityEnsure flow securityDigital data protectionDigital data authenticationData accessEngineering
The invention discloses a data management method and device, electronic equipment and a storage medium. The method comprises: receiving a data access request sent by a user side, querying an access database based on the data access request to determine to-be-returned data, and determining a first security policy implemented to the to-be-returned data; determining an access label of the to-be-returned data and an access standard security policy corresponding to the access label according to the field information of the to-be-returned data; determining whether the first security policy is consistent with an access standard security policy; and when the first security policy is inconsistent with the access standard security policy, blocking the current data access, and recording the current abnormal access. According to the embodiment of the invention, the access label of the data is automatically identified by utilizing the enterprise classification and grading rule, the standard security policy required to be implemented by the to-be-returned data is determined by utilizing the access label, and whether the security policy of the to-be-returned data is completely implemented or not is determined according to the standard security policy, so that the security of the data access is ensured, and the integrity of the database is reserved.
Owner:SHENZHEN LEXIN SOFTWARE TECH CO LTD
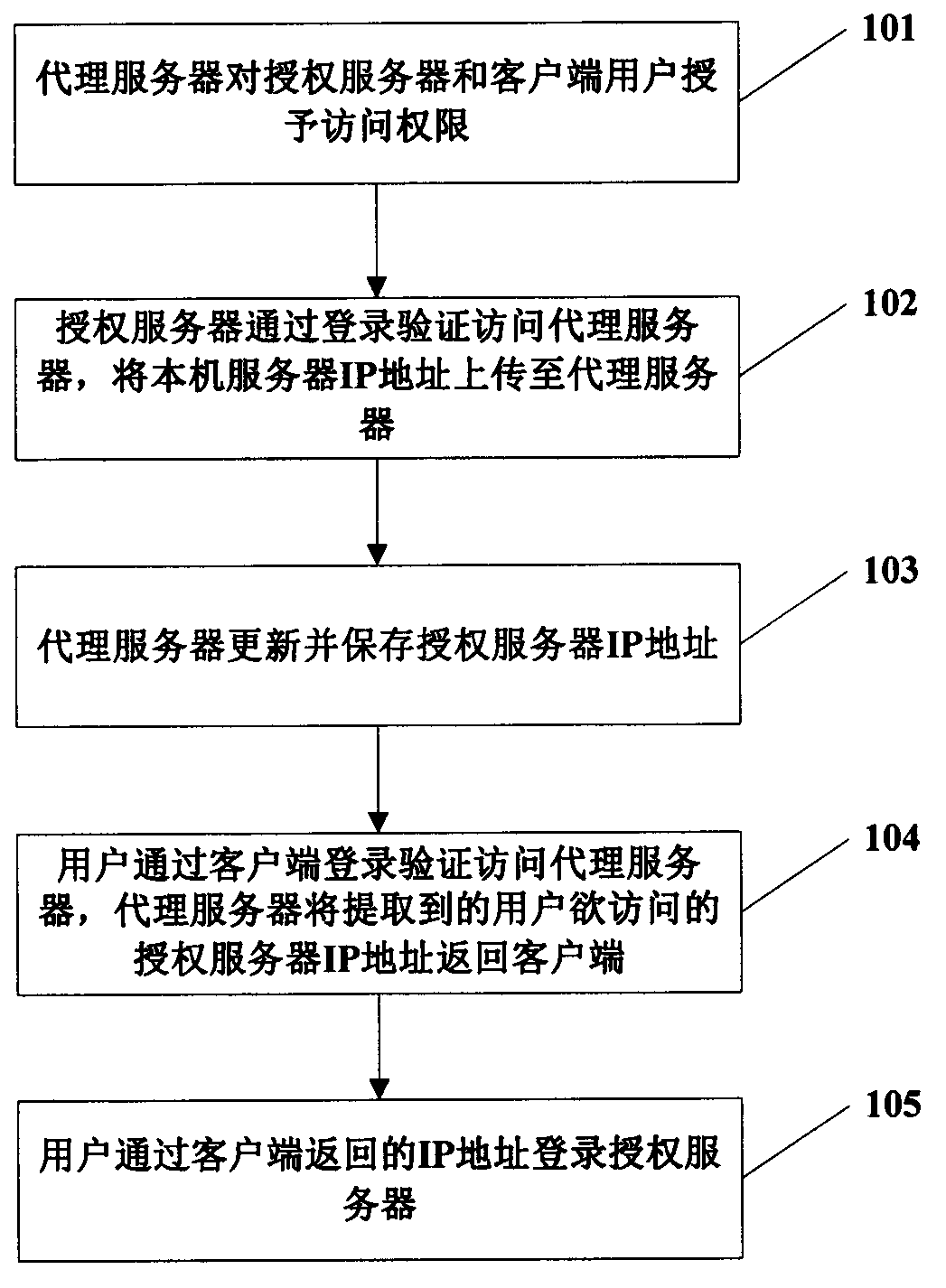
Method for acquiring dynamic IP address of server in real time
InactiveCN103780713AGet dynamic IP in real timeEnsure access securityTransmissionIp addressClient-side
The invention provides a method for acquiring a dynamic IP address of a server in real time. The method comprises following steps: a) that a proxy server confers access authority on an authorized server and a client user; b) that the authorized server submits verification information to the proxy server so as to verify the verification information and uploads the IP address of the authorized server to the proxy server after verification successes; c) that the proxy server updates the IP address of the authorized server and stores the IP address of the authorized server in a specific storage space; d) that a user submits the verification information with a client in order to have access to the proxy server and the proxy server returns extracted IP address of the authorized server that the user wants to have access to back to the client after verification succeeds; and e) that the user logs in the authorized server with the IP address returned from the client. The method authentically achieves a fact that a user is not required to purchase a static IP address with high price and saves cost. Access steps related to the invention are all required to be verified such that access security is guaranteed.
Owner:SUZHOU JINGYIHUI INFORMATION TECH
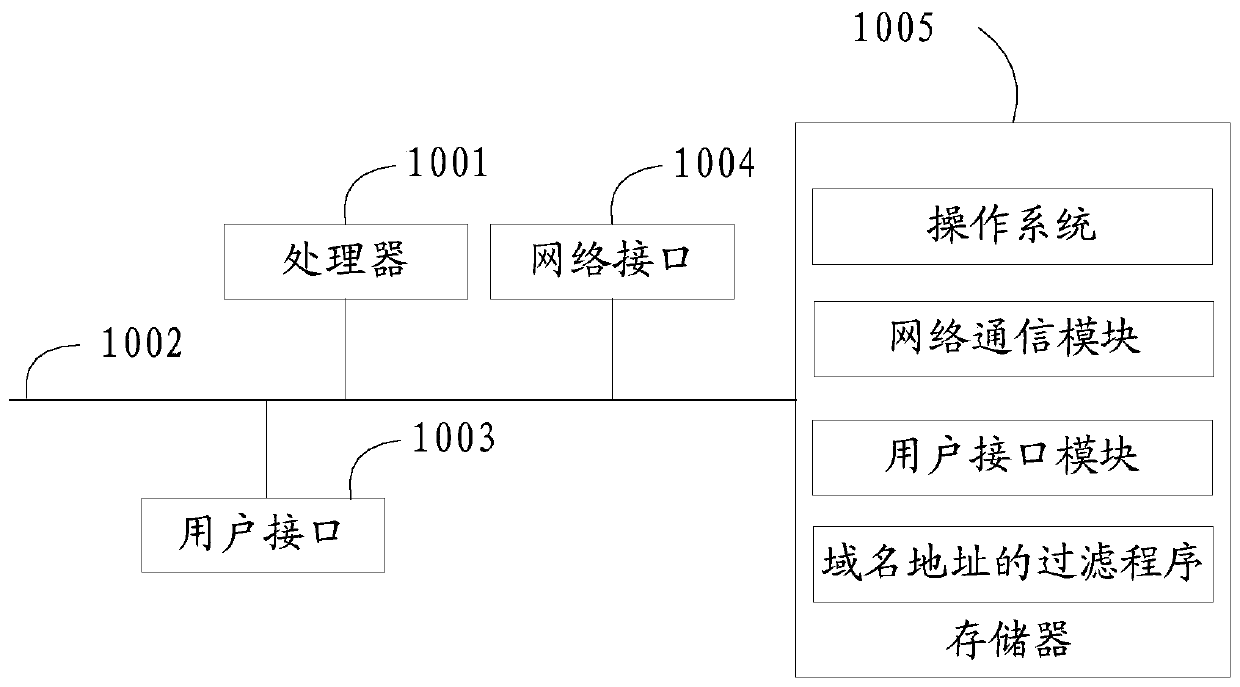
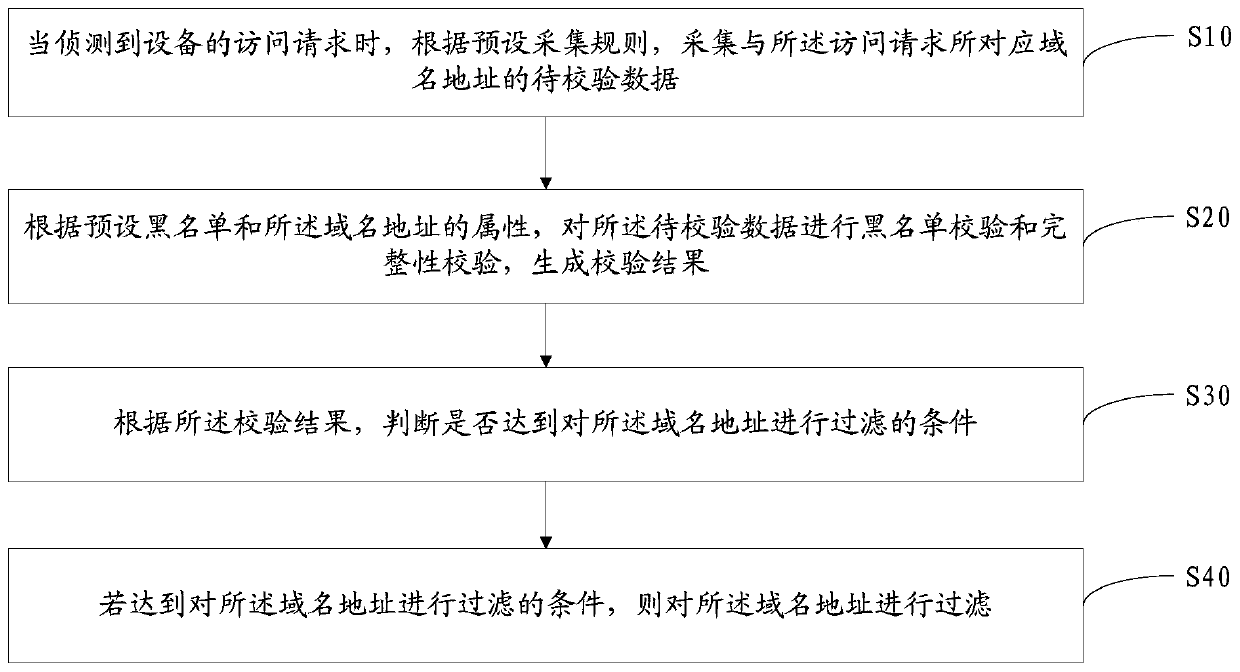
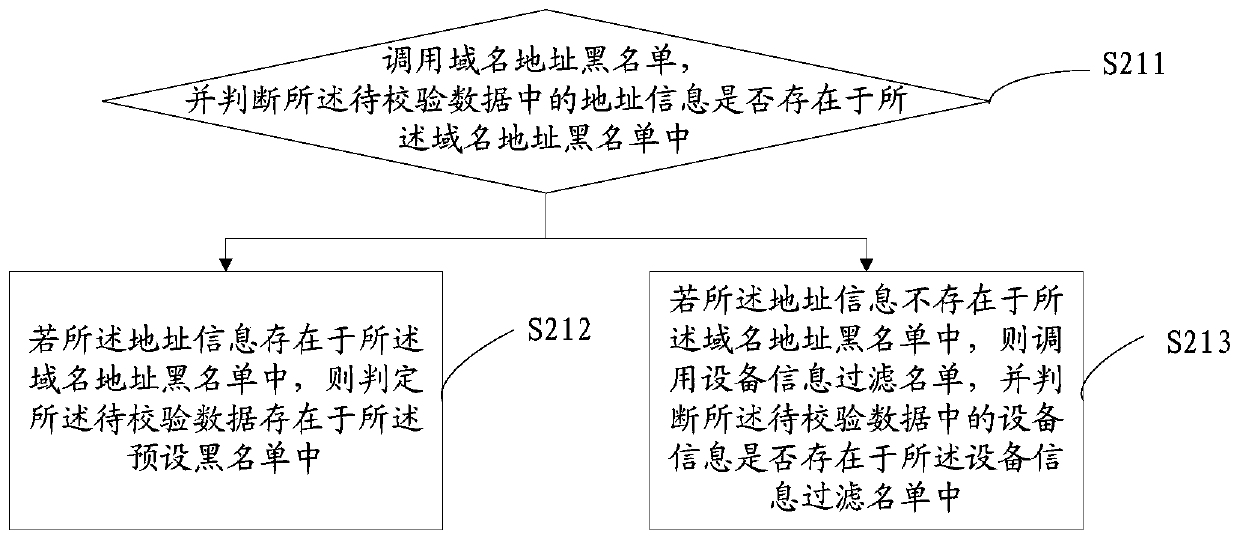
Domain name address filtering method and device and computer readable storage medium
InactiveCN111049816AReduce in quantityTimely responseTransmissionDomain nameTheoretical computer science
The invention discloses a domain name address filtering method, domain name address filtering equipment and a computer readable storage medium. The method comprises the following steps: collecting to-be-verified data of a domain name address corresponding to an access request according to a preset collection rule when the access request of the equipment is detected; performing blacklist verification and integrity verification on the to-be-verified data according to a preset blacklist and attributes of the domain name address to generate a verification result; judging whether a condition of filtering the domain name address is met or not according to the verification result; If the condition of filtering the domain name address is met, filtering the domain name address. According to the invention, by setting the filtering mechanism, the domain name addresses with definite risks and incompleteness are filtered and intercepted, and only the effective domain name addresses need to be identified, so that the recognition efficiency is improved, and the access request can be timely and quickly responded while the access safety is ensured.
Owner:BEIJING QIHOO TECH CO LTD
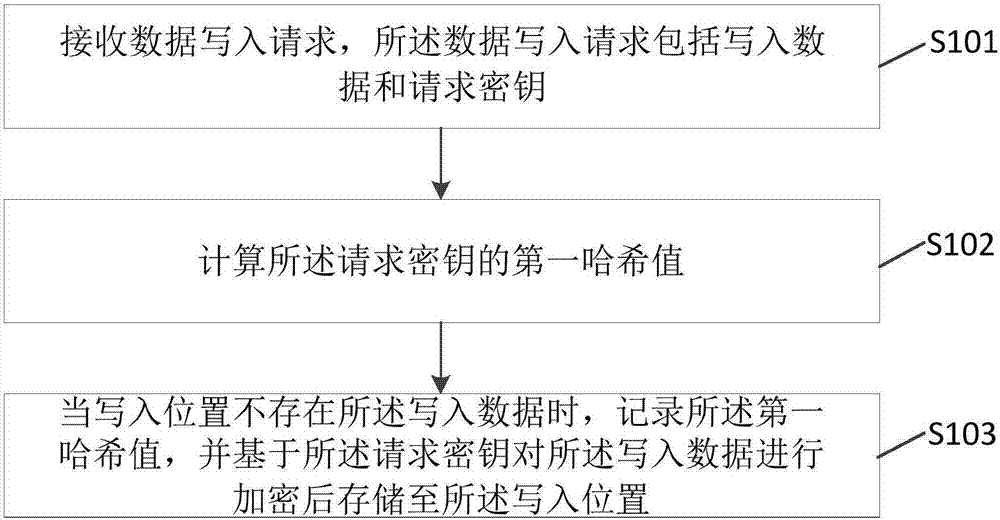
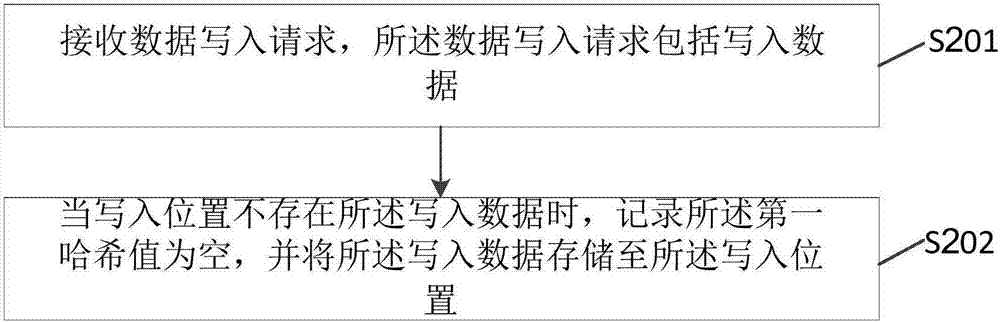
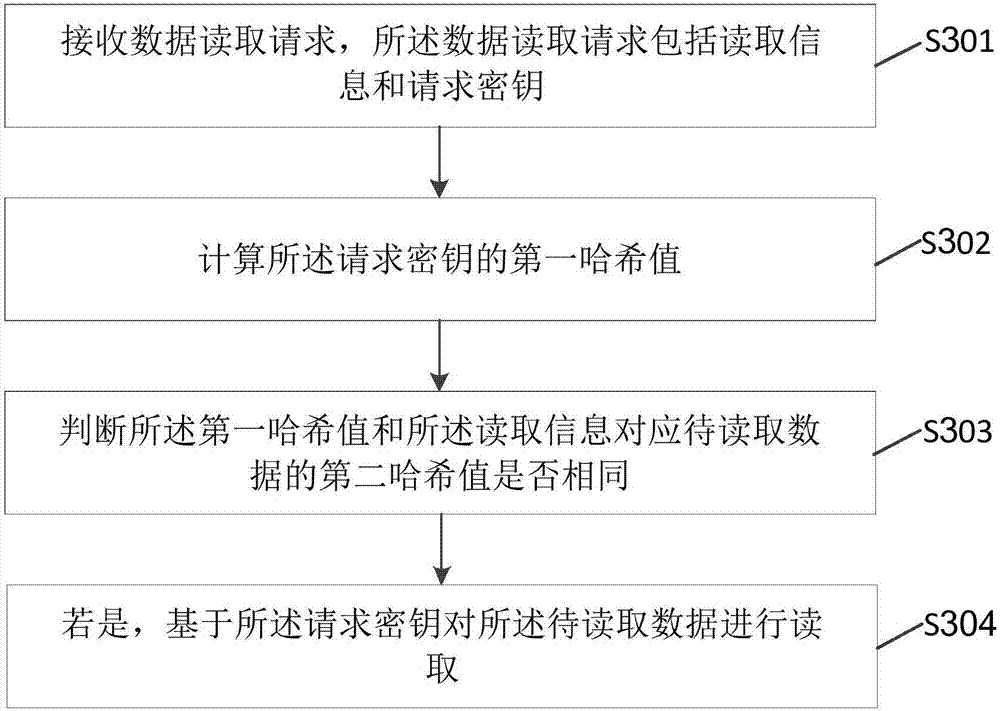
Data writing method and device and data reading method and device
InactiveCN107122139AEnsure access securityTaking into account the access speedInput/output to record carriersDigital data protectionComputer hardwareData access
The embodiment of the invention provides a data writing method and device and a data reading method and device. According to the embodiment, a data writing process and a data reading process are included; after a Hash value of written data is recorded, the written data is encrypted and stored; and in the data reading process, corresponding data cannot be read unless a Hash value of a reading request key is matched with a Hash value of to-be-read data. Compared with the prior art, it is allowed to save the Hash value of the written data only, a request key of the written data does not need to be saved, different keys can be used for different data, and therefore data access speed can be considered on the premise of guaranteeing data access security.
Owner:SHENZHEN TINNO WIRELESS TECH
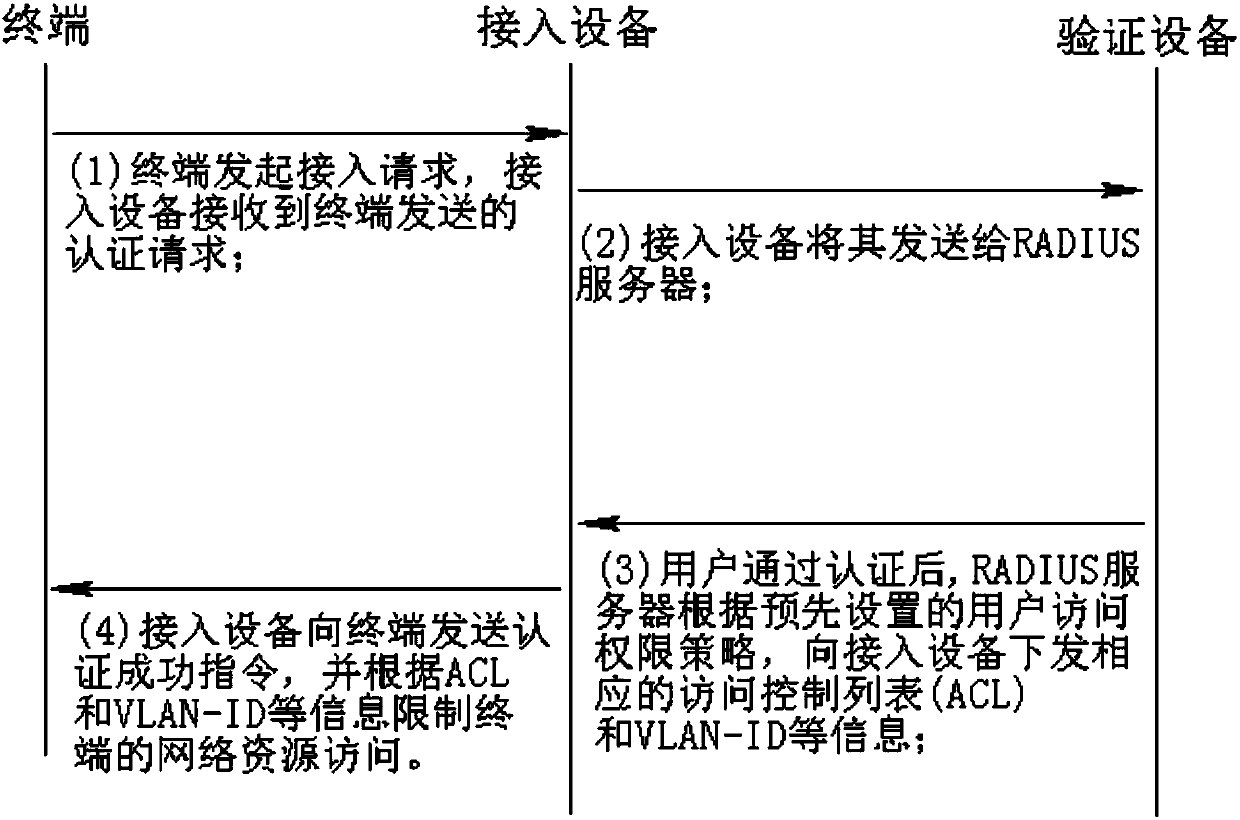
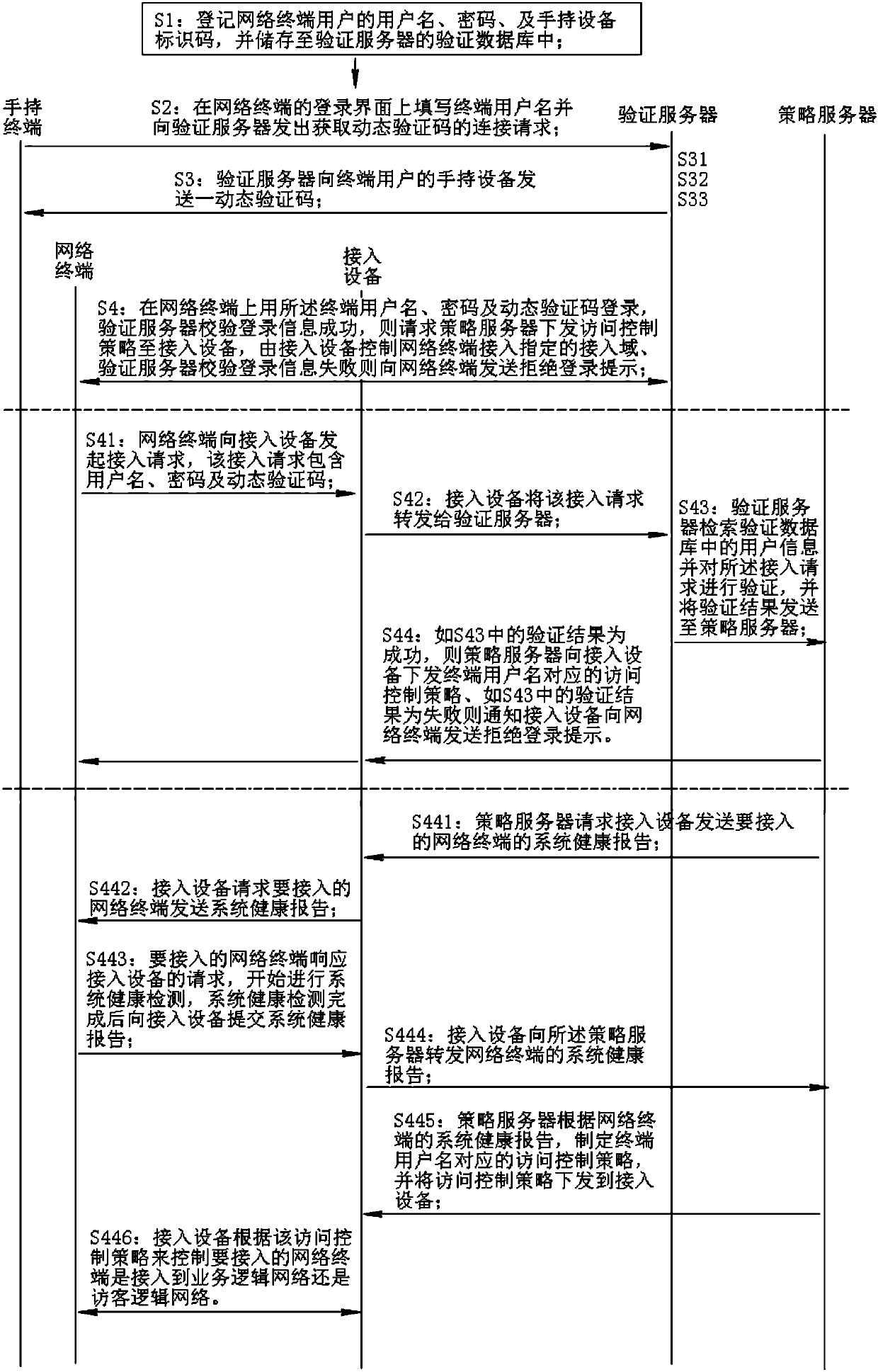
Network access control method with system health detection prior to access
InactiveCN107770003AImprove access authentication performanceEnsure access securitySecurity arrangementWide area networksNetwork terminationPassword
The present invention discloses a network access control method with system health detection prior to access. The method comprises the steps of: S1: registering a user name, passwords and a handheld device identification code of a user of network terminal; S2: filling the user name of the terminal on a login interface of the network terminal, and emitting a connection request for obtaining dynamicverification codes to an authentication server; S3: sending one dynamic verification code to the handheld device of the terminal user by the authentication server; and S4: performing login authentication by employing the user name and the passwords of the terminal and the dynamic verification codes, and issuing corresponding access control policies to an access device by a policy server accordingto a system health report of the terminal. The network terminal requests one dynamic verification code to the authentication server, the dynamic verification code is employed to determine a legal identity of a user, a system health report is submitted to the policy server prior to access of a terminal, and therefore virus or hacker attack from the network terminal is effectively avoided and network access safety is comprehensively guaranteed.
Owner:台山市金讯互联网络科技有限公司
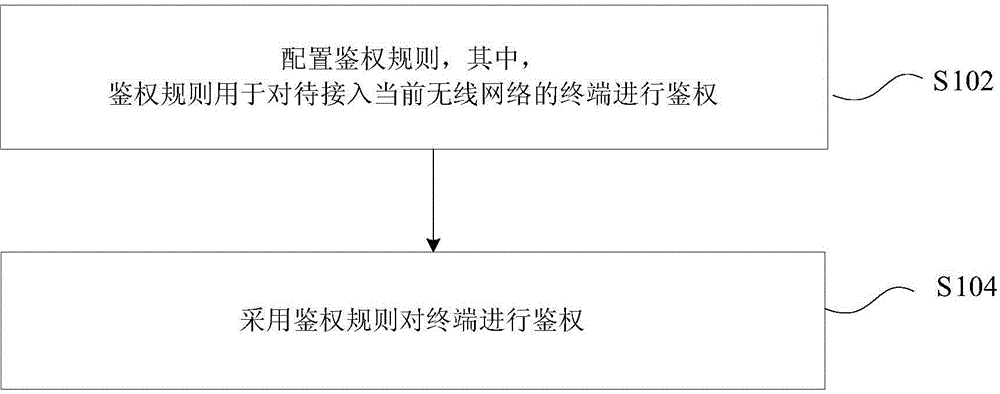
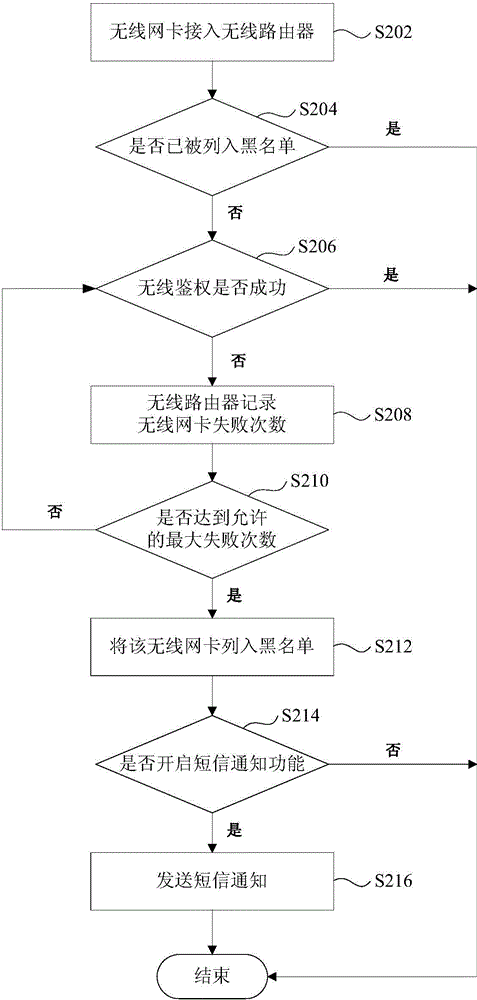
Wireless access authentication method and device
InactiveCN105228145AEnsure access securityImprove experienceSecurity arrangementWireless networkAuthentication
The invnetion discloses a wireless access authentication method and device. In the method, an authentication rule is configured, wherein the authentication rule is used to perform authentication for a terminal to be accessed to a wireless network; and the authentication rule is adopted to perform the authentication for the terminal. According to the technical scheme provided by the invention, and then through the custom authentication rule, most illegal accesses can be effectively identified, and then access safety of wireless equipment is ensured.
Owner:ZTE CORP
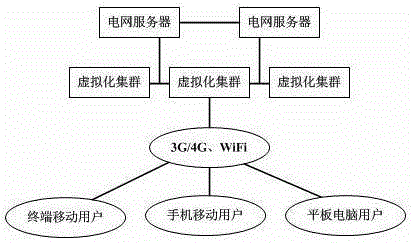
Power grid mobile office system based on virtualization
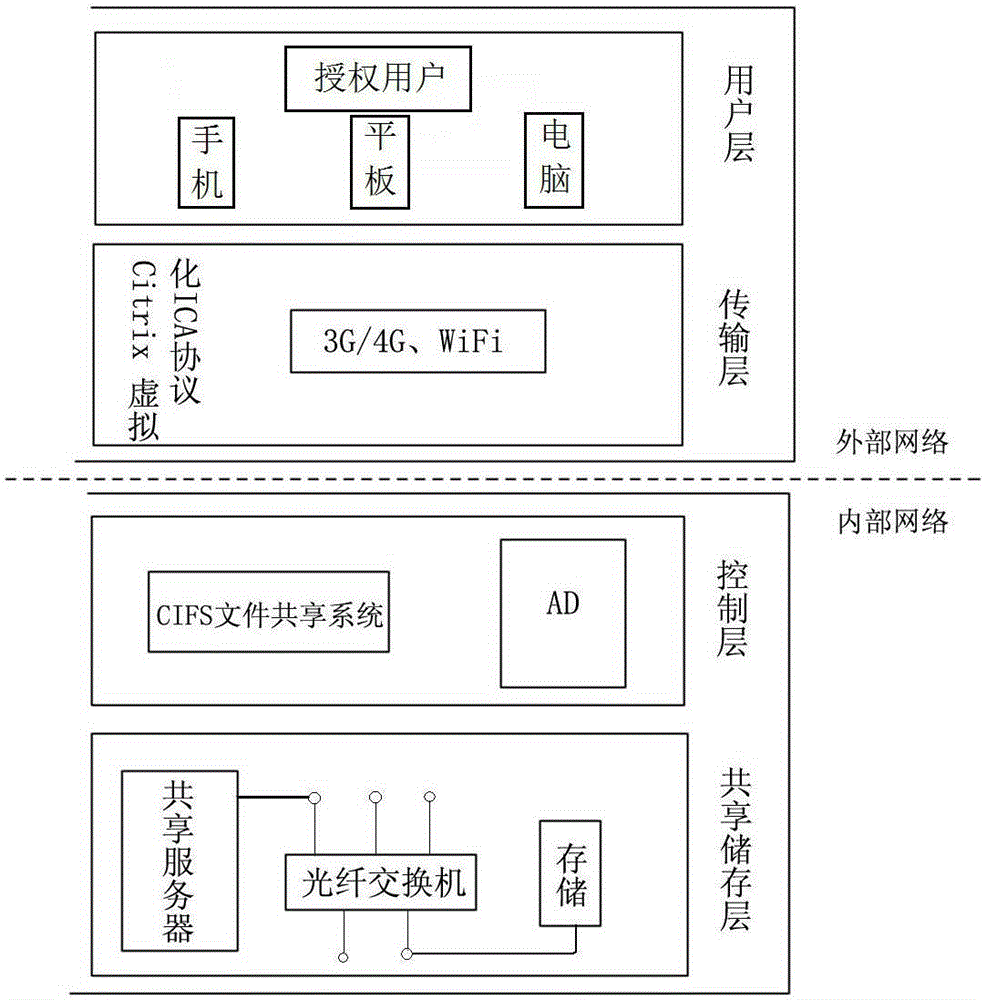
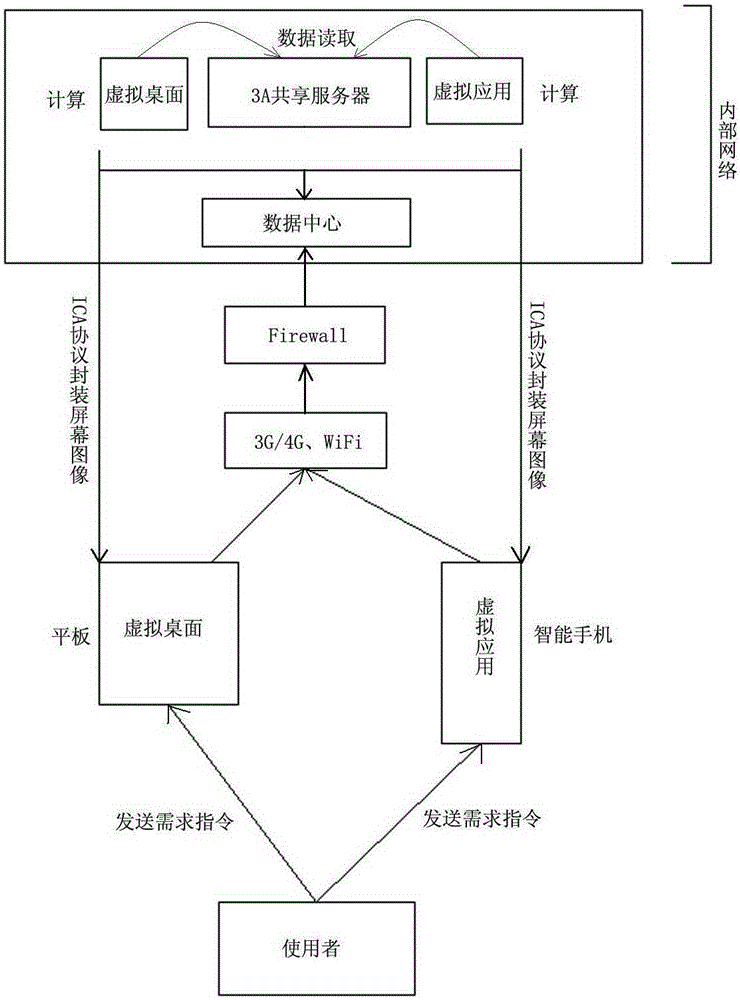
InactiveCN105227641ABreaking the limitations of "scheduled and fixed-point" officeRealize 3A office requirementsTransmissionAuthenticationVirtual desktop
The invention discloses a power grid mobile office system based on virtualization. The system comprises a shared storage layer, a transport layer, a control layer and a user layer; the shared storage layer virtualizes a Windows server through a Citrix server virtualization technology, and forms a file share server to store files and data shared by users in a virtual desktop and a virtual application through a mount FC storage device; the transport layer respectively controls individual virtual channels through the data compression, encryption and join optimization technologies based on a specific ICA (Independent Computing Architecture) protocol of a Citrix virtualization technology; the control layer links a Microsoft file shared service with an AD domain; the user layer makes a subscriber access the virtual desktop and the virtual application via C / S (Client / Server) or B / S (Browser / Server) after AD domain authentication by terminal equipment, and acquires corresponding files and data of the shared storage layer through the file shared service. The power grid mobile office system based on virtualization provided by the invention has the characteristics of being stable in performance, high in efficiency and safe.
Owner:GUIYANG POWER SUPPLY BUREAU OF GUIZHOU POWER GRID CO LTD
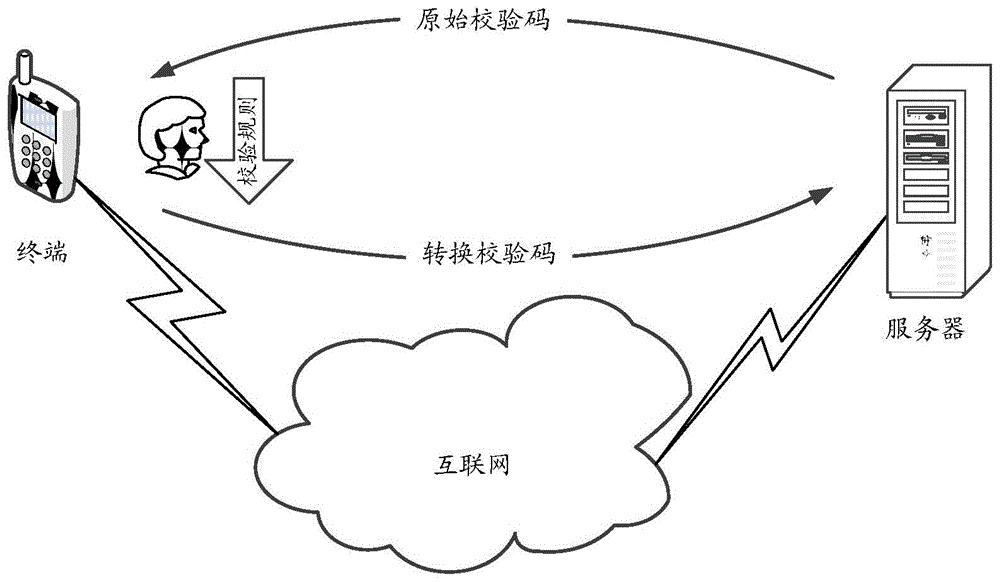
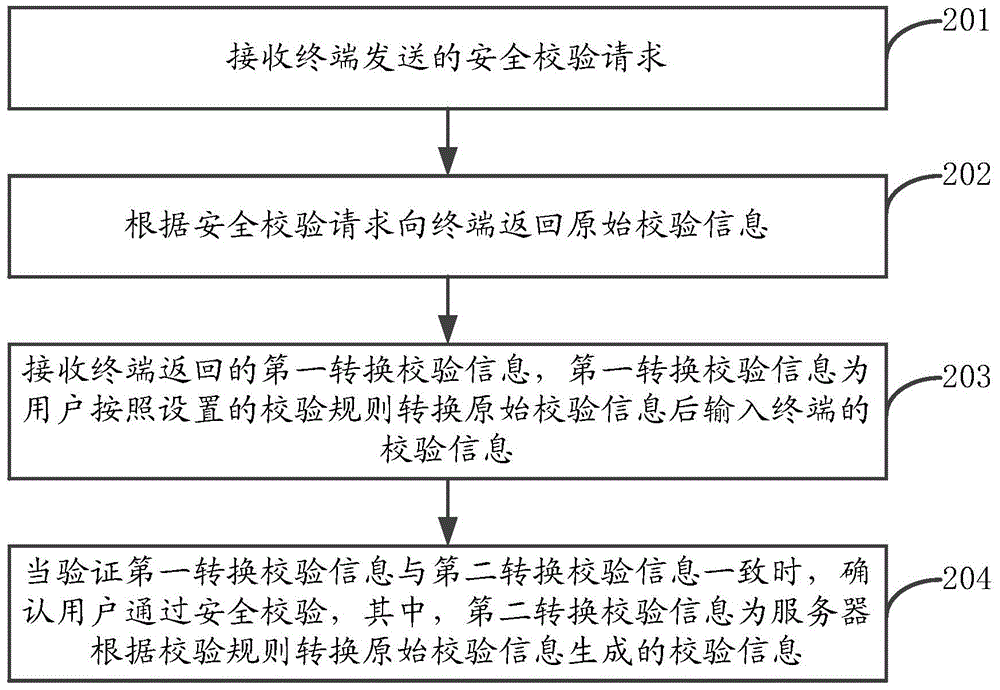
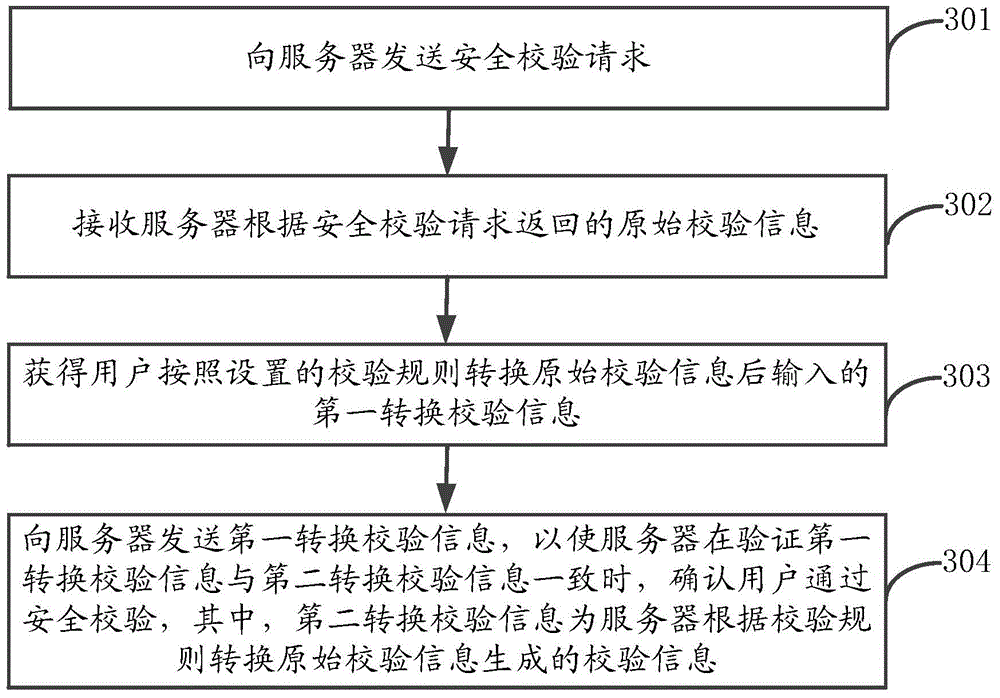
Safety verification method and device, server and terminal
InactiveCN105450592AImprove reliabilityEnsure access securityUser identity/authority verificationDigital data authenticationThird partyComputer terminal
The invention discloses a safety verification method and device, a server and a terminal. The method comprises the following steps: receiving a safety verification request sent by the terminal; returning original verification information to the terminal according to the safety verification request; receiving first conversion verification information returned by the terminal, wherein the first conversion verification information is the verification information input to the terminal by a user after the original verification information is converted based on preset verification rules; and when the first conversion verification information is identical to second conversion verification information, determining that the user passes safety verification. According to the safety verification method and device, the server and the terminal, the terminal carries out safety verification through the verification rules obtained through negotiation with the server; since a malicious third party cannot obtain the verification rules, the malicious third party cannot finish the safety verification even thought the third party obtains the original verification codes; and therefore, reliability of safety verification can be improved, and network application access safety is ensured.
Owner:ALIBABA GRP HLDG LTD
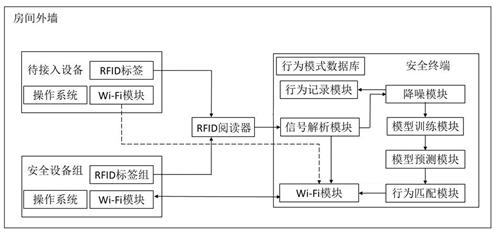
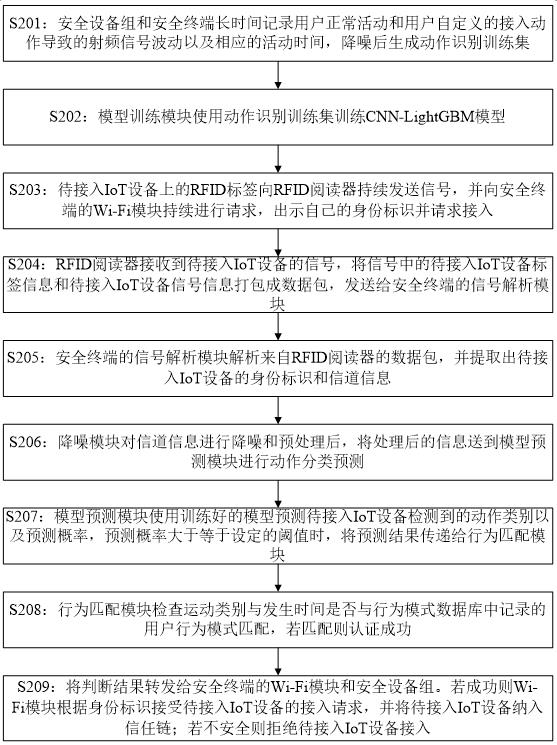
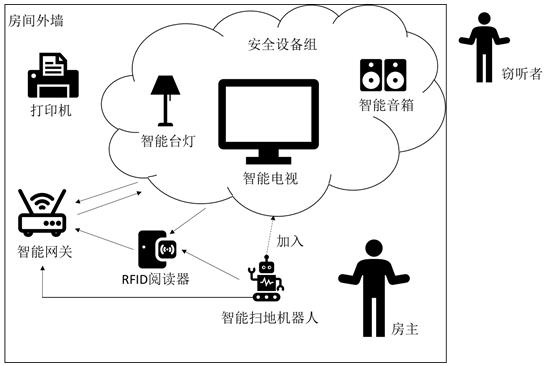
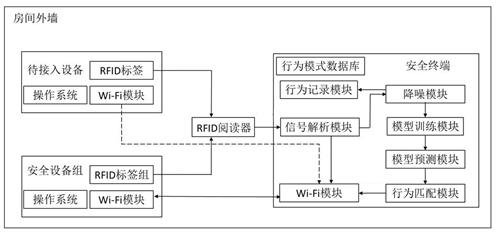
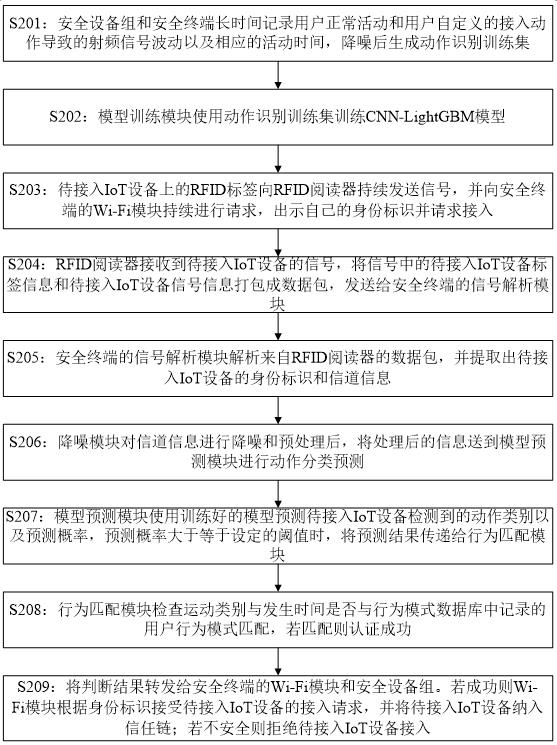
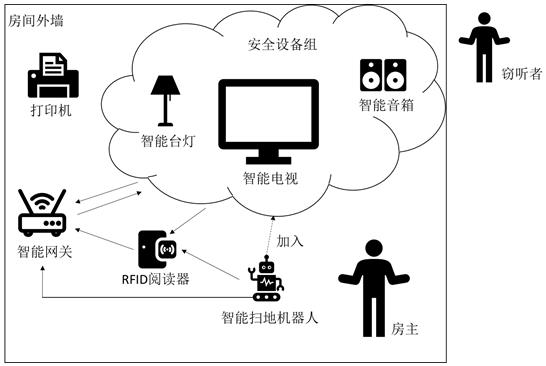
IoT equipment security access method and system based on RFID signal
ActiveCN113993134ALightweight data processingPrevent malicious devices from randomly accessing the security domainNetwork topologiesCo-operative working arrangementsReal-time computingEquipment Safety
The invention relates to an IoT equipment security access method based on an RFID signal. The method comprises the following steps that the change of the RFID signal caused after a user makes an action in a mode database iscollected; corresponding RFID features are extracted to construct an action recognition training set; the CNN-LightGBM model is constructed and trained; after an RFID signal sent by the IoT equipment to be accessed is received, corresponding RFID features are extracted; the extracted RFID features are input into a CNN-LightGBM model; the CNN-LightGBM model outputs an action category and a prediction probability; whether the output action type and the time for receiving the RFID signal sent by the IoT equipment to be accessed are matched with the action and the corresponding time period in the behavior mode database or not is judged, and if so, the access request of the IoT equipment to be accessed is permitted; or otherwise, the access request of the IoT equipment to be accessed is refused.
Owner:广州优刻谷科技有限公司
A two-way anonymous authentication system and method based on the principle of mimic defense
ActiveCN111741008BEnsure access securityEnsure safetyUser identity/authority verificationThe InternetHigh availability
The invention discloses a bidirectional anonymous authentication system and method based on a mimicry defense principle, and is applied to the technical field of information security. The method comprises the steps that a certificate issuer is initialized; a Join sub-protocol runs between a platform and the certificate publisher; the platform operates a Sign sub-protocol between the TPM and the Host; and a signature detection party operates the Verify sub-protocol through a heterogeneous executive body. According to the invention, a DAA bidirectional anonymous authentication technology is adopted; a mimicry module is added in the signature detection party; while remote anonymous authentication of the underlying equipment accessing the Internet of Things network is realized, the endogenoussecurity function of the mimicry module can effectively resist any security threat implemented by using a known and unknown software and hardware vulnerability back door in a target system, so that the access security of the Internet of Things equipment is ensured at the technical architecture level, the three-in-one attribute of high reliability, high credibility and high availability is achieved, and the security of the Internet of Things system is ensured.
Owner:NANJING REDMATRIX NETWORK SECURITY TECH R & D INST
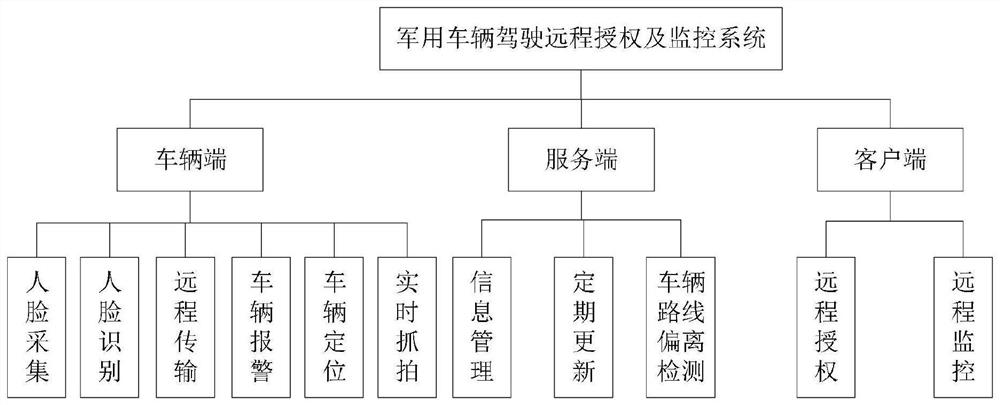
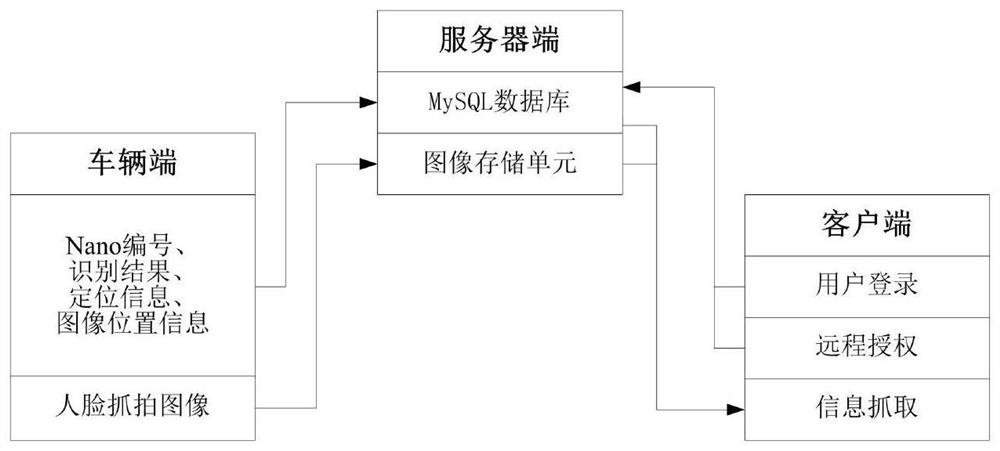
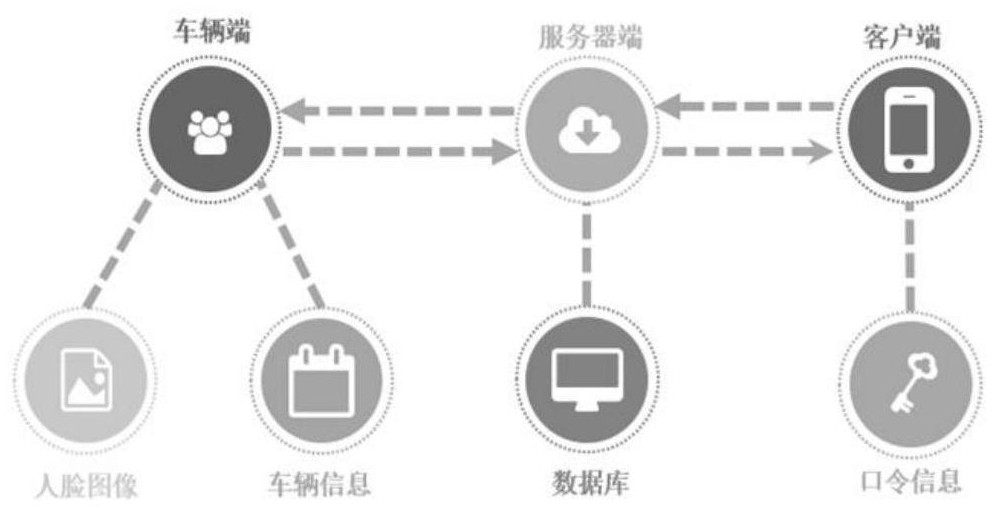
Military vehicle driving remote authorization and monitoring system
InactiveCN112565352AReal-time driving situationGuaranteed multiple usesRoad vehicles traffic controlTransmissionDriver/operatorVehicle driving
The invention discloses a military vehicle driving remote authorization and monitoring system, and the system adopts a face recognition technology, a network technology and a remote connection authorization technology and consists of a vehicle end, a server end and a client end. The vehicle end is used for carrying out driver face acquisition, face recognition, real-time snapshot, vehicle positioning and vehicle alarm, and remotely transmitting related information to the server end through an HTTP protocol. The server side is deployed in a cloud server, and the running software is a managementprogram established based on SpringBoot and is used for managing information of the vehicle side and the client side, summarizing data uploaded by the vehicle side, establishing a data bridge betweenthe vehicle side and the client side and carrying out vehicle route deviation detection. And the client is deployed at a mobile intelligent terminal and is used for carrying out remote authorization,remote monitoring and the like. The system can achieve the automatic management of the vehicle, thereby preventing the improper use of the vehicle, and guaranteeing the management safety of the vehicle.
Owner:NAVAL AVIATION UNIV
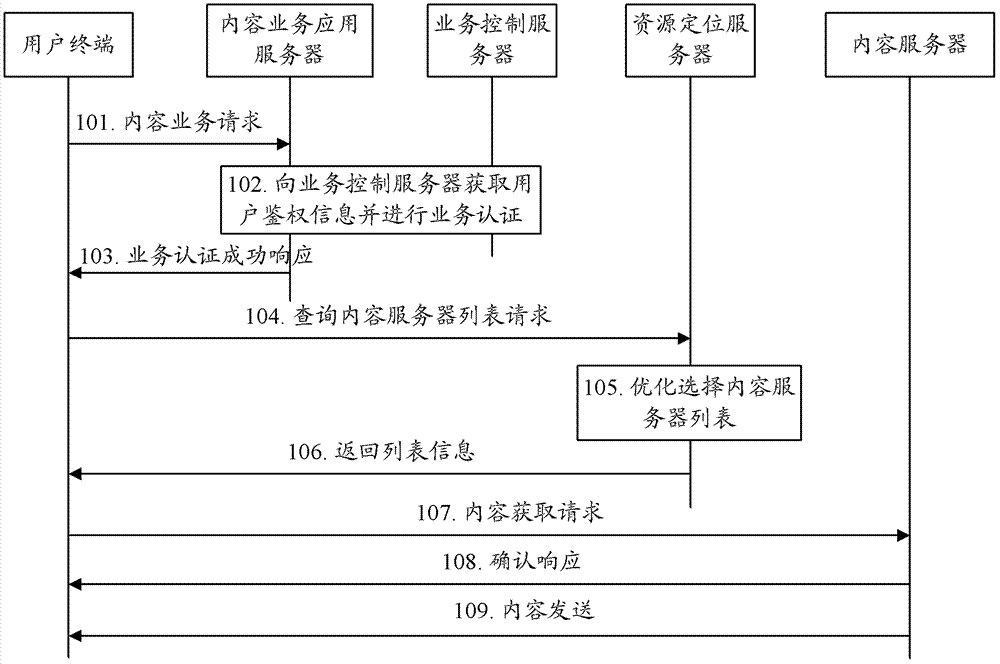
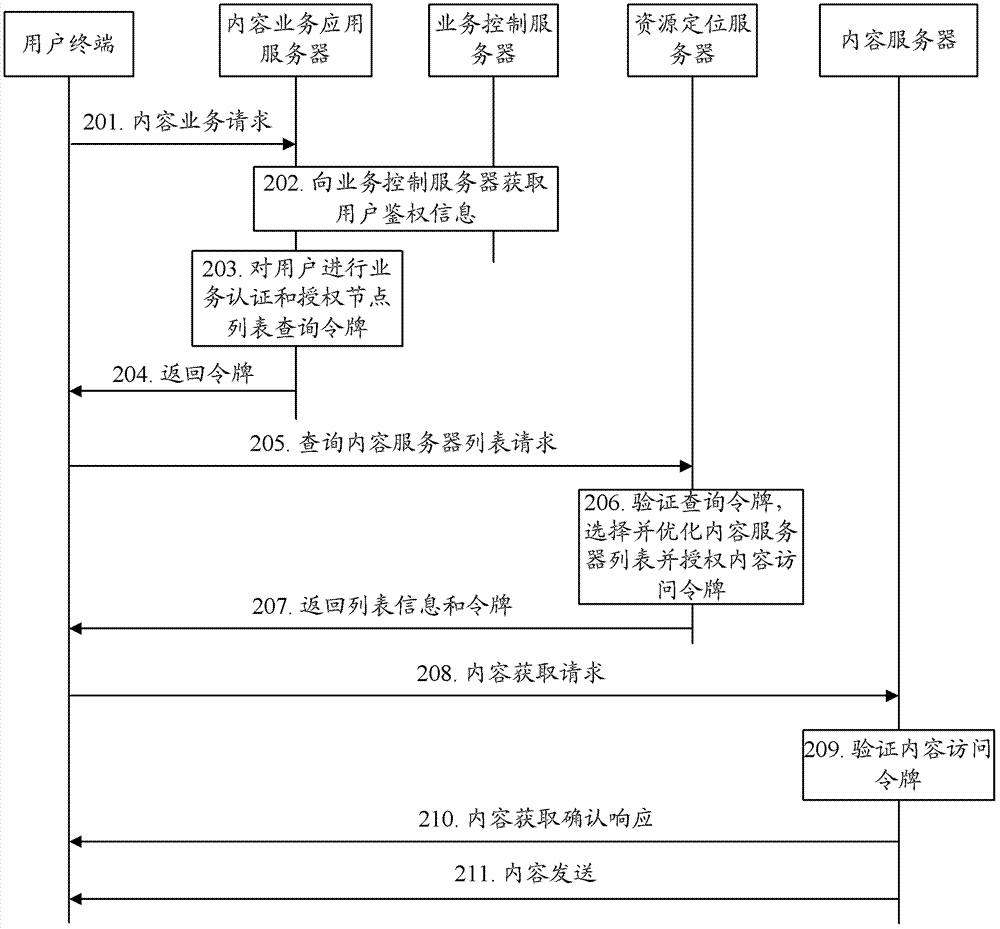
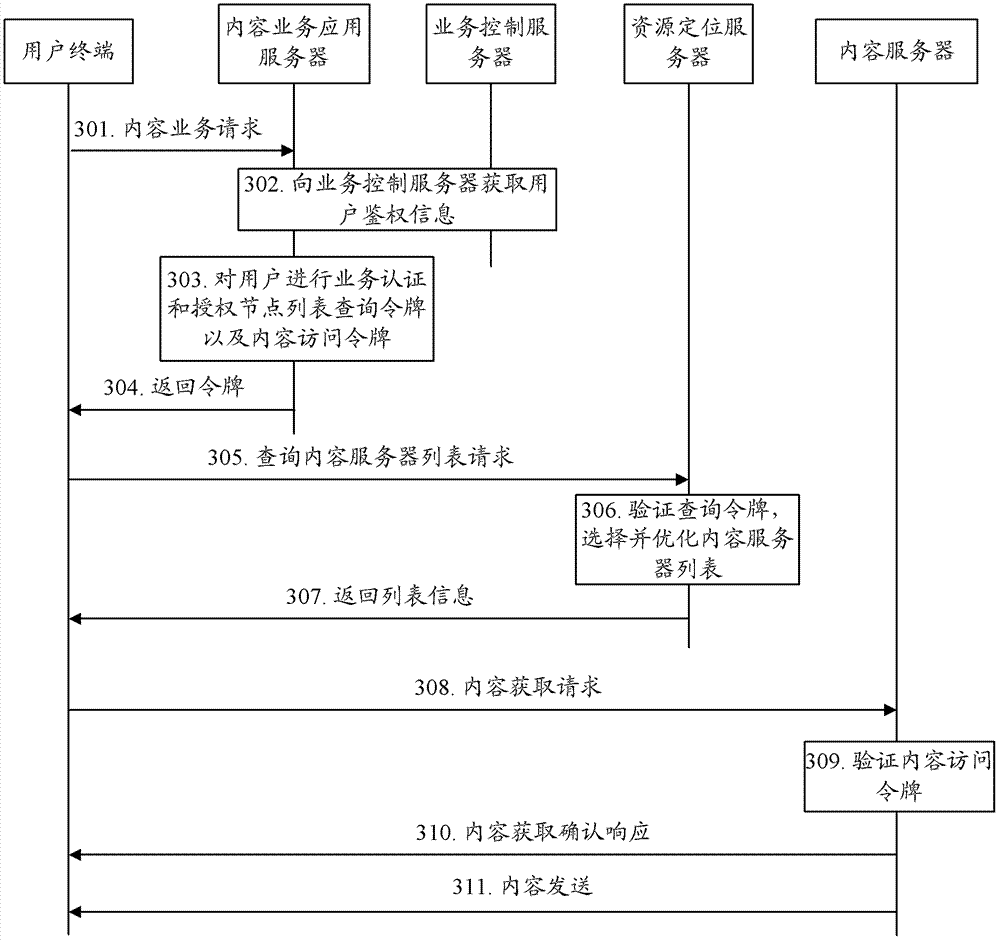
A method and system for realizing DSN content service access security
The invention discloses a method and a system for realizing DSN content service access security, which can both authorize a content server list query token token and a content access token for a user terminal, and when a user terminal queries a content server, query the content server list The token is verified, and after the verification is passed, the user terminal is allowed to access the resources on the content server; when the user terminal obtains the content from the content server, the content access token is verified, and the user terminal is allowed to obtain the content resources after the verification is passed. The method and system of the present invention can perform two-level verification (including the previous query token verification and the subsequent content access token verification) for the user terminal, and provide content resources to the user terminal after the second-level verification is finally passed, so it can Ensure access security of content services.
Owner:ZTE CORP
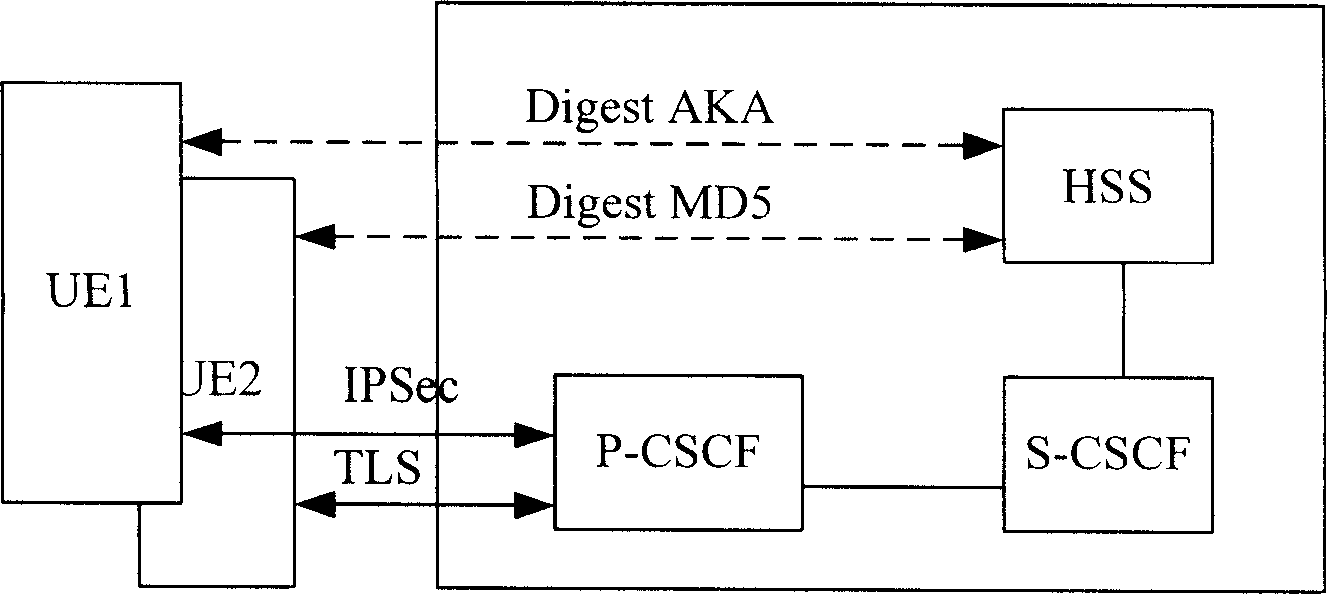
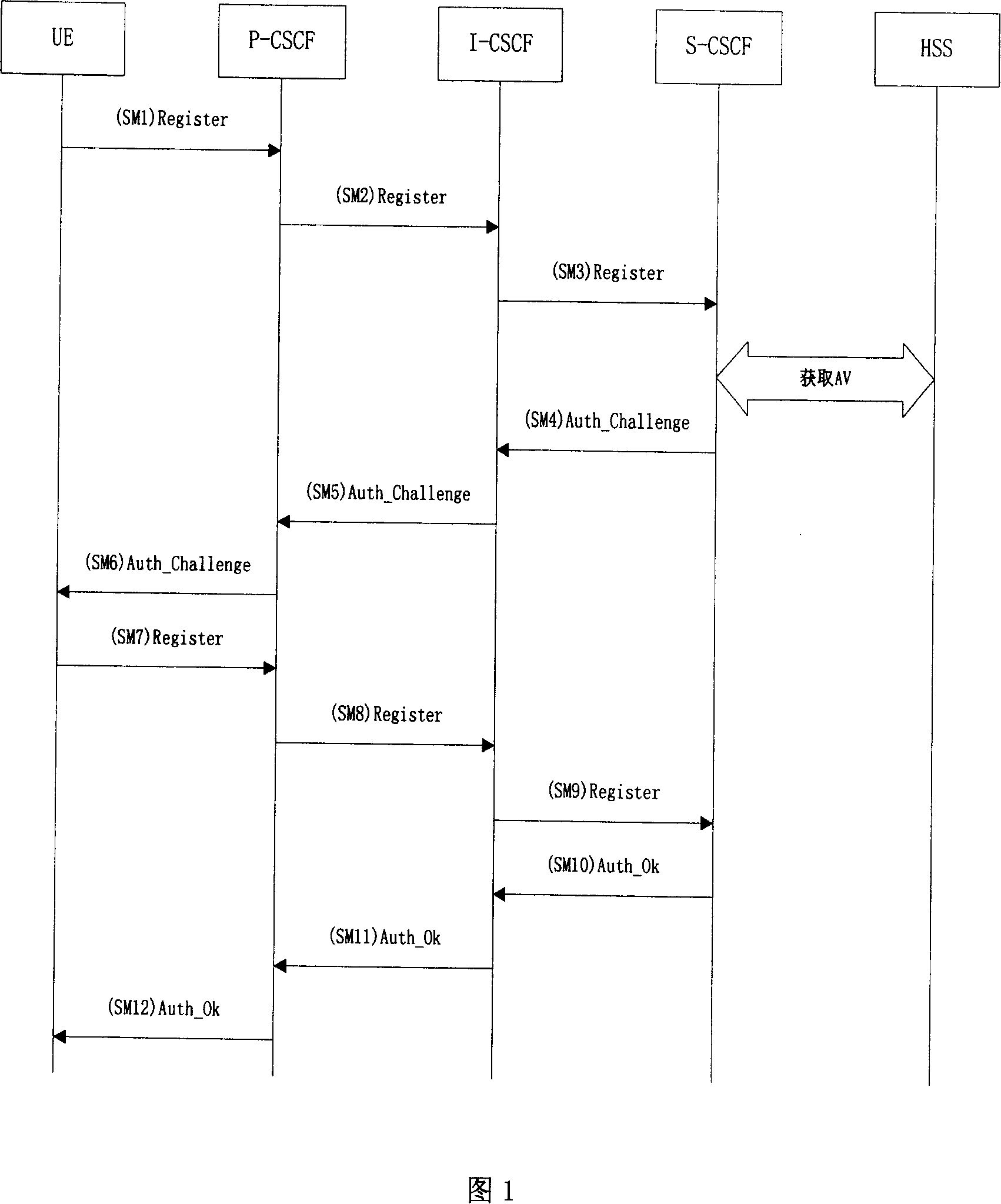
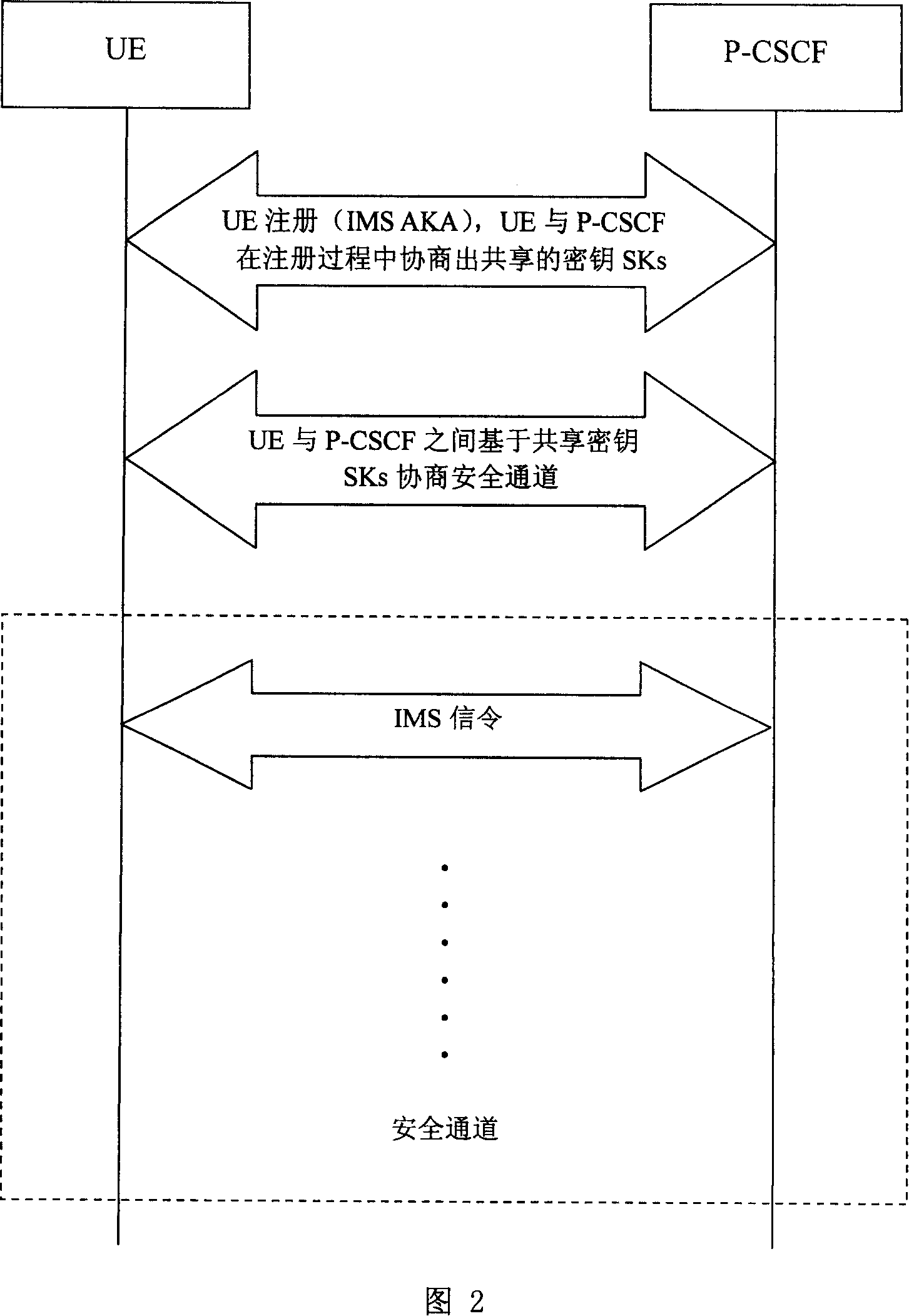
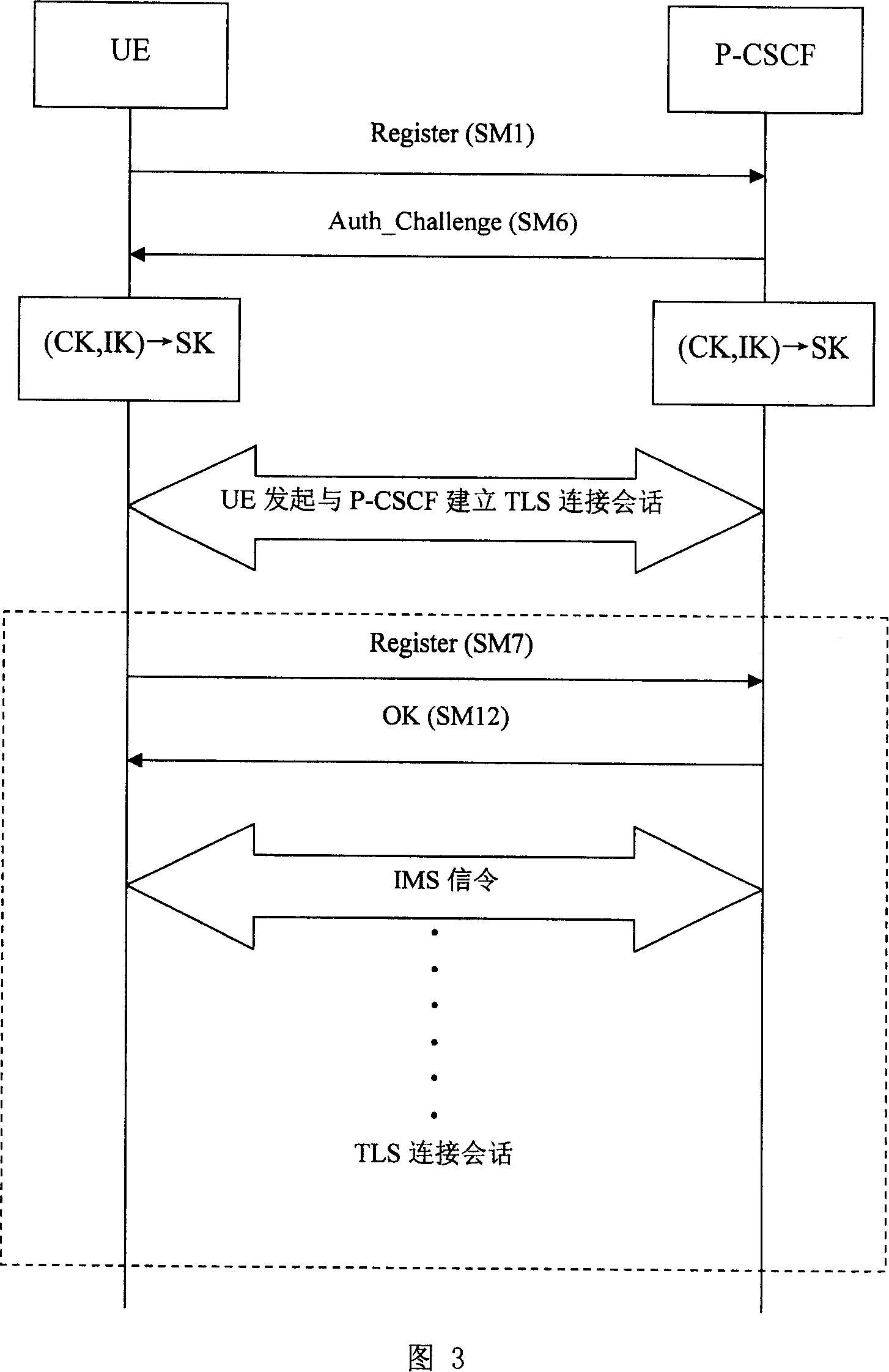
A protection method for access security of IP multimedia subsystem
ActiveCN100369430CEnsure access securityGuaranteed PenetrationSynchronising transmission/receiving encryption devicesData switching by path configurationMan-in-the-middle attackSafety Communications
This invention discloses a method for protecting the switch-in safety of the IP multimedia subsystem, characterized in that the UE and P-CSCF will negotiate a sharing code when the UE registering, setting up a safety communication channel based on the sharing code, making the IMS message transmitting between UE and P-CSCF safety, and the protected IMS message will penetrate the NAT transparently. The method combines the UE' registering process, safety channel negotiating process and the data coding process together, making sure the two-way identification between UE and P-CSCF; besides, the method also prevent the attacker attacking the go-between.
Owner:ZTE CORP
A method and system for securely accessing IoT devices based on RFID signals
ActiveCN113993134BLightweight data processingAvoid random accessNetwork topologiesCo-operative working arrangementsAccess methodPrediction probability
The present invention relates to a secure access method for IoT devices based on RFID signals, comprising: collecting changes in RFID signals caused by users taking actions in the pattern database; extracting corresponding RFID features to construct an action recognition training set; constructing And train the CNN-LightGBM model; after receiving the RFID signal sent by the IoT device to be connected, extract the corresponding RFID feature; input the extracted RFID feature into the CNN-LightGBM model; the CNN-LightGBM model outputs the action category and prediction Probability; judge whether the output action category and the time of receiving the RFID signal sent by the IoT device to be connected match the action in the behavior pattern database and the corresponding time period, and if so, agree to the access request of the IoT device to be connected; otherwise reject the pending connection Access requests from IoT devices.
Owner:广州优刻谷科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com