Method for selecting safety mechanism of IP multimedia subsystem acess field
A technology of multimedia subsystem and security mechanism, applied in the field of communication, can solve the problems of poor scalability and flexibility of security mechanism, and achieve the effect of satisfying security requirements and strong scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
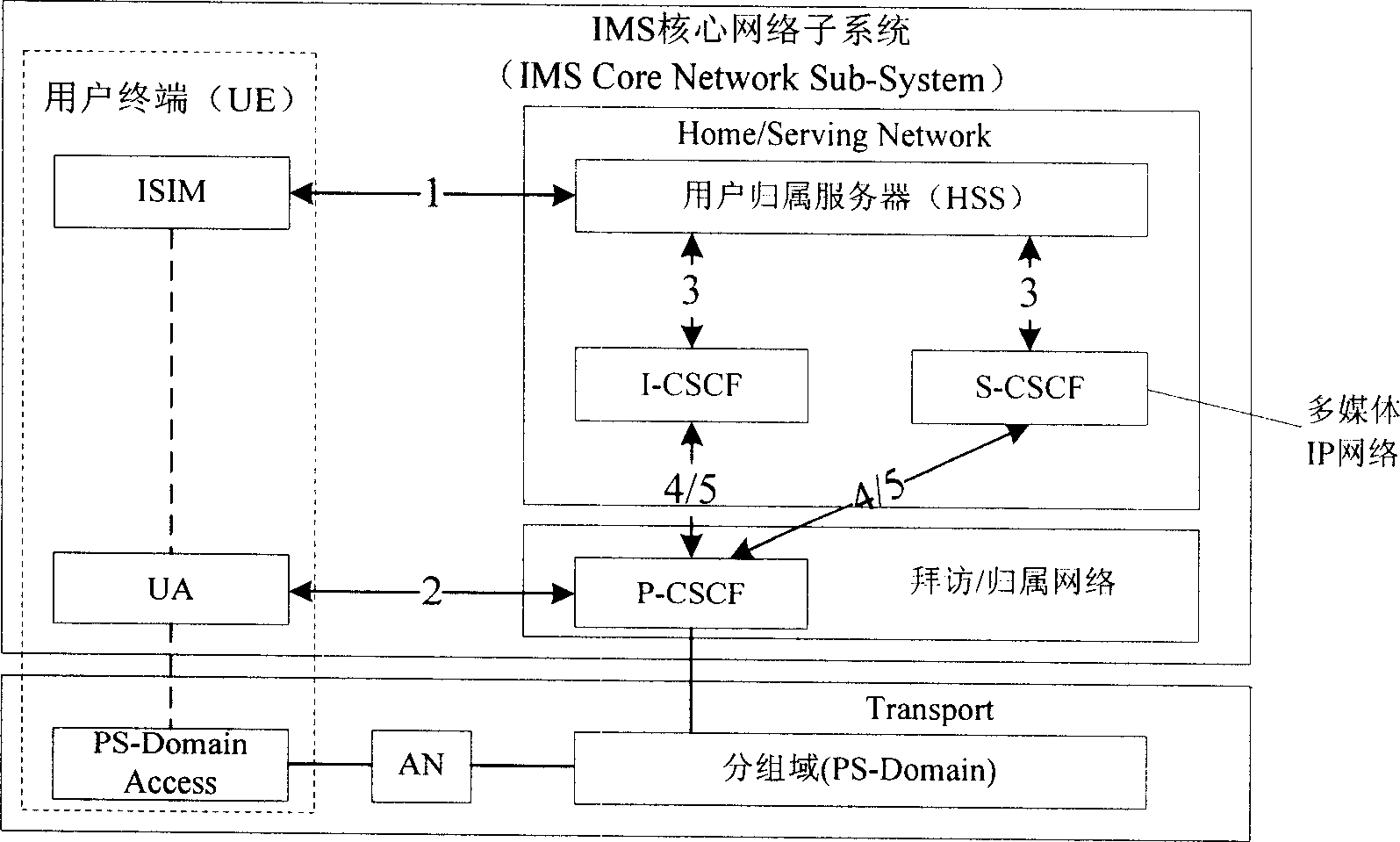
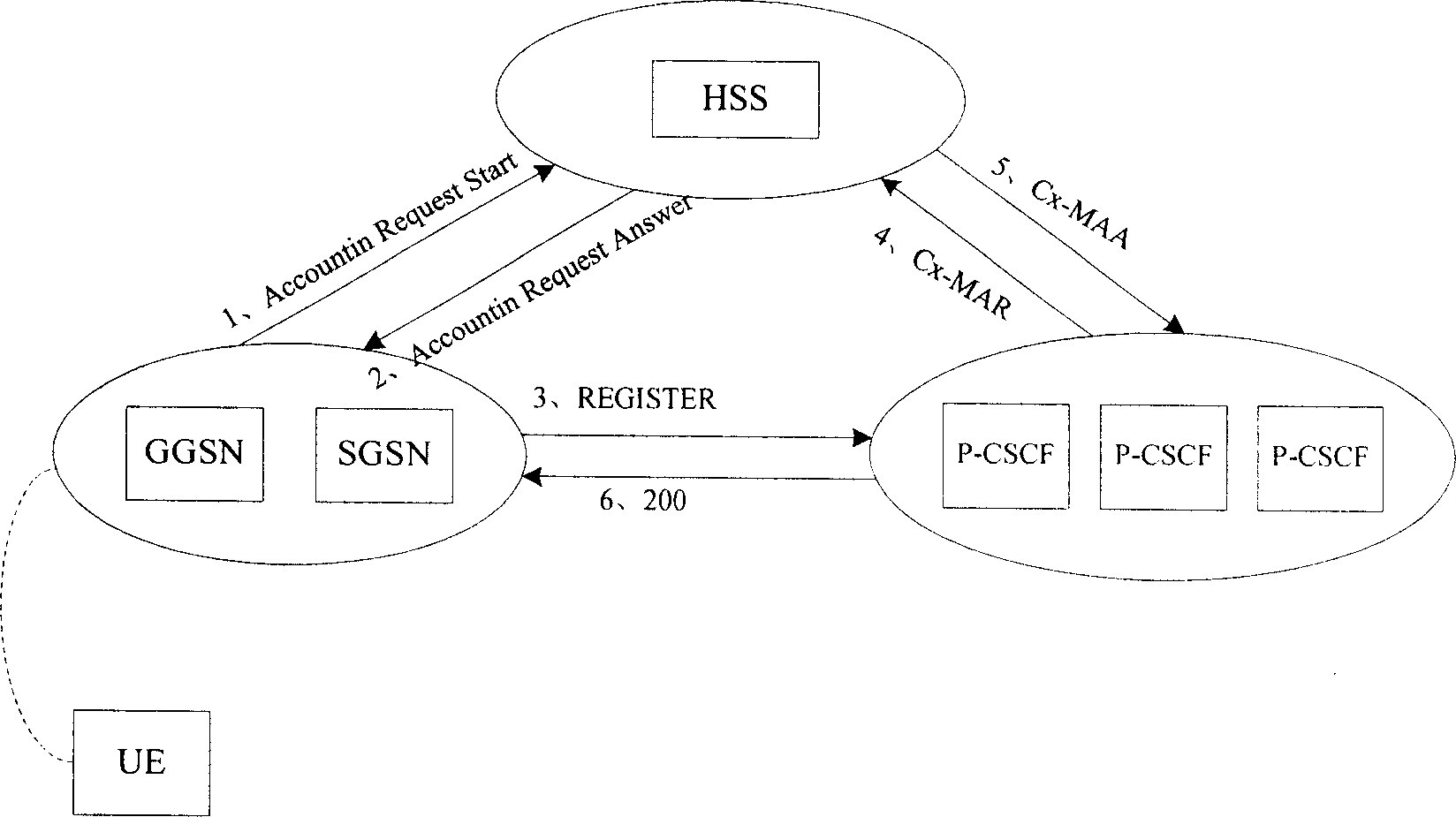
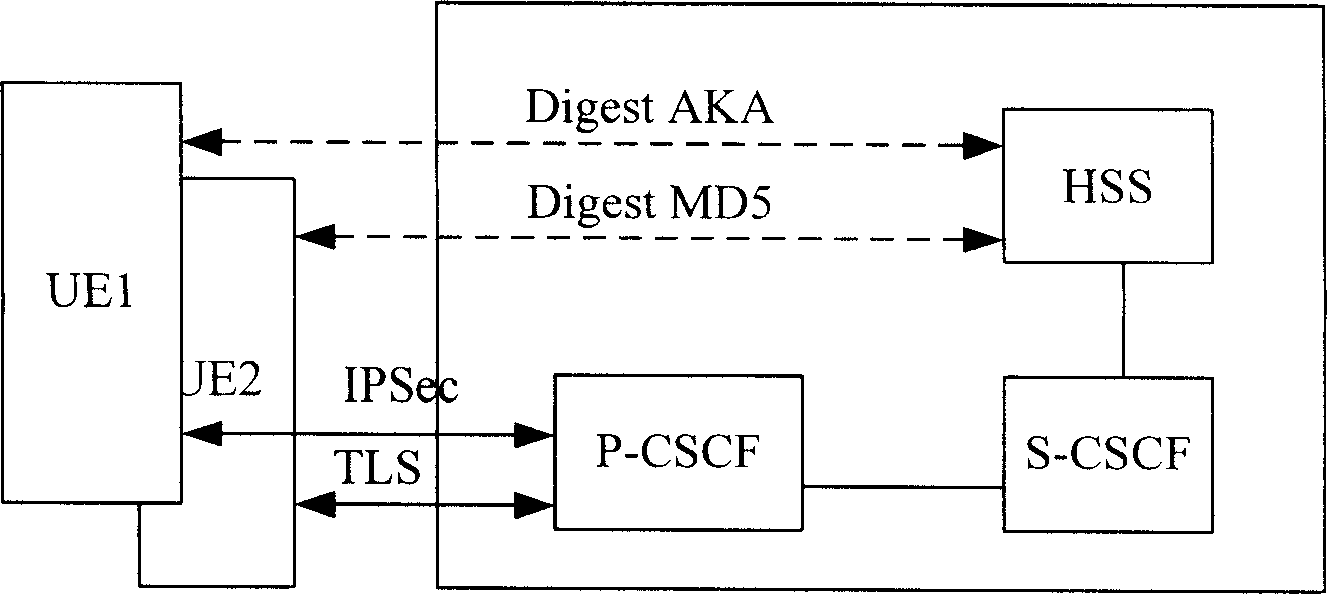
[0036] In order to improve the scalability and flexibility of the IMS access domain security mechanism and meet different security requirements, the present invention configures one or more access domain security mechanisms on the network equipment of the IMS network, and according to the user's request message, Select to determine the access domain security mechanism used.
[0037] The network devices in the IMS network simultaneously support the implementation of multiple access domain security mechanisms, such as Figure 3A shown. The access domain security mechanism includes authentication methods adopted for users (such as Figure 3A Digest AKA, DigestMD5, etc.) and the type of secure channel that needs to be established between the user terminal and the Proxy-Call Session Control Function (P-CSCF) entity in the IMS network (such as Figure 3A IPSec in , TLS, etc.). One or more authentication methods and one or more security channel types can be configured on the HSS f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com