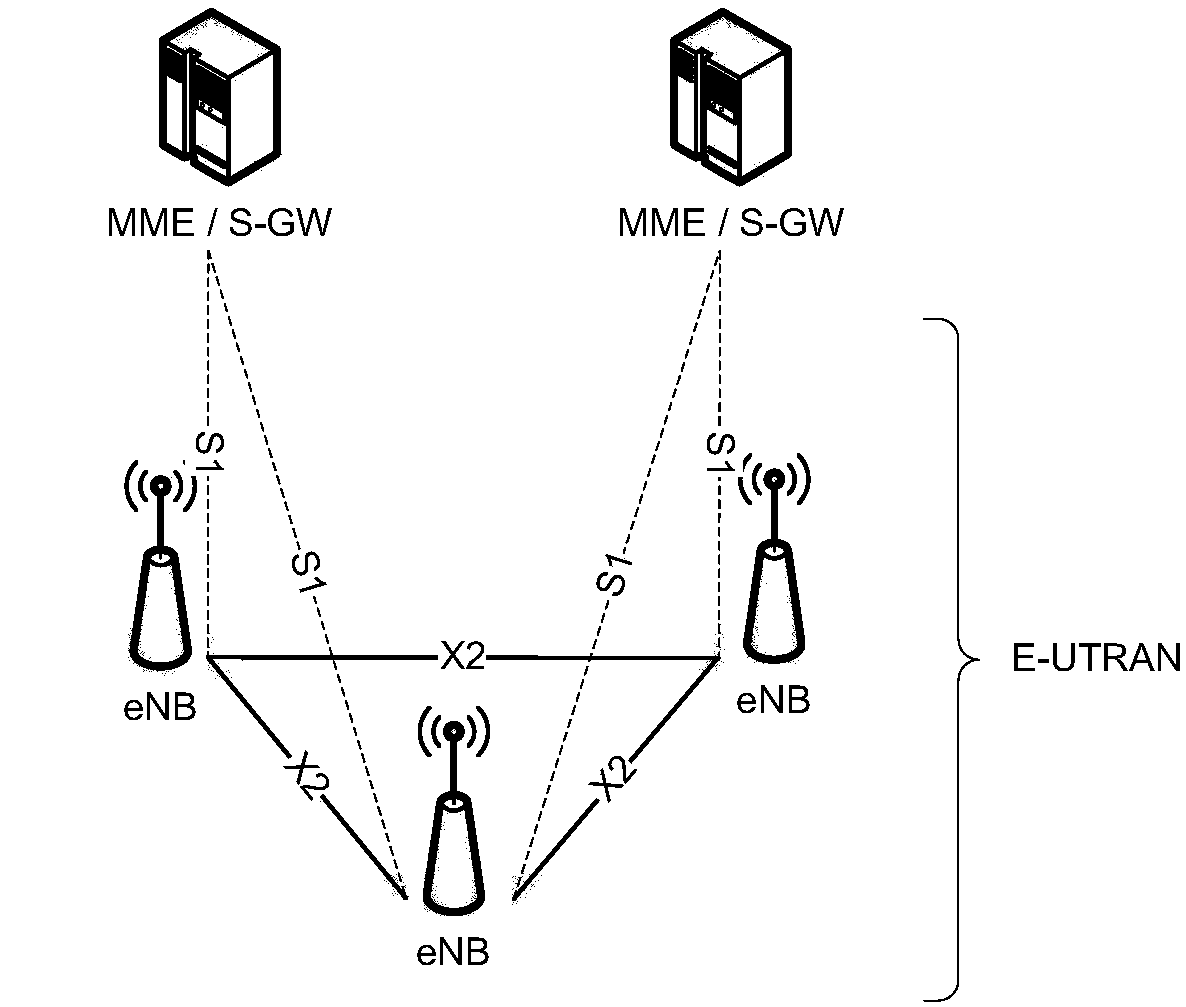
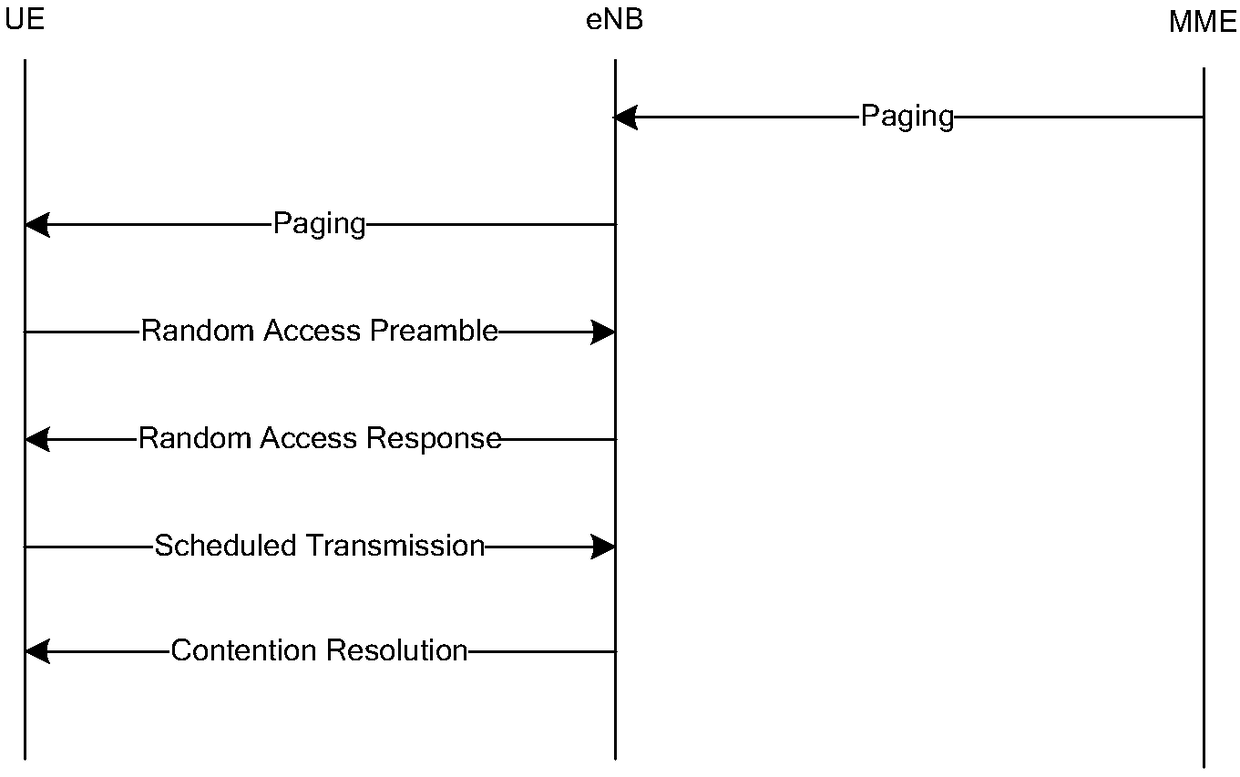
Patents
Literature
112results about How to "Avoid random access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for random access process in mobile communication system
InactiveUS20100214984A1Avoid random accessEnergy efficient ICTError prevention/detection by using return channelTelecommunicationsMobile communication systems
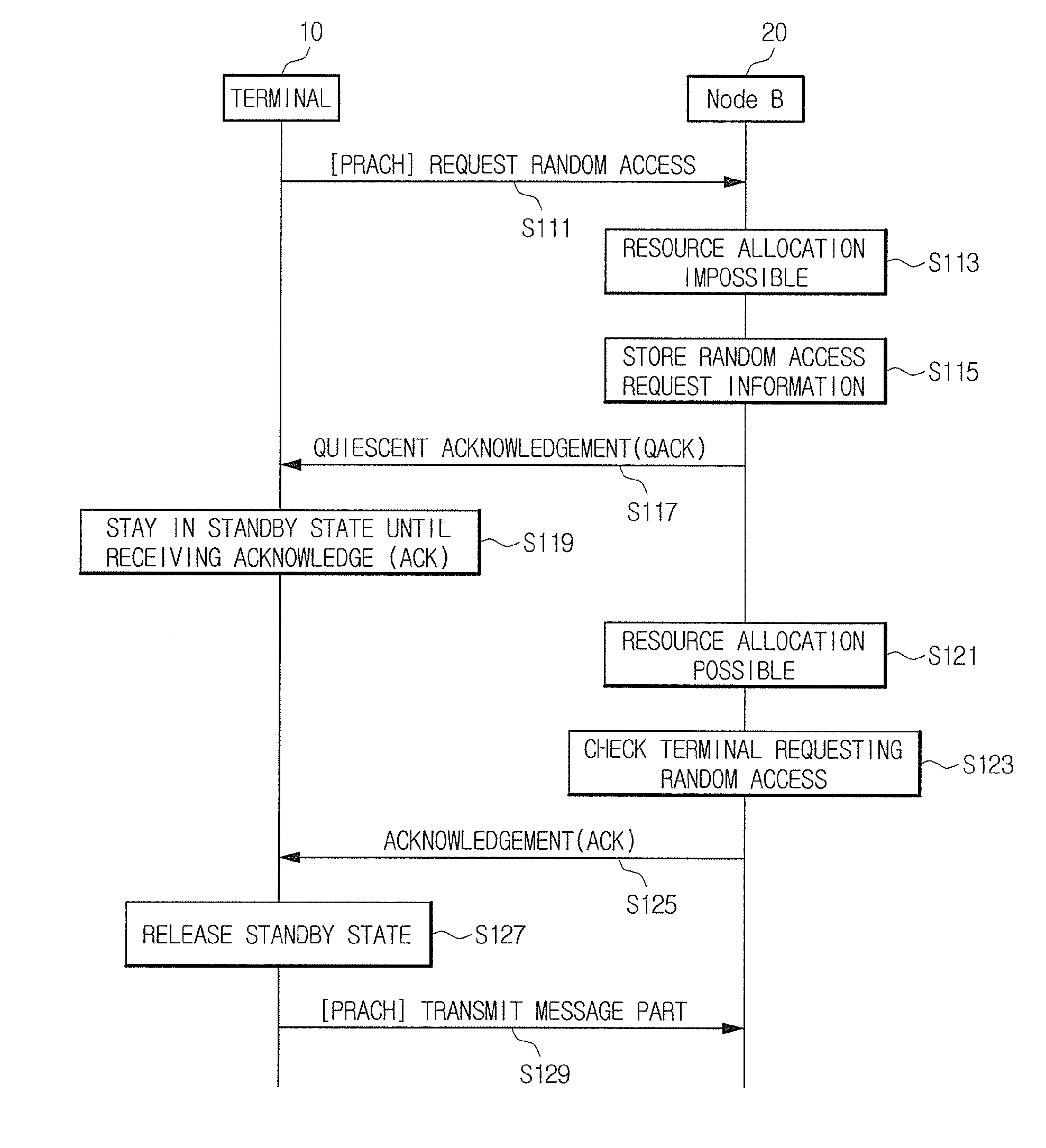
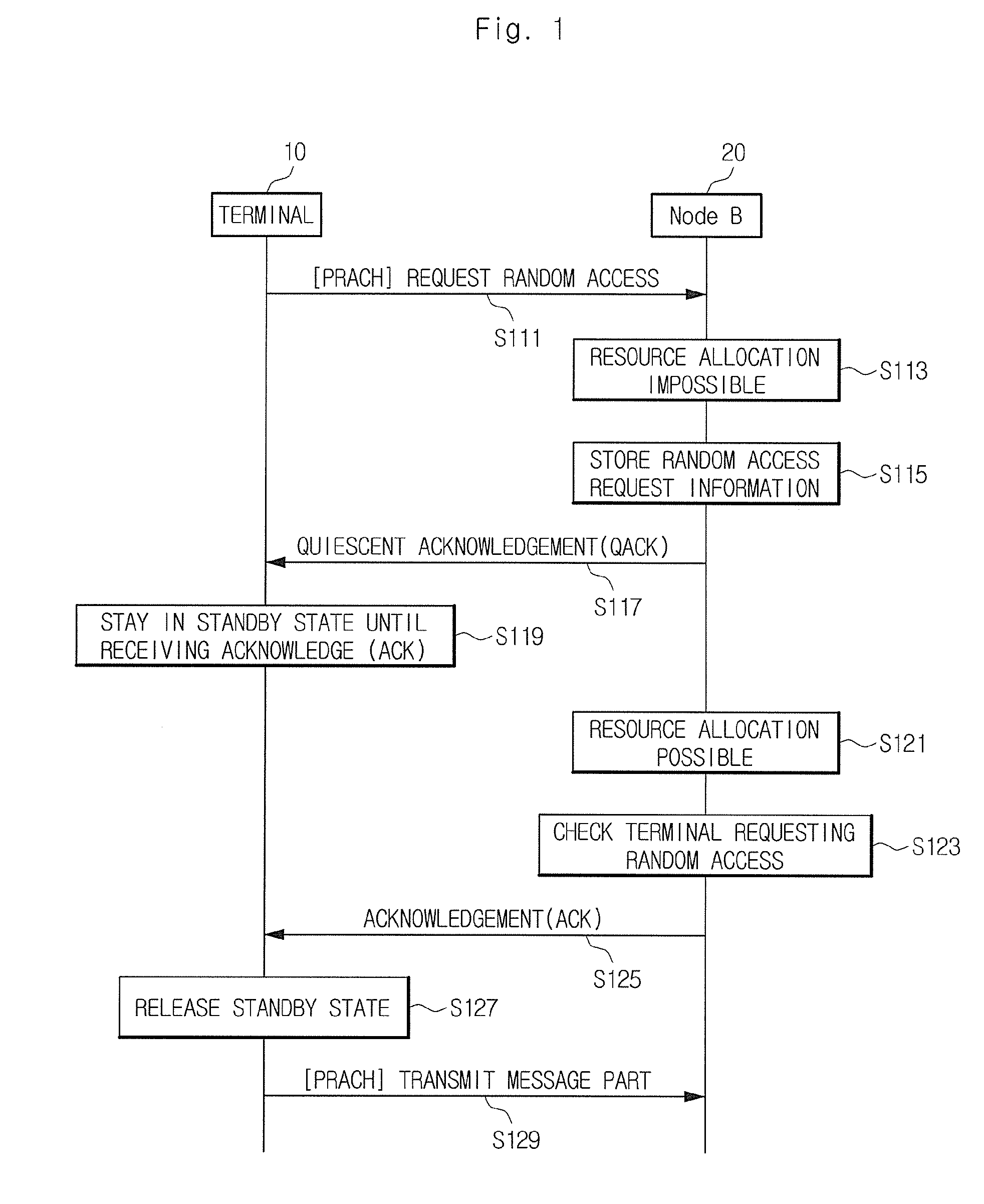
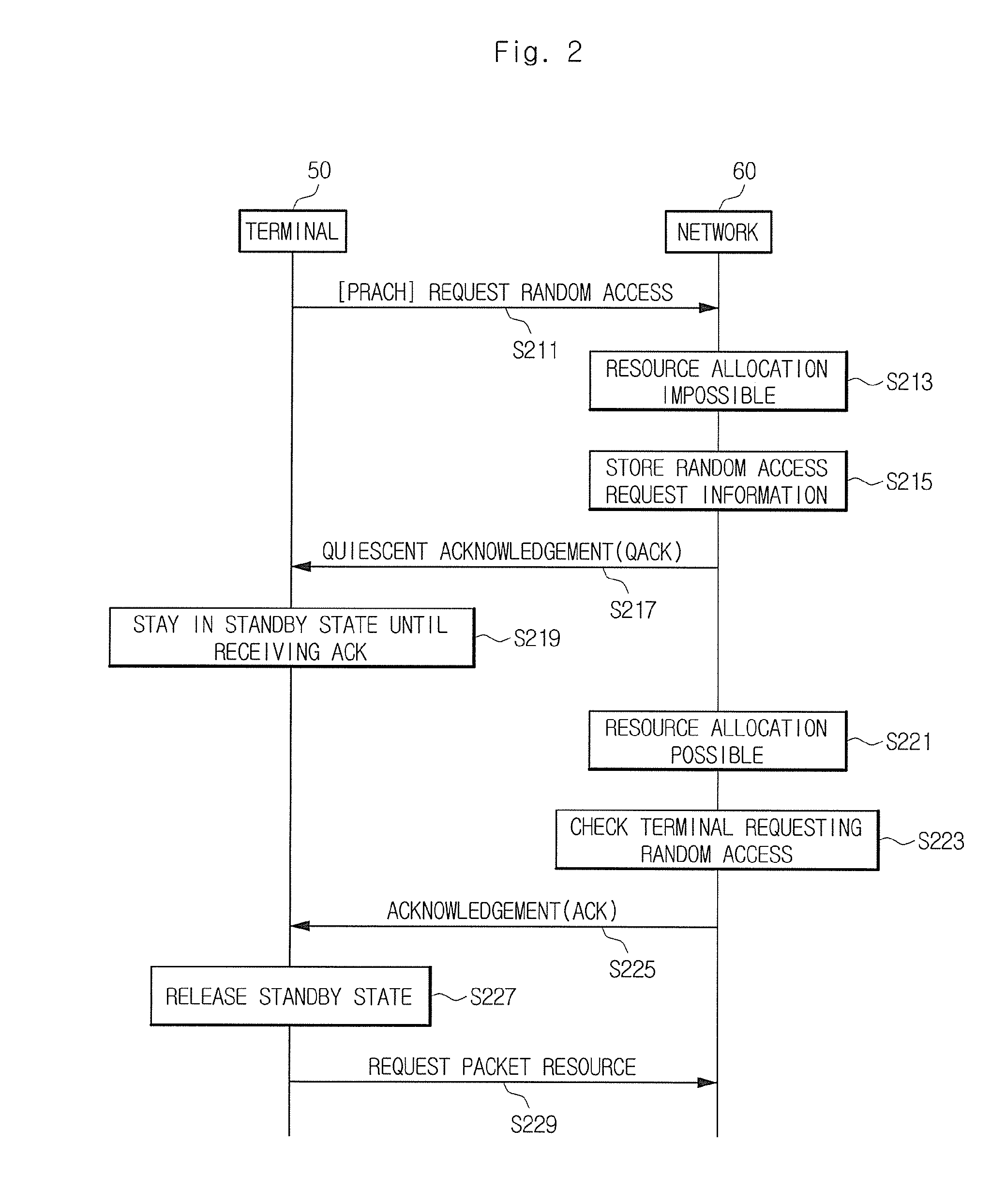
The present invention relates to a method for a random access process in a mobile communication system. According to the exemplary embodiments, in the case where a mobile terminal requests a random access to a network, when the network is not able to promptly allocate a resource for the random access to the mobile terminal due to an insufficient resource, the mobile terminal is maintained in a standby state without repeatedly requesting the random access to the network. Accordingly, it is possible to reduce the uplink signal interference caused by the repeated random access request, reduce the possibility of communication contention between the mobile terminals for the access to the mobile communication system, and reduce the power consumption of the mobile terminal.
Owner:PANTECH CO LTD
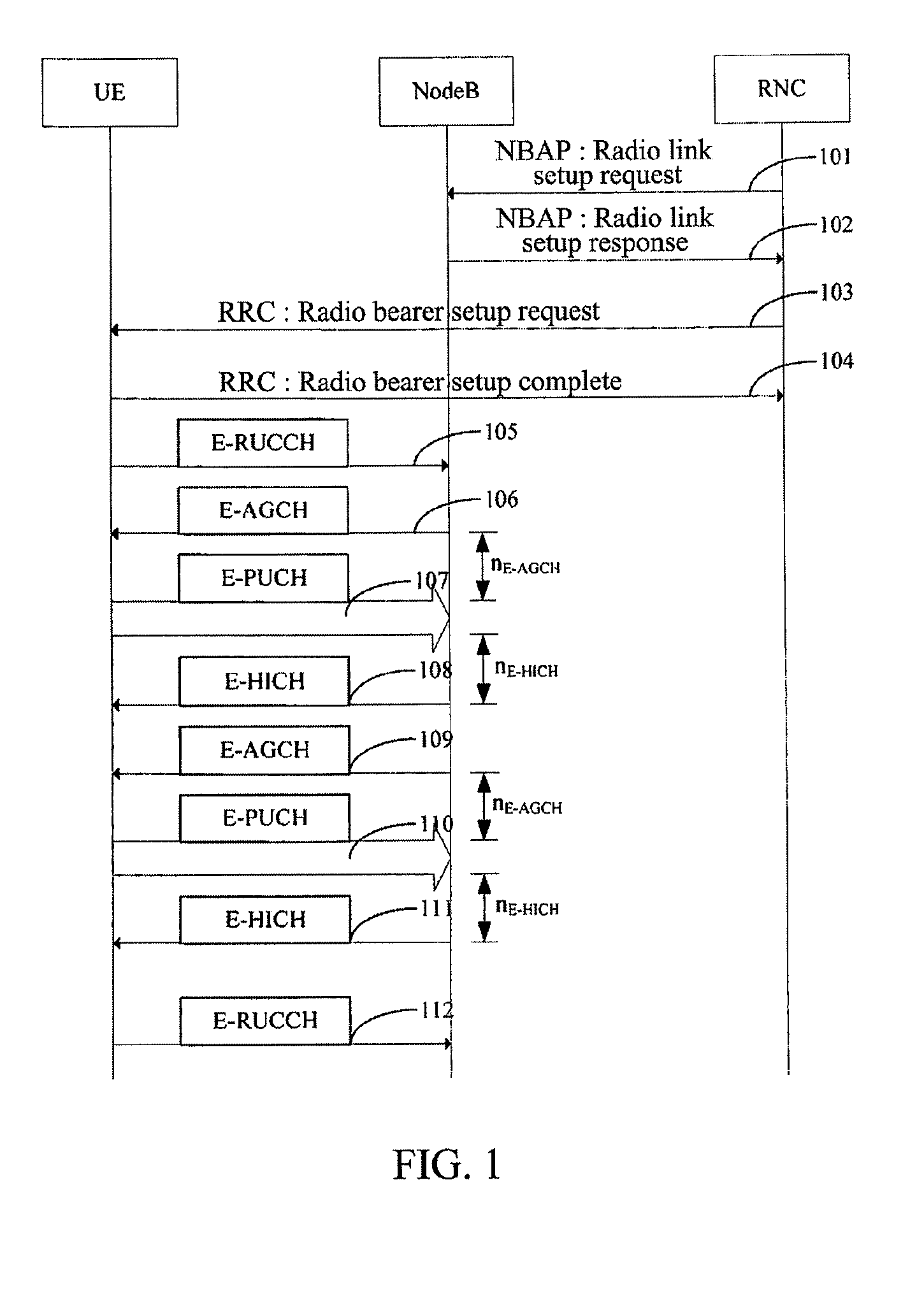
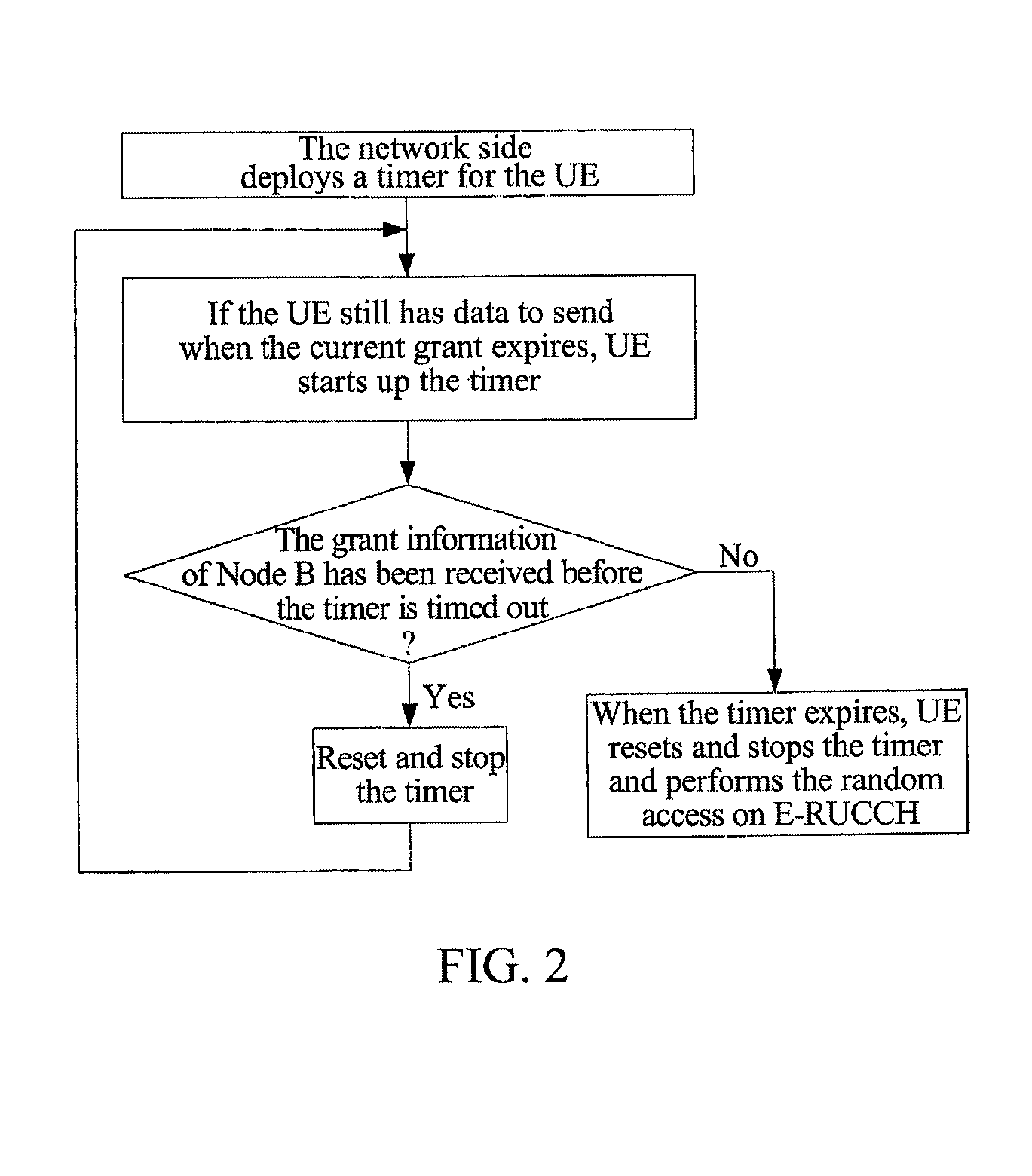
TD-SCDMA System and a Method for Controlling HSUPA Random Access Thereof
InactiveUS20100165953A1Avoiding invalid random accessImprove system efficiencyNetwork traffic/resource managementRadio transmissionTime delaysDelayed time
The present invention provides a time division synchronous code division multiple access (TD-SCDMA) system for controlling enhanced uplink random access, including user equipment (UE), node B and serving radio network controller. The present invention also provides a method for controlling the enhanced uplink random access in a time division synchronous code division multiple access system, including: in high speed uplink packet access scheduling service of time division synchronous code division multiple access system, the higher layer of network side deploys a timer at the user equipment side; if the user equipment still needs to transmit data when the current available grant expires, it starts up the timer which is used as the delay time of initiating the enhanced uplink random access. According to the ability of the network side in controlling E-DCH resources, the present invention can be used to control the time delay that UE initiates the enhanced uplink random access after one grant expires, so as to avoid invalid random access; meanwhile the present invention provides a reliable mechanism for the enhanced uplink random access. By using the method of this invention, system resources can be reasonably utilized, thereby greatly improving the system efficiency.
Owner:ZTE CORP
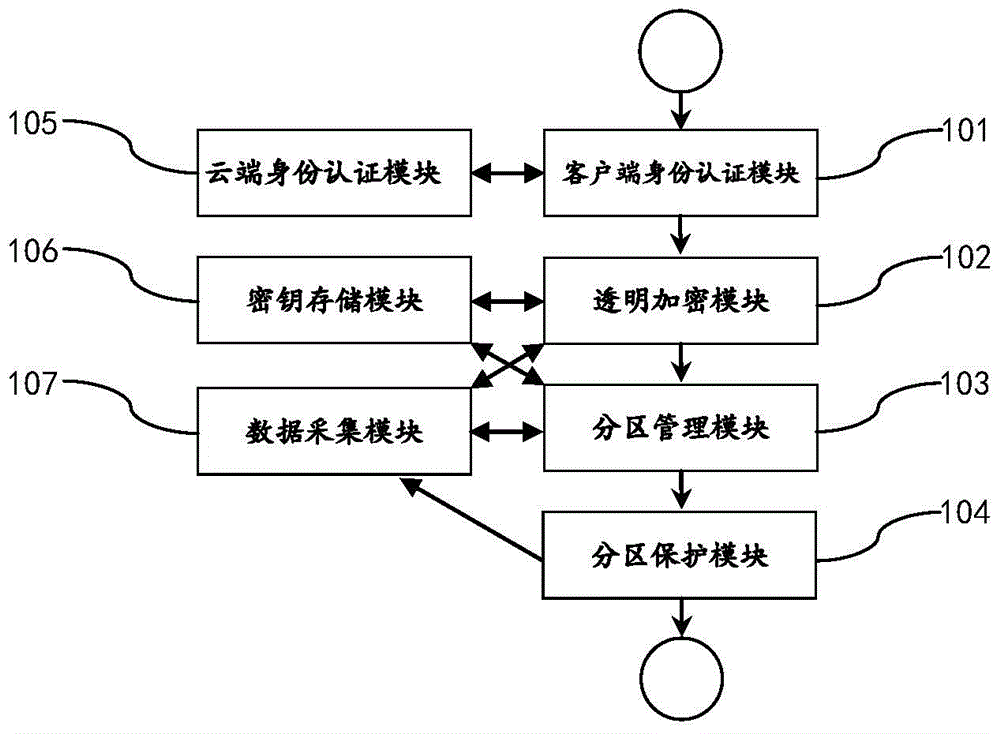
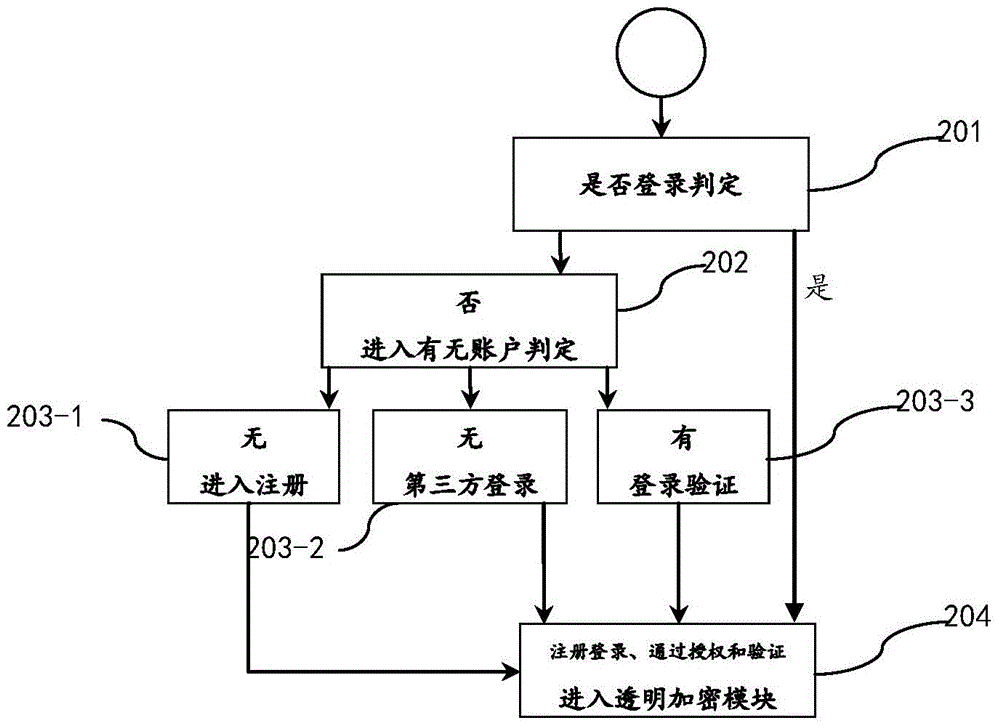
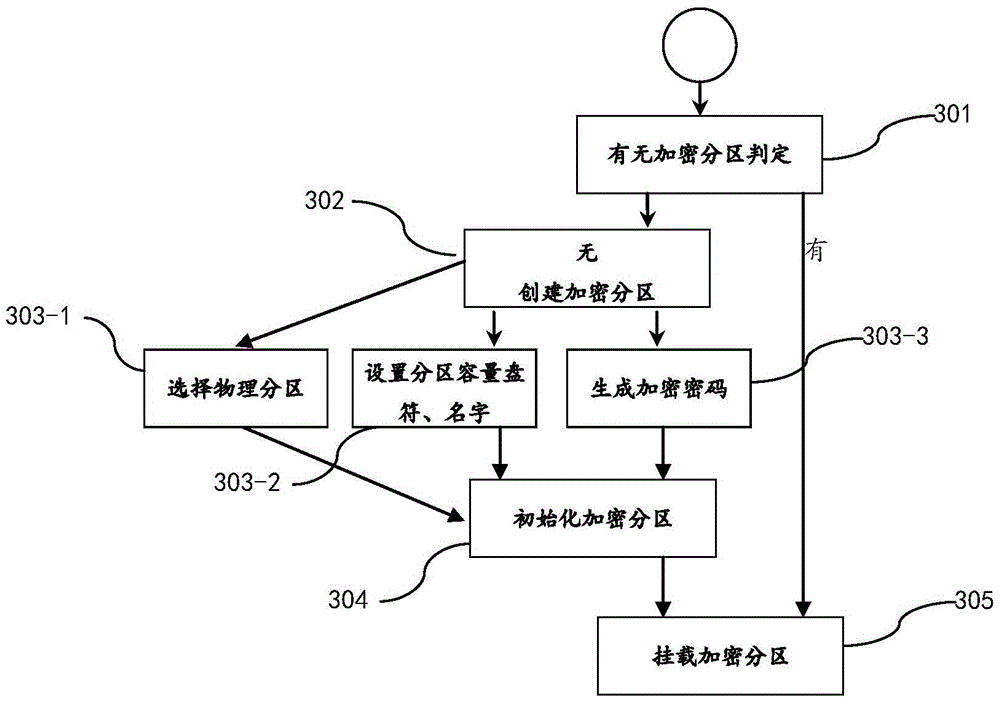
Method and apparatus for performing electronic data file protection based on encrypted partition
The present invention discloses a method and an apparatus for performing electronic data file protection based on an encrypted partition, and belongs to the field of electronic data file protection. The apparatus disclosed by the present invention adopts an overall design of ''a cloud server+a client''. The cloud server comprises a data acquisition module, a key storage module and a cloud identity authentication module. The client comprises a client identity authentication module, a transparent encryption module, a partition management module and a partition protection module. According to the method and apparatus disclosed by the present invention, ''a cloud server+a client'' dynamic authentication and transparent encryption / decryption are combined, so that files and folders can be effectively prevented from being freely accessed, duplicated or deleted by others, and the security of privacy data is ensured.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
Data transmitting method and transmission resource allocating method and device
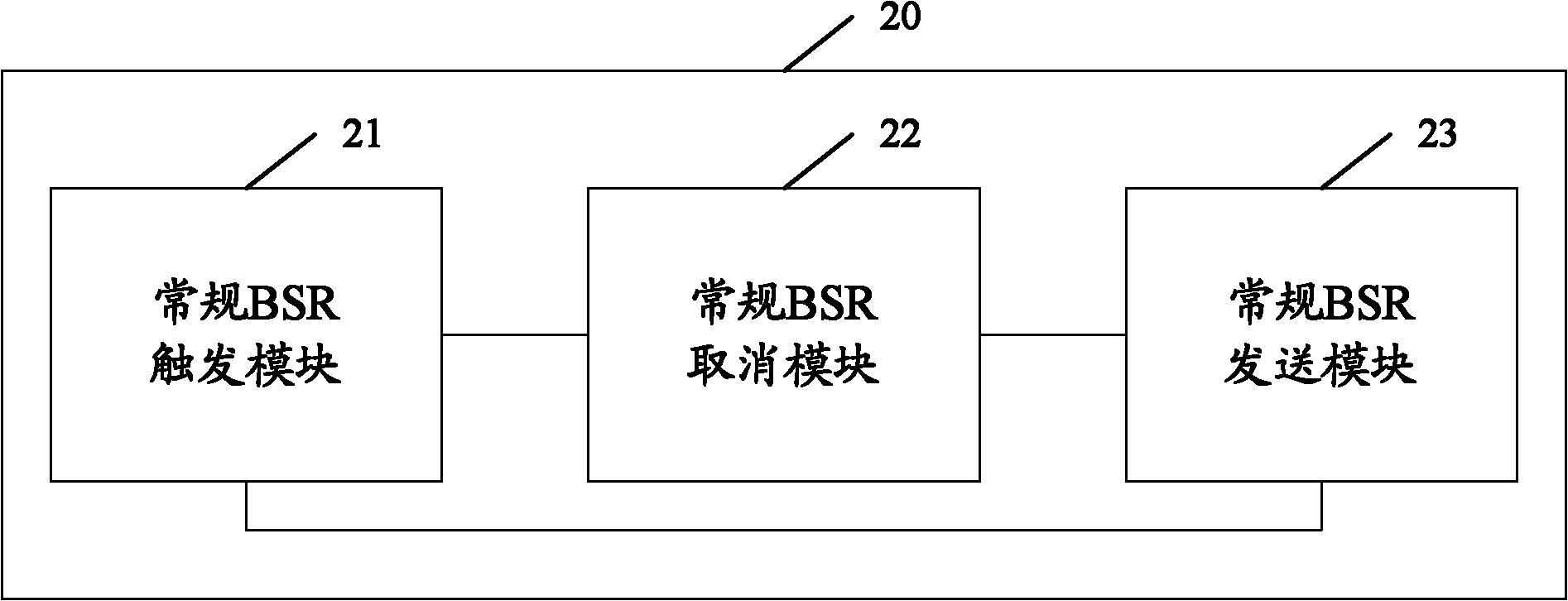
InactiveCN102761967AAvoid receivingAvoid processing powerWireless communicationTelecommunicationsUplink transmission
The invention discloses a transmitting method for a BSR (Buffer Status Report). The transmitting method comprises the following steps of: if an LCG (Logical Channel Group) logical channel meets trigger conditions of a conventional BSR, triggering a first conventional BSR; or if a BSR retransmission timer is overtime and transmittable data exist in the LCG logical channel, triggering a second conventional BSR; if the LCG logical channel triggering the first conventional BSR meets non-transmittable conditions, canceling the first conventional BSR; or if the second conventional BSR is triggered, all LCG logical channels meet the non-transmittable conditions, canceling the second conventional BSR; and if uplink transmission resources exist on the current TTI (Transmission Time Interval) and the first or second conventional BSR which is triggered and not canceled exist, transmitting a BSR MAC CE (Buffer Status Report Media Access Control Control Equipment) by using the uplink transmission resources. According to the transmitting method disclosed by the invention, the forming and reporting of the BSR MAC CE having no significance in the UE is avoided, and thus transmission resources are saved.
Owner:HUAWEI TECH CO LTD
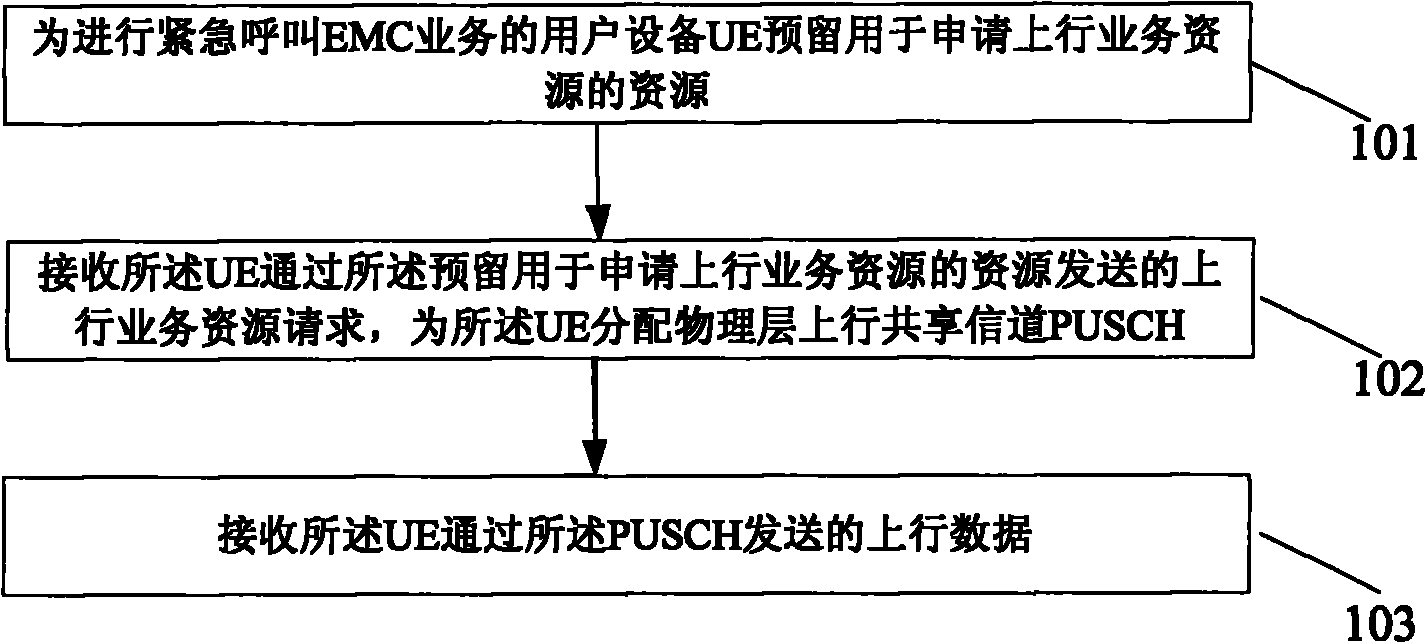
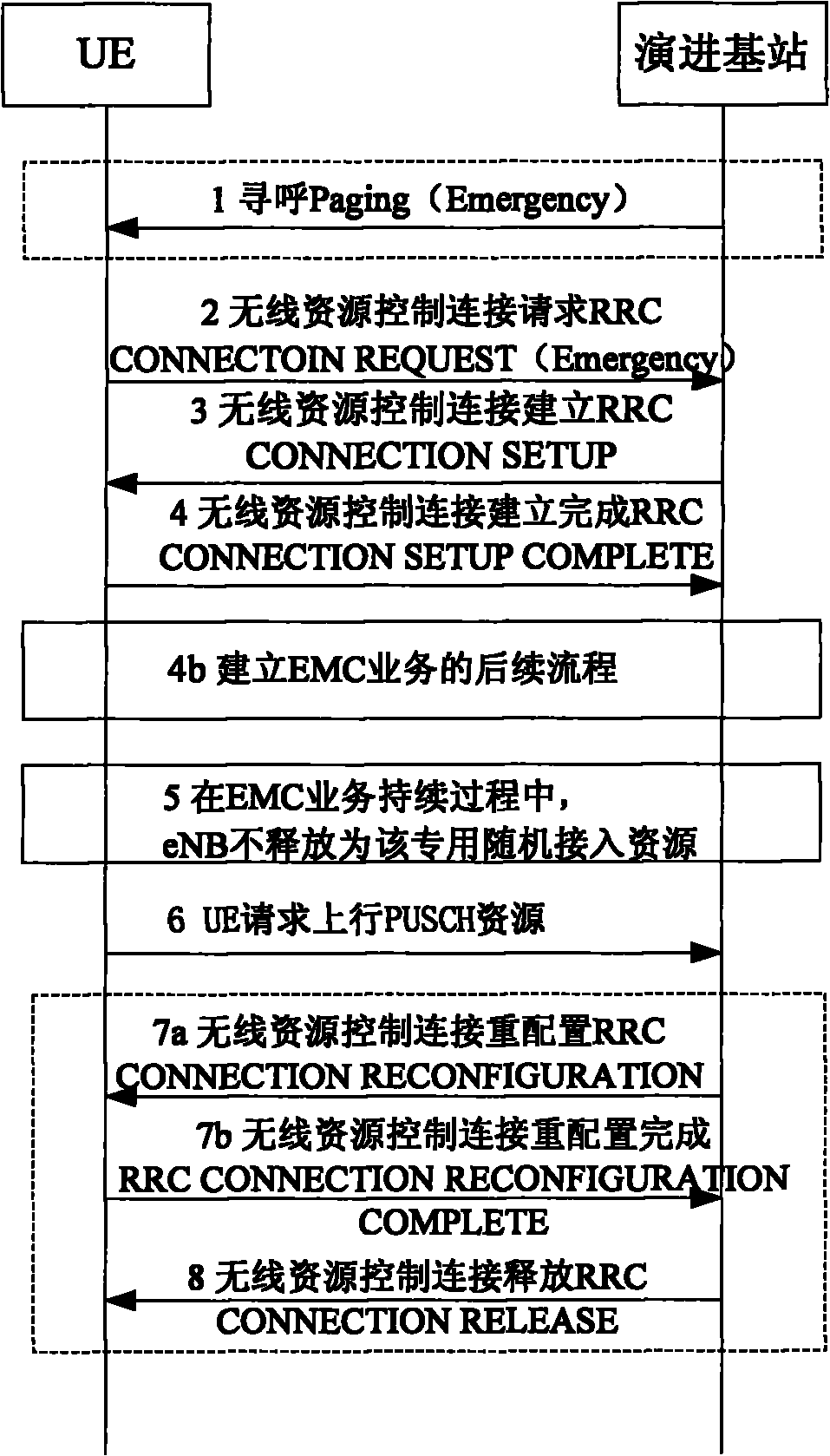
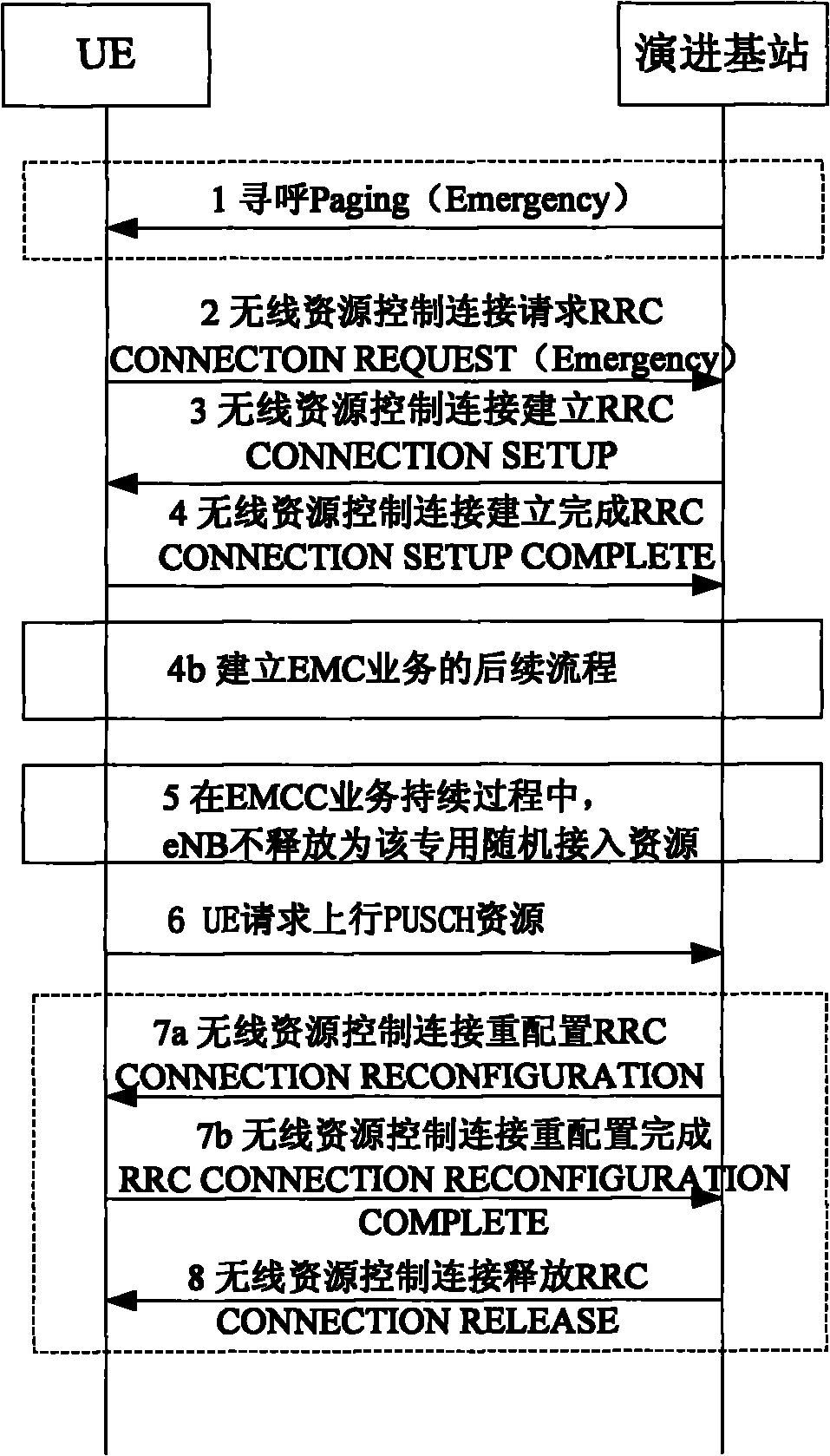
Method, evolution base station and system for emergency call service
InactiveCN101841791AGuaranteed Urgency RequirementsImprove business experienceWireless commuication servicesService resourceResource use
The invention discloses a method, an evolution base station and a system for an emergency call service, which solve the probably-occurred problem of resource scarcity in an emergency call. The method comprises the following steps of: reserving a resource, used for applying for an uplink service resource, for user equipment (UE) which performs the emergency call (EMC) service; receiving an uplink service resource request sent by the UE through the reserved resource used for applying for the uplink service resource, and allocating a physical layer uplink shared channel (PUSCH) to the UE; and receiving uplink data sent by the UE through the PUSCH.
Owner:HUAWEI TECH CO LTD
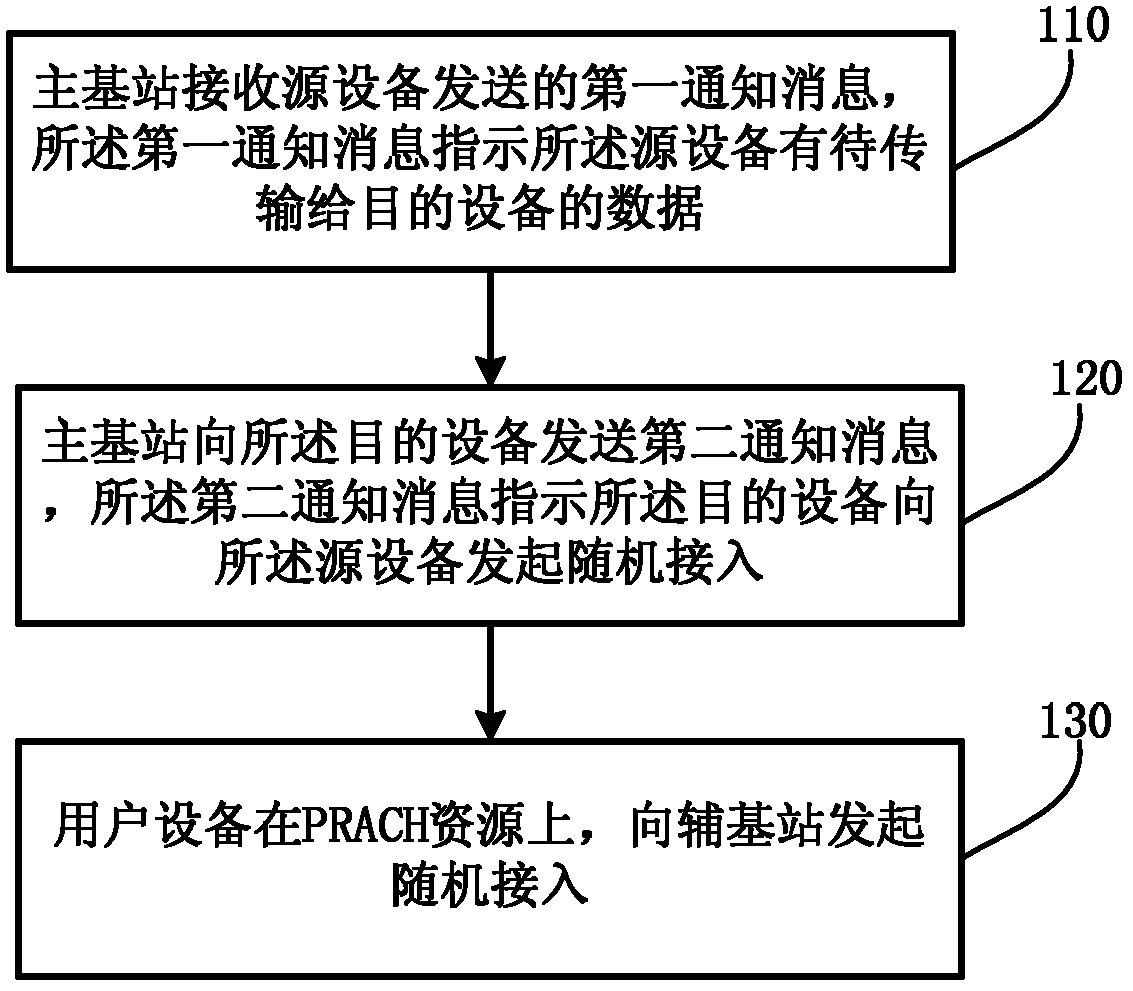
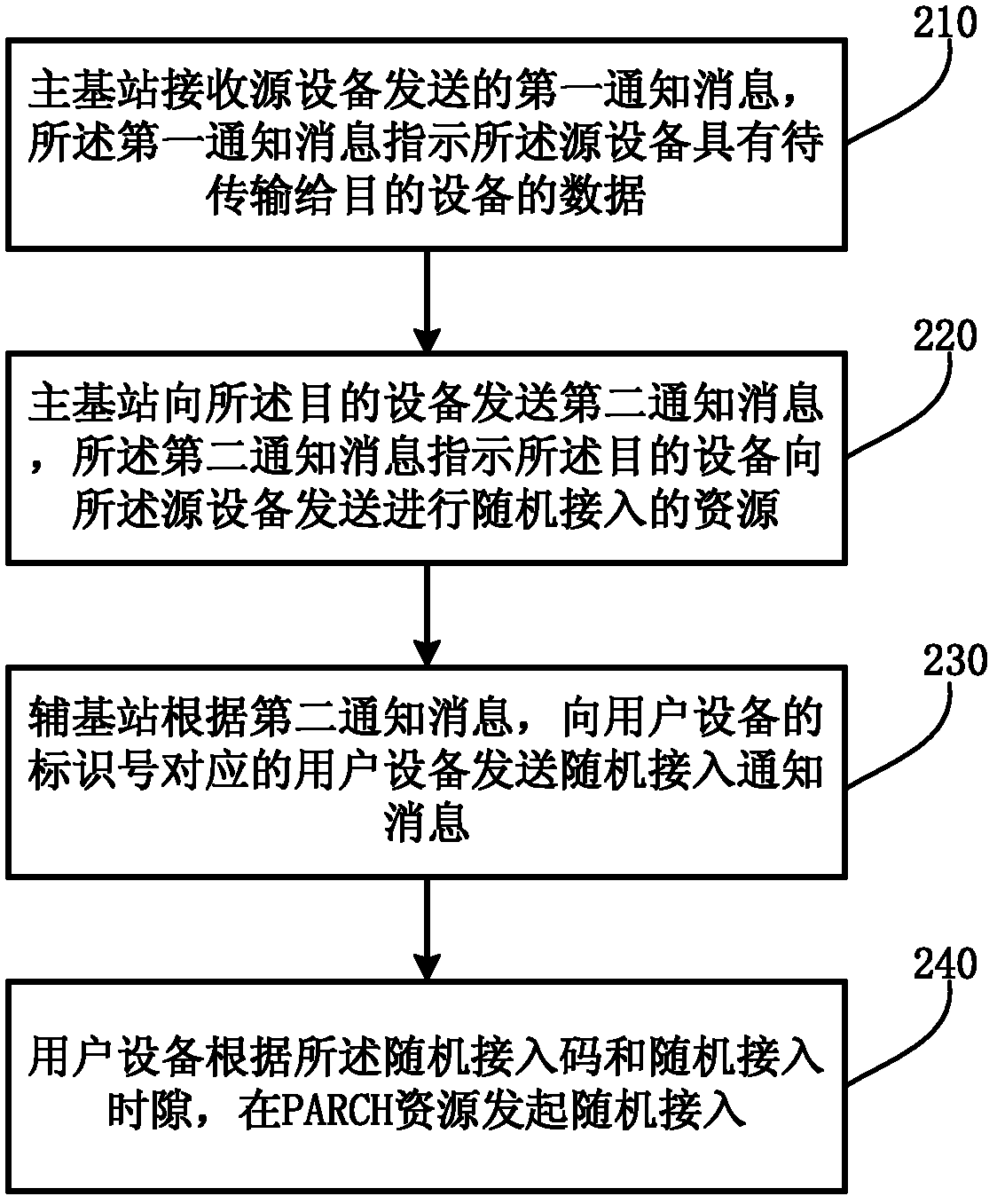
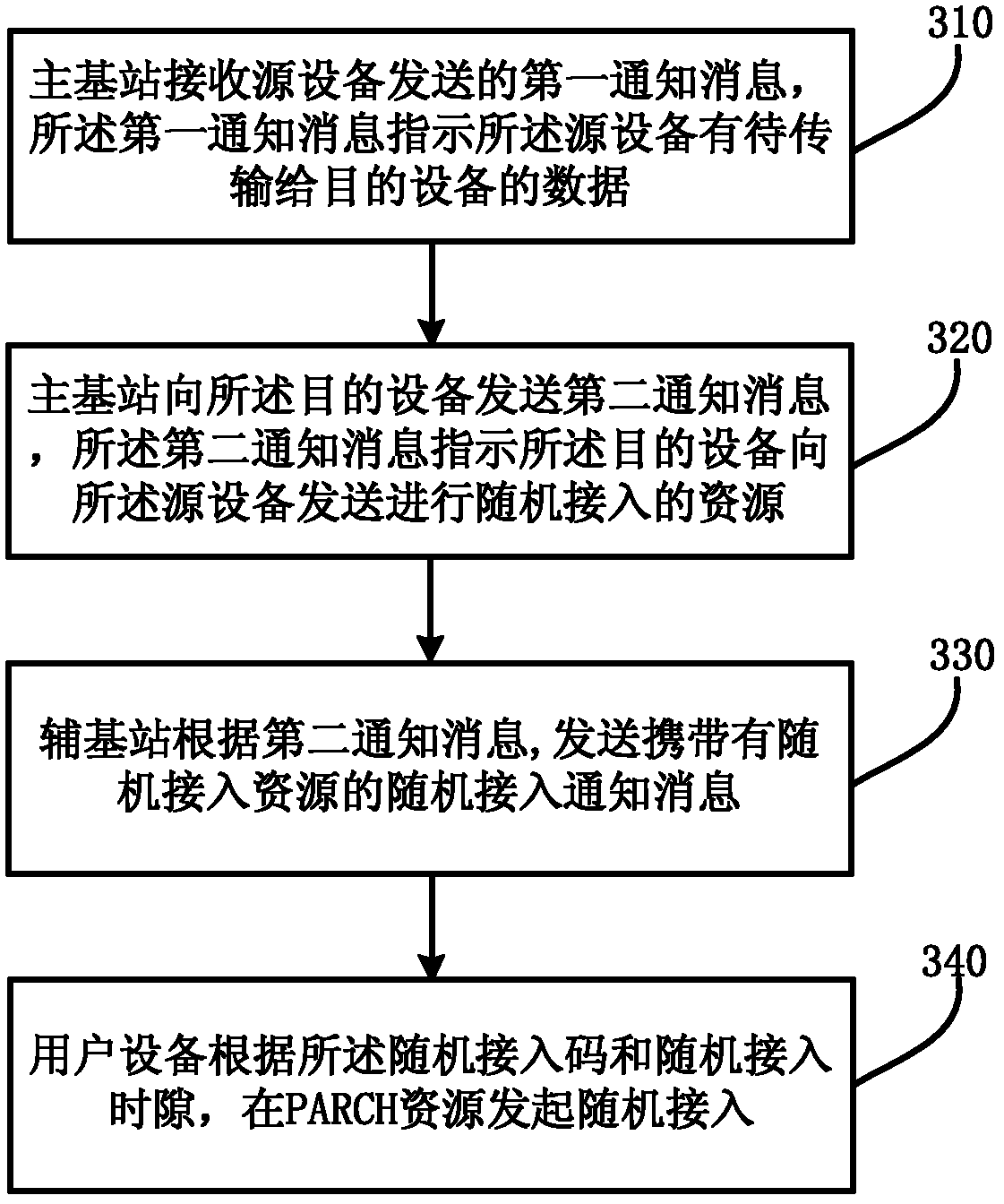
Notification method of random access initiating, notification method of random access resource, and main base station
ActiveCN103188792AContention-proof random accessAvoid random accessWireless communicationData transmissionRandom access
The embodiment of the invention relates to a notification method of random access initiating, a notification method of a random access resource, a notification method of a data transmission resource, and a main base station. The notification method of the random access initiating comprises the steps that the main base station receives first notification information from source equipment; the first notification information indicates data of the source equipment to be transmitted to target equipment; the main base station sends second notification information to the target equipment; and the second notification information indicates the target equipment to initiate random access to the source equipment. With the adoption of the notification methods and the main base station, physical downlink control channel commands on various base stations are prevented from being monitored by user equipment.
Owner:HUAWEI TECH CO LTD
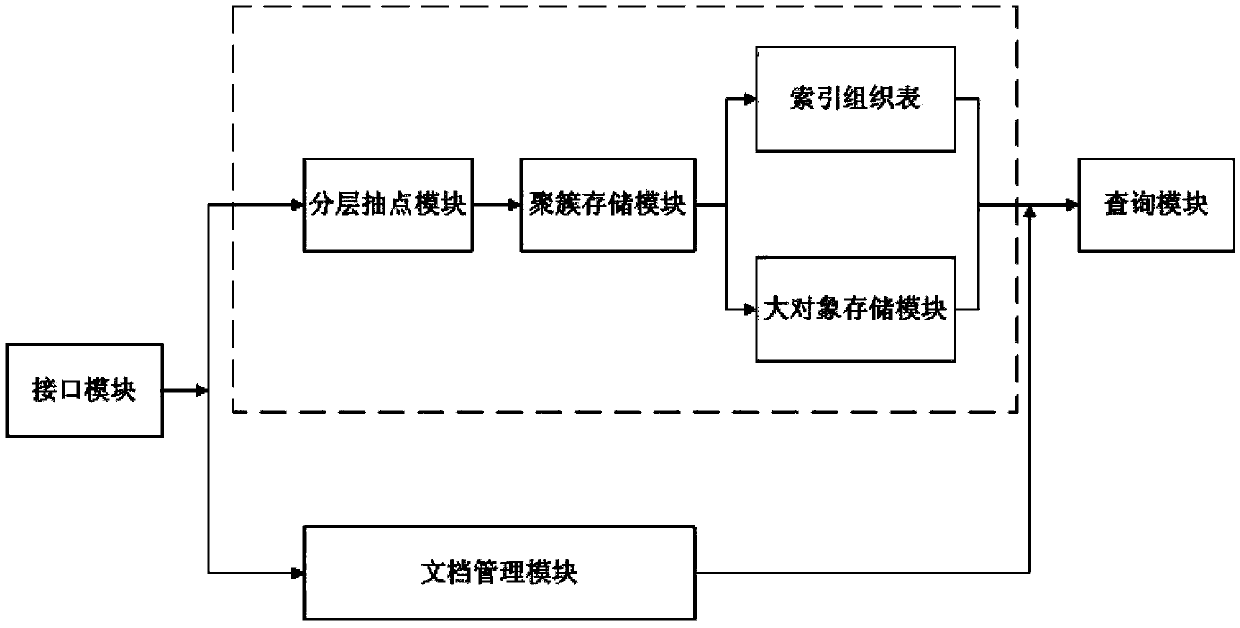
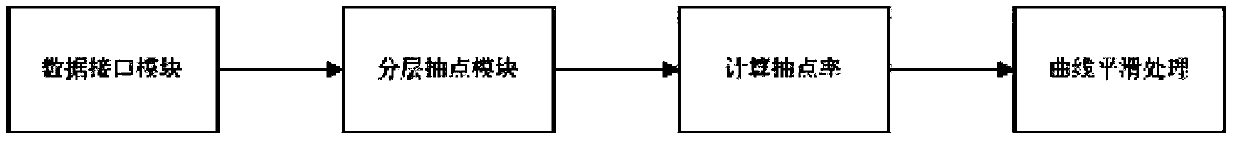
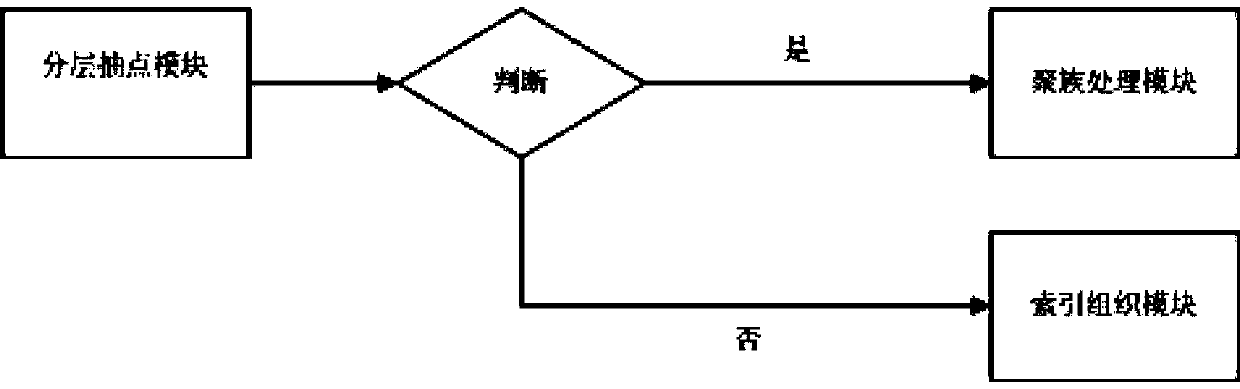
Concurrency OLAP (On-Line Analytical Processing)-oriented test data hierarchy cluster query processing system and method
ActiveCN103473260AReduce loadImprove query efficiencySpecial data processing applicationsObject basedHandling system
The invention discloses a concurrency OLAP (On-Line Analytical Processing)-oriented test data hierarchy cluster query processing system and a concurrency OLAP (On-Line Analytical Processing)-oriented test data hierarchy cluster query processing method. The I / O price of a test data access in the concurrency OLAP is reduced by a series of DBMS (Data Base Management System) technologies of hierarchy test count, cluster, an index organization chart, large object-based storage and the like, so the processing capacity of concurrency query is imporved. According to the system and the method, the concurrency query processing and optimization techniques can be realized in a database management system by aiming at the I / O performance and concurrency OLAP processing performance, and the oriented I / O performance is supported to optimize and set a concurrency OLAP so as to process a load, thereby improving the predictable performance displayed by test data waveforms, and realizing the accelerated processing of the test data query of the large-scale concurrency OLAP.
Owner:BEIJING INST OF CONTROL ENG
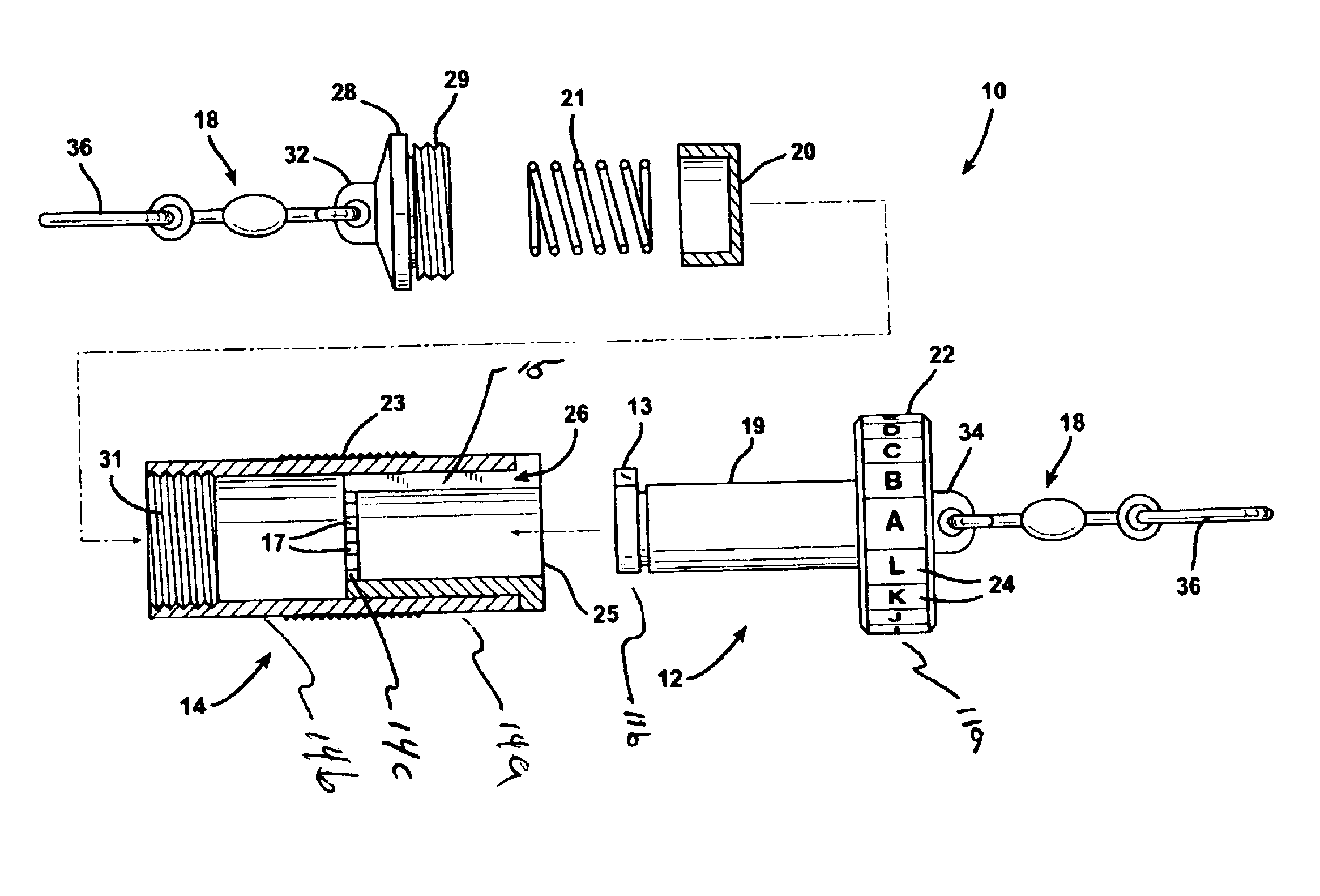
Keyless locking device
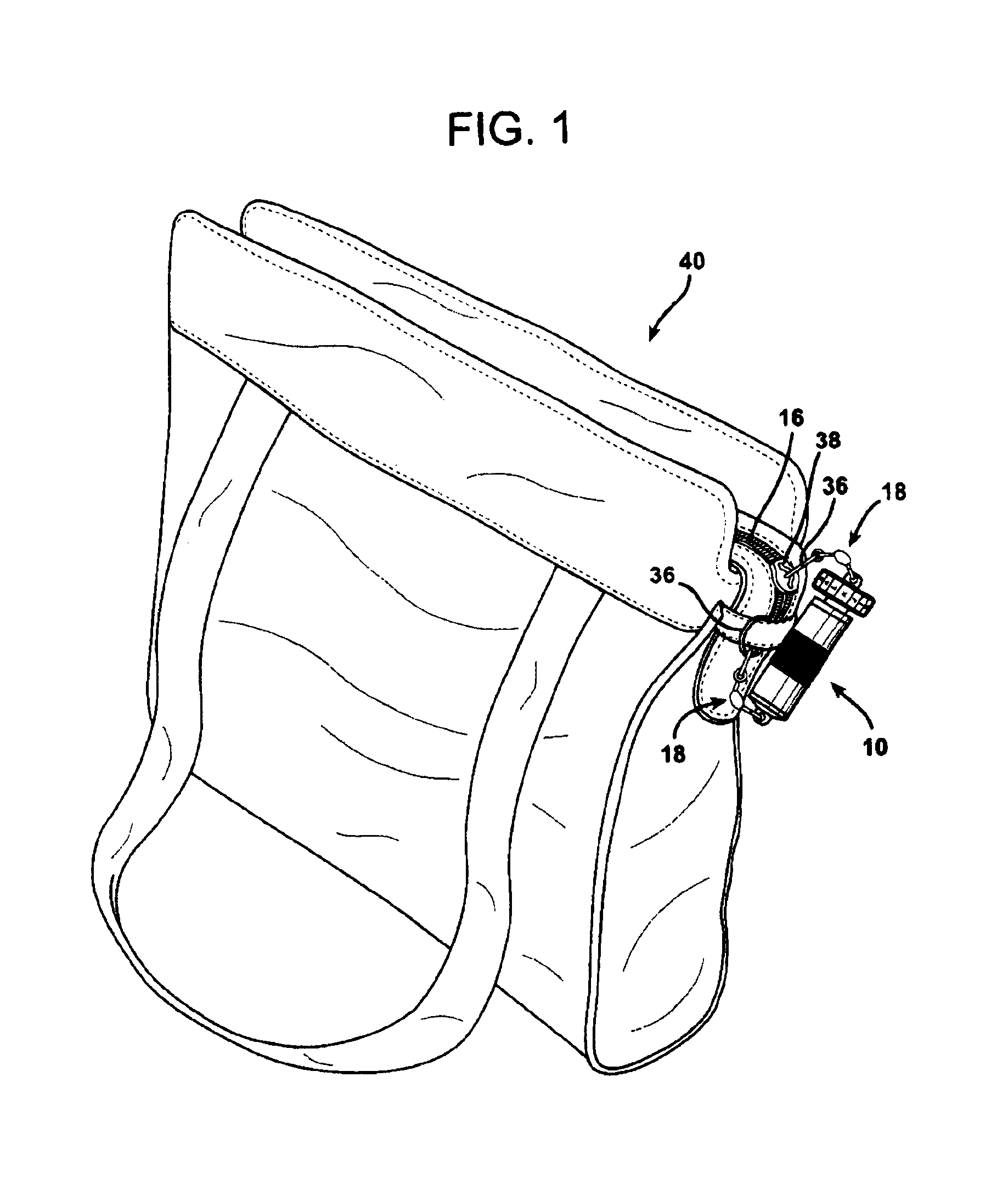
InactiveUS6851285B1Easy to openAvoid random accessPadlocksPuzzle locksEngineeringMechanical engineering
A locking device having a cylindrical plunger with a key thereon and a cylindrical sleeve for receiving the plunger and key. The sleeve has a lip therein with a mating keyway that passes therethrough. An indicium on the sleeve is aligned with the keyway. To lock the device the plunger is inserted into the sleeve, the key sliding along the keyway through the lip into the bottom portion compressing a spring member therein. The sleeve and plunger are then rotated with respect to each other and released, the spring biasing the plunger upward to lock the key onto the bottom surface of the lip. To unlock the device, the sleeve and plunger are pressed together and rotated with respect to each other until, by noting the position of the known indicium, the key and keyway are aligned with each other. The plunger is then removed from the sleeve.
Owner:TECCO
Safe and fair data sharing system and method capable of protecting privacy
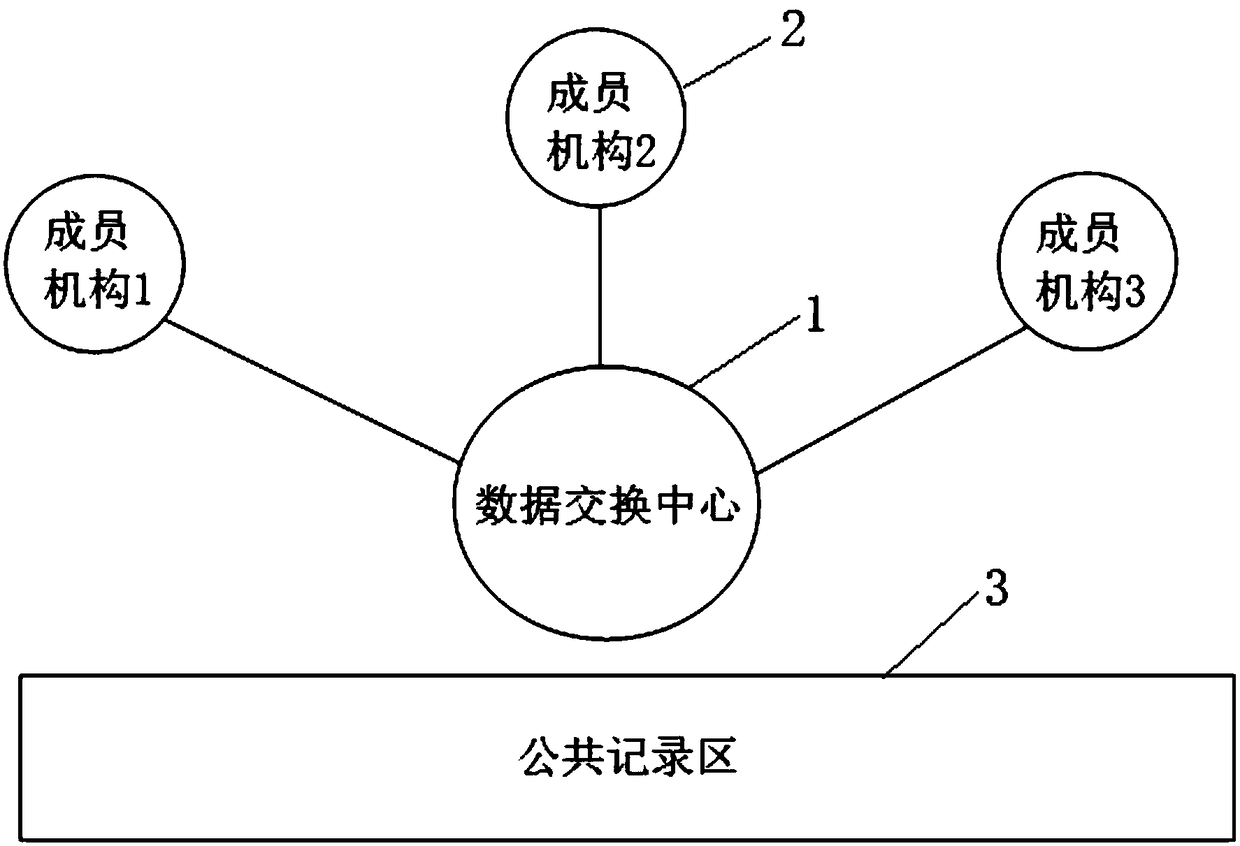
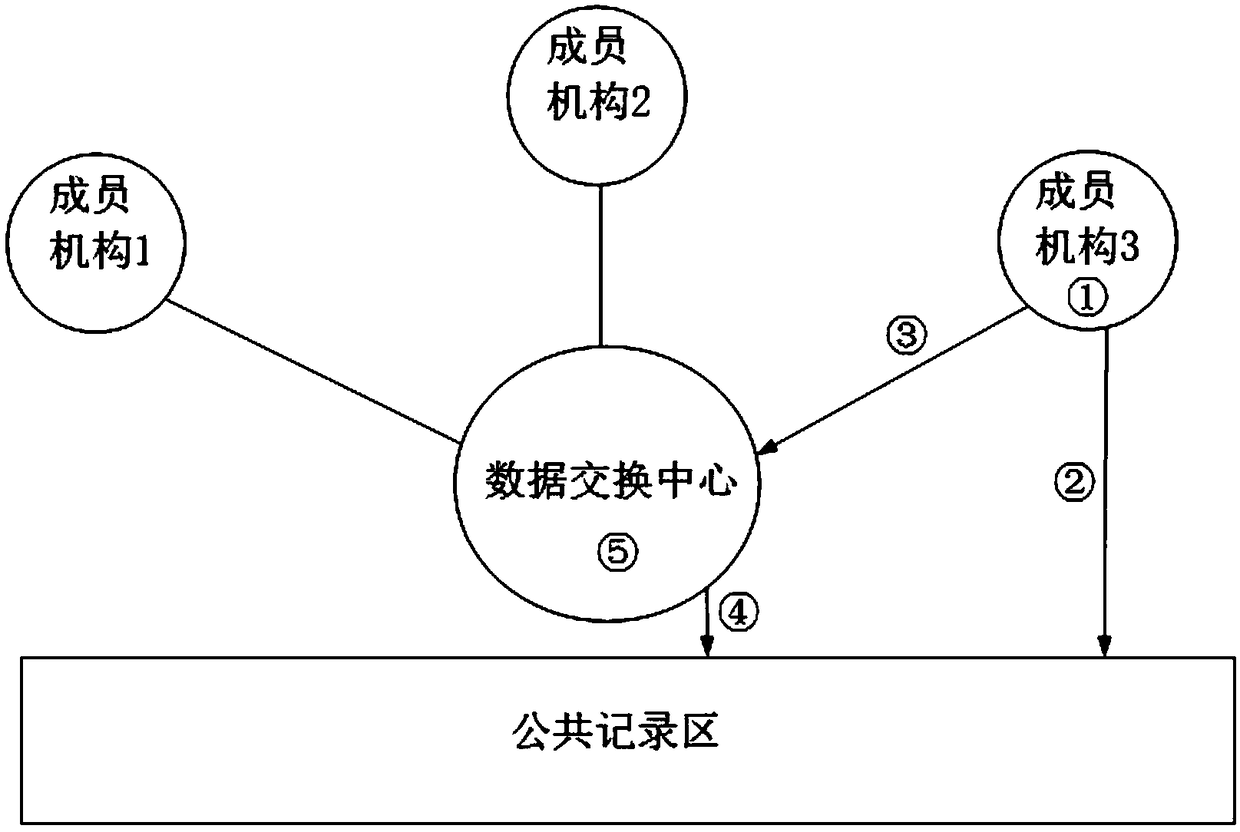
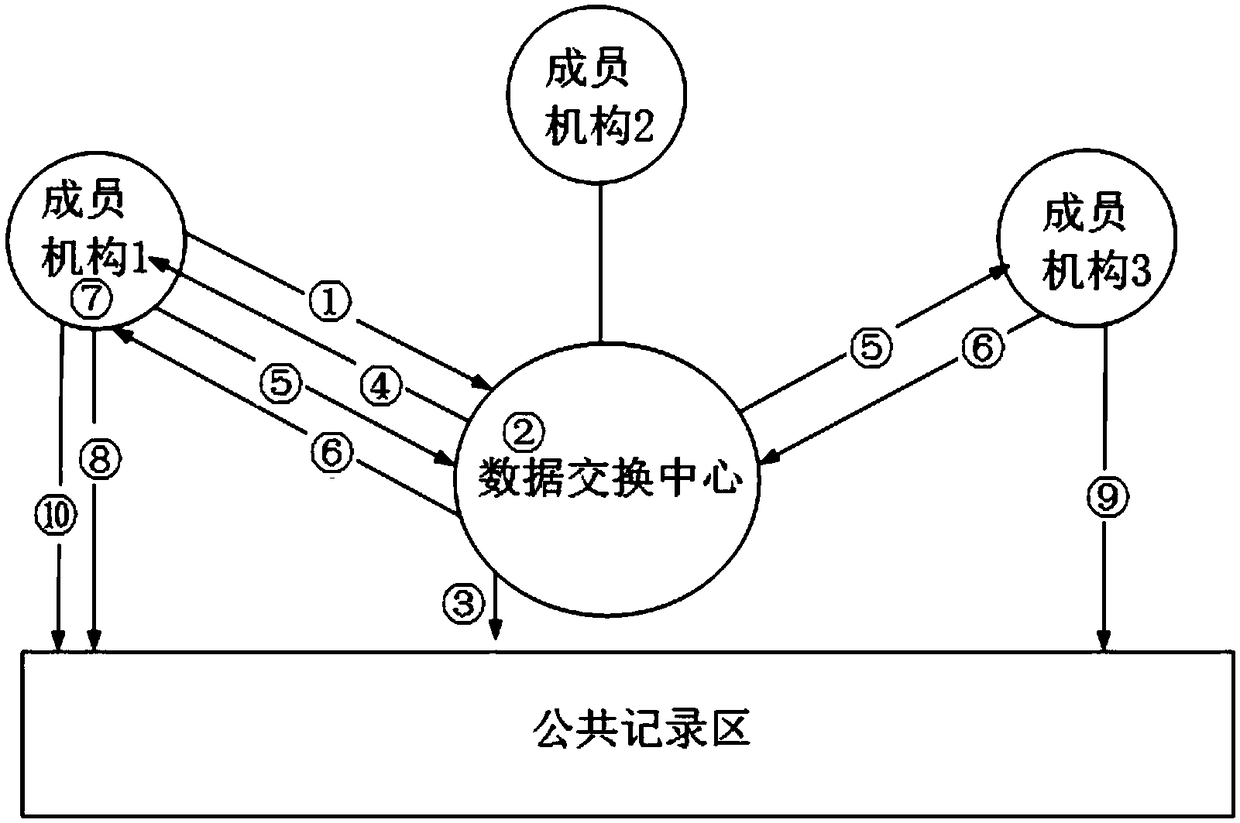
ActiveCN108650252AEnhanced authenticationAvoid random accessTransmissionSpecial data processing applicationsThird partyInternet privacy
The invention discloses a safe and fair data sharing system and method capable of protecting privacy. The system comprises a data exchanging center, a member institution, and a public recording area;the data exchanging center is built and operated by an independent third party, and is used for constructing a basic communication frame, hiding connection and communication among the member institutions, managing authentication and access of each member institution, specifying a information standard and a exchange transaction rule, and maintaining the transaction order; the member institution participates the data sharing, and is used for maintaining external sharing information, responding information query request sent by an external member institution, and initiating query to acquire the data of the external member institution; the public recording area is an information recording area, and is used for realizing the recording function that the information cannot be tampered and deletedaccording to the time sequence; both the data exchanging center and the member institution can visit and write the public recording area; and the public recording area is used for recording the behaviors, storing the evidence and authenticating after the event during the data sharing process.
Owner:浙江红极互联网科技有限公司
Middle and primary school and kindergarten campus pick-up system based on biological recognition technology
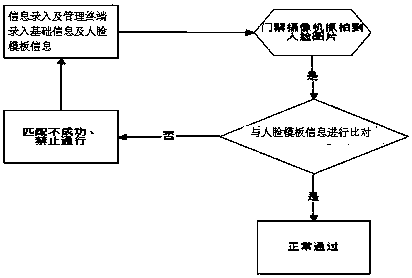
InactiveCN110009789AEnsure personal safetyAvoid random accessData processing applicationsIndividual entry/exit registersPattern recognitionComputer terminal
The invention discloses a middle and primary school and kindergarten campus pick-up system based on a biological recognition technology. A pick-up identification unit takes a face picture of a personto be identified and compares the shot face picture with face template information stored in the pick-up identification unit; after comparing the face picture of the person to be identified shot in real time with any piece of face template information stored in the pick-up identification unit successfully, the person to be identified is allowed to pass through; if the comparison is unsuccessful, the person to be identified is not allowed to pass through, so that the personal safety of students in the campus is effectively ensured, strangers or lawbreakers are prevented from entering the campusat will, parents serving as the person to be identified can enter the campus conveniently without carrying pick-up cards, and the use is more convenient. In addition, the pick-up identification unitcan also upload the shot face picture of the person to be identified and the comparison result to a server for storage, so that an information input and management terminal can call related contents for viewing in real time by the server.
Owner:广东德融汇科技有限公司
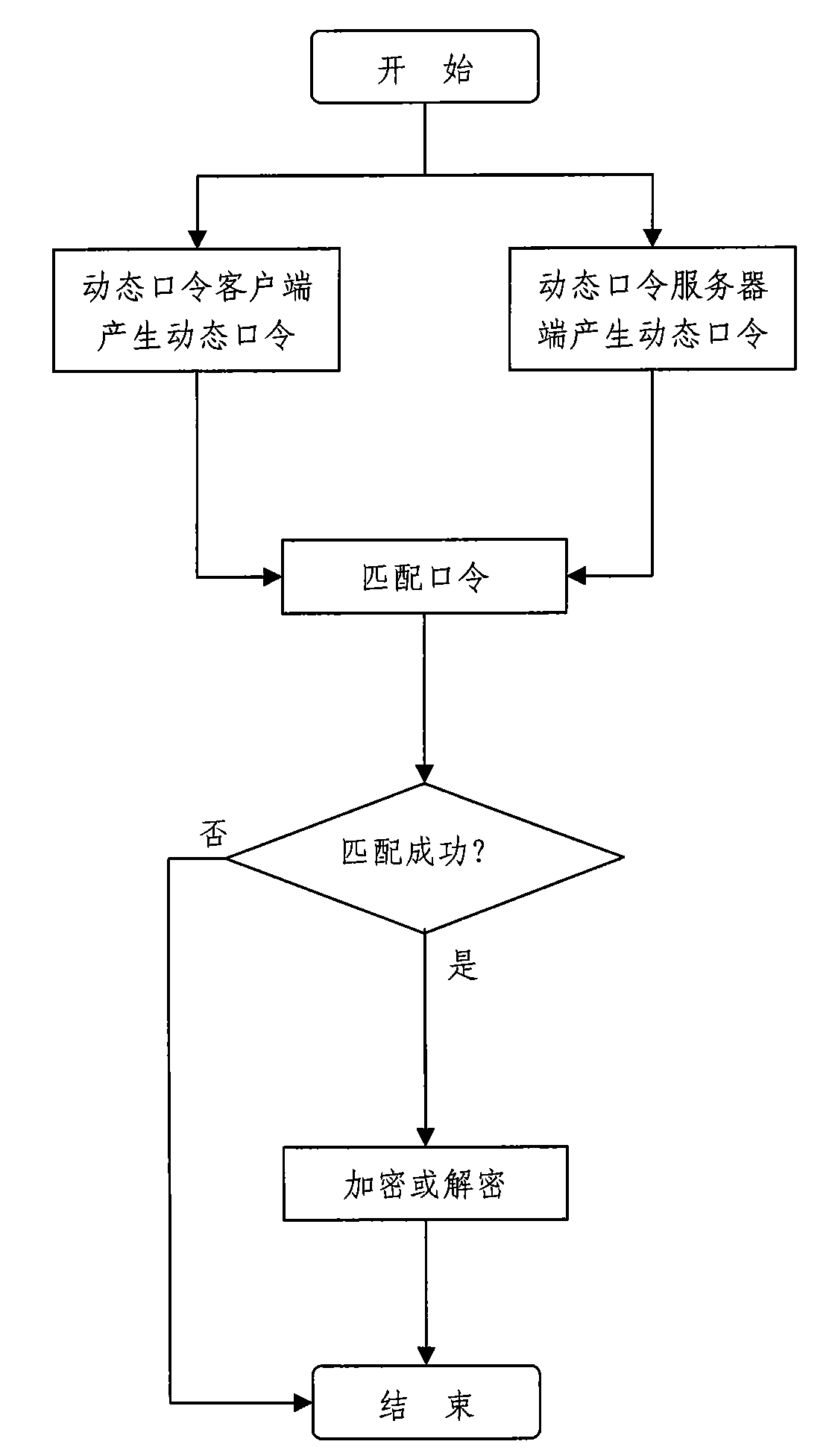
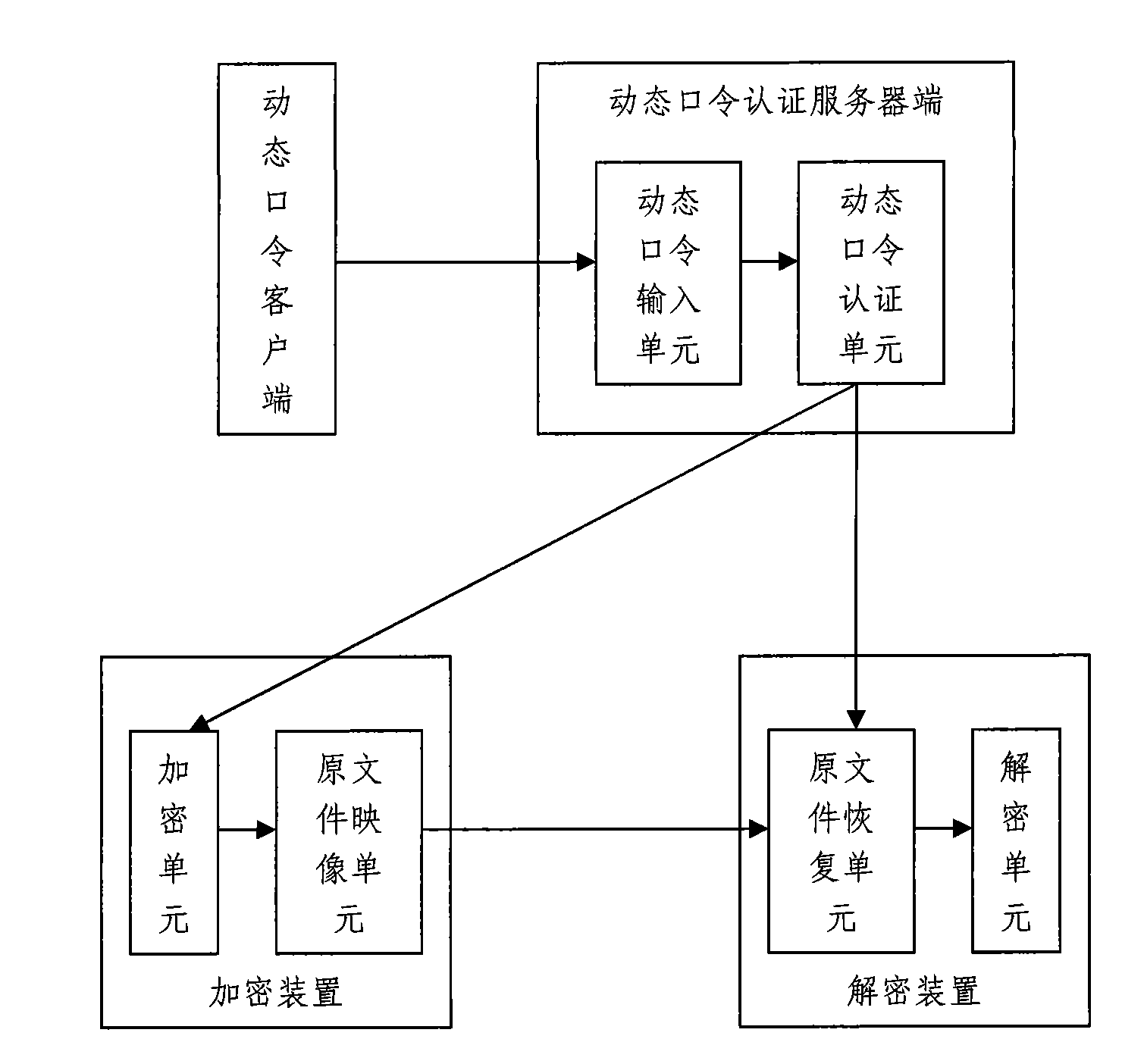
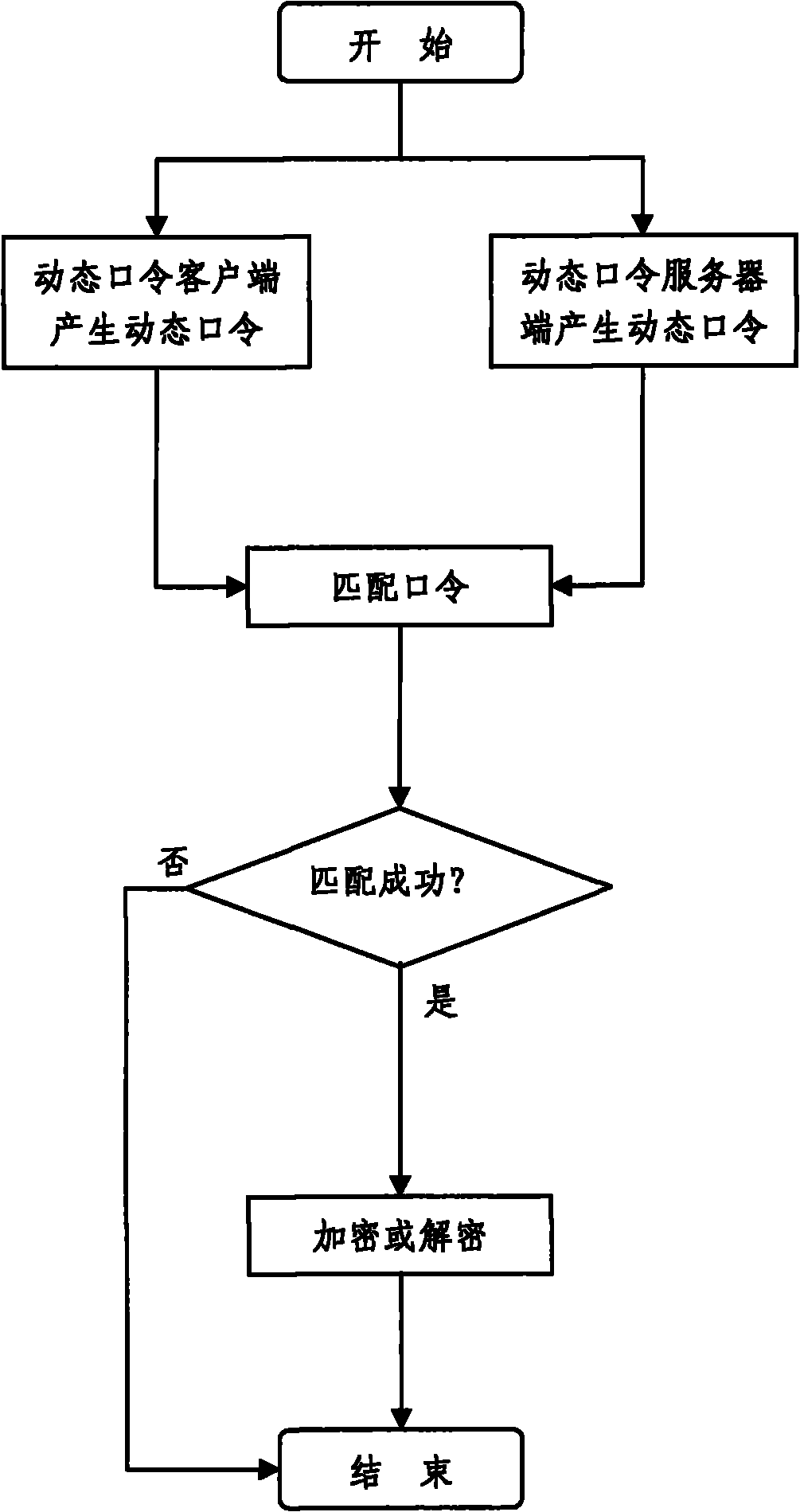
File and folder safety protection method based on dynamic password and system thereof
InactiveCN101833625AAvoid random accessEnsure safetyDigital data protectionTransmissionClient-sideServer-side
The invention discloses a file and folder safety protection method based on a dynamic password, comprising a dynamic password client for generating a dynamic password, and a dynamic password authentication server end for authenticating the dynamic password. When encrypting, the file or folder is encrypted after the authentication is passed; and when decrypting, the file or folder is decrypted after the authentication is passed. The invention also discloses a file and folder safety protection system based on a dynamic password, comprising a dynamic password client for generating a dynamic password, a dynamic password authentication server end, for authenticating the dynamic password, an encryption device for encrypting the file or folder after the authentication is passed when encrypting and a decryption device for decrypting the file or folder after the authentication is passed when decrypting. The invention applies the mode combining the dynamic authentication, encryption and decryption, can effectively prevent others from optionally accessing, copying and deleting the file and folder, so that the safety of the individual privacy is ensured.
Owner:SHANGHAI ZHONGSHUO INFORMATION TECH
Data transmission method, base station, and terminal
PendingCN109246744ARealize data transmissionAvoid random accessConnection managementAir interfaceComputer terminal
The invention discloses a data transmission method, a base station, and a terminal. The method comprises the steps that the base station configures a DRX parameter and / or measurement parameter for UEwhen the UE is in a preset state or enters the preset state, wherein the preset state is a state that an air interface between the UE and the base station is switched off and the connection, corresponding to the UE, of the base station and a core network remains. The method can achieve the data transmission through the configuration of the DRX parameter when the UE is in a non-connected or unactivated state, and can prevent the initiation of a random access process of the UE in the data transmission process, thereby effectively reducing the time delay. In addition, because the DRX mode is employed for data transmission, the method can well solve a problem of data forwarding between the base stations, effectively responds to a condition that the UE switches a cell, reduces the signaling load between the base stations, and reduces the network load.
Owner:ZTE CORP
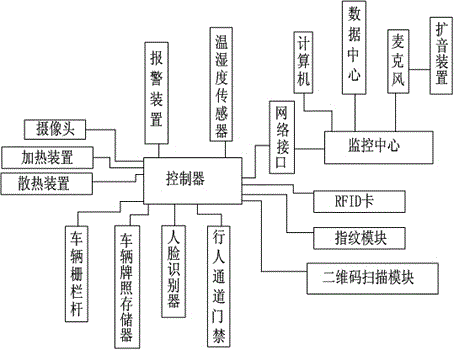
Community management system based on cloud platform
InactiveCN106296936AAvoid random accessEnsure safetyIndividual entry/exit registersPasswordData center
The invention discloses a community management system based on a cloud platform. The community management system comprises a monitoring center, wherein the monitoring center is connected with a controller by virtue of a network interface, the controller is in communication connection with a pedestrian passage access control, a camera, a face recognizer, an FRID card, a fingerprint module and a two-dimensional code scanning module, and the monitoring center is connected with a computer and a data center. By arranging the face recognizer, the camera and the pedestrian passage access control which cooperate mutually, entry by face is realized; meanwhile, entry by swiping the RFID card can also be realized, as well as the entry by pressing fingerprints and scanning the two-dimensional code and inputting a password by virtue of a mobile phone terminal can be realized, so that the random entry of strangers to the community can be effectively prevented, the security of the community is effectively guaranteed; and the picture that the personnel enters and exits a gate can be observed in real time by virtue of the monitoring center, so that the security of the community is further controlled.
Owner:成都海蜃网络科技有限公司
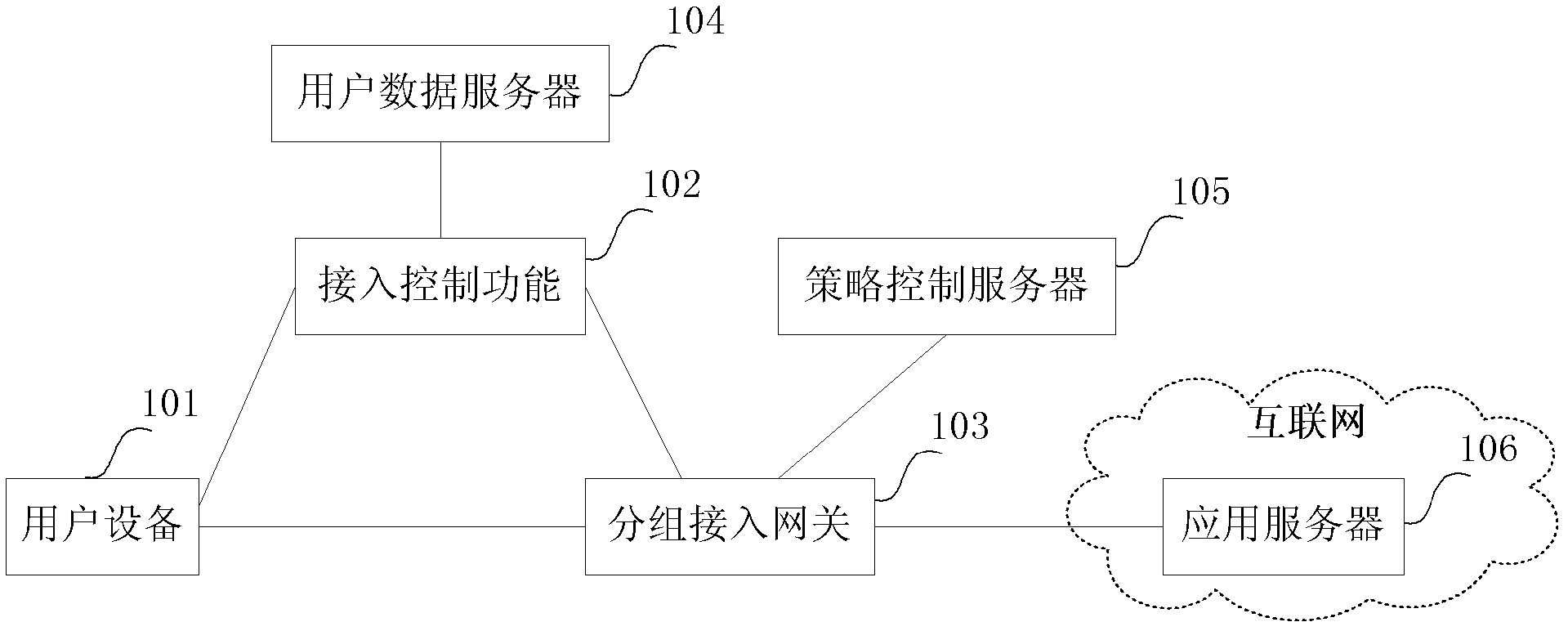
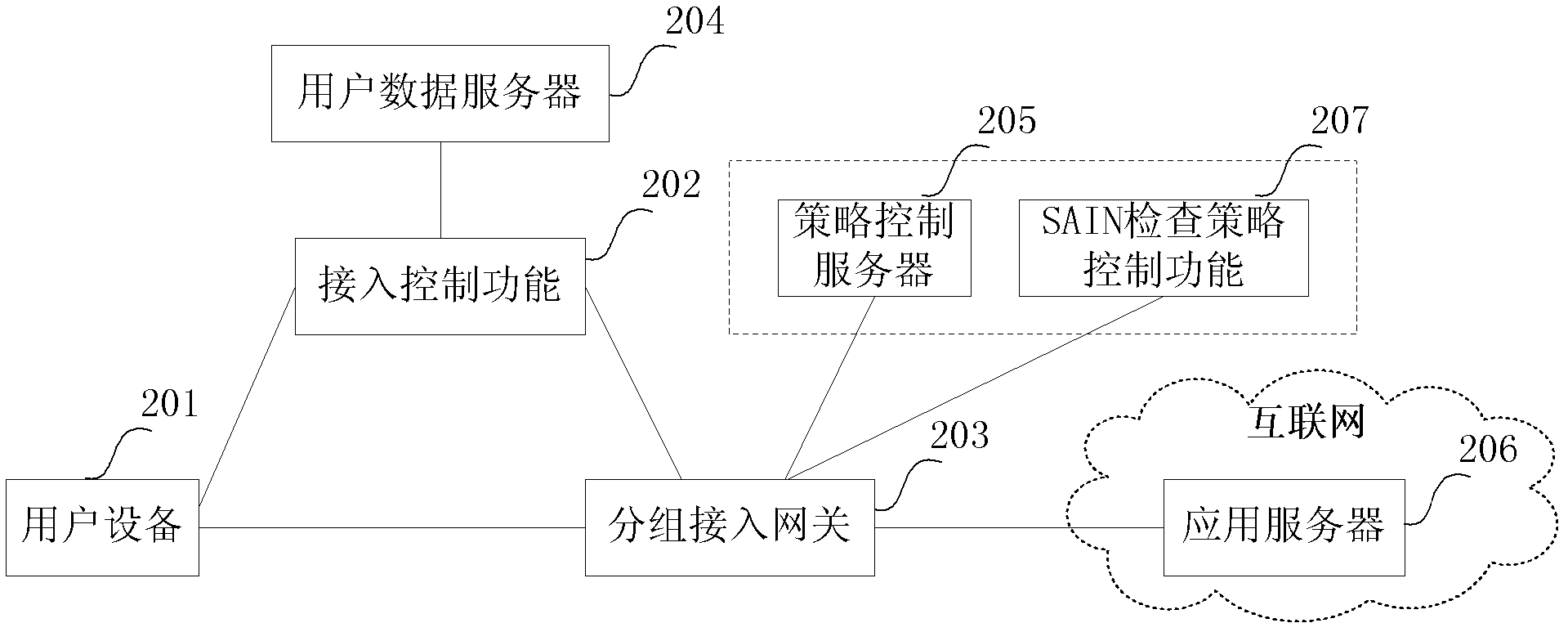
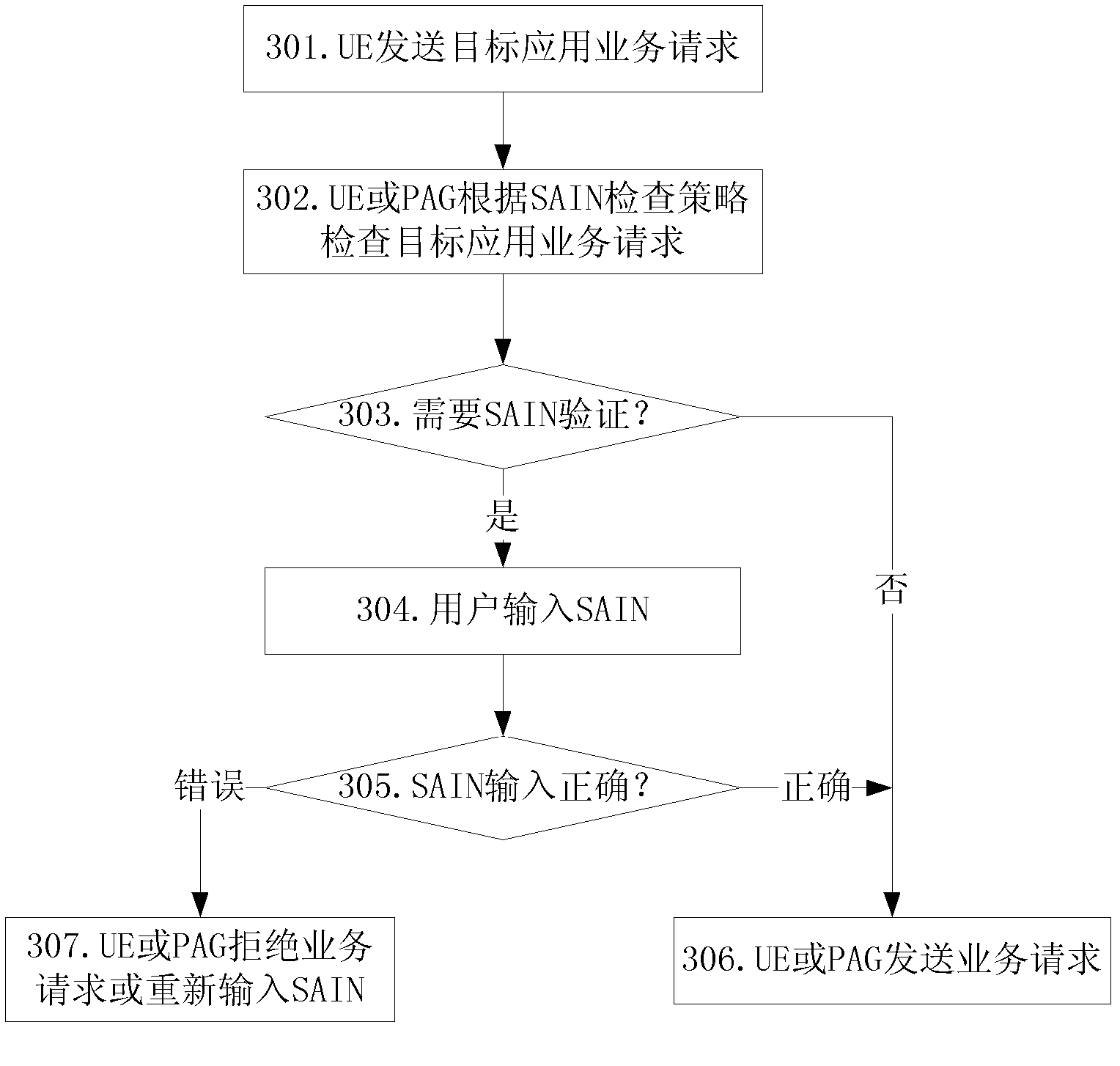
Method, user equipment and packet access gateway for secure access to Internet services
InactiveCN103051598AImprove securityPrevent random accessTransmissionInternet businessAccess network
The invention discloses a method for secure access to Internet services. In a packet access network, the control problem caused when the current technology does not consider the user access to specific target application is solved. After UE (User Equipment) successfully accesses to the Internet, when a certain target application is to be accessed, the method comprises the following steps of: checking a service request for the target application by an SAIN (Secure Access Identity Number) checking point according to an SAIN check policy, and when the SAIN checking point determines that the service request needs the SAIN check, prompting a user to input an SAIN by the UE; and if the SAIN checking point determines that the input SAIN result is correct, transferring the target application service request, and if not, refusing the service request. By introducing the SAIN, the secure inspection and protection of the corresponding data stream are applied to a target Internet, thereby the access security of the Internet application is improved. The method especially aims at a scene of Internet access in a user identification mode.
Owner:ZTE CORP
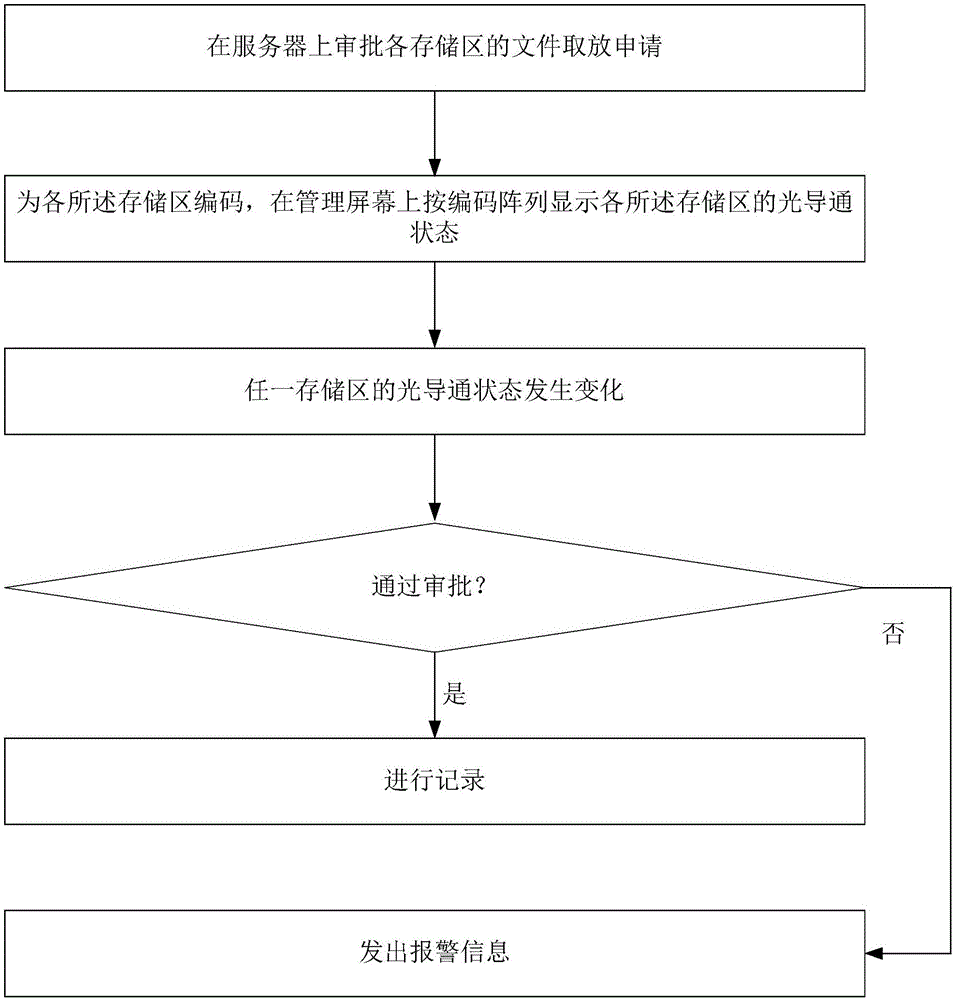
File management method
ActiveCN105023372AEffective Rights ManagementHard to findCash registersResourcesRights managementComputer technology
The invention relates to a file management method. TH method comprises the following steps that file taking and putting applications of different storage areas are examines by a server; the storage areas are coded, and light conduction states of the storage areas are displayed on a management screen according to a coding array; and when the light conduction state of any storage area changes, whether the file taking and putting application of the storage area is approved is determined, if yes, recording is carried out, and otherwise, alarm information is emitted. According to the file management method, traditional file management is combined with modern computer technology, paper files are hard to find and tend to be messy are solved, whether files are taken from or put into the storage areas is determined automatically, file taking and removing is timely recorded, and alarm is raised when abnormity occurs; a computer can be used to effectively manage the privilege, an officer cannot take or put the files unless the file taking and putting application is approved by a manager, thereby avoiding the files from loss or misplacement; and the method is especially suitable for management of property files.
Owner:上海新建设工程咨询有限公司
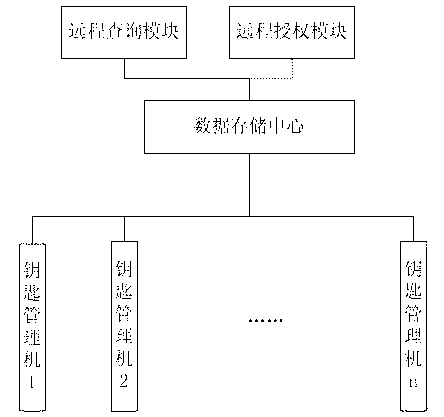
Intelligent remote hierarchical key management and control system
InactiveCN102710016AImplement lock managementAvoid random accessCircuit arrangementsControl systemCentralized management
The invention discloses an intelligent remote hierarchical key management and control system, which comprises a plurality of key managers and a data storage center communicating with the key managers. A user queries the data of the data storage center through a remote query module. The system also comprises a remote authorization module, wherein the remote authorization module communicates with the remote key managers, and authorizes a corresponding key manager to unlock a specified unlocking key. The key managers realize locking and unlocking management over keys by performing locking and unlocking detection on the keys, so that the keys can be prevented from being randomly taken for use. Remote hierarchical authorization is realized, so that any point can be remotely authorized, and the applicability and efficiency of the system in a using process are improved. Key data is managed in a centralized way, so that the data query, counting, tracking and the like of different users are facilitated.
Owner:STATE GRID CORP OF CHINA +1
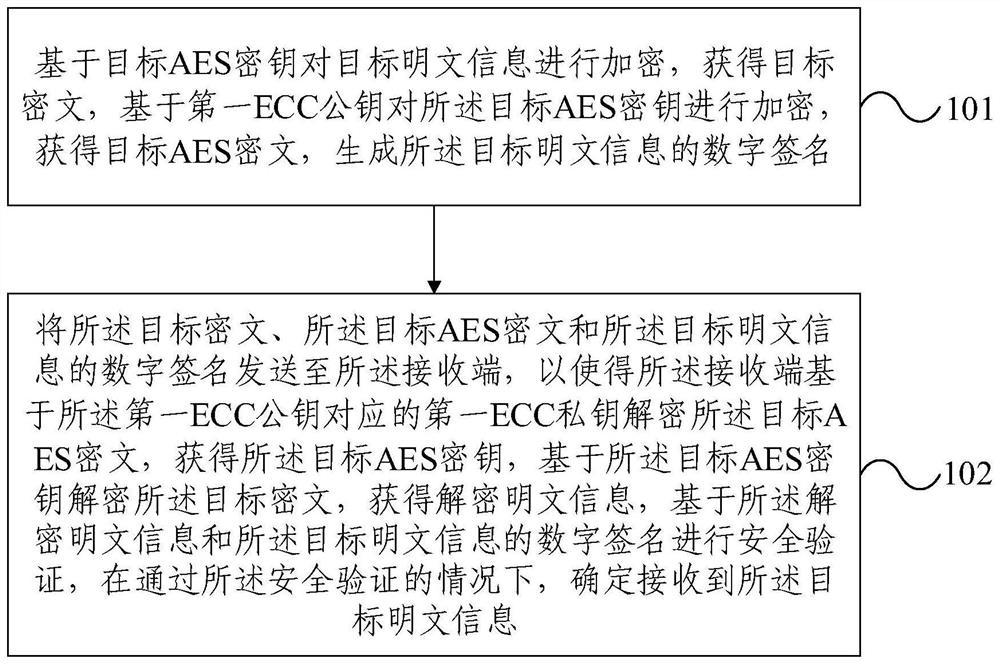
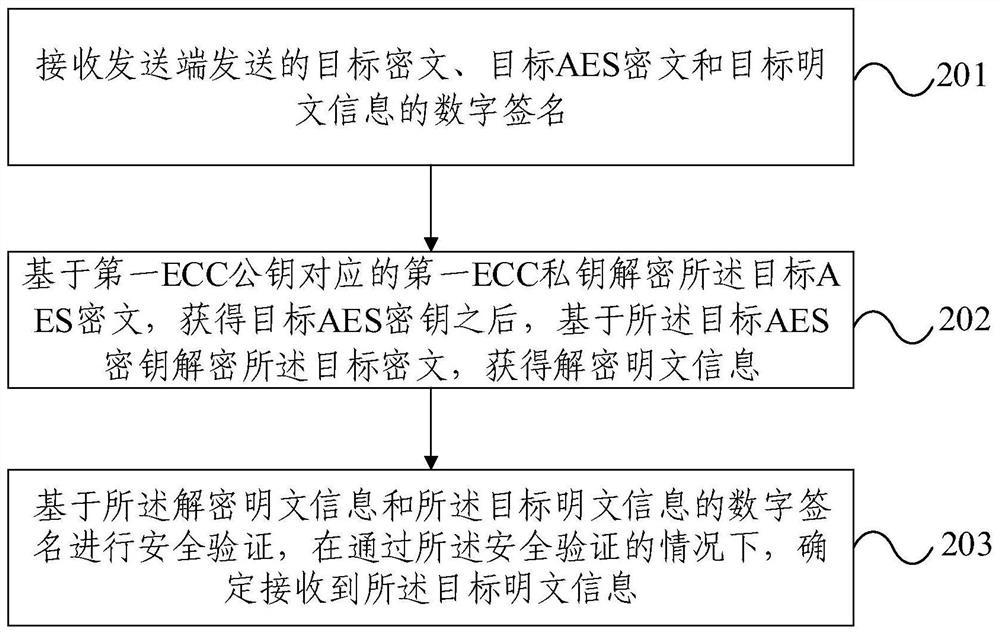
Information encryption transmission method and device based on block chain
PendingCN113806772AEncrypted transmission securityEfficient encrypted transmissionDigital data protectionPlaintextDigital signature
The invention provides an information encryption transmission method and device based on a block chain. The method comprises the following steps: encrypting target plaintext information based on a target AES key to obtain a target ciphertext, encrypting the target AES key based on a first ECC public key to obtain a target AES ciphertext, and generating a digital signature of the target plaintext information; and sending the target ciphertext, the target AES ciphertext and the digital signature of the target plaintext information to a receiving end, so that the receiving end decrypts the target AES ciphertext based on a first ECC private key corresponding to the first ECC public key to obtain a target AES key; decrypting the target ciphertext based on the target AES key to obtain decrypted plaintext information, and performing security verification based on the decrypted plaintext information and the digital signature of the target plaintext information, and determining that the target plaintext information is received under the condition that the security verification is passed. According to the information encryption transmission method and device based on the block chain provided by the invention, safer and more efficient information encryption transmission can be realized.
Owner:WUHAN HONGXU INFORMATION TECH
Keyless locking device
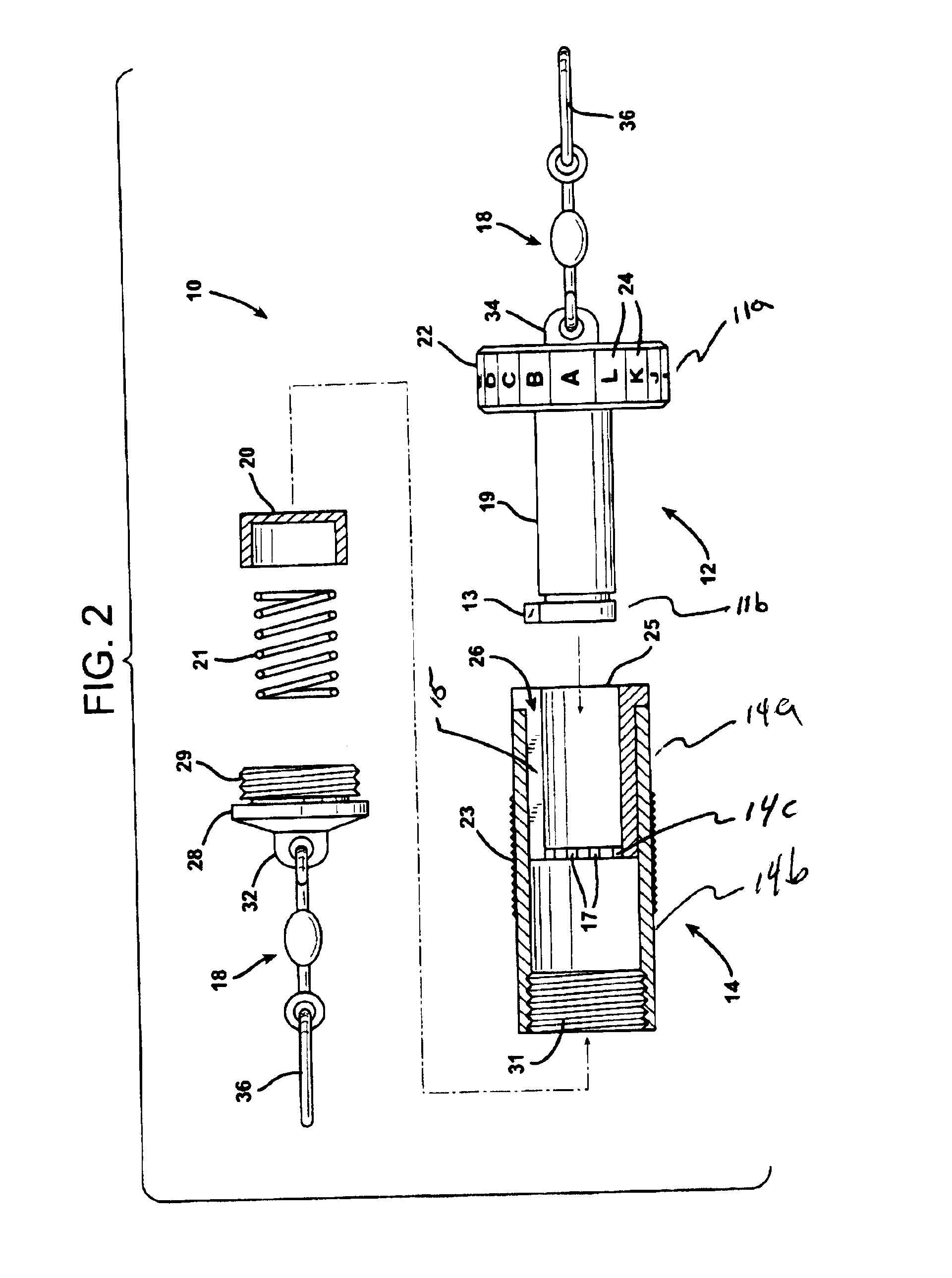
A locking device having a cylindrical plunger and a cylindrical sleeve for releasably and rotatably receiving the plunger, the sleeve having an open top portion, and a bottom portion. A keyway is provided axially disposed along the length of one of the plunger or sleeve, and a lip circumferentially disposed around the same plunger or sleeve. A key is also provided on the other of the plunger or sleeve, the key slidably mating with the keyway. A spring member is disposed within the sleeve and is compressed when the plunger is inserted into the sleeve biasing the plunger out of the sleeve. To lock the device the plunger is inserted into the sleeve, the key sliding along the keyway through the lip, the plunger compressing the spring member, and then the sleeve and plunger are rotated with respect to each other and released, the spring biasing the plunger out of the sleeve and locking the key onto a surface of the lip. To unlock the device the sleeve and plunger are pressed together, the plunger compressing the spring member, and rotated with respect to each other until the key and keyway are aligned with each other, the spring biasing the plunger out of the sleeve. The plunger is then removed from the sleeve, the key sliding along the keyway through the lip.
Owner:TECCO
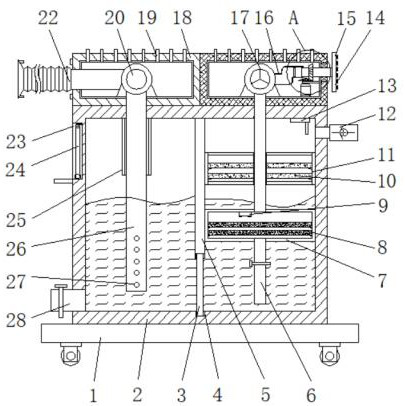
Air purification device and using method thereof
InactiveCN112169489APrevent seepageInto the uniformCombination devicesUsing liquid separation agentEngineeringDrive motor
The invention discloses an air purification device and a using method thereof. The air purification device comprises a bottom plate, wherein a box body is fixedly connected to the top of the bottom plate, connecting boxes are fixedly connected to the two sides of the top of the box body, and sound insulation felts are fixedly connected to the inner walls of the connecting boxes. According to the invention, through the cooperative use of a partition plate, a water inlet pipe, a water purifying tank, a water purifying material placing screen plate, a water quality sensor, a purifying material placing screen plate, a purifying tank, a one-way valve, an air sensor, an atomizing nozzle, a hollow disc, a water conveying pipe, a water suction pump, an exhaust fan, an air inlet pipe, an exhaust pipe, an exhaust hole, a blow-off pipe, a breathable screen plate, an ultrafiltration membrane, a driving motor, a driving bevel gear, a driven bevel gear and a transverse pipe, the problems that most of existing air purification devices adopt one-time filter screen adsorption, harmful gas in air cannot be classified and purified many times, the purification effect is common, the functions of atomization, humidification and dust falling are not achieved, and the requirements of users cannot be met are solved.
Owner:刘林旭
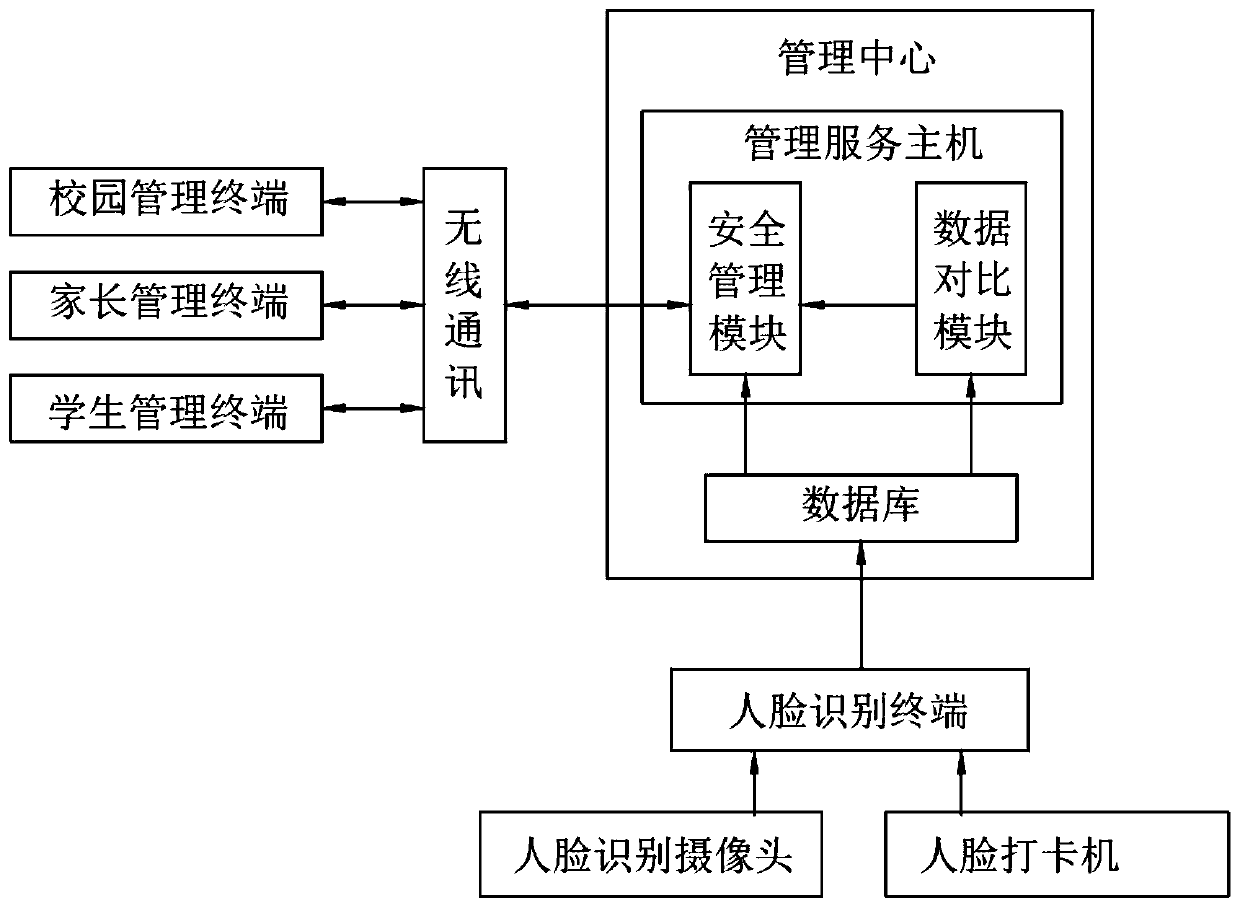
Campus safety management system based on AI face recognition
InactiveCN110363181AAvoid random accessEnsure safetyRegistering/indicating time of eventsCharacter and pattern recognitionSafety management systemsFile comparison
The invention discloses a campus safety management system based on AI face recognition. The system comprises a face recognition terminal. The face recognition terminal is electrically connected with the management center. The management center comprises a management service host and a database. The management service host comprises a data comparison module and a safety management module. The safety management terminal is in signal connection with the management center. The safety management terminal comprises a campus management terminal, a parent management terminal and a student management terminal and is used for receiving safety warning. According to the invention, the AI face recognition technology is used to obtain the face features of the school personnel. Outsiders can be discriminated in time. Foreign personnel are prevented from entering the campus at will. The safety of teachers and students in the school is guaranteed. Absent students can be found in time through curriculumschedule data, teachers, students and parents can master the states of students in the school in time and master the behaviors of students in the school in time. The supervision and management of teachers and parents on students are improved. The safety of students in the school is guaranteed.
Owner:安徽锦星信息技术有限公司
Unidirectional fence gate
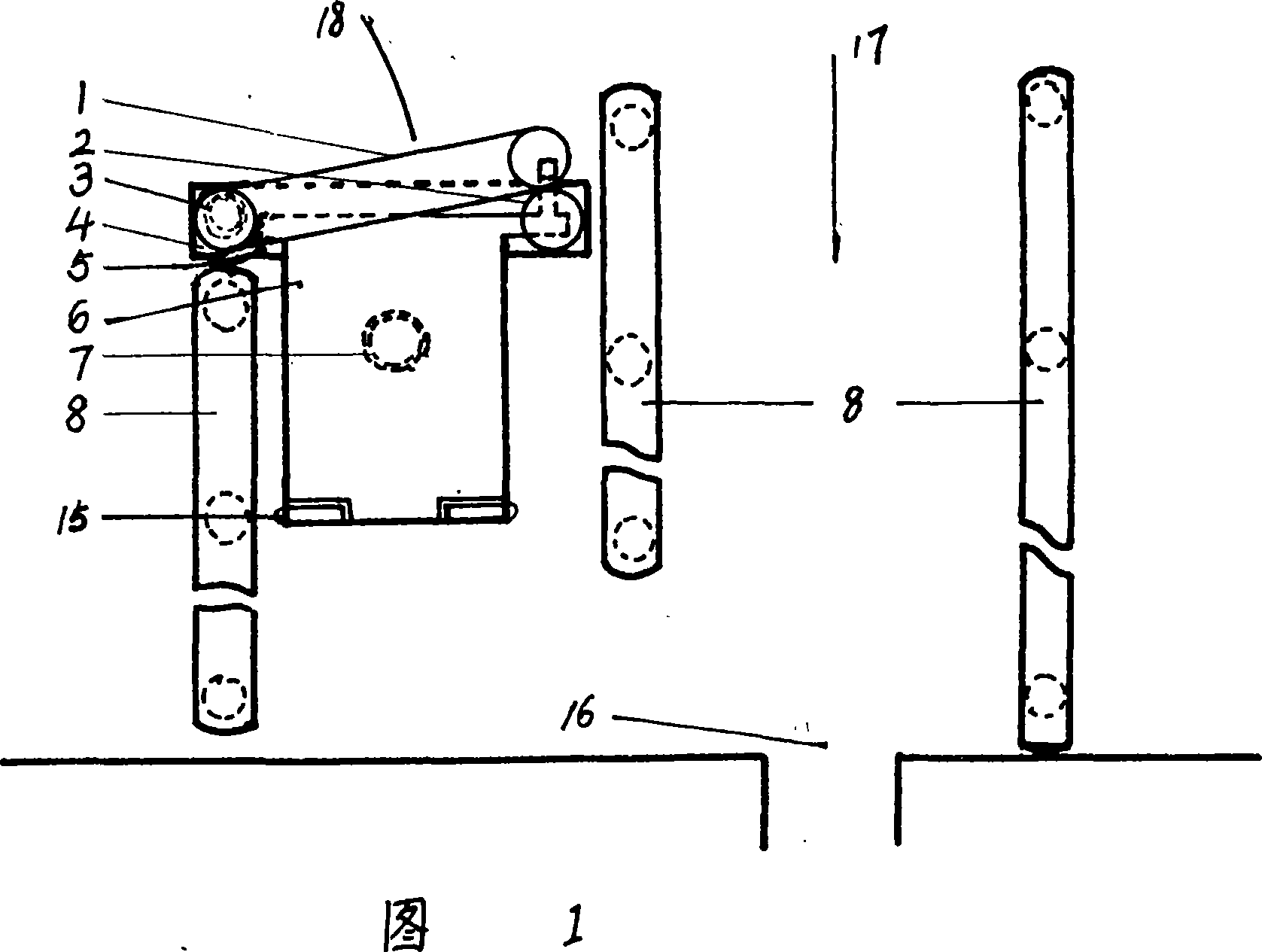
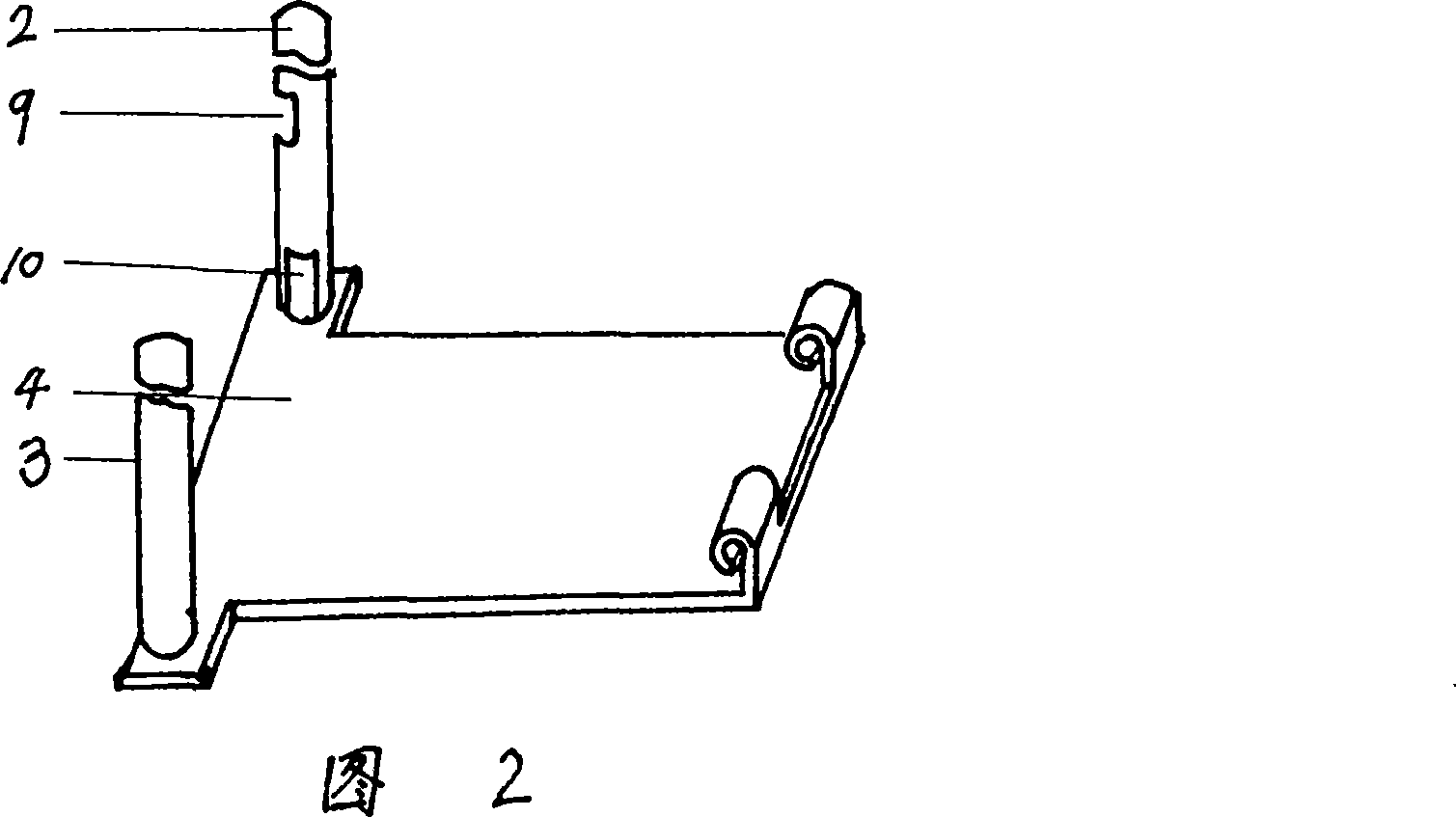
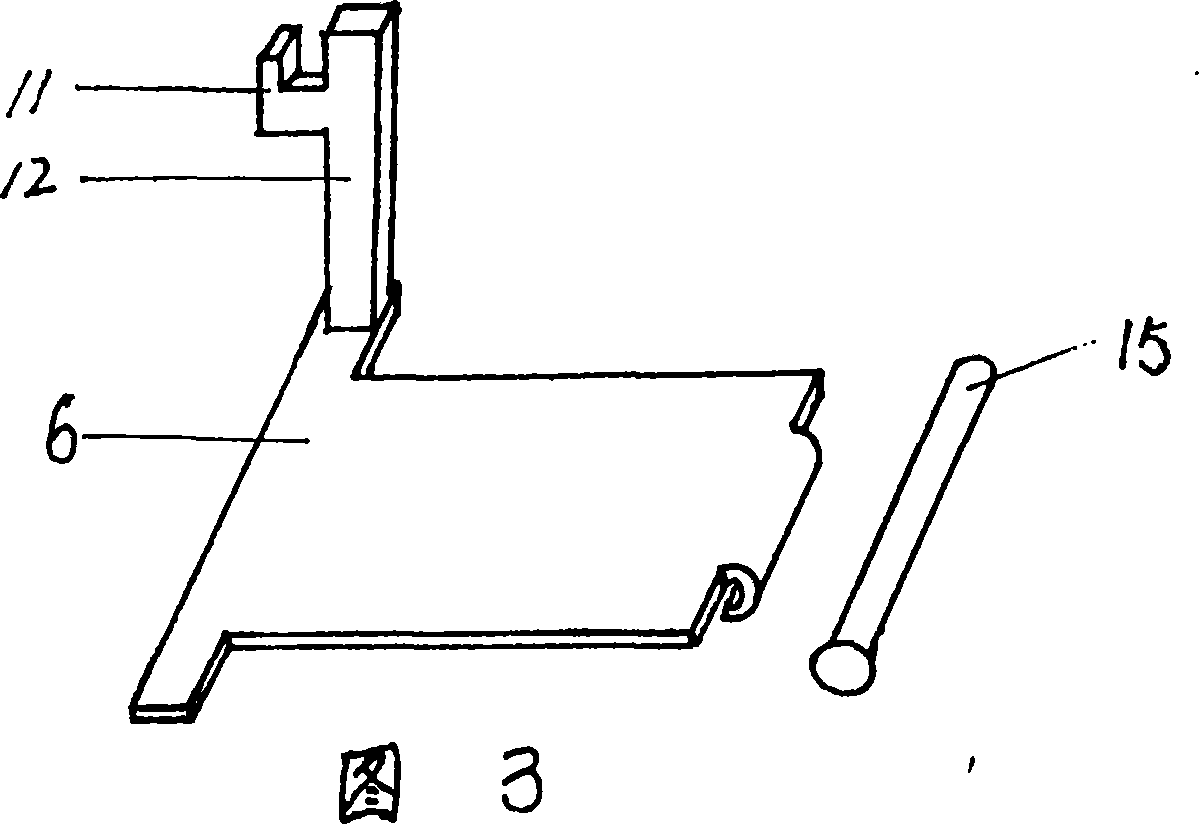
The invention relates to a unidirectional fence door, comprising door, closing tube, door shaft, bottom plate, stop block, foot board, compressing spring, hanging column, hook, torsion spring and live shaft. When humans go away through the fence, at first they can tread the foot board and make the position of foot board moves downward. So stop block and hook so on, which formerly make door close tightly, are set in opening status. Then they go out by pushing door. Opened door is returned in the closed status under the force of torsion spring after outer force is removed. Here the compressing force to foot board by the stop block is removed. Under the force of compressing spring, the foot board is returned to the highest position and the hook moves upward to enter into the hanging hole at the edge of door. In this way, only when humans in fence tread the foot board, the door can be opened. But outer humans can not pull the door to enter in. so it is provided with the unidirectional passing performance and can prevent human entering from the export randomly.
Owner:熊德
Canteen consumption supervision system based on face recognition
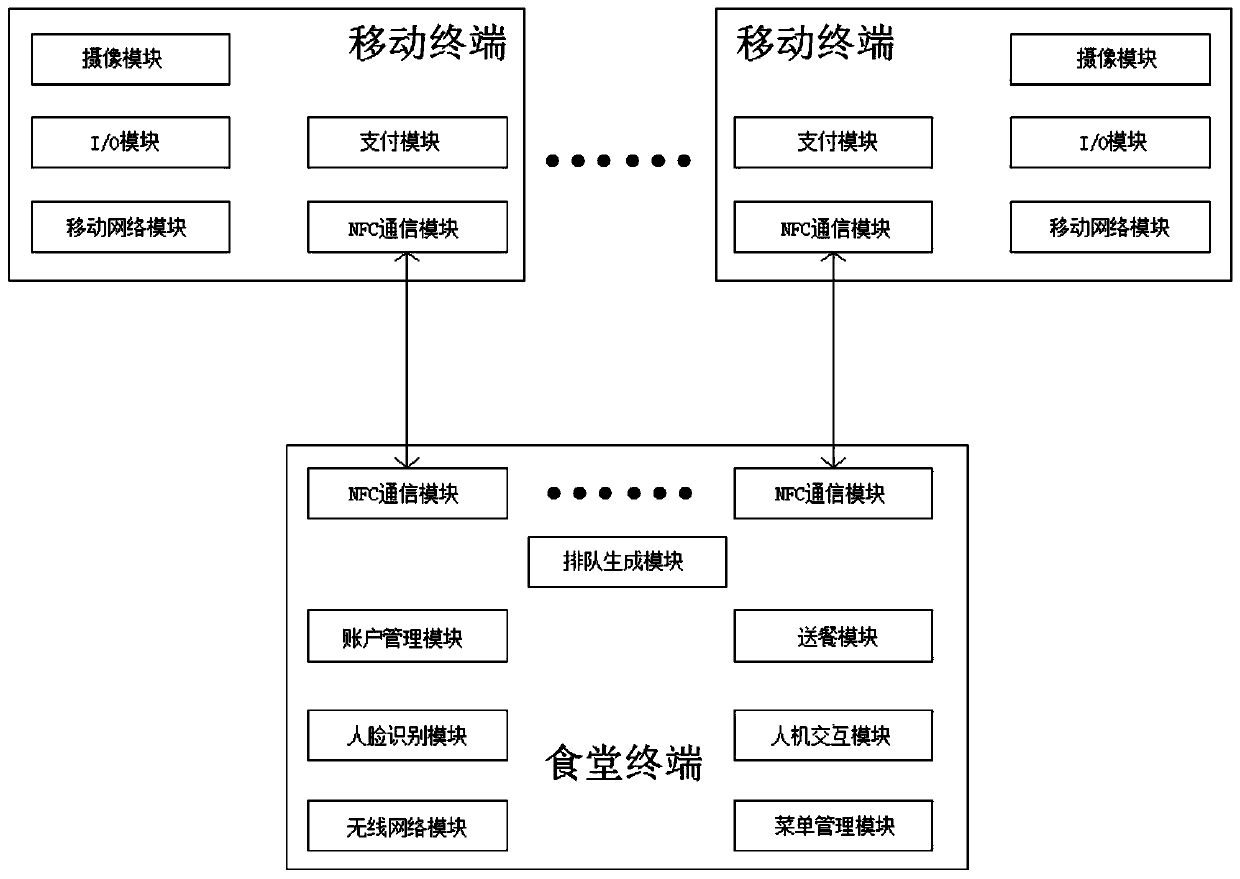
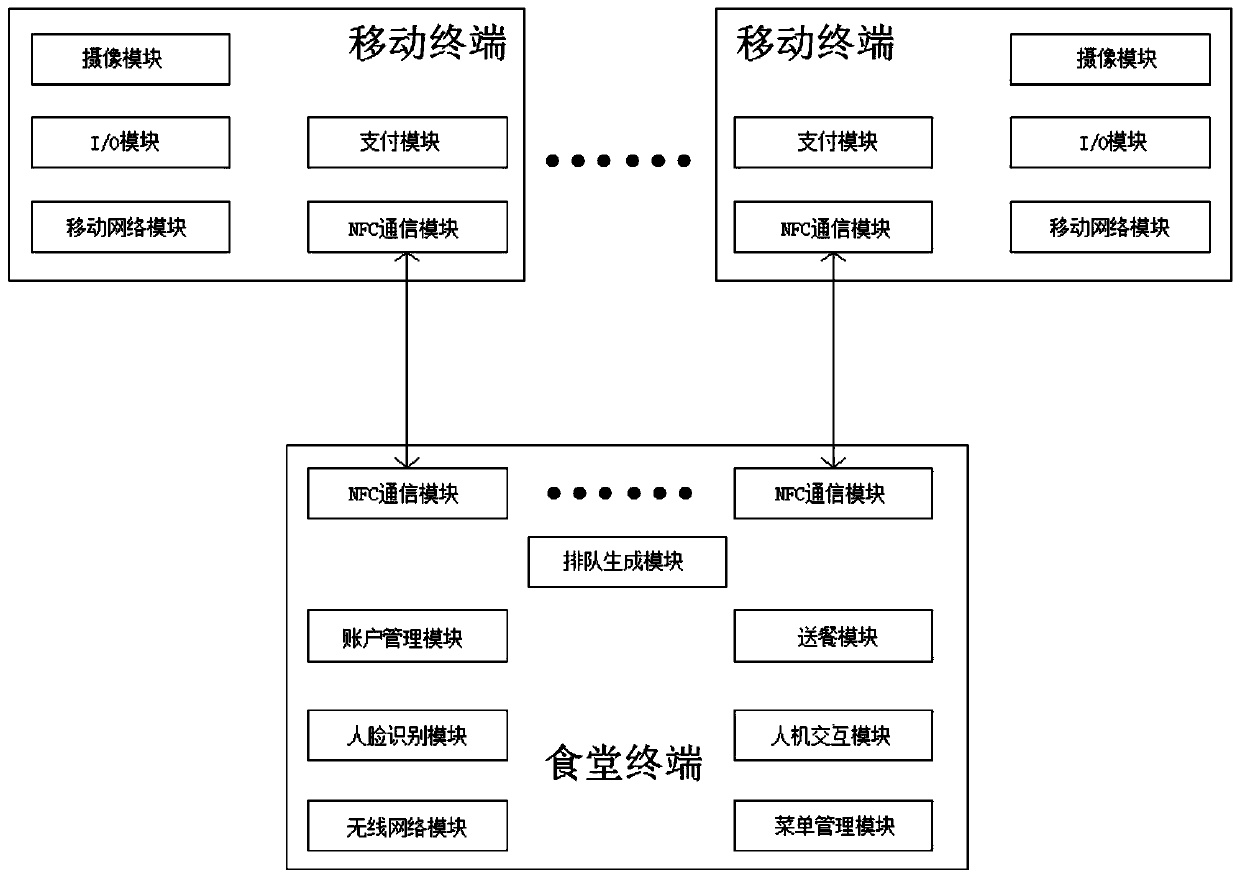
InactiveCN109961378ASmooth transmissionFast transferCo-operative working arrangementsPayment architecturePaymentRush hour
The invention discloses a canteen consumption supervision system based on face recognition, which comprises mobile terminals and canteen terminals arranged in a canteen, wherein the mobile terminals and the canteen terminals are equipped and used by users, and payment efficiency is improved through an NFC communication module. Through the queuing production module, queuing digitization can be realized, and in cooperation with other modules, a series of steps of vegetable selection, payment, waiting for vegetable distribution and recharging are completed only through the mobile terminal, so that the problems of poor queuing order, crowded people in rush hours and the like of a canteen are solved, and the dining experience of a user is improved. Personnel entering is controlled through the face recognition technology, non-dinning personnel are prevented from entering the canteen at will, multi-user simultaneous food ordering is achieved by using the digital menu, the food ordering time is shortened, the payment efficiency is improved, the average dining time is shortened, the reception amount of the canteen is increased, and the problem of order chaos caused by queuing in the peak period is solved.
Owner:合肥浮点信息科技有限公司
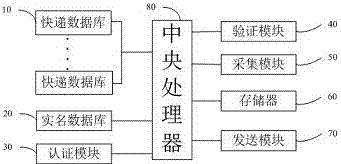
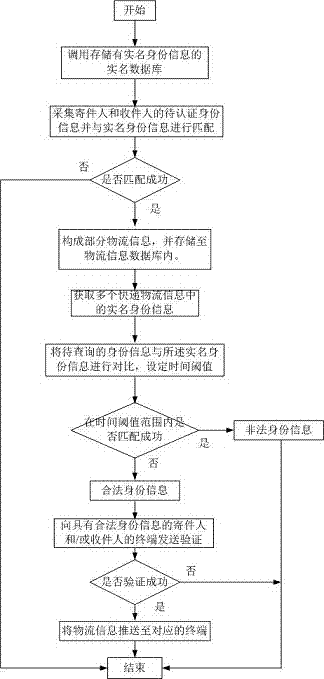
Real-name system logistics information management method and system
The invention discloses a real-name system logistics information management method. The method comprises steps that the logistics information of multiple express deliveries is acquired, and the logistics information at least comprises the real-name identity information of senders and addressees; the to-be-queried identity information is compared with the real-name identity information, a time threshold is set, if the to-be-queried identity information is successfully matched with the real-name identity information within the set time threshold, the to-be-queried identity information is determined to be the legal identity information; if matching surpassing the set time threshold is not successful, the to-be-queried identity information is determined to be the illegal identity information; verification messages are sent to the senders and / or the addressees having the legal identity information, if verification is qualified, the logistics information is pushed to corresponding terminals. The invention discloses a real-name system logistics information management system for performing the management method, a real-name system of the senders and the addressees is realized, query efficiency is improved, and query privacy is protected.
Owner:MORAL ELECTRICAL APPLIANCE KUNSHAN
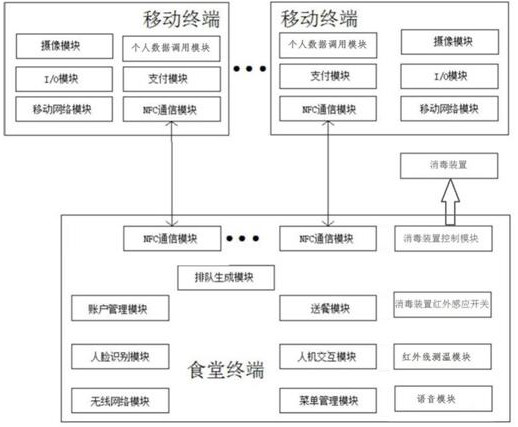
Canteen consumption supervision system based on face recognition
PendingCN112233307ARealize managementSmooth transmissionChecking apparatusCash registersCamera moduleHuman–computer interaction
The invention relates to a canteen consumption supervision system based on face recognition. The system comprises a mobile terminal used by users and a canteen terminal arranged in a canteen, whereinthe mobile terminal comprises a camera module, an I / O module, a mobile network module, a payment module, an NFC communication module and a personal data calling module, the personal data calling module comprises personal health code information and personal face recognition data; the canteen terminal comprises a queuing generation module, a man-machine interaction module, a menu management module,a voice module, an account management module, a wireless network module, a meal delivery module, face recognition modules arranged at an exit and an entrance of a canteen, an infrared temperature measurement module, a disinfection device infrared induction switch and a disinfection device control module. The system further comprises a two-dimensional code arranged at the entrance of the canteen and used for information association. The system is advantaged in that problems of detecting whether a mask is worn or not, scanning a health code for authentication, measuring the body temperature, disinfecting with alcohol, selecting dishes in a canteen, paying, waiting and the like are solved.
Owner:云南乐进科技有限公司
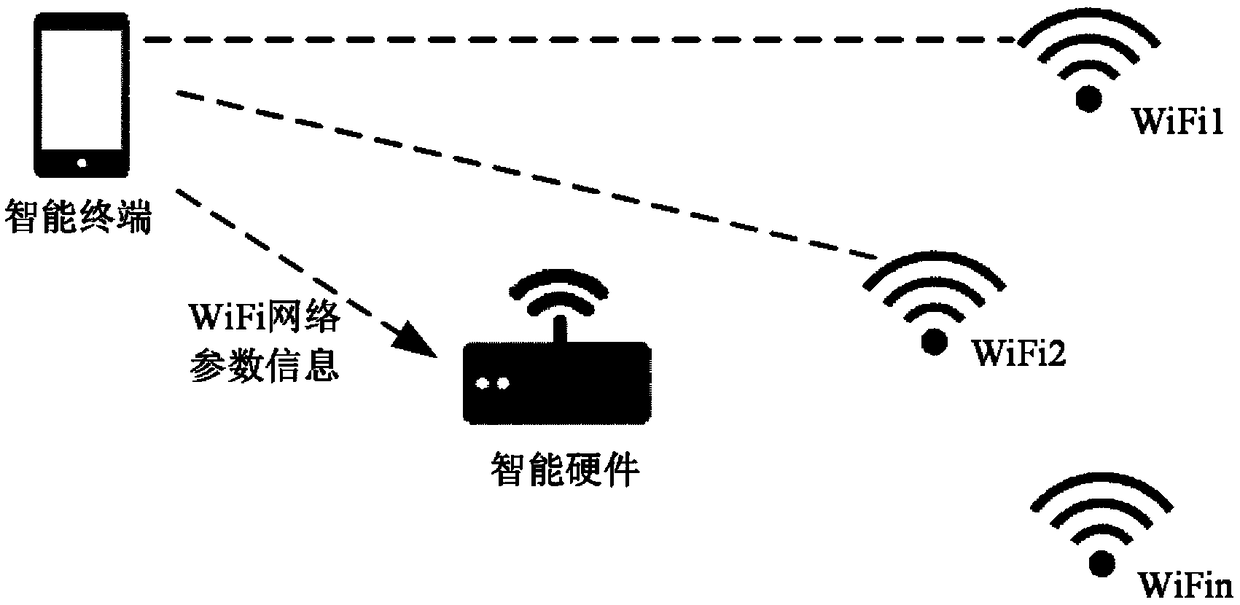
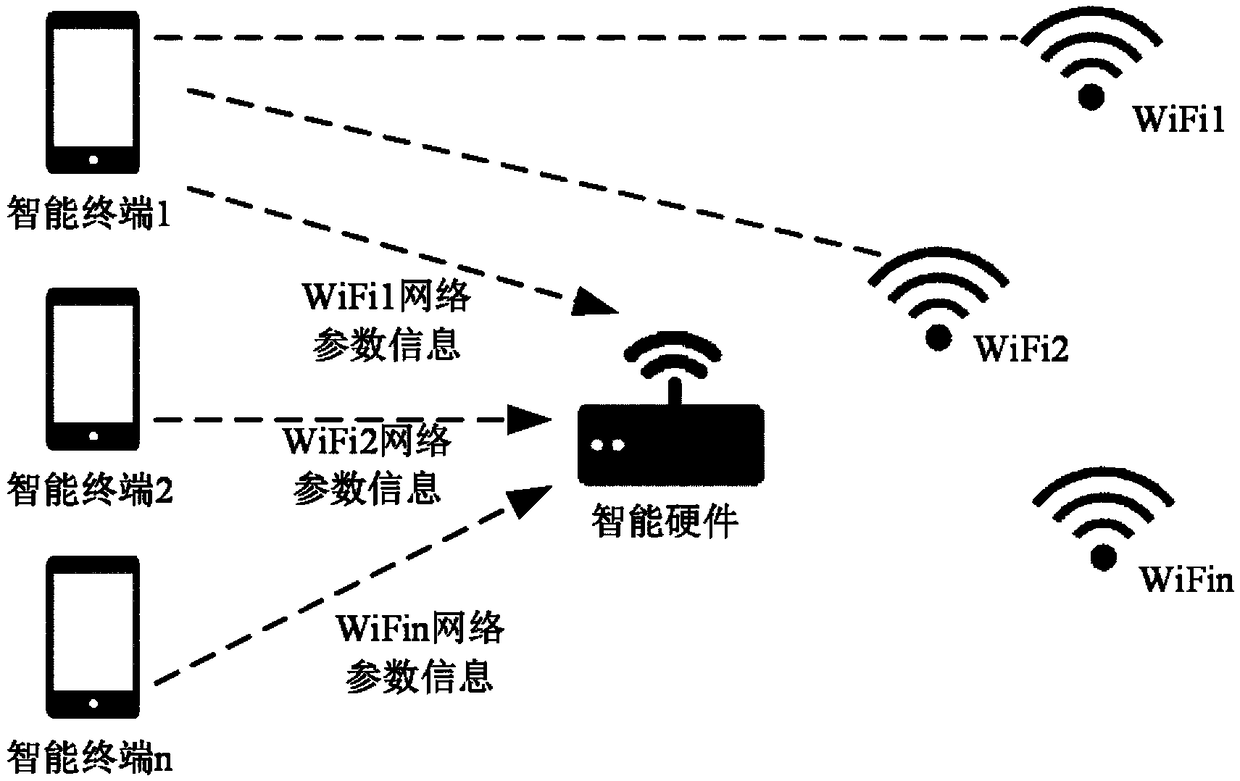
Intelligent hardware networking method, intelligent terminal and intelligent hardware
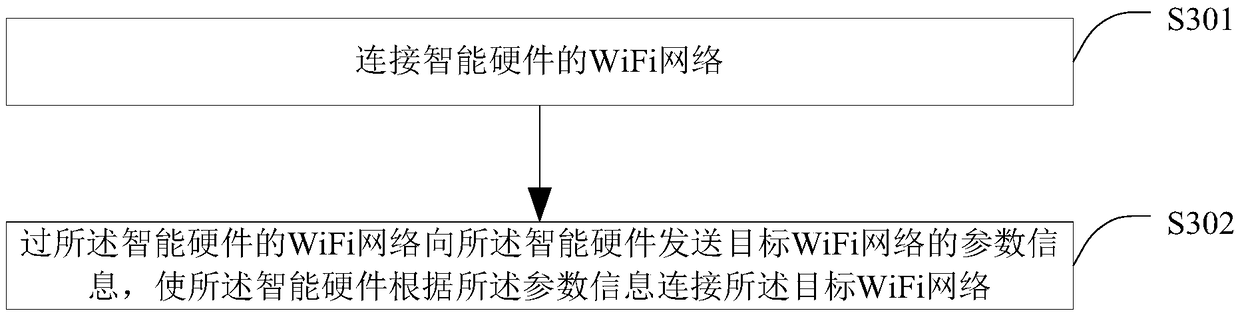
InactiveCN108882339AImprove accuracyAvoid blind acceptanceAssess restrictionTransmissionPasswordWifi network
The invention provides an intelligent hardware networking method, an intelligent terminal and intelligent hardware. The intelligent hardware networking method is applied to the intelligent terminal, and comprises the following steps: connecting a WiFi network of the intelligent hardware; sending parameter information of the target WiFi network to the intelligent hardware through the WiFi network of the intelligent hardware, thereby enabling the intelligent hardware to connect the target WiFi network according to the parameter information, wherein the parameter information comprises a network name and network password information. By adopting the above technical scheme, the intelligent hardware can precisely access to the predetermined WiFi network.
Owner:天津和合科技有限公司
Internet of things physical signal setting method and device and computer readable storage medium
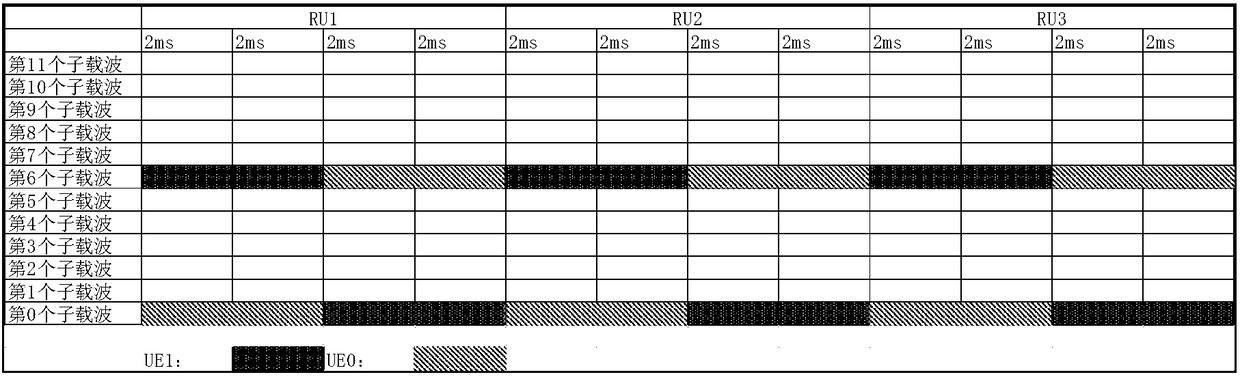
ActiveCN109088708AContinuous transmissionAvoid random accessSynchronisation arrangementSignal allocationThe InternetUser equipment
The invention provides an Internet of things physical signal setting method and device and a computer readable storage medium. The method includes the following steps: setting each RU in a signal-tonesignal as a set number of transmission durations; and determining a subcarrier frequency for transmitting the single-tone signal within each transmission duration in the EU by taking a preset range of a subcarrier frequency internal of the single-tone signal transmitted with the adjacent transmission durations in the RU within a range of the subcarrier transmitting the single-tone signal according to scheduling of the subcarriers in a NB-IoT. The Internet of things physical signal setting method and device can transmit the single-tone signal by frequency hopping, and so a NB-IoT base stationcan estimate time offset of an uplink service channel, the NB-IoT base station can be ensured to feed back uplink timing advance to user equipment in real time, the user equipment can be effectively ensured to continuously transmit data in a mobile scene, and the user equipment can be effectively prevented from initiating a novel round of random access. The single-tone signal transmitting by the frequency hopping effectively improves the ability of anti-multipath fading of uplink signal-tone signal transmission and suppresses co-frequency interference.
Owner:ZTE CORP
Classification type medicine storage cabinet capable of automatically rotating and using method thereof
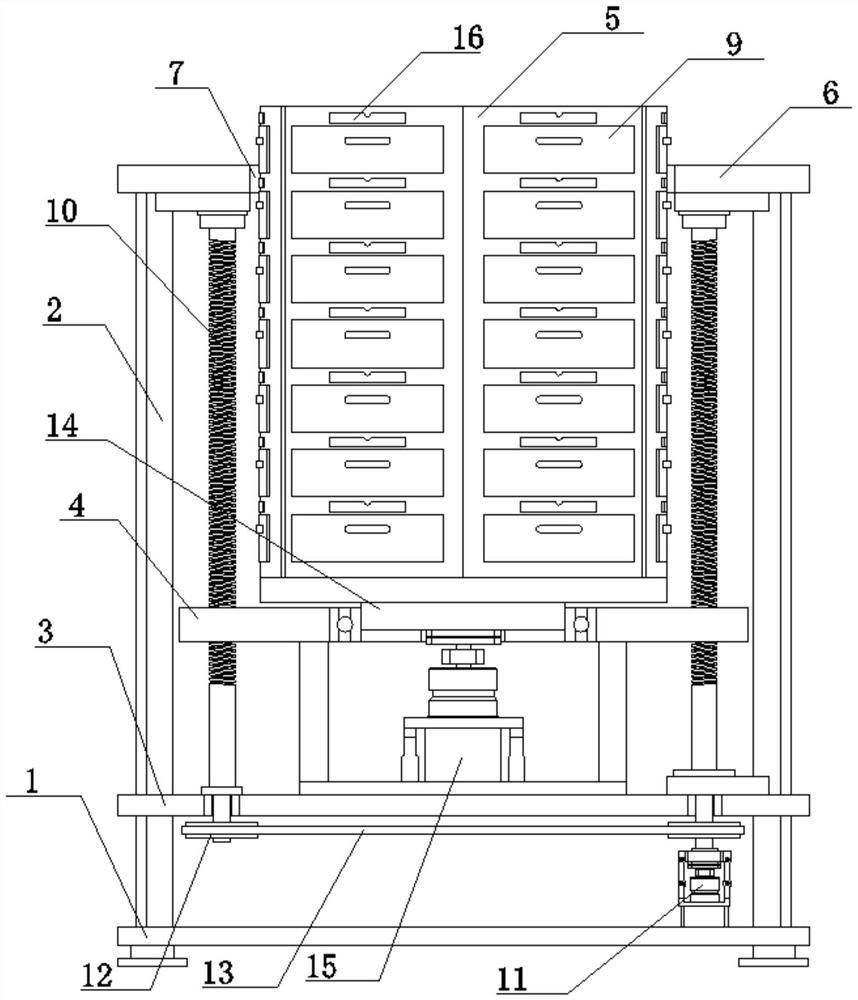
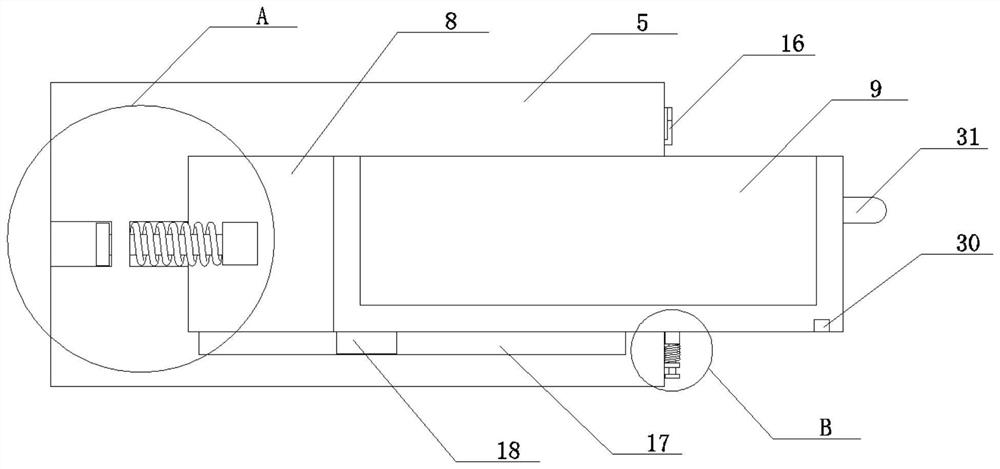
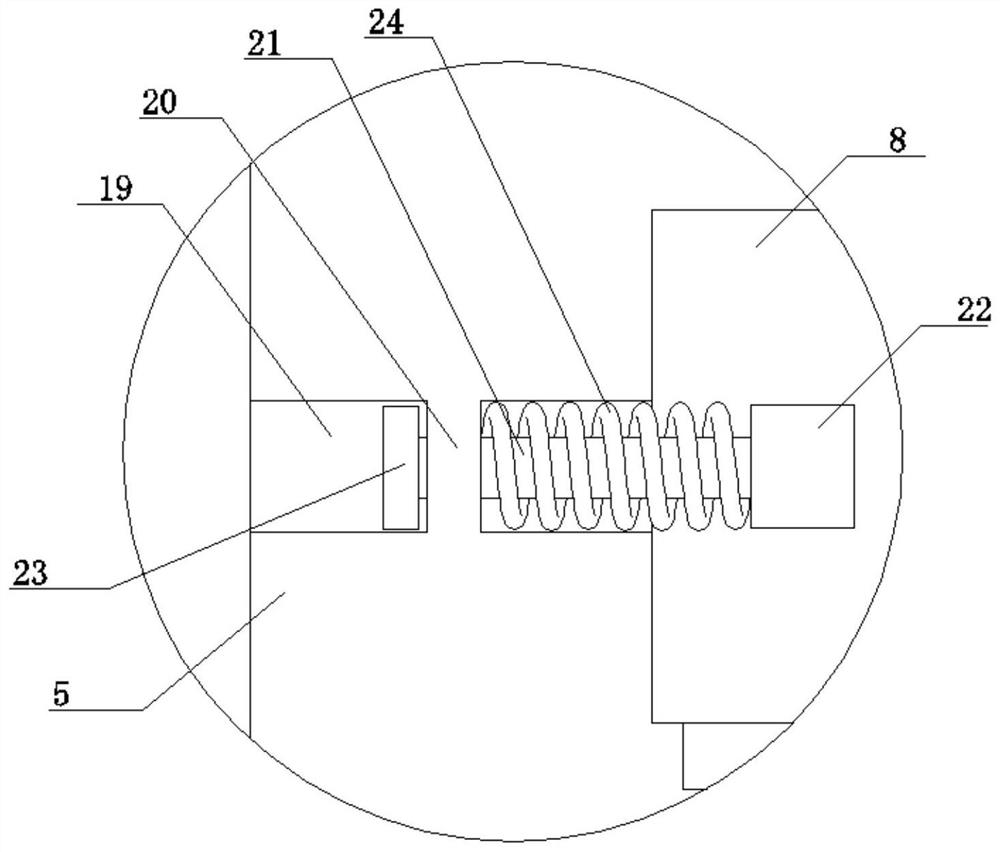
InactiveCN111887617AAvoid random accessPlay a protective effectChestsDressing tablesMedicinal herbsEngineering
The invention discloses a classification type medicine storage cabinet capable of automatically rotating and a using method thereof. The classification type medicine storage cabinet includes a base, and the upper surface of the base is fixedly connected with a fixed frame. The lower part of the fixed frame is fixedly connected with a fixed seat; the fixed seat is positioned above the base; a height adjusting assembly is arranged on the fixed seat; the height adjusting assembly is connected with a moving seat; the upper surface of the moving seat is fixedly connected with a cabinet body; a rotating assembly is arranged on the moving seat, a top plate is fixedly connected to the top end of the fixed frame, an opening is formed in the surface of the top plate and matched with the cabinet body, the cabinet body is an octahedral cabinet body, a plurality of containing cavities are formed in the surfaces of all the side faces of the cabinet body, drawing drawers are slidably connected into the containing cavities, and fixing assemblies are arranged between the drawing drawers and the containing cavities. By arranging the height adjusting assembly, the height of the cabinet body can be flexibly adjusted, the cabinet body is lifted through the height adjusting assembly when medicinal materials are not taken, it can be avoided that non-medical staff take the medicinal materials at will,the protection effect is achieved, and the cabinet body can be rapidly descended through the height adjusting assembly when the medicinal materials are taken.
Owner:湖州天启家居科技有限公司
Transformer substation entrance guard system
InactiveCN105894626AImprove management levelAvoid random accessIndividual entry/exit registersManagement unitTransformer
The invention discloses a transformer substation entrance guard system, belongs to the technical field of transformer substations and aims to achieve the purpose of providing an entrance guard system which is simple in structure and can prevent equipment polling people from entering a transformer substation at will. According to the technical scheme, the transformer substation entrance guard system comprises an entrance guard controller and an entrance guard management control host, wherein the entrance guard controller is arranged at an entrance of a machine room in the transformer substation and connected with a door lock, and the entrance guard management control host is arranged at a remote control center. The entrance guard system further comprises a duty management host which is used for arranging work for operators on duty according to the actual situation of the transformer substation and sending the information of the operators on duty on the current date to the entrance guard management control host. The entrance guard management control host comprises an entrance guard management unit used for arranging control for the entrance guard controller according to the information, sent by the duty management host, of the operators on duty. The entrance guard controller comprises an information collection unit, a processor and a blocking device.
Owner:杨晓斌
Method for efficiently extracting flavone from ginkgo leaves and converting flavone into aglycon flavone
InactiveCN107158048AImproved mass transfer propertiesAvoid random accessGinkgophyta medical ingredientsPlant ingredientsVitis viniferaFreeze-drying
The invention relates to a method for efficiently extracting flavone from ginkgo leaves and converting flavone into aglycon flavone. Ginkgo leaves are washed clean and ground, the ginkgo leaves are mixed with water, loaded into a fermentation tank and sterilized under 121 DEG C, and steam explosion is then carried out; aspergillus niger is then added for fermentation; mixed enzyme solution is then added, the added amount is 2 to 5 percent of reaction substrate, and the time of reaction under the condition of 25 DEG C to 30 DEG C is 3 to 6 hours; Beta-glucosidase is then added, the added amount is 1 percent of the reaction substrate, the reaction condition is that pH is 4.3 under the condition of 42 DEG C, and the reaction time is 5 hours; 1 percent of protease is then added, and the time of reaction under the condition of 25 DEG C to 30 DEG C is 3 to 4 hours; temperature is increased to 95 DEG C for 10 minutes, extractant is then added to extract flavone, 12000g centrifuging is carried out for 20 minutes, supernatant is extracted and concentrated, ethanol is then adopted for extraction, so that ethanol eluent is obtained, the ethanol eluent is concentrated, freeze-drying is adopted, and thereby the product is obtained.
Owner:HUNAN UNIV OF SCI & ENG
Intelligent door lock control equipment, method and system
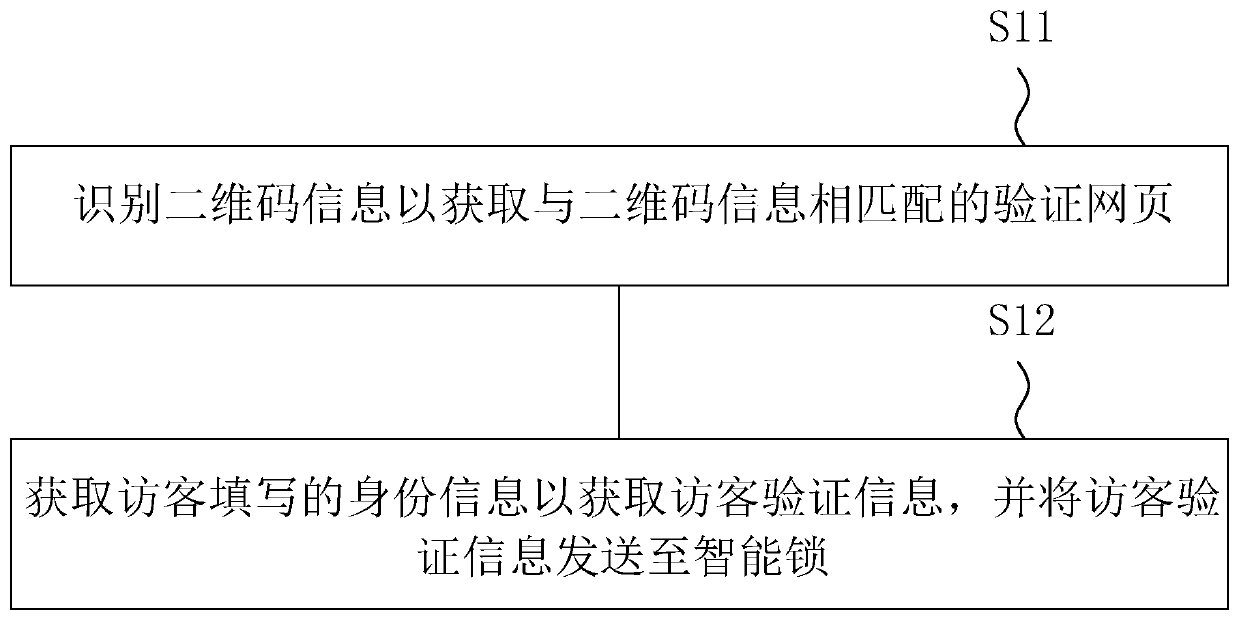
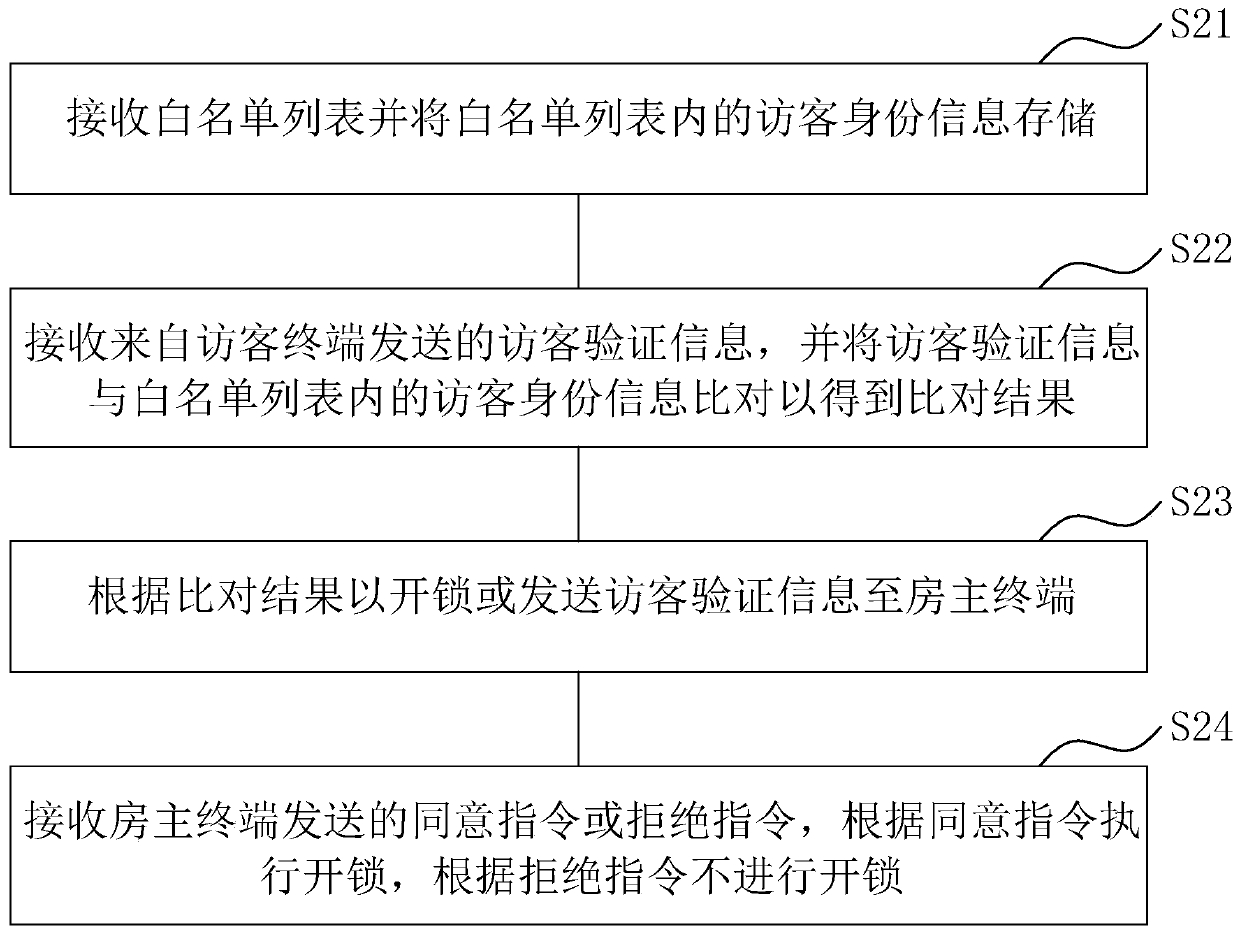
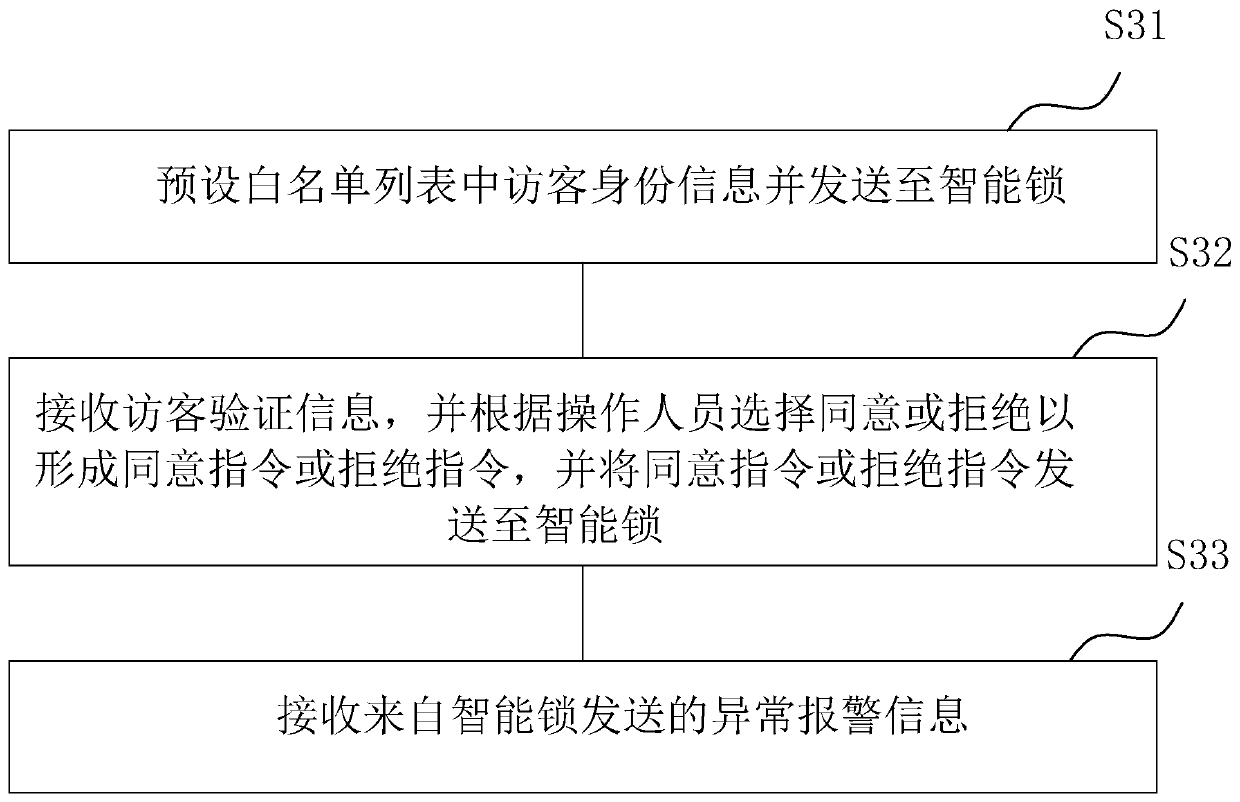
InactiveCN111260831AImprove convenienceEasy to unlockIndividual entry/exit registersSoftware engineeringWeb page
The invention discloses an intelligent door lock control device, method and system. The method is executed by a visitor terminal and comprises the following steps: identifying two-dimensional code information to obtain a verification webpage matched with the two-dimensional code information; and obtaining identity information filled by a visitor to obtain visitor verification information, and sending the visitor verification information to an intelligent lock. According to the invention, the visitor inputs the identity information after scanning a two-dimensional code such that the visitor verification information corresponding to the identity information is verified and then unlocked, the visitor can finish unlocking only by scanning and filling in the identity information, and the unlocking entering convenience of the visitor is improved.
Owner:深圳桔子智能科技发展有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com