Method, user equipment and packet access gateway for secure access to Internet services
An Internet business and secure access technology, applied in the field of secure Internet access business, can solve privacy issues, user security and privacy threats, without considering user security issues, etc., to enhance security, prevent random access, improve safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
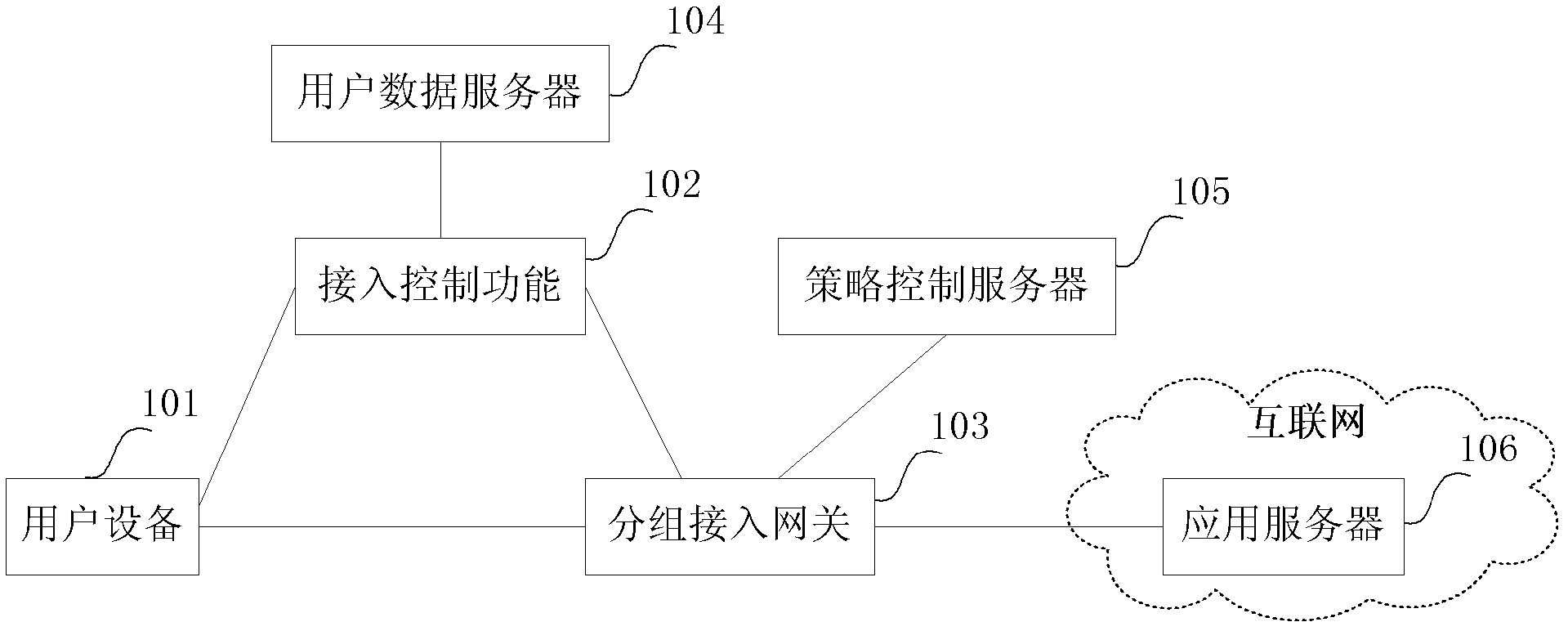
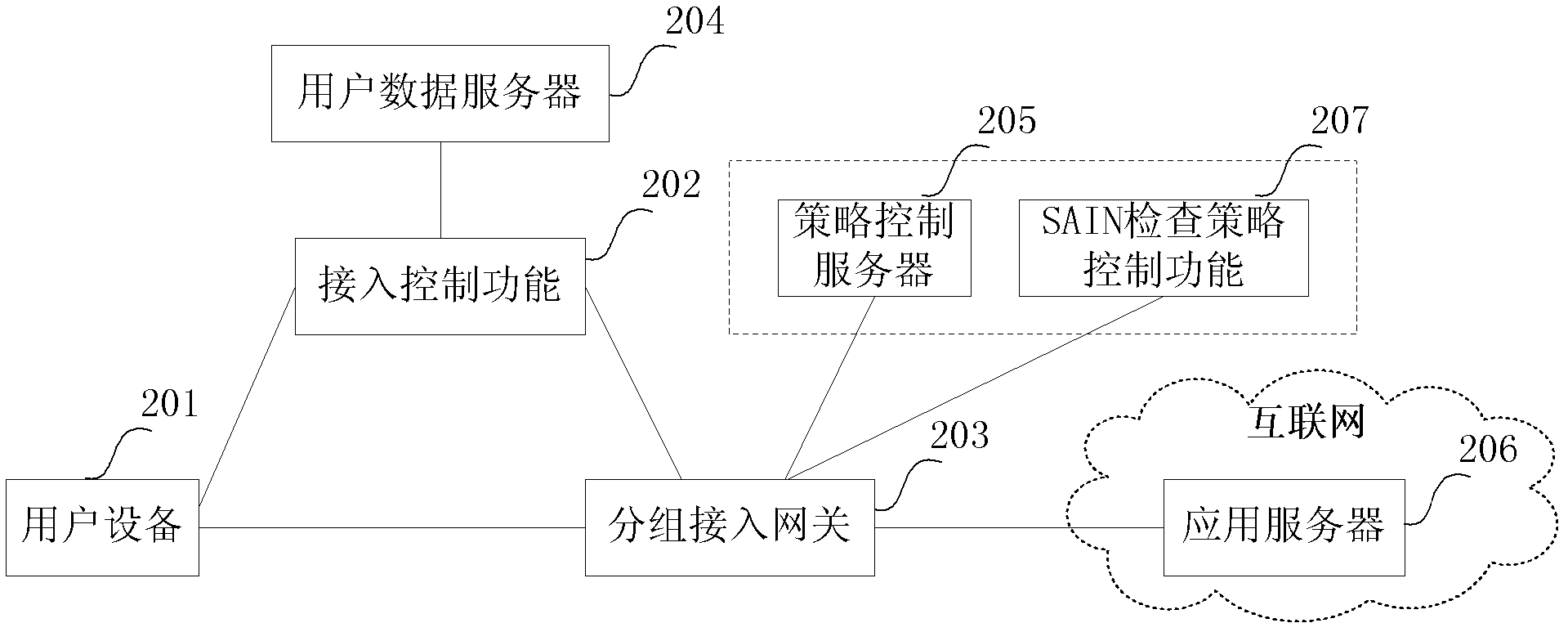
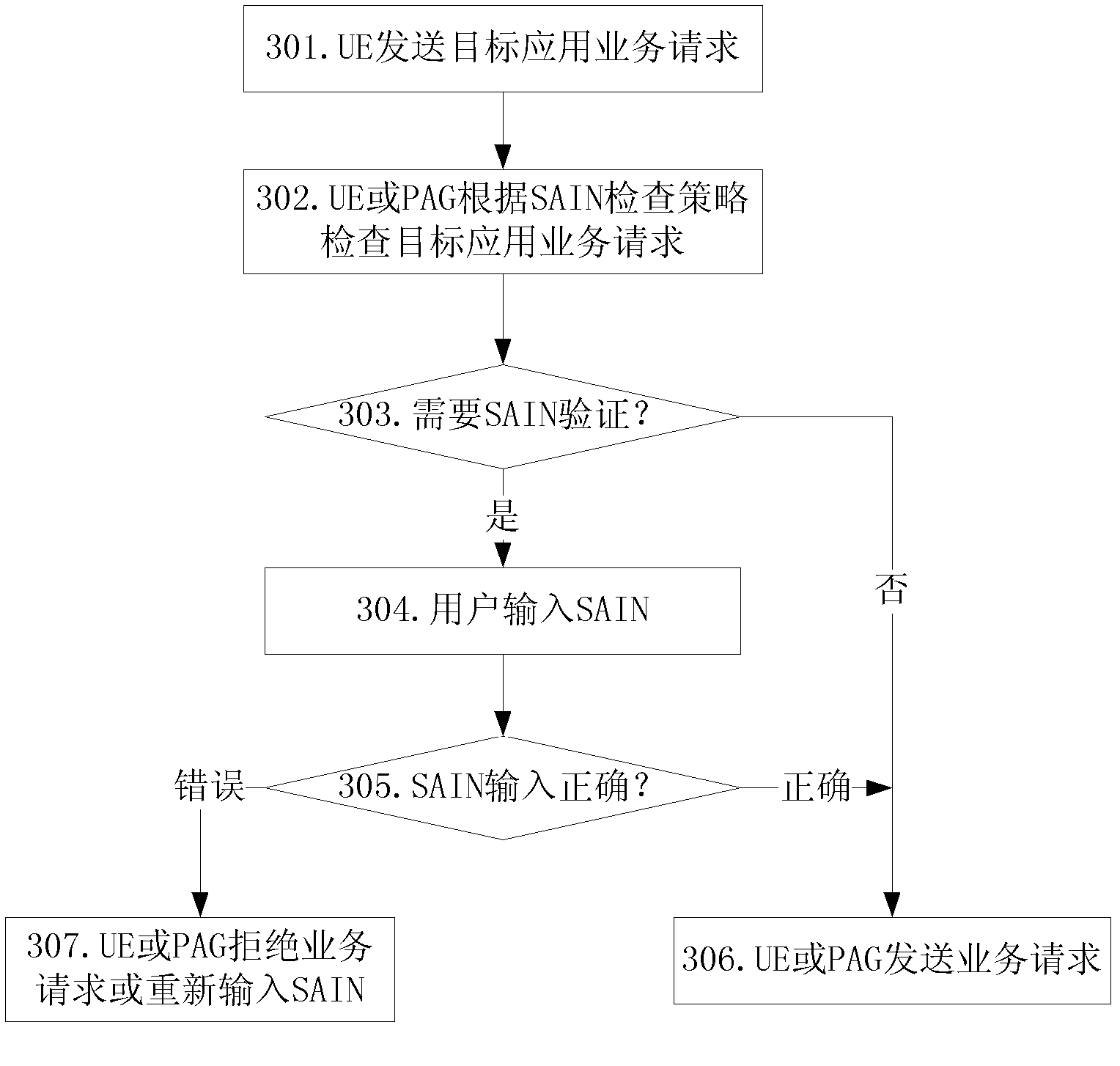
[0060] In order to meet the needs of users to access the Internet safely, the present invention introduces a Security Access Identification Number (SAIN for short). SAIN can be a string of readable character strings, consisting of numbers, English letters, and some Read symbols (such as "*", "!", etc.). According to the security requirements, set the SAIN check policy on the UE side or the network side. When the user uses the Internet service, the SAIN check point such as the UE or packet access network checks the user's service request according to the SAIN check policy. When it is found that the user accesses a specific target application That is, when the data flow corresponding to the service request needs to be protected by SAIN, the user is required to input SAIN on the user equipment, and only when the SAIN input by the user is correct, the SAIN checkpoint allows the user equipment to access the target application. In this way, the security of Internet access services i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com