A method and system for realizing DSN content service access security
A technology for content access and business access, applied in the field of communications, can solve problems such as the inability to prevent a large number of illegal accesses, denial of service, and low service efficiency of business systems, and achieve the effect of ensuring access security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
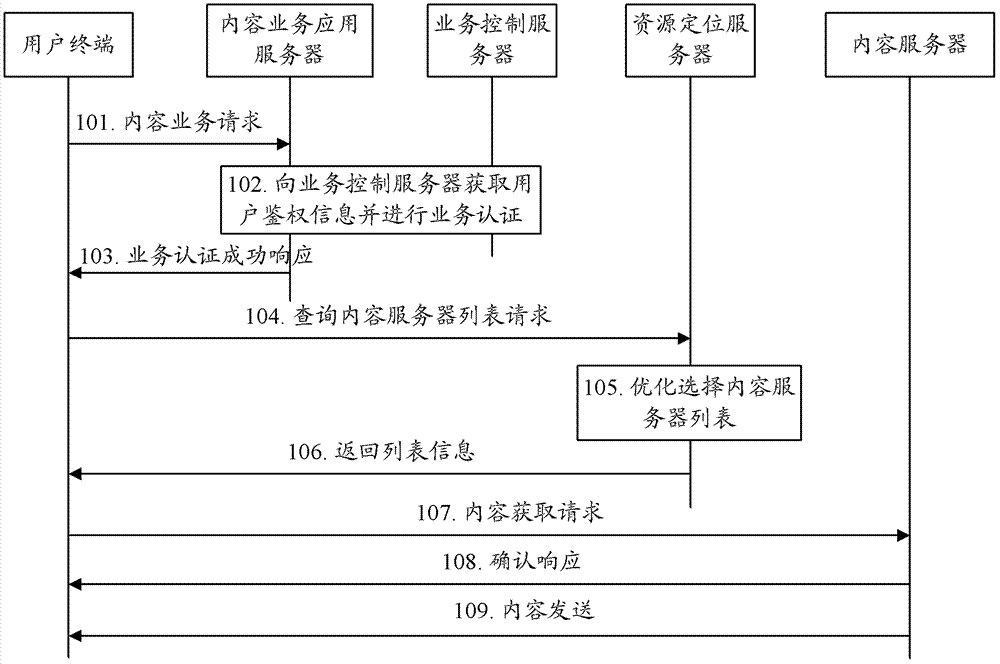
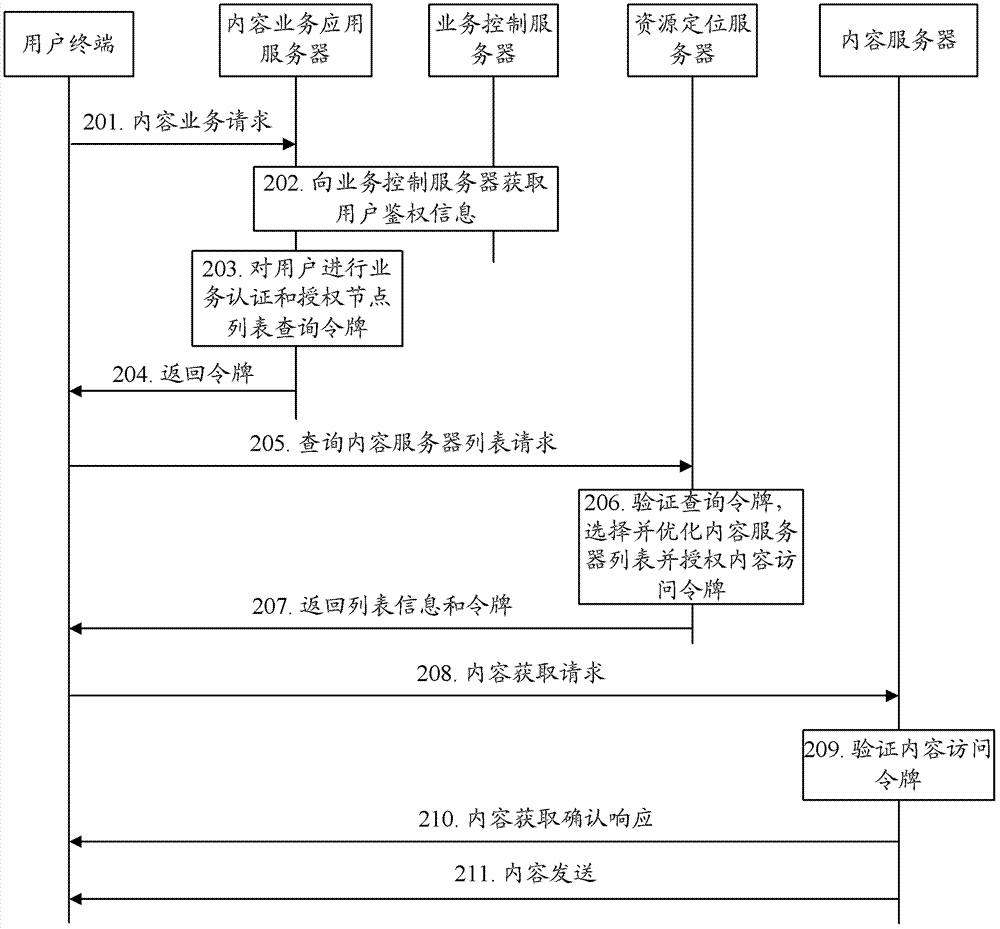
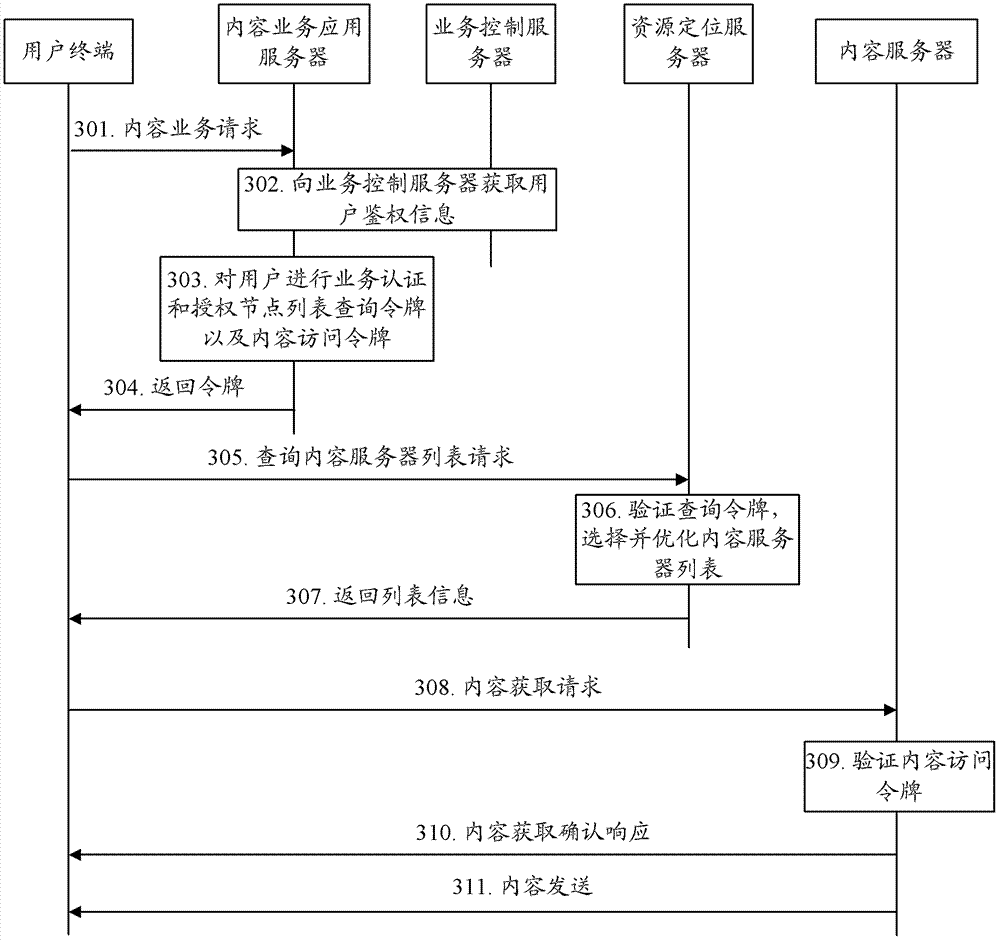
[0052] In practical applications, the content service application server may authorize the content server list query token (token) and the content access token for the user terminal, or the resource location server may authorize the content access token for the user terminal. For the convenience of description, the content server list query token is referred to as query token for short below.
[0053] When the user terminal queries the content server list, the resource location server verifies the query token of the user terminal, and allows the user terminal to obtain content from the content server after the verification is passed. When the user terminal obtains the content resource of the content server, the content server verifies the content access token of the user terminal, and provides the content resource to the user terminal after passing the verification, thereby ensuring the access security of the content service.
[0054] It can be seen that it is necessary to car...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com