Bidirectional anonymous authentication system and method based on mimicry defense principle
An anonymous authentication, anonymous authentication protocol technology, applied in the field of two-way anonymous authentication system, can solve the problems of poor network information security, DAA anonymous authentication can not be actively defended and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention discloses a two-way anonymous authentication system and method based on the mimic defense principle. The scheme will be further described and explained below in conjunction with the accompanying drawings.
[0055] The symbols and their definitions used in this scheme are shown in Table 1;
[0056]
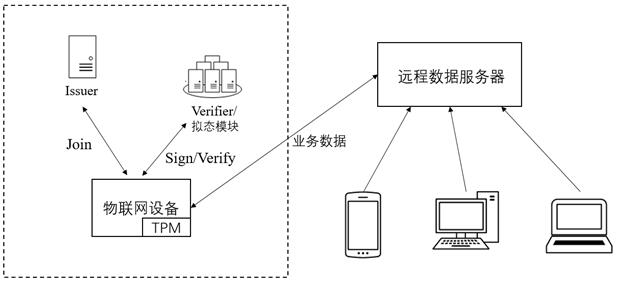
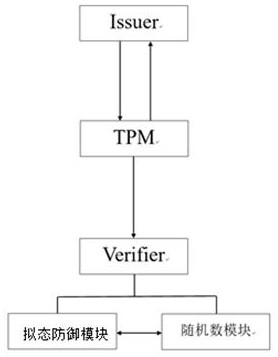
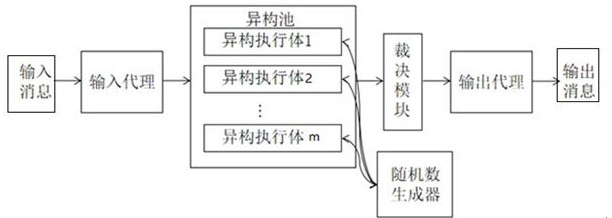
[0057] This solution includes the issuer of the certificate, the signer, the signer, and the signature checker Verifier. The signer is also called the platform platform. The platform platform can be divided into: the host host and the trusted computing platform module TPM.
[0058] The basic principles involved in this program are as follows:
[0059] 1) CL signature: CL signature is Camenisch-Lysyanskaya signature. It is used in group signature or aggregate signature scenarios to improve the anonymity of the signature and reduce the computational complexity of the signature. CL signature is also a signature scheme suitable for zero-knowledge proof, which can s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com