Network access control method with system health detection prior to access
A technology of health detection and network access, which is applied in transmission systems, wide area networks, security devices, etc., can solve the problems of verifying the legal identity of end users and the lack of security, so as to improve access verification performance and avoid viruses or Effects of hacker attacks and ensuring access security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
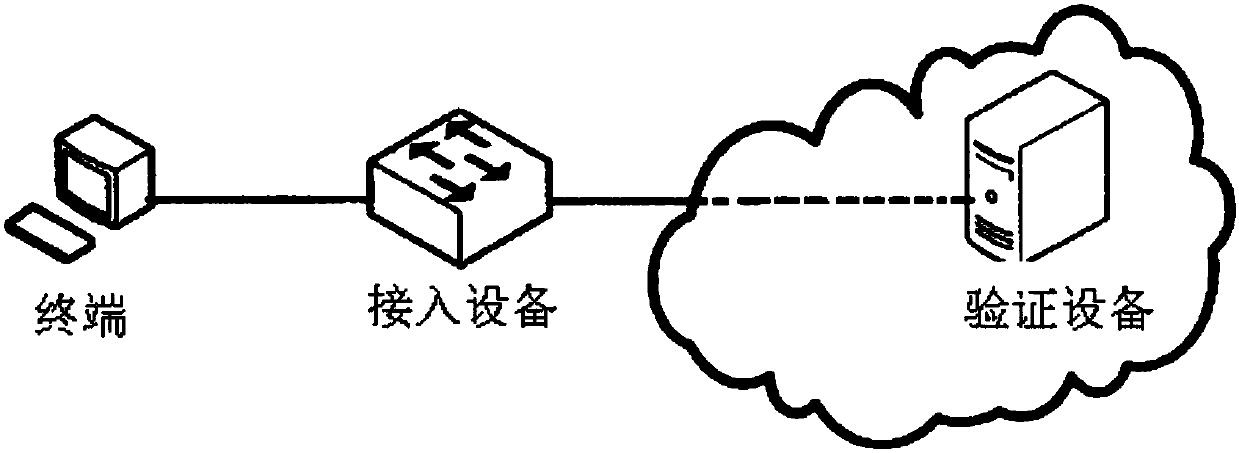
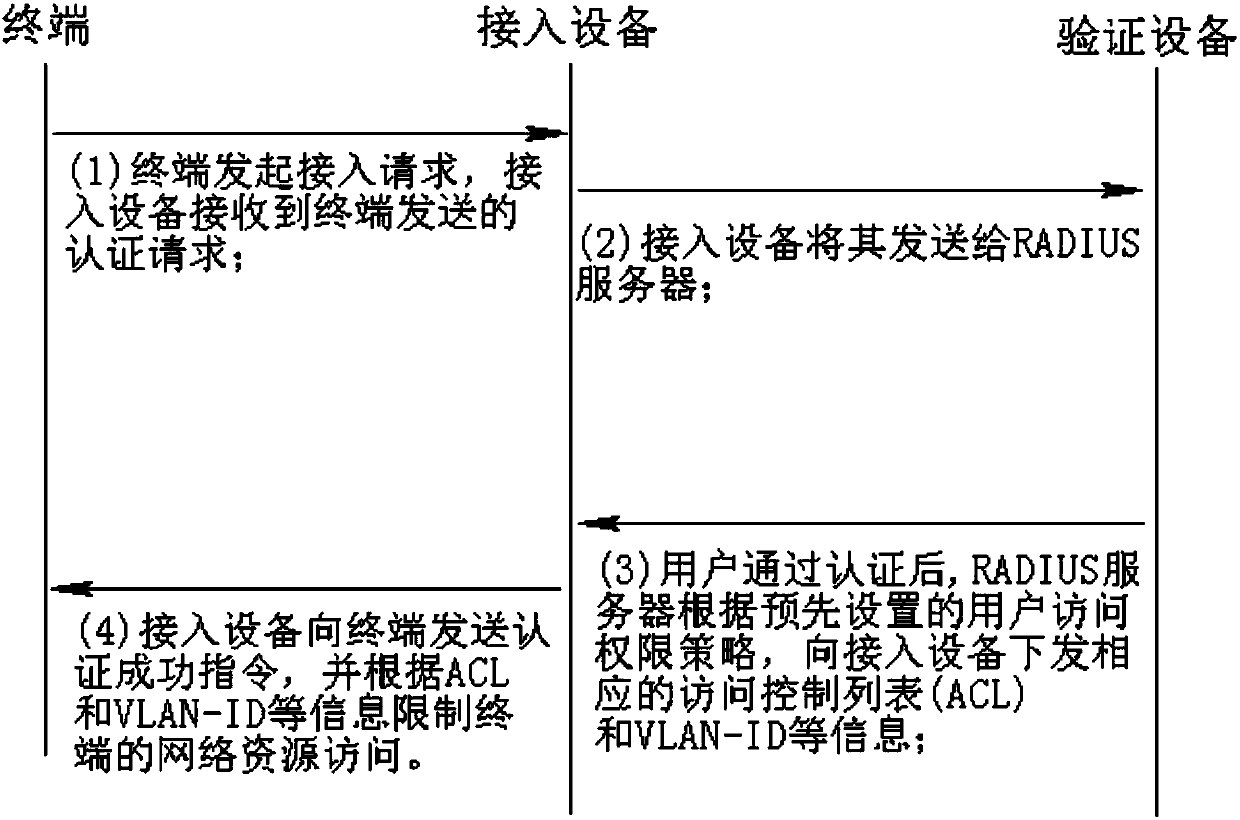
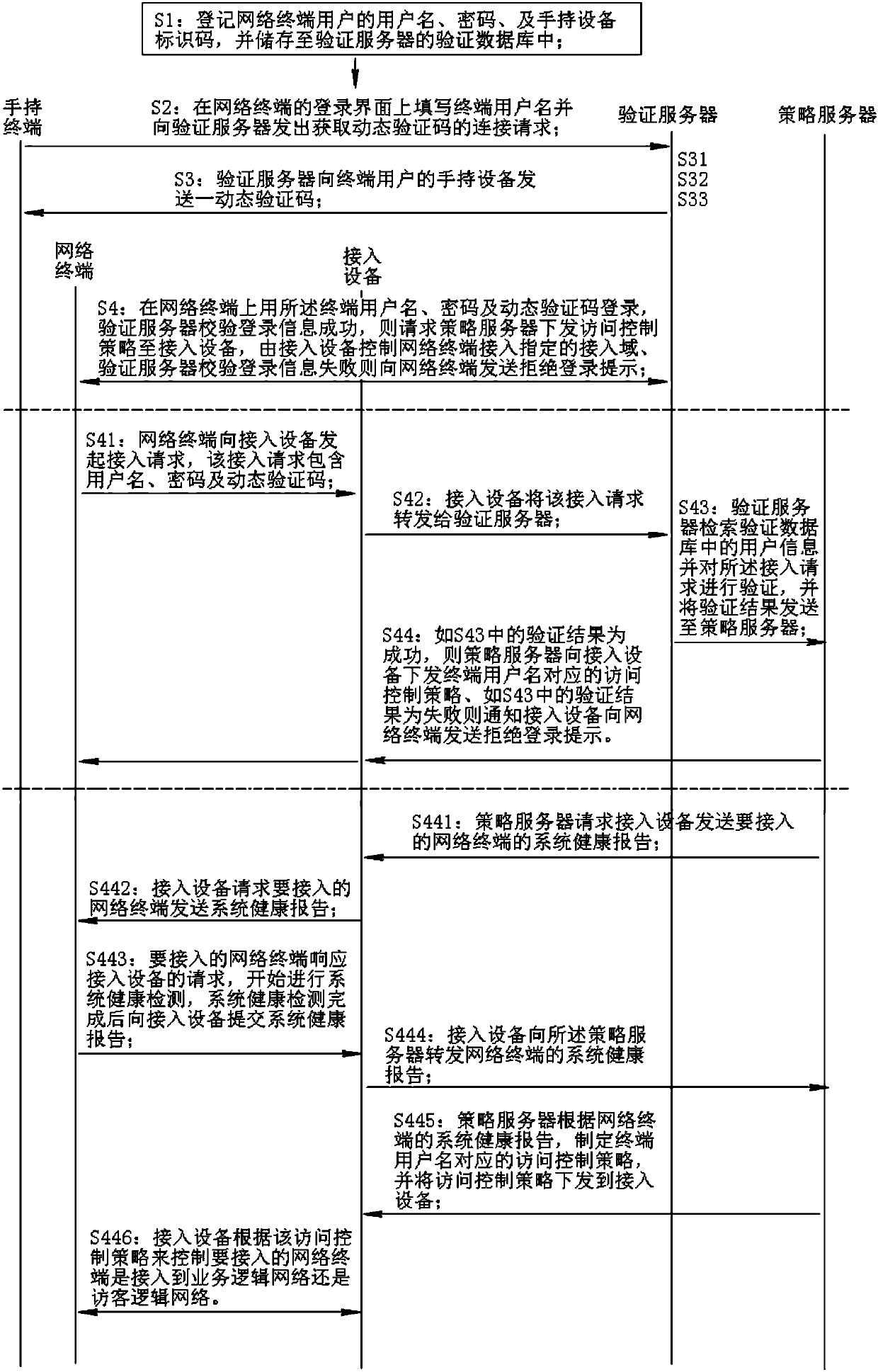
[0044] Please also see Figure 1 to Figure 7 , figure 1 It is a schematic diagram of a network connection using the RADIUS protocol for terminal access verification in the prior art, figure 2 It is a schematic diagram of signaling for terminal access verification using the RADIUS protocol in the prior art, image 3 A schematic diagram of the signaling steps of the network access control method that performs system health detection before access in the present invention, Figure 4 The flow chart of the network access control method for performing system health detection before accessing in the present invention, Figure 5 yes Figure 4 The flowchart in S3, Figure 6 yes Figure 4 The flowchart in S4, Figure 7 yes Figure 4 The flow chart of the authentication server delivering the access control policy in the middle.
[0045]A network access control method of the present invention that performs system health detection before access, and its corresponding network topol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com