Wireless sensor network dynamic encryption method based on encryption parameter lists
A wireless sensor and dynamic encryption technology, applied in wireless communication, electrical components, security devices, etc., can solve the problems of increasing ciphertext length, large key volume, and difficult expansion and use, and achieve the goal of enhancing confidentiality and security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The preferred embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings; it should be understood that the various data and methods of this embodiment, the preferred embodiment is only a special example for illustrating the implementation method of the present invention, and is not intended to limit protection scope of the present invention.
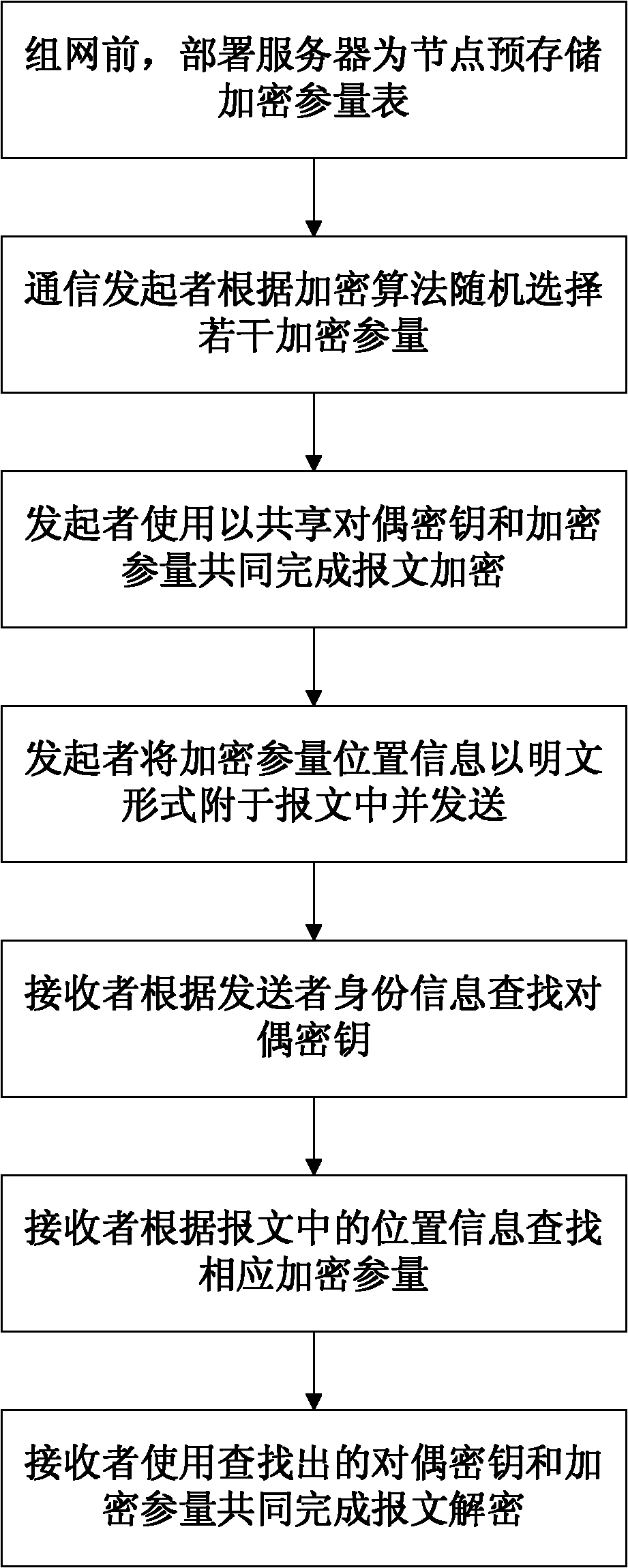
[0026] figure 1 The schematic diagram of the work control process provided by the embodiment of the present invention is shown in the figure: a dynamic encryption method for wireless sensor networks based on an encryption parameter table provided by the present invention includes the following steps:
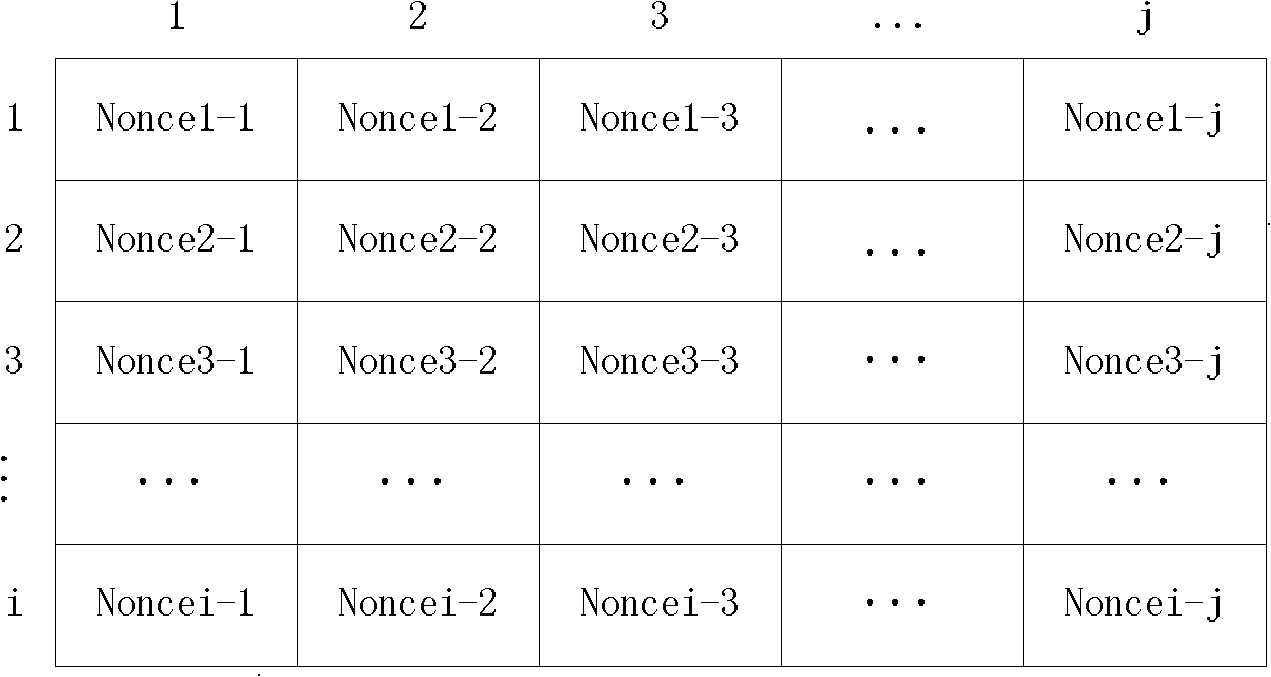
[0027] S1: Before networking, the deployment server sequentially stores the encryption parameter table for each node according to the node type; the location information of the encryption parameter is arranged according to the row order of the encryption parameter table, and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com