Terminal, server side, and terminal access management method
A terminal access and server-side technology, applied in the field of communications, can solve the problems of being easily attacked, downtime, and poor push request connection access security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
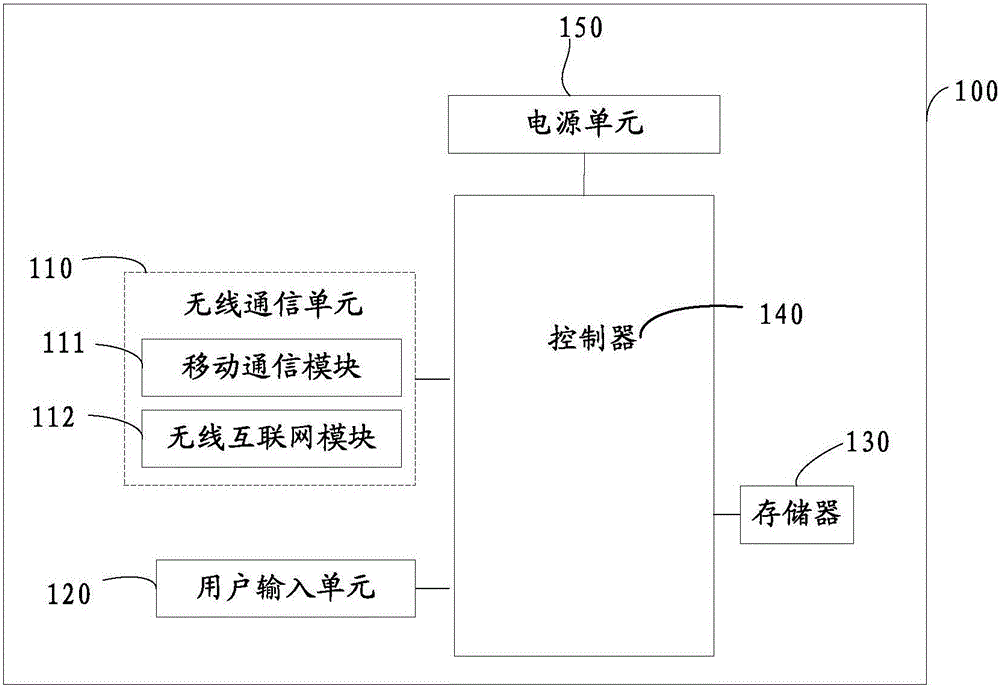
[0062] This embodiment proposes a terminal, please refer to image 3 , including: a first acquisition module 11, an encapsulation module 12 and a first sending module 13, the first acquisition module 11 is used to acquire a token from the server; the encapsulation module 12 is used to encapsulate the information containing the token into an access request message ; The first sending module 13 is used to send the access request message to the server.
[0063] See Figure 4 , the terminal further includes a second obtaining module 14, and the second obtaining module 14 is configured to obtain an access address and a security verification code.
[0064] Specifically, before the push project or other project is connected to the real access server, it needs to visit the interface of the routing server first, and the first obtaining module 11 obtains the request token, that is, the terminal first sends a request message to the server to obtain the token , and the second obtaining ...
Embodiment 2
[0067] This embodiment provides a server, please refer to Figure 5 , including: a token generating module 21, a second sending module 22, a receiving module 23 and a judging module 24, further, the token generating module 21 is used to generate a token; the second sending module 22 is used to receive After obtaining the request, the token is sent to the terminal; the receiving module 23 is used to receive the access request message sent by the terminal, and the access request message contains the token; the judging module 24 is used to judge whether the access request message is based on the access request message Allow terminal access.
[0068] Further, the access request message also includes an access address and a security verification code.
[0069] Further, see Figure 6 , the judging module 24 includes an access location determination submodule 241, a first verification submodule 242 and a second verification submodule 243, specifically, the location determination su...
Embodiment 3
[0075] This embodiment provides a terminal access management method. For details, please refer to Figure 8 ,include:
[0076] Step 101, the terminal obtains a token from the server, encapsulates information including the token into an access request message, and sends the access request message to the server;
[0077] Step 102, after receiving the access request message, the server determines whether to allow terminal access according to the access request message.
[0078] Specifically, for step 101, before the push project or other project is connected to the real access server, it is necessary to visit the interface of the routing server once to obtain the request token, that is, the terminal first sends a request message to the server to obtain the token, and Request routing list information. After the server receives the request message, it obtains information such as the number of online users and the performance of the push access server for analysis, and the routing s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com