Patents
Literature
64 results about "Memory profiling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
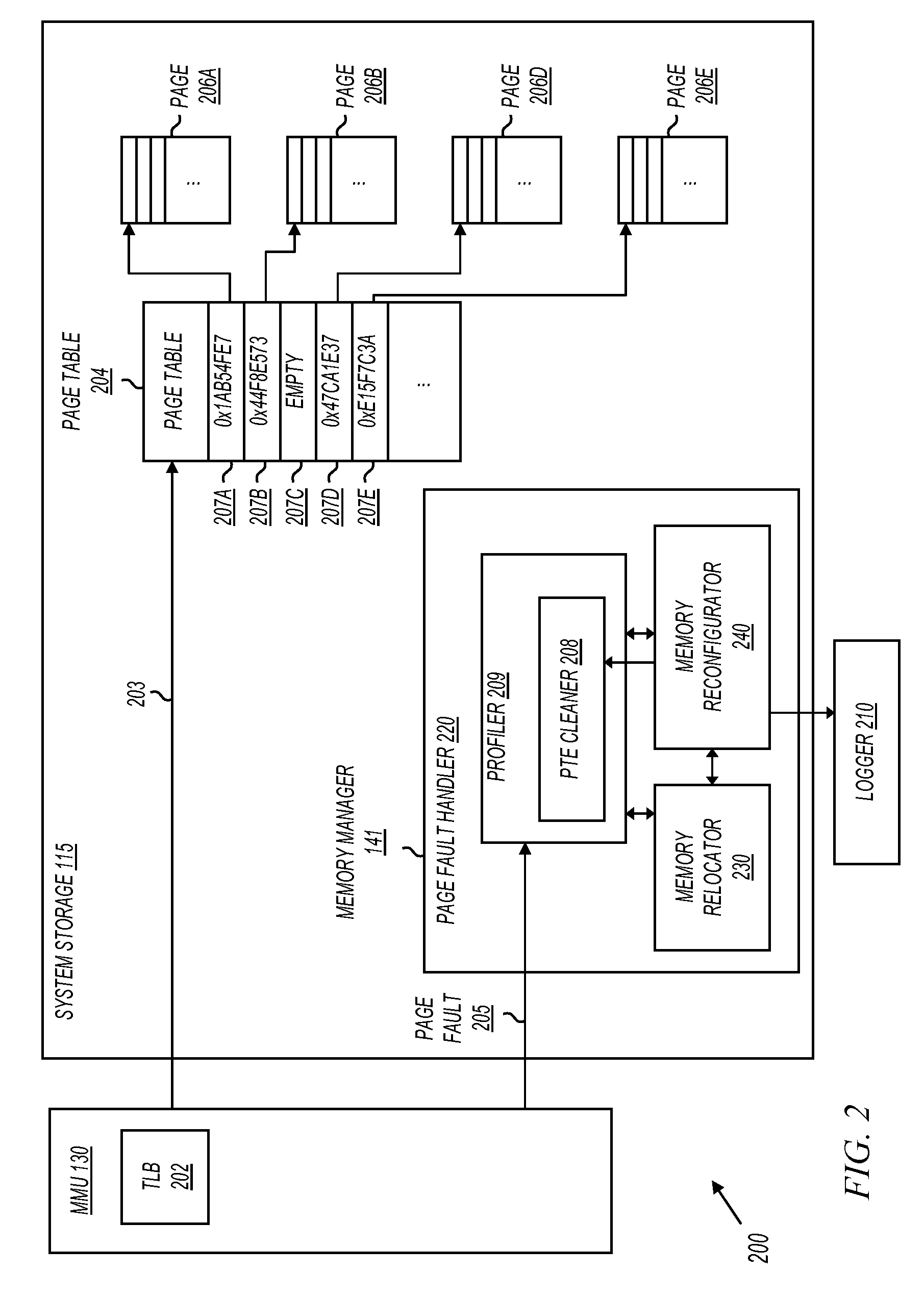
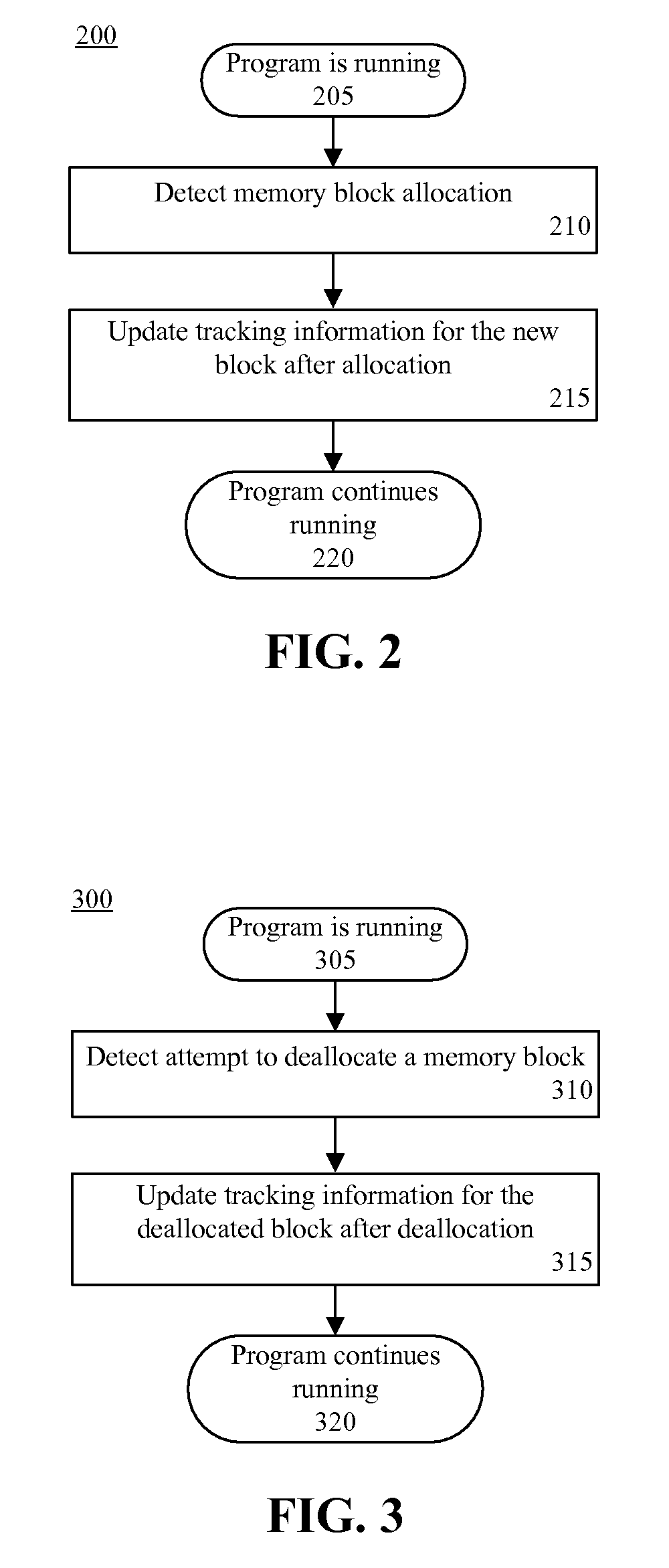
The Memory Profiler collects CLR memory usage data during the execution of a program. It allows you to optimize memory usage and easily identify memory leaks by comparing snapshots which include data about .NET instance allocations. To start a memory profiling session in...
Physical Memory Forensics System and Method
ActiveUS20140032875A1Accurate reconstructionMemory adressing/allocation/relocationDigital data protectionMemory forensicsData pack
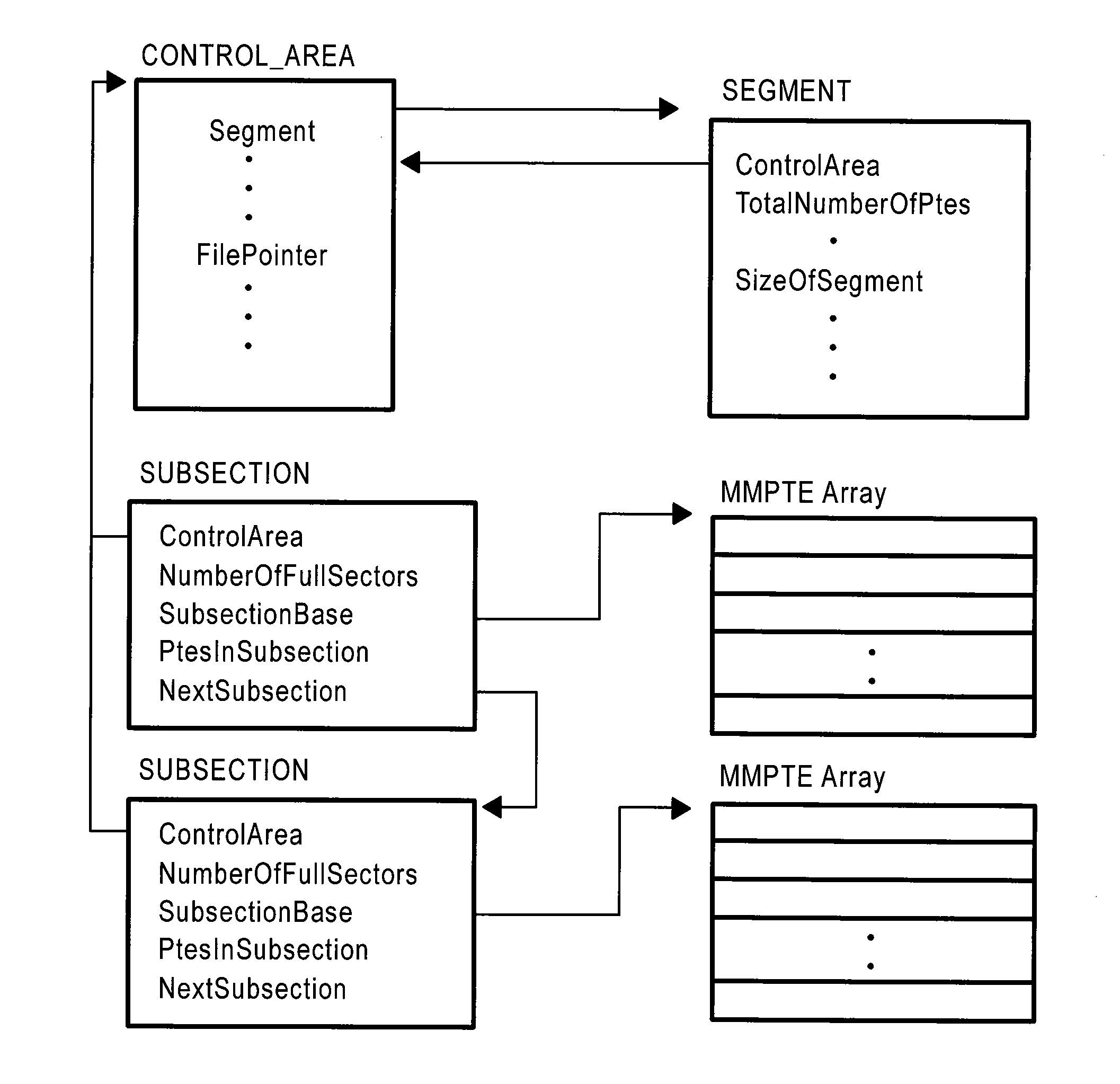
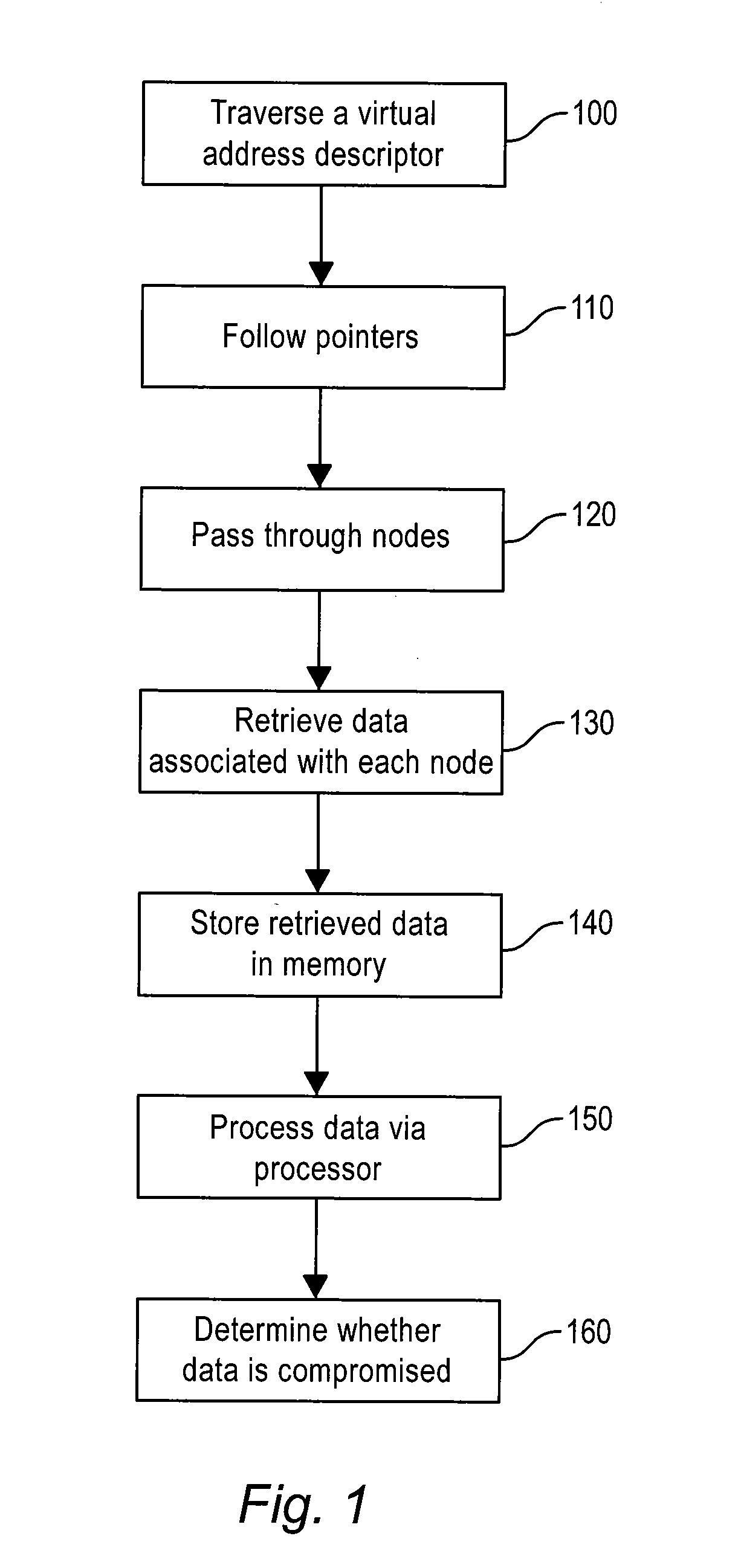
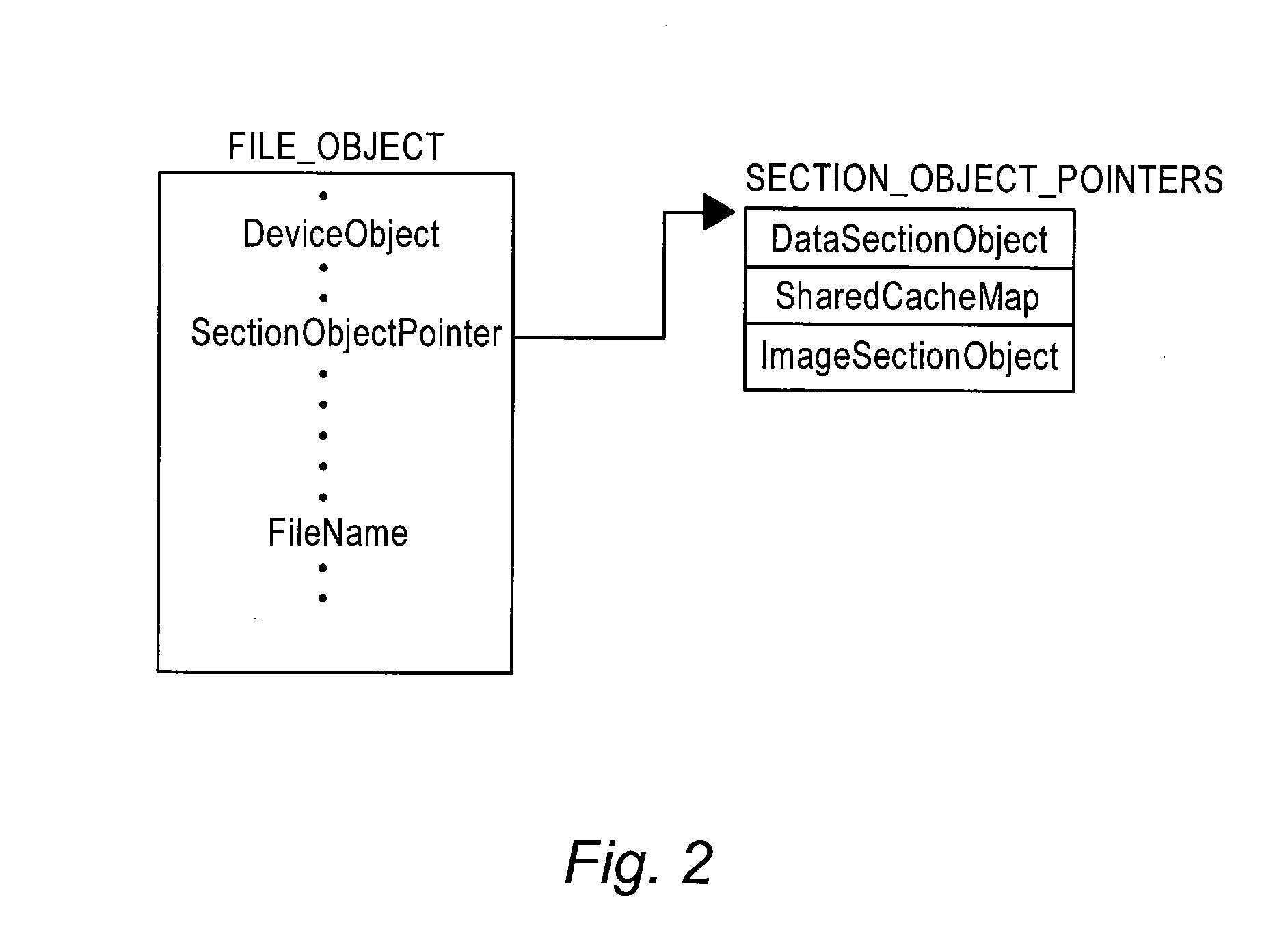
The method of the present inventive concept is configured to utilize Operating System data structures related to memory-mapped binaries to reconstruct processes. These structures provide a system configured to facilitate the acquisition of data that traditional memory analysis tools fail to identify, including by providing a system configured to traverse a virtual address descriptor, determine a pointer to a control area, traverse a PPTE array, copy binary data identified in the PPTE array, generate markers to determine whether the binary data is compromised, and utilize the binary data to reconstruct a process.
Owner:FIREEYE SECURITY HLDG US LLC
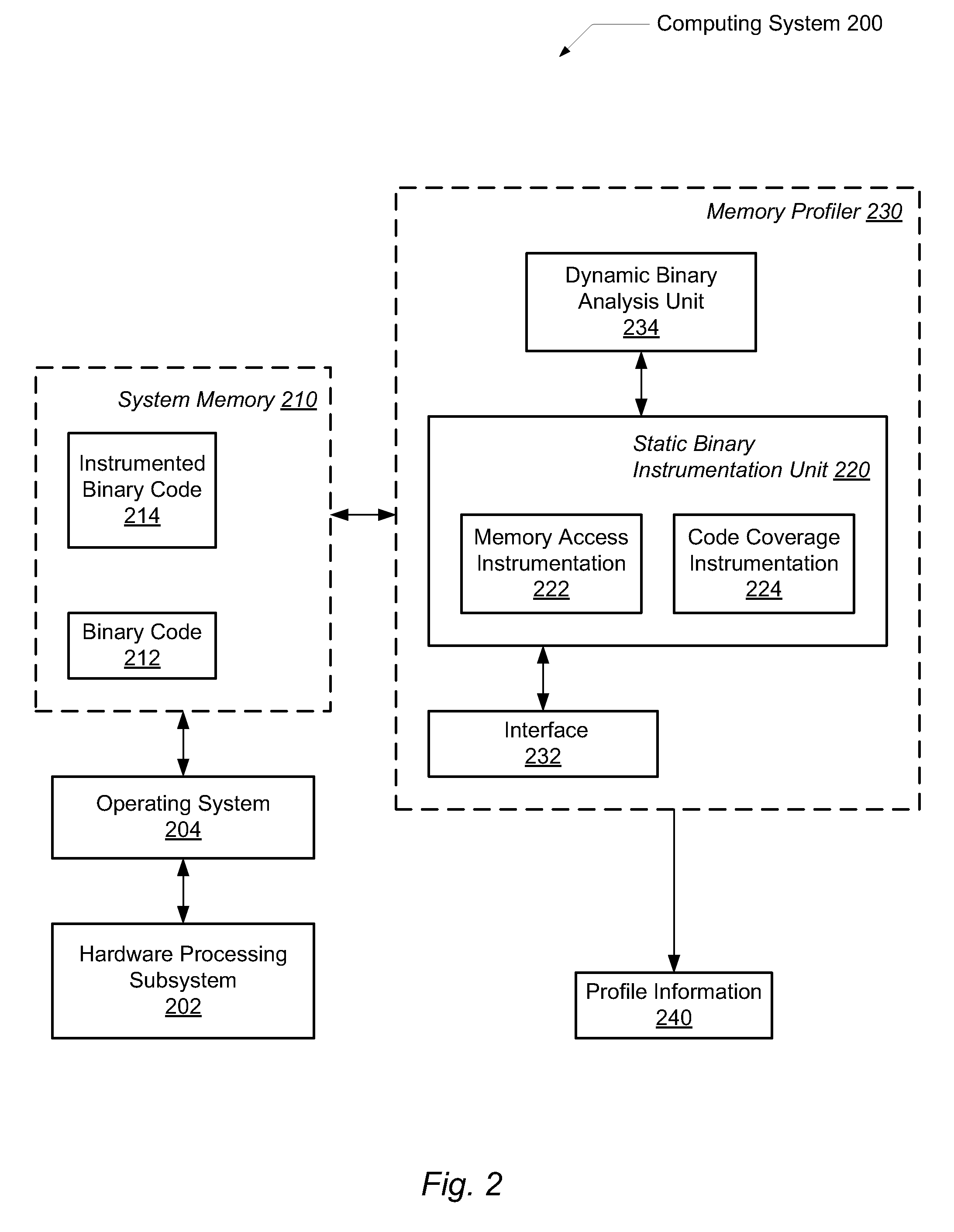
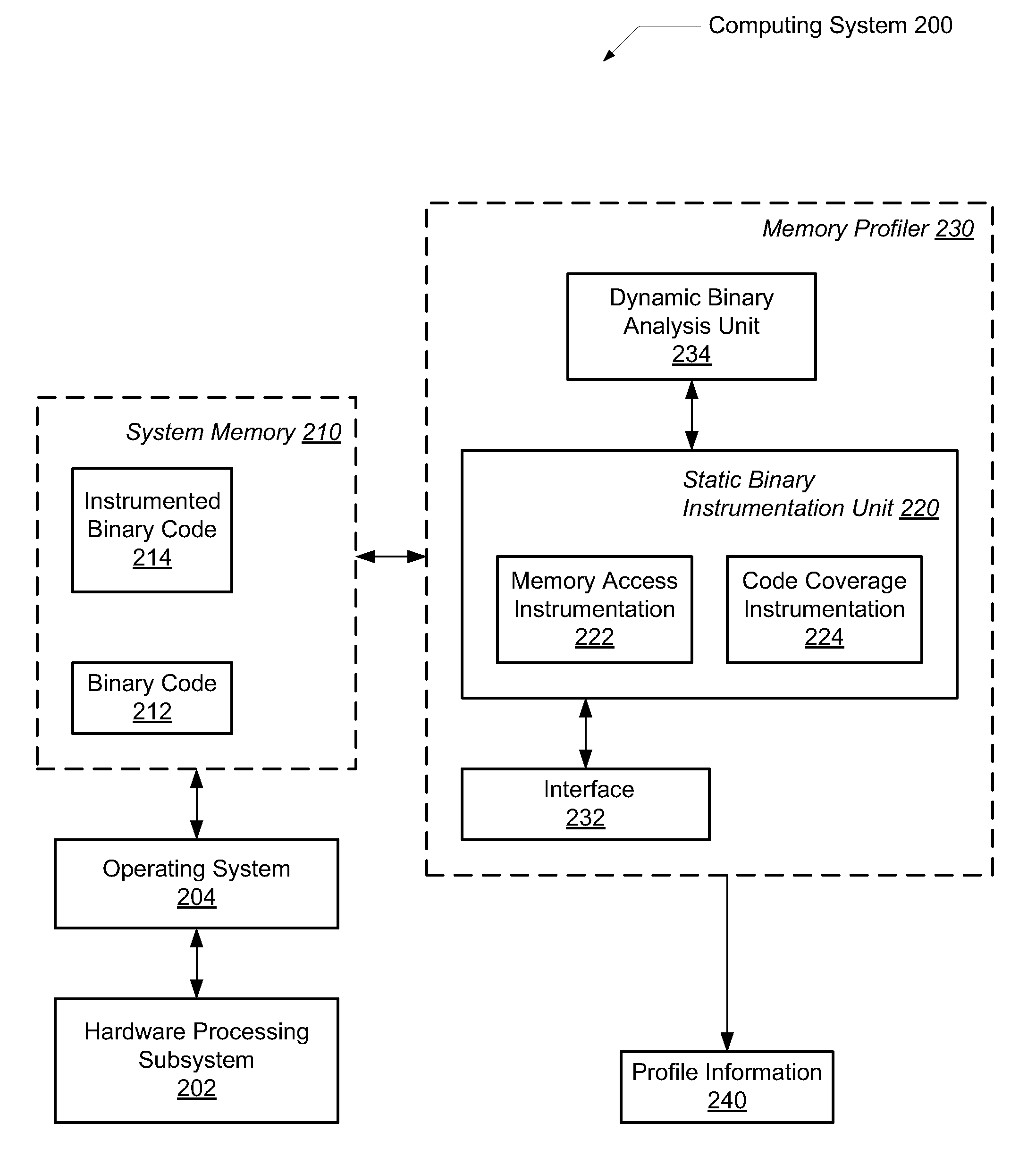
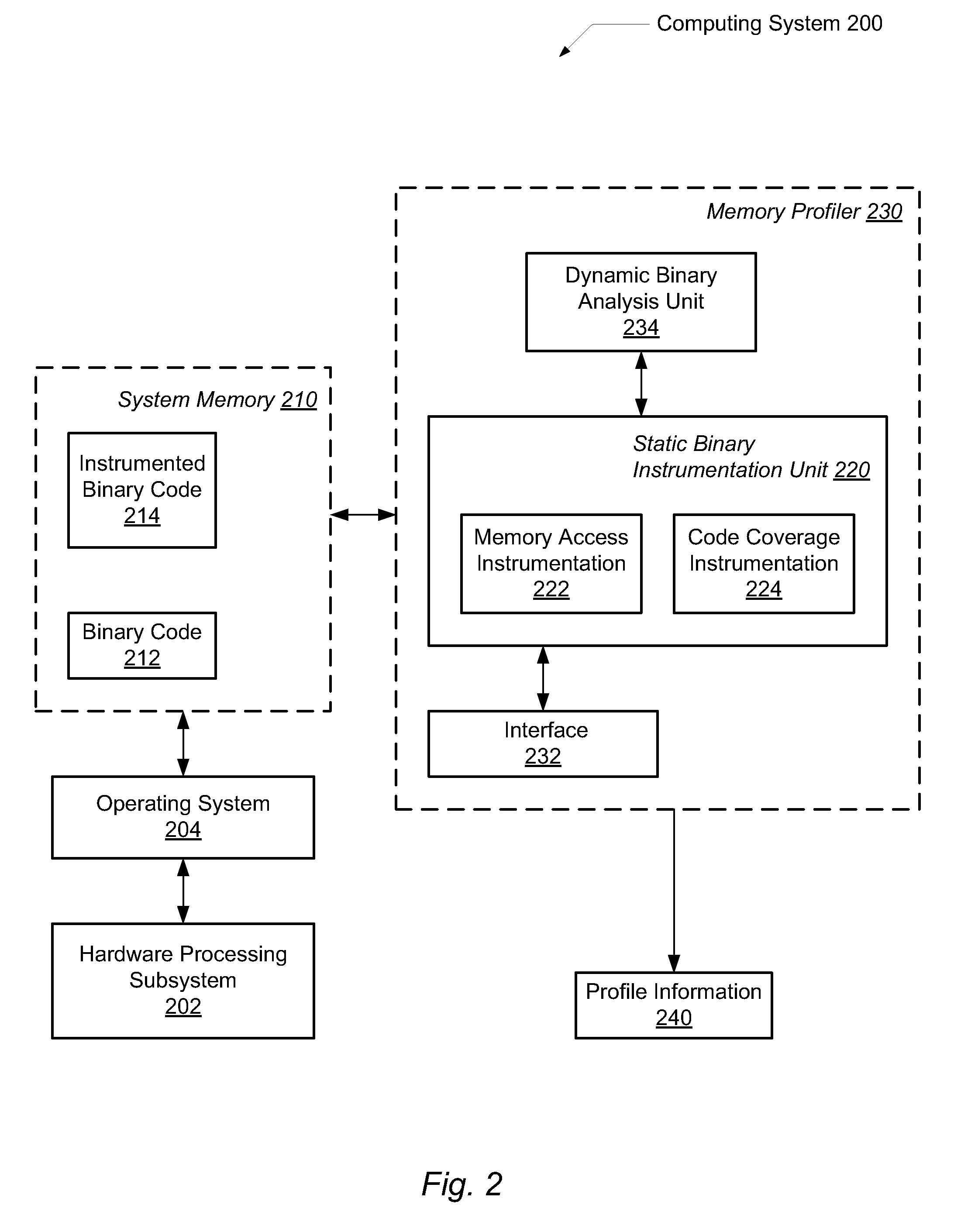
Efficient program instrumentation for memory profiling
ActiveUS20100146220A1Improve system performanceReduce false positiveError detection/correctionSpecific program execution arrangementsMemory profilingLoad instruction
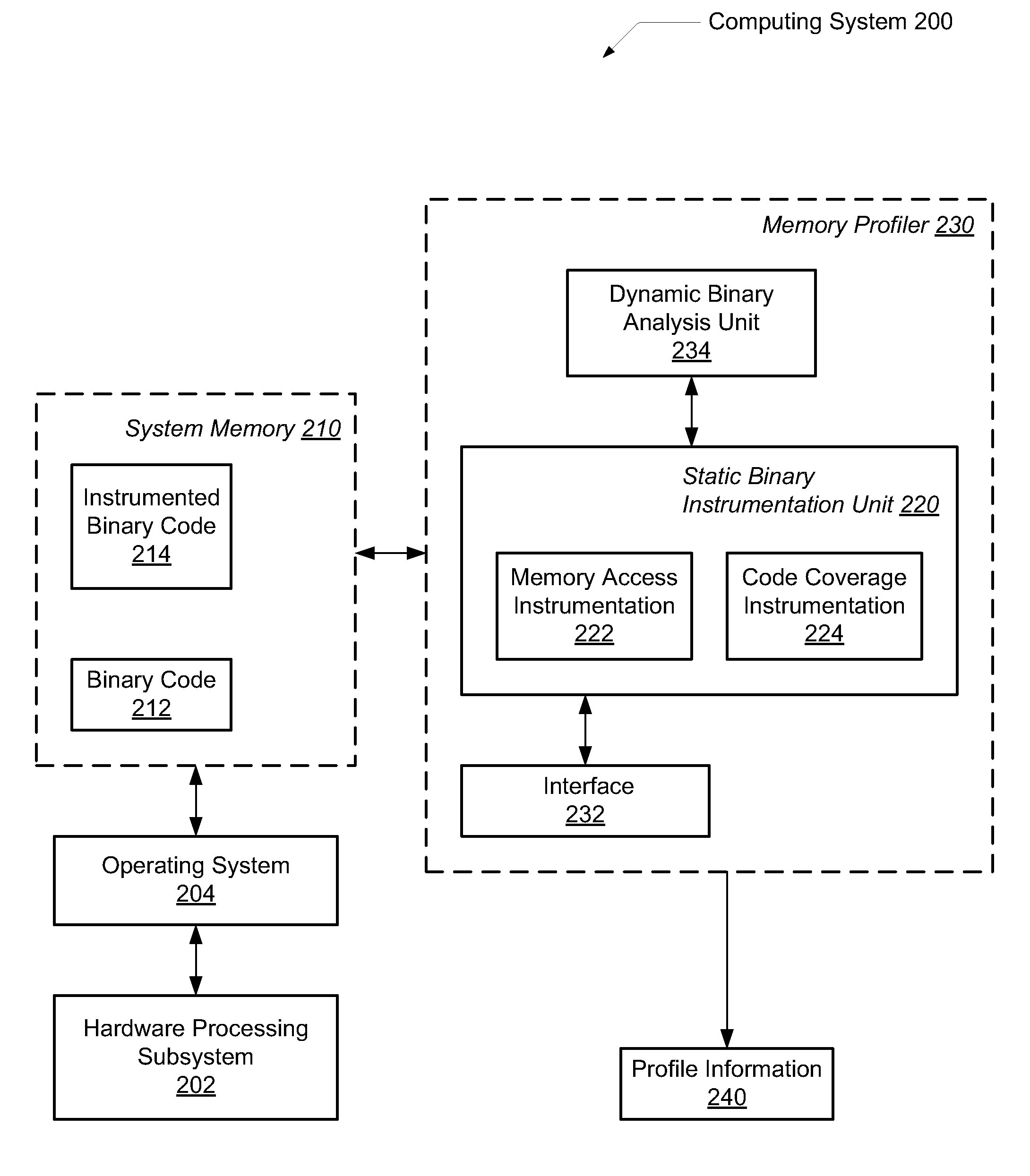
A system and method for performing efficient program instrumentation for memory profiling. A computing system comprises a memory profiler comprising a static binary instrumentation (SBI) tool and a dynamic binary analysis (DBA) tool. The profiler is configured to selectively instrument memory access operations of a software application. Instrumentation may be bypassed completely for an instruction if the instruction satisfies some predetermined conditions. Some sample conditions include the instruction accesses an address within a predetermined read-only area, the instruction accesses an address within a user-specified address range, and / or the instruction is a load instruction accessing a memory location determined from a data flow graph to store an initialized value. An instrumented memory access instruction may have memory checking analysis performed only upon an initial execution of the instruction in response to determining during initial execution that a read data value of the instruction is initialized. Both unnecessary instrumentation and memory checking analysis may be reduced.
Owner:ORACLE INT CORP
Method and Apparatus for Efficient Memory Placement
InactiveUS20100169602A1Memory architecture accessing/allocationMemory systemsMemory profilingMemory type
A memory profiling system profiles memory objects in various memory devices and identifies memory objects as candidates to be moved to a more efficient memory device. Memory object profiles include historical read frequency, write frequency, and execution frequency. The memory object profile is compared to parameters describing read and write performance of memory types to determine candidate memory types for relocating memory objects. Memory objects with high execution frequency may be given preference when relocating to higher performance memory devices.
Owner:MICRON TECH INC
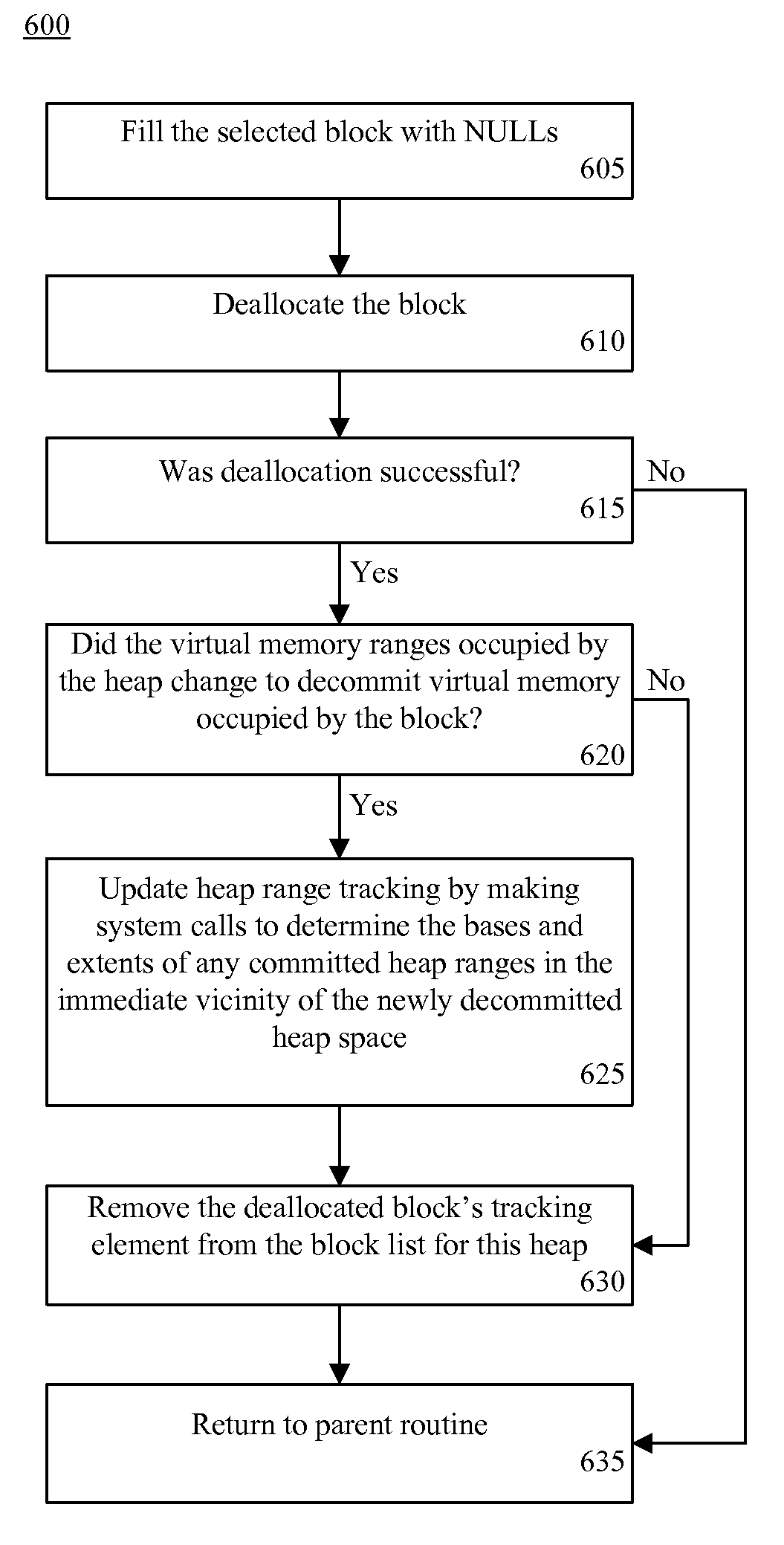
Use of Region-Oriented Memory Profiling to Detect Heap Fragmentation and Sparse Memory Utilization
InactiveUS20070136546A1Error detection/correctionMultiprogramming arrangementsVirtual memoryMemory profiling
A method of detecting inefficient use of virtual memory by an application that is programmed using memory pointers. The method can include selecting a first heap from a list of tracked heaps and identifying allocated memory blocks within the first heap. A first total can be determined as a sum of sizes of the identified memory blocks. A second total can be determined as a sum of unallocated, NULL-filled bytes within the first heap that are not located outside outermost memory block addresses in each range of committed memory in the first heap. A ratio of the first total and the second total can be determined, and a memory profile corresponding to the ratio can be generated.
Owner:IBM CORP
Method and system for efficient tracing and profiling of memory accesses during program execution
ActiveUS8478948B2Reduces instrumentationImprove system performanceError detection/correctionSpecific program execution arrangementsMemory profilingLoad instruction
A system and method for performing efficient program instrumentation for memory profiling. A computing system comprises a memory profiler comprising a static binary instrumentation (SBI) tool and a dynamic binary analysis (DBA) tool. The profiler is configured to selectively instrument memory access operations of a software application. Instrumentation may be bypassed completely for an instruction if the instruction satisfies some predetermined conditions. Some sample conditions include the instruction accesses an address within a predetermined read-only area, the instruction accesses an address within a user-specified address range, and / or the instruction is a load instruction accessing a memory location determined from a data flow graph to store an initialized value. An instrumented memory access instruction may have memory checking analysis performed only upon an initial execution of the instruction in response to determining during initial execution that a read data value of the instruction is initialized. Both unnecessary instrumentation and memory checking analysis may be reduced.
Owner:ORACLE INT CORP
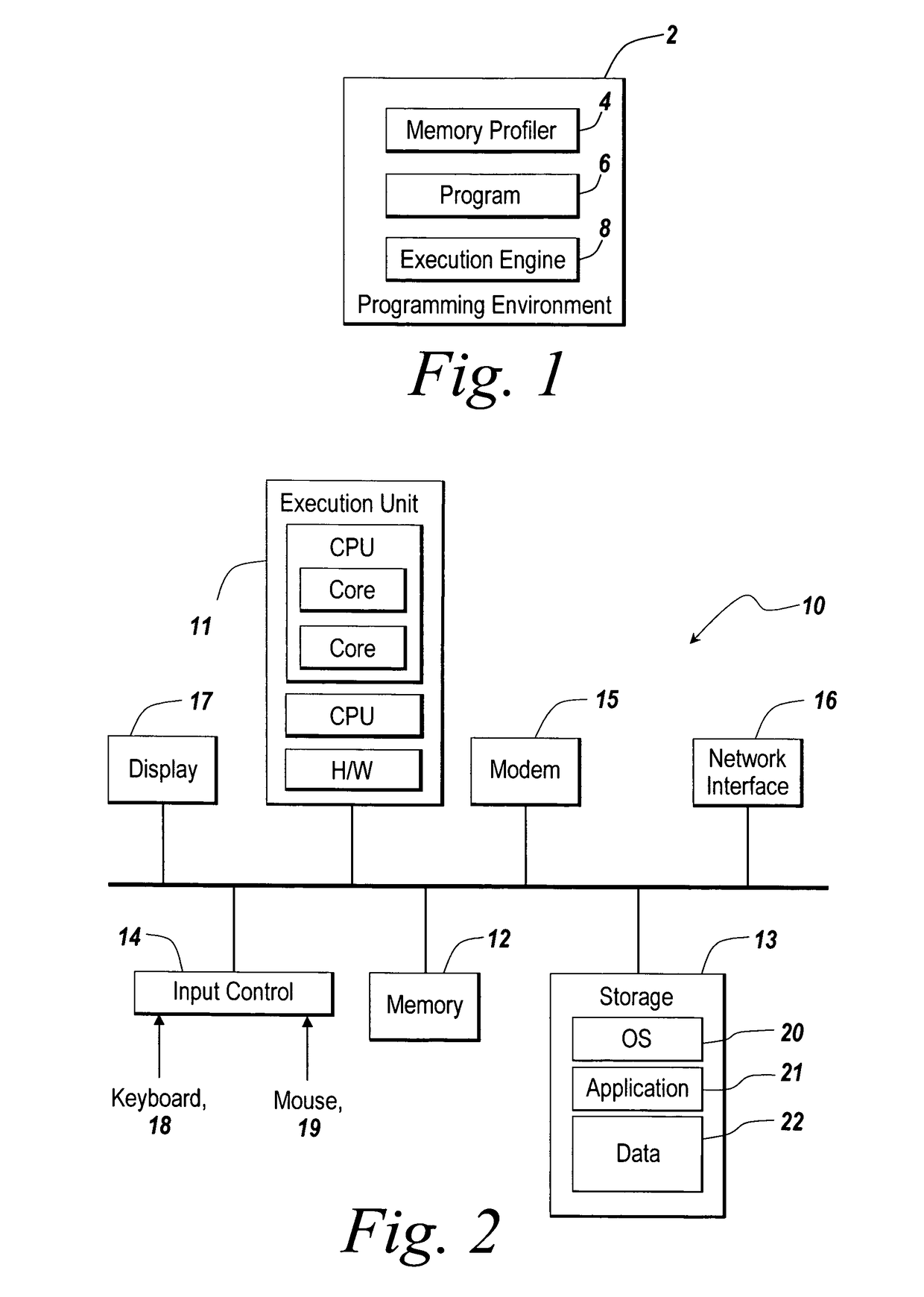
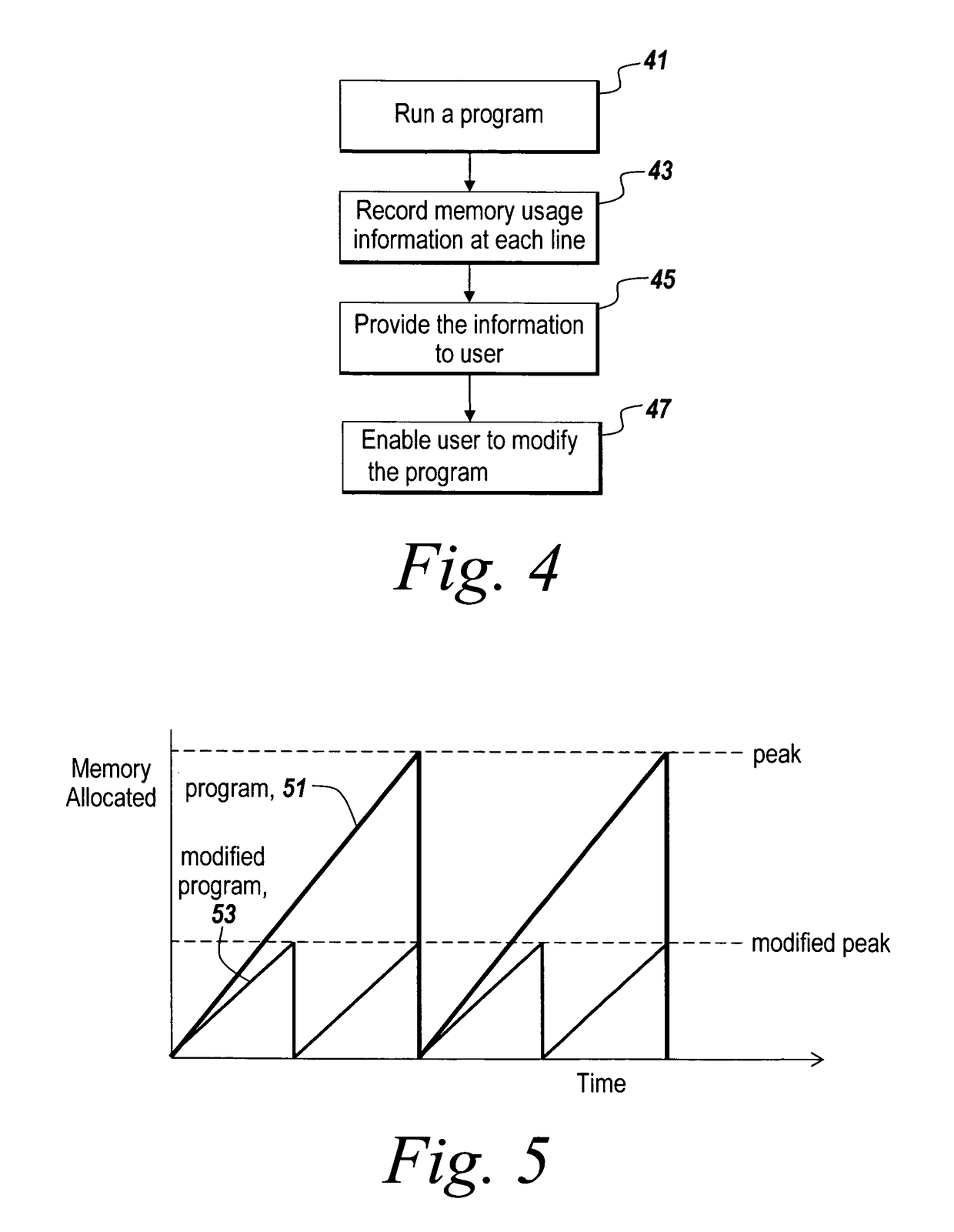
Memory profiling
ActiveUS7908591B1Reduce total usageReduce and eliminate effectError detection/correctionSoftware designMemory profilingOperating system
A memory profiler is provided in a programming environment. The memory profiler records memory usage information at a point of a program that runs in the programming environment. The memory profiler may record information on the amount of allocated memory, the amount of freed memory and the amount of peak memory usage. The memory profiler may also record the number of allocations and frees. The memory usage information is associated with individual points in the program so that a user can utilize this information to change the program to use less memory. With the memory usage information, the present invention enables a user to recognize how much memory is being allocated and used on behalf of a program and to track down what code is actually causing a problem in the program.
Owner:THE MATHWORKS INC
Use of region-oriented memory profiling to detect heap fragmentation and sparse memory utilization
InactiveUS7500077B2Error detection/correctionMemory adressing/allocation/relocationVirtual memoryMemory profiling
A method of detecting inefficient use of virtual memory by an application that is programmed using memory pointers. The method can include selecting a first heap from a list of tracked heaps and identifying allocated memory blocks within the first heap. A first total can be determined as a sum of sizes of the identified memory blocks. A second total can be determined as a sum of unallocated, NULL-filled bytes within the first heap that are not located outside outermost memory block addresses in each range of committed memory in the first heap. A ratio of the first total and the second total can be determined, and a memory profile corresponding to the ratio can be generated. A memory profile suggestion also can be generated.
Owner:IBM CORP
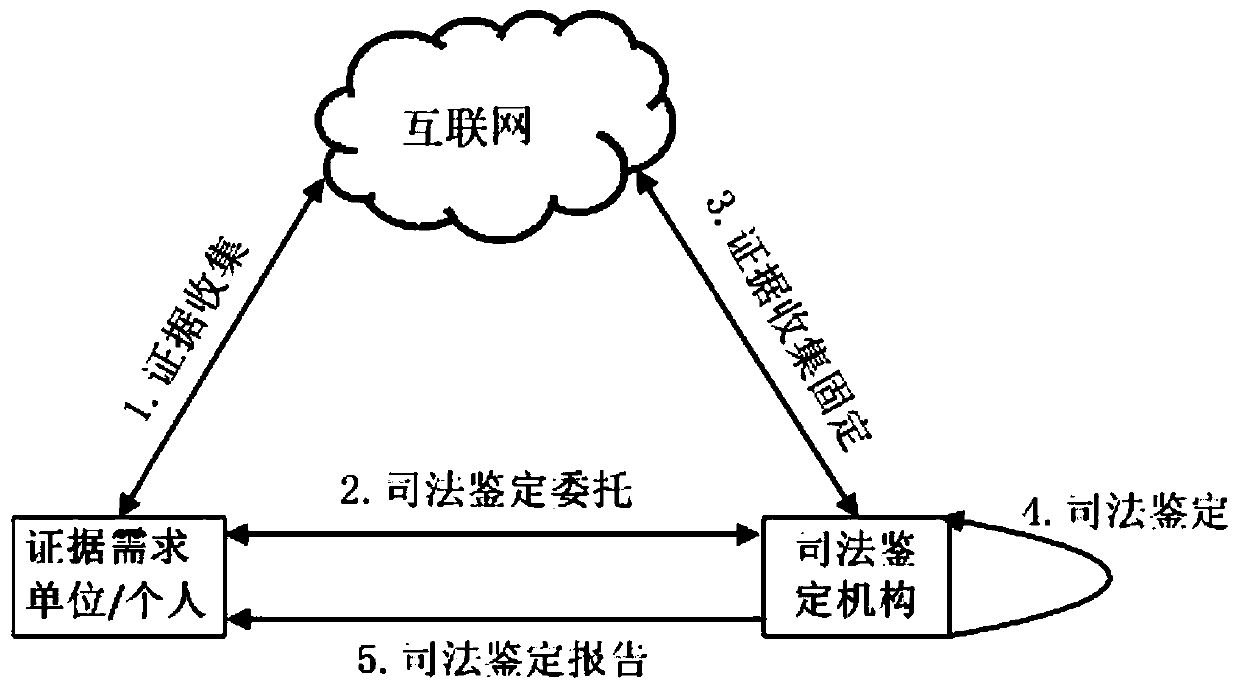
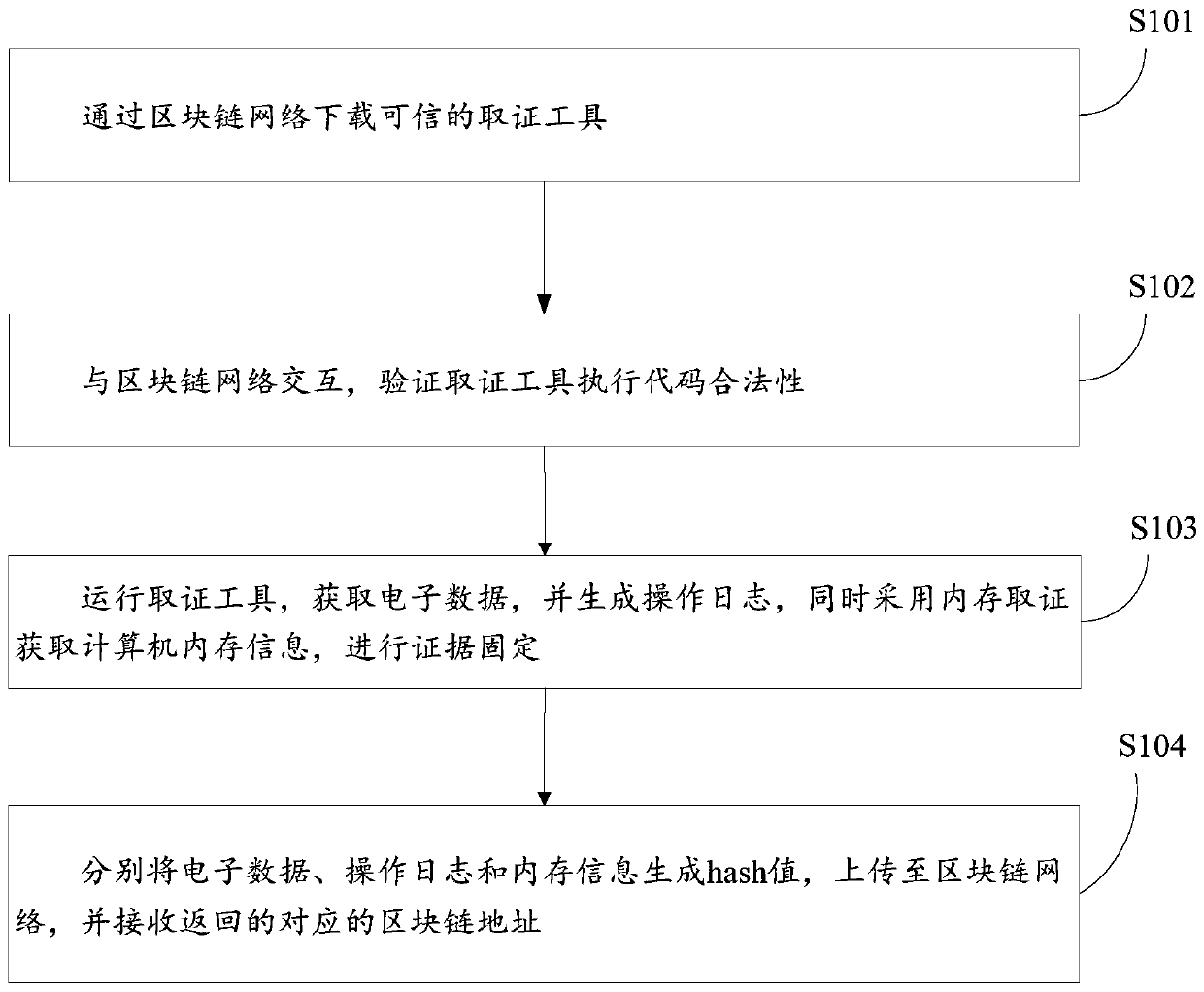
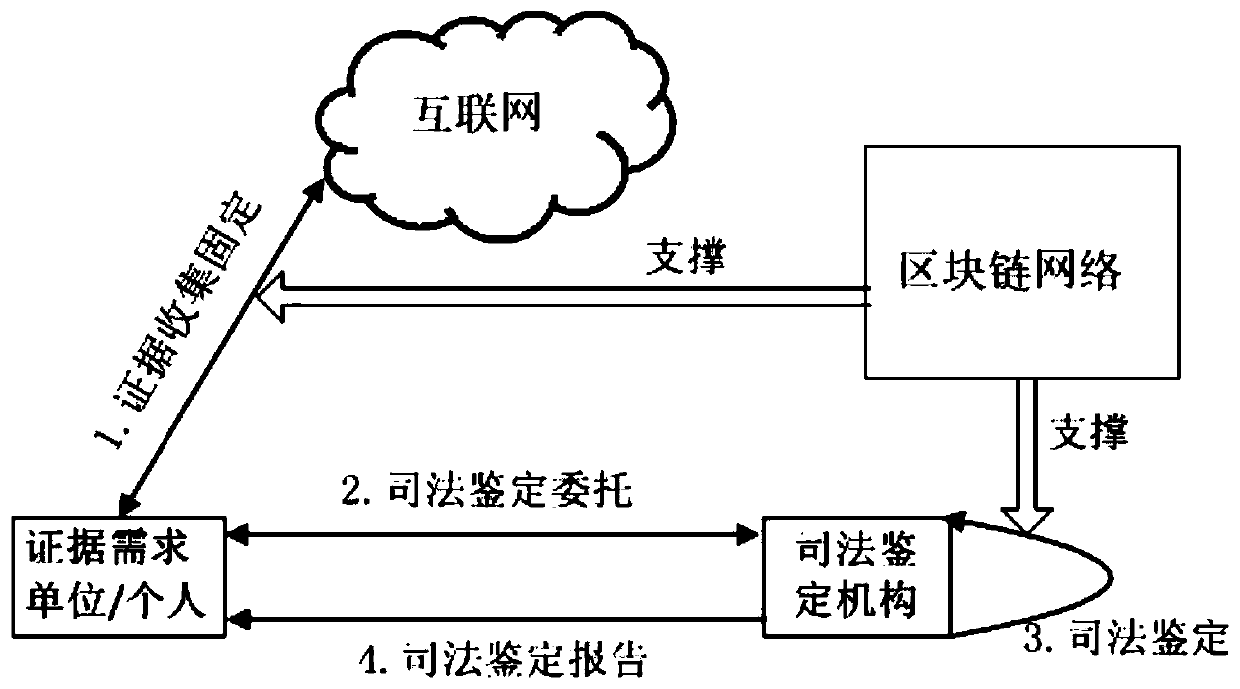
Electronic evidence fixing and network evidence obtaining method and system based on memory evidence obtaining and block chain
ActiveCN110232645AYi CaixinAvoid delayData processing applicationsDigital data protectionMemory profilingMemory forensics
The invention discloses an electronic evidence fixing and network evidence obtaining method and system based on memory evidence obtaining and a block chain. An electronic evidence fixing terminal downloads a credible evidence obtaining tool through the block chain network. The legality of the evidence obtaining tool execution code is verified. The evidence obtaining tool is operated, electronic data are obtained, an operation log is generated, meanwhile, computer memory information is obtained through the memory evidence obtaining technology, and evidence fixing is conducted. A hash value is generated.and uploaded to the block chain network. A returned corresponding block chain address is received. The data is sent to a judicial certification authority terminal. A judicial certification mechanism terminal receives the block chain address sent by the electronic evidence fixing terminal. Information on the block chain is inquired, and legality is verified. The memory information is analyzed by adopting a memory evidence obtaining technology. The system state is extracted when the electronic evidence is obtained, and verifying the conformity. A judgment is verified whether the evidence obtaining tool is hooked or injected during operation or not through memory analysis, and the reliability of the operation environment of the evidence obtaining tool is verified. Judicial authentication reports are generated.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
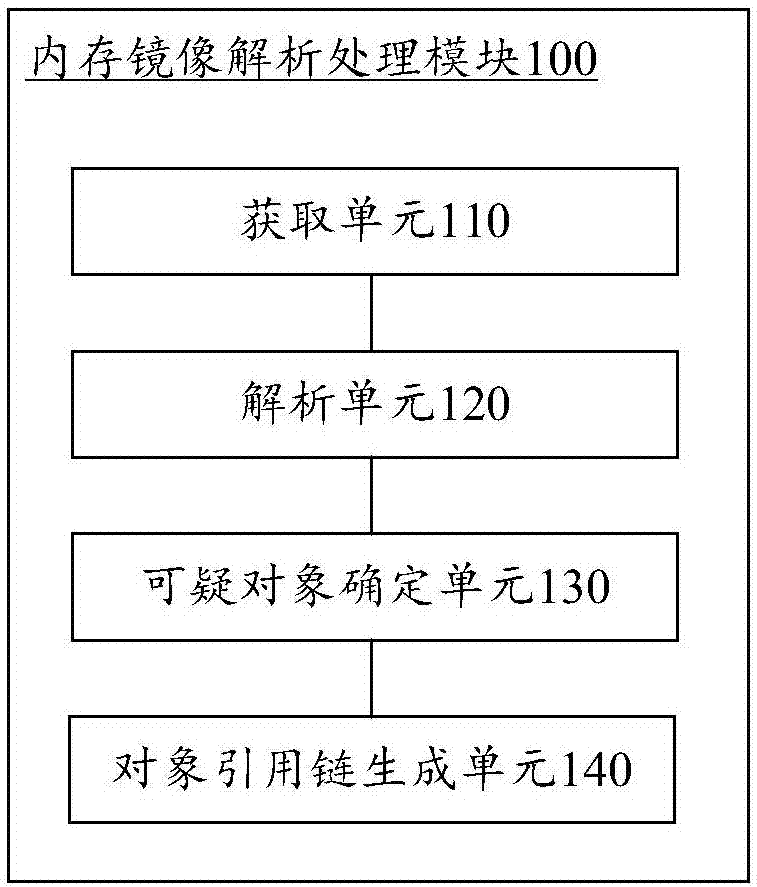
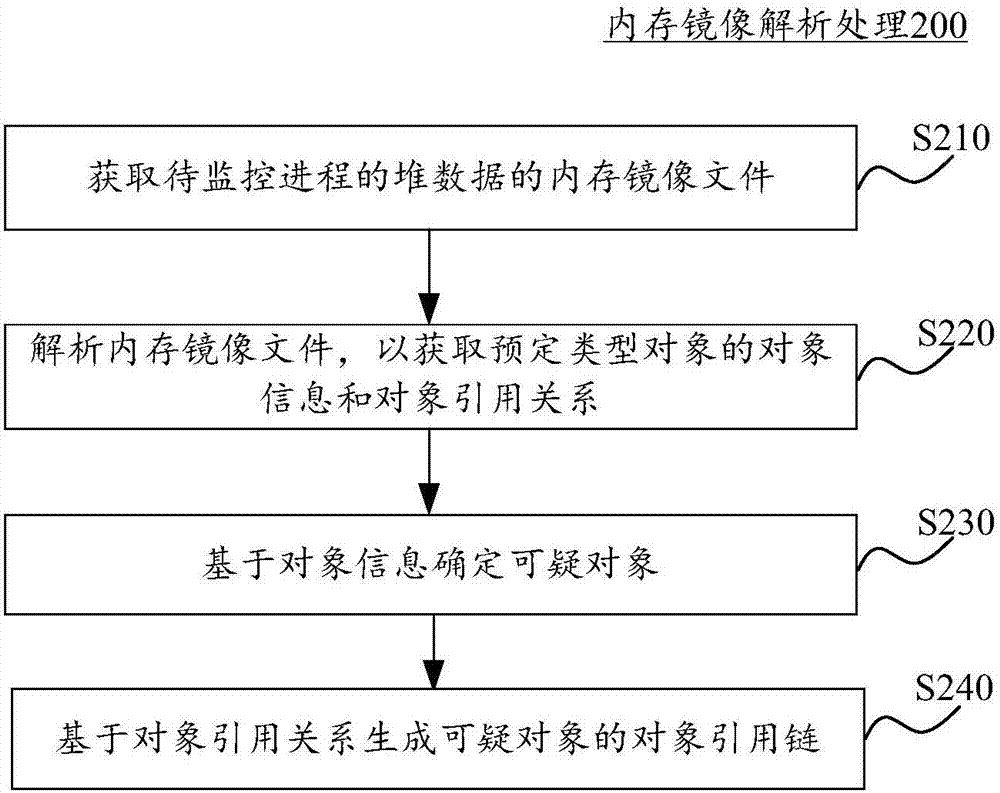
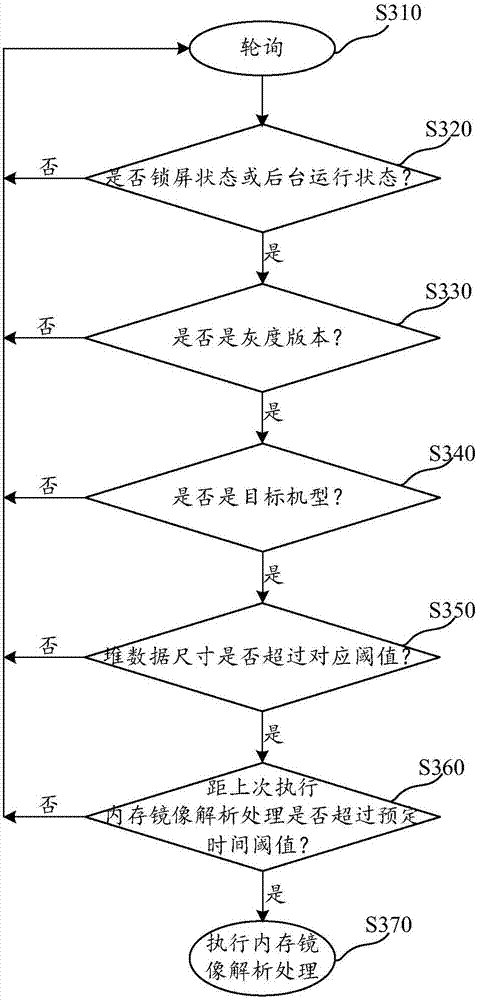
Memory analysis method and device, system and computing device
The invention discloses a memory analysis method and device, a system and a computing device. In the method, a memory image file of the heap data of a to-be-monitored process is obtained and parsed toobtain the object information and the object reference relationship of the predetermined type of object, then suspicious objects are determined based on the object information, and object reference chains of the suspicious objects are generated based on the object reference relationship. In this way, for the problem of excessive heap occupancy of the Java program, according to the long-tail theory and the actual situation, the memory analysis method and device, the system and the computing device place the analysis focus on large objects (such as a very long byte array), classify large objects as the suspicious objects, and can find out the cause of excessive heap occupancy of the Java program by obtaining the suspicious objects in the heap data of the process and the reference chains ofthe suspicious objects.
Owner:ALIBABA (CHINA) CO LTD
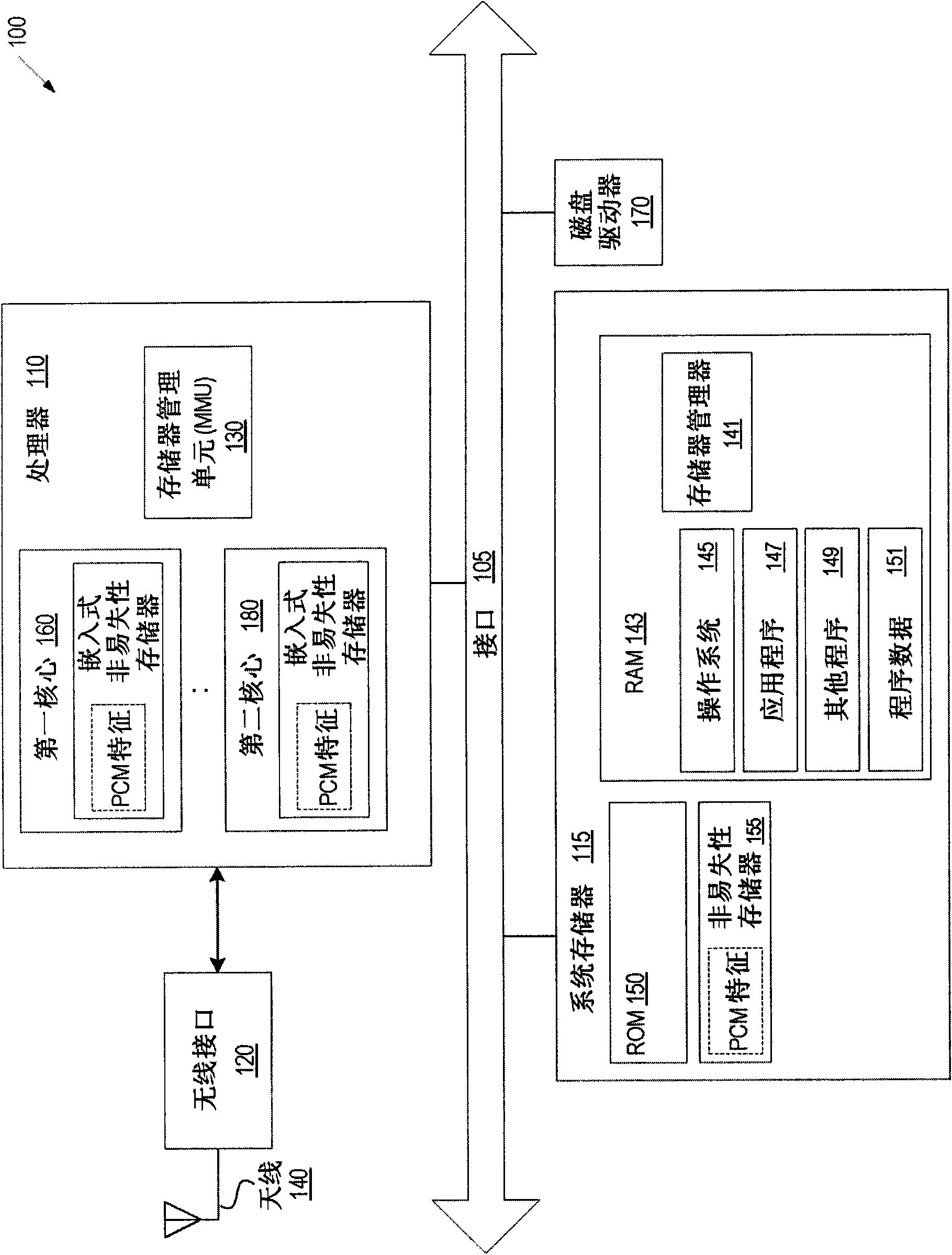
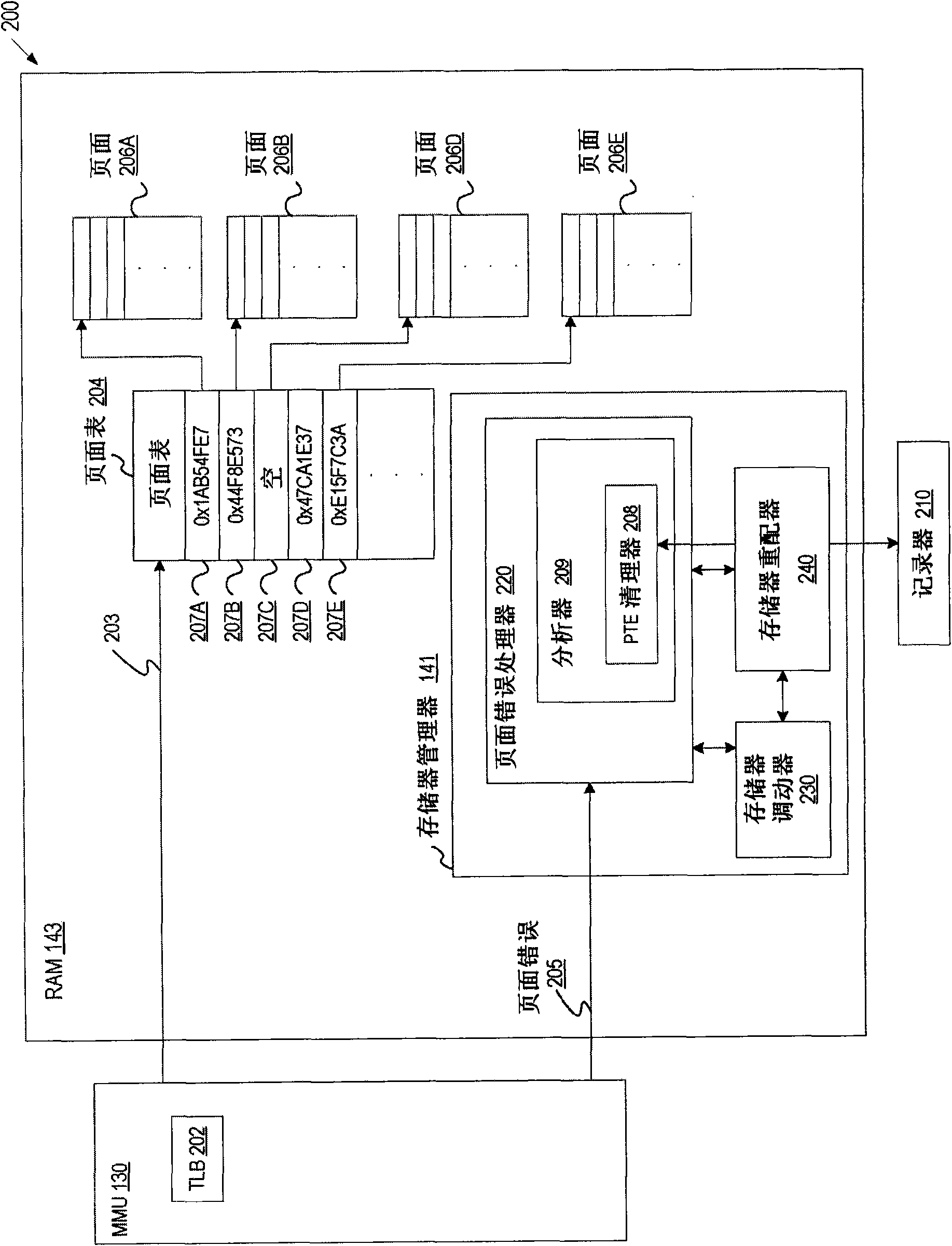
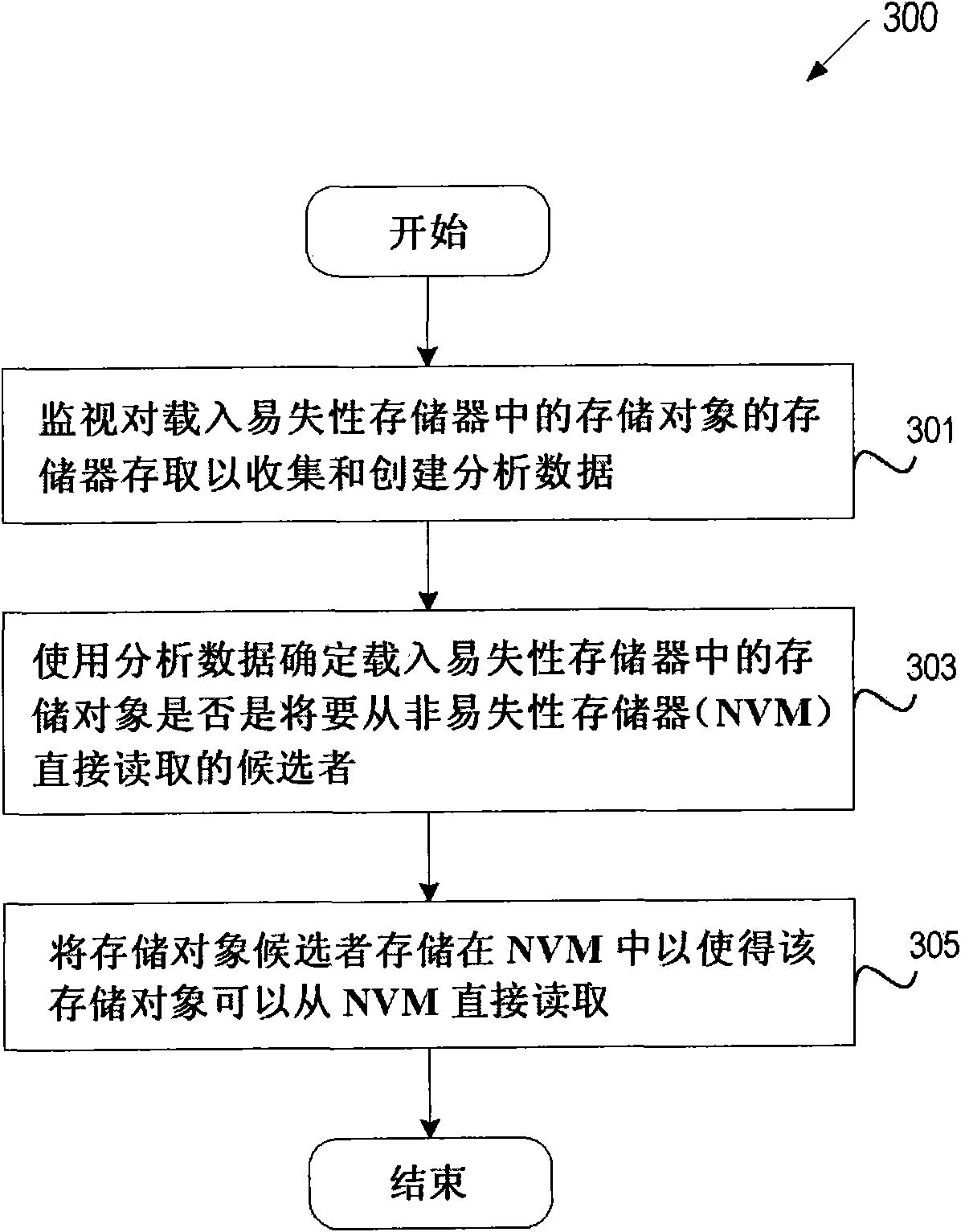
Method and apparatus to profile RAM memory objects for displacement with nonvolatile memory
InactiveCN101770430AMemory architecture accessing/allocationError detection/correctionMemory profilingMemory object
A memory profiling system profiles memory objects in volatile memory and identifies memory objects as candidates to be stored and read directly from nonvolatile memory. The profiling system monitors memory accesses via page faults and identifies a memory object to be loaded in volatile memory. The profiling system uses page faults to determine a page fault type and a write frequency for the memory object, and determines the memory object's memory access type. The profiling system determines whether the object's memory access type meets the capabilities of the nonvolatile memory technology. Ifthe memory access type meets the nonvolatile memory technology capabilities, the profiling system identifies the memory object as a candidate to be transitioned to and read directly from nonvolatile memory (e.g., NOR and PCM). The profiling system stores the memory object candidates in nonvolatile memory such that the memory objects are read directly from nonvolatile memory.
Owner:J·鲁德利克 +2
Automated scalable and adaptive system for memory analysis via identification of leak root candidates
InactiveUS7568192B2Error detection/correctionDigital computer detailsMemory profilingTheoretical computer science
Owner:INT BUSINESS MASCH CORP
Systems, Methods, and Computer Readable Medium for Analyzing Memory
InactiveUS20060225044A1Specific program execution arrangementsMemory systemsMemory typeMemory profiling
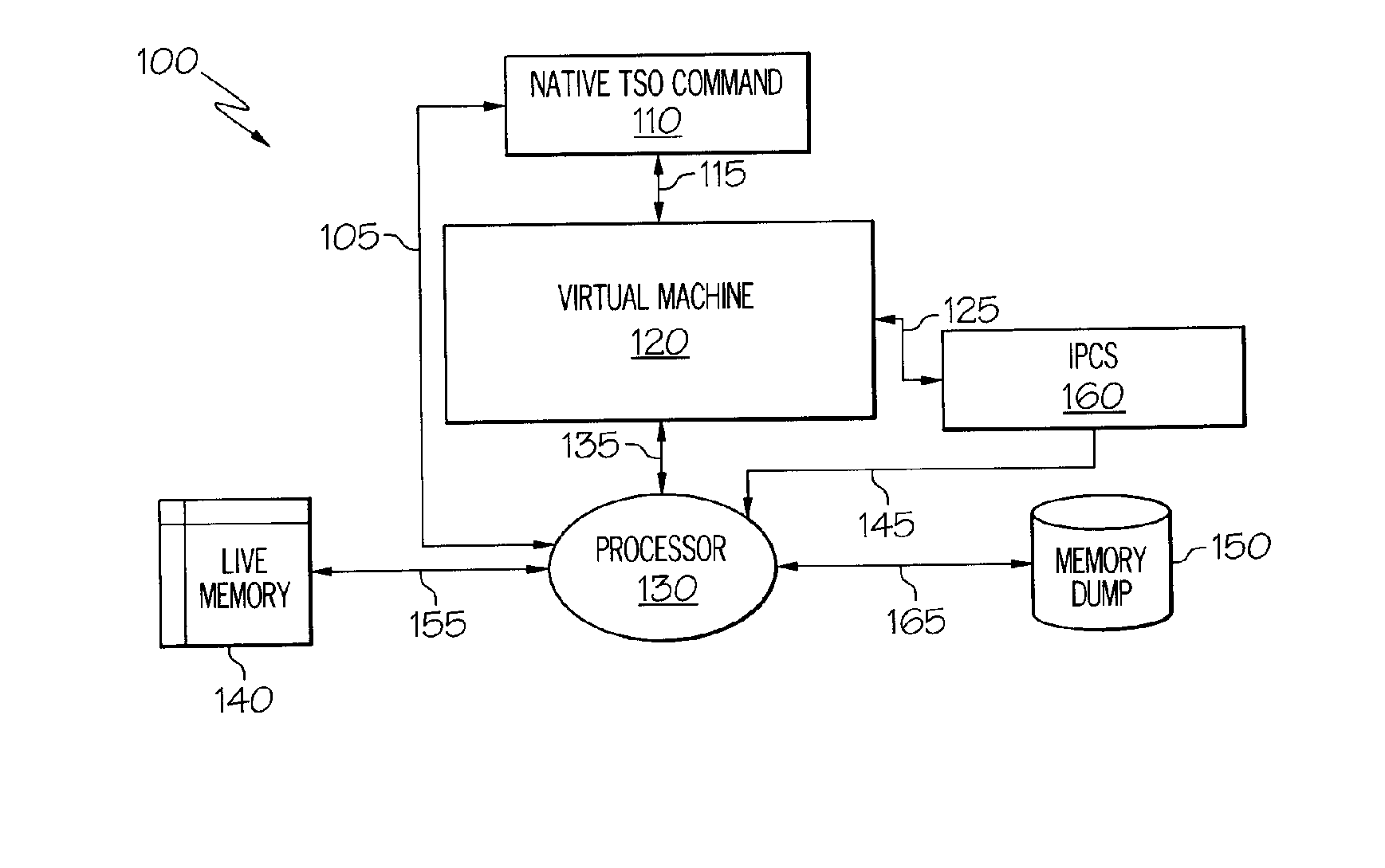
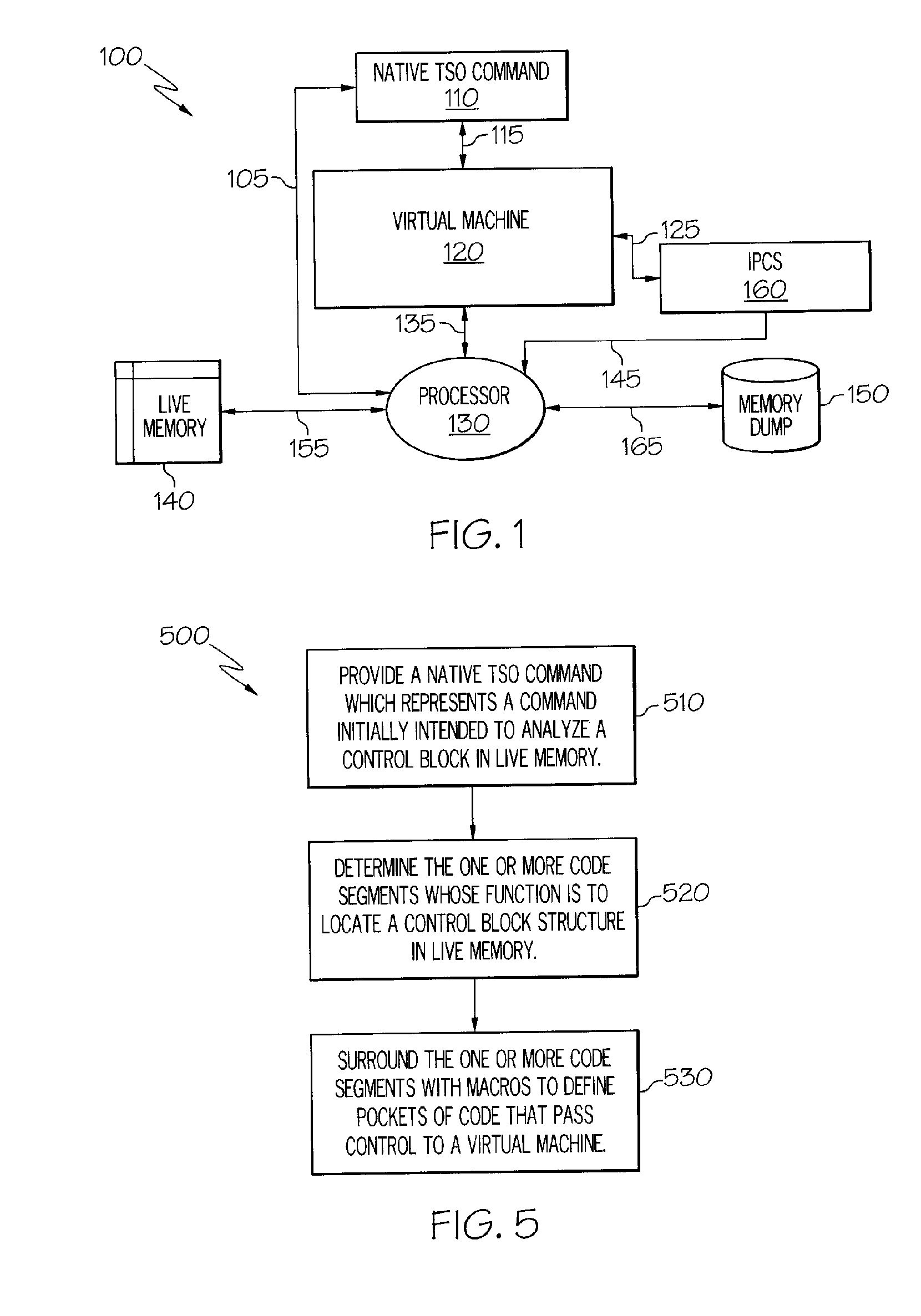
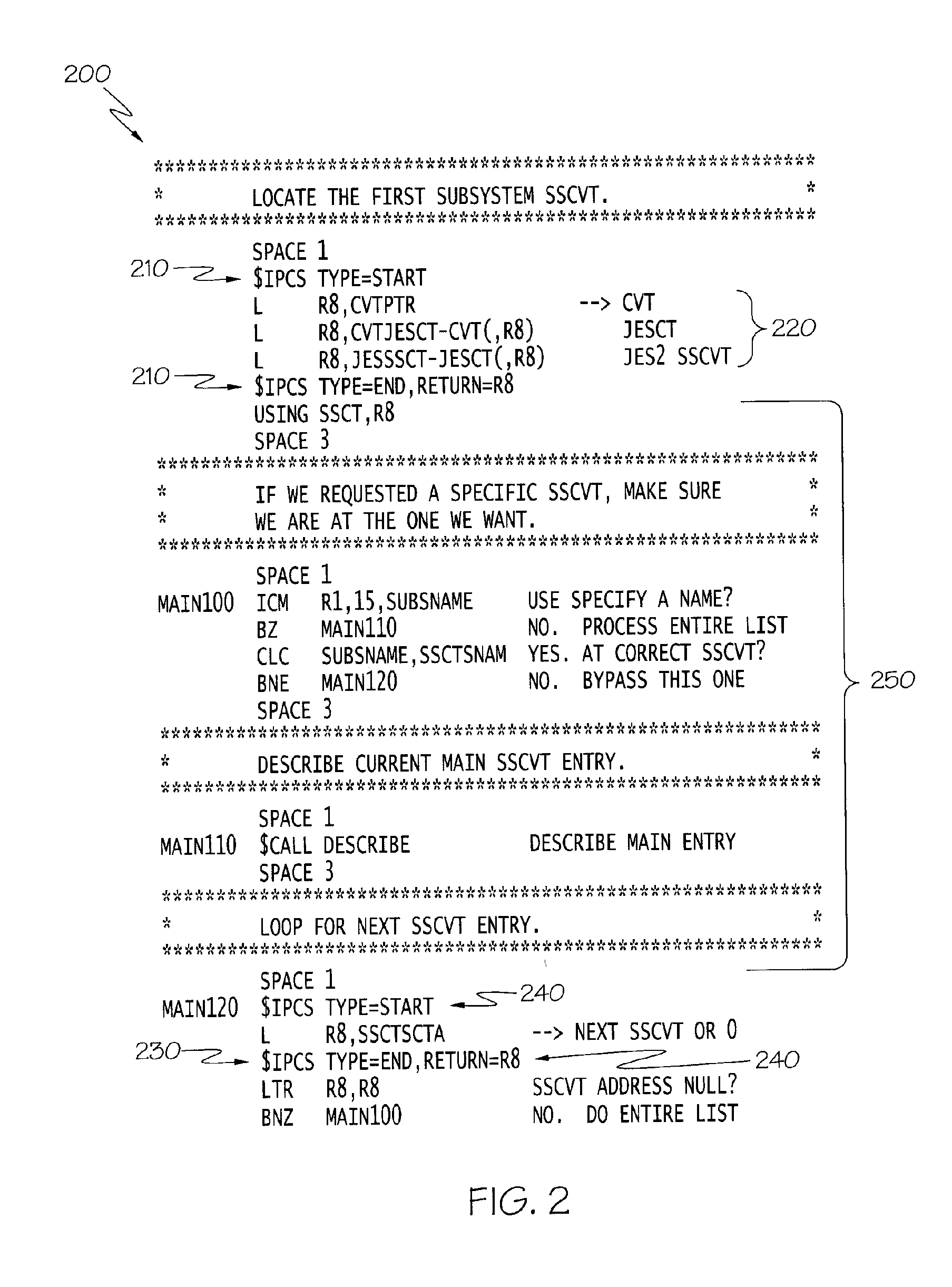
Techniques are provided for expanding the functionality of live memory analysis commands to analyze a memory dump or other differing memory types. To this end, a live memory command which normally analyzes live memory is modified to invoke a virtual machine. Live memory commands, in general, have different code segments including a locate code segment which, when executed, locates a first control block in live memory. The locate code segment of the live memory command is modified to invoke a virtual machine for locating a second control block in a memory dump. When the modified code segment is executed, the second control block from a memory dump is accessed.
Owner:GOOGLE LLC
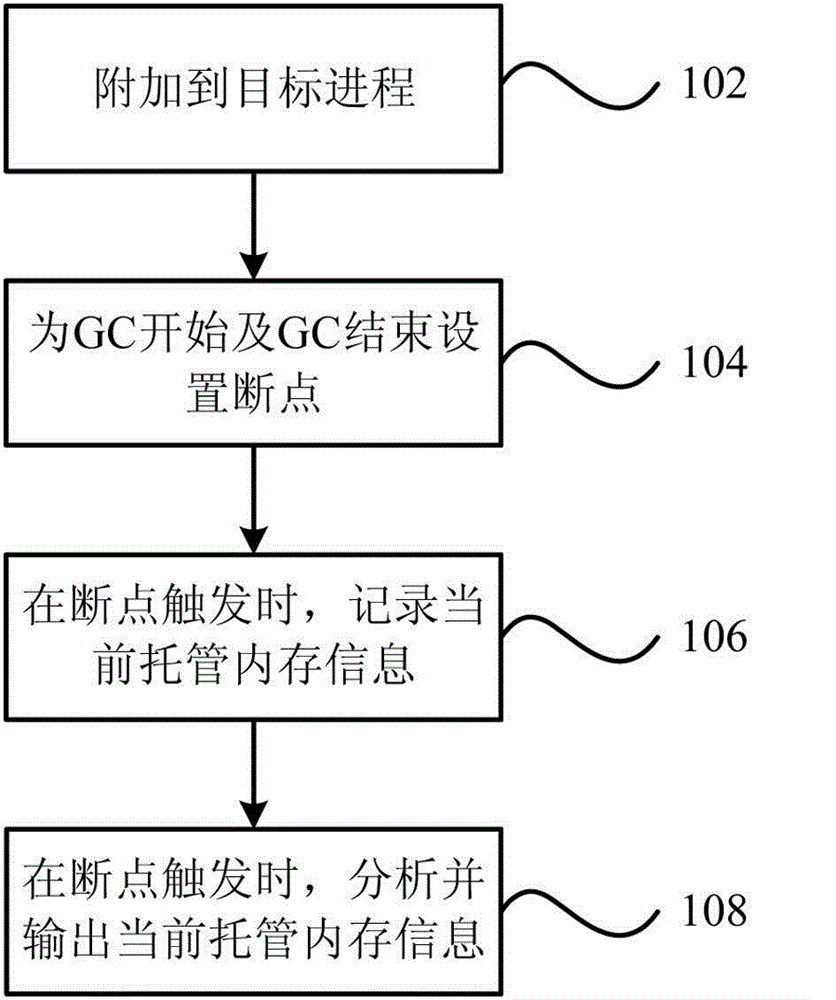
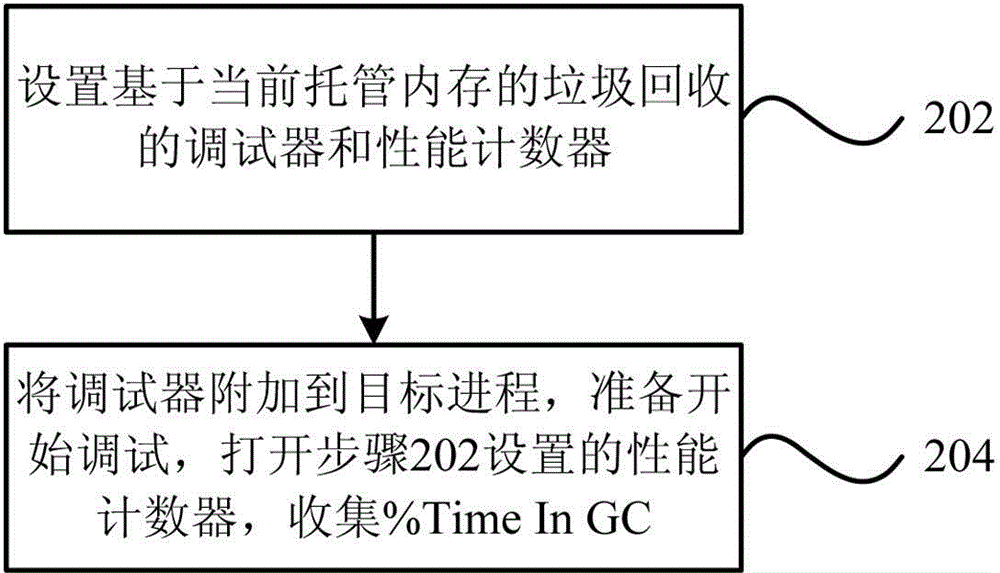
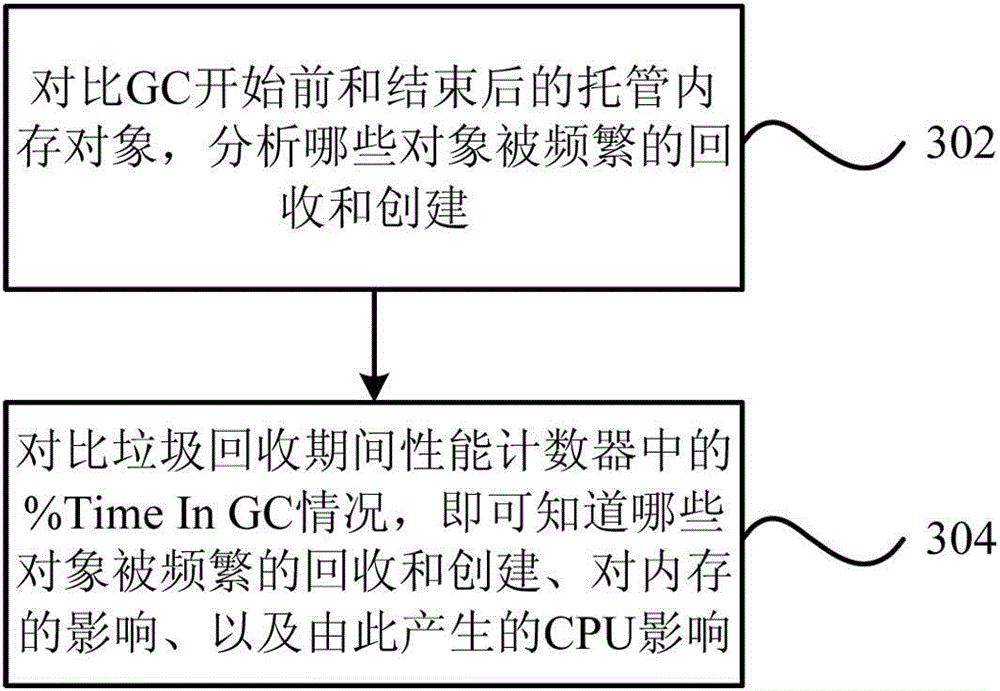
Memory analysis and optimization method and system based on garbage collection
The invention provides a memory analysis and optimization method based on garbage collection. The method comprises the steps as follows: appending garbage collection of current hosted memory to a target process; based on the garbage collection of the current hosted memory, which is appended to a target program, setting breakpoints for the beginning and ending of the garbage collection; when the set breakpoints are triggered, analyzing and outputting the information of the current hosted memory. The invention further provides a memory analysis and optimization system based on garbage collection. Through the technical scheme provided by the invention, a universal and unified analysis and optimization ideal can be created by fully utilizing memory analysis and optimization of accurately evaluating influence on system performance caused in each garbage collection process with existing codes on the basis of existing memory analysis based on garbage collection.
Owner:YONYOU NETWORK TECH
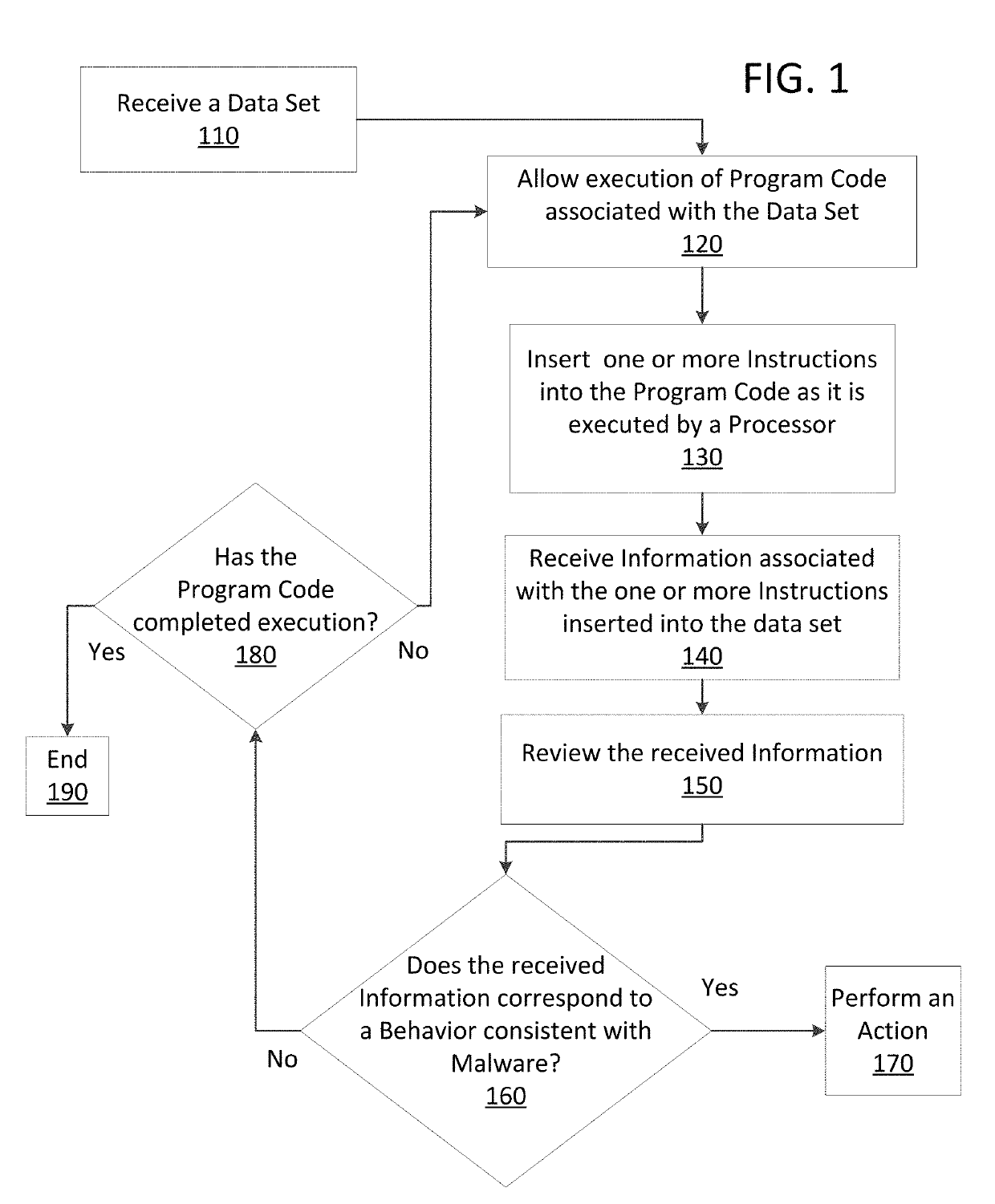
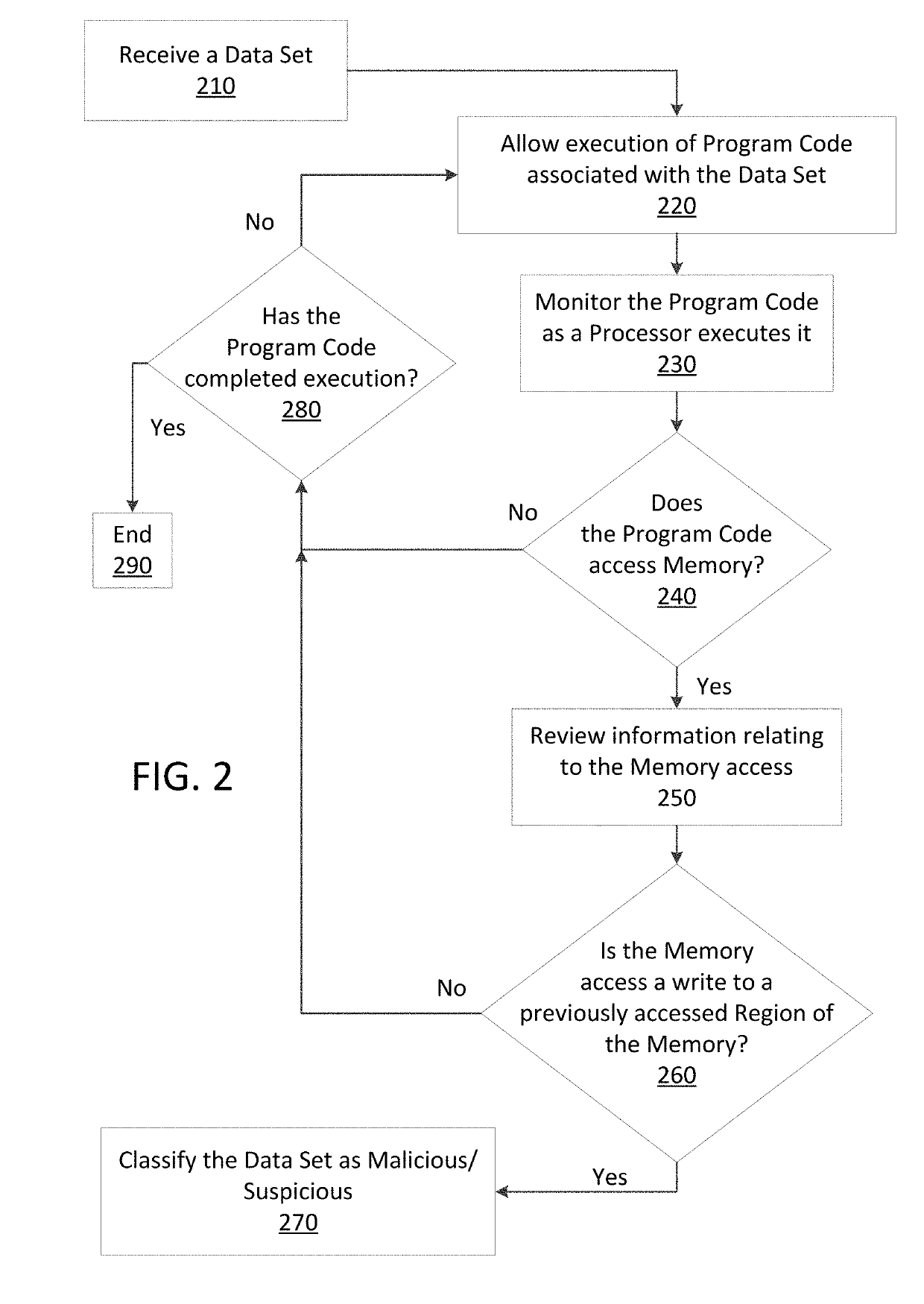
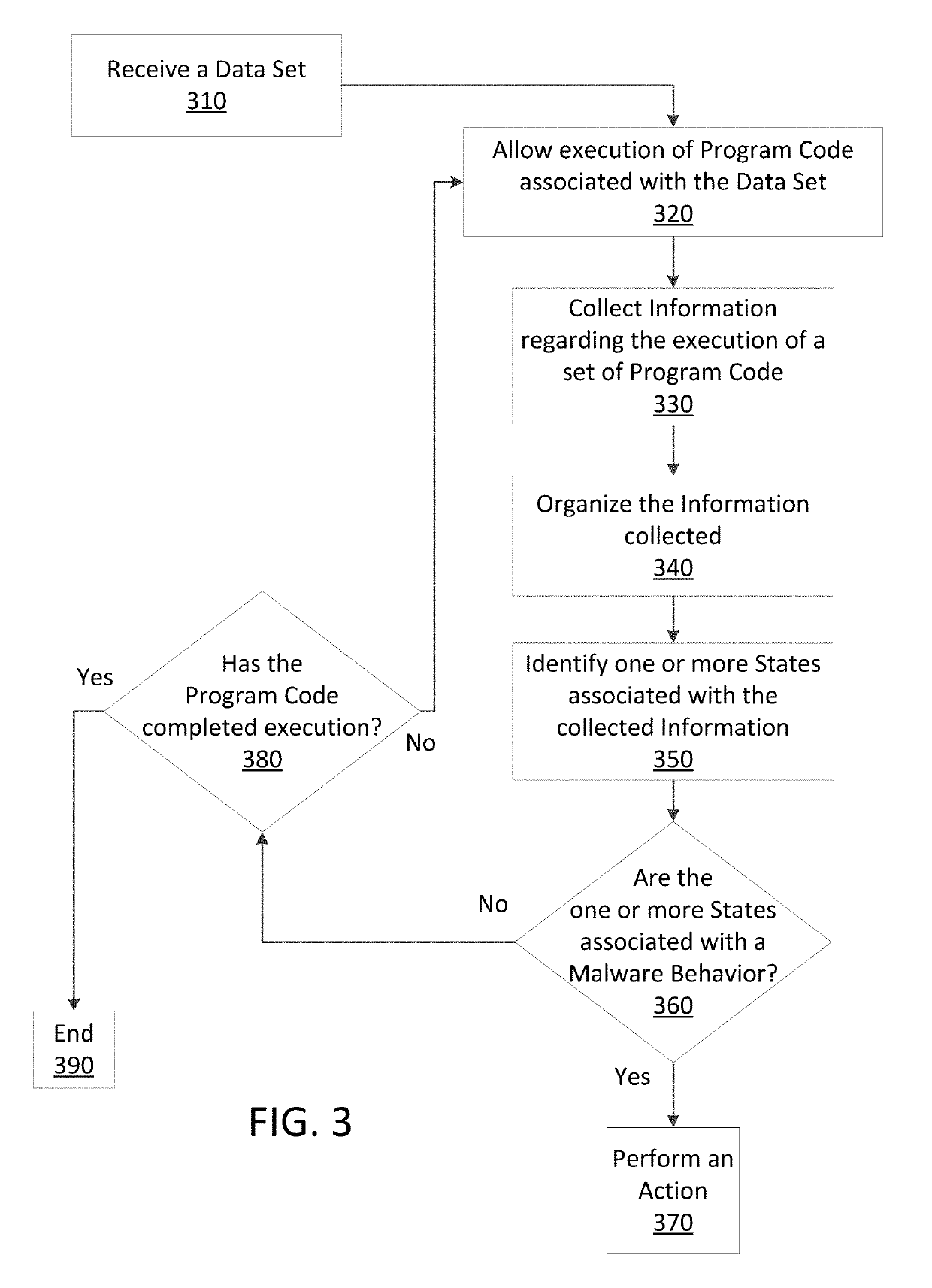
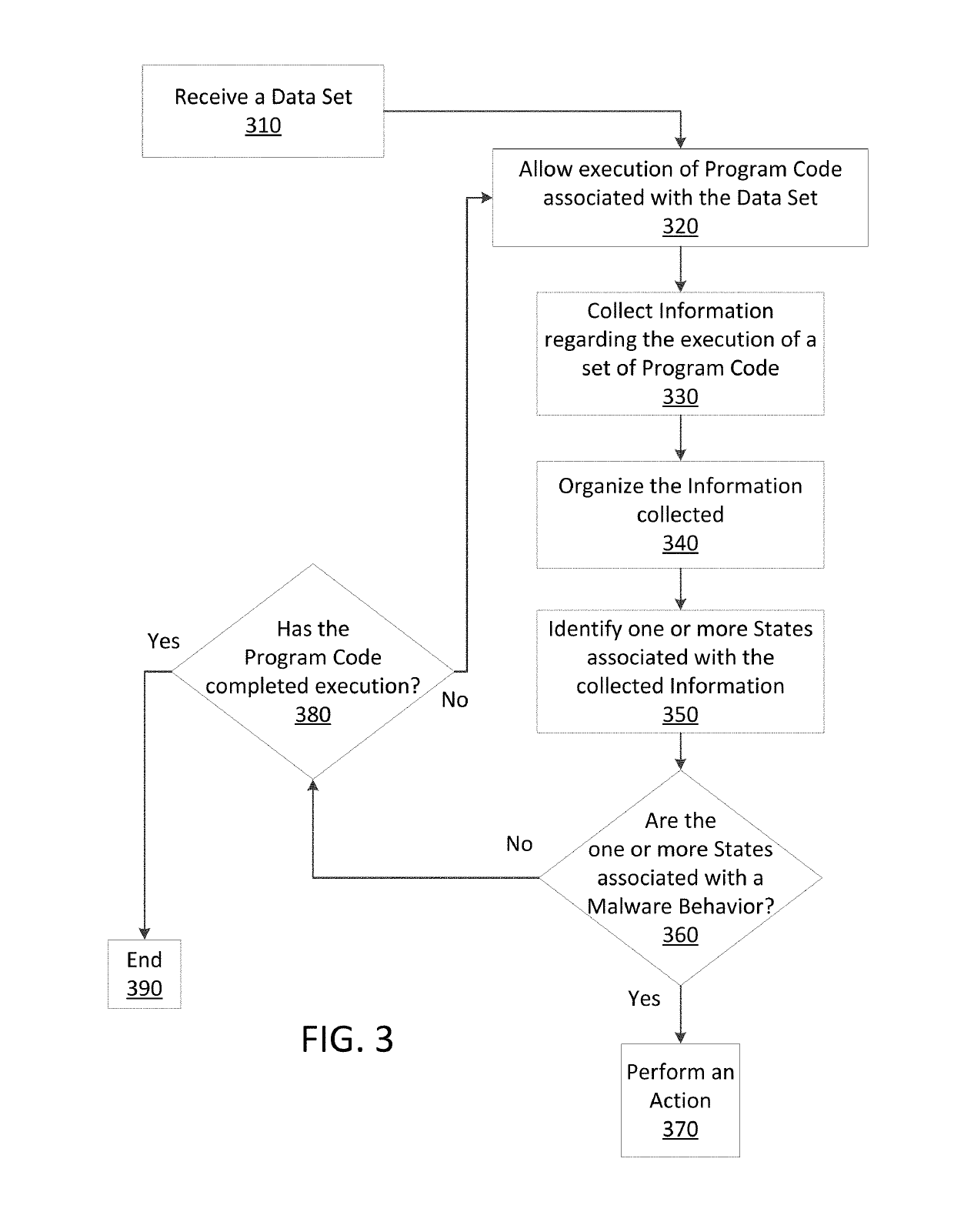
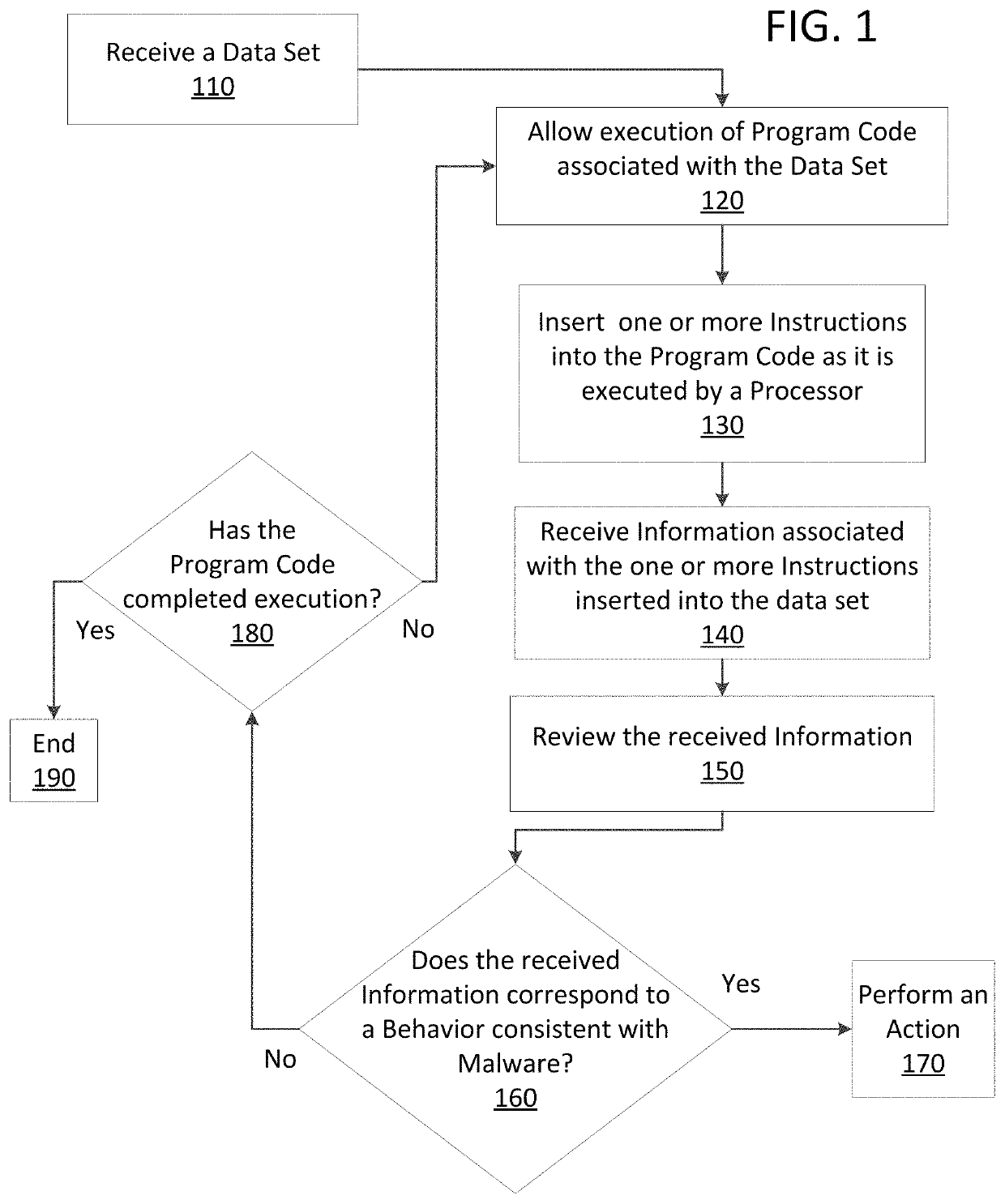
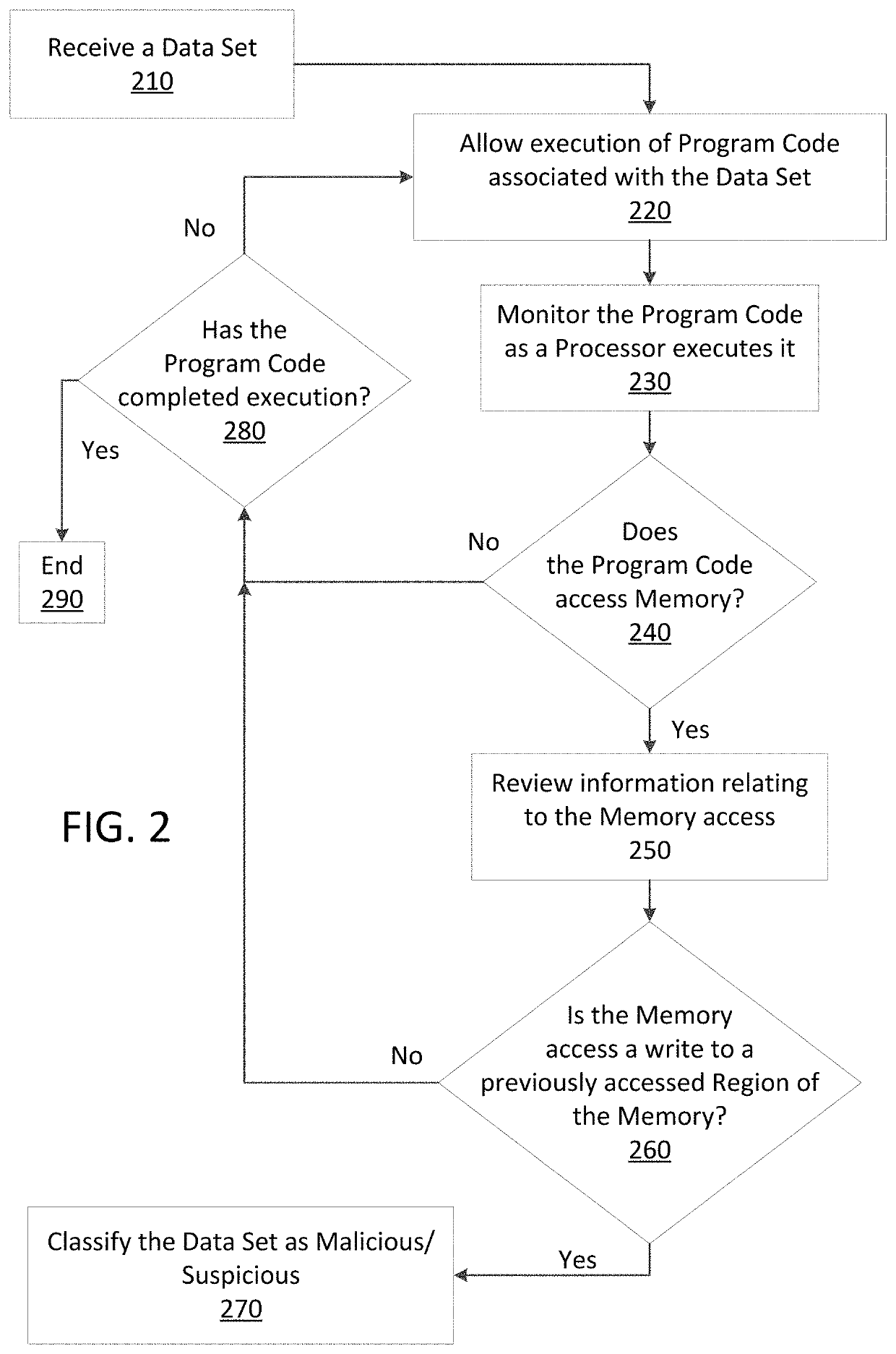
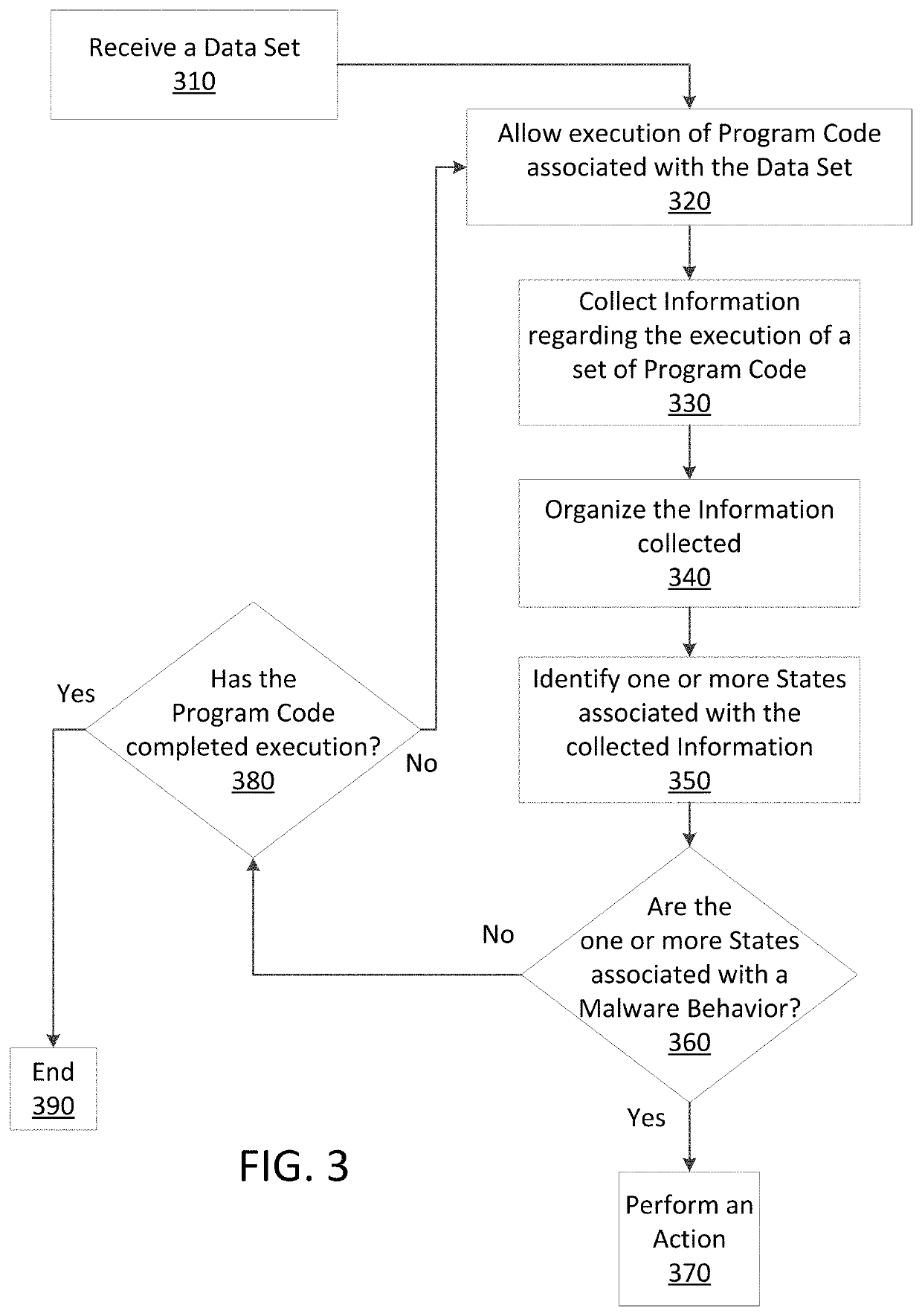
Just in time memory analysis for malware detection
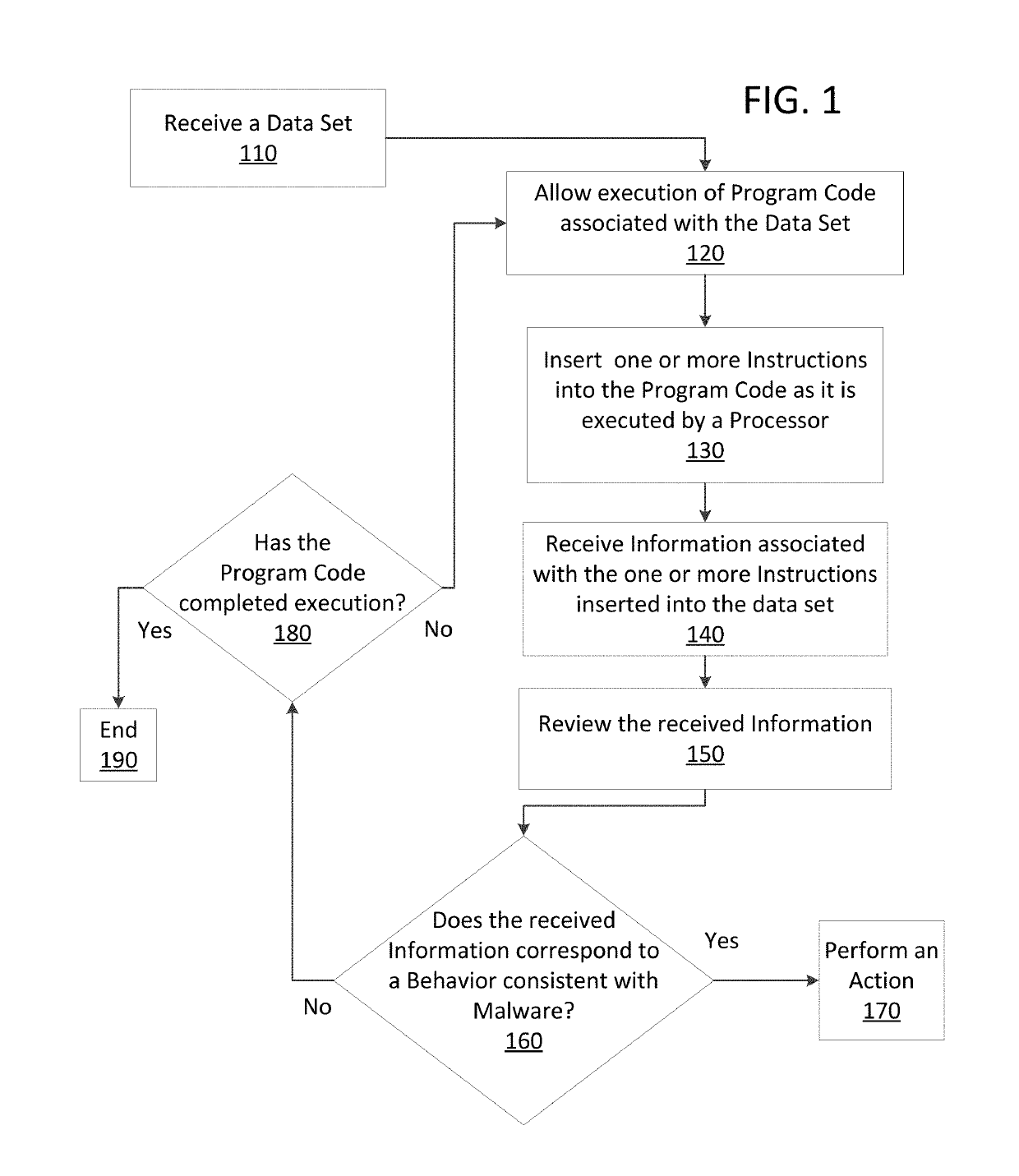
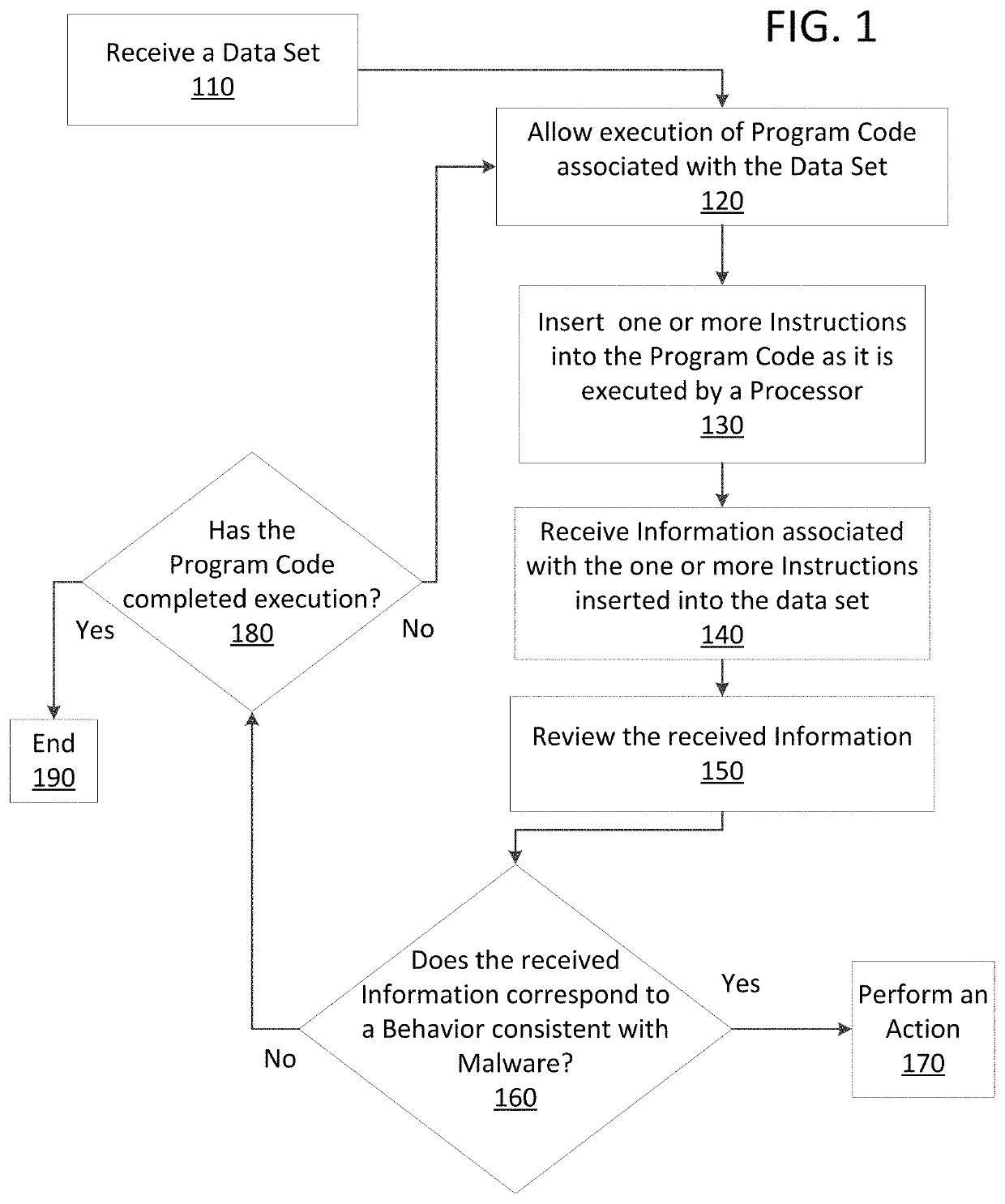
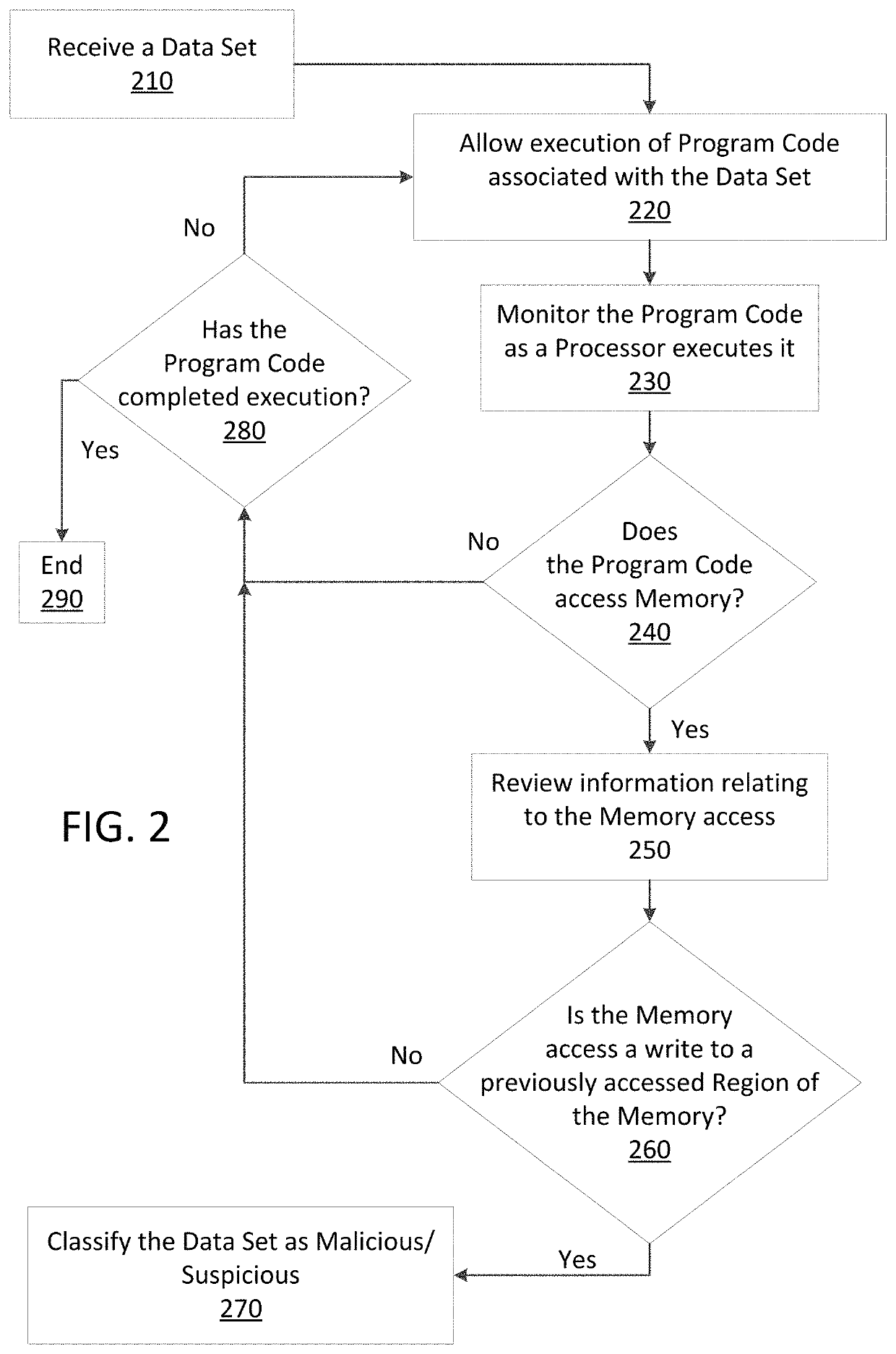
ActiveUS20190114421A1Preventing executionPrevent wrong actionPlatform integrity maintainanceMemory profilingData set
Methods and apparatus consistent with the present disclosure may use instrumentation code that remains transparent to an application program that the instrumentation code has been injected into. In certain instances, data sets that include executable code may be received via packetized communications or be received via other means, such as, receiving a file from a data store. The present technique allows a processor executing instrumentation code to monitor actions performed by the program code included in a received data set. Malware may be detected by scanning suspect program code with a malware scanner, malware may be detected by identifying suspicious actions performed by a set of program code, or malware may be detected by a combination of such techniques.
Owner:SONICWALL
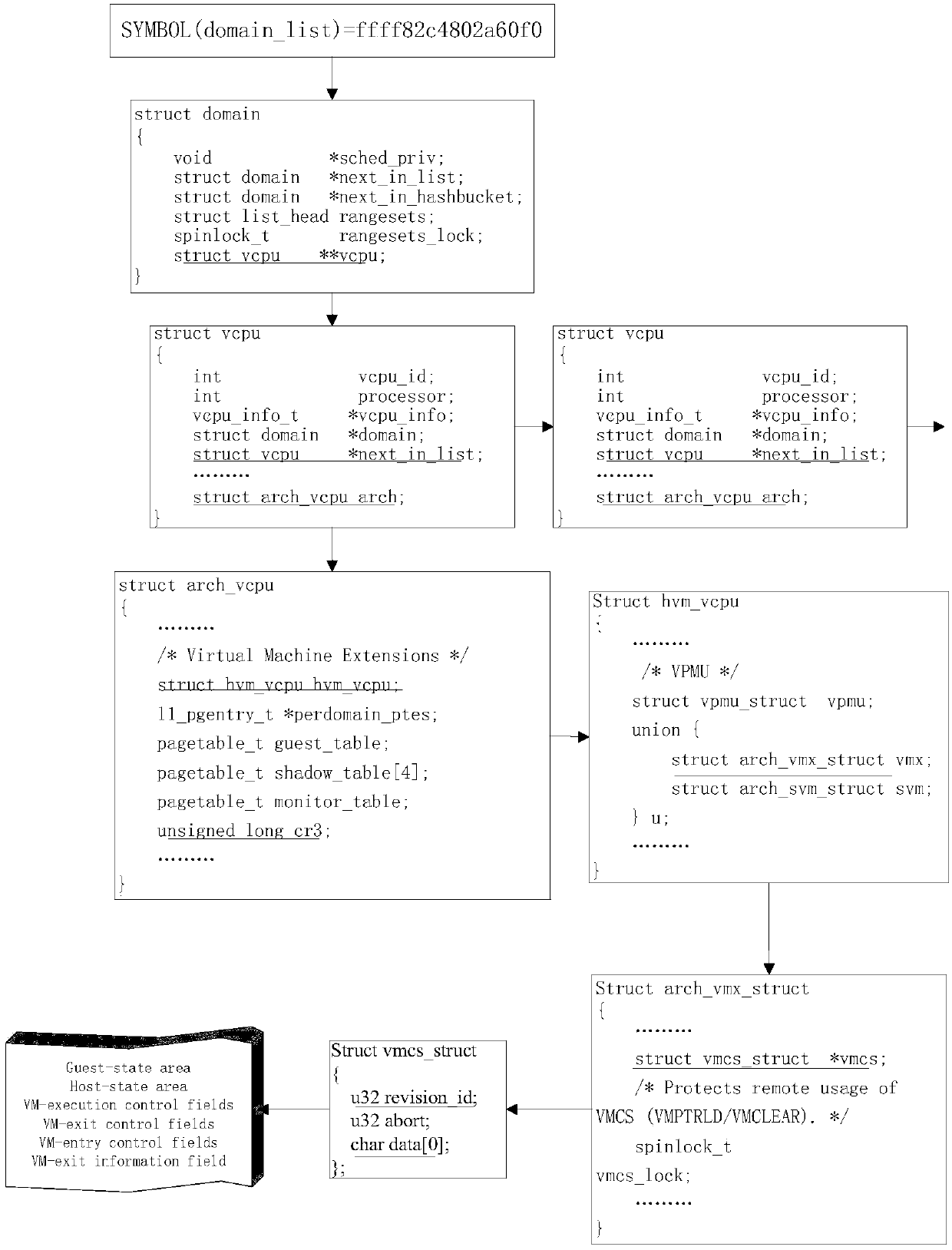
XenServer-platform-oriented Virtual machine memory evidence collection method
ActiveCN107621971ADoes not affect running statusNo eigenvalue retrieval requiredResource allocationSoftware simulation/interpretation/emulationMemory profilingMirror image
The invention discloses a XenServer-platform-oriented virtual machine memory evidence collection method. The method comprises the steps of obtaining physical memory information of a host computer as amemory mirror image file; obtaining a kernel symbol table file in the host computer; obtaining a physical address of vmcoreinfo_xen content; obtaining the vmcoreinfo_xen content according to the physical address, and parsing virtual addresses of domain_list and pgd_l4 of kernel symbols; converting the virtual address of pgd_l4 into a physical address; obtaining a structure body address; obtainingstructure bodies corresponding to virtual machines according to relationshipsamong structure bodies; achieving address conversion of the physical addresses of the virtual machines; judging versions of virtual machine operating systems after the content of physical memories of the virtual machines is obtained; analyzing the physical memories by using corresponding memory analysis methods accordingto the different versions of the virtual machine operating systems after the virtual machine operating systems are determined.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Method and System for Facilitating Memory Analysis
InactiveUS20110078684A1Easy to analyzeError detection/correctionMultiprogramming arrangementsMemory access patternMemory analysis
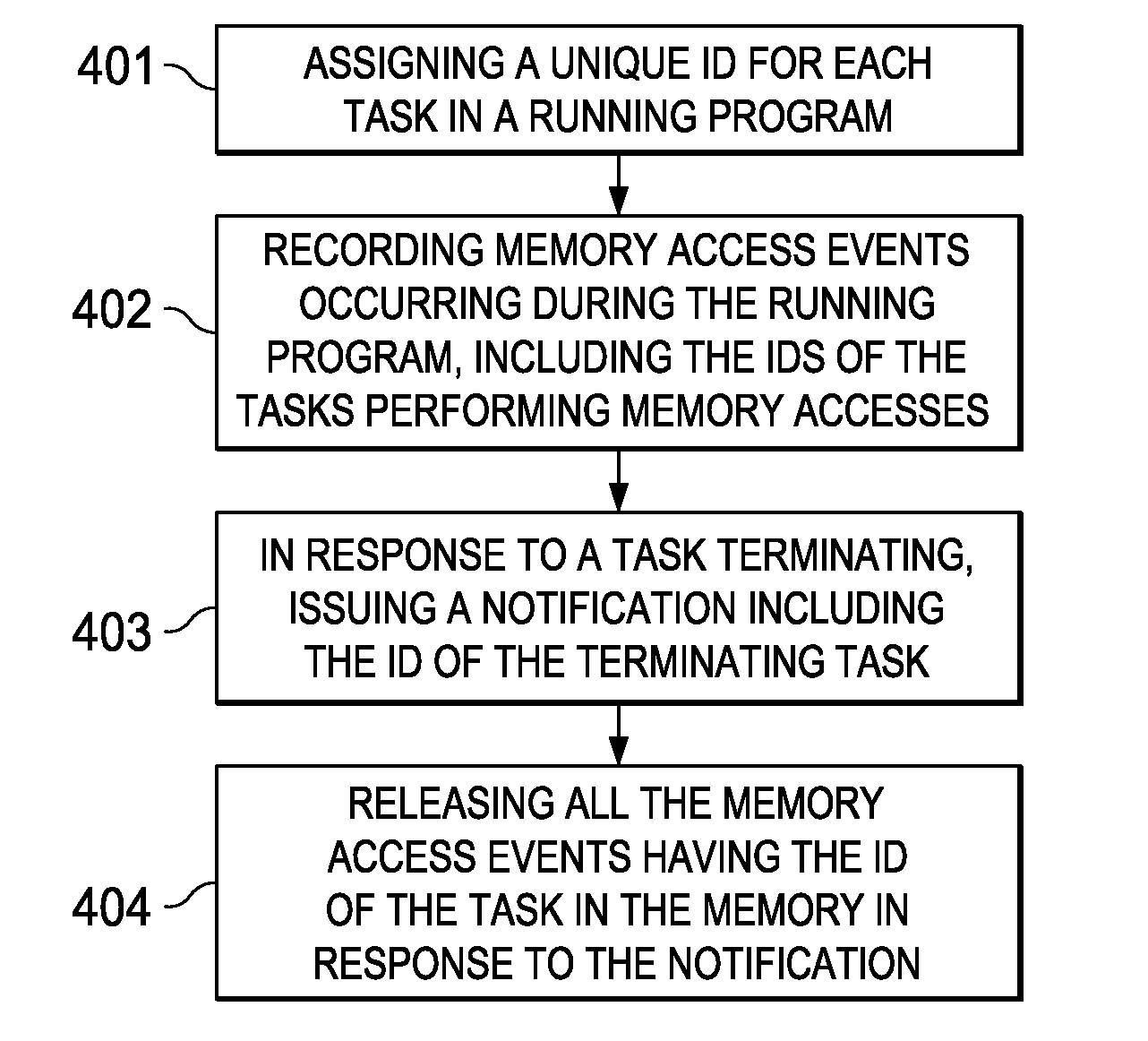
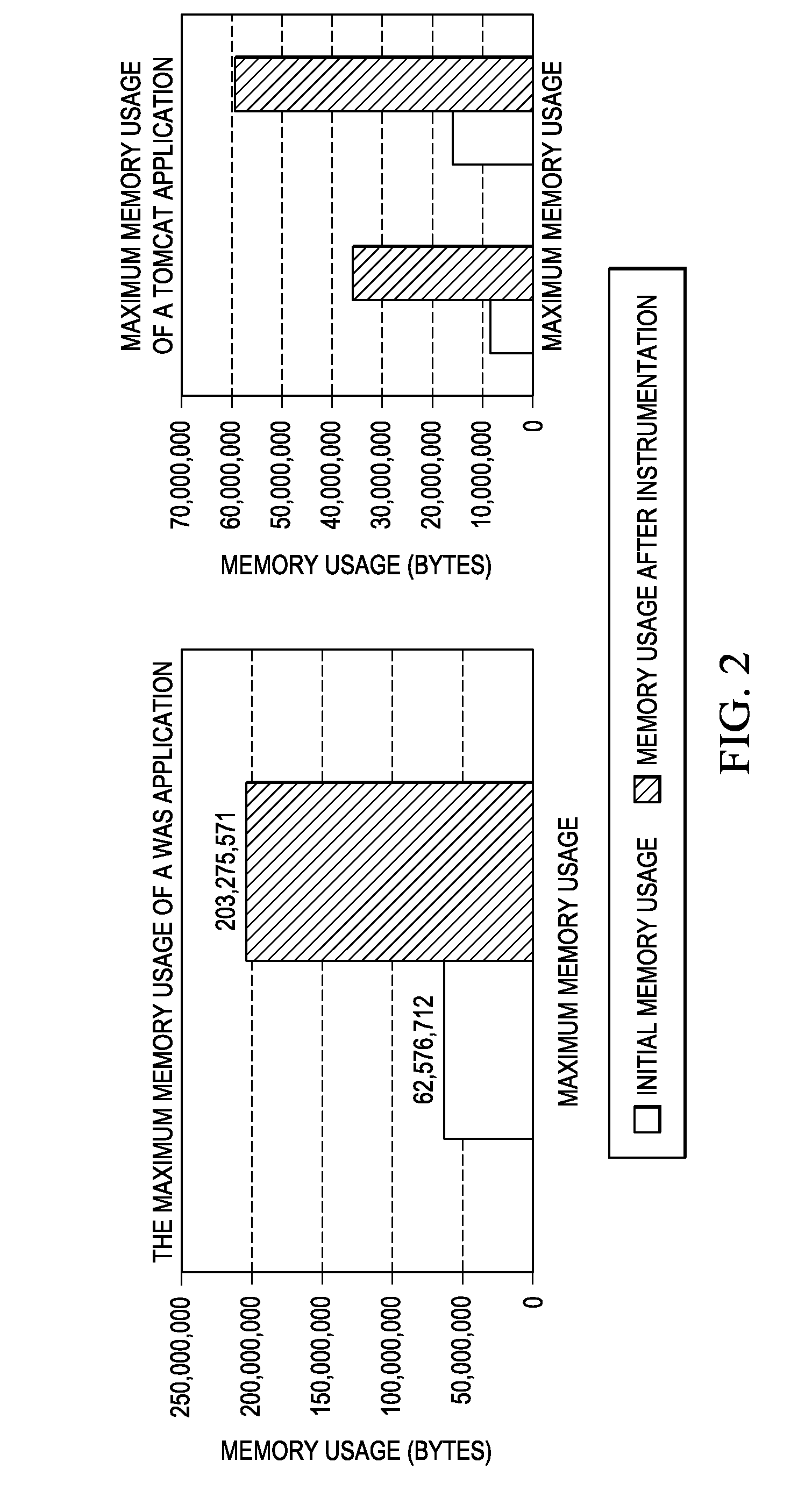
A method and system for facilitating runtime memory analysis. The method includes: assigning a unique ID for each task in a running program; recording memory access events occurring during the running program, including the IDs of the task performing the memory accesses; issuing a task termination notification in response to a task terminating, the task termination notification including the ID of the terminating task; and releasing all the memory access events having the ID of the terminating task in the memory, in response to the task termination notification. This method and system can ensure that the memory access events stored in the memory will not increase unlimitedly, so that the memory overhead is reduced remarkably and dynamic memory analysis can be faster and more efficient.
Owner:IBM CORP
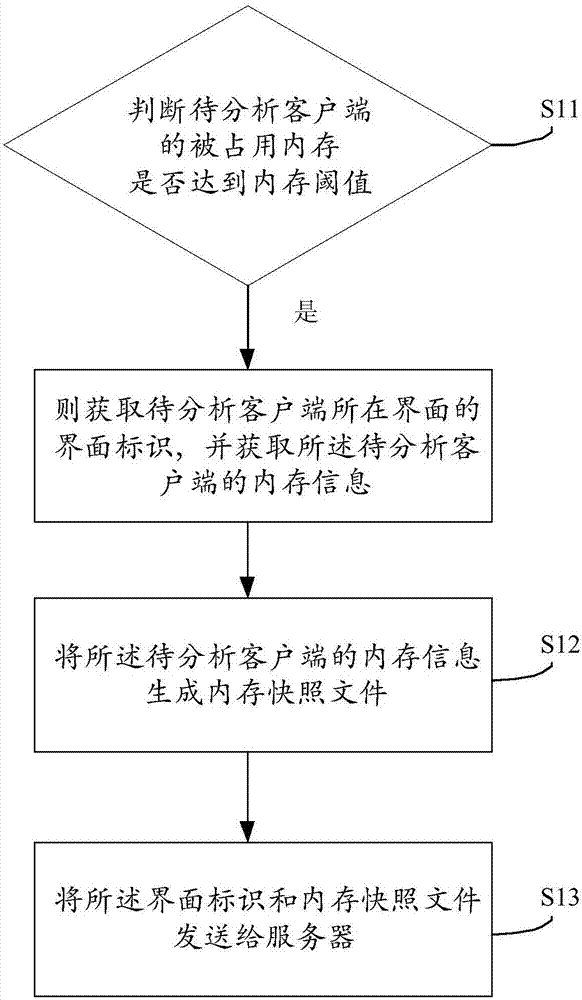
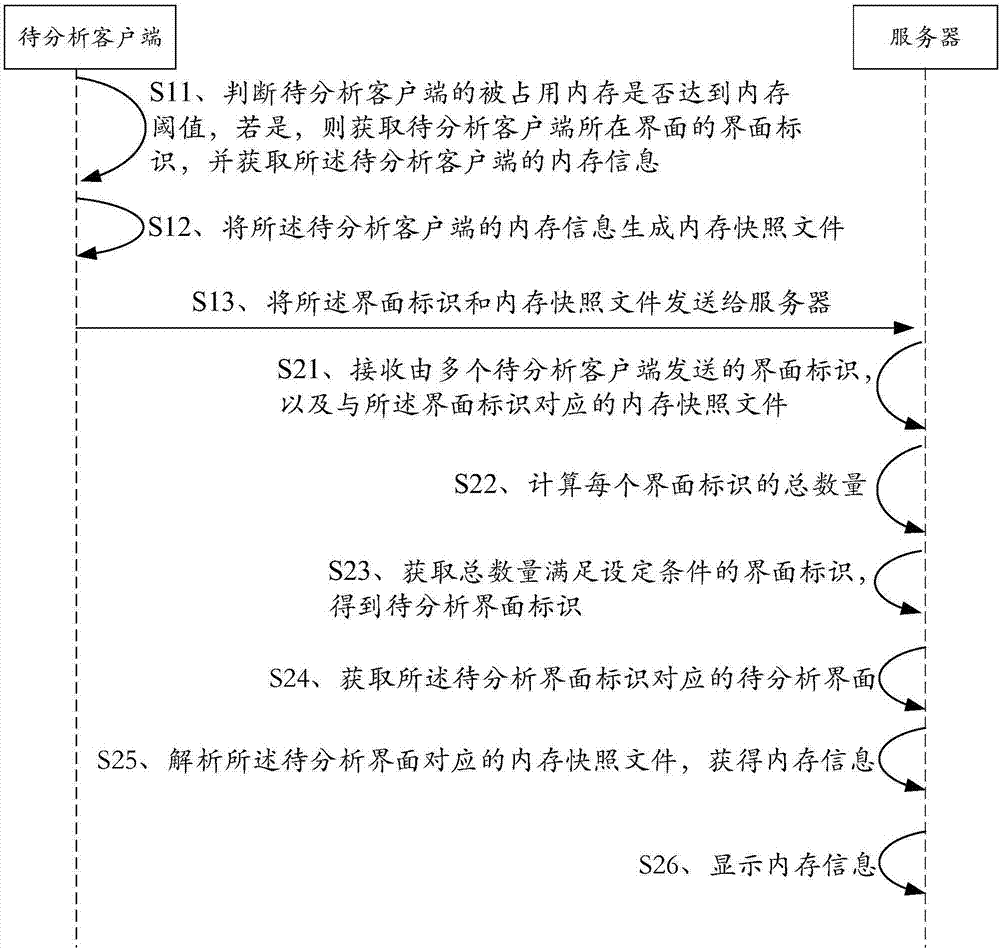
Memory analysis method, device and system for client side
The invention discloses a memory analysis method, device and system for a client side. The memory analysis method for the client side comprises the following steps that: receiving interface identification sent from a plurality of client sides to be analyzed, and memory snapshot files corresponding to the interface identification; calculating the total amount of each piece of interface identification; obtaining the interface identification of which the total amount meets a set condition to obtain interface identification to be analyzed; obtaining a to-be-analyzed interface corresponding to the interface identification to be analyzed; and analyzing the memory snapshot file corresponding to the to-be-analyzed interface to obtain memory information. By use of the method, memory problems generated in a process that the user practically uses the client side, and a corresponding interface can be obtained, and test personnel or development personnel can make a corresponding improvement on the client side.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Automated scalable and adaptive system for memory analysis via online region evolution tracking
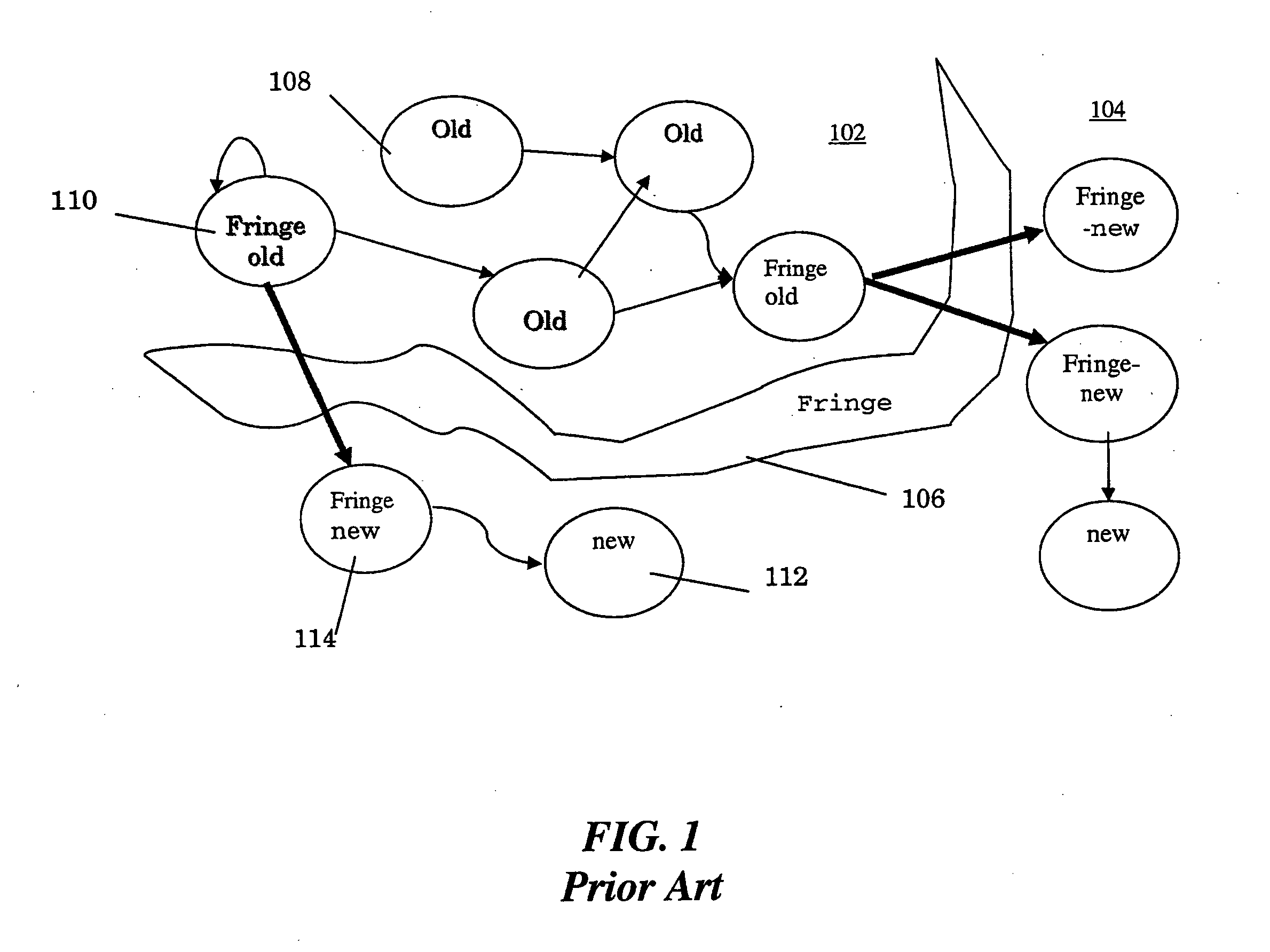
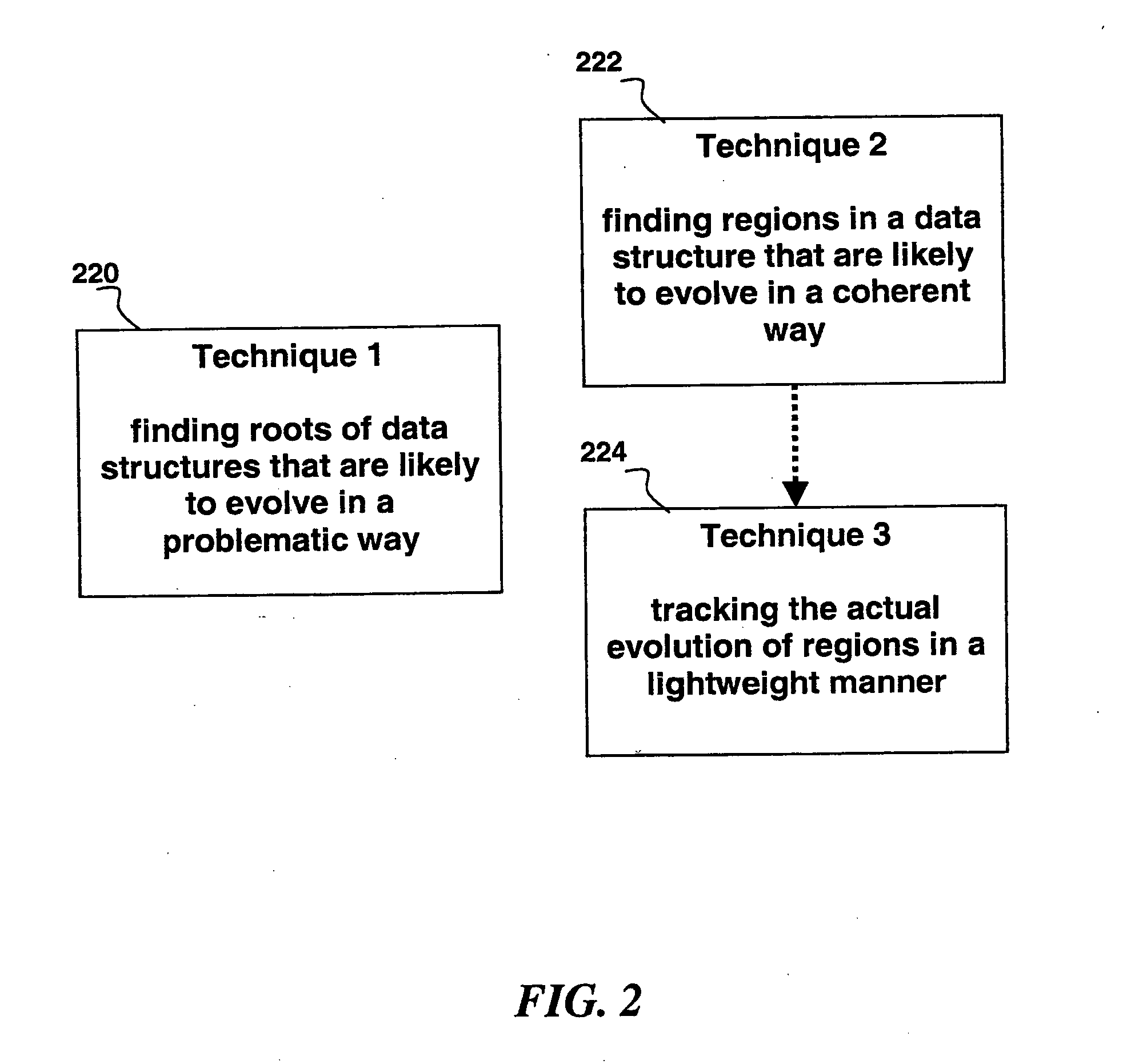
InactiveUS20050071343A1Non-redundant fault processingSpecial data processing applicationsMemory profilingMulti method
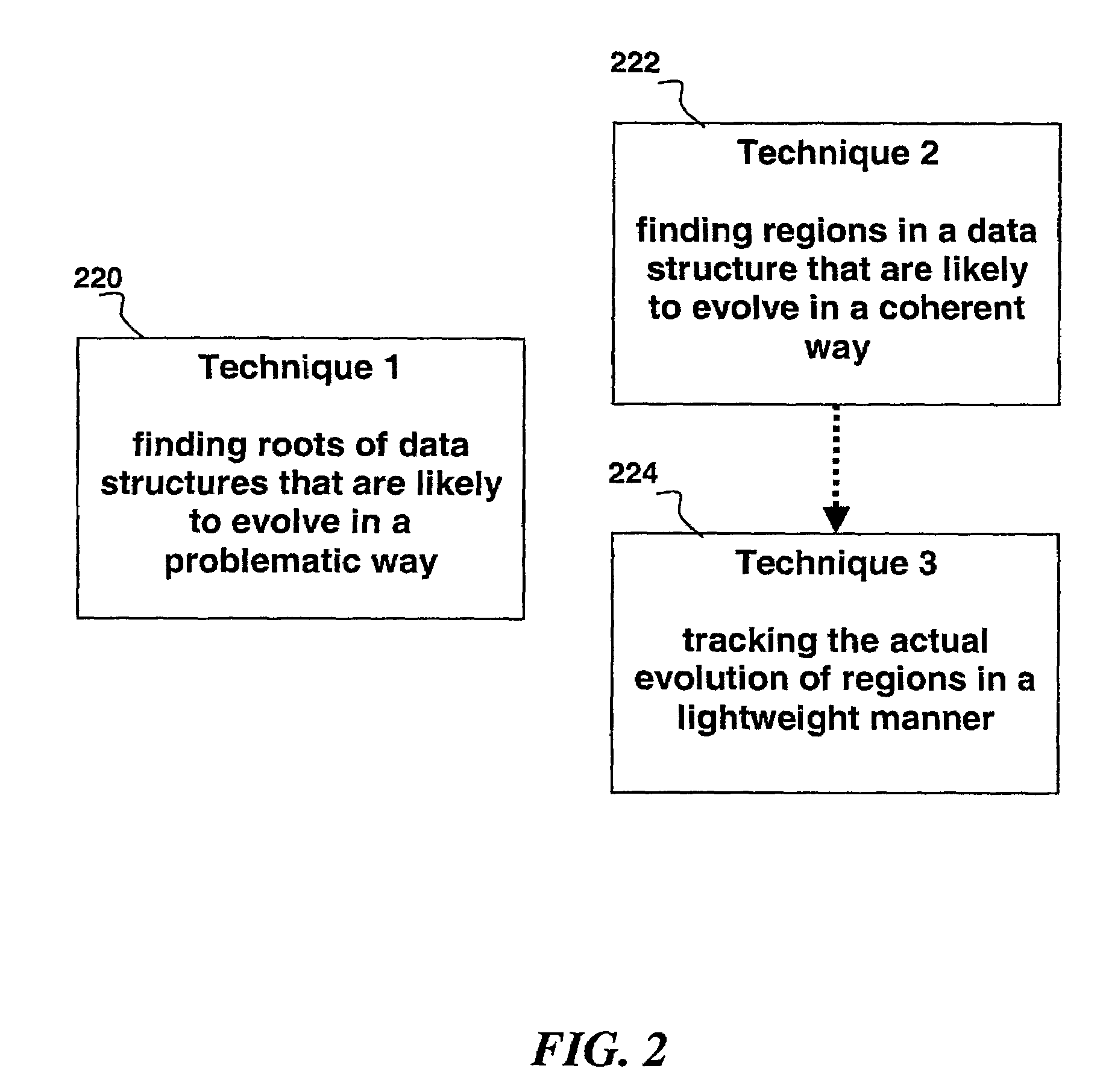
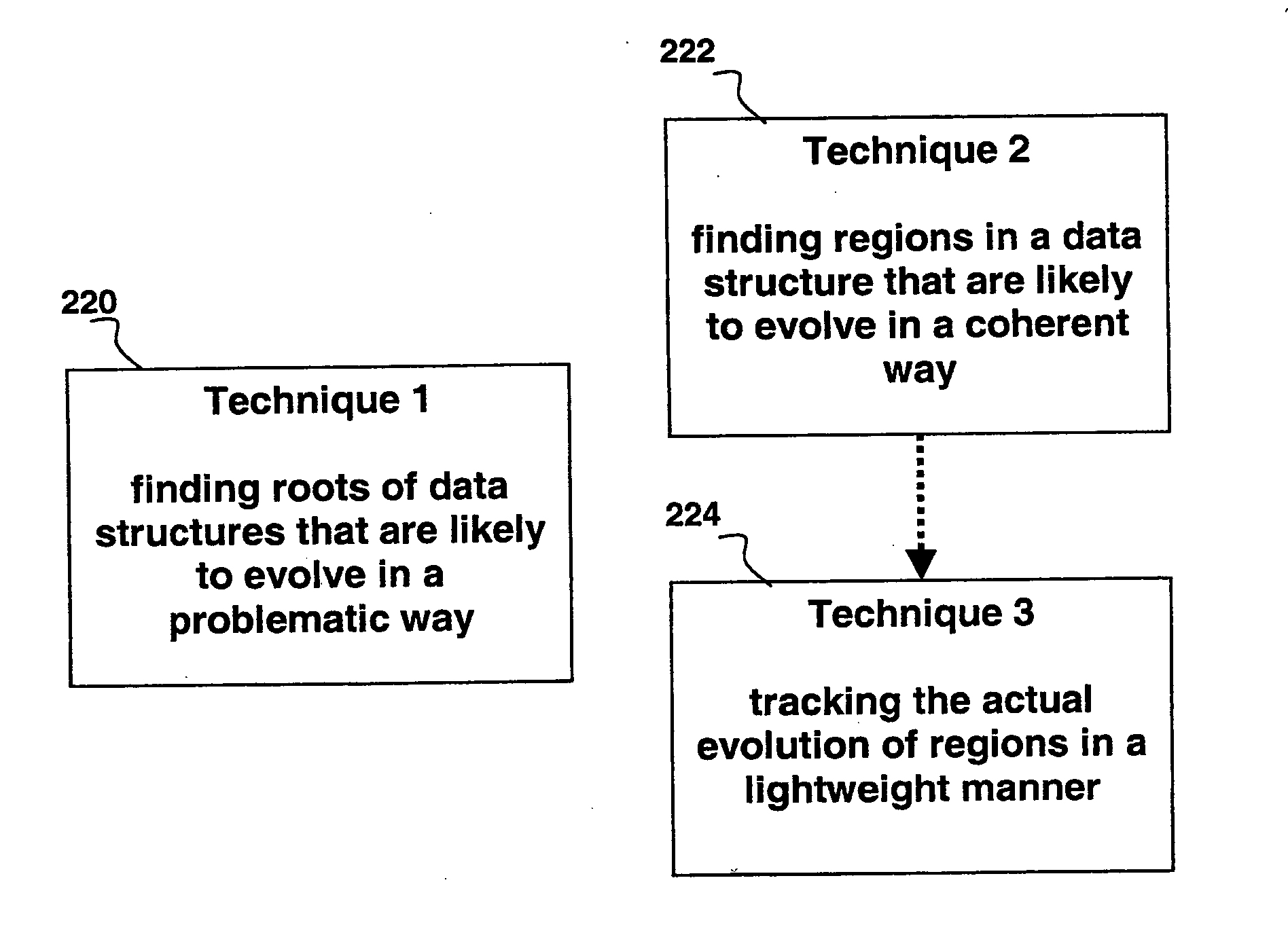
A method for determining how a region of a data structure in an application evolves comprises the steps of: periodically traversing selected subgraphs of the region in the running application; location structural changes in the subgraphs; using these structural changes to describe, characterize, and identify changes to the region as a whole; and reporting the region changes to an analysis agent. Determining how a region of a data structure evolves is a continuous and adaptive process. The process is made continuous and adaptive through several methods, including: identifying a set of desired updates; adjusting the period in between traversals based on whether the desired updates have been witnessed; and adjusting the frequency of sampling any one traversal based on whether that traversal has detected desired updates. Additionally, the method comprises updating qualitative and quantitative characterizations of the regions under analysis based on structural changes to the regions as whole.
Owner:IBM CORP
Just in time memory analysis for malware detection
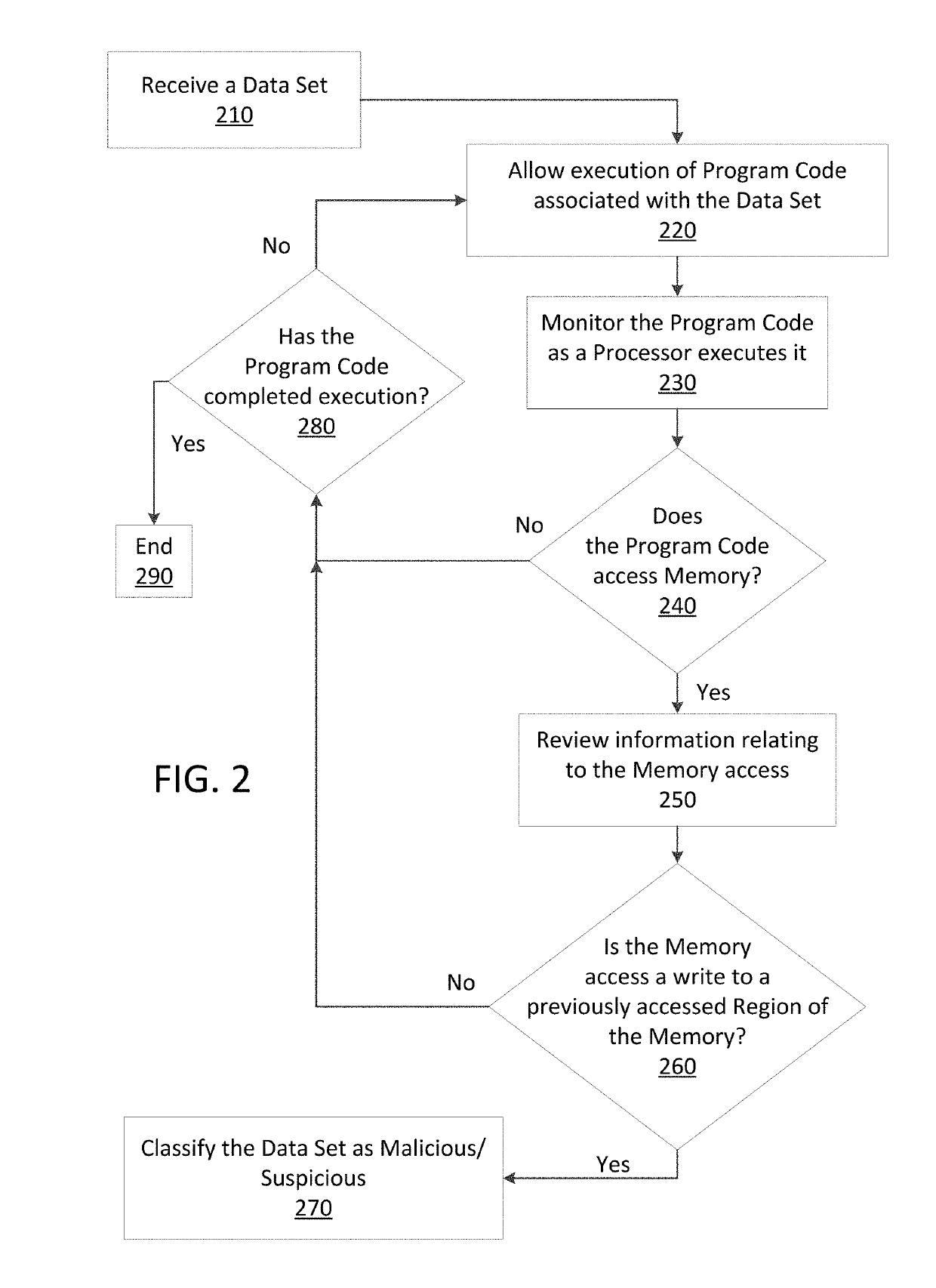
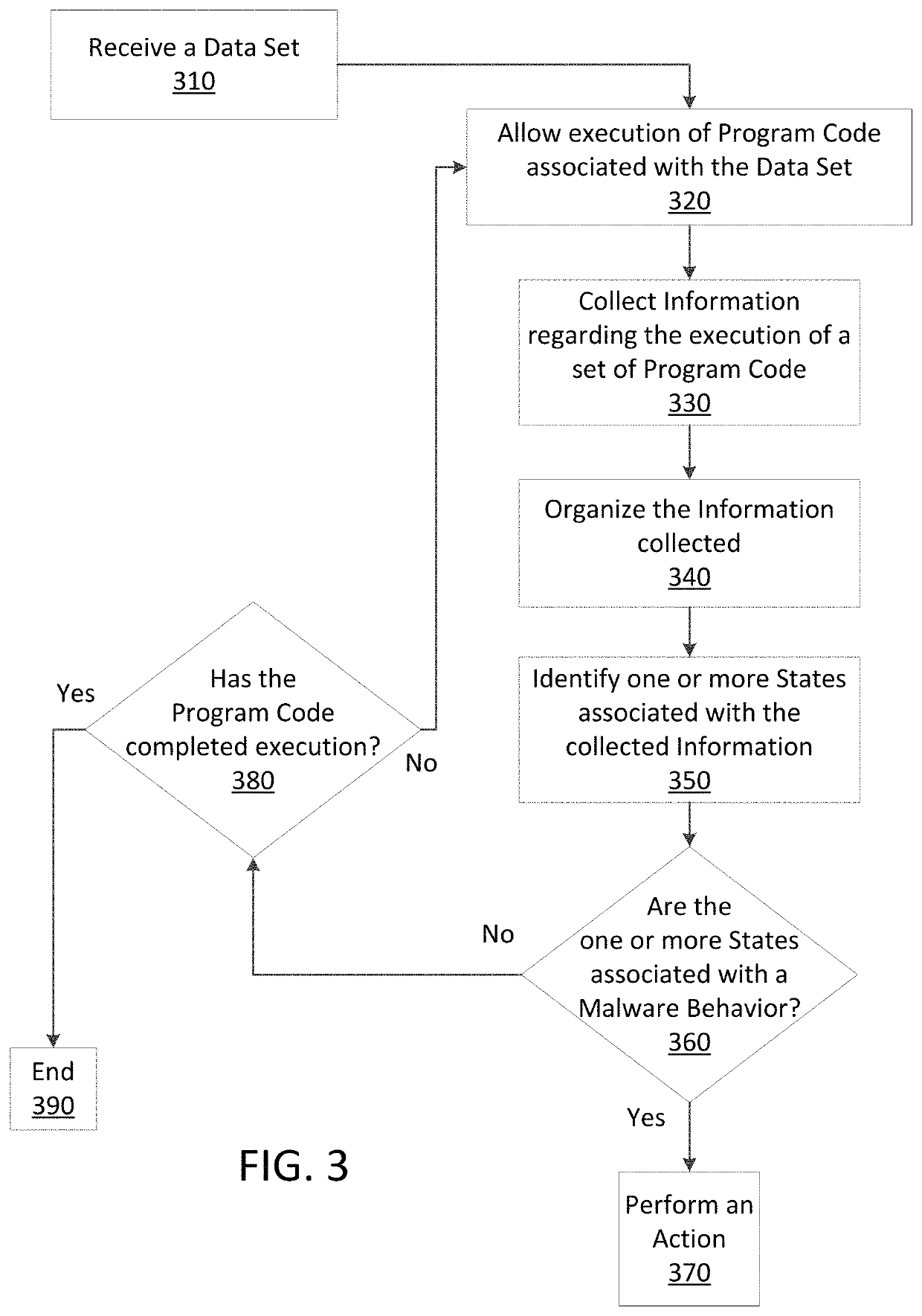
ActiveUS20190236275A1Preventing executionInhibitory contentPlatform integrity maintainanceMemory profilingData set
Methods and apparatus consistent with the present disclosure may use instrumentation code that remains transparent to an application program that the instrumentation code has been injected into. In certain instances, data sets that include executable code may be received via packetized communications or be received via other means, such as, receiving a file from a data store. The present technique allows one or more processors executing instrumentation code to monitor actions performed by the program code included in a received data set. Malware can be detected using exception handling to track memory allocations of the program code included in the received data set.
Owner:SONICWALL
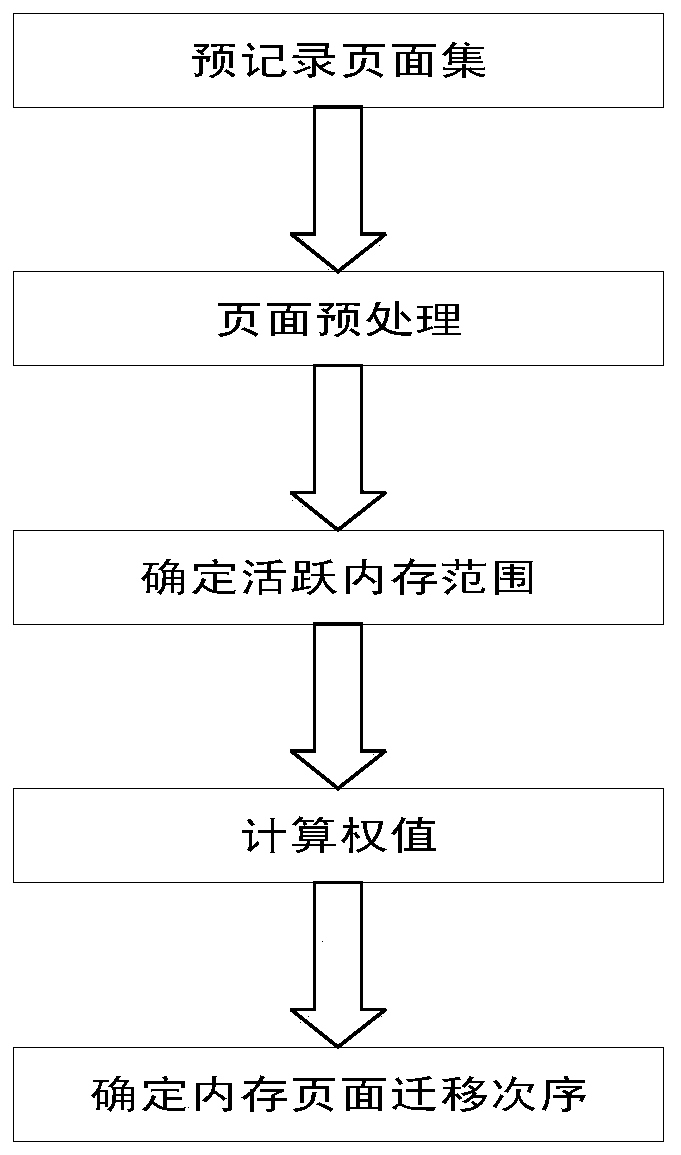
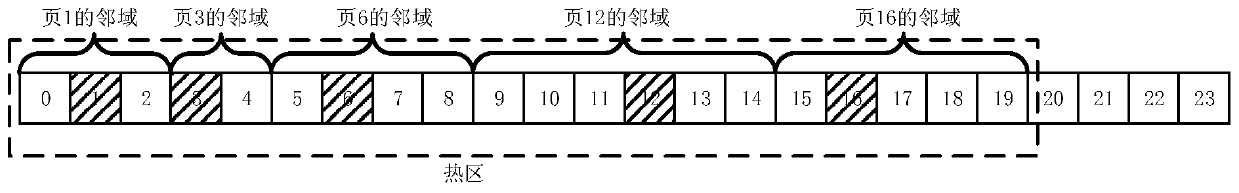
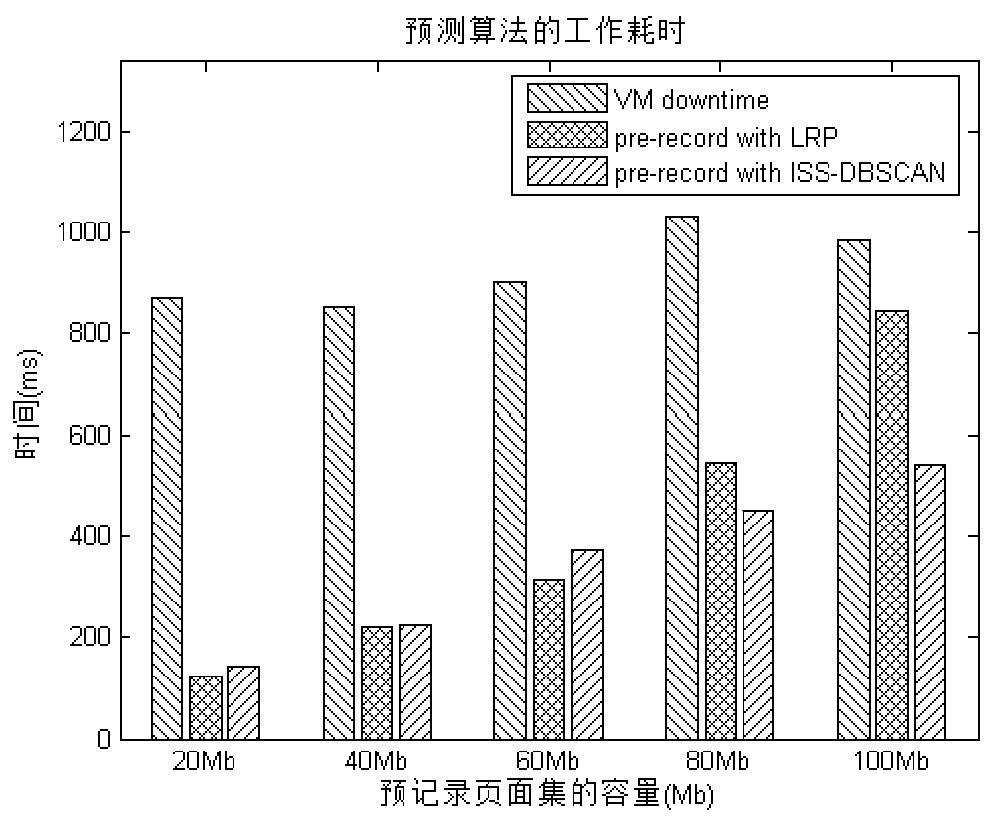
Active memory prediction migration method in virtual machine migration process
ActiveCN110795213AIndicates the situation of being visitedReflect the active stateSoftware simulation/interpretation/emulationParallel computingTheoretical computer science
The invention discloses an active memory prediction migration method in a virtual machine migration process and belongs to the technical field of virtual machine migration. The method comprises the following steps of: firstly, preprocessing a pre-recorded page set consisting of an address of an accessed memory and accessed time recorded by a virtual machine manager by adopting a method of expressing each memory page by using a six-tuple; and then calculating a priority weight of the memory page, and performing clustering analysis by adopting an ISS-DBSCAN clustering algorithm to determine an active memory range; and finally, adjusting the sending sequence of the active memory pages by taking the priority weight of the memory pages as a judgment basis of the priority. According to the method, a theoretical basis and a method are provided for active memory analysis, the activity degree of the memory page can be effectively predicted, and the memory migration efficiency is improved.
Owner:宁波谦川科技有限公司
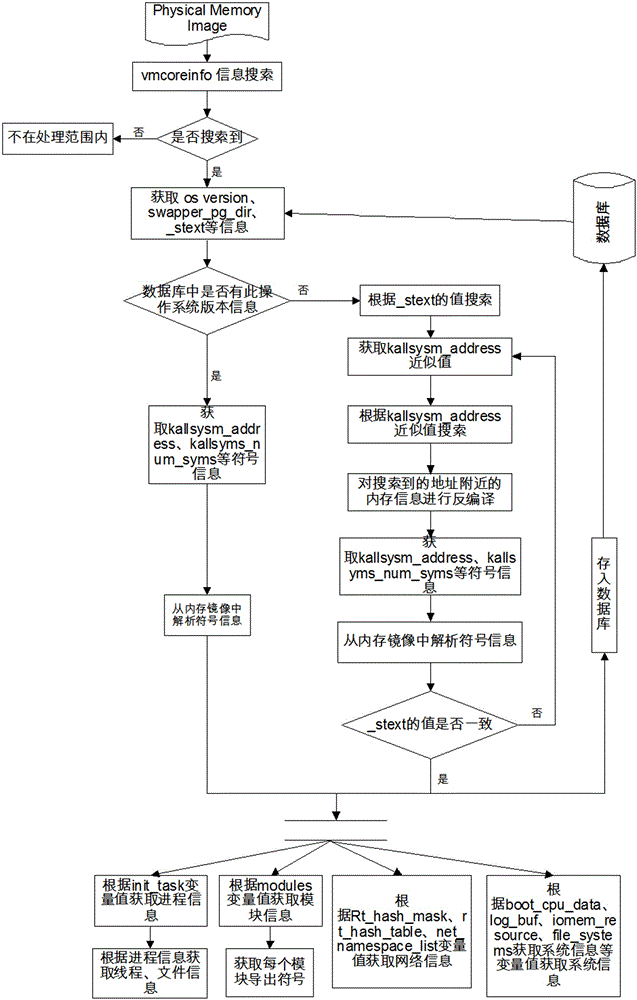
Physical memory mirror image document analysis method of Linux system
ActiveCN105160001AAchieve recoveryBreak the limitationsFile/folder operationsSpecial data processing applicationsMemory profilingDocument analysis
The invention discloses a physical memory mirror image document analysis method of a Linux system. The physical memory mirror image document analysis method of the Linux system comprises the following steps: a) judging the version of an operating system and obtaining a page directory address; b) carrying out address conversion; c) recovering a stored system kernel symbol table in a database; d) recovering system kernel symbols which are not stored in the database; e) obtaining system key information; and f) obtaining a module exporting symbol table. The step c) comprises the following steps: c-1) obtaining a number of kernel symbols; c-2) obtaining the types and the names of the kernel symbols; and c-3) obtaining the virtual addresses of the kernel symbols. The step e) comprises the following steps: e-1) obtaining process information and document information; e-2) obtaining loaded module information; and e-3) obtaining a network, a CPU (Central Processing Unit), a log and debugging information. The analysis method exhibit general applicability, breaks through boundedness that a traditional method must know internal system version information and additional kernel symbol table documents, provides the general analysis method for the memory of the Linux system, and has outstanding beneficial effects.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Mobile terminal memory analysis method and device, storage medium and electronic equipment
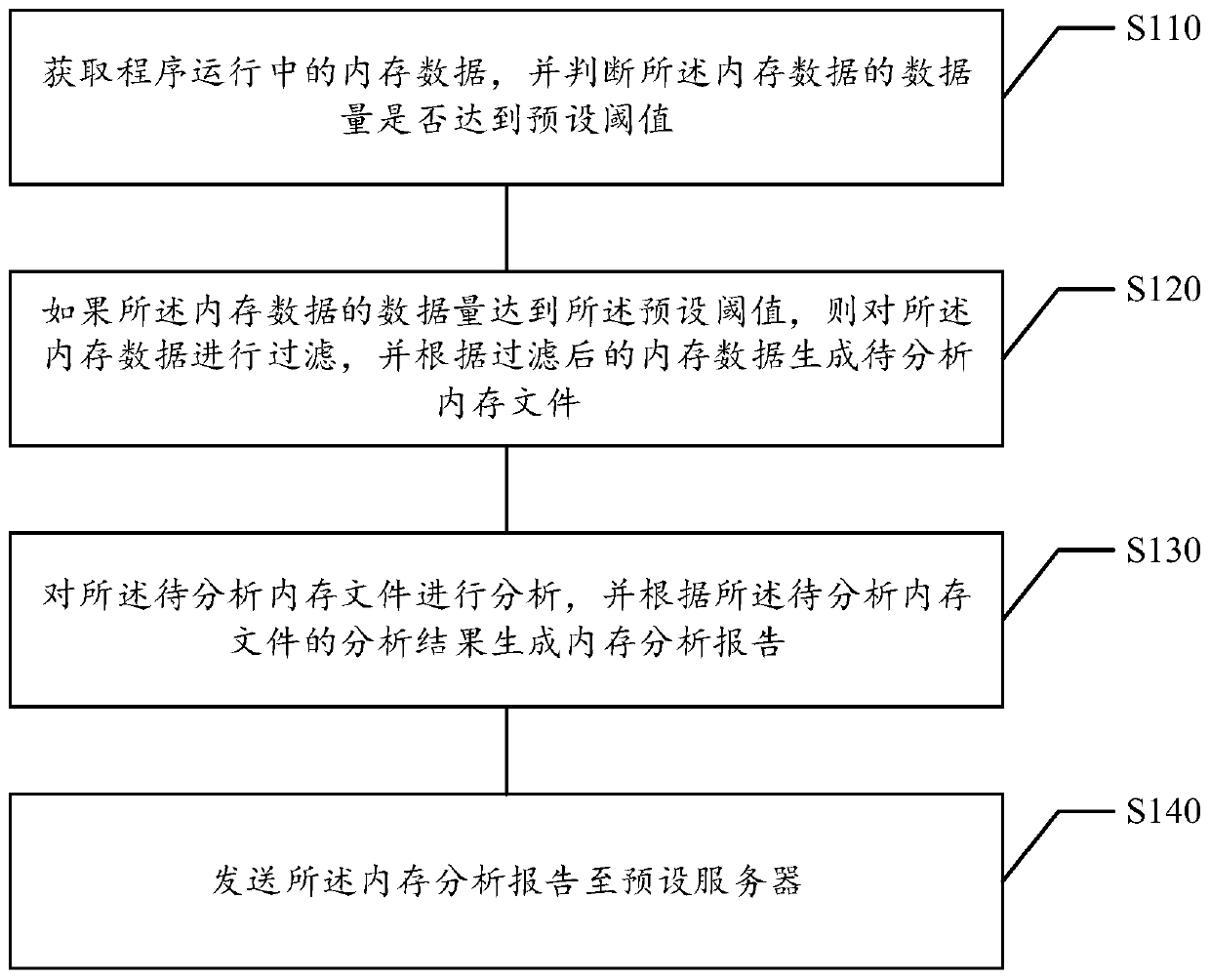
ActiveCN109828859ASolve complex problemsHigher level of problem reductionFault responseEnergy efficient computingMemory profilingAnalysis method
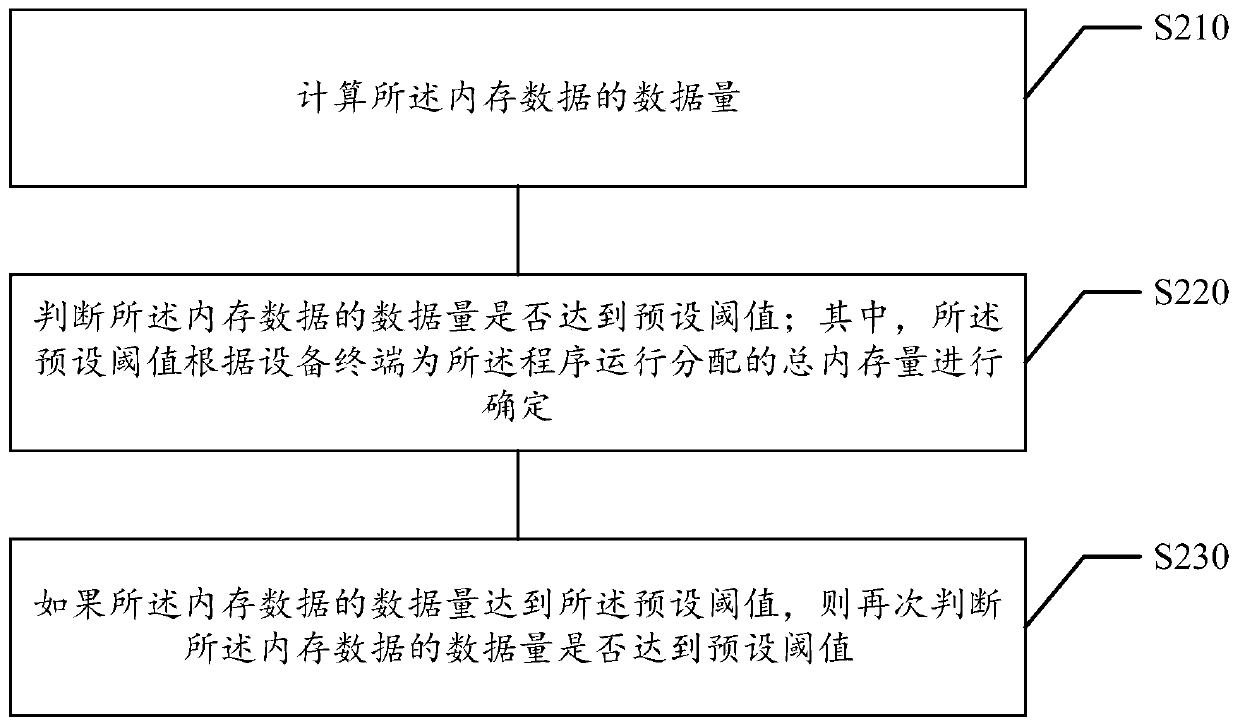
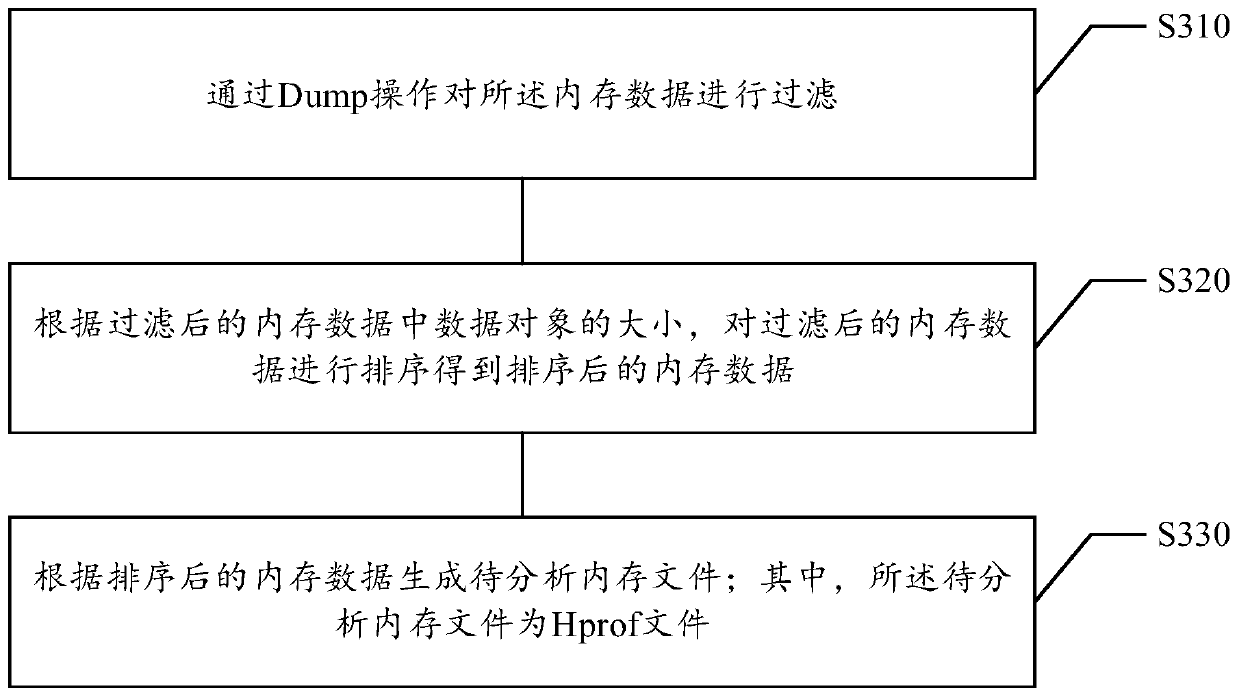
The embodiment of the invention relates to a mobile terminal memory analysis method and device, and belongs to the technical field of computers, and the method comprises the steps: obtaining memory data in program operation, and judging whether the data volume of the memory data reaches a preset threshold value or not; if the data size of the memory data reaches the preset threshold value, filtering the memory data, and generating a to-be-analyzed memory file according to the filtered memory data; analyzing the memory file to be analyzed, and generating a memory analysis report according to ananalysis result of the memory file to be analyzed; And sending the memory analysis report to a preset server. The method solves the problem that in the prior art, memory analysis complexity is high due to the fact that memory problems need to be reproduced, the memory analysis complexity is reduced, and meanwhile the memory analysis speed is increased.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Memory analysis method and device and computer readable storage medium
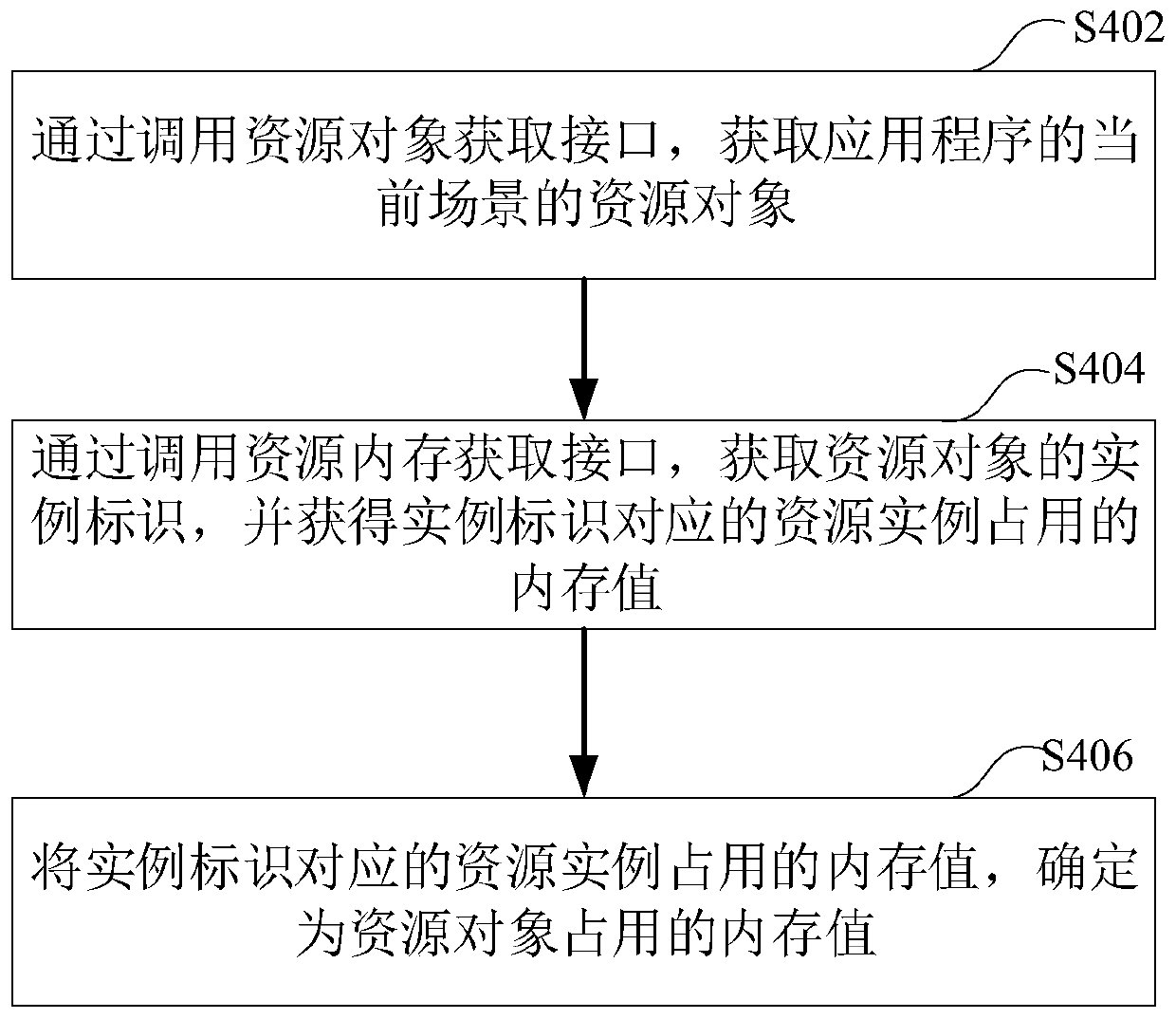
PendingCN110231994AImprove performanceResource allocationSoftware simulation/interpretation/emulationMemory profilingApplication software
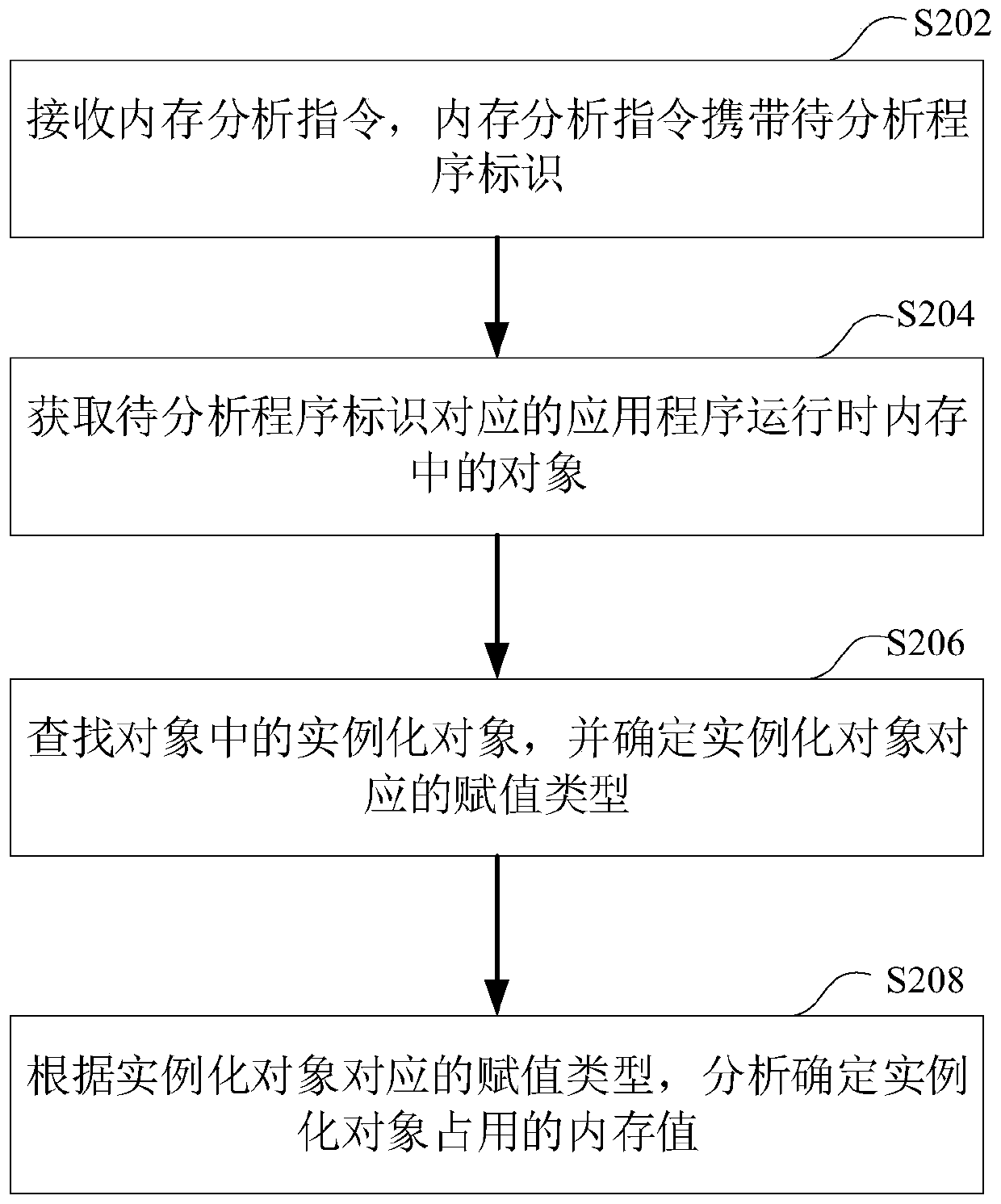
The invention relates to a memory analysis method and device, a computer readable storage medium and computer equipment, and the method comprises the steps: receiving a memory analysis instruction, the memory analysis instruction carrying a to-be-analyzed program identifier; obtaining an object in a memory when the application program corresponding to the to-be-analyzed program identifier runs; searching an instantiation object in the object, and determining an assignment type corresponding to the instantiation object; and according to the assignment type corresponding to the instantiation object, analyzing and determining a memory value occupied by the instantiation object. The memory value occupied by the instantiated object can be specifically determined. The use condition of the memorycan be accurately positioned. When the application program performance is perfected, parts needing to be perfected are accurately found out directly according to the memory value occupied by an instantiated object, and the application program performance perfection efficiency is improved.
Owner:深圳市腾讯网域计算机网络有限公司
Memory overflow management method and device, electronic equipment and storage medium
PendingCN111984401AAccurate detectionShorten the timeResource allocationNon-redundant fault processingVirtual memoryData pack
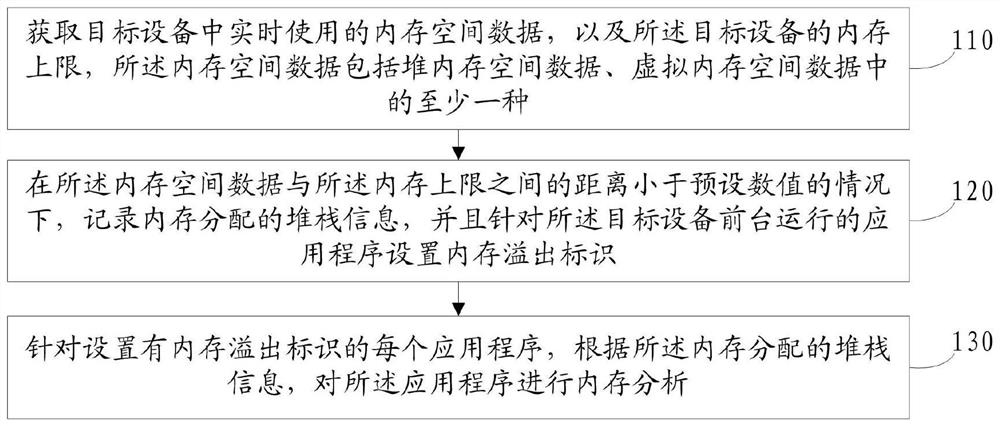
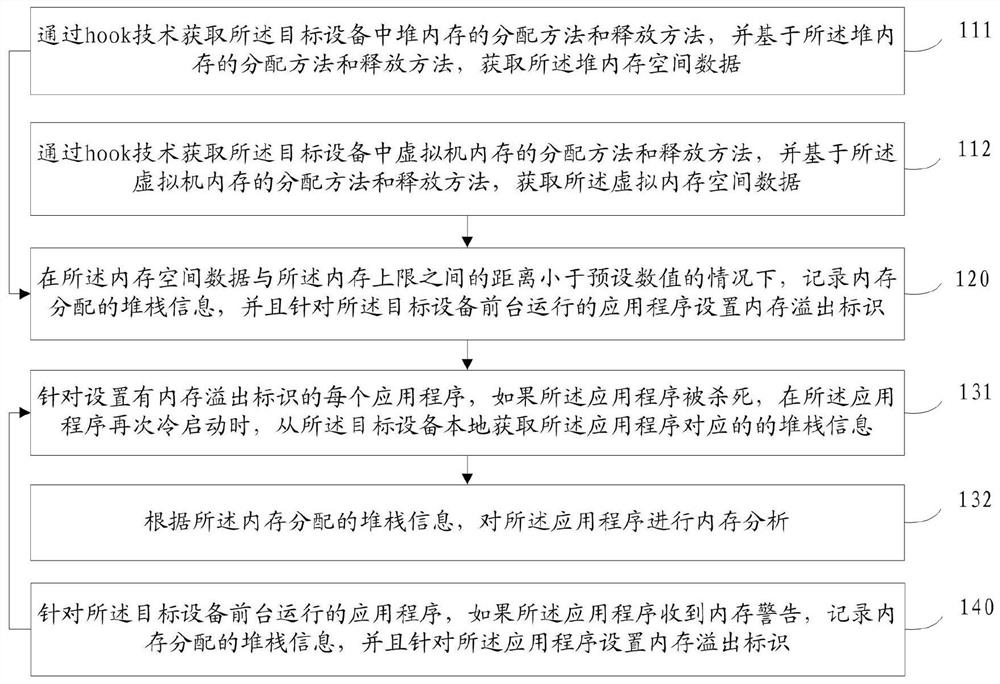
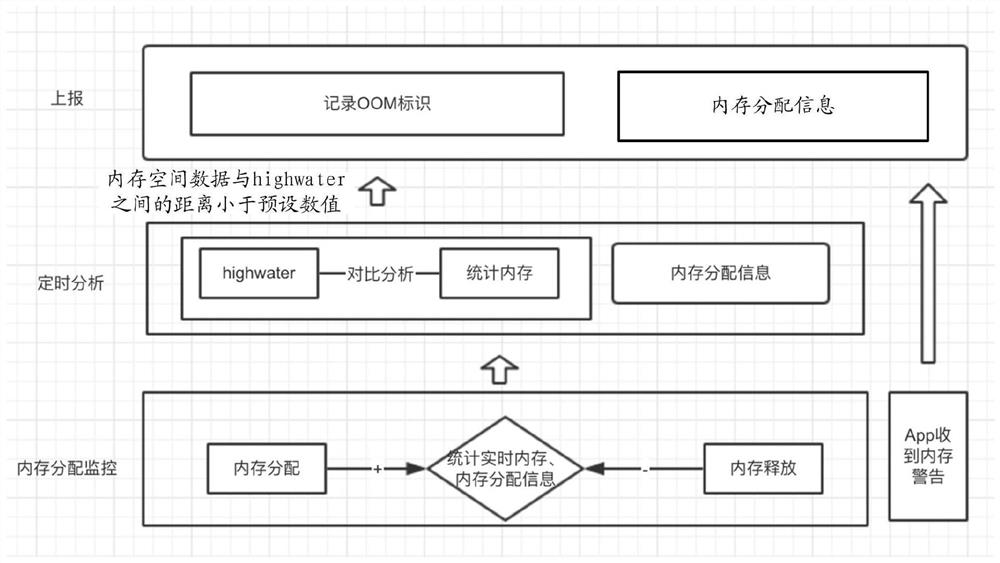
The invention provides a memory overflow management method and device, electronic equipment and a storage medium. The method comprises the steps of acquiring memory space data used in target equipmentin real time and a memory upper limit of the target equipment, wherein the memory space data comprise at least one of heap memory space data and virtual memory space data; under the condition that the distance between the memory space data and the memory upper limit is smaller than a preset numerical value, recording stack information of memory allocation, and setting a memory overflow identifierfor an application program running in the foreground of the target equipment; and for each application program provided with the memory overflow identifier, performing memory analysis on the application program according to the stack information allocated by the memory. Therefore, the memory does not need to be analyzed manually in the development stage, the problem positioning time in demand development is saved, meanwhile, the development time is saved, and the development efficiency is improved. And the problem that the system kills the App due to the OOM can be accurately detected.
Owner:WUBA
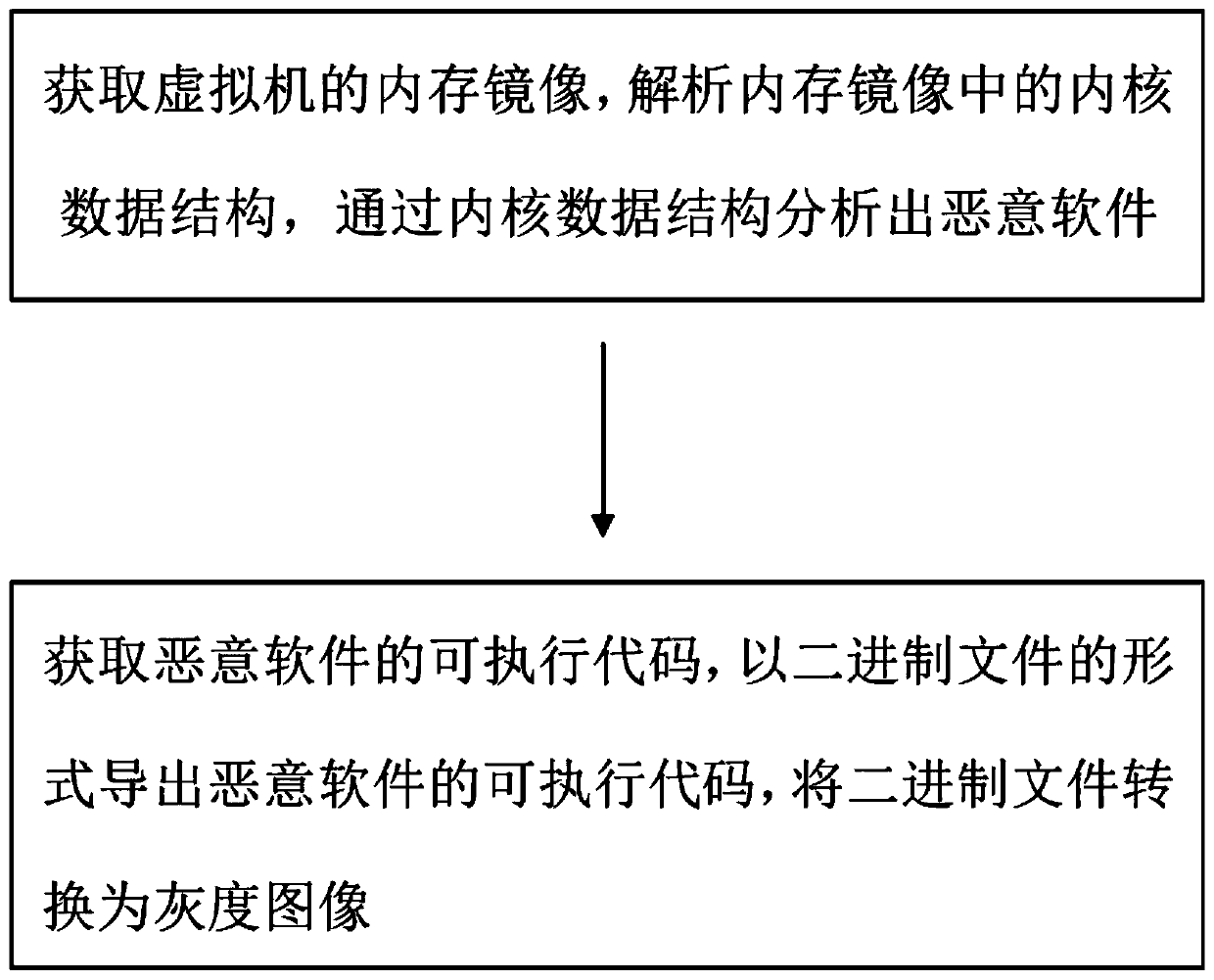
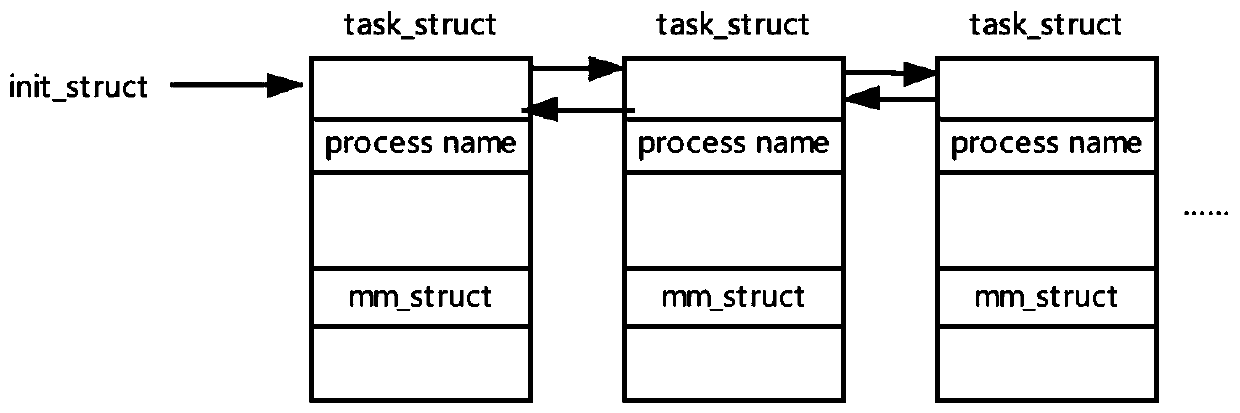
Malicious software detection method and system based on memory analysis
PendingCN110837641AReduce performance loadImprove training accuracyPlatform integrity maintainanceMemory profilingOperational system
The invention belongs to the technical field of computer security, and particularly relates to a malicious software detection method based on memory analysis. The method comprises the steps of obtaining a memory mirror image of a virtual machine, analyzing a kernel data structure in the memory mirror image, analyzing malicious software through the kernel data structure, obtaining an executable code of the malicious software, exporting the executable code of the malicious software in a binary file mode, and converting the binary file into a gray level image. The malicious software detection security is high, the method and system are suitable for detecting various types of malicious software and operating in different operating system versions, and the detection universality and portabilityare greatly improved. In addition, the invention further provides a malicious software detection system based on memory analysis.
Owner:INST OF ELECTRONICS & INFORMATION ENG OF UESTC IN GUANGDONG +1
Just in time memory analysis for malware detection
ActiveUS10902122B2Inhibitory contentPreventing executionPlatform integrity maintainancePacket communicationMemory profiling
Owner:SONICWALL
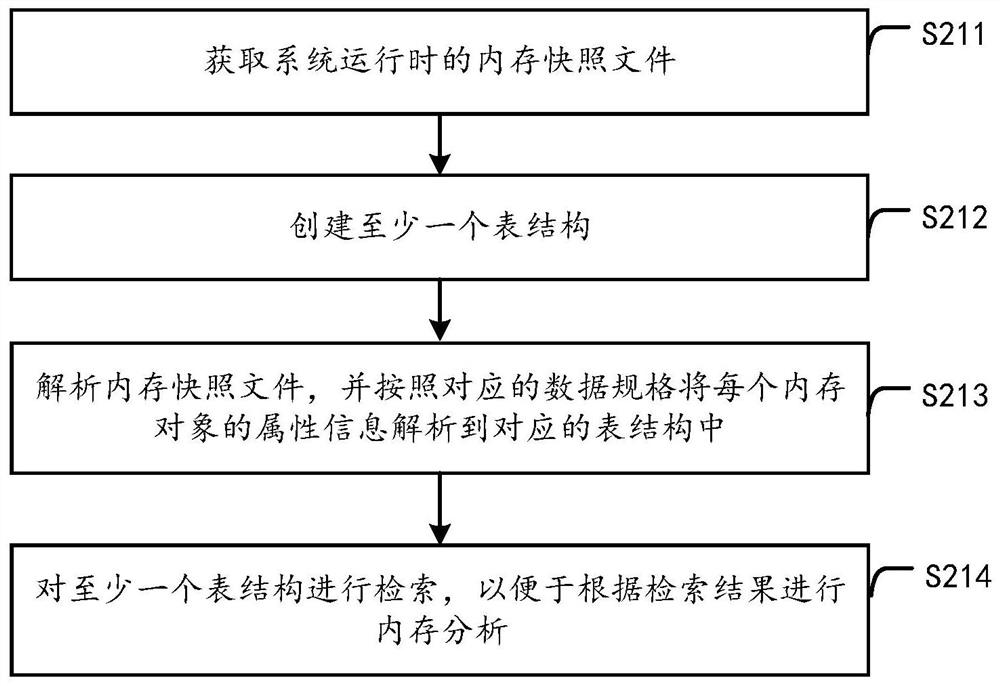
Memory analysis method, device and system
PendingCN113297057AEasy to analyze and locateConvenient location analysisSoftware testing/debuggingFile system administrationComputer hardwareProgramming language
The invention discloses a memory analysis method, device and system. The method comprises the steps of obtaining a memory snapshot file during system running, wherein the memory snapshot file comprises at least one type of memory objects, and each type of memory objects comprises attribute information organized according to a preset data specification; creating at least one table structure, wherein each table structure corresponds to one type of memory object; analyzing the memory snapshot file, and analyzing attribute information of each memory object into a corresponding table structure according to a corresponding data specification; and retrieving the at least one table structure so as to perform memory analysis according to a retrieval result. According to the method, the attribute information of the memory object in the memory snapshot file is collected into a plurality of table structures, so that the memory problem is analyzed and positioned by retrieving data in the table structures.
Owner:ALIBABA GRP HLDG LTD
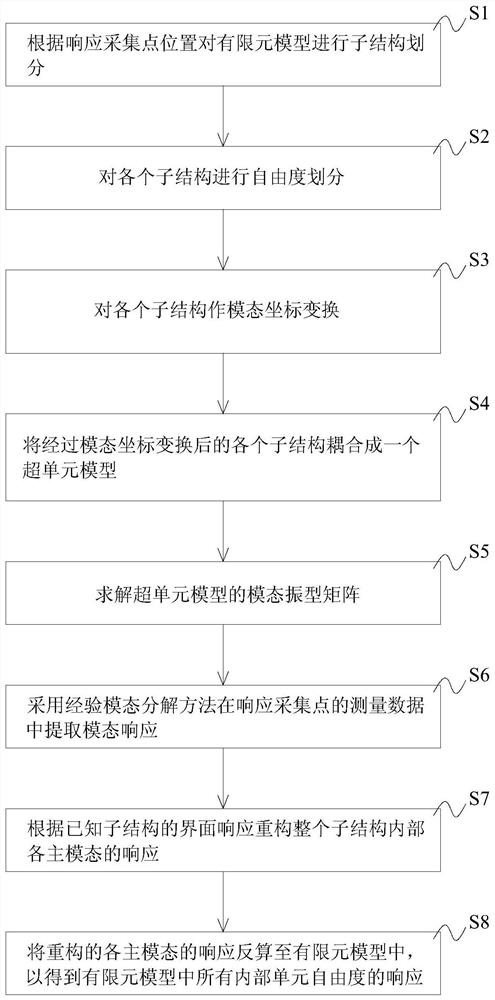
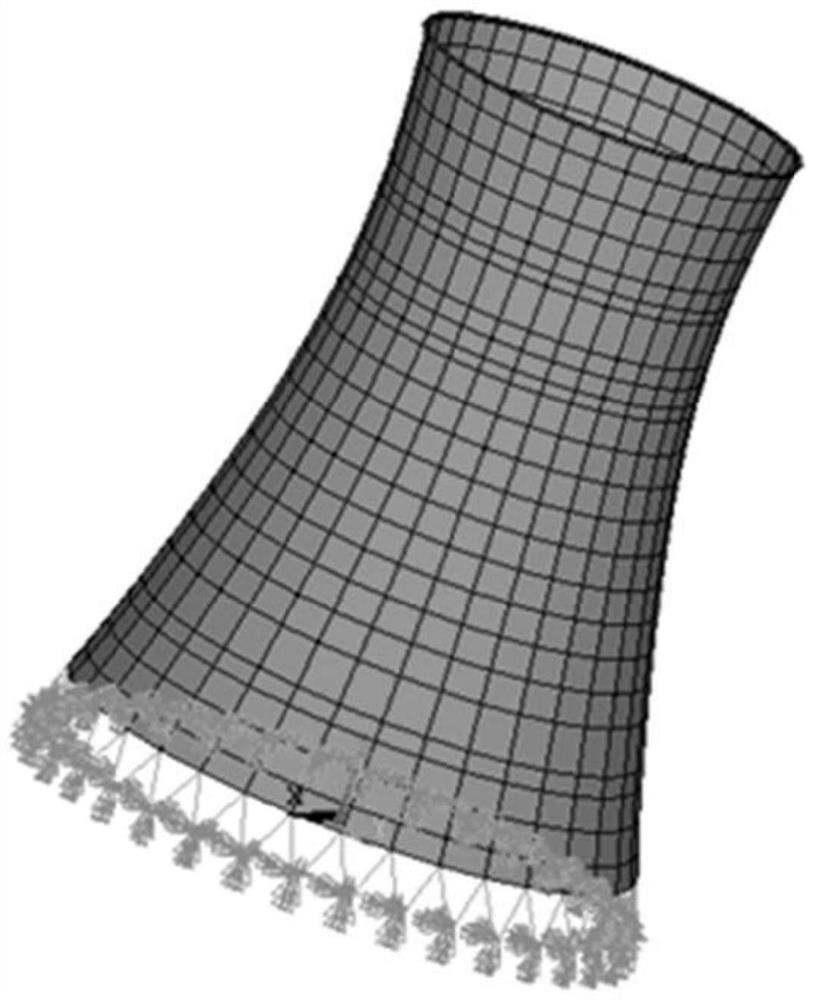
Substructure response reconstruction method and system, and storage medium
ActiveCN112580239ASave memoryGuaranteed accuracyGeometric CADDesign optimisation/simulationTime domainMemory profiling
The invention discloses a substructure response reconstruction method and system, and a storage medium. The method employs model condensation to generate a super-unit model based on a finite element model, does not need to consider the boundary conditions of all substructures, can better adapt to the dynamic response reconstruction of a large-scale complex engineering structure, and expands a current time domain reconstruction method based on EMD decomposition, the modal synthesis is used in the response reconstruction method for the first time, the response of each main modal in the whole substructure is reconstructed based on the interface response of the known substructure, the response reconstruction only needs to be carried out under the condensed substructure, and then the main modeof a super-unit model is expanded to the response of the degrees of freedom of all internal units in the finite element model through coordinate back calculation, so that the accuracy is ensured, thereconstruction efficiency is greatly improved, the computer memory is saved, and the analysis speed is high.
Owner:CENT SOUTH UNIV
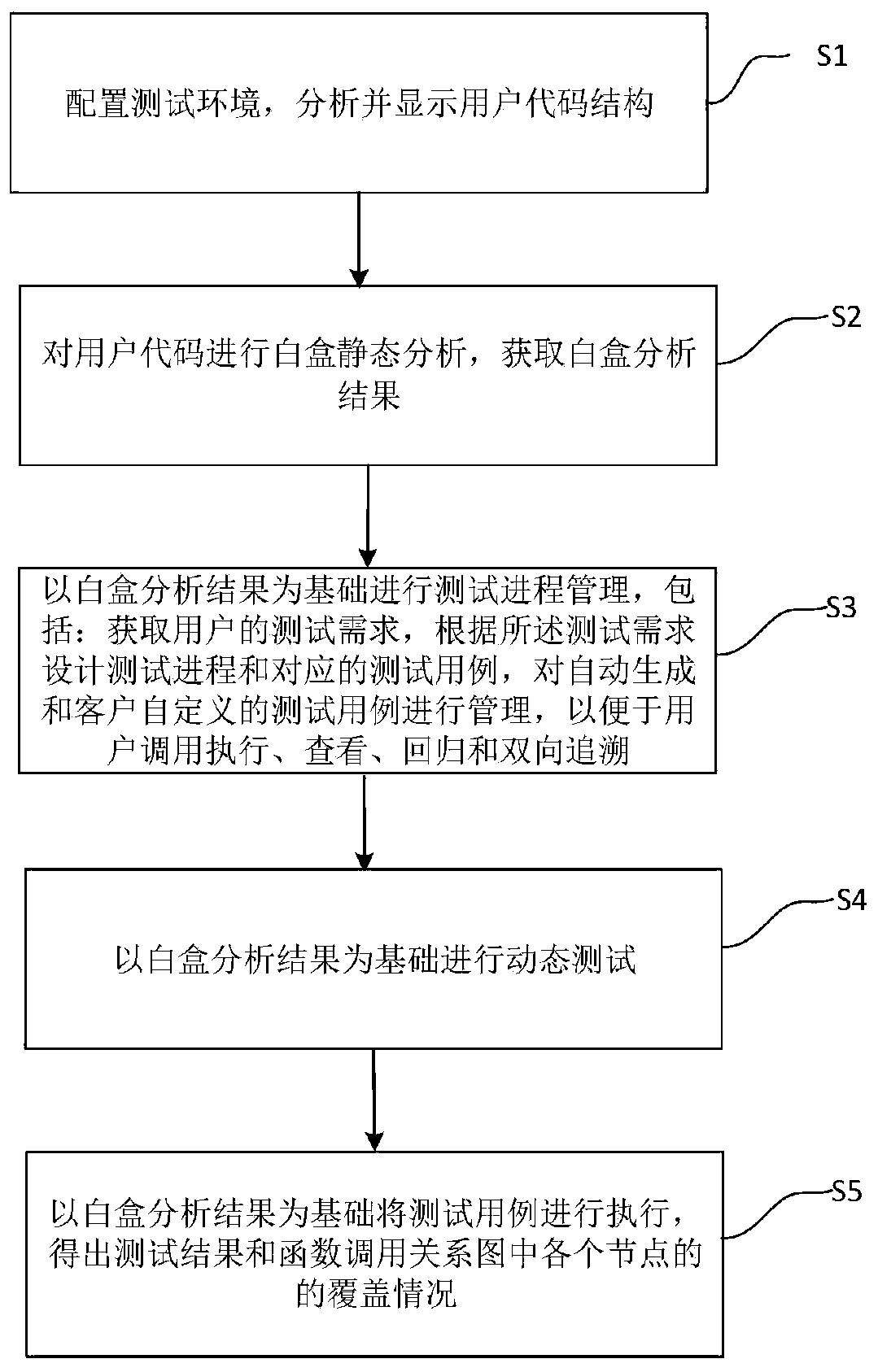
Automatic test case generation and test process management method based on white box analysis
The invention provides an automatic test case generation and test process management method based on white box analysis, which comprises the following steps: configuring a test environment, and analyzing and displaying a user code structure; performing white box static analysis on the user code to obtain a white box analysis result; carrying out test process management on the basis of a white boxanalysis result, including the steps of obtaining a test demand of a user, designing a test process and a corresponding test case according to the test demand, and managing the test case which is automatically generated and customized by the user; carrying out dynamic tests on the basis of a white box analysis result, including adequacy test, coverage rate test, function test, time performance test, variable dynamic analysis and dynamic memory analysis, and then generating a dynamic test report; and executing the test cases on the basis of the white box analysis result to obtain the test result and the coverage condition of each node in the function call relation graph. The invention can reduce the test workload of the user and improve the test efficiency.
Owner:天津汇缘诚信科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com