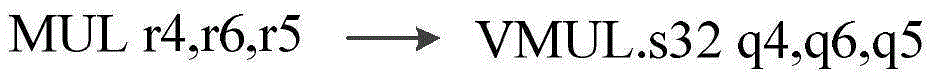Patents
Literature
81 results about "Memory analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
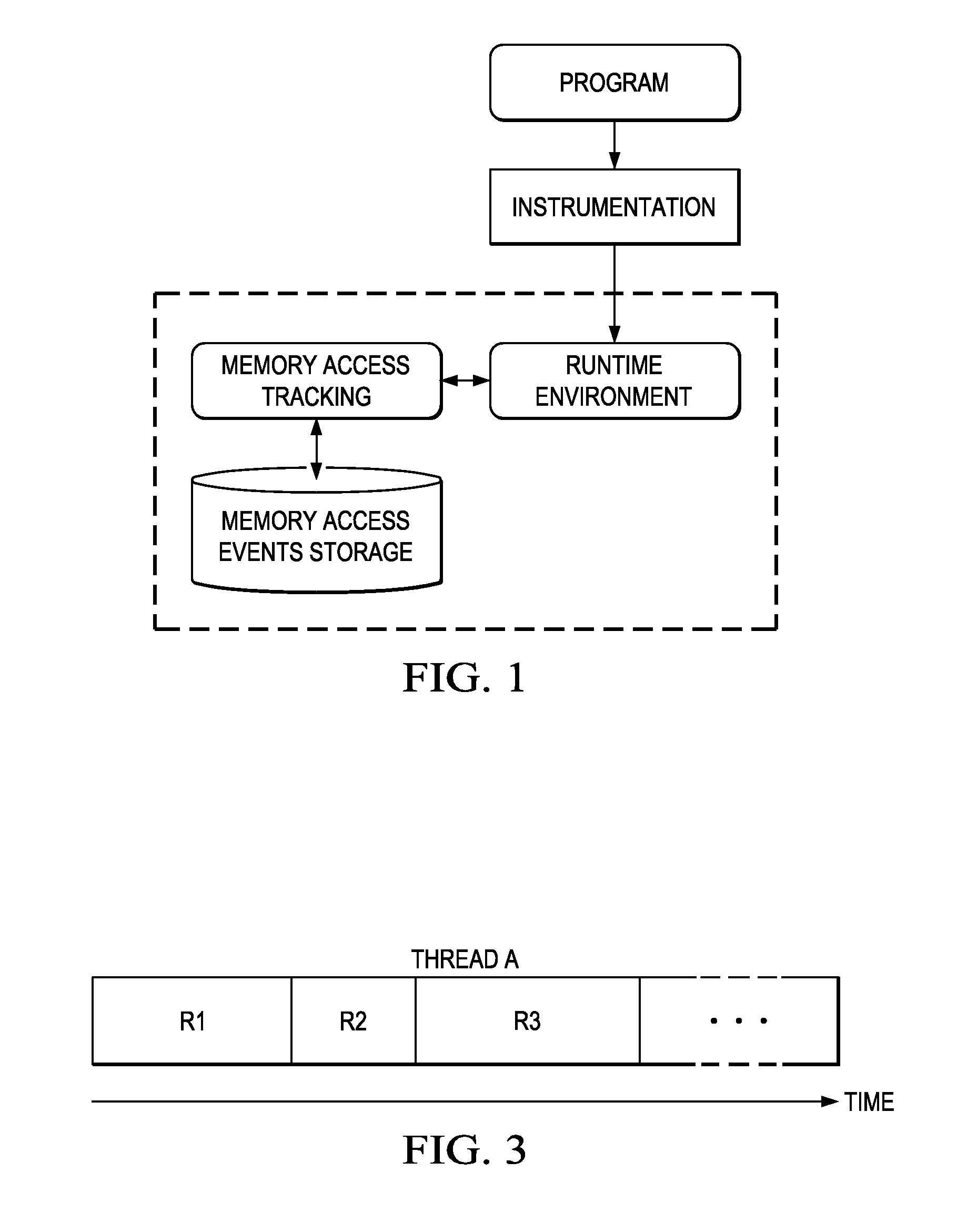
Physical Memory Forensics System and Method
ActiveUS20140032875A1Accurate reconstructionMemory adressing/allocation/relocationDigital data protectionMemory forensicsData pack
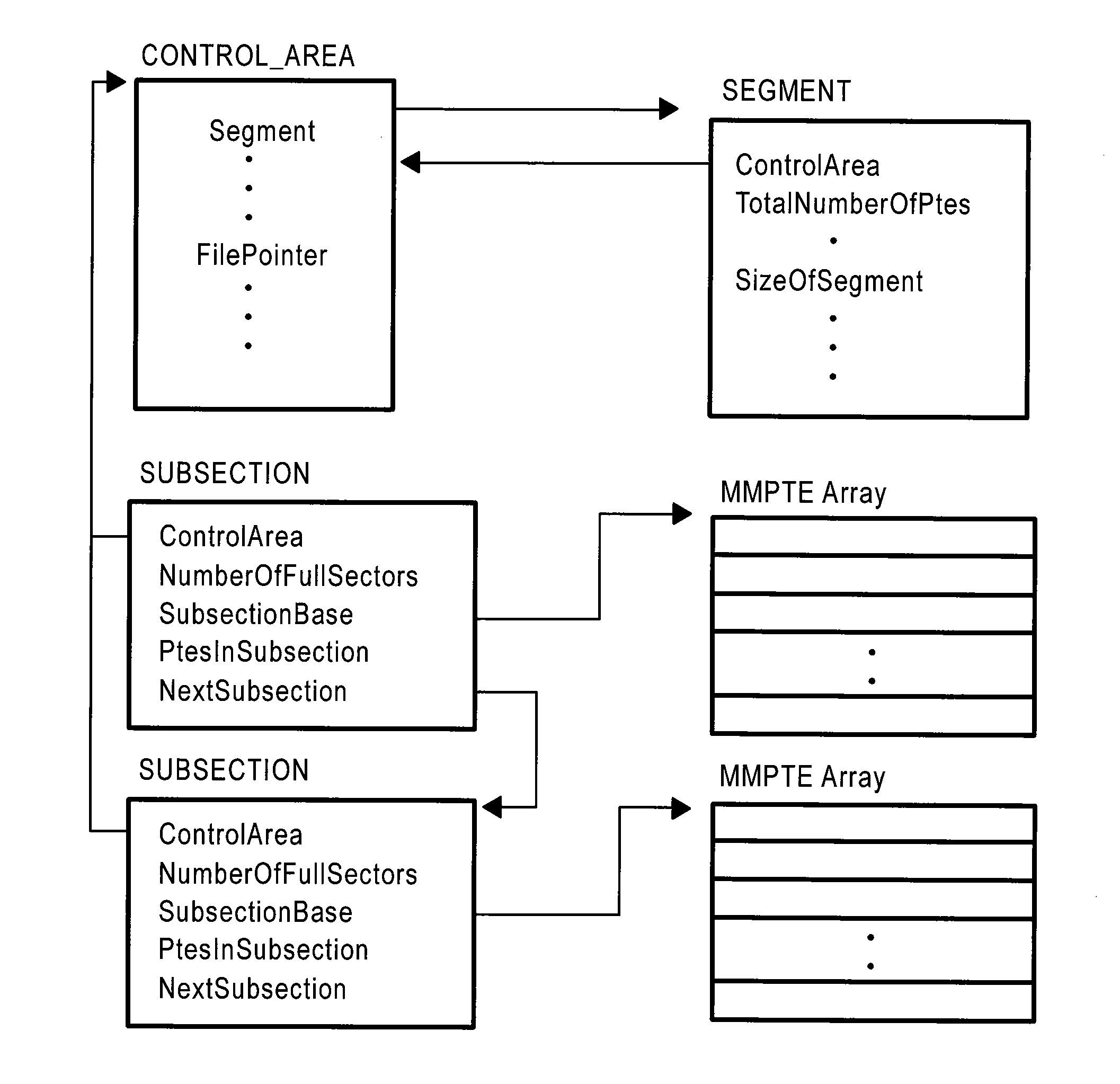
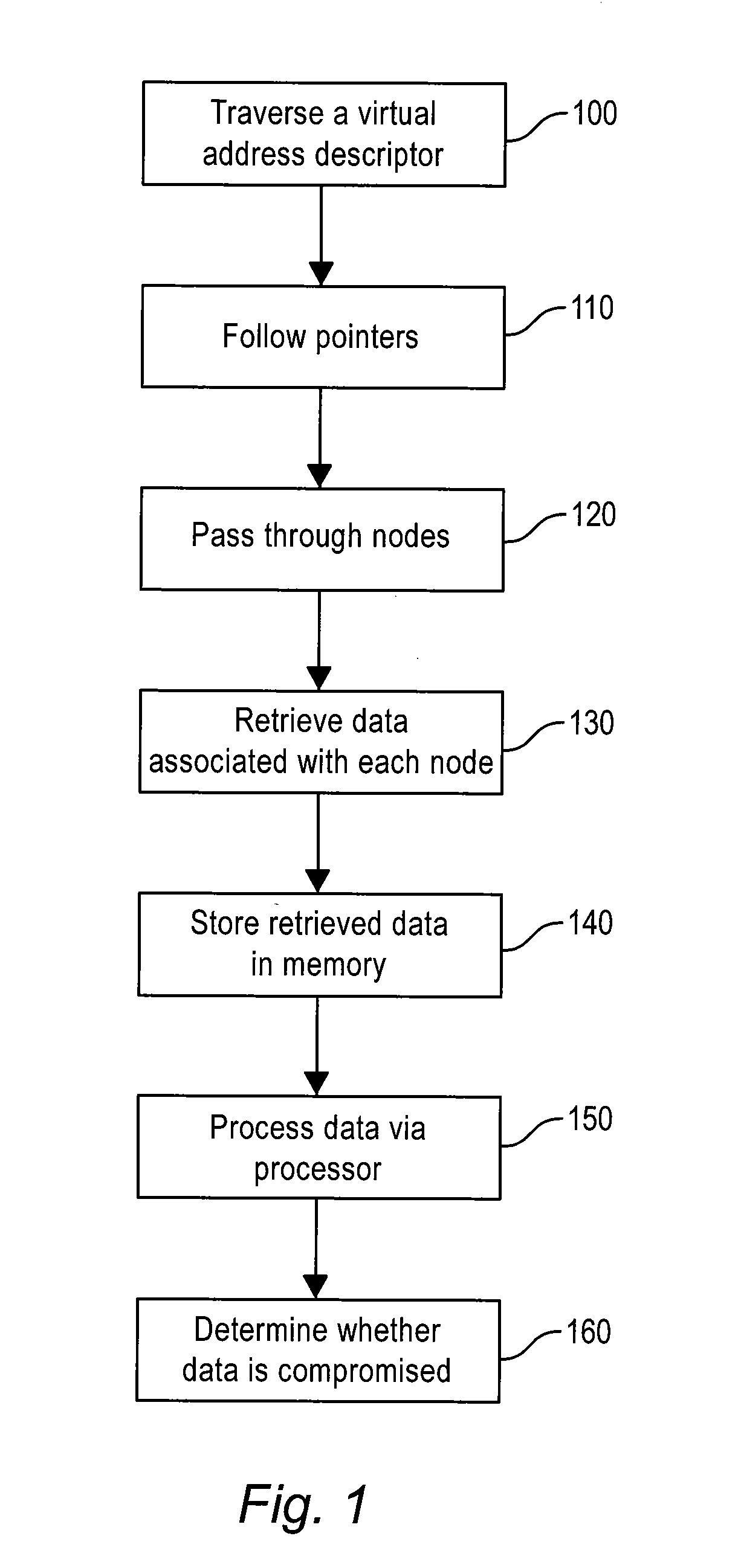
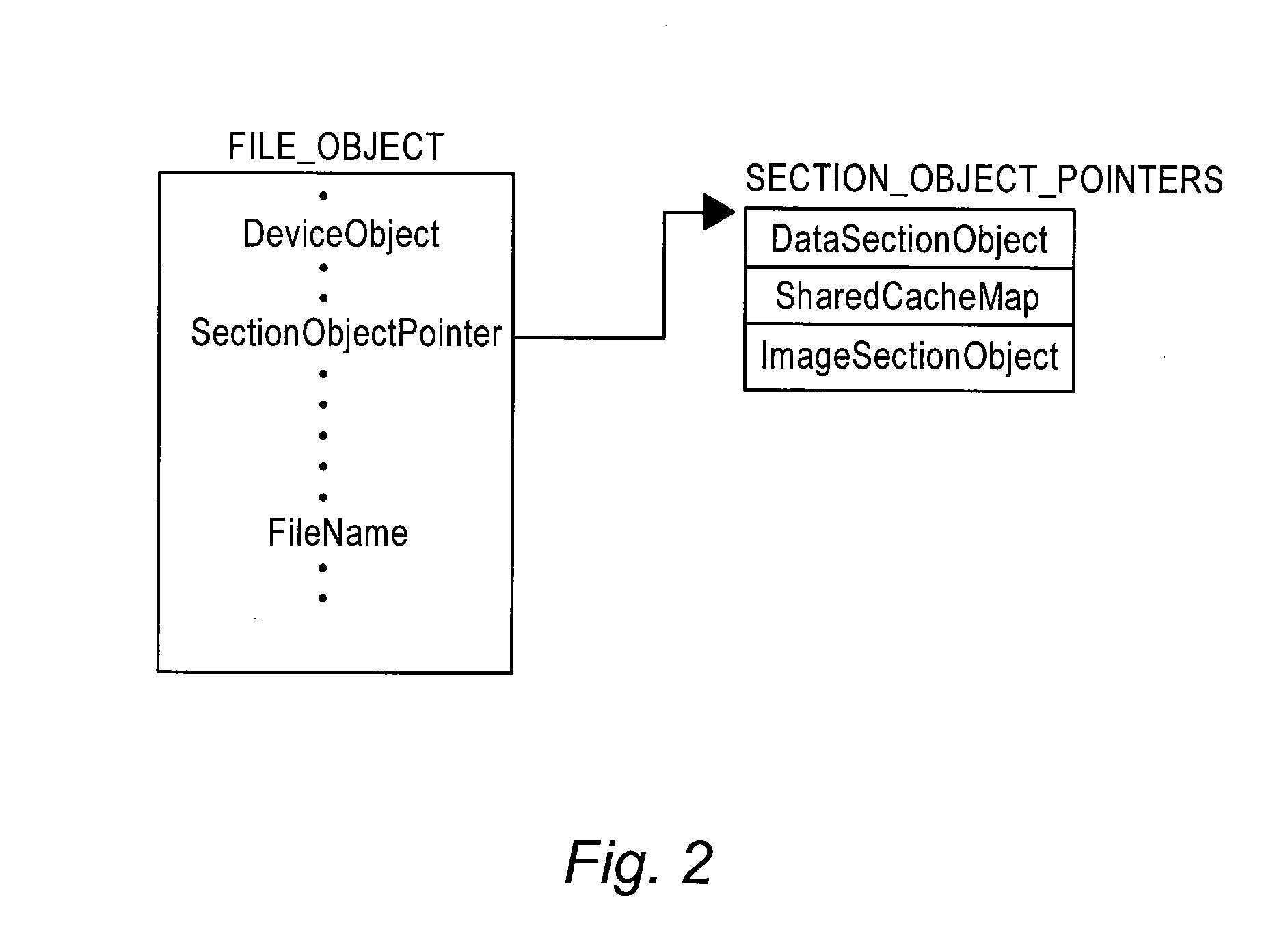
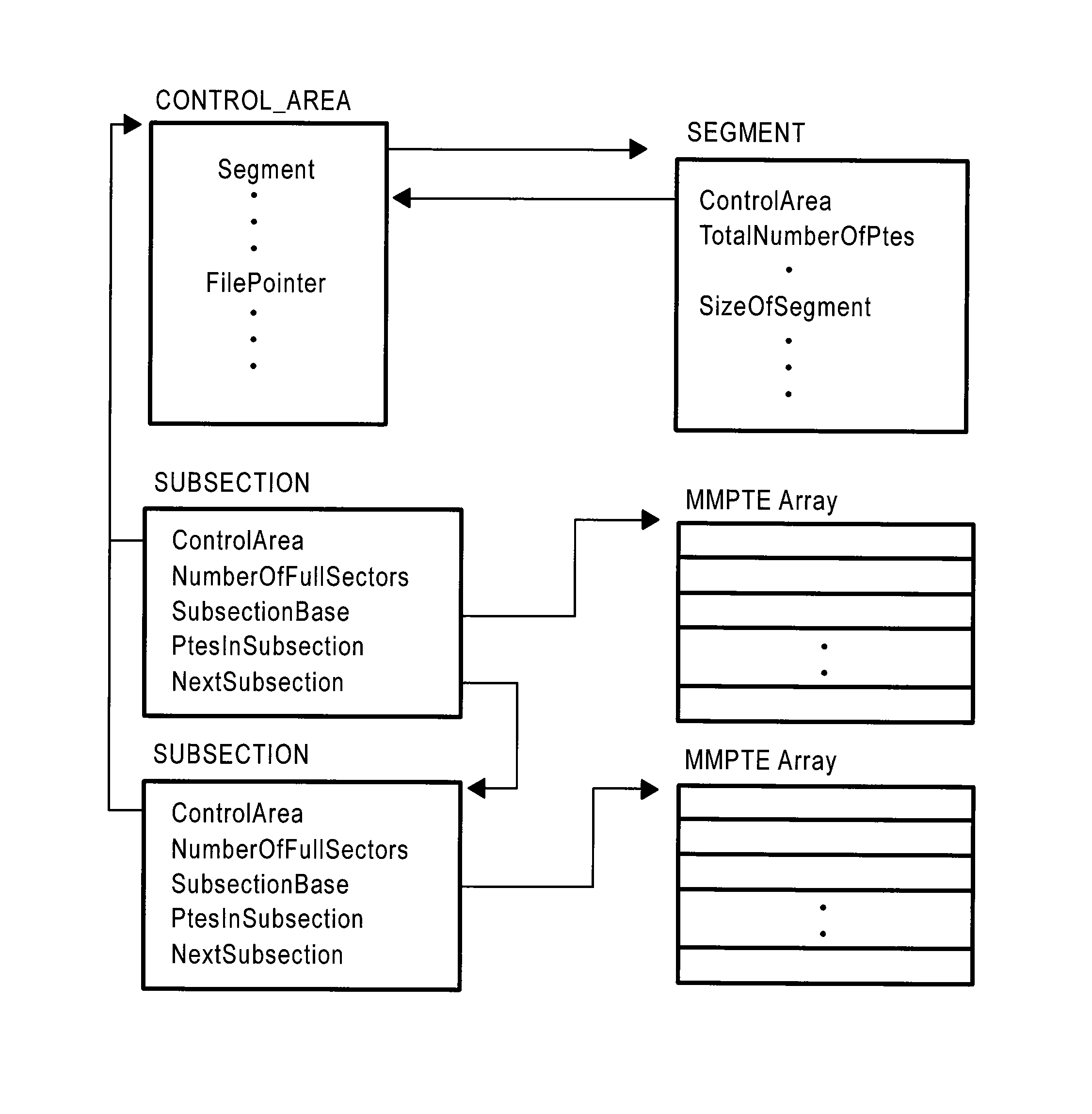
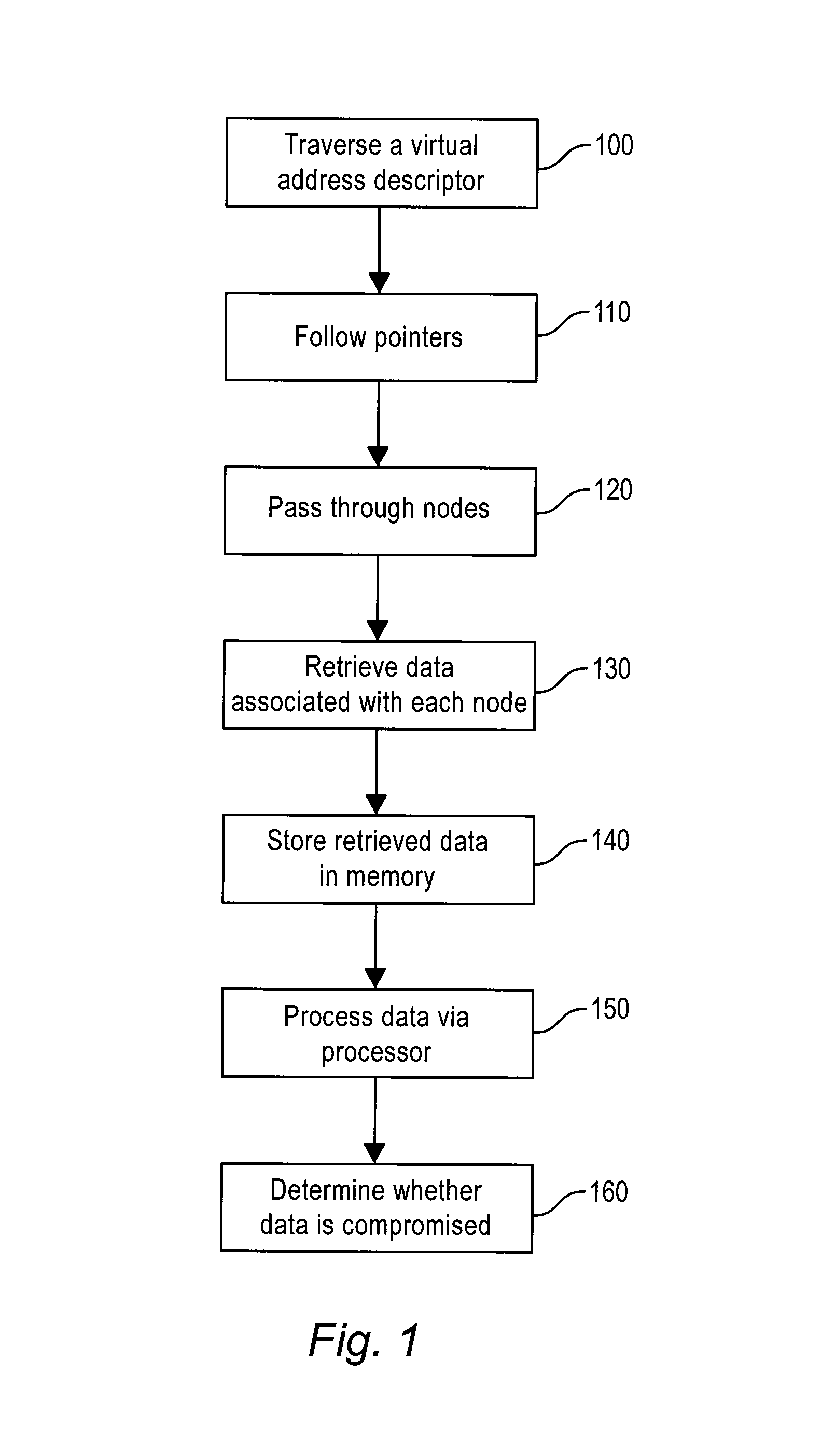
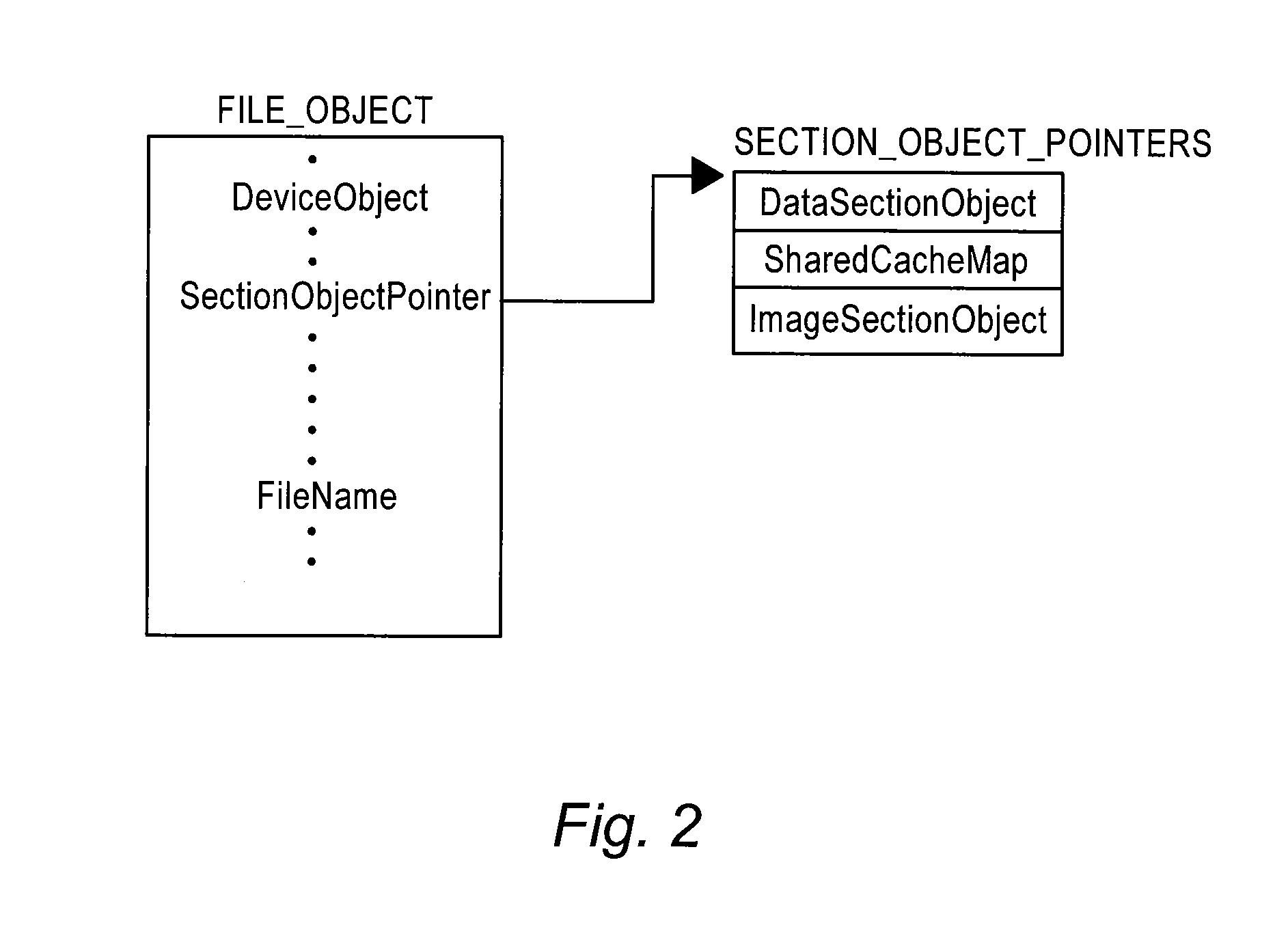
The method of the present inventive concept is configured to utilize Operating System data structures related to memory-mapped binaries to reconstruct processes. These structures provide a system configured to facilitate the acquisition of data that traditional memory analysis tools fail to identify, including by providing a system configured to traverse a virtual address descriptor, determine a pointer to a control area, traverse a PPTE array, copy binary data identified in the PPTE array, generate markers to determine whether the binary data is compromised, and utilize the binary data to reconstruct a process.
Owner:FIREEYE SECURITY HLDG US LLC
Physical memory forensics system and method
ActiveUS9268936B2Memory adressing/allocation/relocationDigital data protectionMemory forensicsOperational system
The method of the present inventive concept is configured to utilize Operating System data structures related to memory-mapped binaries to reconstruct processes. These structures provide a system configured to facilitate the acquisition of data that traditional memory analysis tools fail to identify, including by providing a system configured to traverse a virtual address descriptor, determine a pointer to a control area, traverse a PPTE array, copy binary data identified in the PPTE array, generate markers to determine whether the binary data is compromised, and utilize the binary data to reconstruct a process.
Owner:FIREEYE SECURITY HLDG US LLC
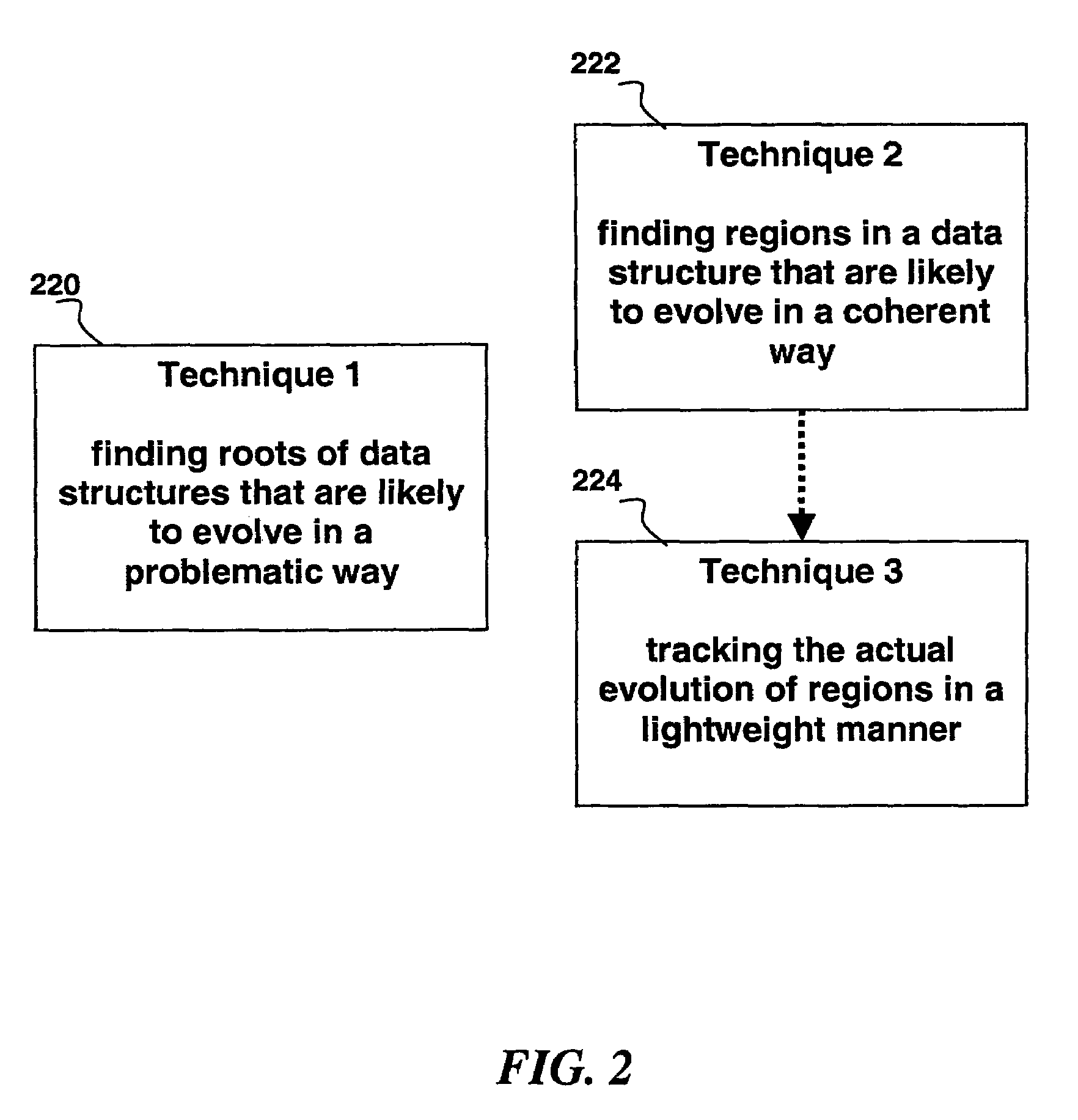
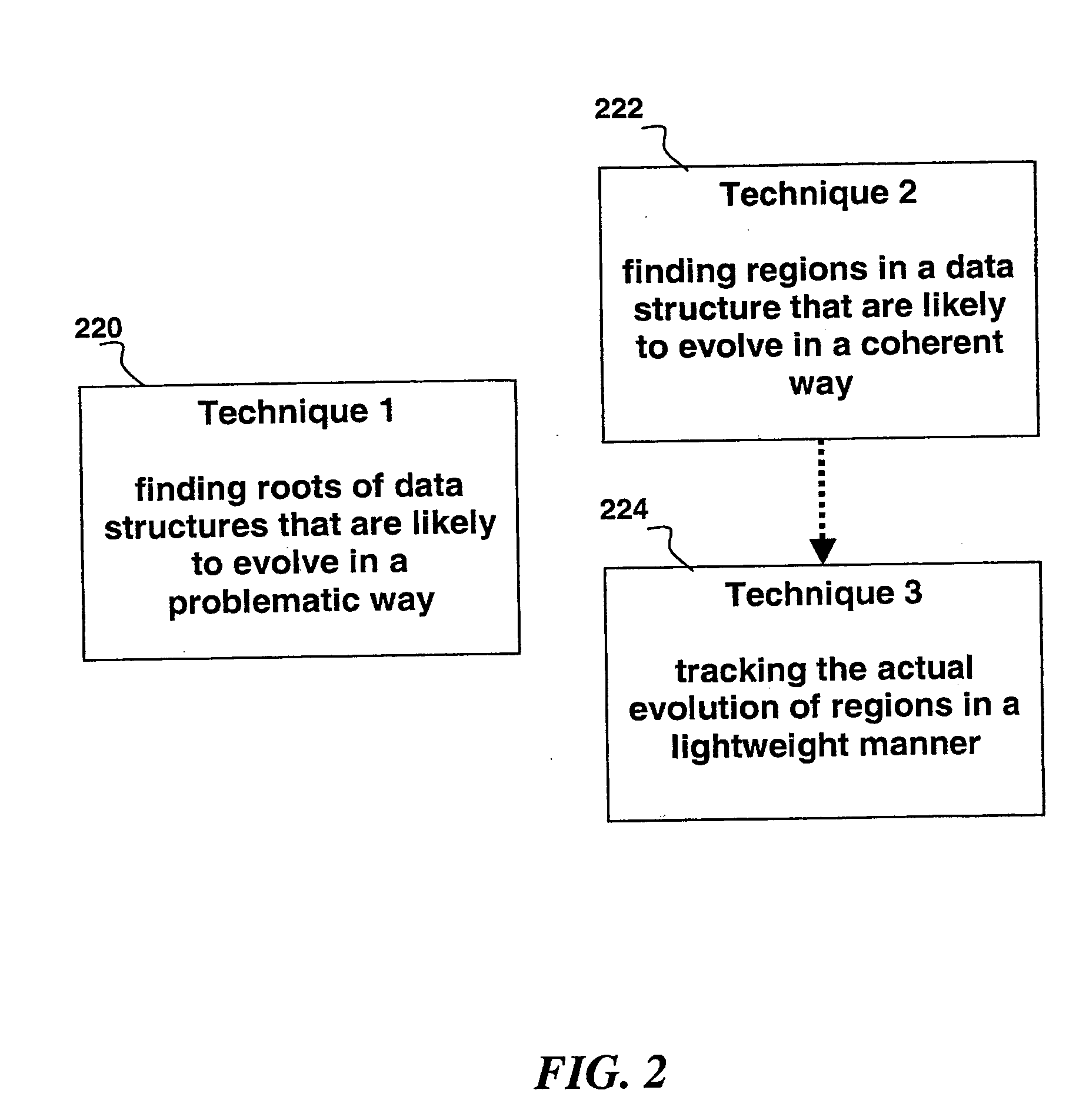
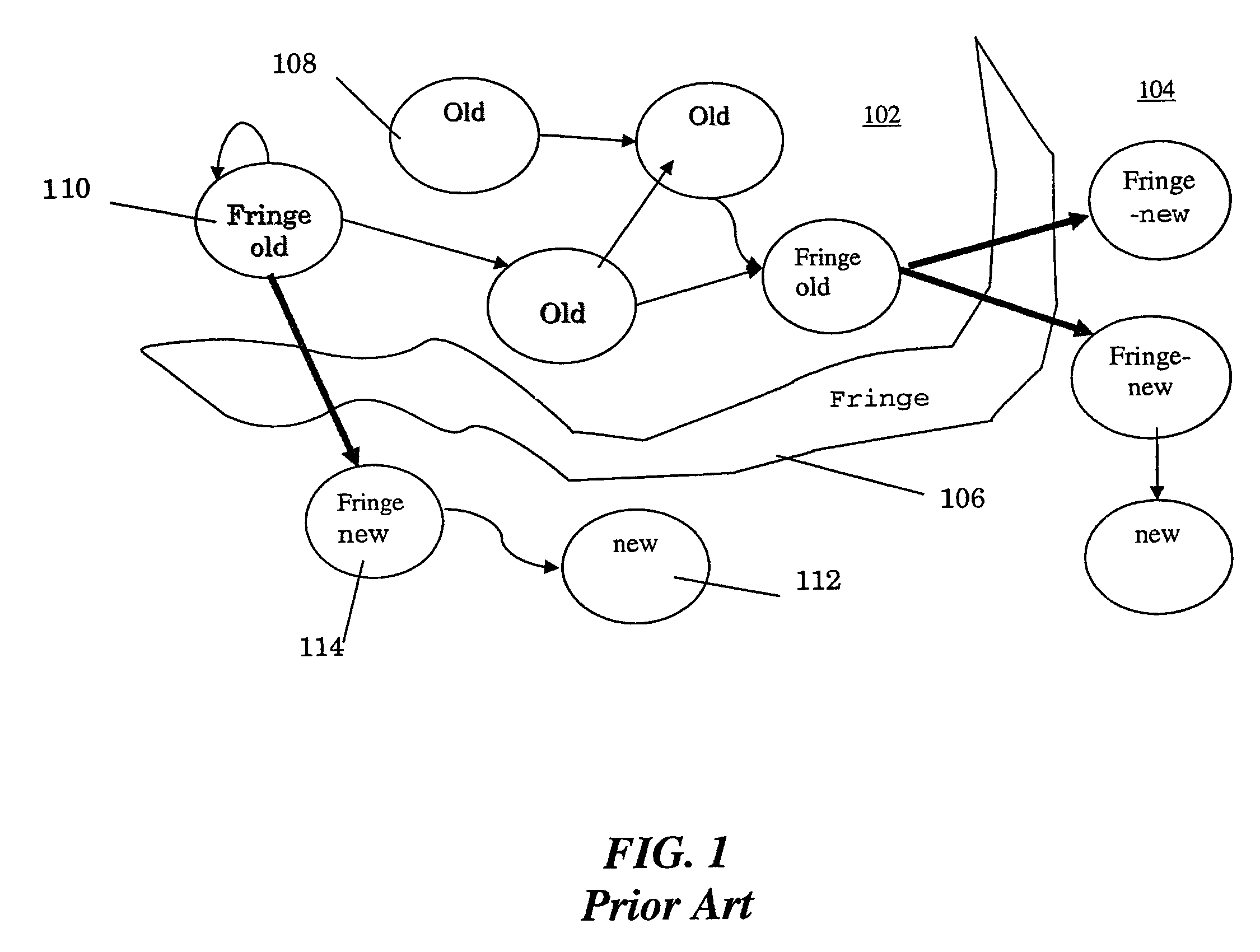
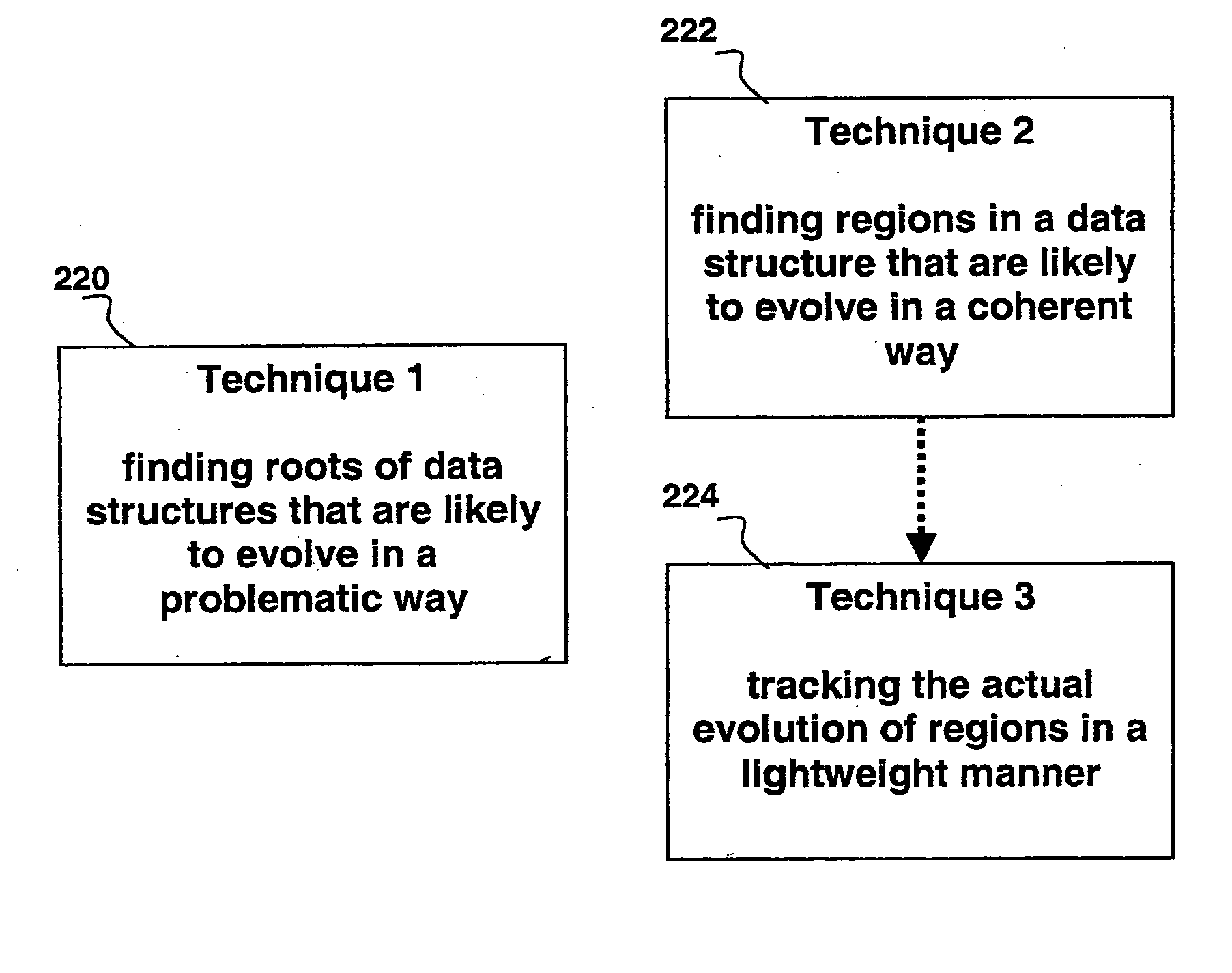
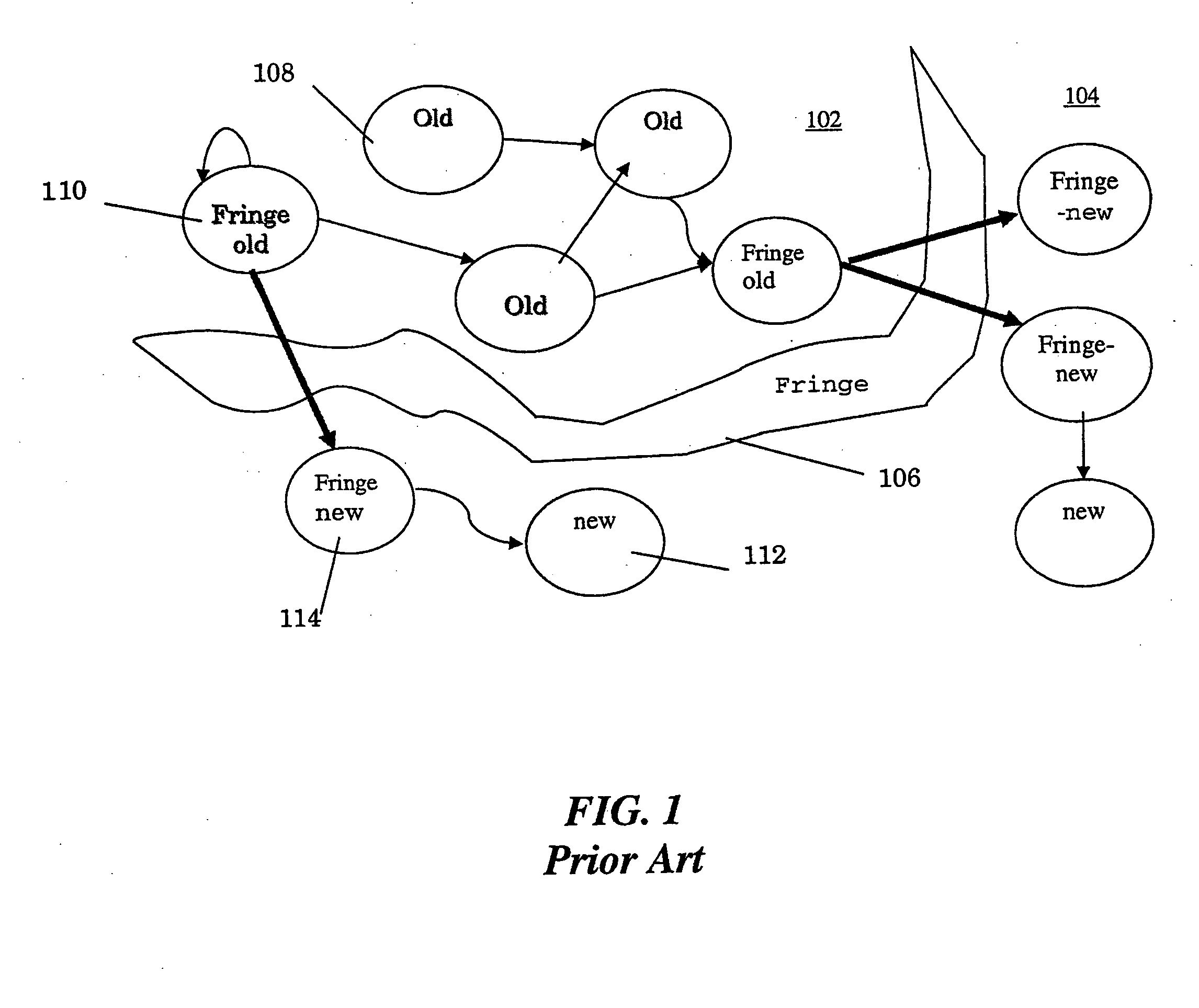
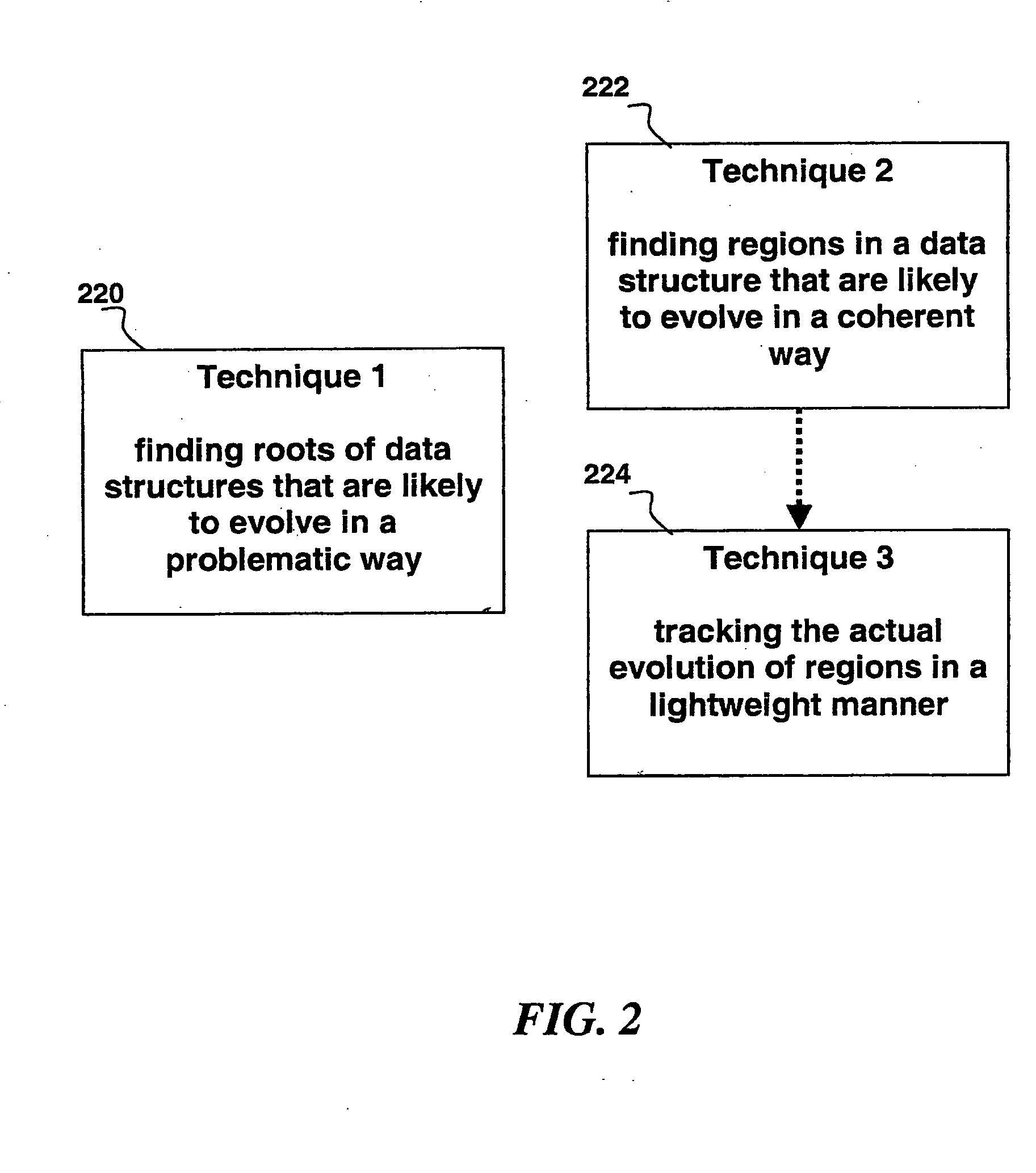
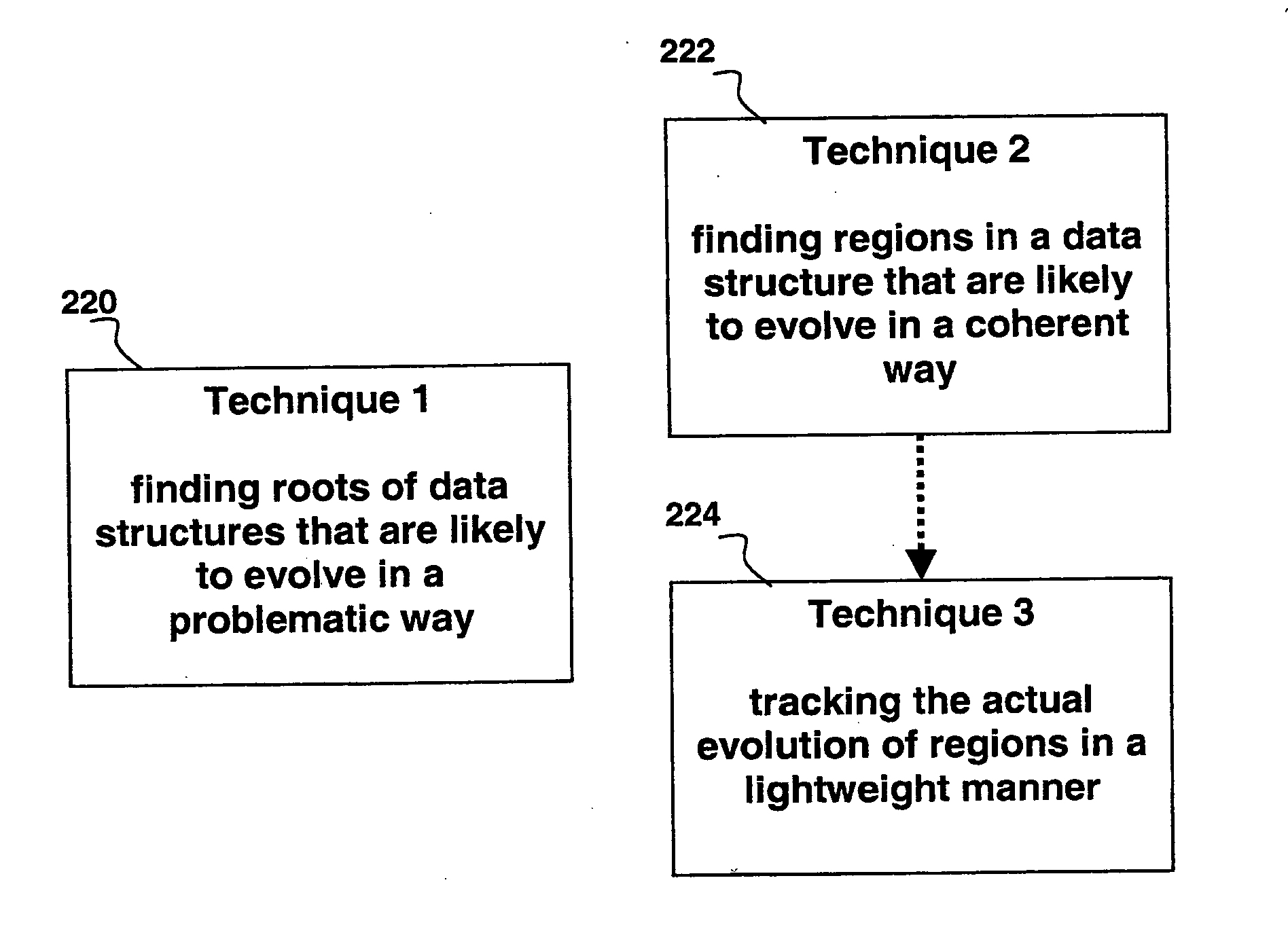
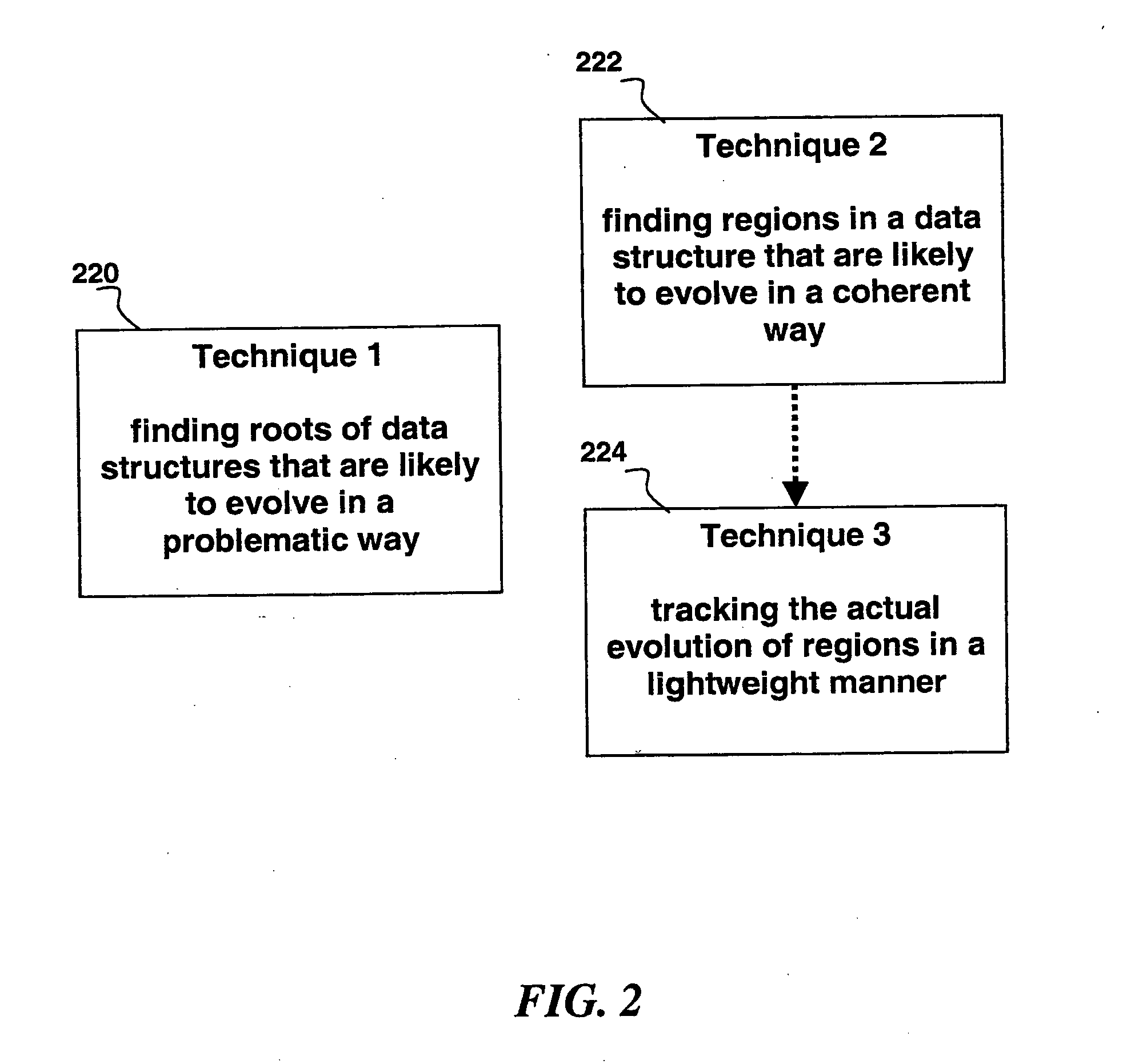
Automated scalable and adaptive system for memory analysis via online region evolution tracking
InactiveUS7447694B2Digital data processing detailsNon-redundant fault processingData miningSelf adaptive
A method for determining how a region of a data structure in an application evolves comprises the steps of: periodically traversing selected subgraphs of the region in the running application; locating structural changes in the subgraphs; using these structural changes to describe, characterize, and identify changes to the region as a whole; and reporting the region changes to an analysis agent. Determining how a region of a data structure evolves is a continuous and adaptive process. The process is made continuous and adaptive through several methods, including: identifying a set of desired updates; adjusting the period in between traversals based on whether the desired updates have been witnessed; and adjusting the frequency of sampling any one traversal based on whether that traversal has detected desired updates. Additionally, the method comprises updating qualitative and quantitative characterizations of the regions under analysis based on structural changes to the regions as whole.
Owner:IBM CORP
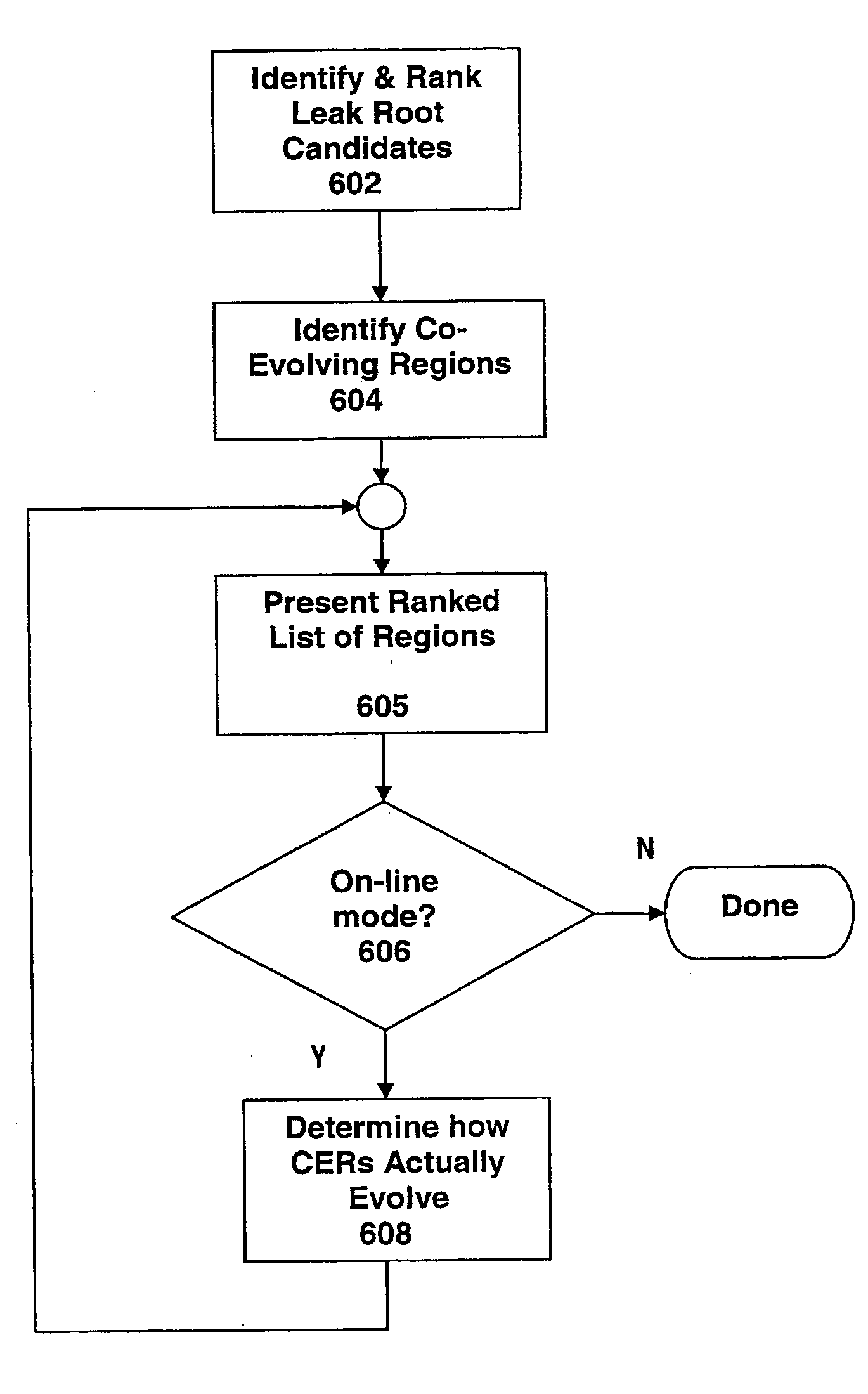
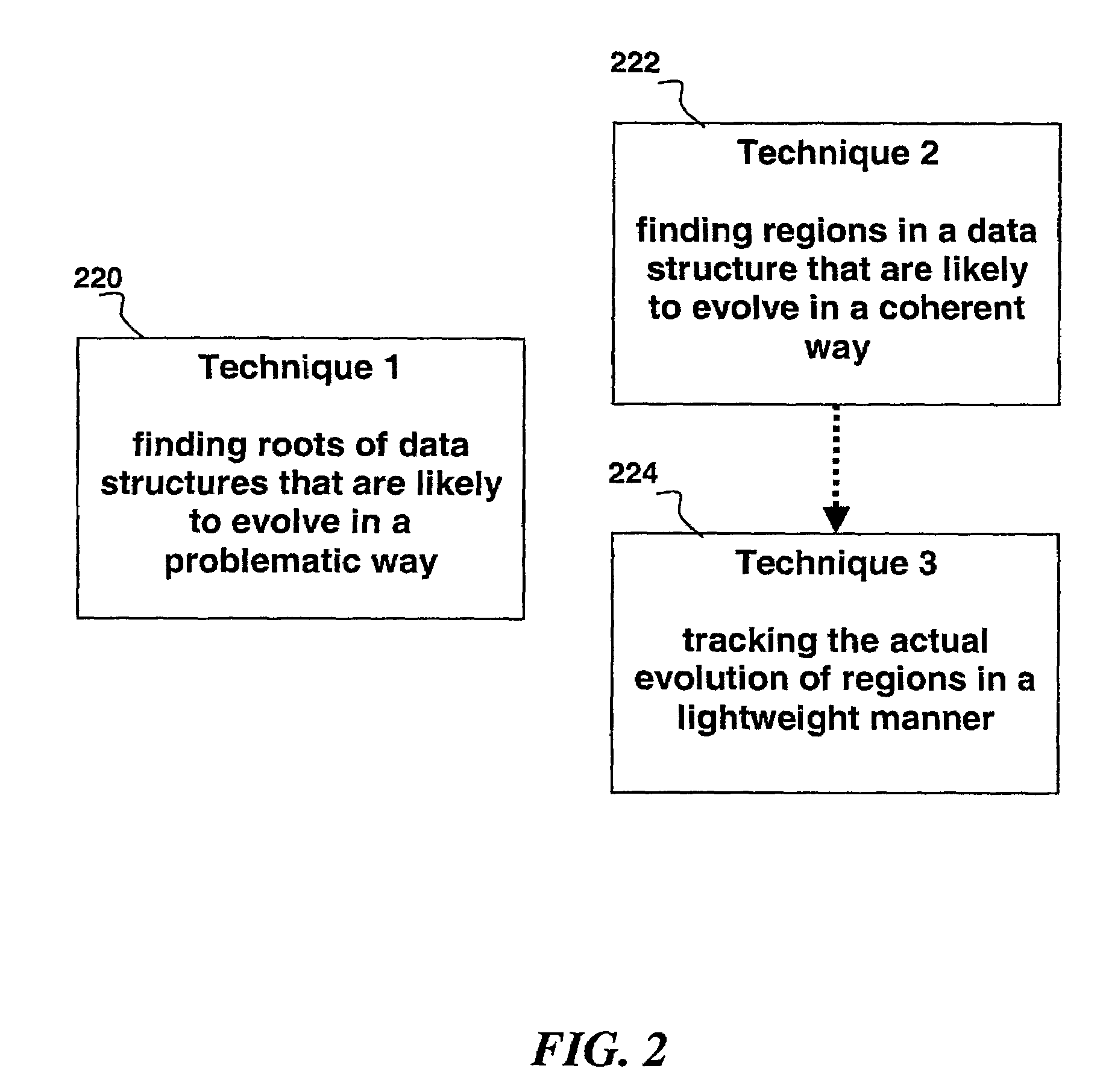
Automated scalable and adaptive system for memory analysis via identification of leak root candidates
InactiveUS20050071460A1Error detection/correctionDigital computer detailsTheoretical computer scienceRanking
A method for identifying a set of objects in a target application program comprises: receiving a plurality of samples of one or more object reference graphs, wherein each object reference graph comprises live objects and their references; deriving a plurality of data structures from the samples; determining a plurality of properties of each of the live objects in relation to data structures over time; combining the plurality of the properties of each live object; generating the object reference graph; generating a rank; and identifying suspicious regions that are likely to have leaks within the data structure. The method also comprises the identification of an initial set of highly-ranked candidate objects that are possible causes of at least one object leak, wherein the higher the ranking the smaller the identified set.
Owner:IBM CORP
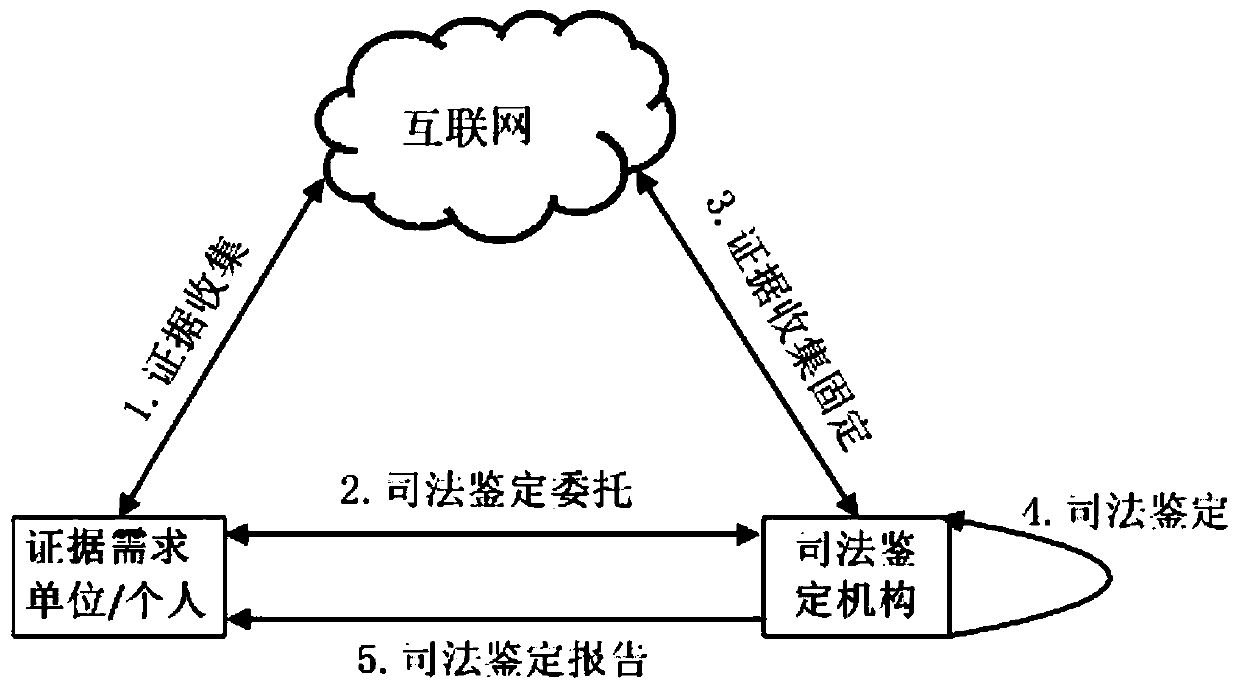
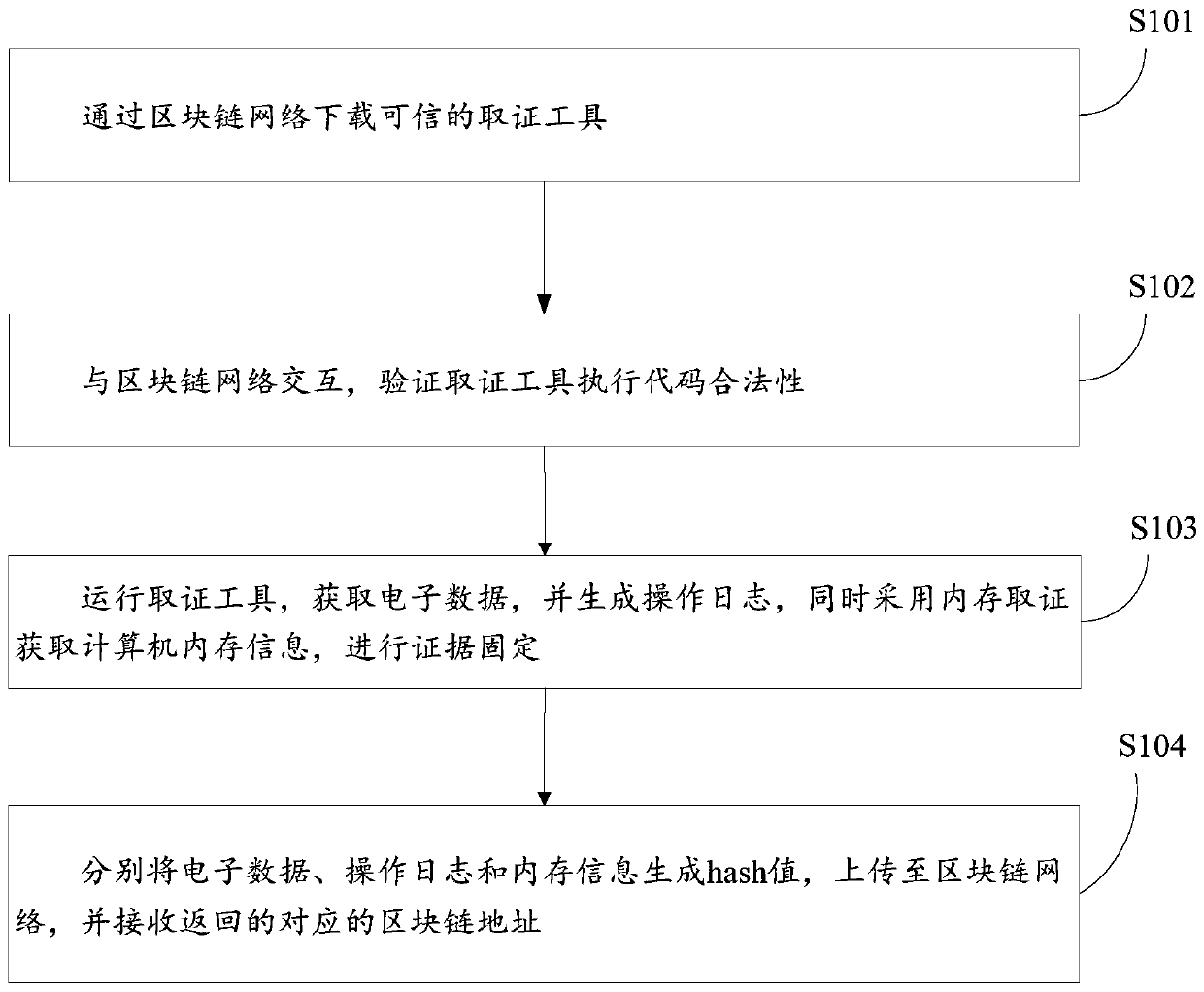
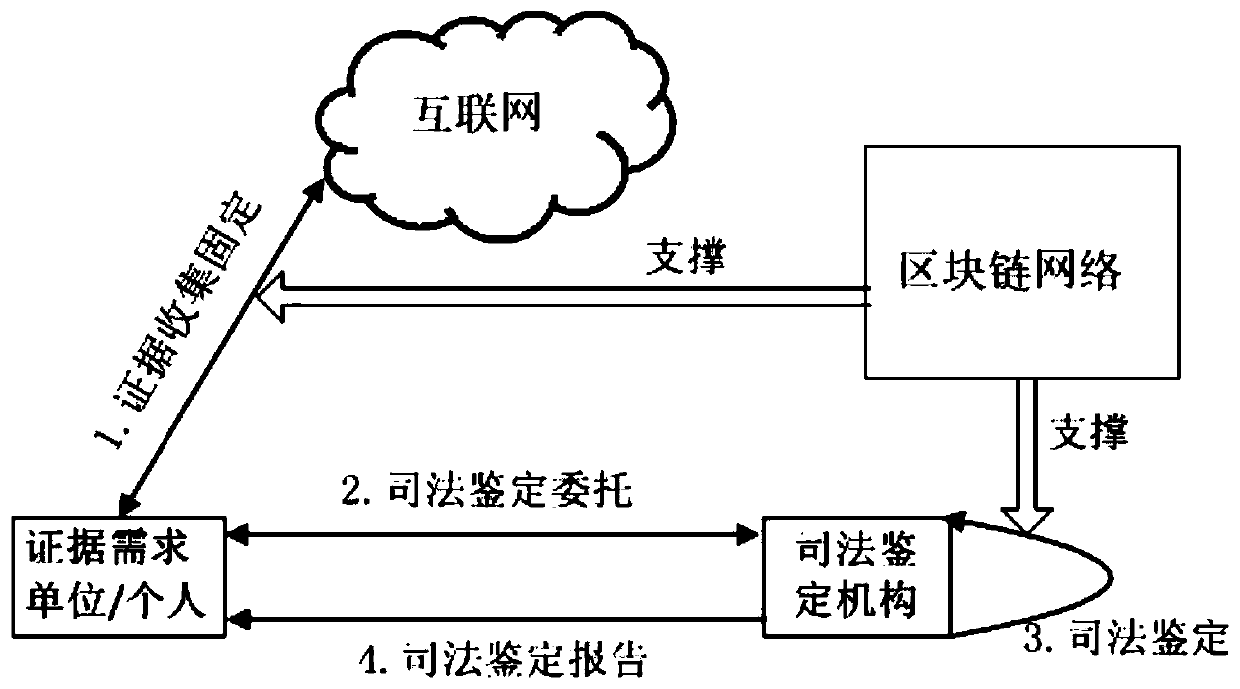
Electronic evidence fixing and network evidence obtaining method and system based on memory evidence obtaining and block chain
ActiveCN110232645AYi CaixinAvoid delayData processing applicationsDigital data protectionMemory profilingMemory forensics
The invention discloses an electronic evidence fixing and network evidence obtaining method and system based on memory evidence obtaining and a block chain. An electronic evidence fixing terminal downloads a credible evidence obtaining tool through the block chain network. The legality of the evidence obtaining tool execution code is verified. The evidence obtaining tool is operated, electronic data are obtained, an operation log is generated, meanwhile, computer memory information is obtained through the memory evidence obtaining technology, and evidence fixing is conducted. A hash value is generated.and uploaded to the block chain network. A returned corresponding block chain address is received. The data is sent to a judicial certification authority terminal. A judicial certification mechanism terminal receives the block chain address sent by the electronic evidence fixing terminal. Information on the block chain is inquired, and legality is verified. The memory information is analyzed by adopting a memory evidence obtaining technology. The system state is extracted when the electronic evidence is obtained, and verifying the conformity. A judgment is verified whether the evidence obtaining tool is hooked or injected during operation or not through memory analysis, and the reliability of the operation environment of the evidence obtaining tool is verified. Judicial authentication reports are generated.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
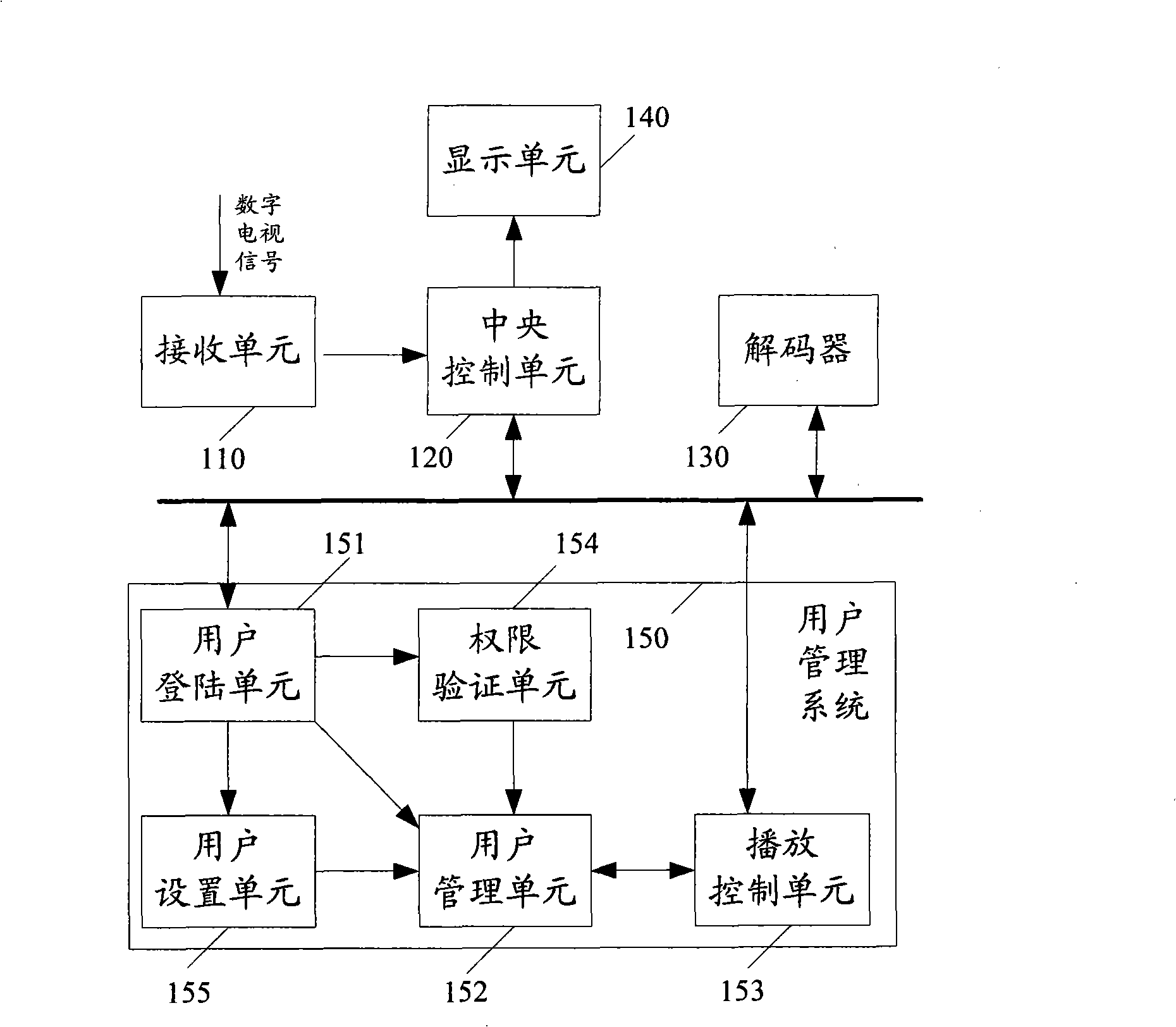
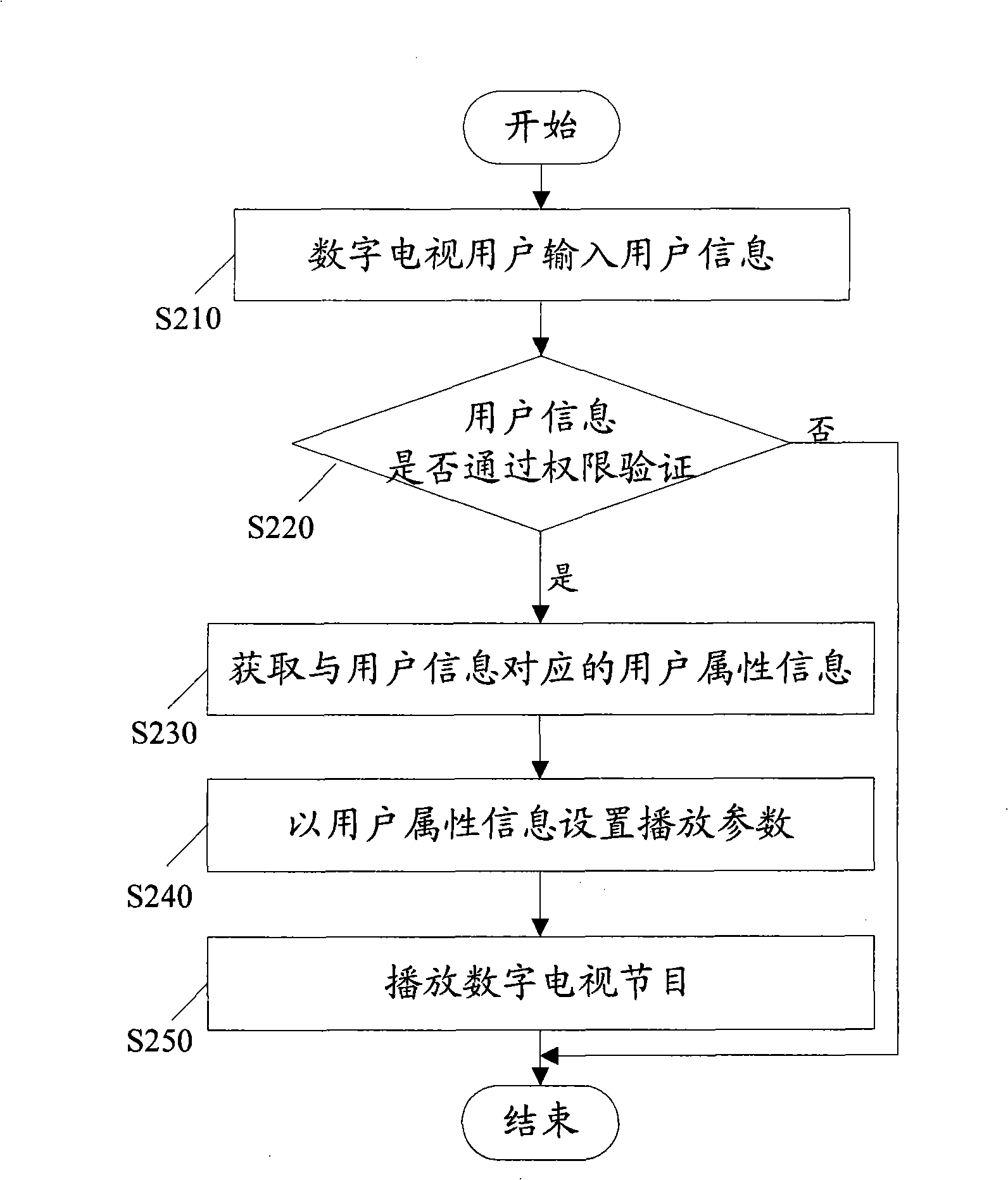
Digital TV receiving system, digital TV user management method and system
ActiveCN101267511AAutomatic memory analysis viewing habitsMeet individual requirementsTelevision system detailsColor television detailsPersonalizationUser management
The invention discloses a system and a method for digital television user management, as well as a digital television receiving system. The digital television user management system comprises a user login unit for providing a user information interface for a digital television user; a user management unit for storing the user attribute information corresponding to each digital television user; a playing control unit for obtaining user attribute information form the user management unit according to the user information inputted by the digital television user, setting the playing parameters of the digital television with the user attribute information, and playing digital television programs. By setting and managing multiple digital television user accounts, different watch attributes for different users are set, personal requirements of different users are met, watch habits of users can be automatically memorized and analyzed, more convenient intelligent selections and better audiovisual services can be provided for users.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
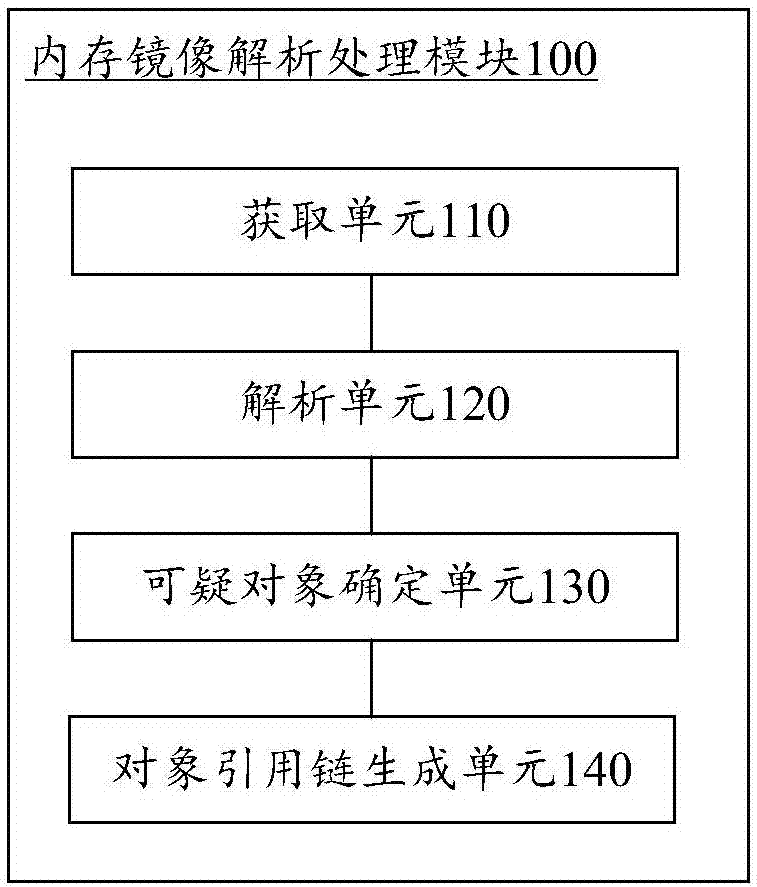
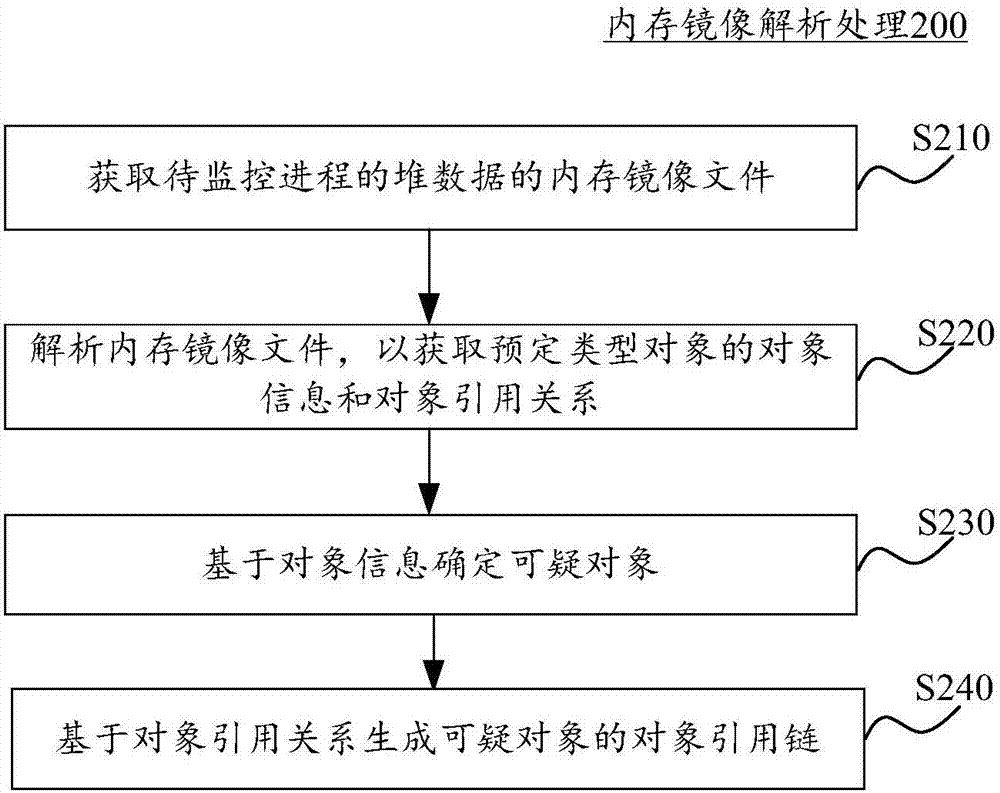
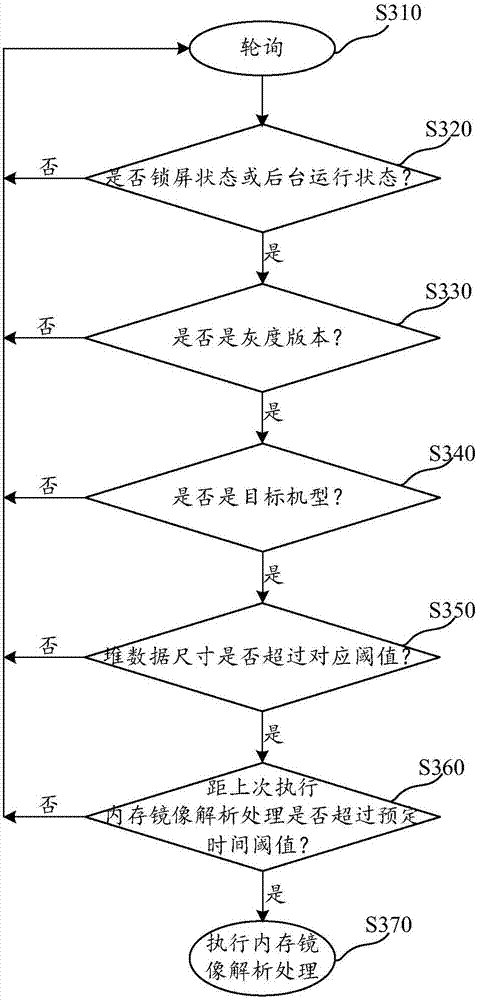
Memory analysis method and device, system and computing device
The invention discloses a memory analysis method and device, a system and a computing device. In the method, a memory image file of the heap data of a to-be-monitored process is obtained and parsed toobtain the object information and the object reference relationship of the predetermined type of object, then suspicious objects are determined based on the object information, and object reference chains of the suspicious objects are generated based on the object reference relationship. In this way, for the problem of excessive heap occupancy of the Java program, according to the long-tail theory and the actual situation, the memory analysis method and device, the system and the computing device place the analysis focus on large objects (such as a very long byte array), classify large objects as the suspicious objects, and can find out the cause of excessive heap occupancy of the Java program by obtaining the suspicious objects in the heap data of the process and the reference chains ofthe suspicious objects.
Owner:ALIBABA (CHINA) CO LTD
Remote evidence taking system based on physical memory analysis
InactiveCN105138709ACredibleGreat effectivenessTransmissionSpecial data processing applicationsRemote controlClient-side
The invention provides a remote evidence taking system based on physical memory analysis. The remote evidence taking system is characterized by comprising a client and a server, wherein a physical memory of the client is mirrored and stored locally, and a mirror image file is subjected to hash value calculation; the mirror image file is analyzed by calling a physical memory analysis line program, and an analysis result and the mirror image file are sent to the server together; the server is used for monitoring the client; if a client connection request is provided, a client fixing character string is sent, and the physical memory mirror image file and the corresponding mirror image file analysis result of the client are mainly collected; the server collects multiple threads and can simultaneously collect the physical memory mirror image files of multiple clients and memory analysis result information and store the memory analysis results into a database; on the other hand, the server is connected with a remote control terminal to mainly send log information of the client to the remote control terminal; retrieval information meeting retrieval conditions are searched from the database according to the conditions of the remote control terminal.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Automated scalable and adaptive system for memory analysis via identification of leak root candidates
InactiveUS7568192B2Error detection/correctionDigital computer detailsMemory profilingTheoretical computer science
Owner:INT BUSINESS MASCH CORP
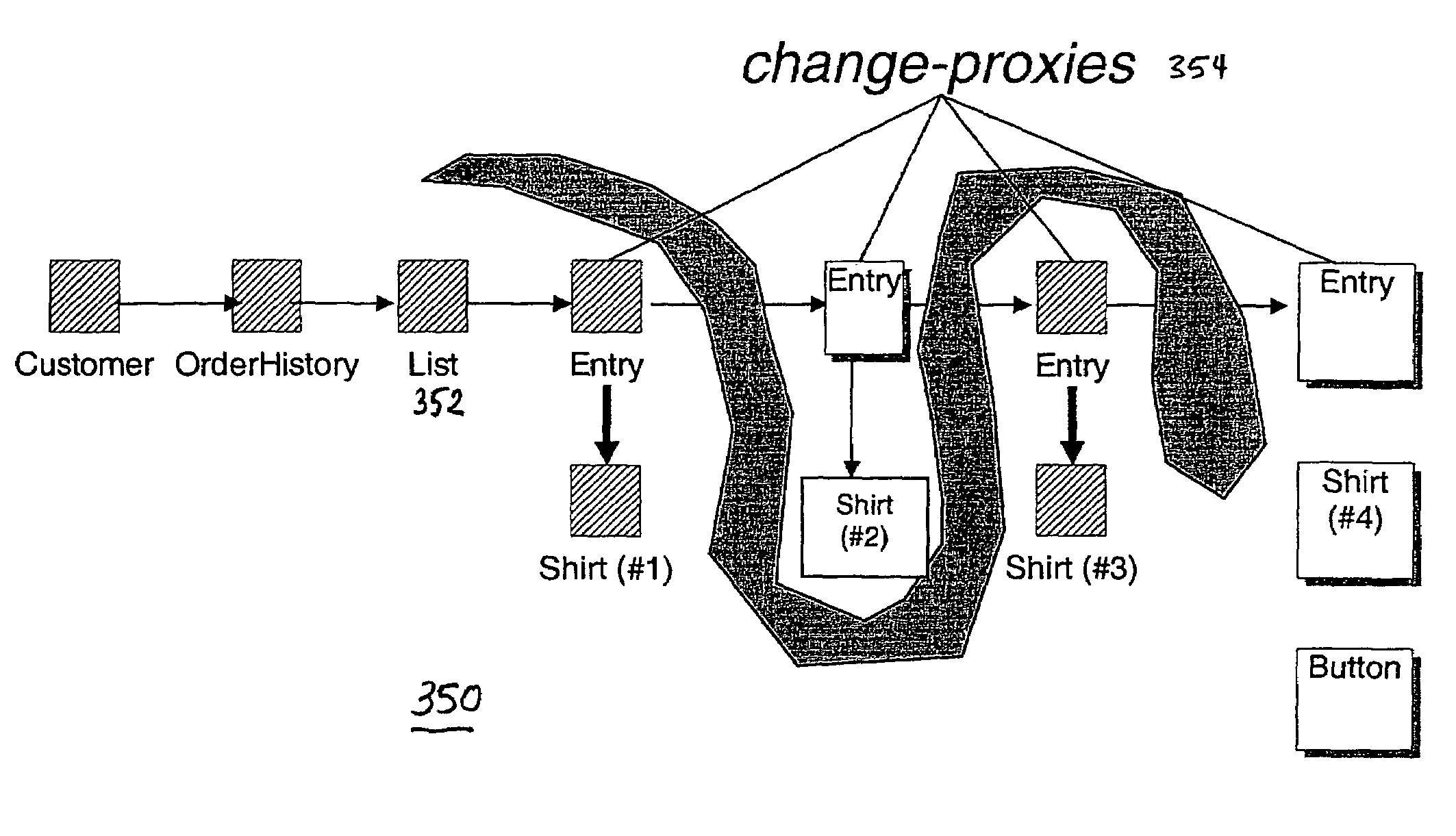
Automated scalable and adaptive system for memory analysis via the discovery of co-evolving regions
A method for identifying co-evolving regions in the memory of a target application comprises the steps of: receiving information identifying a set of data structures that are evolving; and classifying the constituents of the data structures based on their likelihood to evolve in a single coherent manner. Classifying the constituents of the data structures based on their likelihood to evolve in a single coherent manner further comprises determining coherency by similarity of key structural features and data type of the constituents. The method also comprises qualitative and quantitative characterizations of the co-evolving regions based on their observed evolutions.
Owner:IBM CORP
Systems, Methods, and Computer Readable Medium for Analyzing Memory
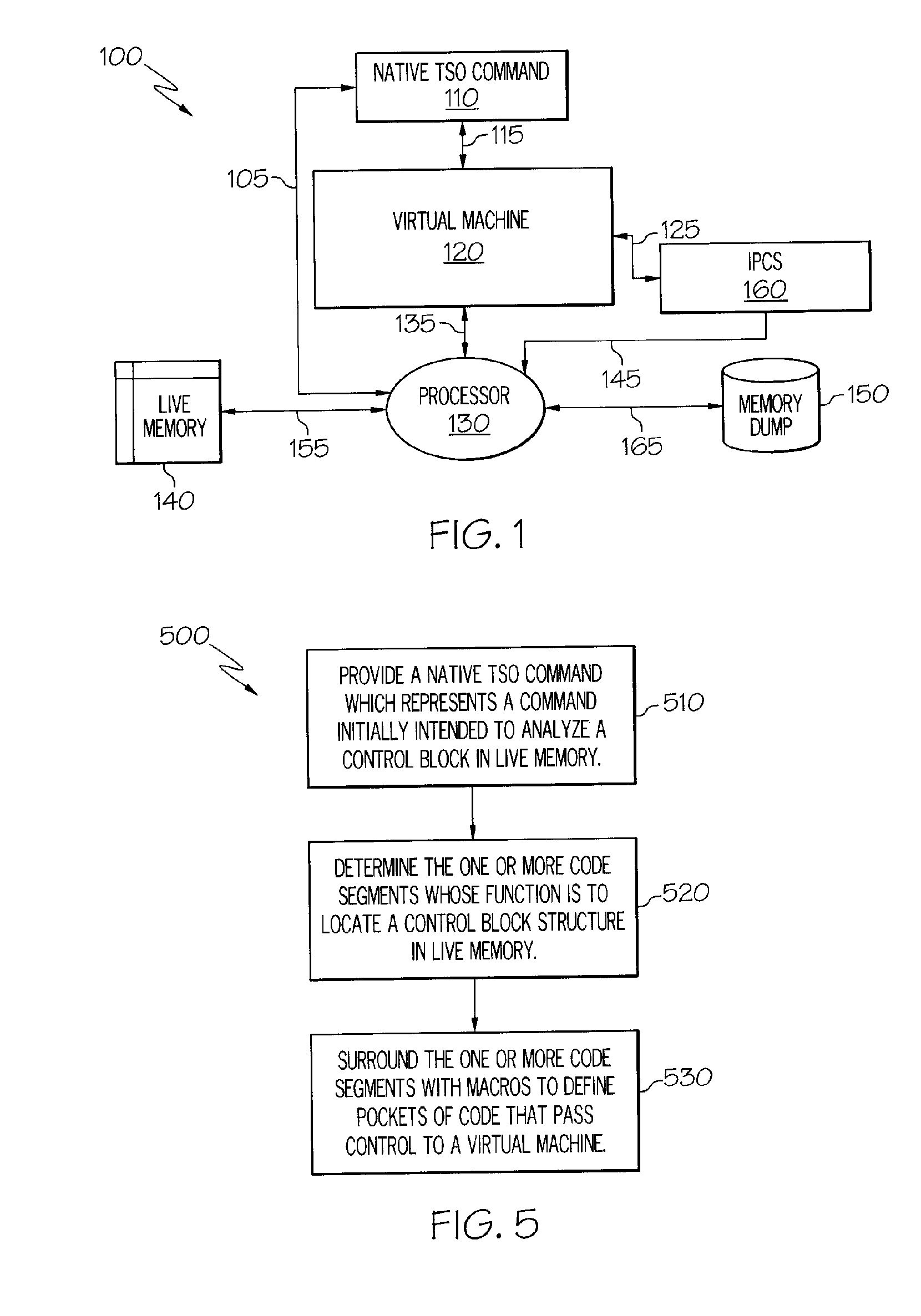
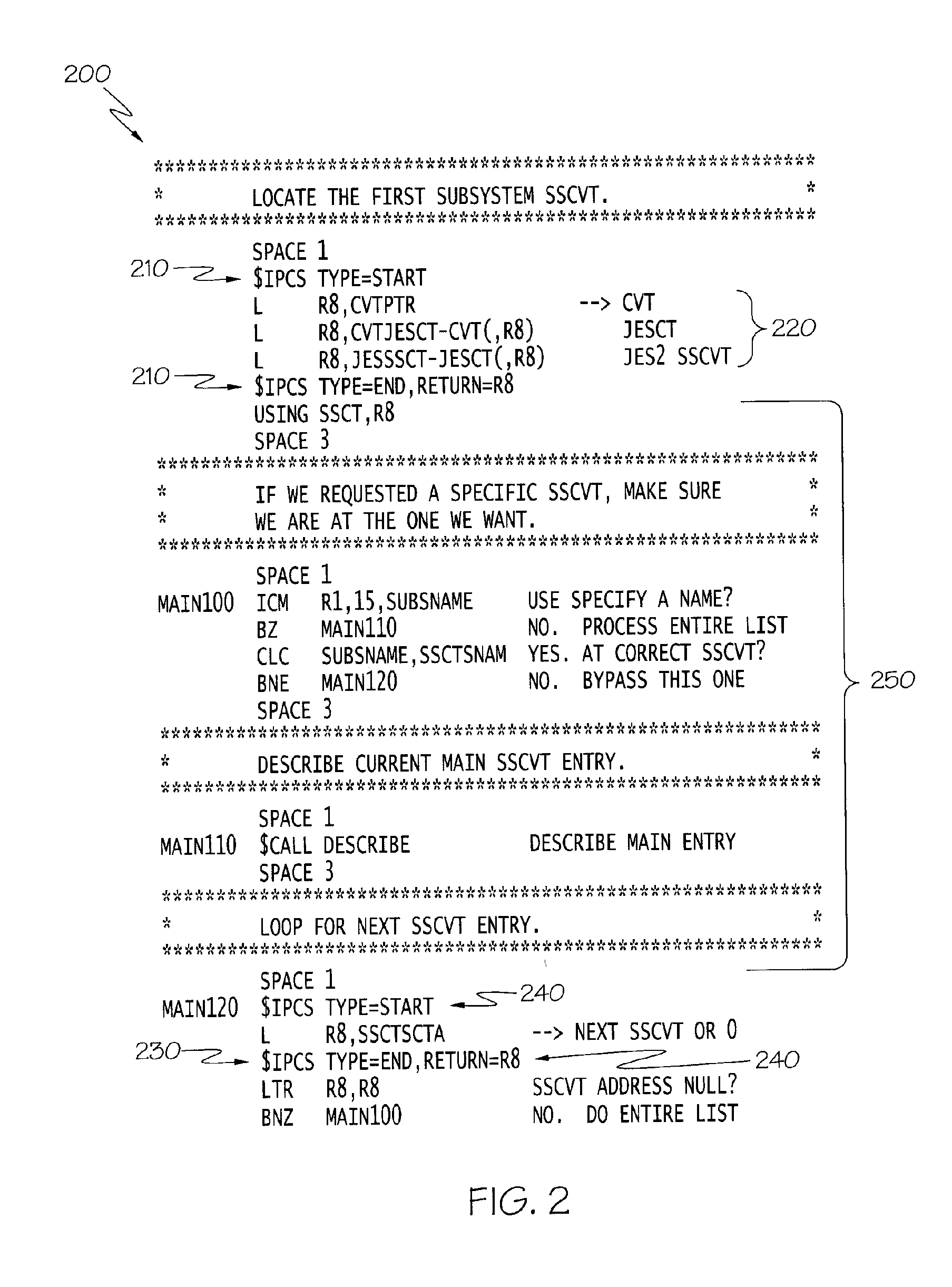
InactiveUS20060225044A1Specific program execution arrangementsMemory systemsMemory typeMemory profiling
Techniques are provided for expanding the functionality of live memory analysis commands to analyze a memory dump or other differing memory types. To this end, a live memory command which normally analyzes live memory is modified to invoke a virtual machine. Live memory commands, in general, have different code segments including a locate code segment which, when executed, locates a first control block in live memory. The locate code segment of the live memory command is modified to invoke a virtual machine for locating a second control block in a memory dump. When the modified code segment is executed, the second control block from a memory dump is accessed.
Owner:GOOGLE LLC
NEON vectorization conversion method for ARM (Advanced RISC Machine) binary code
ActiveCN105242907AMaximize utilizationReduce visitsConcurrent instruction executionProcessor registerGraph generation
The present invention discloses a NEON vectorization conversion method for an ARM (Advanced RISC Machine) binary code. The method comprises the following steps: step 1. carrying out disassembling; step 2. carrying out flow graph generation; step 3. carrying out cycle detection; step 4. carrying out memory analysis; step 5. carrying out instruction translation; and step 6. carrying out assembly instruction output. According to the NEON vectorization conversion method for the ARM binary code disclosed by the present invention, after disassembling the binary code of an ARM, a control flow graph is established and reaching fixed value analysis is performed, and a basic block that a target optimization object is located at is found, and an access mode in the optimized basic block is analyzed, and according to resource scheduling of a free extension register and core register on a chip, a part of repeated access results are stored in a free on-chip register, so that a time overhead of program access is reduced by accessing a high-speed register, thereby achieving the goal of speeding up.
Owner:XI AN JIAOTONG UNIV
Emotional intelligent sound equipment system
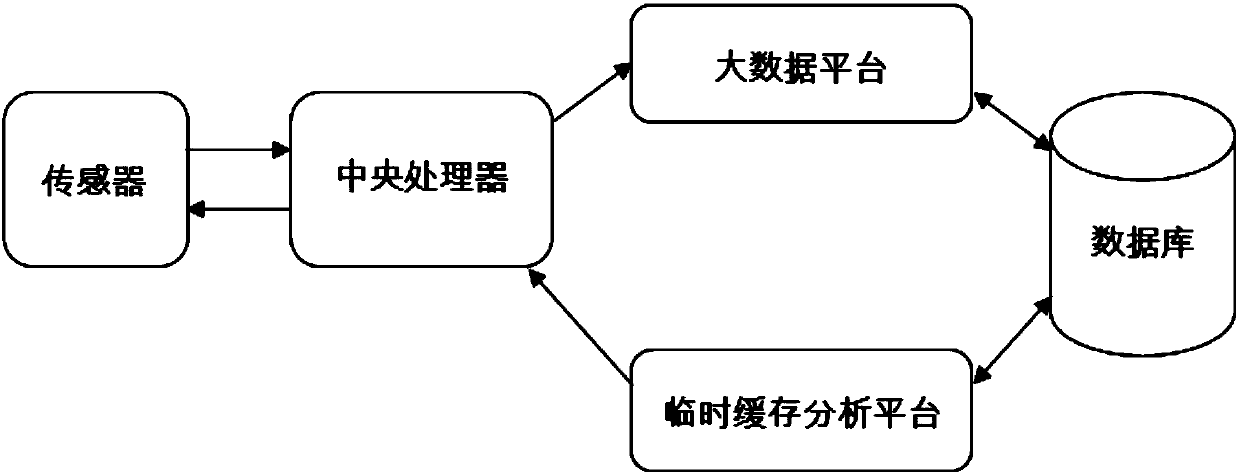
InactiveCN107942695ALow costEasy to acceptComputer controlSpeech analysisData platformSmart technology
The invention relates to an emotional intelligent sound equipment system which is composed of sensors, a central processor, a big data platform, a temporary buffer memory analysis module and a database. The intelligent sound equipment system analyzes expressions and sounds of humans via the sensors and the central processor, and correct emotion information of the humans is obtained via artificialintelligence and big data technologies. The system can use different types of sensors to collect information and analyze big data, obtain correct emotions of the humans from different aspects by meansof technical tools as the emotion characteristic sample database and historical analysis of user information, and make natural and elegant interaction aimed at the corresponding emotion of the humans. Especially, the emotional intelligent sound equipment system uses different emotion characteristic databases to overcome disadvantages in the prior art, the human emotions are analyzed and identified more accurately, the system is very low in cost, and users can accept and use the system much conveniently.
Owner:北京贞宇科技有限公司
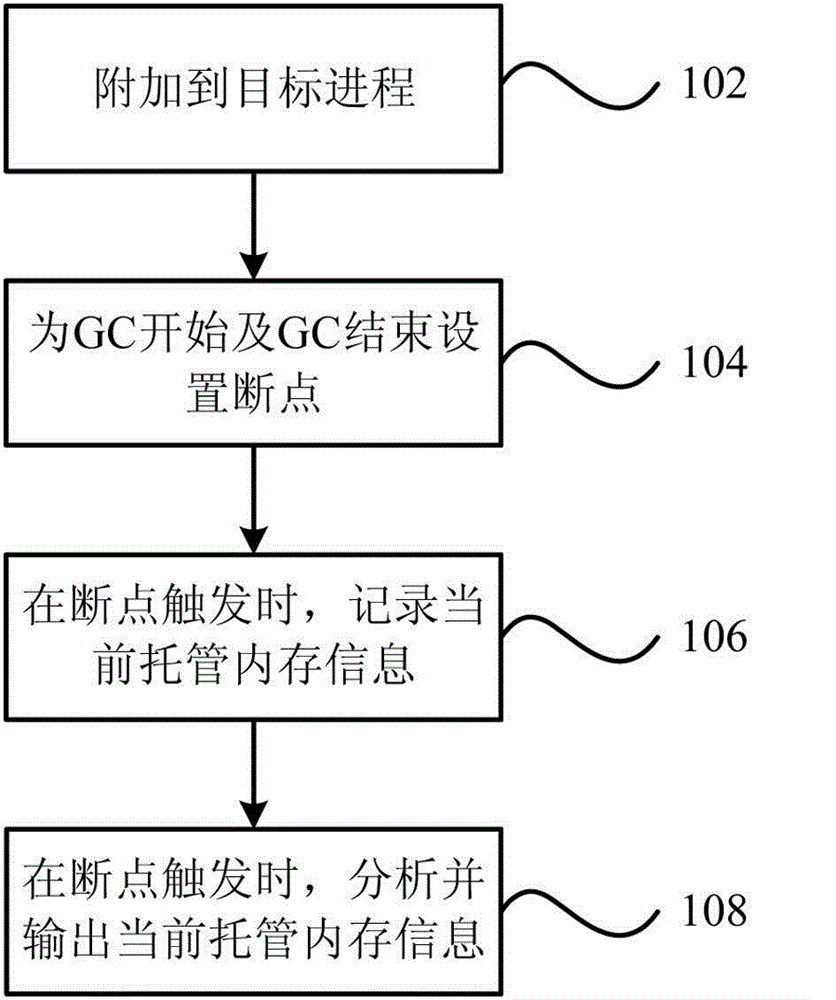
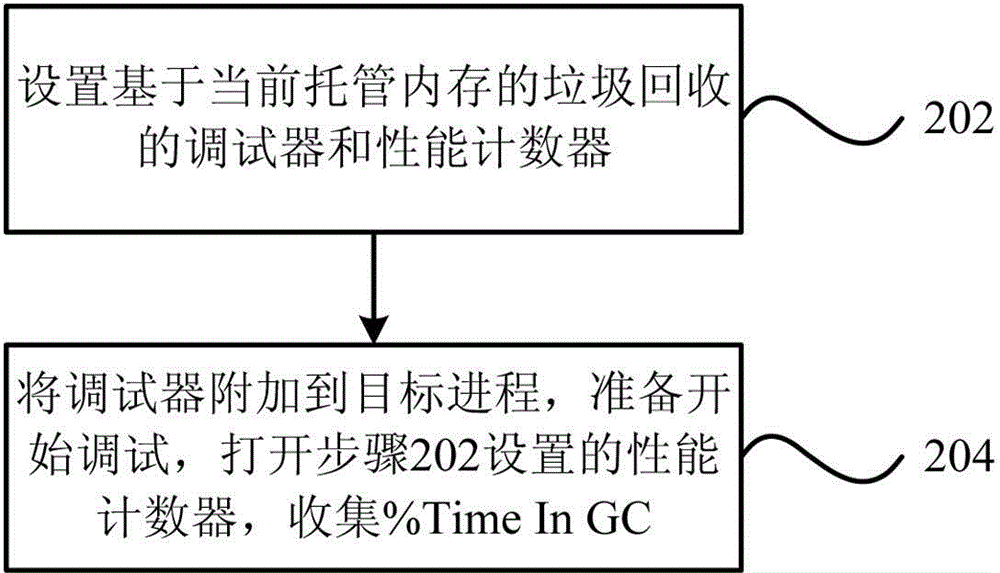
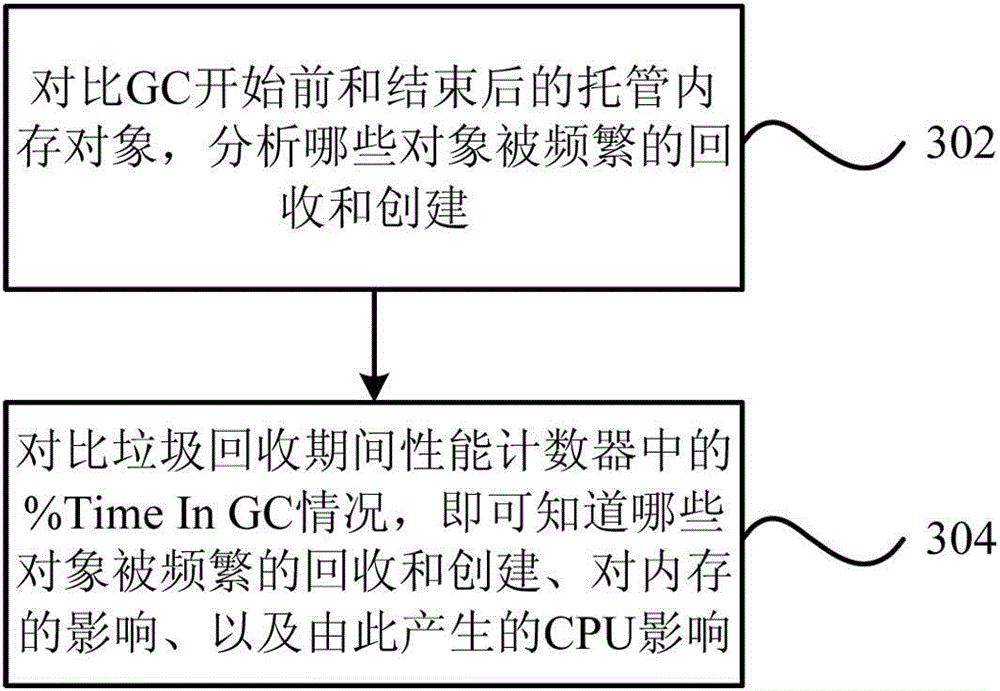
Memory analysis and optimization method and system based on garbage collection
The invention provides a memory analysis and optimization method based on garbage collection. The method comprises the steps as follows: appending garbage collection of current hosted memory to a target process; based on the garbage collection of the current hosted memory, which is appended to a target program, setting breakpoints for the beginning and ending of the garbage collection; when the set breakpoints are triggered, analyzing and outputting the information of the current hosted memory. The invention further provides a memory analysis and optimization system based on garbage collection. Through the technical scheme provided by the invention, a universal and unified analysis and optimization ideal can be created by fully utilizing memory analysis and optimization of accurately evaluating influence on system performance caused in each garbage collection process with existing codes on the basis of existing memory analysis based on garbage collection.
Owner:YONYOU NETWORK TECH
System and method for performing on-cloud memory analysis, forensic and security operations on connected devices
The invention relates to a system for protecting IoT devices from malicious code, which comprises: (a) a memory extracting module at each of said IoT devices, for extracting a copy of at least a portion of the memory content from the IoT device, and sending the same to an in-cloud server; and (b) an in-cloude server for receiving said memory content, and performing an integrity check for a possible existance of malicious code within said memory content.
Owner:B G NEGEV TECH & APPL LTD
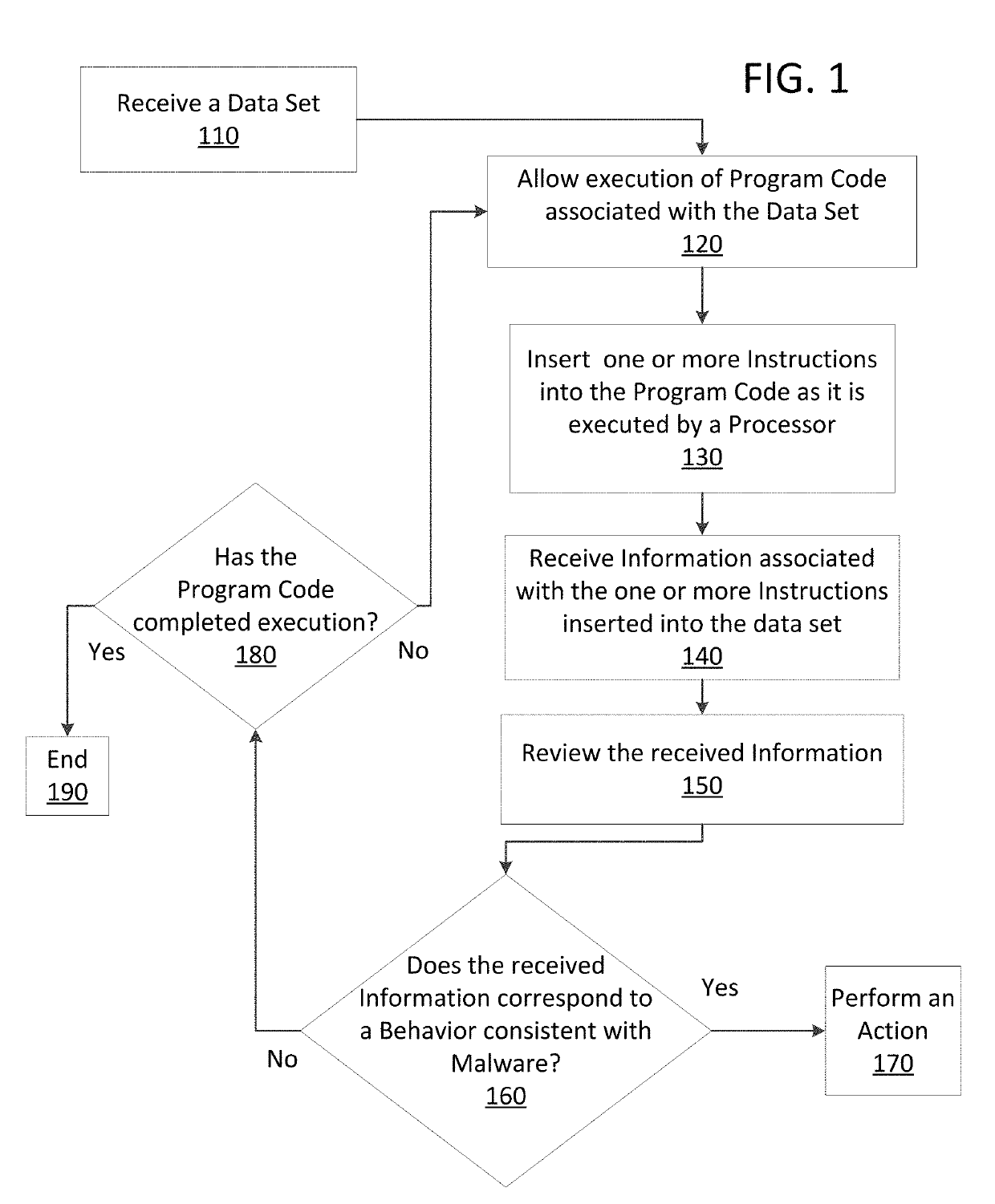
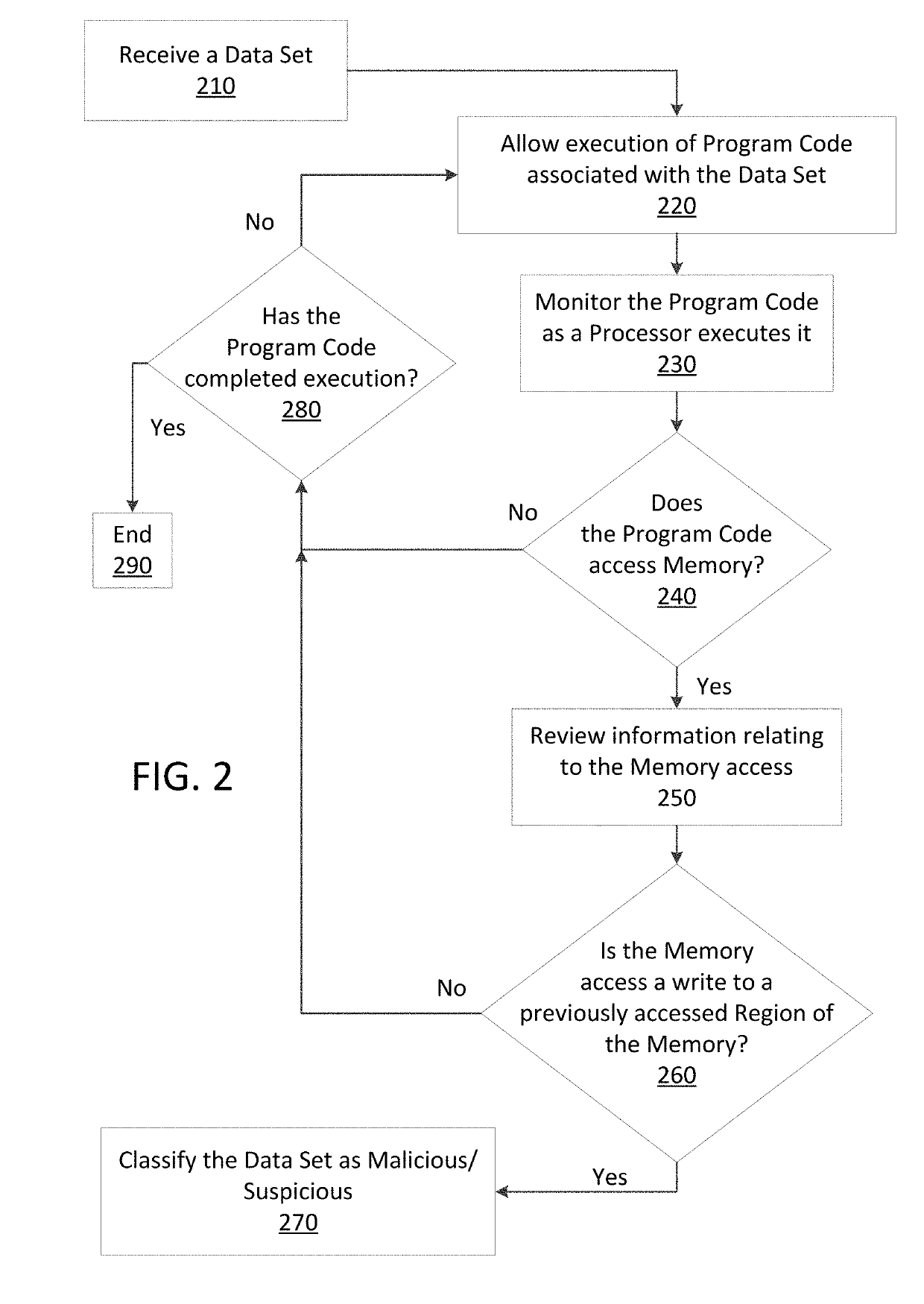
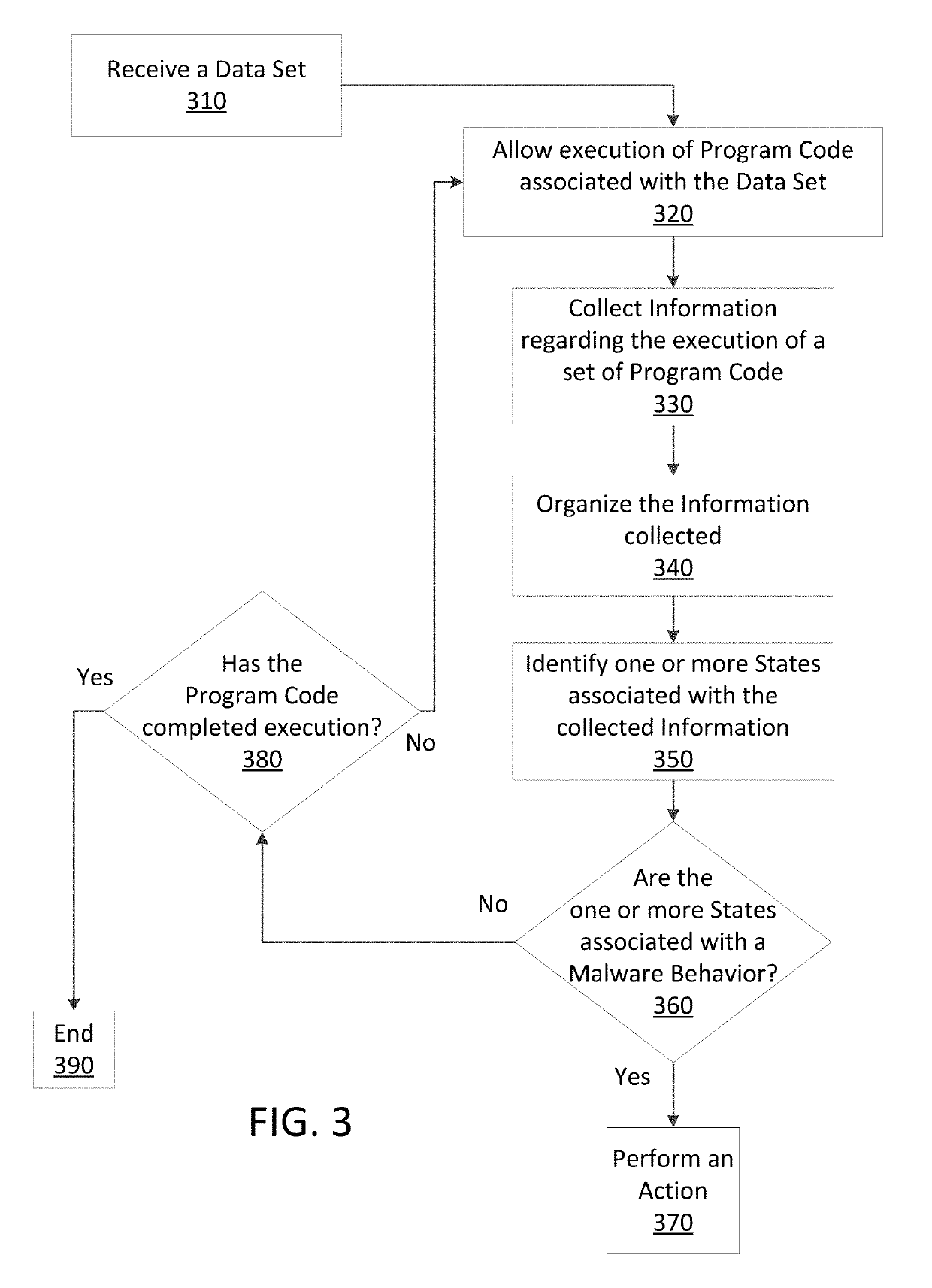
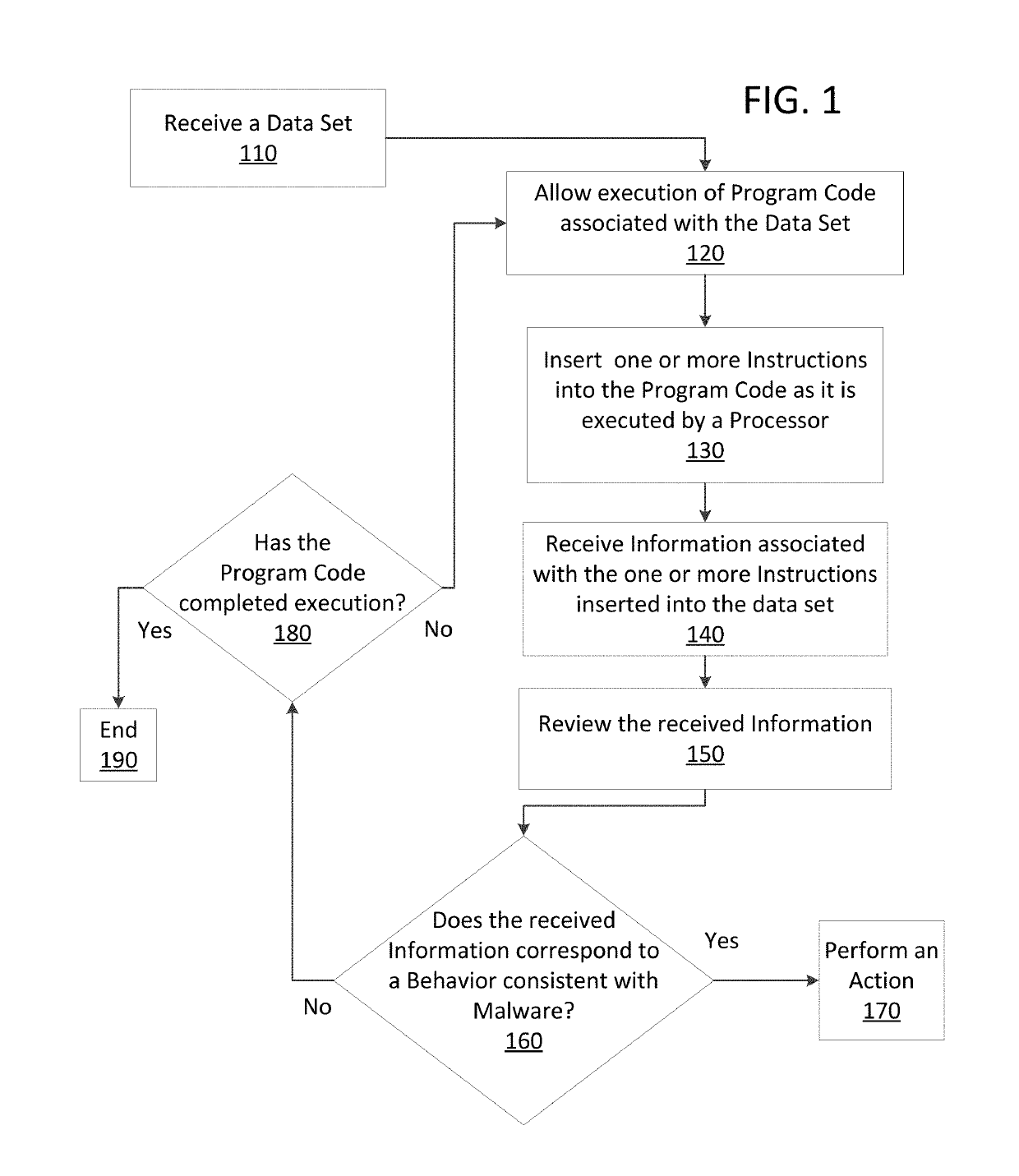
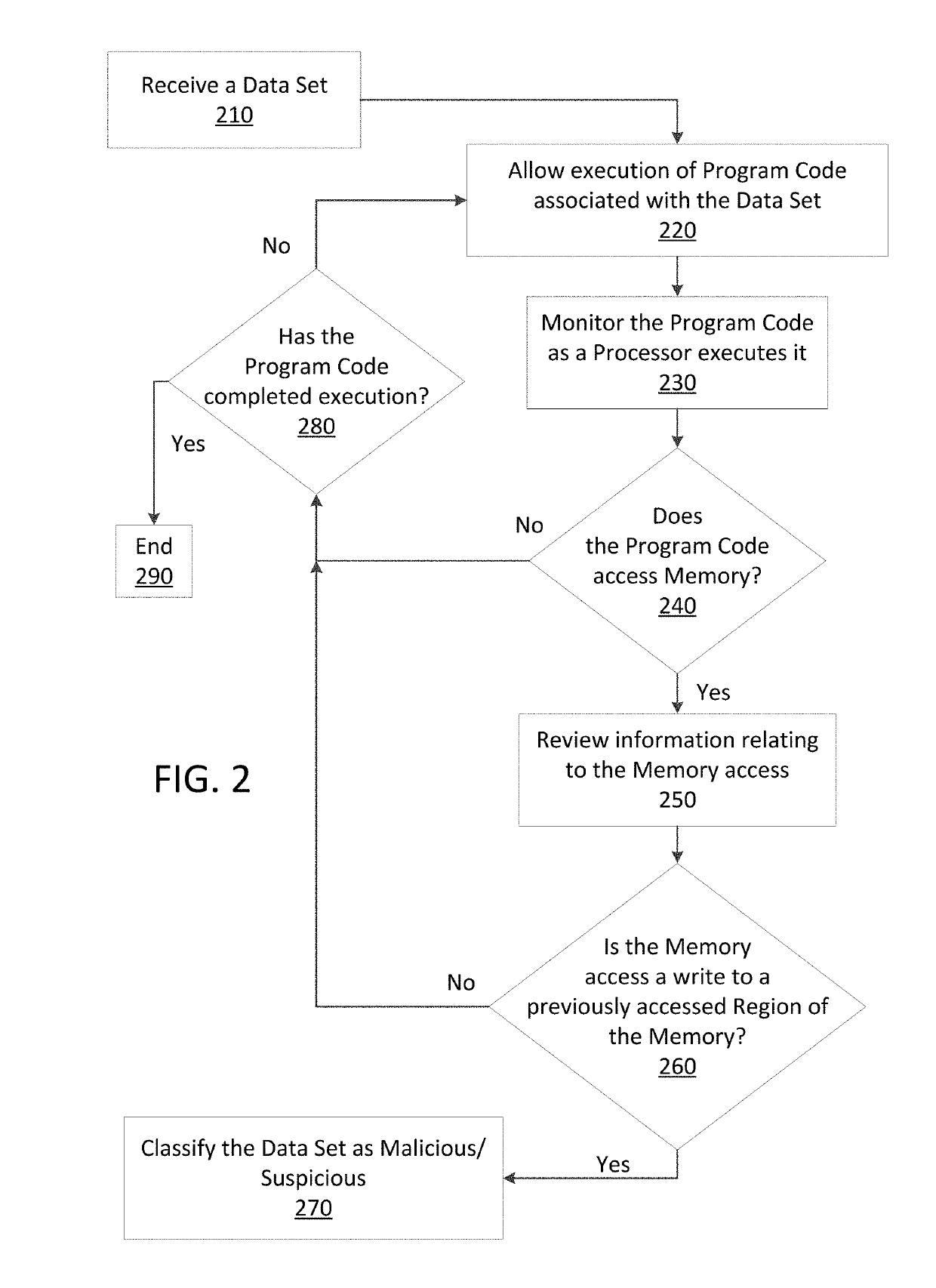
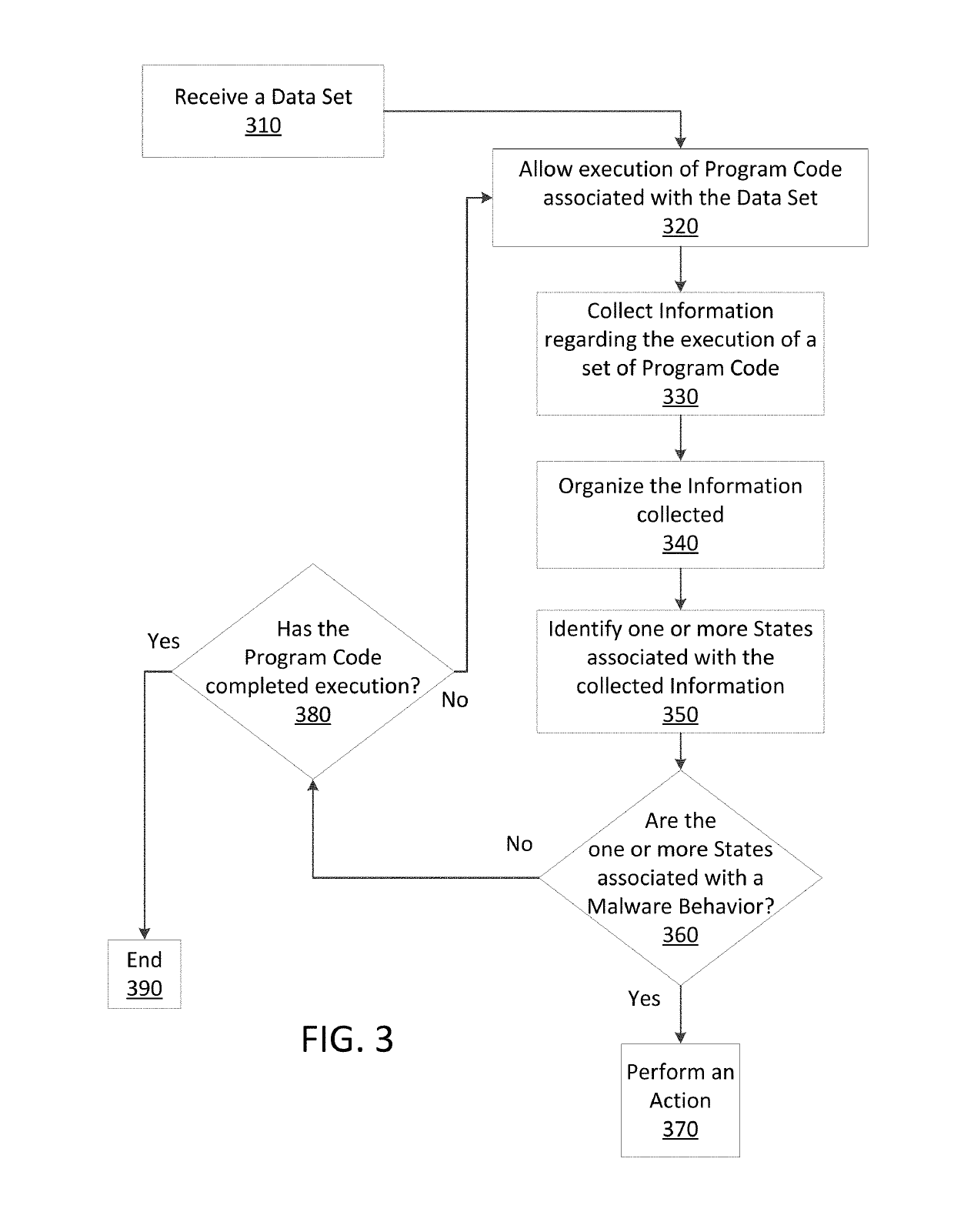
Just in time memory analysis for malware detection
ActiveUS20190114421A1Preventing executionPrevent wrong actionPlatform integrity maintainanceMemory profilingData set
Methods and apparatus consistent with the present disclosure may use instrumentation code that remains transparent to an application program that the instrumentation code has been injected into. In certain instances, data sets that include executable code may be received via packetized communications or be received via other means, such as, receiving a file from a data store. The present technique allows a processor executing instrumentation code to monitor actions performed by the program code included in a received data set. Malware may be detected by scanning suspect program code with a malware scanner, malware may be detected by identifying suspicious actions performed by a set of program code, or malware may be detected by a combination of such techniques.
Owner:SONICWALL
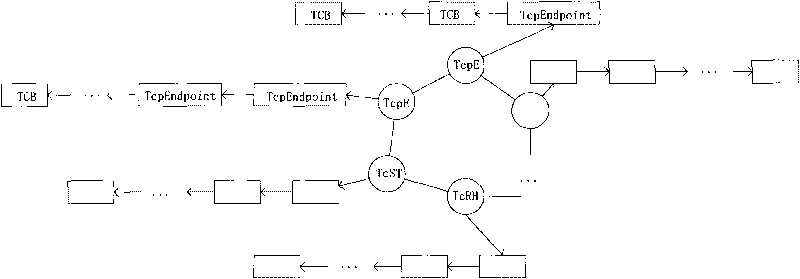
Obtaining method of network information under Vista operating system
InactiveCN101727323AReliable method of acquisitionMemory adressing/allocation/relocationSpecific program execution arrangementsOperational systemNetwork connection
The invention discloses an obtaining method of network information under a Vista operating system, which comprise the following steps of: obtaining the virtual address of a base address of a tcpip.sys module through physical memory analysis, further obtaining the virtual address for obtaining a double linked list TcpEndpointPool under the base address, and obtaining network connection information through traversing the double linked list. The obtaining method has the advantages of high reliability and high speed.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Virtual machine-based dynamic introspection function-level virtual machine kernel detection system and method
ActiveCN108469984AAnalytical integrityIntegrity checkSoftware simulation/interpretation/emulationControl flowVirtual machine introspection
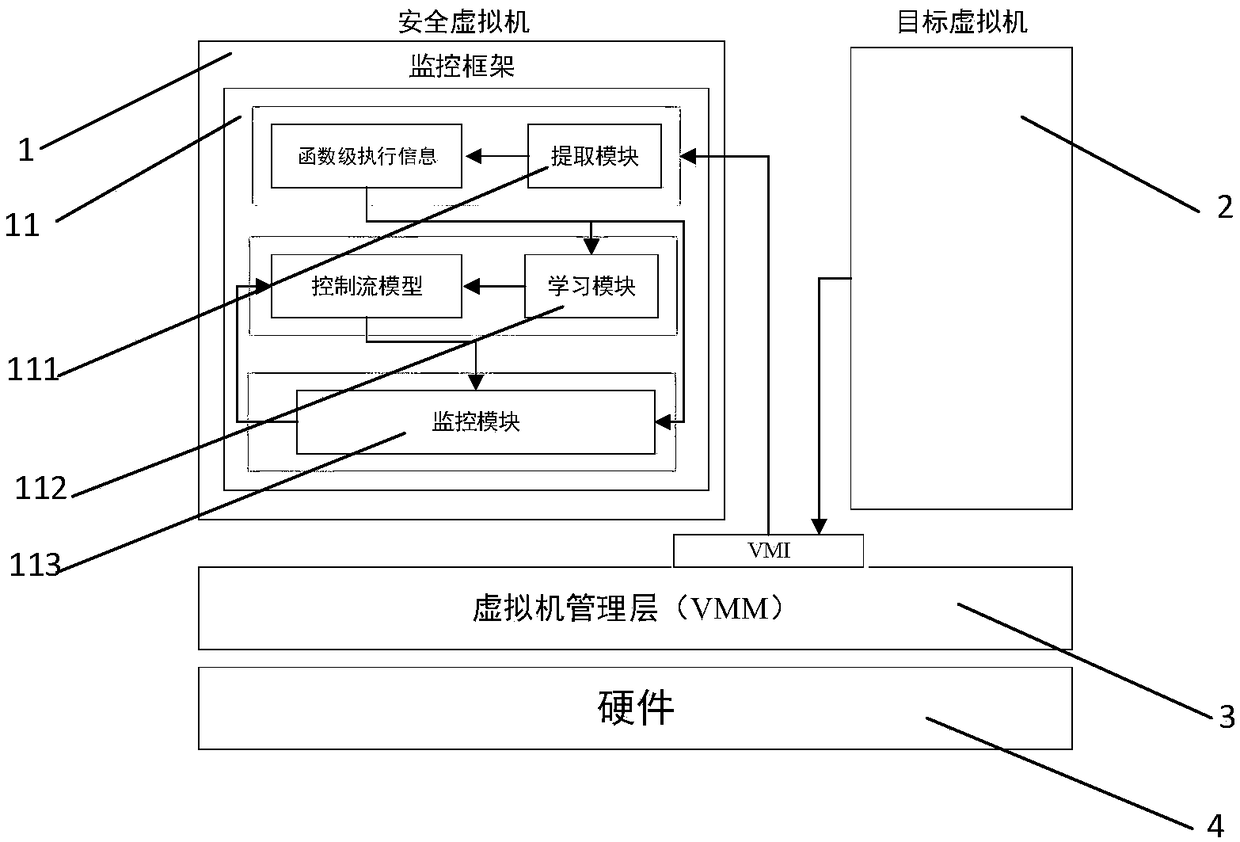
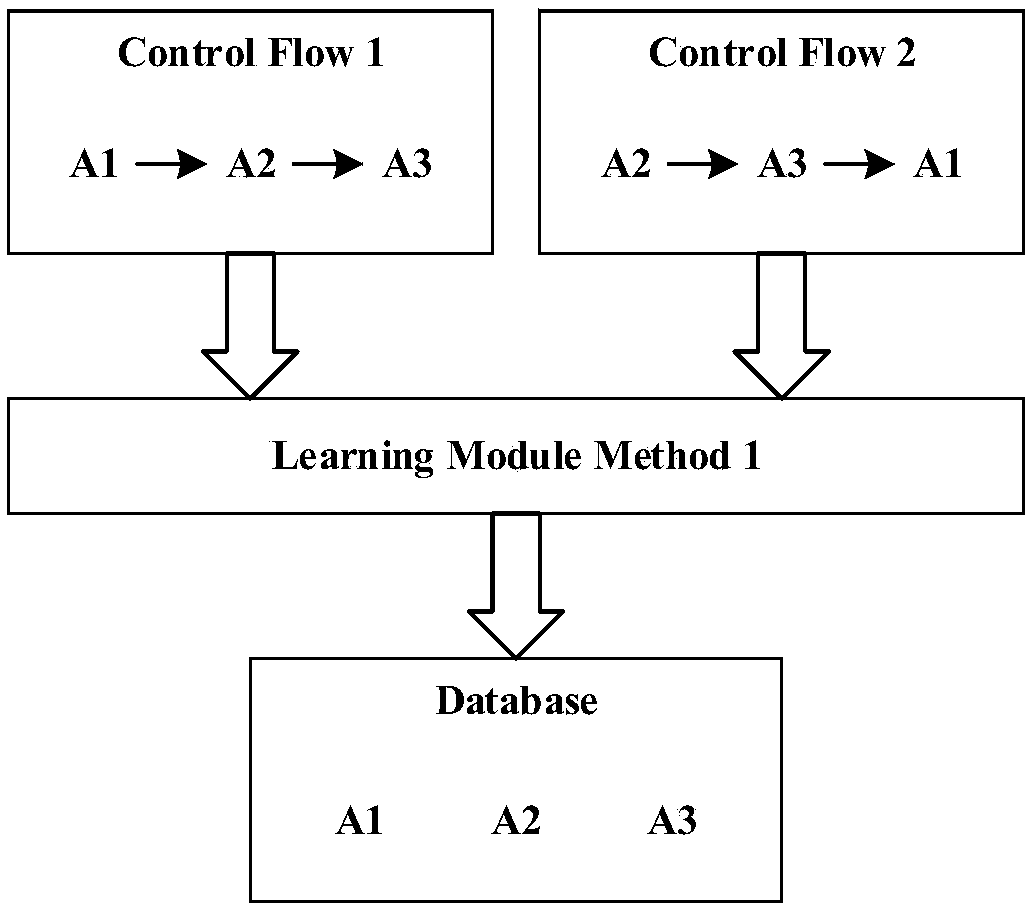
The invention discloses a virtual machine-based dynamic introspection function-level virtual machine kernel detection system and method, and belongs to the field of cloud safety. The device compriseshardware which is used for providing hardware basis for a secure virtual machine, a target virtual machine and a virtual machine management layer; the secure virtual machine comprises a monitoring framework; the secure virtual machine interacts with the target virtual machine through the virtual machine management layer; the virtual machine management layer comprises a connection extraction module; and the extraction module is connected with each of the learning module and a monitoring module through page execution information. The method comprises the following steps of: starting a monitor, injecting a monitoring point to the target virtual machine by the extraction module, so as to ensure that the virtual machine management layer can monitor sub-functions in calling; carrying out staticanalysis by utilizing a static memory analysis method and dynamic tracking, so as to obtain subsequent sub-functions and carry out monitoring; and carrying out loop execution until system calling is returned. According to the system and method, execution information is modeled through three learning methods, so that integrity of kernel control flows is detected, and the kernel control flows are prevented from being detected and broken through by attackers.
Owner:HARBIN INST OF TECH +1
XenServer-platform-oriented Virtual machine memory evidence collection method
ActiveCN107621971ADoes not affect running statusNo eigenvalue retrieval requiredResource allocationSoftware simulation/interpretation/emulationMemory profilingMirror image
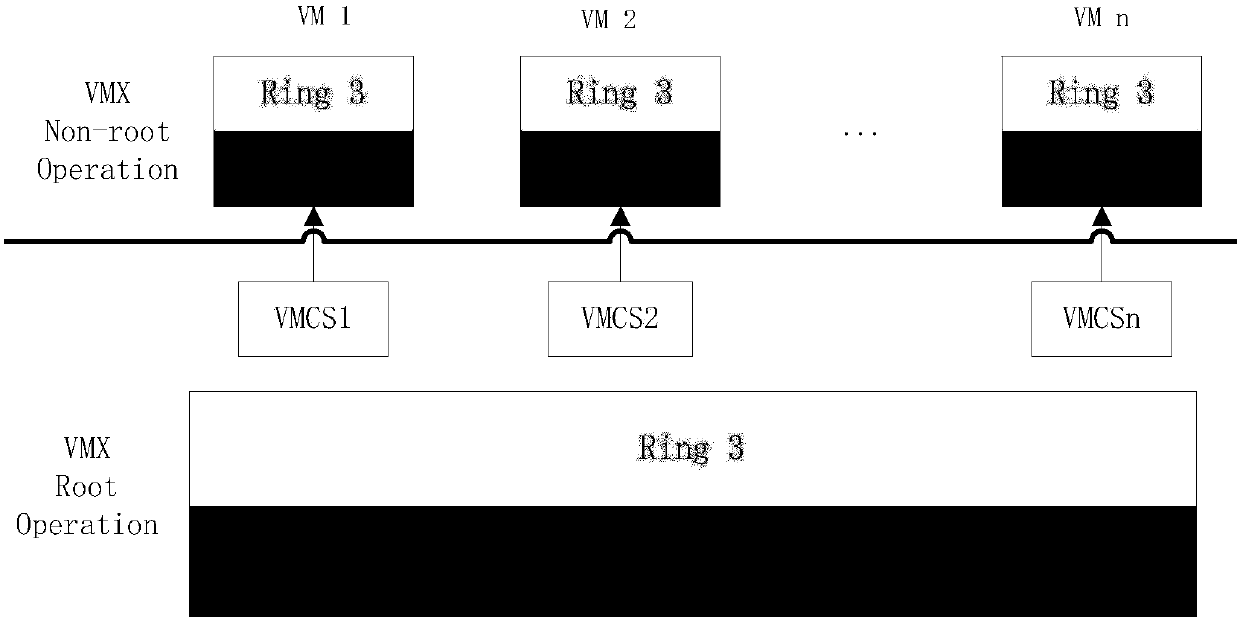
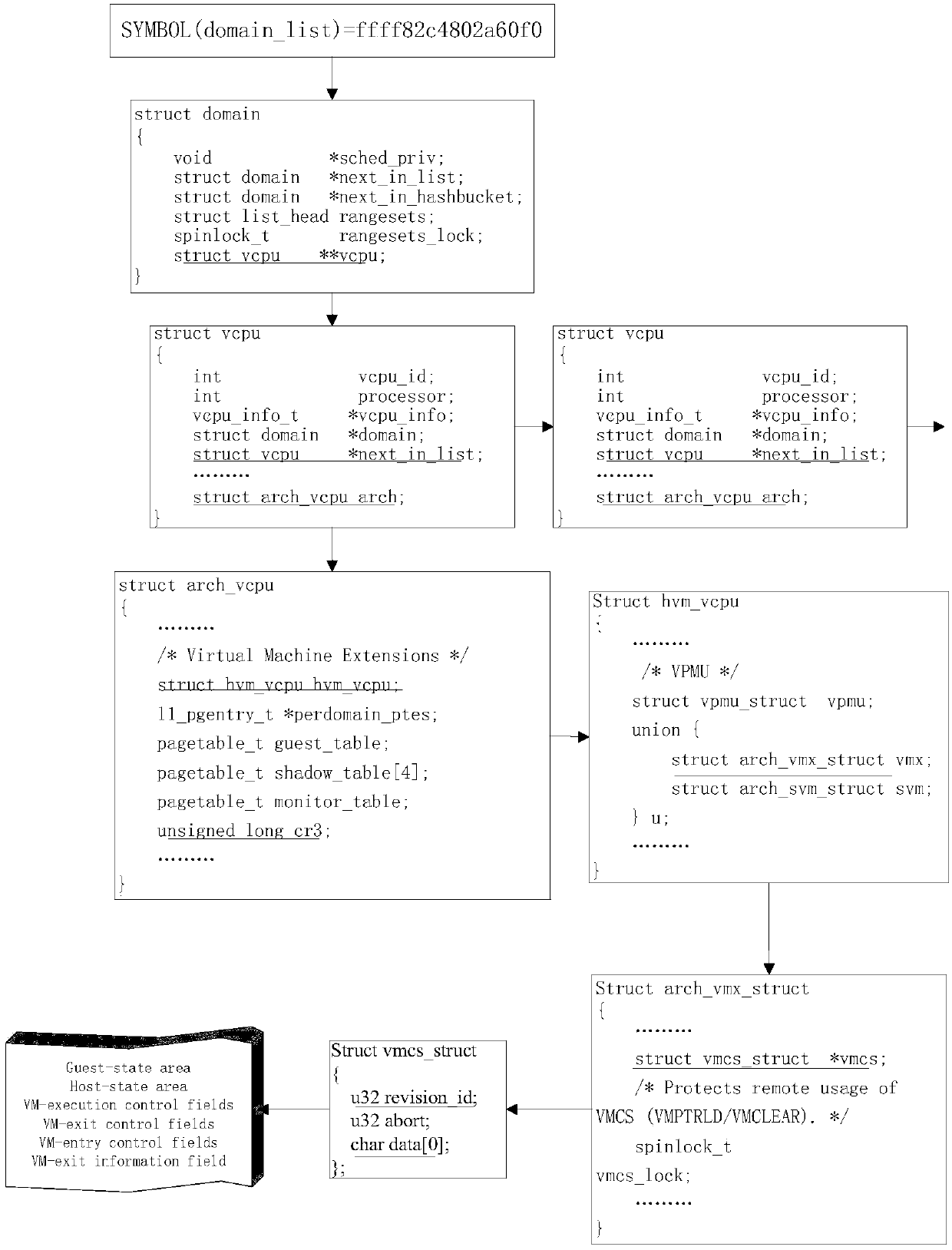
The invention discloses a XenServer-platform-oriented virtual machine memory evidence collection method. The method comprises the steps of obtaining physical memory information of a host computer as amemory mirror image file; obtaining a kernel symbol table file in the host computer; obtaining a physical address of vmcoreinfo_xen content; obtaining the vmcoreinfo_xen content according to the physical address, and parsing virtual addresses of domain_list and pgd_l4 of kernel symbols; converting the virtual address of pgd_l4 into a physical address; obtaining a structure body address; obtainingstructure bodies corresponding to virtual machines according to relationshipsamong structure bodies; achieving address conversion of the physical addresses of the virtual machines; judging versions of virtual machine operating systems after the content of physical memories of the virtual machines is obtained; analyzing the physical memories by using corresponding memory analysis methods accordingto the different versions of the virtual machine operating systems after the virtual machine operating systems are determined.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
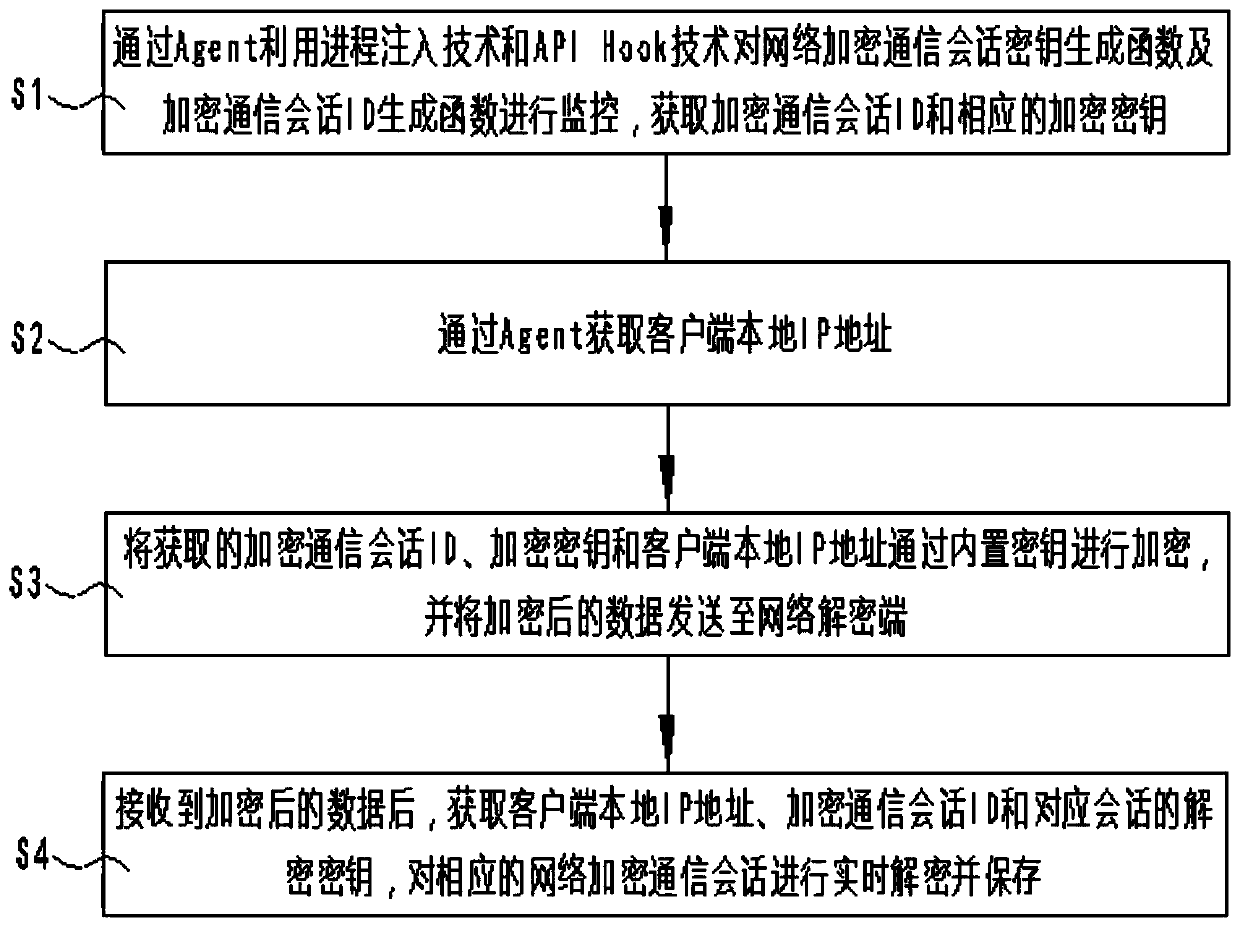
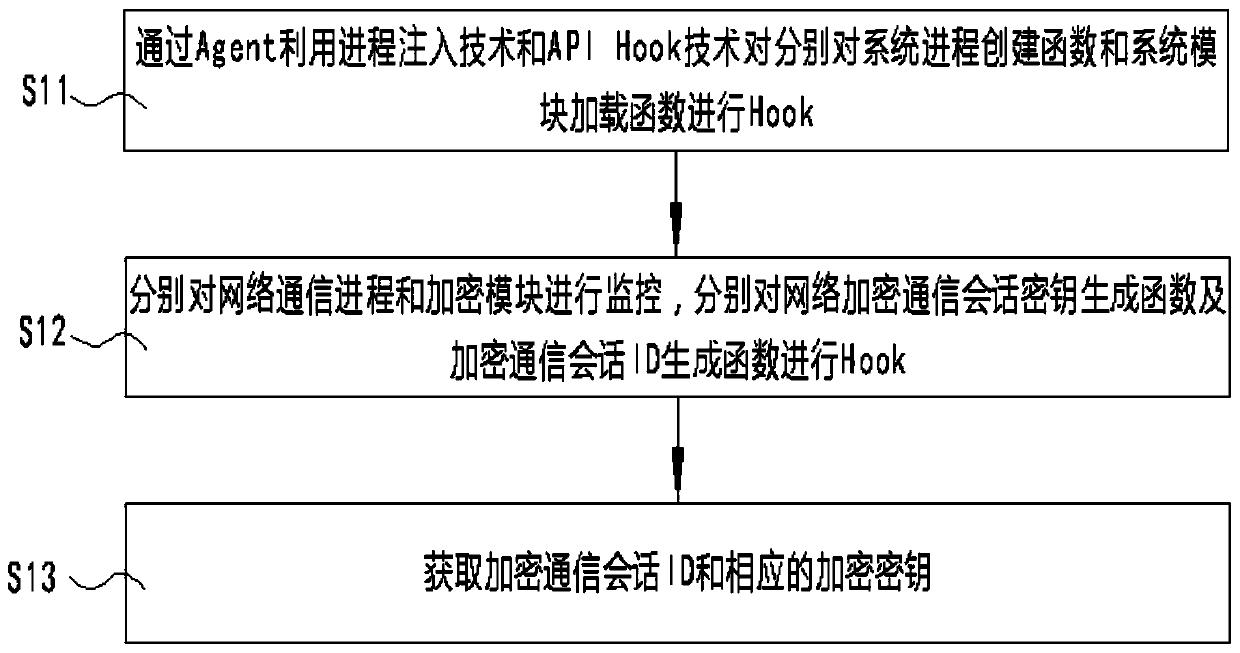
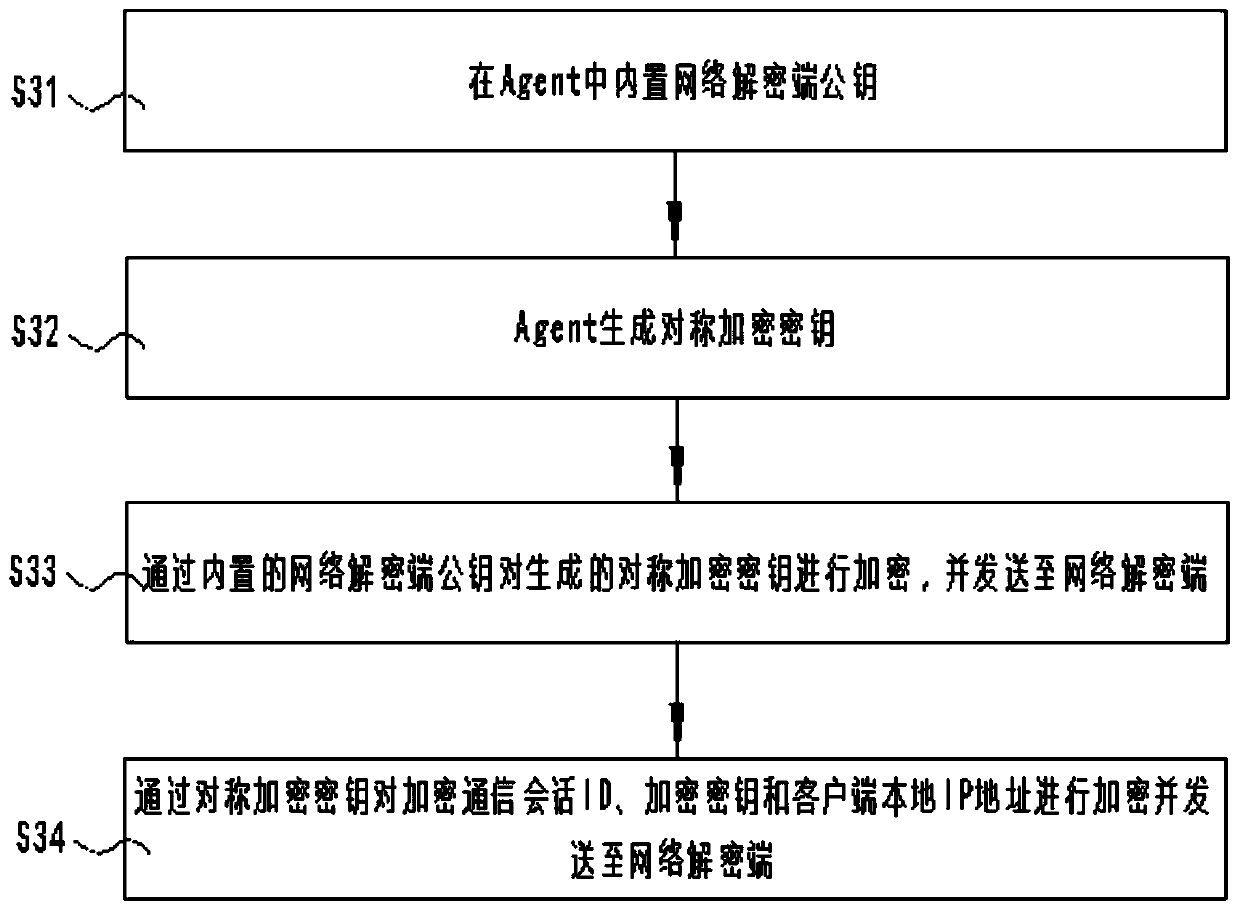
SSL/TLS network encryption communication information real-time decryption method based on memory analysis
The invention discloses an SSL / TLS network encryption communication information real-time decryption method based on memory analysis. The method comprises the following steps: monitoring a network encryption communication session key generation function and an encryption communication session ID generation function by using a process injection technology and an API Hook technology through an Agentto obtain an encryption communication session ID and a corresponding encryption key; obtaining a local IP address of the client through the Agent; encrypting the acquired encryption communication session ID, the network encryption communication session key and the local IP address of the client through a temporarily generated symmetric encryption key, and sending the encrypted data to a network decryption end; and after receiving the encrypted data, obtaining a local IP address of the client, the encryption communication session ID and a decryption key of the corresponding session, and decrypting and storing the corresponding network encryption communication session in real time. According to the invention, the extraction of the network communication encryption key and the real-time decryption of the network encryption communication content can be effectively realized, and the detection efficiency is improved.
Owner:成都安舟信息技术有限公司
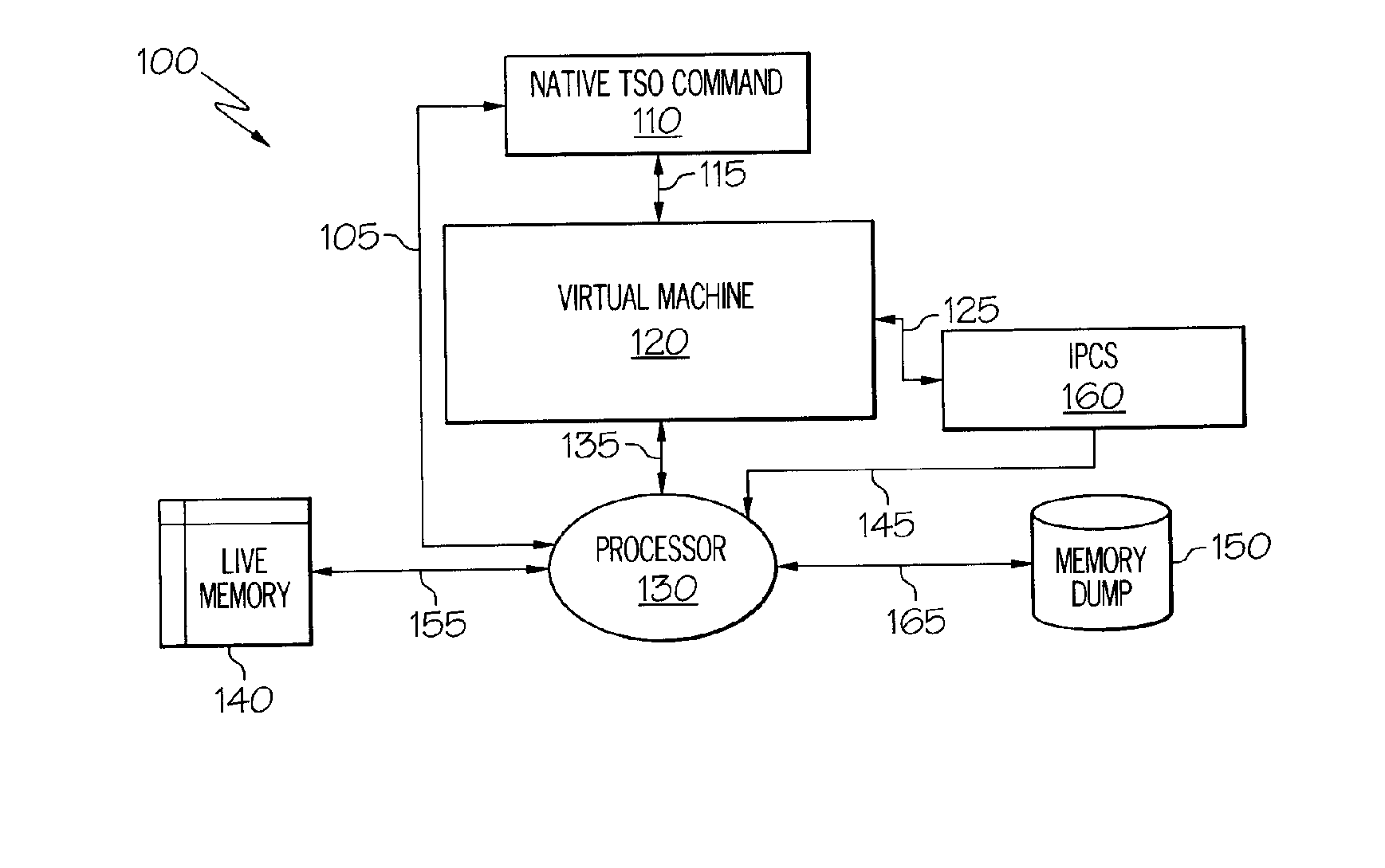
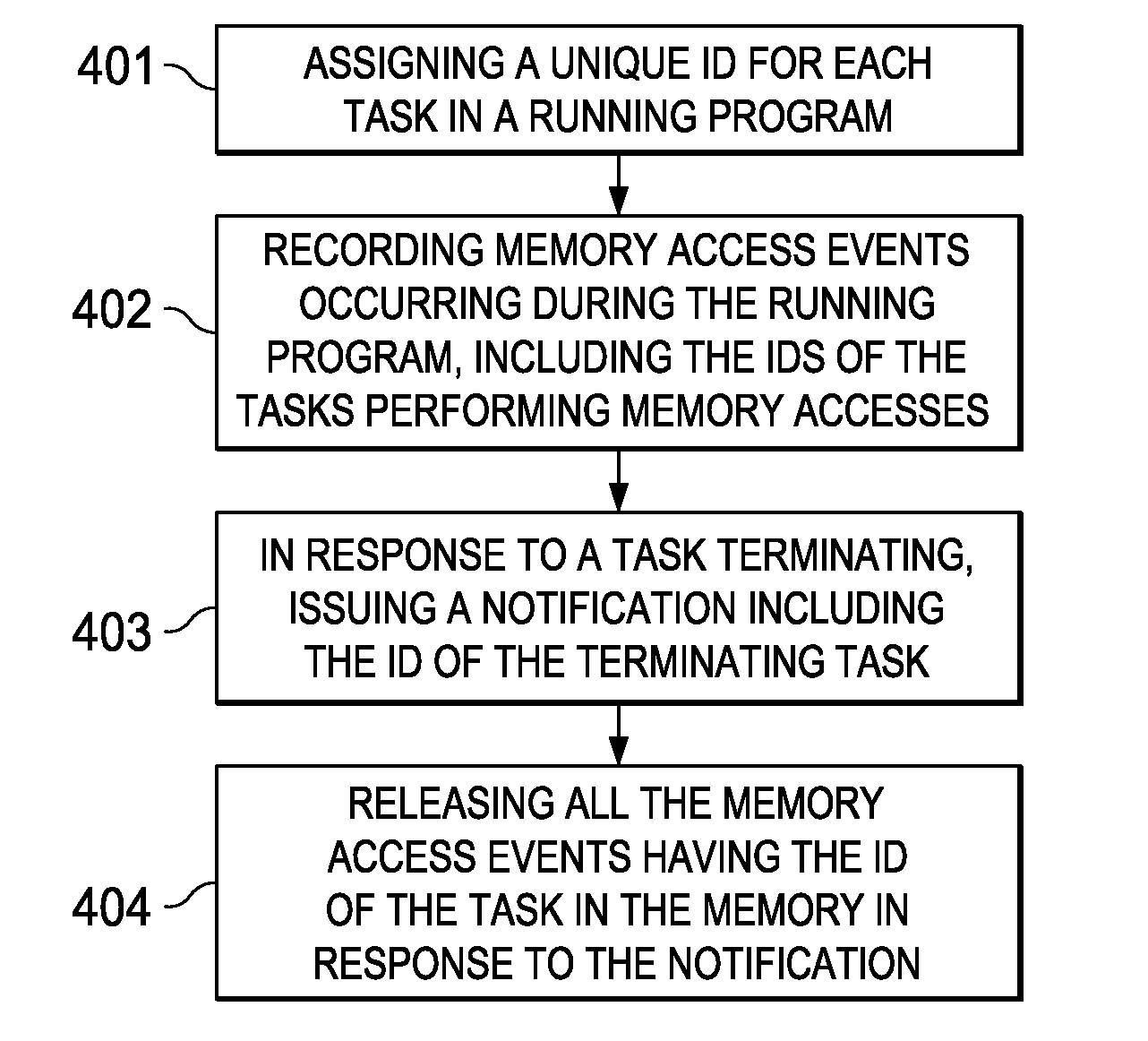
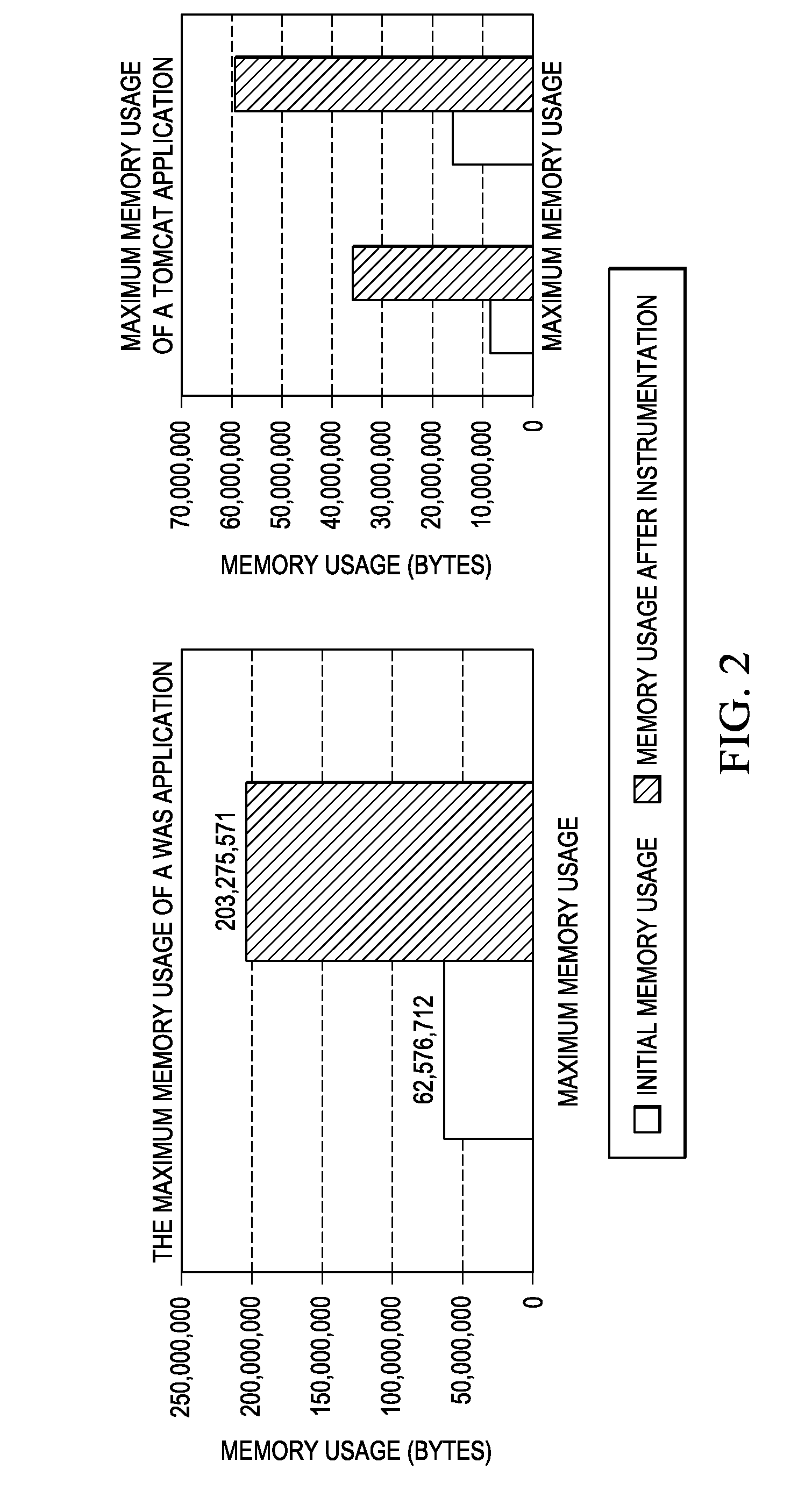
Method and System for Facilitating Memory Analysis
InactiveUS20110078684A1Easy to analyzeError detection/correctionMultiprogramming arrangementsMemory access patternMemory analysis
A method and system for facilitating runtime memory analysis. The method includes: assigning a unique ID for each task in a running program; recording memory access events occurring during the running program, including the IDs of the task performing the memory accesses; issuing a task termination notification in response to a task terminating, the task termination notification including the ID of the terminating task; and releasing all the memory access events having the ID of the terminating task in the memory, in response to the task termination notification. This method and system can ensure that the memory access events stored in the memory will not increase unlimitedly, so that the memory overhead is reduced remarkably and dynamic memory analysis can be faster and more efficient.
Owner:IBM CORP
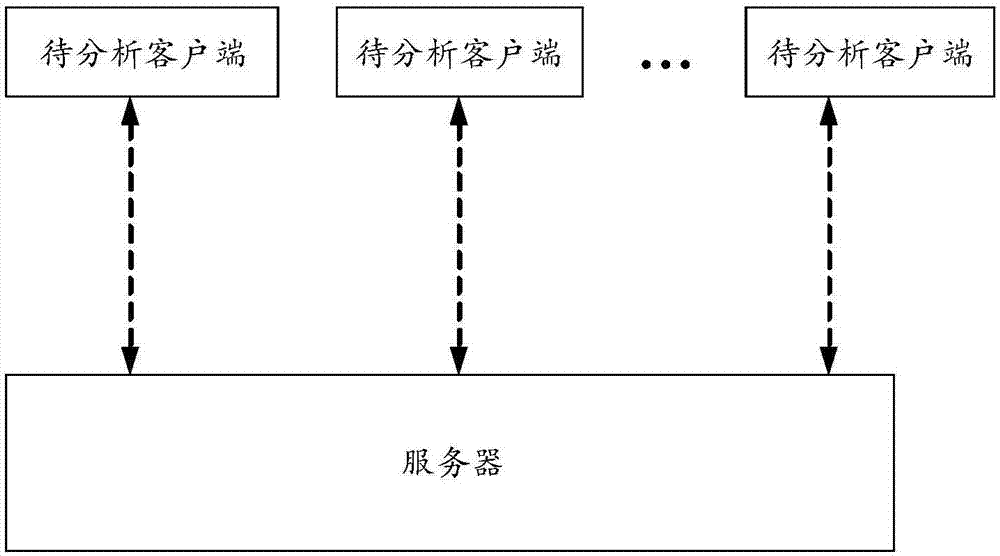
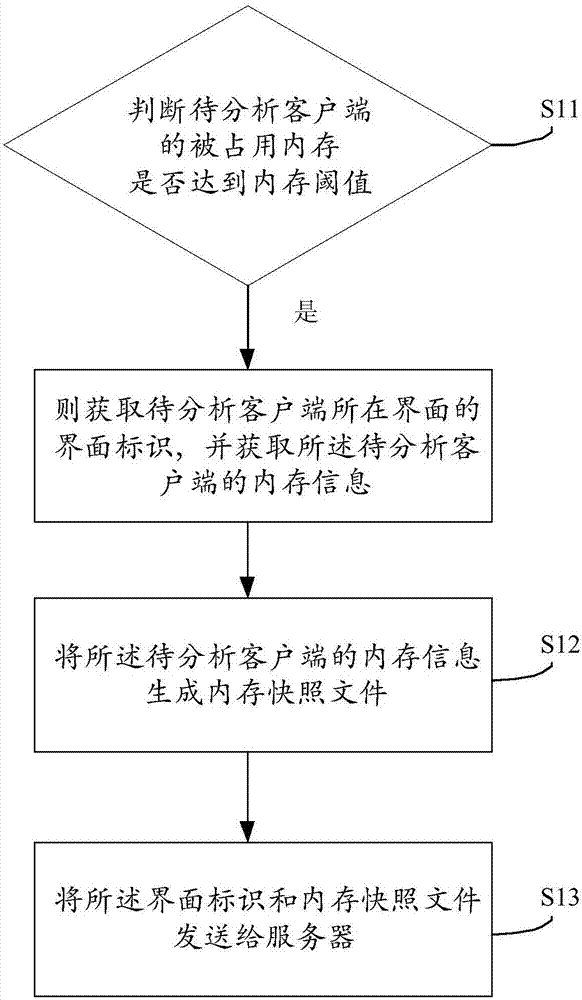
Memory analysis method, device and system for client side
The invention discloses a memory analysis method, device and system for a client side. The memory analysis method for the client side comprises the following steps that: receiving interface identification sent from a plurality of client sides to be analyzed, and memory snapshot files corresponding to the interface identification; calculating the total amount of each piece of interface identification; obtaining the interface identification of which the total amount meets a set condition to obtain interface identification to be analyzed; obtaining a to-be-analyzed interface corresponding to the interface identification to be analyzed; and analyzing the memory snapshot file corresponding to the to-be-analyzed interface to obtain memory information. By use of the method, memory problems generated in a process that the user practically uses the client side, and a corresponding interface can be obtained, and test personnel or development personnel can make a corresponding improvement on the client side.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Automated scalable and adaptive system for memory analysis via online region evolution tracking
InactiveUS20050071343A1Non-redundant fault processingSpecial data processing applicationsMemory profilingMulti method
A method for determining how a region of a data structure in an application evolves comprises the steps of: periodically traversing selected subgraphs of the region in the running application; location structural changes in the subgraphs; using these structural changes to describe, characterize, and identify changes to the region as a whole; and reporting the region changes to an analysis agent. Determining how a region of a data structure evolves is a continuous and adaptive process. The process is made continuous and adaptive through several methods, including: identifying a set of desired updates; adjusting the period in between traversals based on whether the desired updates have been witnessed; and adjusting the frequency of sampling any one traversal based on whether that traversal has detected desired updates. Additionally, the method comprises updating qualitative and quantitative characterizations of the regions under analysis based on structural changes to the regions as whole.
Owner:IBM CORP
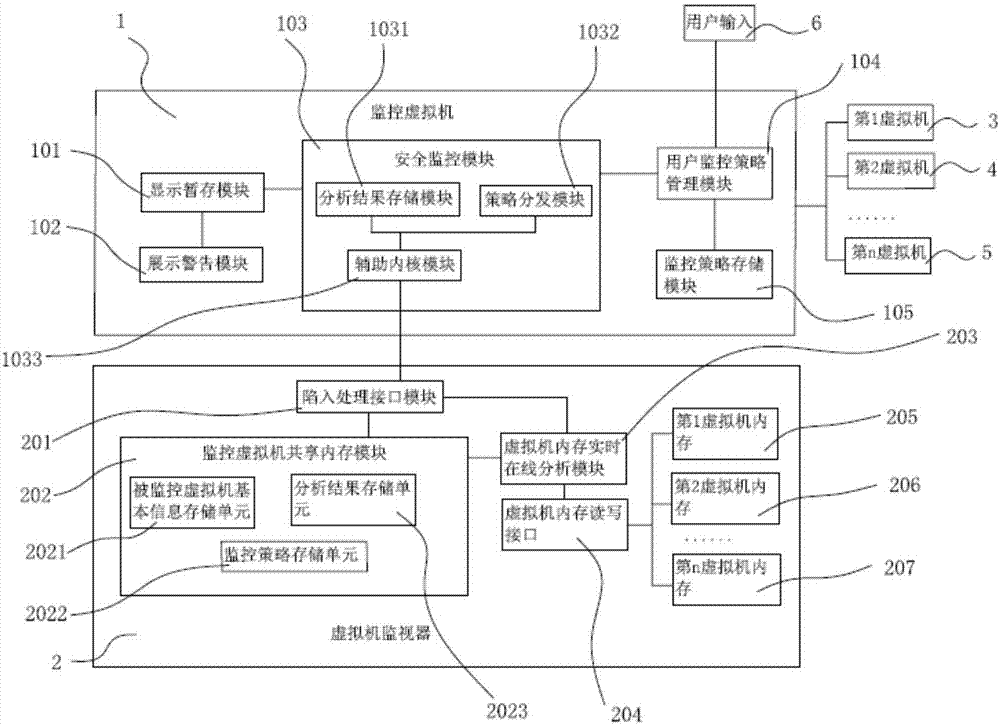
Virtual machine non-agent monitoring method and apparatus based on online memory analysis
PendingCN107357629AAvoid interferenceAvoid Switching LossHardware monitoringSoftware simulation/interpretation/emulationVirtualizationMalware
The invention belongs to the field of cloud computing server management technology, and particularly relates to a virtual machine non-agent monitoring method and apparatus based on online memory analysis. The method comprises the following steps: setting a monitoring virtual machine in a server to receive a monitoring strategy; when a monitored virtual machine is caught in a virtualization layer due to a normal exit event, executing memory analysis on the monitored virtual machine according to the monitoring strategy; and periodically reading the analysis result by the monitoring virtual machine, and performing multi-dimensional display on the user. According to the monitoring method, all security monitoring modules deployed on the virtualization layer at the outside of the virtual machine, thereby effectively avoiding all kinds of possible interference of malicious software in the virtual machine and ensuring high reliability and high security. Because no other hardware is trapped, the method does not cause redundant hardware except for normal virtualization, and avoids the frequent switch loss of a root mode and a non root mode. By virtue of the dynamics created by the virtual machine, the method can be extended very well, and the adaptability of the monitoring service is high.
Owner:成都灵跃云创科技有限公司
Just in time memory analysis for malware detection
ActiveUS20190236275A1Preventing executionInhibitory contentPlatform integrity maintainanceMemory profilingData set
Methods and apparatus consistent with the present disclosure may use instrumentation code that remains transparent to an application program that the instrumentation code has been injected into. In certain instances, data sets that include executable code may be received via packetized communications or be received via other means, such as, receiving a file from a data store. The present technique allows one or more processors executing instrumentation code to monitor actions performed by the program code included in a received data set. Malware can be detected using exception handling to track memory allocations of the program code included in the received data set.
Owner:SONICWALL
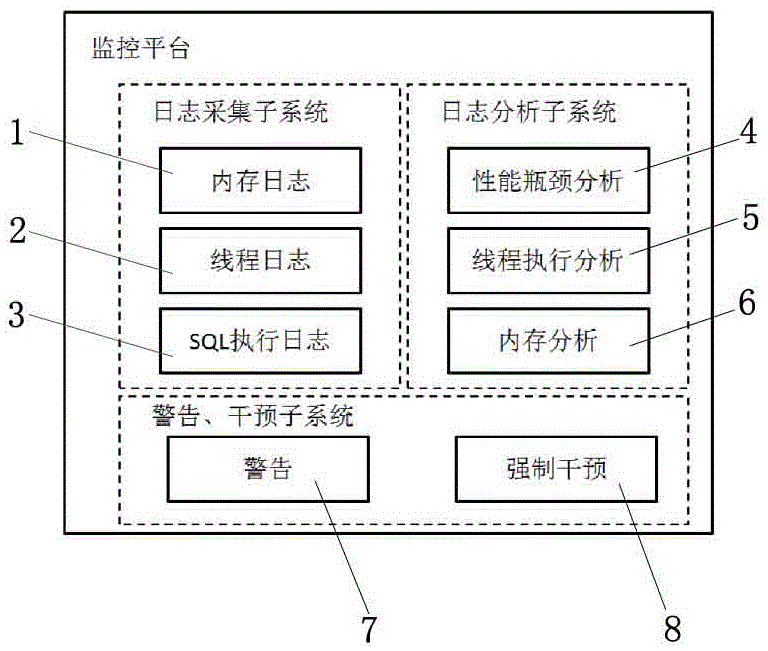
Performance monitoring platform for office management system
ActiveCN106250292AReduce the impactLittle impact on performanceHardware monitoringThird partyOffice management
The invention discloses a performance monitoring platform for an office management system. The platform comprises a log acquisition sub-system, a log analysis sub-system and a warning-intervention sub-system; the log acquisition sub-system is divided into a memory log acquisition module, a thread log acquisition module and a SQL execution log acquisition module; the log analysis sub-system comprises a performance bottleneck analysis module, a thread execution analysis module and a memory analysis module; the warning-intervention sub-system comprises a warning module and an enforcement intervention module. Through the adoption of the platform disclosed by the invention, the running generation system can be immediately analyzed without deployment and introducing the special dependency of the third-party, the analysis can be implemented only needing to use a built-in tool of jdk run on the system; meanwhile, through the development of a log analysis tool, the log can be intelligently analyzed at the permissible time to assist elimination of the reasons of the downtime problem and the performance problem, thereby accomplishing the monitoring and the acquisition of the data; the influence to the system performance is tiny, and the platform guarantees that the production system cannot be influenced by the monitoring tool.
Owner:上海泛微网络科技股份有限公司
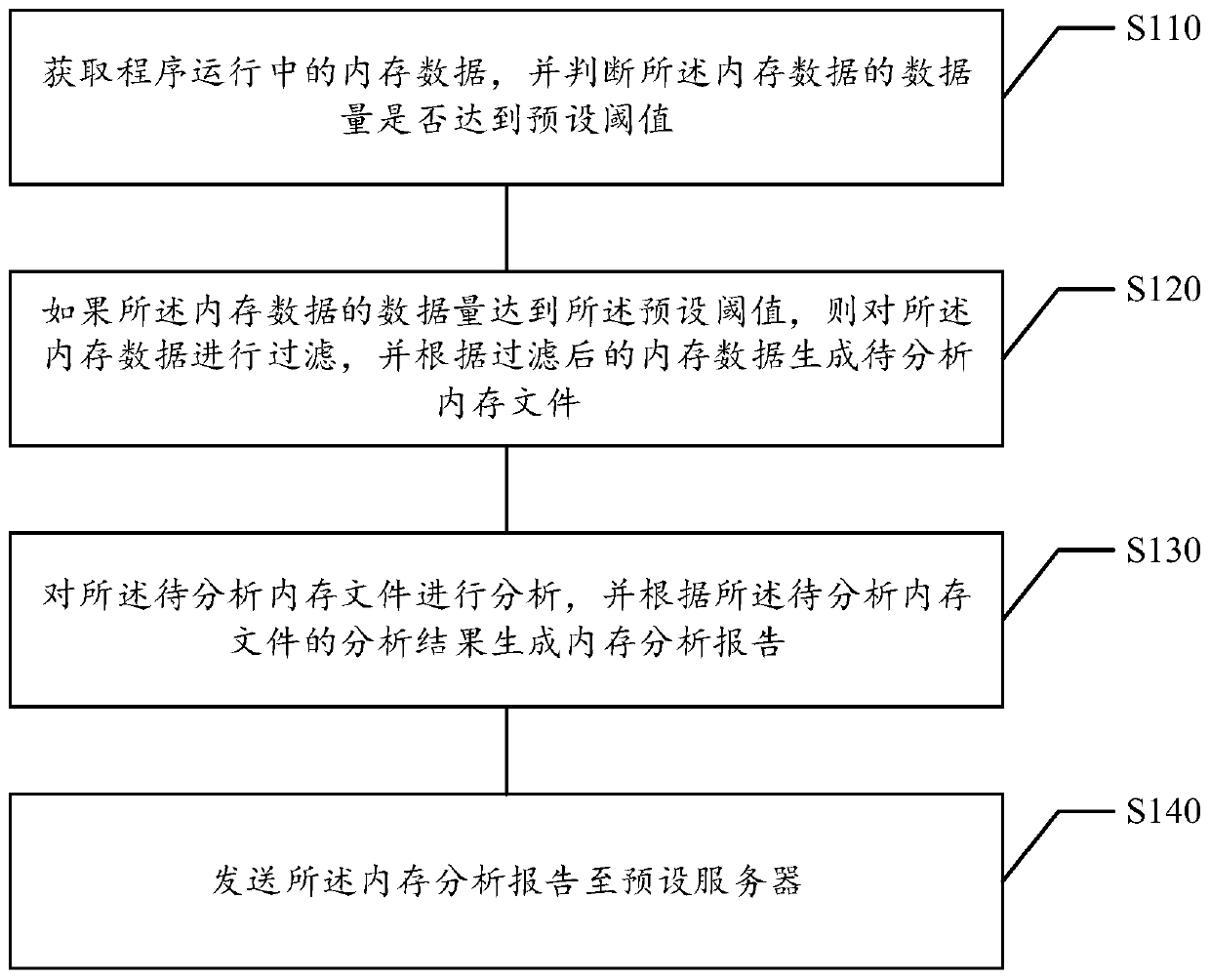
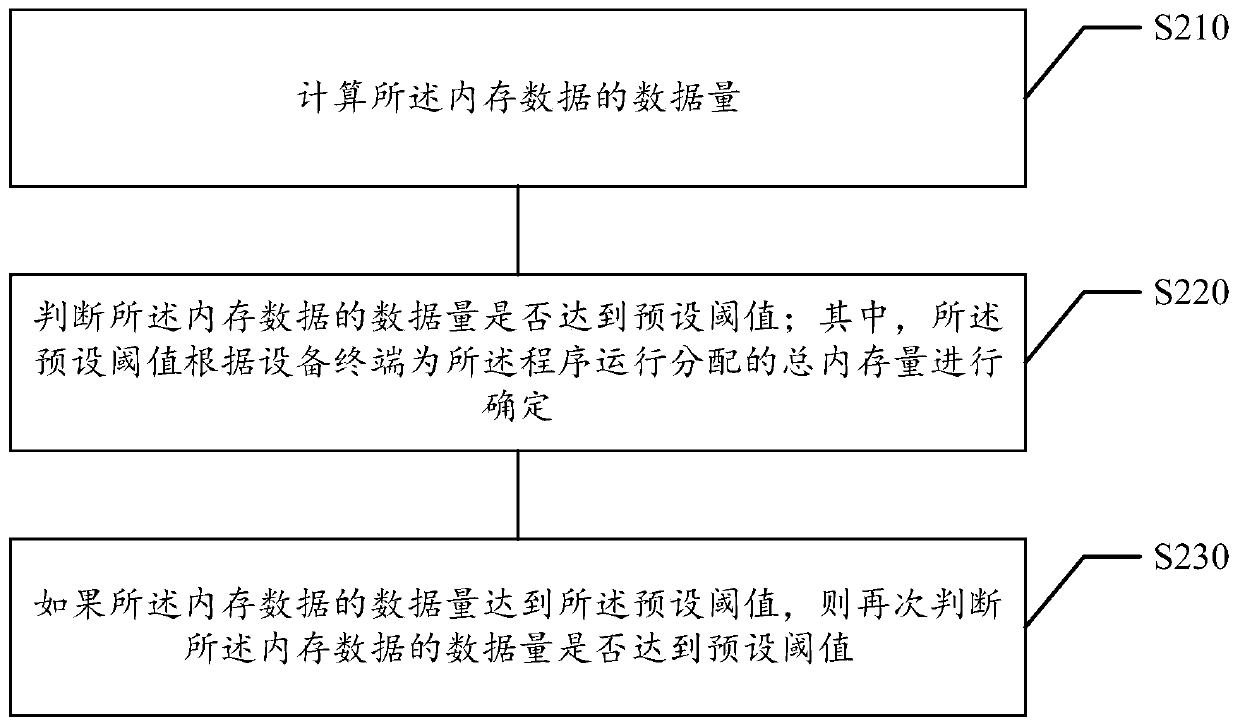
Mobile terminal memory analysis method and device, storage medium and electronic equipment
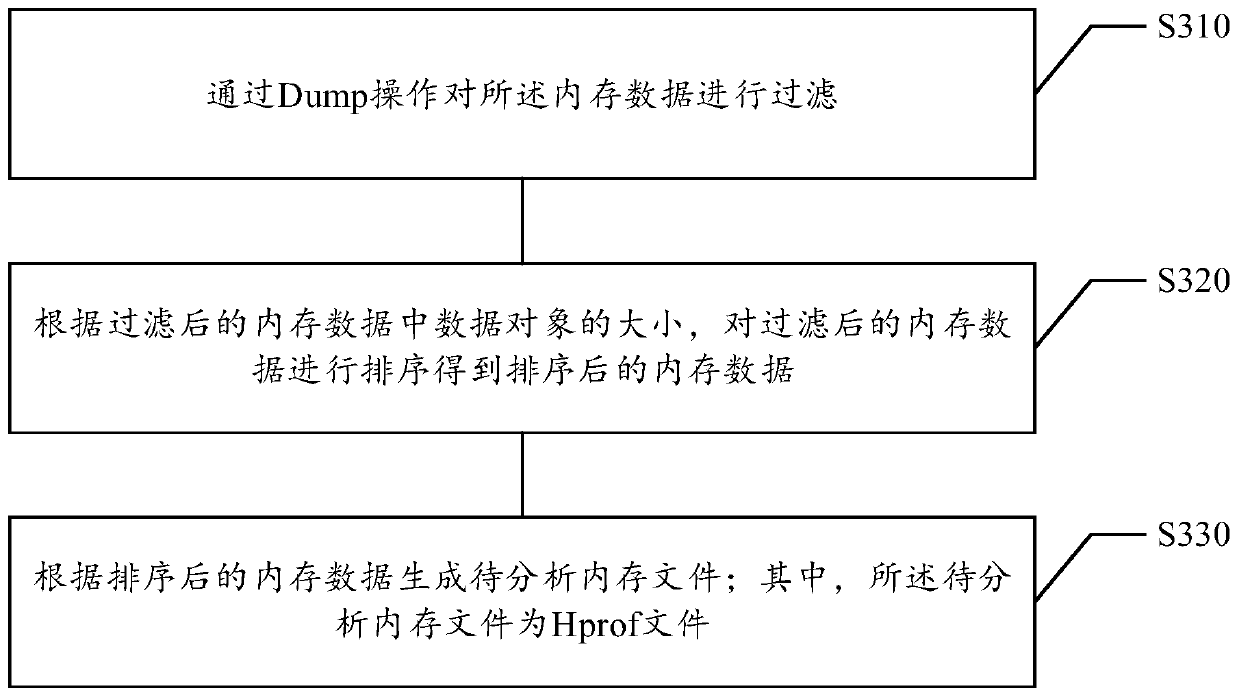
ActiveCN109828859ASolve complex problemsHigher level of problem reductionFault responseEnergy efficient computingMemory profilingAnalysis method
The embodiment of the invention relates to a mobile terminal memory analysis method and device, and belongs to the technical field of computers, and the method comprises the steps: obtaining memory data in program operation, and judging whether the data volume of the memory data reaches a preset threshold value or not; if the data size of the memory data reaches the preset threshold value, filtering the memory data, and generating a to-be-analyzed memory file according to the filtered memory data; analyzing the memory file to be analyzed, and generating a memory analysis report according to ananalysis result of the memory file to be analyzed; And sending the memory analysis report to a preset server. The method solves the problem that in the prior art, memory analysis complexity is high due to the fact that memory problems need to be reproduced, the memory analysis complexity is reduced, and meanwhile the memory analysis speed is increased.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Memory analysis method and device and computer readable storage medium
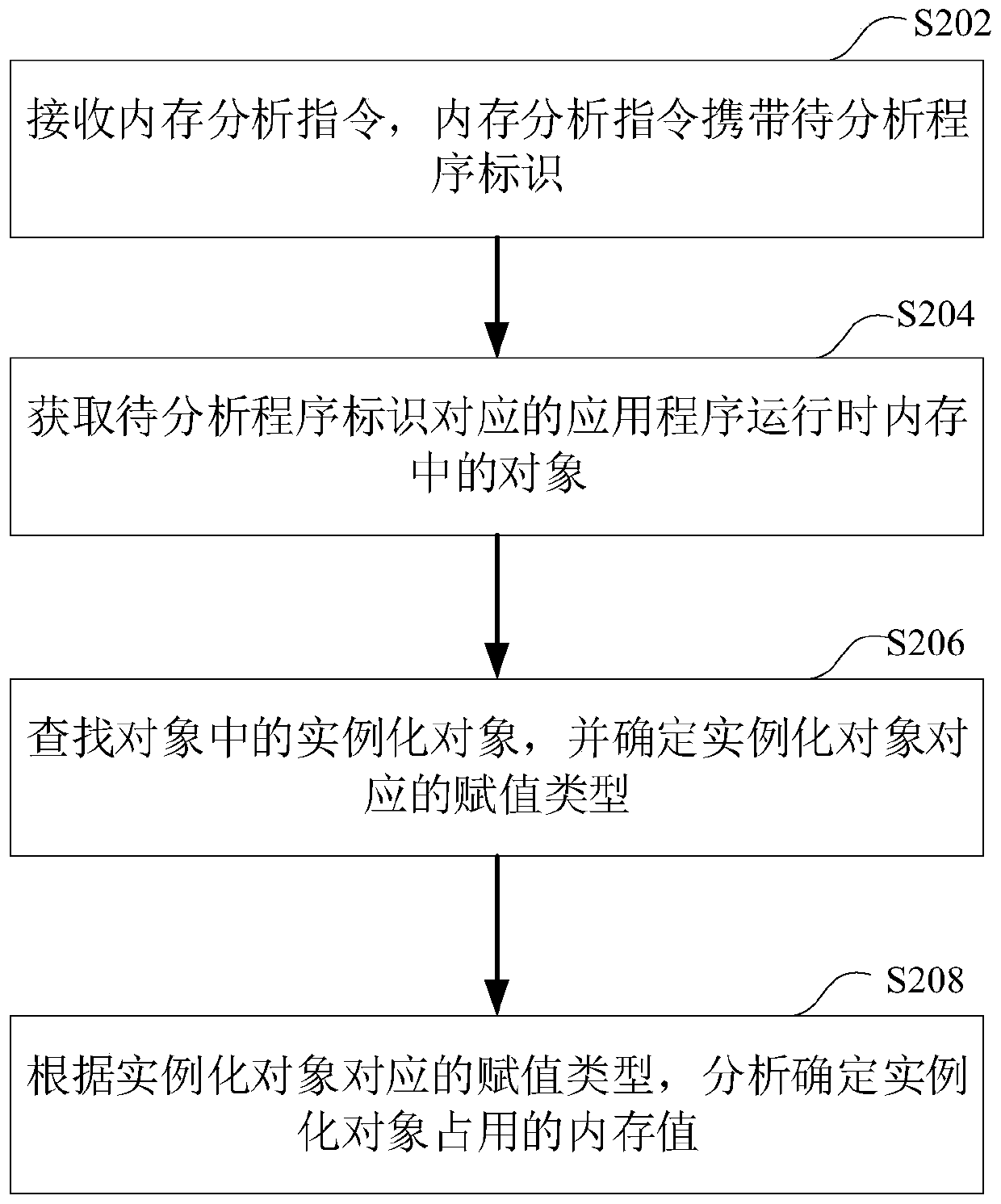
PendingCN110231994AImprove performanceResource allocationSoftware simulation/interpretation/emulationMemory profilingApplication software
The invention relates to a memory analysis method and device, a computer readable storage medium and computer equipment, and the method comprises the steps: receiving a memory analysis instruction, the memory analysis instruction carrying a to-be-analyzed program identifier; obtaining an object in a memory when the application program corresponding to the to-be-analyzed program identifier runs; searching an instantiation object in the object, and determining an assignment type corresponding to the instantiation object; and according to the assignment type corresponding to the instantiation object, analyzing and determining a memory value occupied by the instantiation object. The memory value occupied by the instantiated object can be specifically determined. The use condition of the memorycan be accurately positioned. When the application program performance is perfected, parts needing to be perfected are accurately found out directly according to the memory value occupied by an instantiated object, and the application program performance perfection efficiency is improved.
Owner:深圳市腾讯网域计算机网络有限公司
Memory overflow management method and device, electronic equipment and storage medium
PendingCN111984401AAccurate detectionShorten the timeResource allocationNon-redundant fault processingVirtual memoryData pack
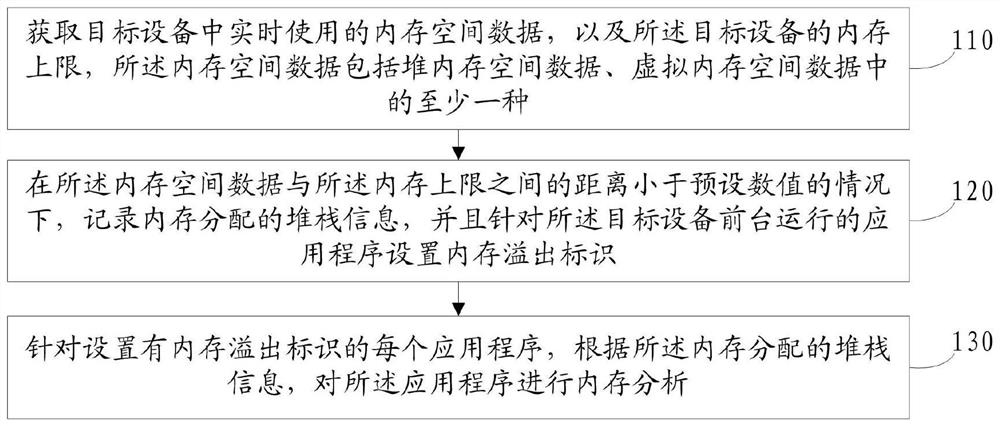
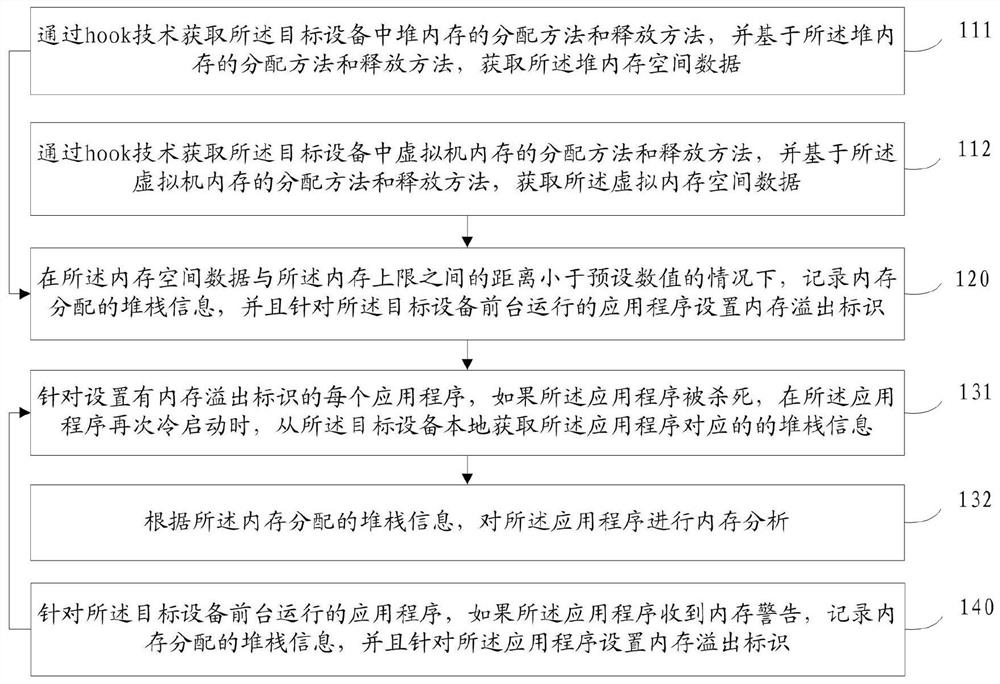
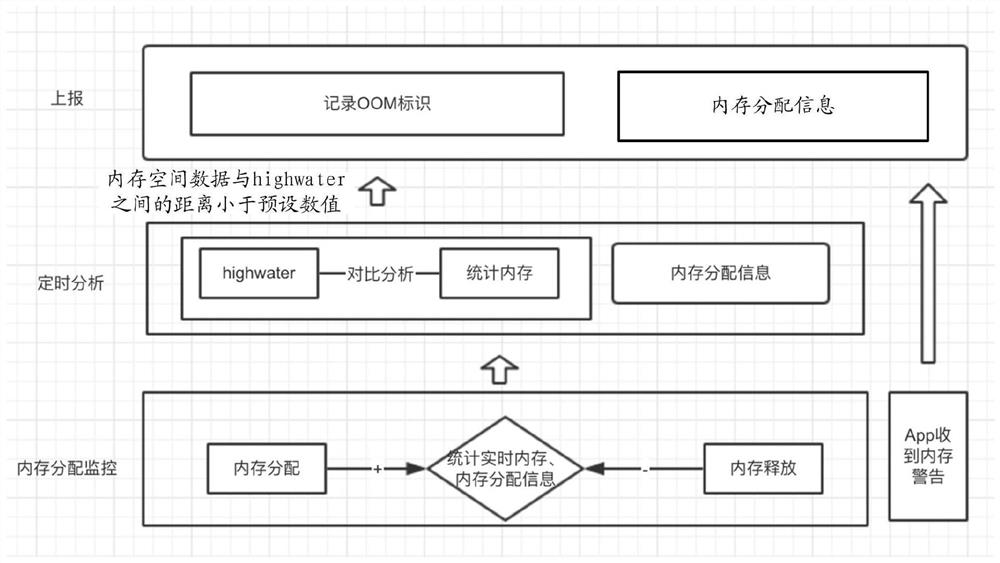
The invention provides a memory overflow management method and device, electronic equipment and a storage medium. The method comprises the steps of acquiring memory space data used in target equipmentin real time and a memory upper limit of the target equipment, wherein the memory space data comprise at least one of heap memory space data and virtual memory space data; under the condition that the distance between the memory space data and the memory upper limit is smaller than a preset numerical value, recording stack information of memory allocation, and setting a memory overflow identifierfor an application program running in the foreground of the target equipment; and for each application program provided with the memory overflow identifier, performing memory analysis on the application program according to the stack information allocated by the memory. Therefore, the memory does not need to be analyzed manually in the development stage, the problem positioning time in demand development is saved, meanwhile, the development time is saved, and the development efficiency is improved. And the problem that the system kills the App due to the OOM can be accurately detected.
Owner:WUBA
Malicious software detection method and system based on memory analysis
PendingCN110837641AReduce performance loadImprove training accuracyPlatform integrity maintainanceMemory profilingOperational system
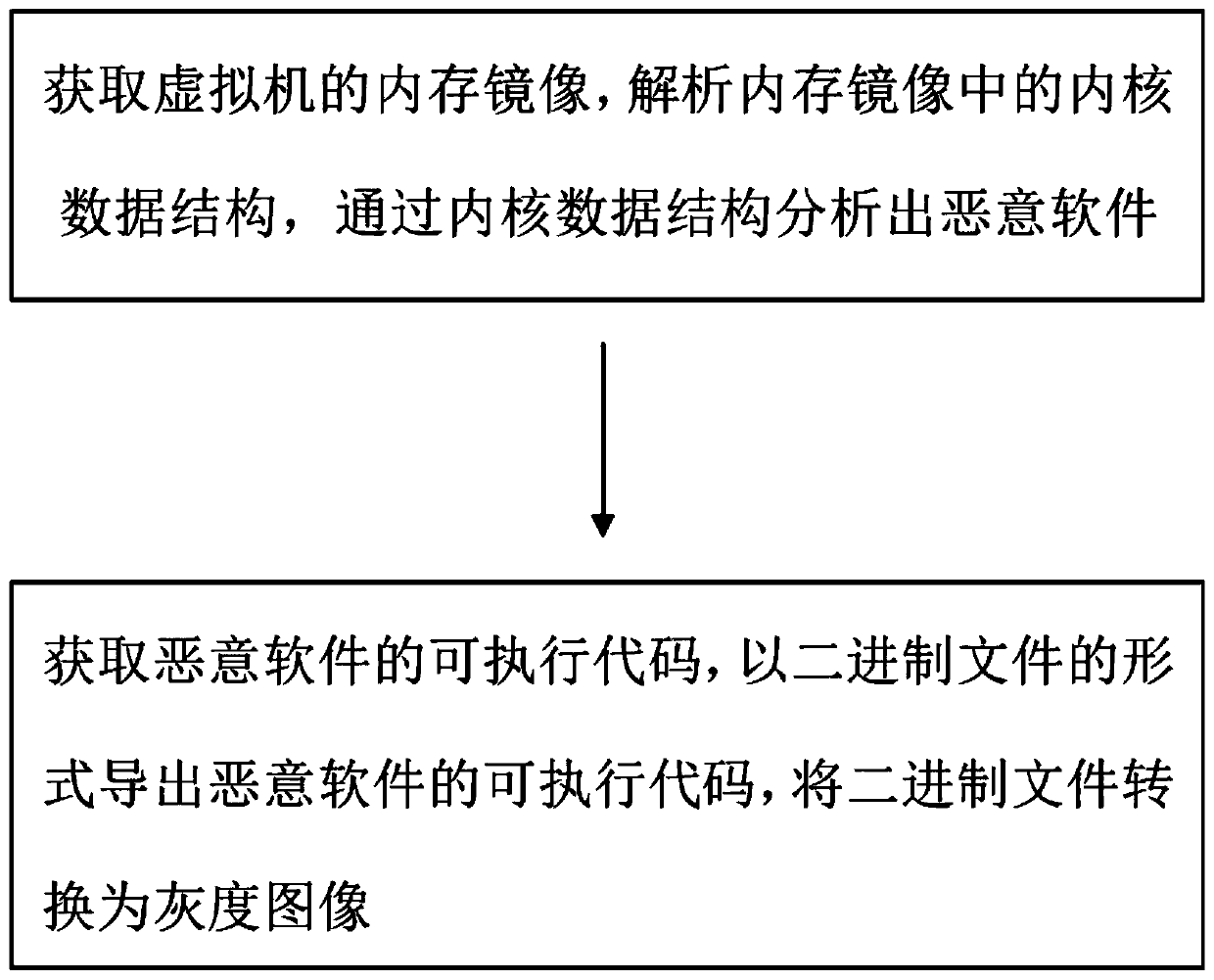
The invention belongs to the technical field of computer security, and particularly relates to a malicious software detection method based on memory analysis. The method comprises the steps of obtaining a memory mirror image of a virtual machine, analyzing a kernel data structure in the memory mirror image, analyzing malicious software through the kernel data structure, obtaining an executable code of the malicious software, exporting the executable code of the malicious software in a binary file mode, and converting the binary file into a gray level image. The malicious software detection security is high, the method and system are suitable for detecting various types of malicious software and operating in different operating system versions, and the detection universality and portabilityare greatly improved. In addition, the invention further provides a malicious software detection system based on memory analysis.
Owner:INST OF ELECTRONICS & INFORMATION ENG OF UESTC IN GUANGDONG +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com