SSL/TLS network encryption communication information real-time decryption method based on memory analysis
An encrypted communication and memory analysis technology, which is applied in the field of real-time decryption of SSL/TLS network encrypted communication information based on memory analysis, can solve problems such as undetectable, and achieve the effects of improving efficiency and accuracy, ensuring accuracy, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
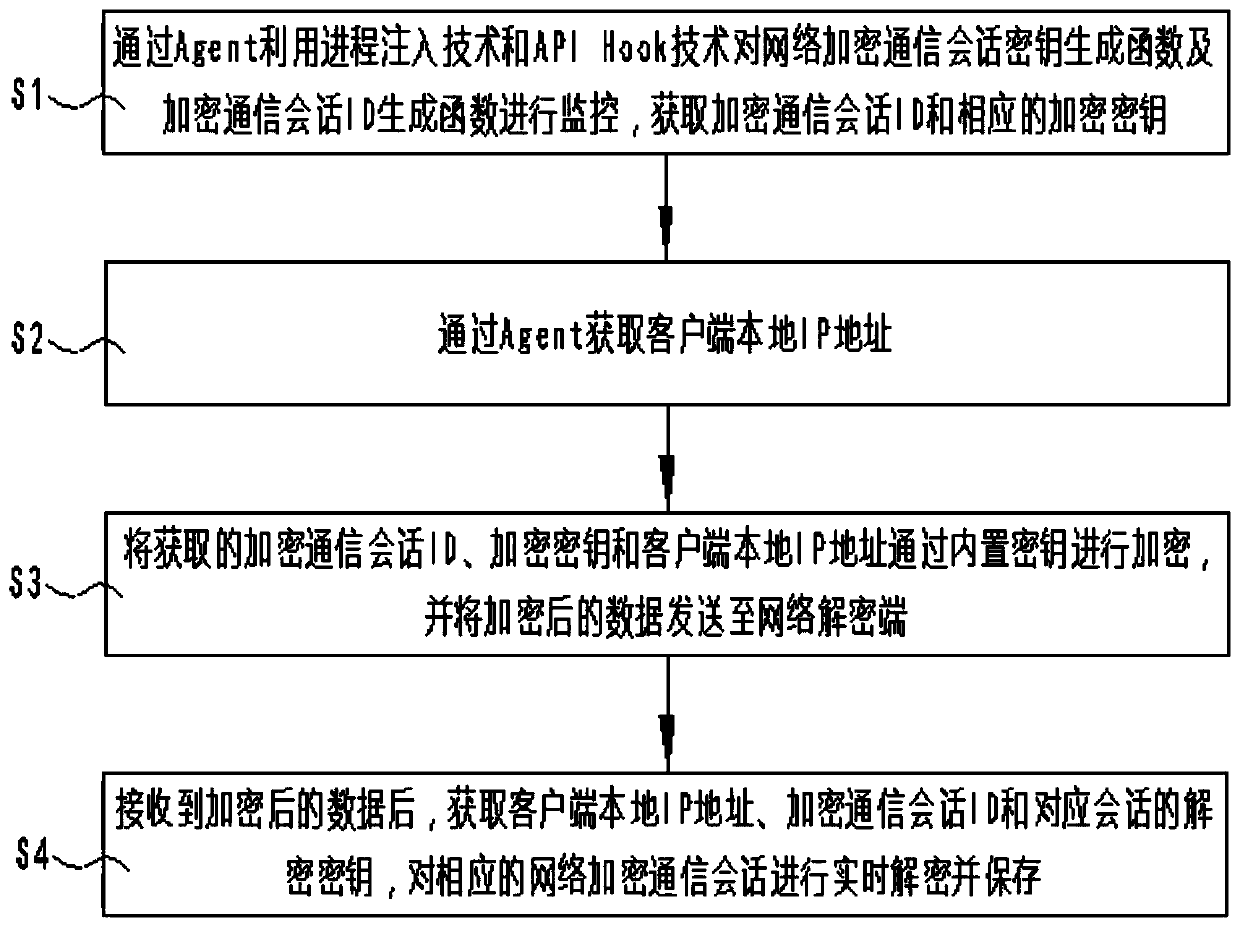
[0054] like figure 1 As shown, a real-time decryption method for SSL / TLS network encrypted communication information based on memory analysis, comprising the following steps:
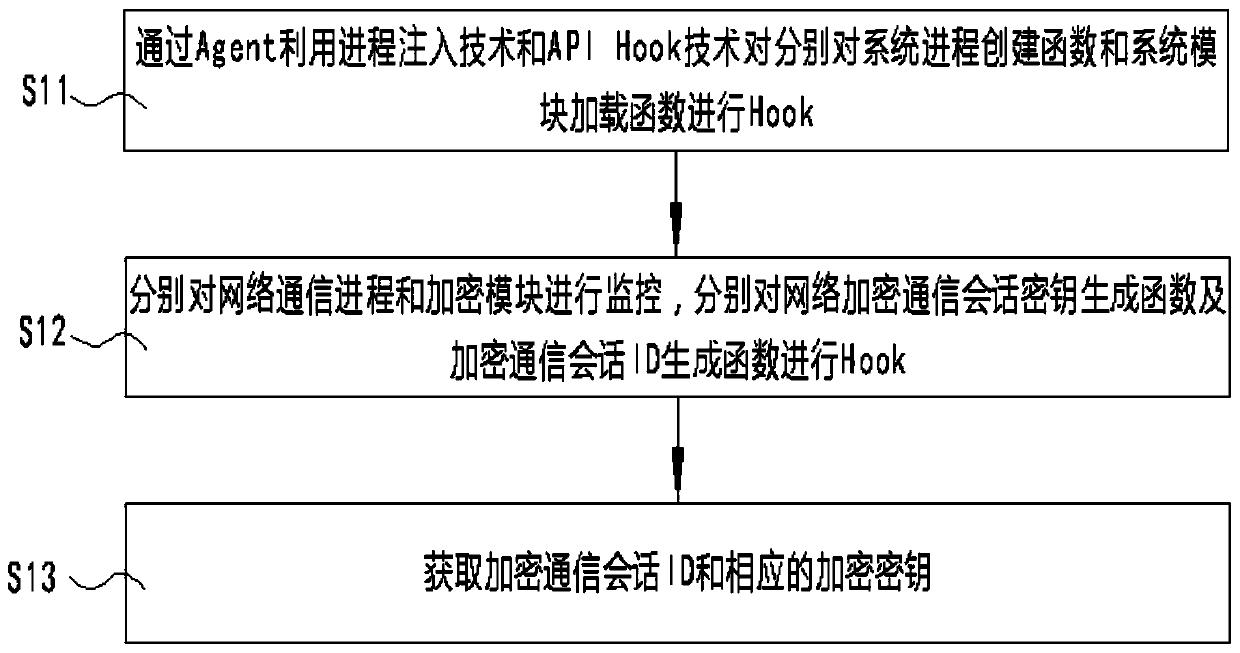
[0055] S1. Monitor the network encrypted communication session key generation function and the encrypted communication session ID generation function through the Agent using process injection technology and API Hook technology, and obtain the encrypted communication session ID and the corresponding encryption key;
[0056] S2. Obtain the local IP address of the client through the Agent;
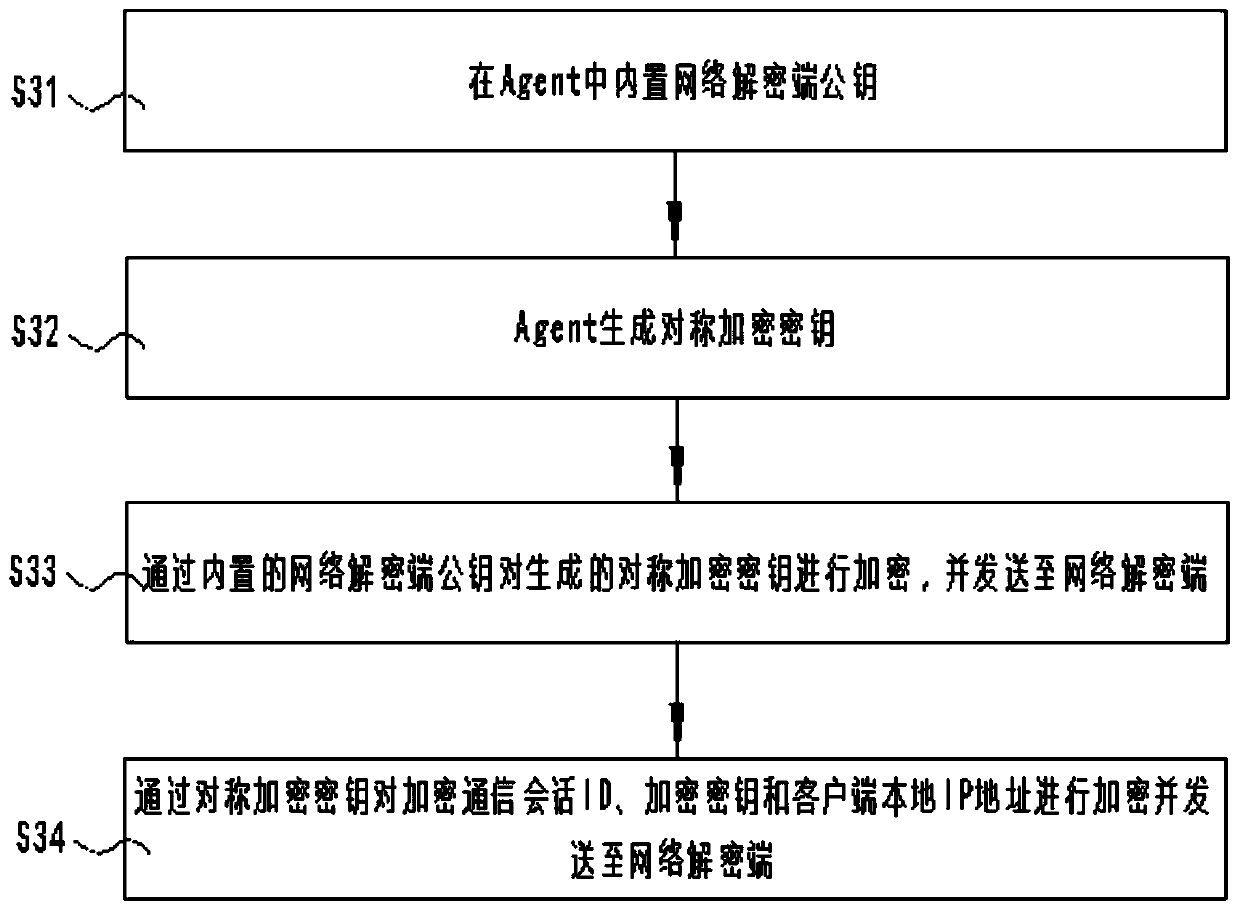
[0057] S3. Encrypt the acquired encrypted communication session ID, network encrypted communication session key and local IP address of the client with a temporarily generated symmetric encryption key, and send the encrypted data to the network decryption terminal;
[0058] S4. After receiving the encrypted data, obtain the local IP address of the client, the encrypted communication session ID and the decryption key o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com