Method and system for running encryption program in Flash in XIP mode
A program and block encryption technology, applied in the field of computer science, can solve problems such as redundant clock cycles and low execution efficiency, and achieve the effects of improving security, preventing active attacks, and improving execution efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] This embodiment proposes a method for encrypting programs in the XIP mode to run Flash, such as figure 1 As shown, the method includes the following steps:
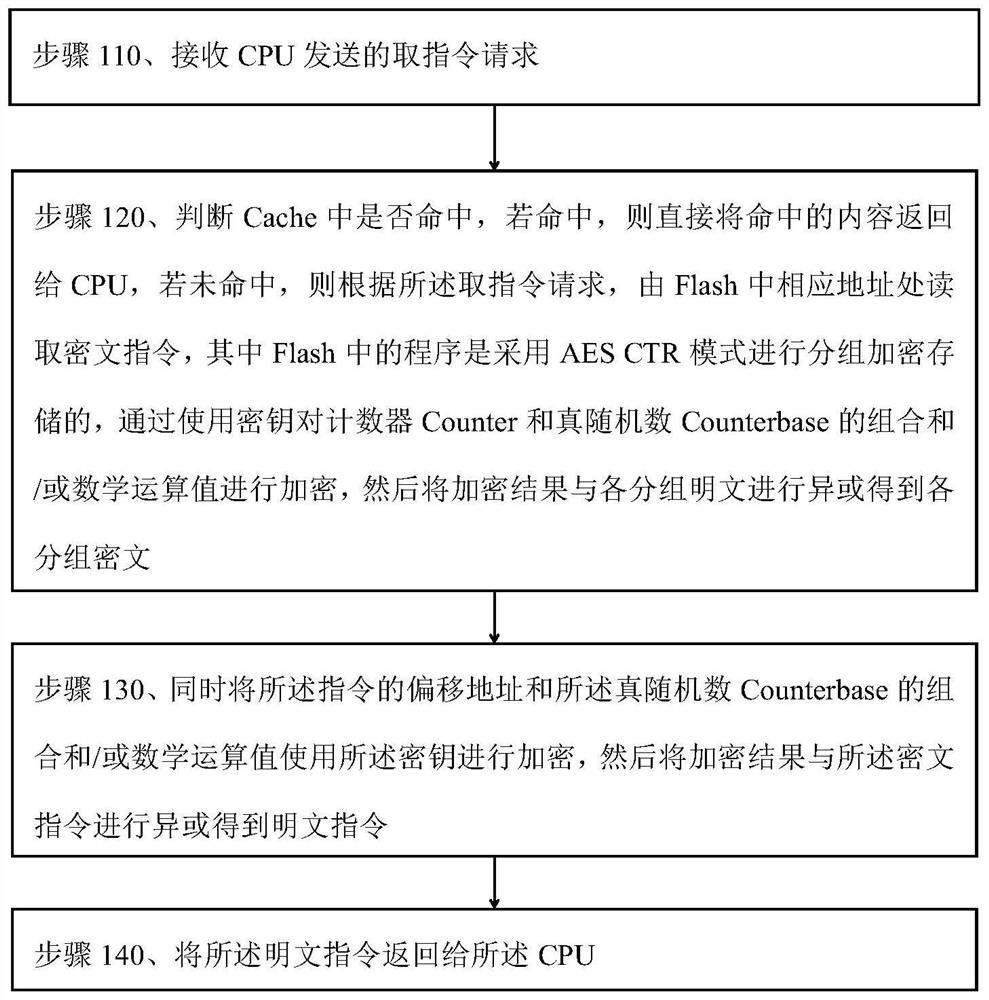
[0034] Step 110, receiving an instruction fetch request sent by the CPU.
[0035] Generally, a cache miss will consume more time. When a cache miss occurs, the CPU fetches instructions in XIP mode.
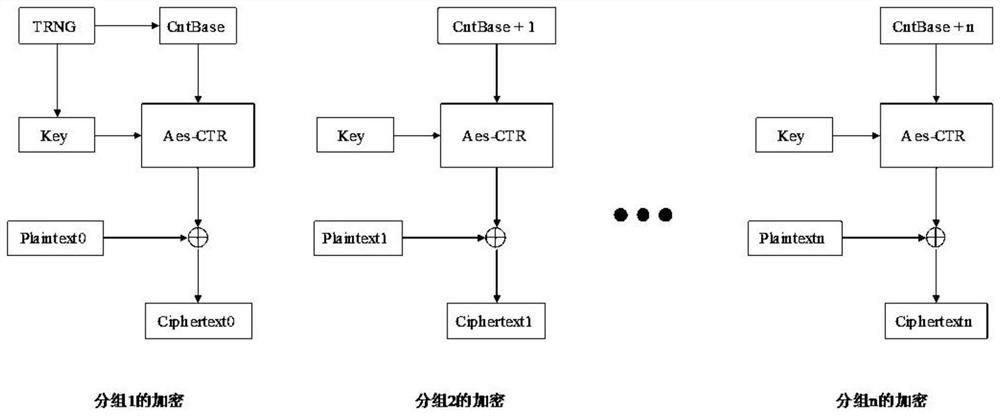
[0036] Step 120, judge whether hit in the Cache, if hit, then directly return the content of hit to CPU, if not hit, then according to the instruction fetch request, read the ciphertext instruction by corresponding address place in Flash, wherein The program is encrypted and stored in AES CTR mode, by using the key to encrypt the combination of the counter Counter and the true random number Counterbase and / or the mathematical operation value, and then XOR the encryption result with the plaintext of each group to obtain the encryption of each group arts.
[0037] Further, the method also includes: before the program ...
Embodiment 2
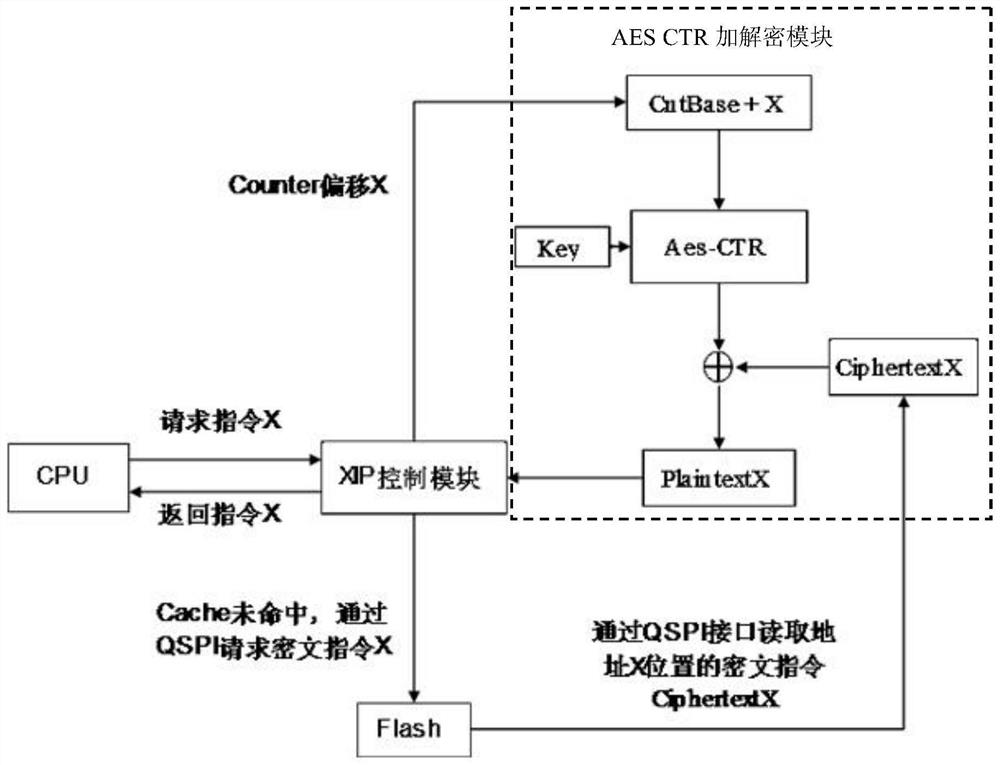
[0046] Corresponding to above-mentioned embodiment 1, present embodiment proposes a kind of system that XIP mode runs encryption program in Flash, described system comprises CPU, XIP control module and AES CTR encryption and decryption module;
[0047] The CPU is used to send an instruction fetch request to the XIP control module;
[0048] The XIP control module is used to receive an instruction fetch request sent by the CPU;
[0049] Judging whether there is a hit in the Cache, if it is a hit, then directly return the content of the hit to the CPU, if it is not a hit, then according to the instruction fetch request, the ciphertext instruction is read from the corresponding address in the Flash, wherein the program in the Flash uses For group encrypted storage in AESCTR mode, the combination of the counter Counter and the true random number Counterbase and / or the mathematical operation value are encrypted by using a key, and then the encrypted result is XORed with the plaintex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com