Method for adding secure address book, information communication method and calling method and system
A technology of security information and communication methods, applied in the field of mobile communication and communication, can solve complex, simple, and unsuitable problems for ordinary users, and achieve the effect of ensuring security and protecting information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0113] In order to describe the technical content of the present invention more clearly, further description will be given below in conjunction with specific embodiments.
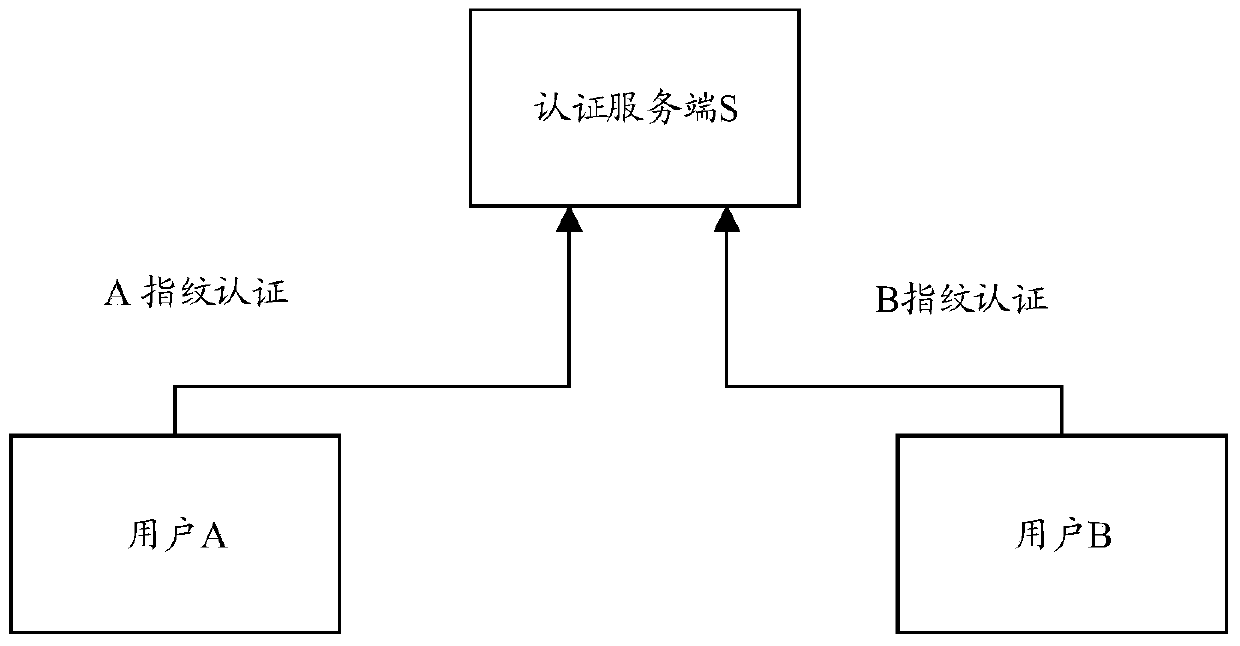
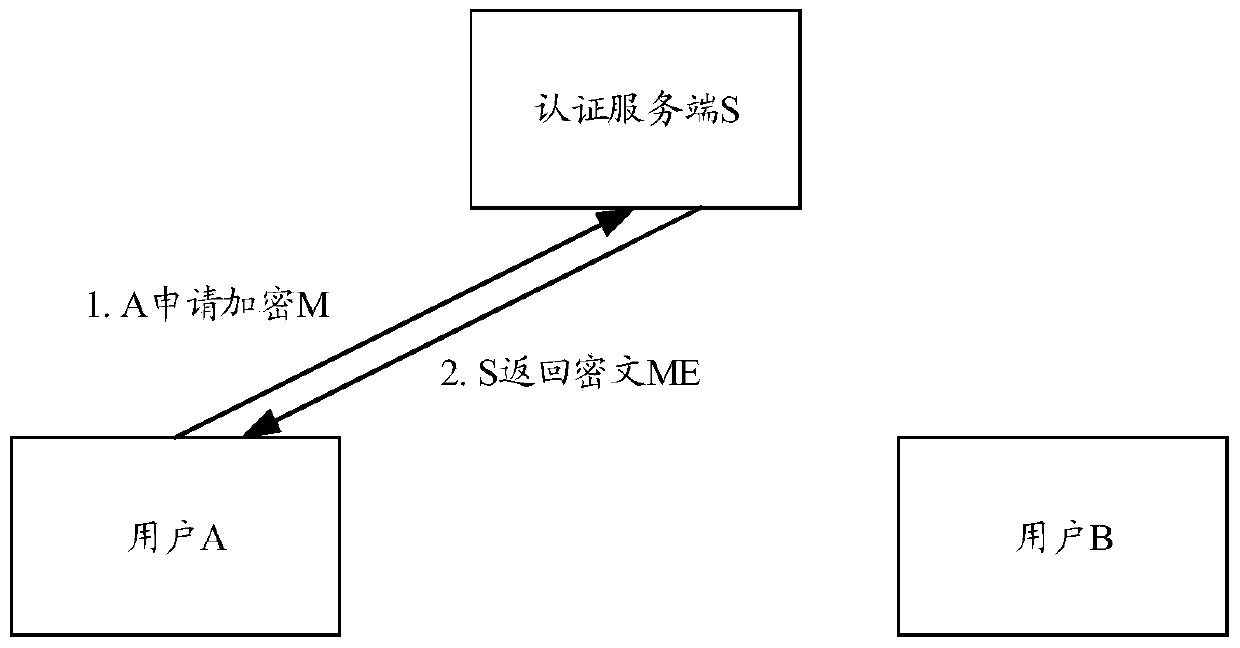
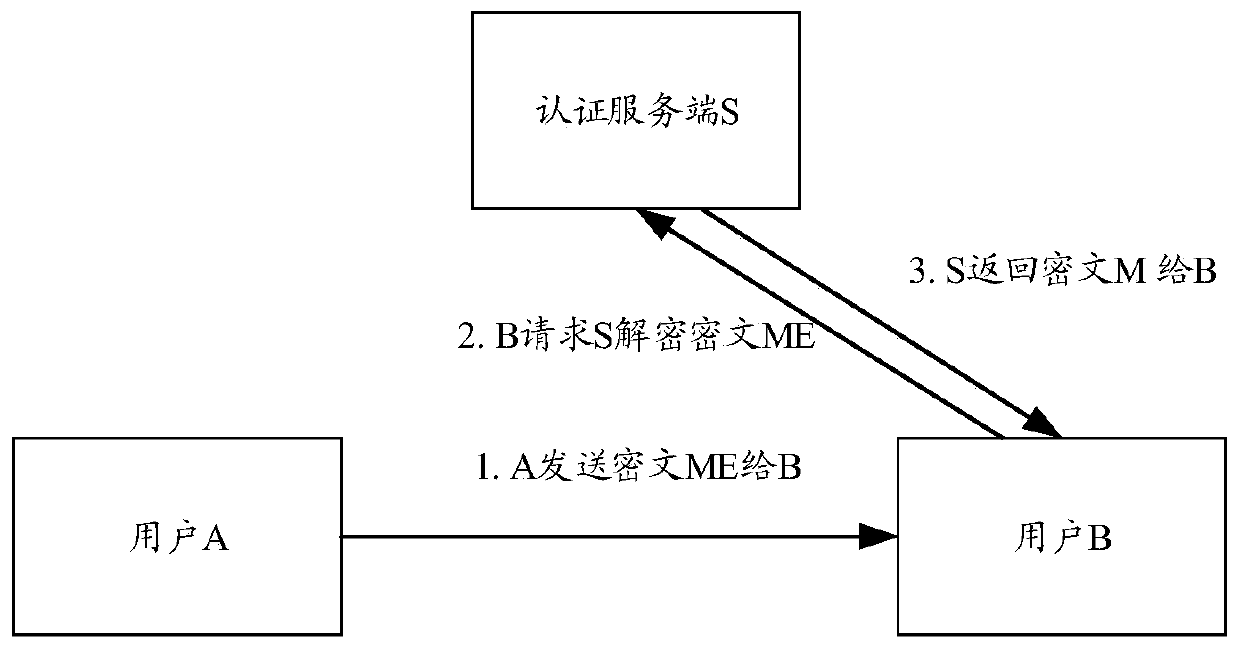
[0114] The user population targeted by the technical solution of the present invention: ordinary users, who only need to protect the content of short messages from being peeped or intercepted, and the phone from being answered and eavesdropped at will; (such as the communication content of so-and-so and her confidante);
[0115] There is no need for strong encryption or confidentiality performance, if it is layered according to the security level: top secret, confidential, secret; only need to ensure that the secret is below. The content that usually needs to be kept secret is usually not related to state secret information, but involves life information, such as personal ID card information, personal bank card number, private voice, etc. It is not expected to be leaked, but the security level is not very hi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com