Malicious software detection method and system based on memory analysis
A malicious software and memory analysis technology, applied in the field of computer security, can solve problems such as virtual machine unavailability, detection tool detection, destruction, etc., to achieve high versatility and portability, high security, and reduce performance load.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
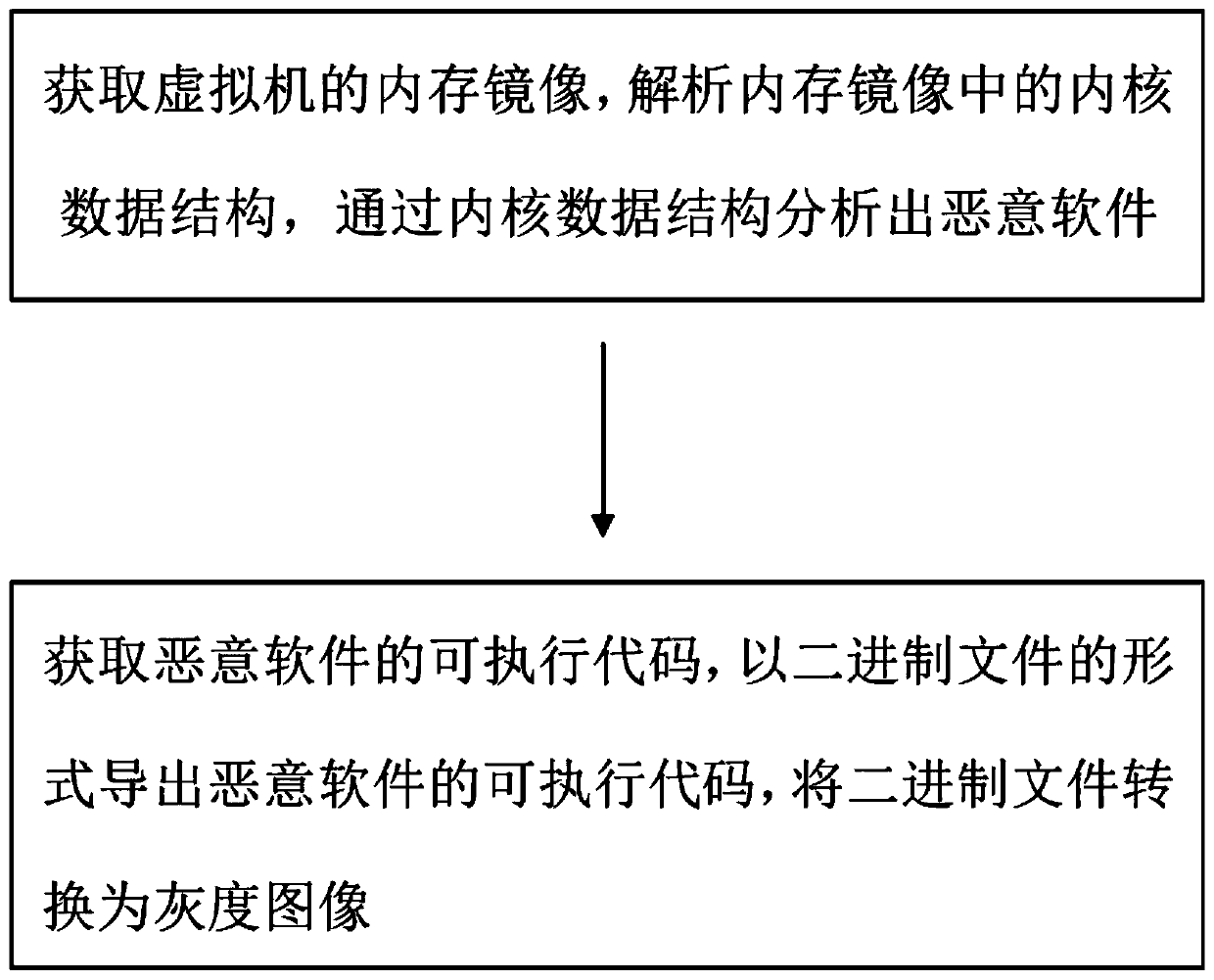
[0032] Such as figure 1 As shown, a malware detection method based on memory analysis, including:
[0033] Step 1: Obtain the memory image of the virtual machine, analyze the kernel data structure in the memory image, and analyze the malware through the kernel data structure;
[0034] Among them, the process of obtaining the memory image of the virtual machine includes: the host submits malware samples to the Cuckoo sandbox; the Cuckoo sandbox restores the operation of the VirtualBox virtual machine through the pre-generated normal memory snapshot; the Cuckoo sandbox uploads the malware samples to the VirtualBox virtual machine. Inside the machine, run malware samples, and generate memory images inside the VirtualBox virtual machine, thereby automatically obtaining a large number of memory images during the running of malware, and realizing the collection of convolutional neural network model training samples.
[0035] Step 2: Obtain the executable code of the malware, export...
Embodiment 2
[0054] A malware detection system based on memory analysis, including:
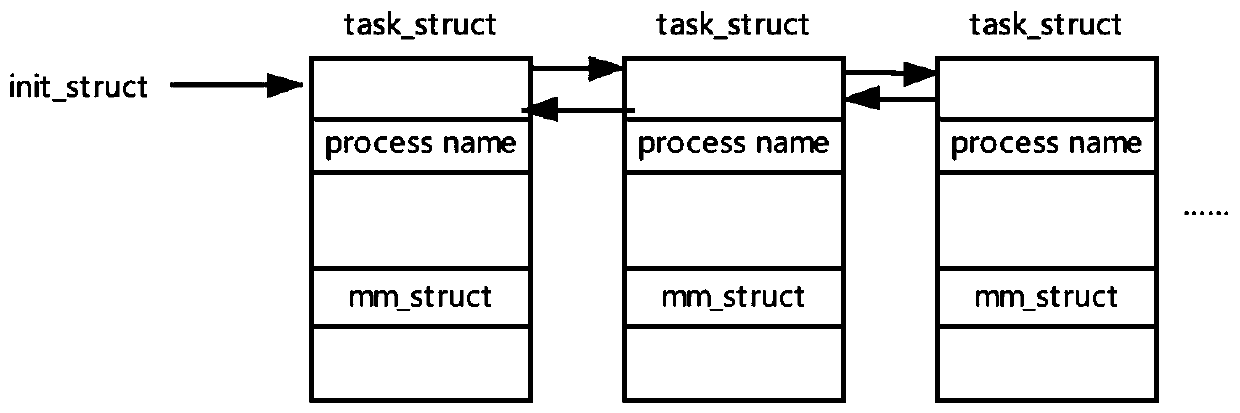
[0055] The acquisition module is used to obtain the memory image of the virtual machine, parse the kernel data structure in the memory image, obtain the process name information and process memory mapping space information residing in the memory image, match the process name information and the malware sample name, and obtain malicious The process of the software, analyze the memory mapping space information of the process, obtain the executable code of the malware, export the executable code of the malware in the form of a binary file, and convert the binary file into a grayscale image;
[0056] The training module is used to receive the grayscale image, and transmit the grayscale image to the convolutional neural network for model training. After the available convolutional neural network model is generated, the convolutional neural network model can be transmitted to the monitoring module, so that the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com