Identification method and system of malicious sample type on the basis of characteristics
A type identification and sample technology, applied in the field of information security, can solve problems such as no specific classification of samples, no horizontal correlation, single data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0028] This embodiment is an embodiment of a method for identifying malicious sample types based on characteristics.
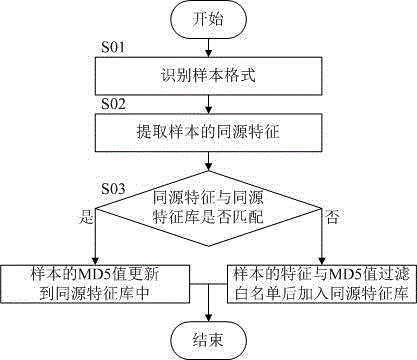
[0029] The method for identifying the type of malicious samples based on characteristics of this embodiment, the flowchart is as follows: figure 1 Shown. The method includes the following steps:
[0030] S01. Identify sample format, identify PE sample, OFFICE document sample or EML mail sample;
[0031] S02: Extract the homologous features of the sample;
[0032] S03: Compare the homology feature with the homology feature library, if:
[0033] Feature matching, update the MD5 value of the sample to the homology feature library;
[0034] If the feature does not match, the feature of the sample and the MD5 value are filtered and whitelisted and added to the same-origin feature database.
[0035] The above-mentioned method for identifying the type of malicious samples based on features illustrates the case of feature matching in step S03.
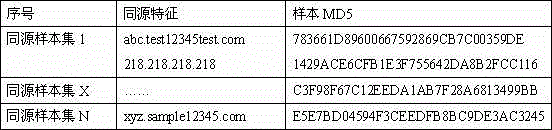
[0036] The homology signature data...
specific Embodiment 2
[0046] This embodiment is an embodiment of a system for identifying malicious sample types based on characteristics.
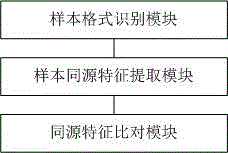
[0047] The feature-based malicious sample type identification system of this embodiment, such as figure 2 Shown. The system includes the following modules:
[0048] Sample format identification module: used to identify sample format, identify PE sample, OFFICE document sample or EML mail sample;
[0049] Sample homology feature extraction module: used to extract the homology feature of the sample;
[0050] Homologous feature comparison module: Compare the homologous feature with the homologous feature library, if:
[0051] Feature matching, update the MD5 value of the sample to the homology feature library;
[0052] If the feature does not match, the feature of the sample and the MD5 value are filtered and whitelisted and added to the same-origin feature database.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com