Dynamic shelling method for Android application
An application program and dynamic technology, applied in the field of Android applications, can solve the problems of program unpacking and repairing restrictions, difficult Android program unpacking and repairing, etc., and achieve the effect of security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
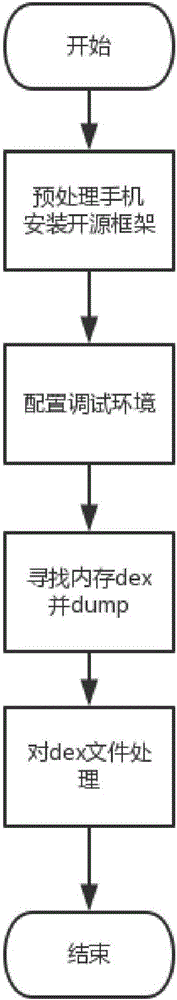
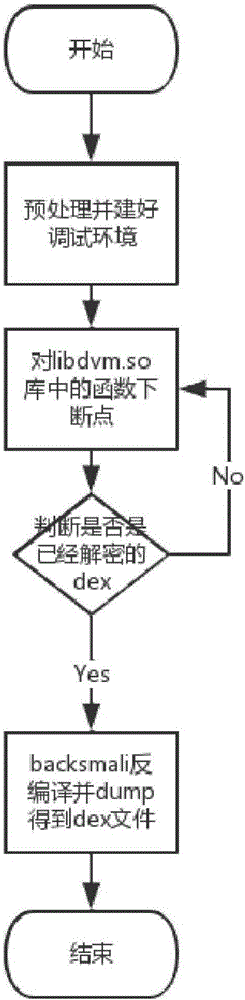
[0031] The invention provides a shelling and repairing method based on the dynamic framework of the Android system, so that the Android program after reinforcement can be shelled and repaired. In addition, it is necessary to ensure that the semantics of the repackaged program does not change after unpacking, and does not affect the normal execution of the program.
[0032] On the Android platform, due to the immature dex packing technology, it is possible to directly dump the source program without analyzing the algorithm of the source program. The Xposed framework is a framework service that can affect the running of the program without modifying the Android installation package (APK). The basic principle is to affect the running of the program by modifying the system. The open source tool ZjDroid ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com