Patents
Literature
403results about How to "Safety protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
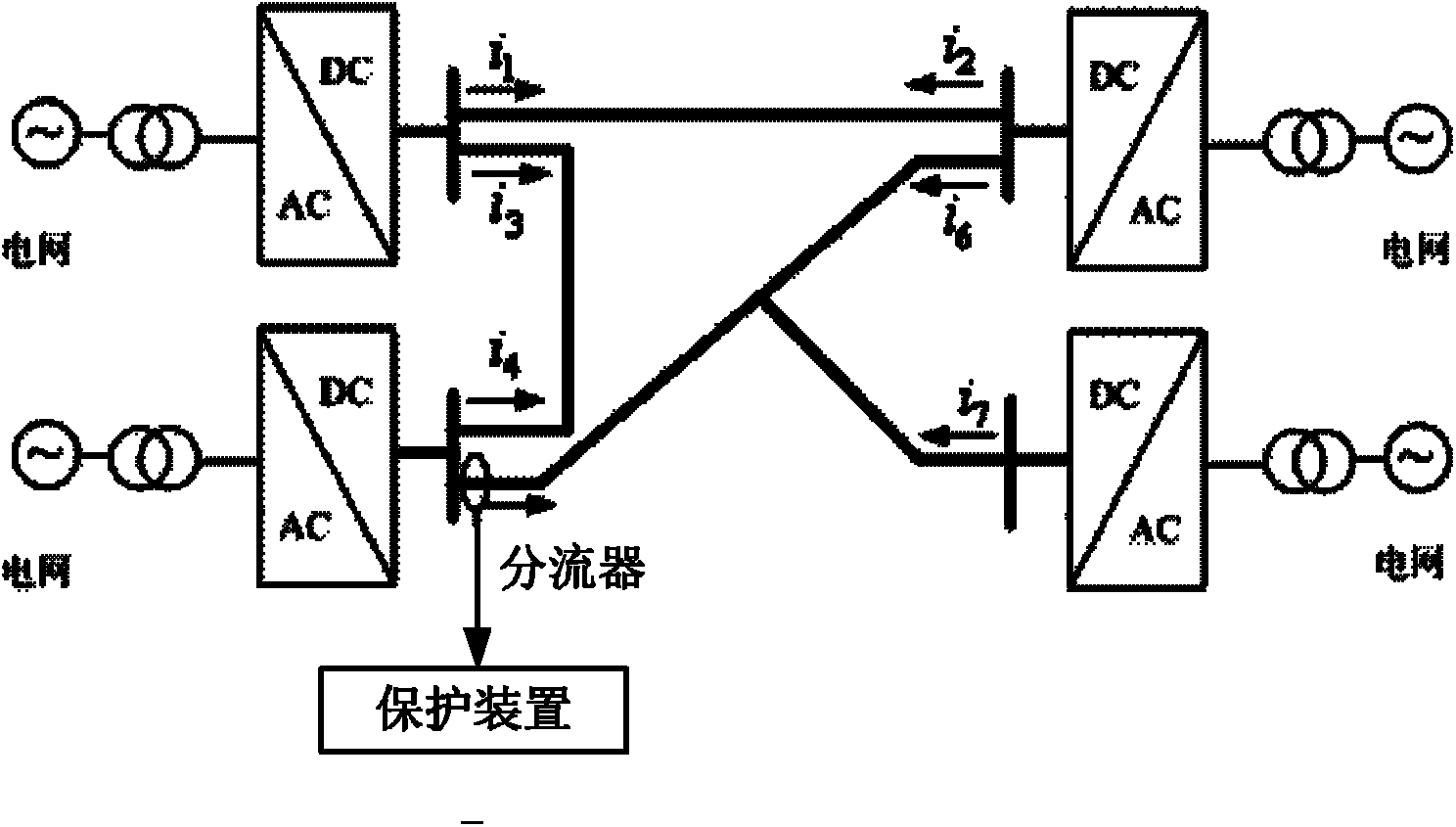
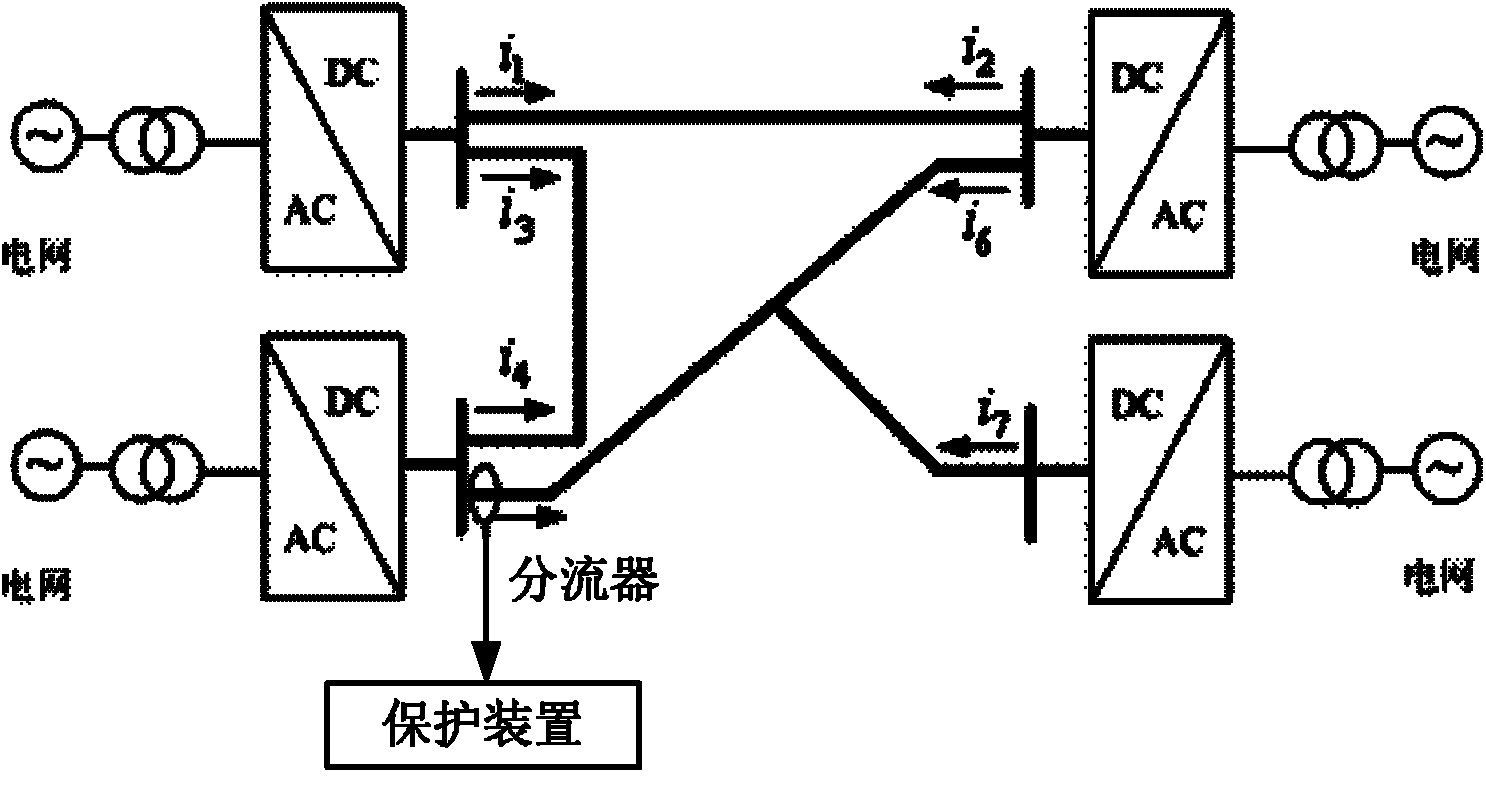
Pilot protection method for direct current line current abrupt change of multi-terminal direct current transmission system
InactiveCN102510050AReduce trafficDownsamplingEmergency protective circuit arrangementsTransient statePower flow
The invention provides a pilot protection method for the direct current line current abrupt change of a multi-terminal direct current transmission system. The method comprises the following steps of: 1, acquiring fault transient state current amperage; 2, calculating the current abrupt change in one period of time by using the acquired fault transient state current amperage, comparing the current abrupt change with a setting value according to the value of the current abrupt change and judging the direction of faults; and 3, distinguishing inside-area and outside-area faults by the cooperation of the current abrupt change directional elements at the terminals of a line; and if the directional element at each terminal is judged to have a forward directional fault, the fault is judged as the inside-area fault, and if at least one directional element is judged to have a reverse directional fault, the fault is judged as the outside-area fault. The method has the advantages that only current data is used, the required sampling rate is low, the current abrupt change is easy to calculate, the communication amount is small, and line faults can be rapidly detected; all energy information but a high frequency signal in a fault transient state is used, the signal energy is strong, and the protection is safety and reliable; and the method is applied to a parallel, a serial and a hybrid multi-terminal direct current system.
Owner:XI AN JIAOTONG UNIV
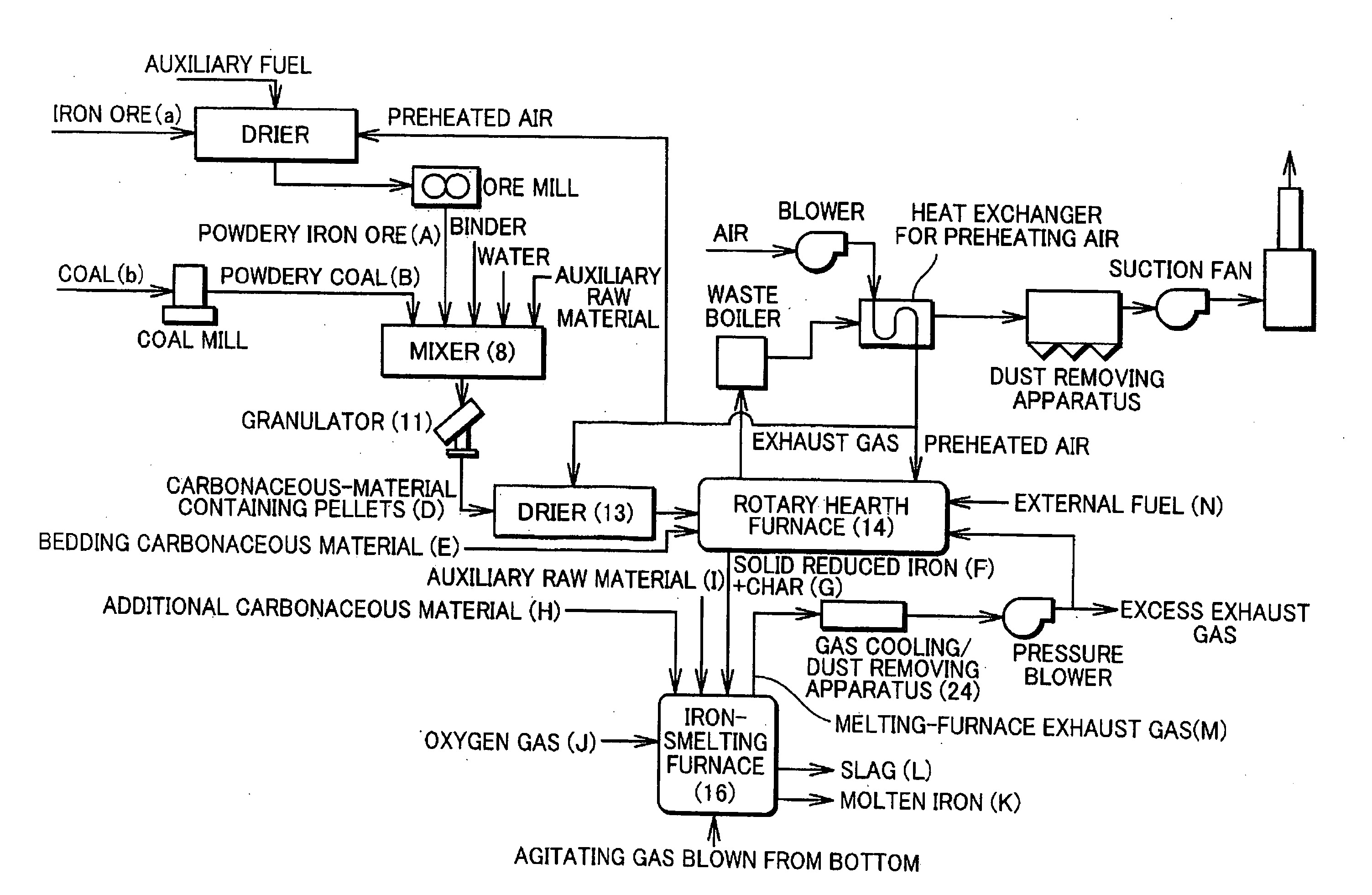
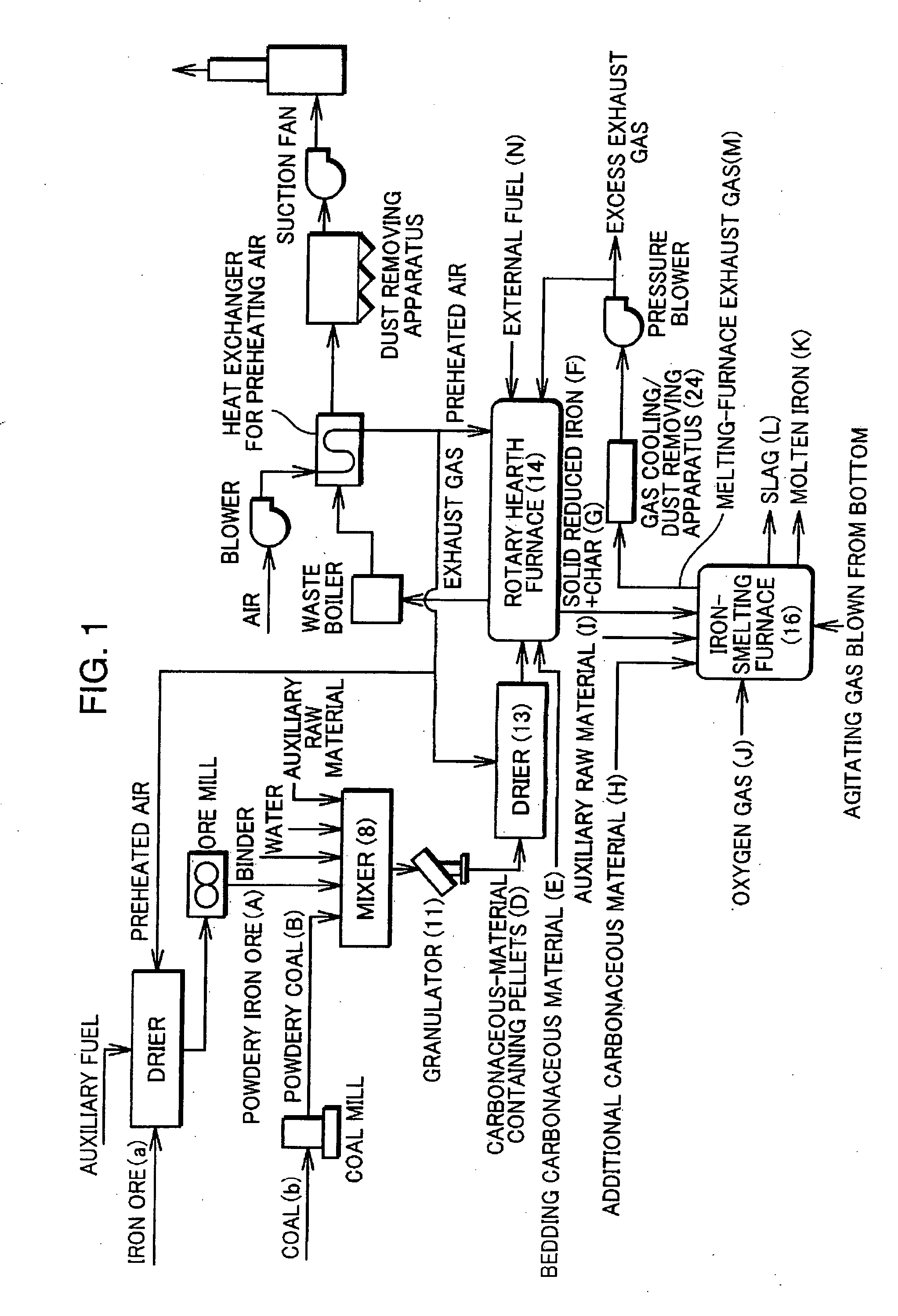
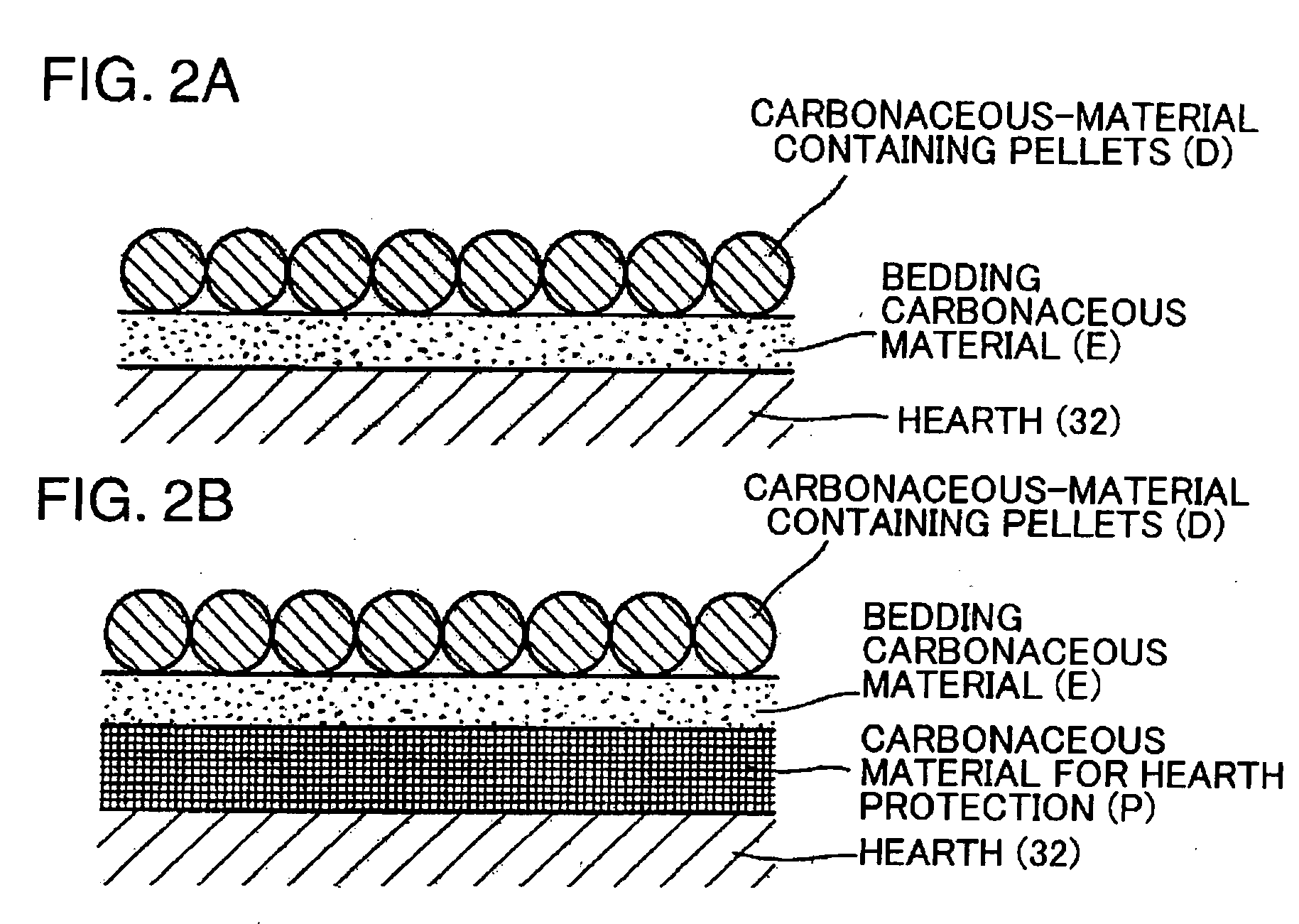
Process for Producing Molten Iron and Apparatus Therefor
A bedding carbonaceous material is charged onto a hearth of a rotary hearth furnace, carbonaceous-material containing pellets containing powdery iron ore and powdery coal are placed on the bedding carbonaceous material, and the hearth is caused to pass inside the rotary hearth furnace to heat and reduce the carbonaceous-material containing pellets to solid reduced iron and to heat and dry the bedding carbonaceous material by distillation into char. Subsequently, the solid reduced iron and the char are charged into an iron-melting furnace without being substantially cooled, and an oxygen gas is blown into the iron-melting furnace to melt the solid reduced iron, thereby obtaining molten iron. At least a part of an exhaust gas from the iron-melting furnace is used as a fuel gas for the rotary hearth furnace after being cooled and having dust removed.
Owner:KOBE STEEL LTD
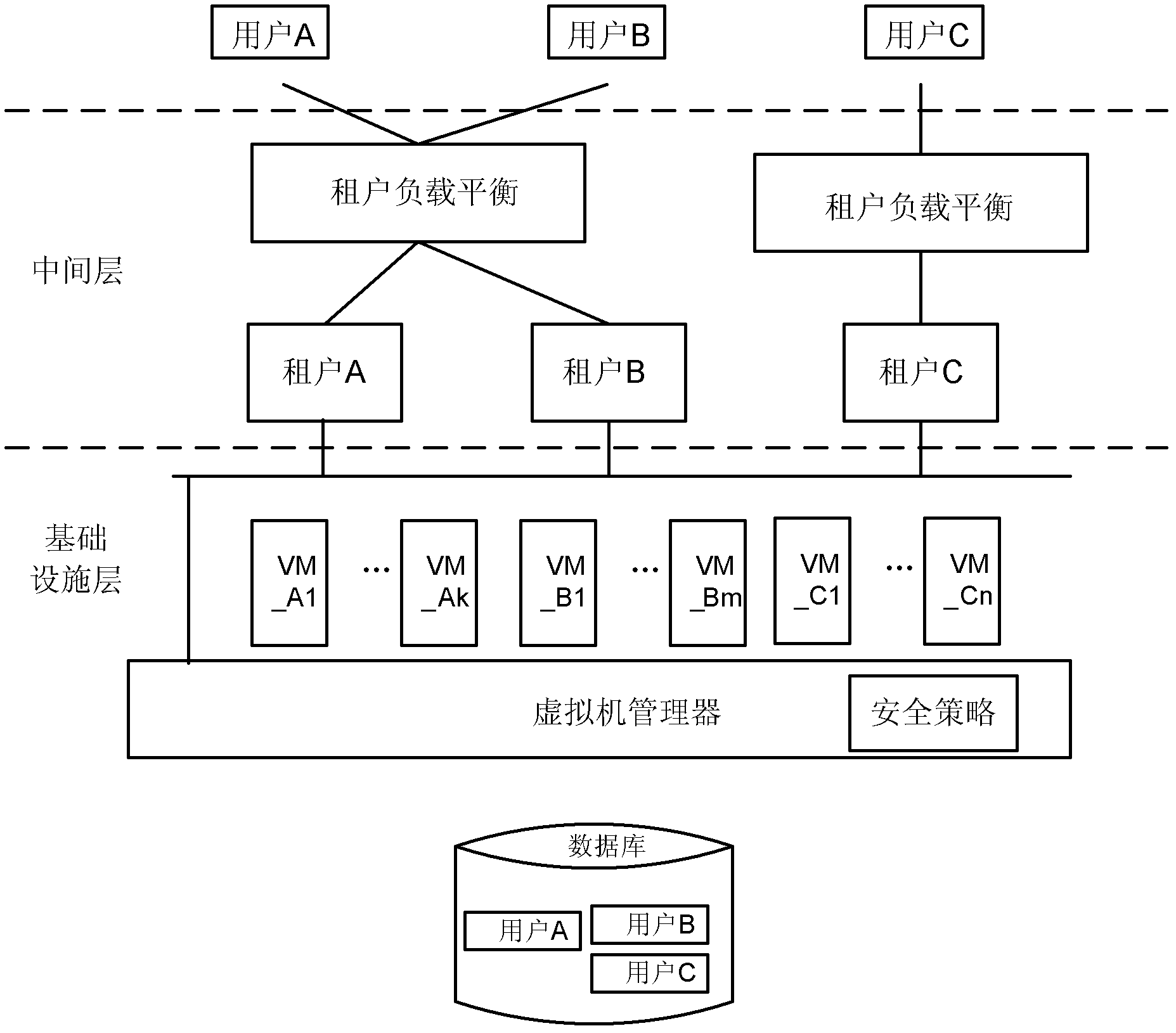
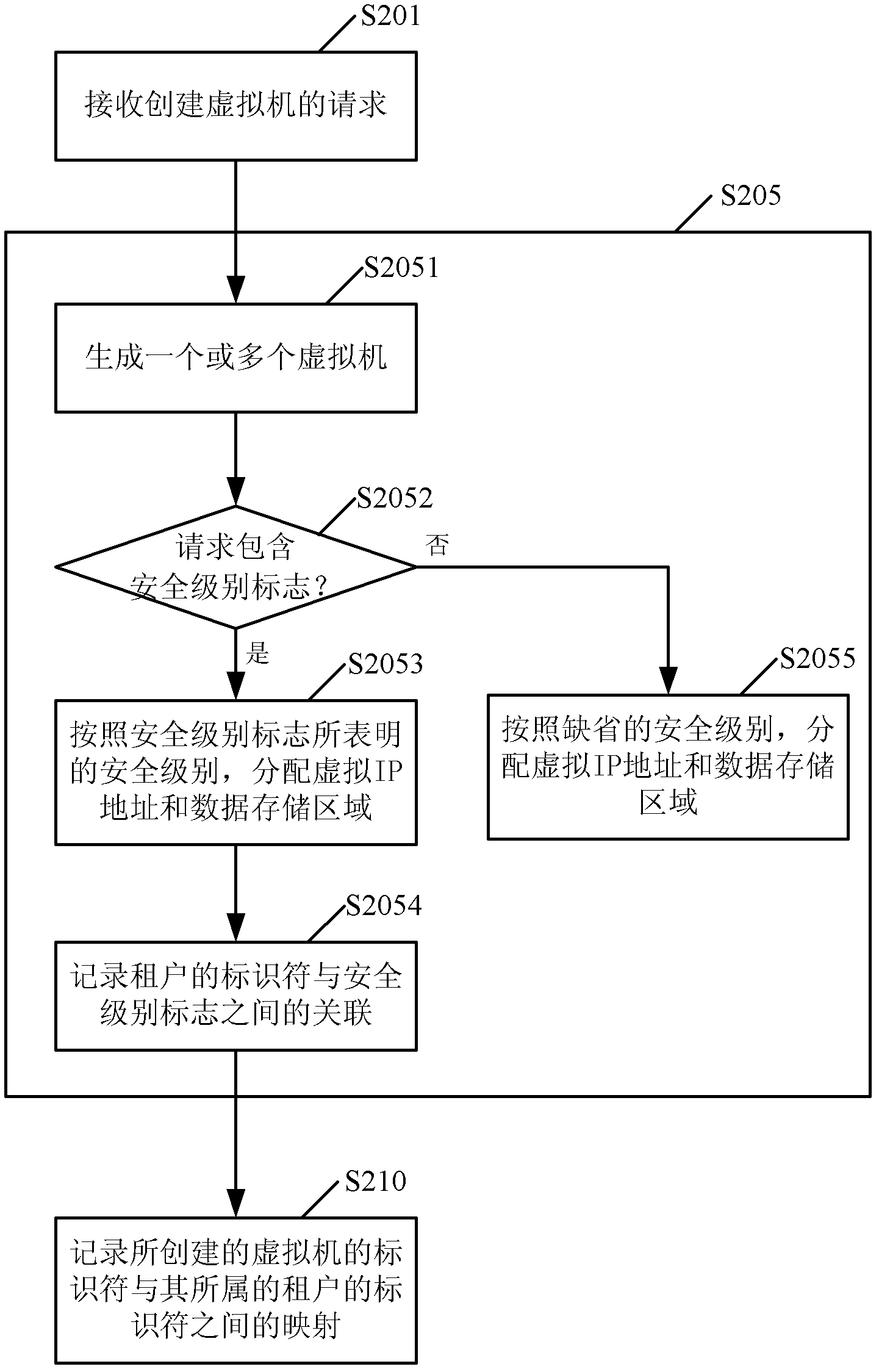
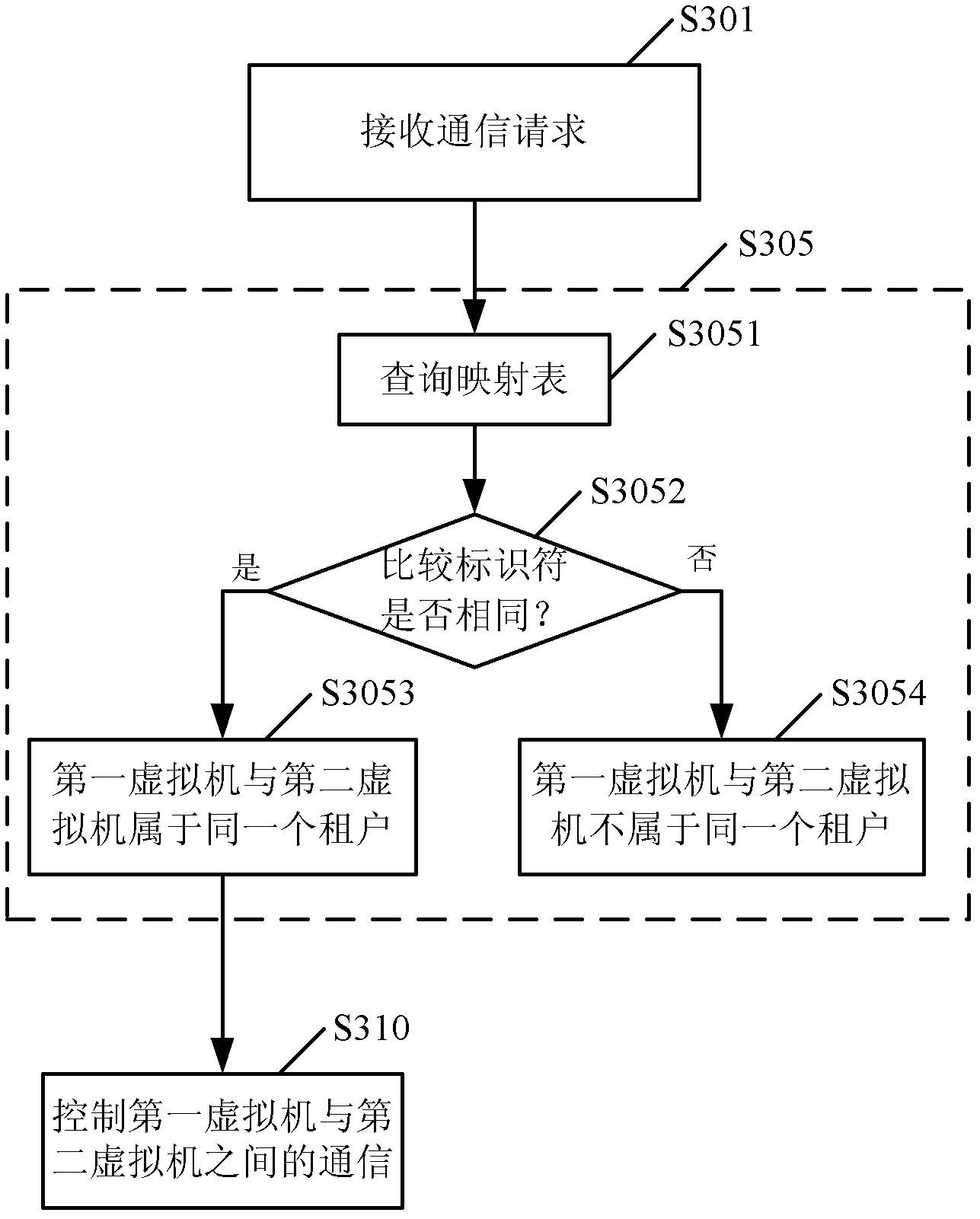
Safety communication among virtual machines in cloud computing framework
Provided is a method used for building a virtual machine of a user in a cloud computing framework. The method used for building the virtual machine of the user in the cloud computing framework comprises receiving a request for building the virtual machine from a tenant built by the user, responding to the request, and building the virtual machine of the user; and recording mapping between an identifier of the built virtual machine and a identifier of the tenant of the virtual machine in a mapping table. Due to the facts that the virtual machine is built, and the mapping between the identifier of the virtual machine and the identifier of the tenant of the virtual machine is recorded at the same time, relevance between the virtual machine and the tenant can be built, and safe communication among virtual machines can be provided. In addition, the invention further provides a corresponding device, and a method and a device used for controlling the safety communication among the virtual machines in the cloud computing framework.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
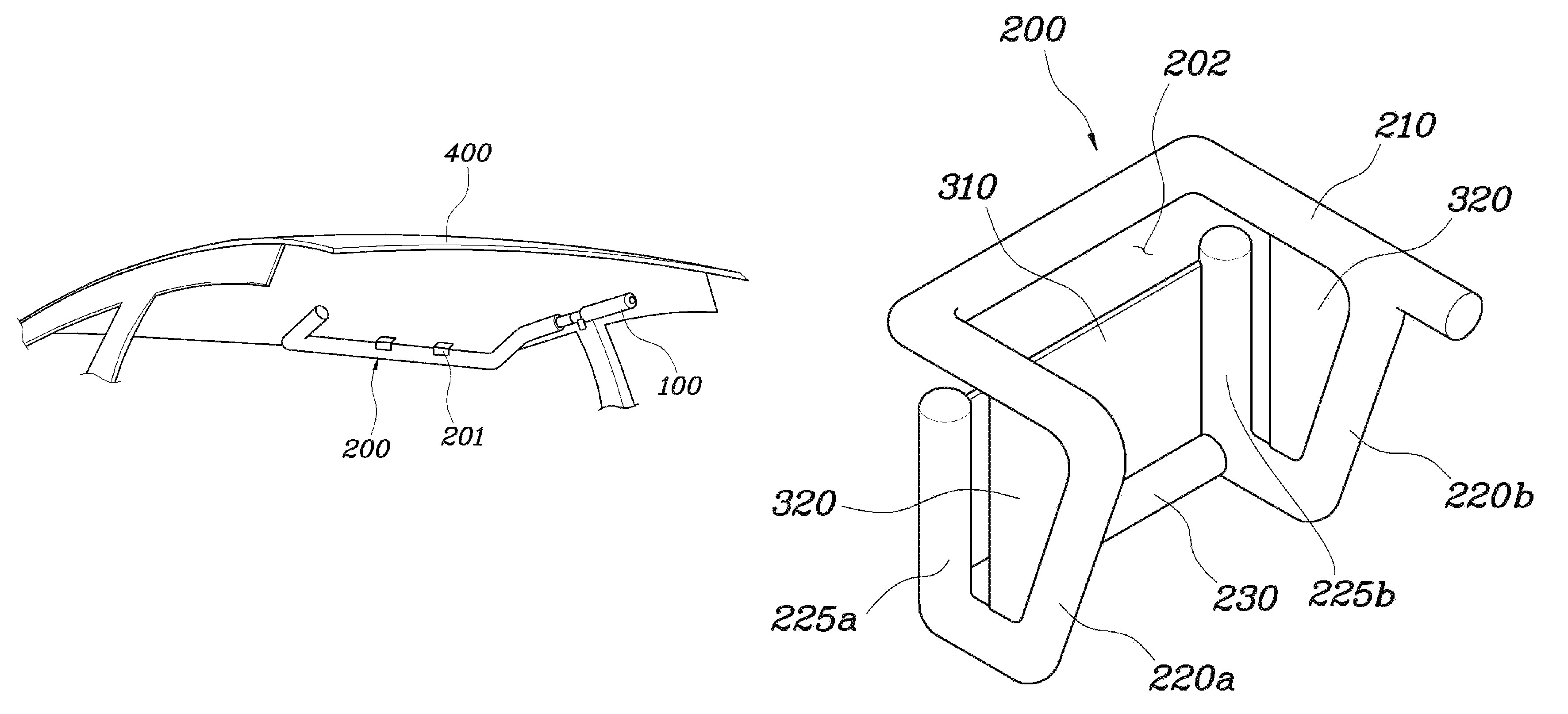
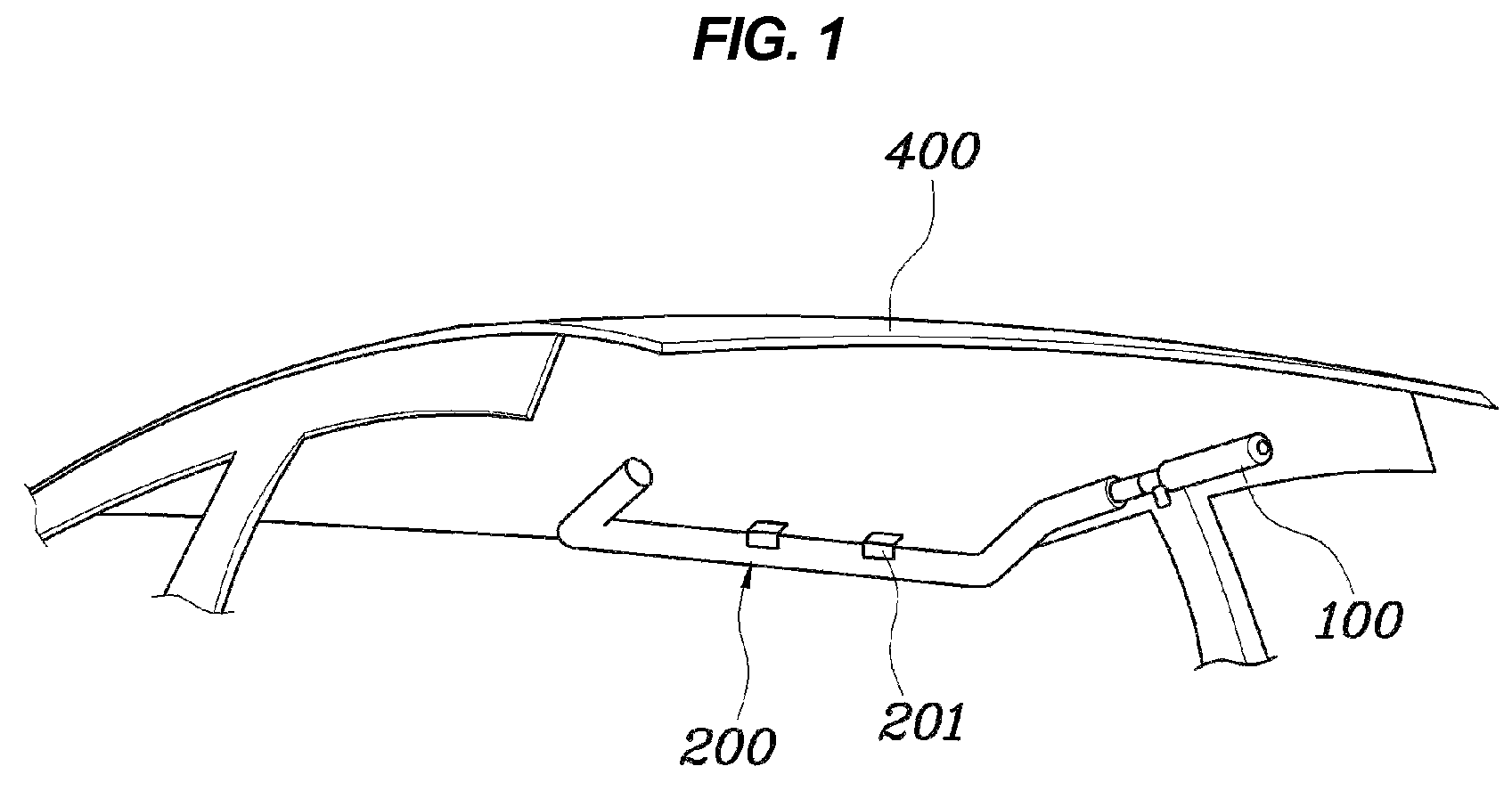
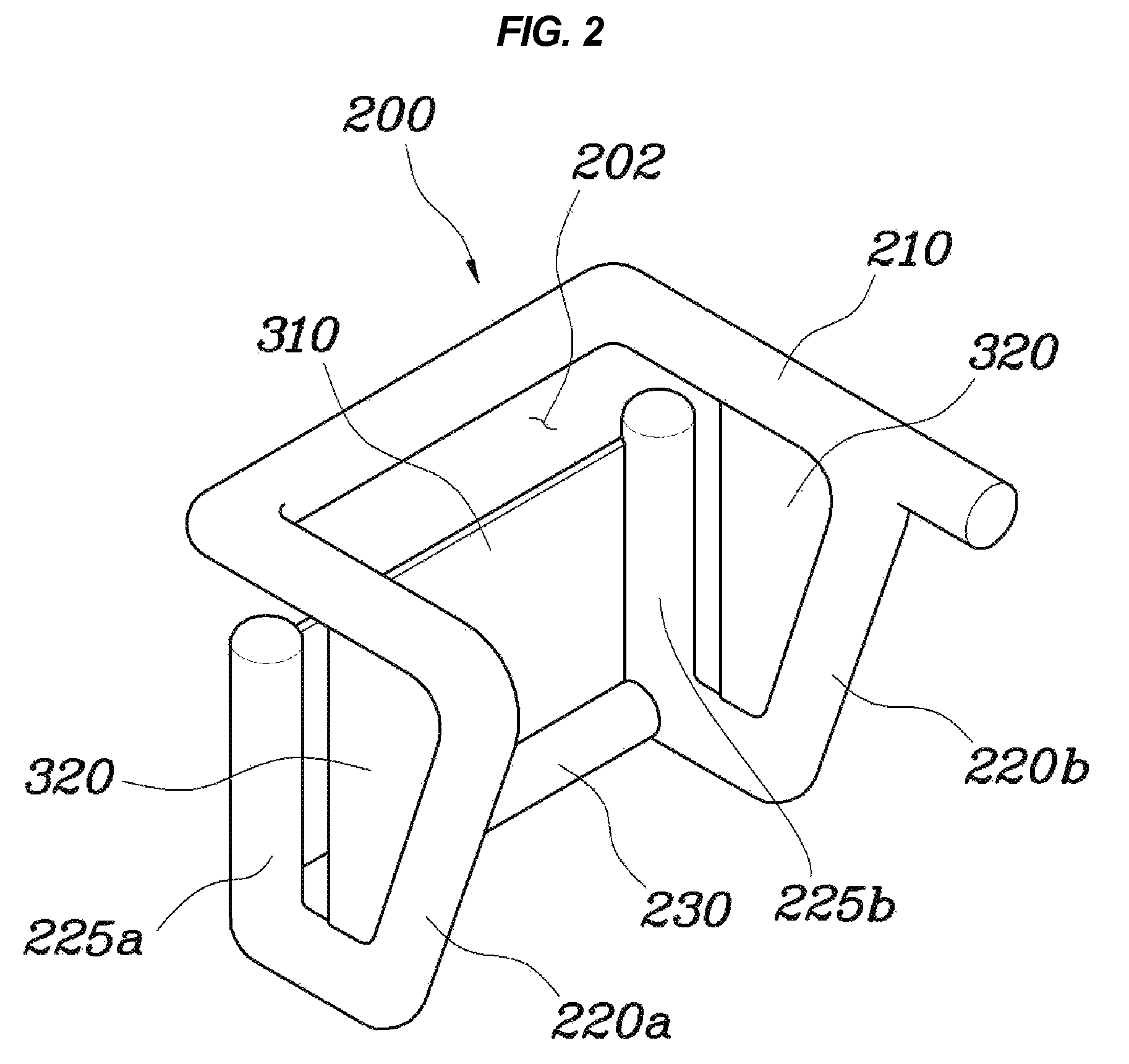
Roof airbag apparatus for vehicle
InactiveUS8414017B2Small volumeImprove securityPedestrian/occupant safety arrangementEngineeringAirbag
A roof airbag apparatus for a vehicle, may include an inflator providing gas pressure, an air tube deploying towards sides of a passenger sitting on a seat when gas may be supplied from the inflator into the air tube, and a front support panel provided on a front end of the air tube to enclose a front portion of the passenger when the air tube may be deployed.
Owner:HYUNDAI MOTOR CO LTD
Battery diaphragm and fabrication method thereof
ActiveCN102820444ALow orientationUniform surface pore size distributionSynthetic resin layered productsSecondary cellsLow-density polyethyleneLinear low-density polyethylene
The invention provides a battery diaphragm. The base material of the diaphragm is a polyvinylidene fluoride non-woven fabric, coating layers are arranged on two sides of the polyvinylidene fluoride non-woven fabric, and the material of the coating layers includes an ultra high molecular weight polyethylene and a linear low density polyethylene. A fabrication method of the battery diaphragm is further provided. According to the battery diaphragm and the fabrication method thereof, the provided battery diaphragm has the advantages that the air permeability is remarkably improved, the closed pore temperature is remarkably lowered, the puncture strength and diaphragm breaking temperature are remarkably improved, a safe protective property is provided for a battery, and the battery diaphragm is applicable to power batteries.
Owner:BYD CO LTD
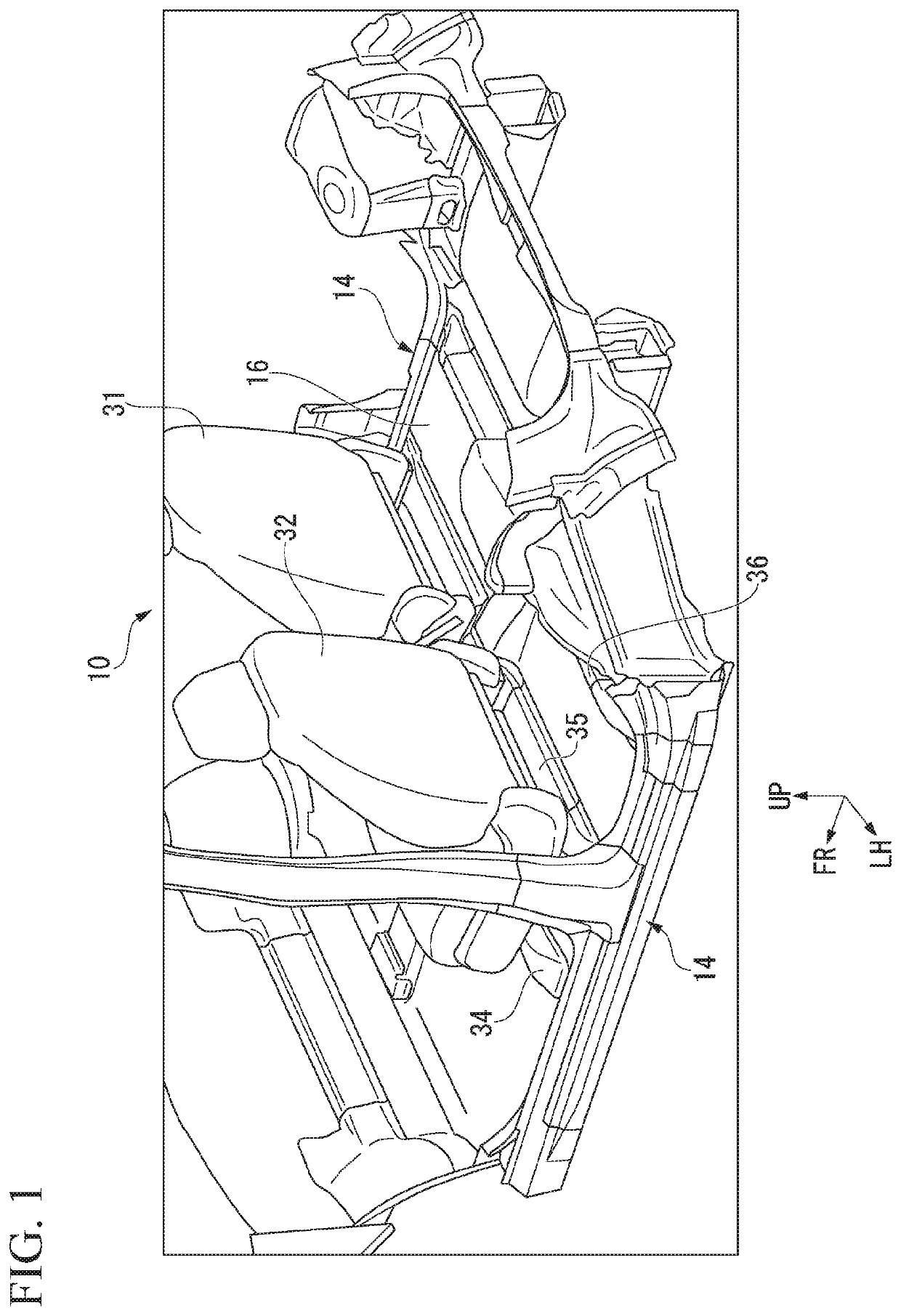
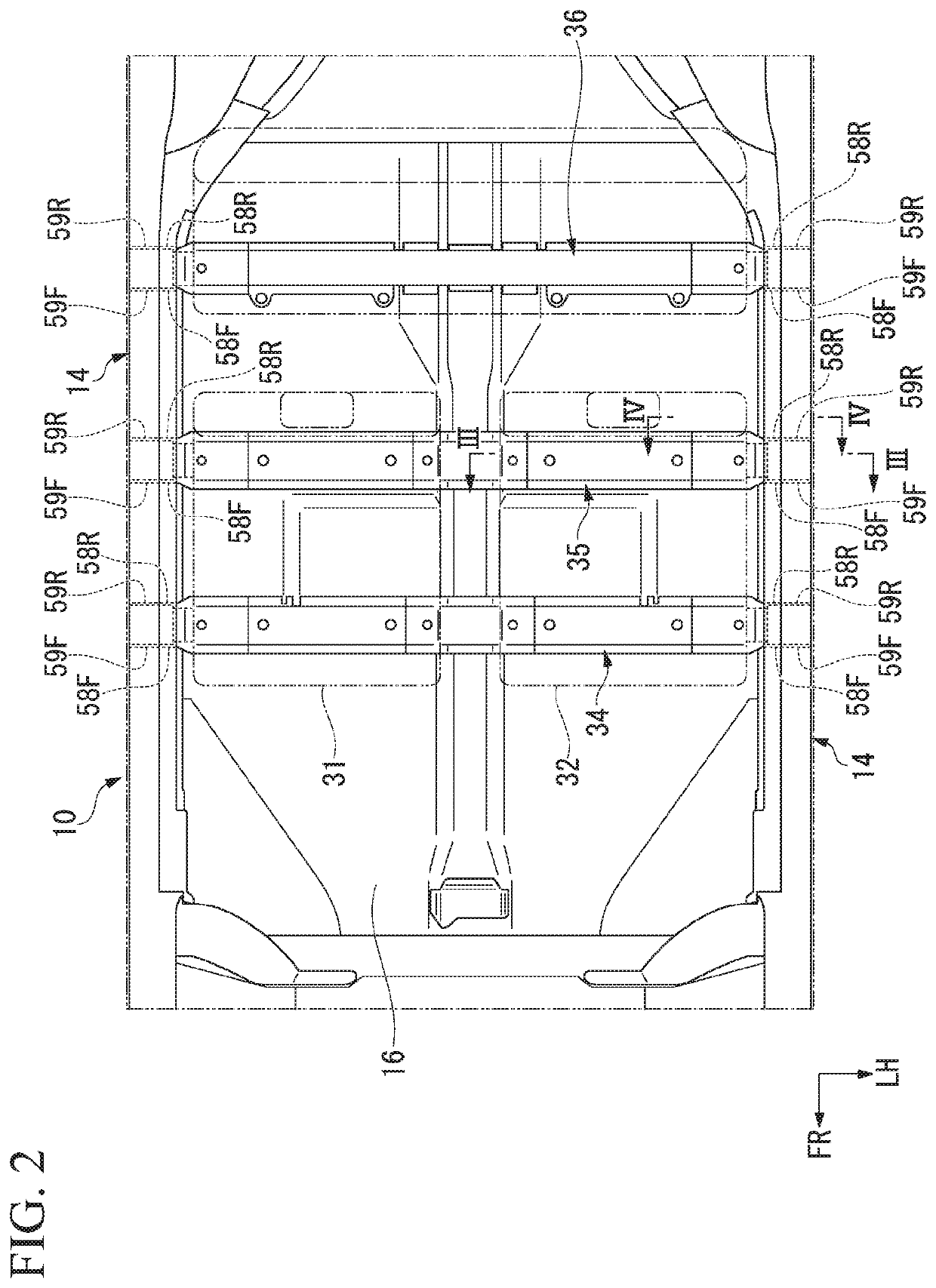
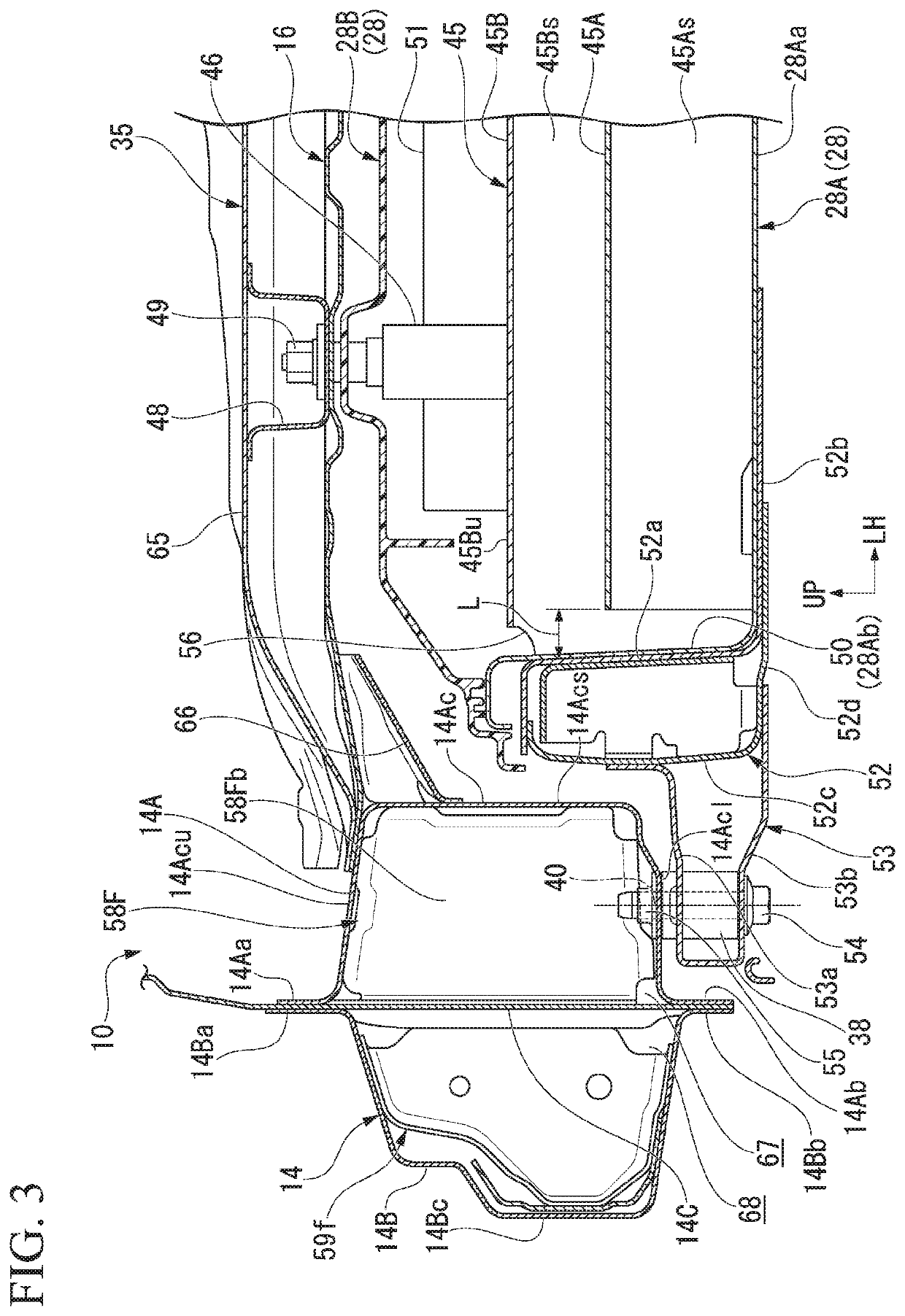
Vehicle body lower structure
ActiveUS20190359260A1Stability protectionStrengthen the strength of attachmentElectric propulsion mountingUnderstructuresBattery cellBattery pack
A vehicle body lower structure includes a pair of left and right side sills, a battery pack and a battery cross member. The battery pack accommodates a battery cell therein, and end portions in a vehicle width direction are coupled to the side sills while being disposed below a floor panel. The battery cross member is disposed inside the battery pack substantially in the vehicle width direction and extends further outward in the vehicle width direction than the battery cell. The battery cross member includes a first cross member and a second cross member extending further outward in the vehicle width direction than the first cross member.
Owner:HONDA MOTOR CO LTD
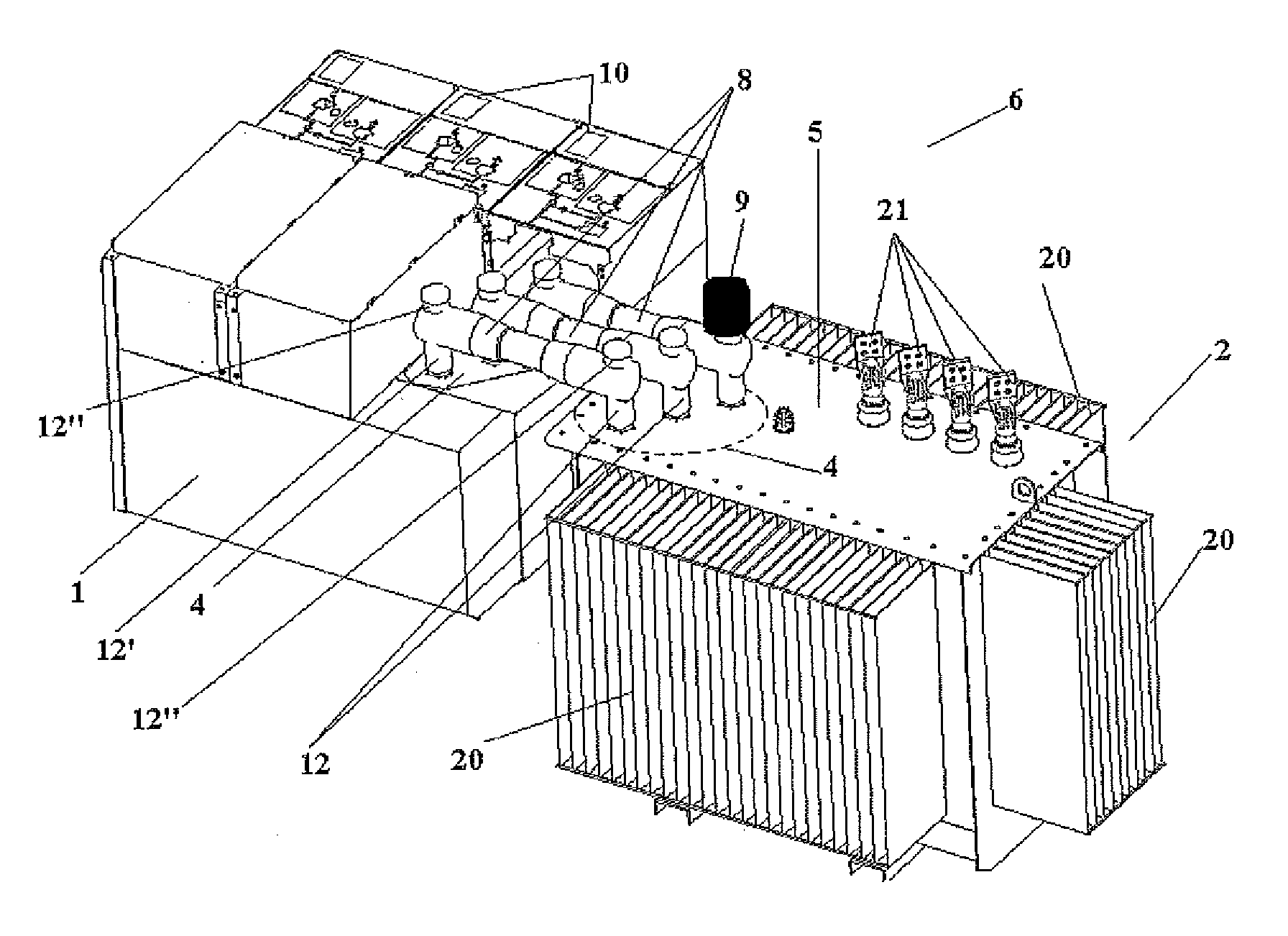
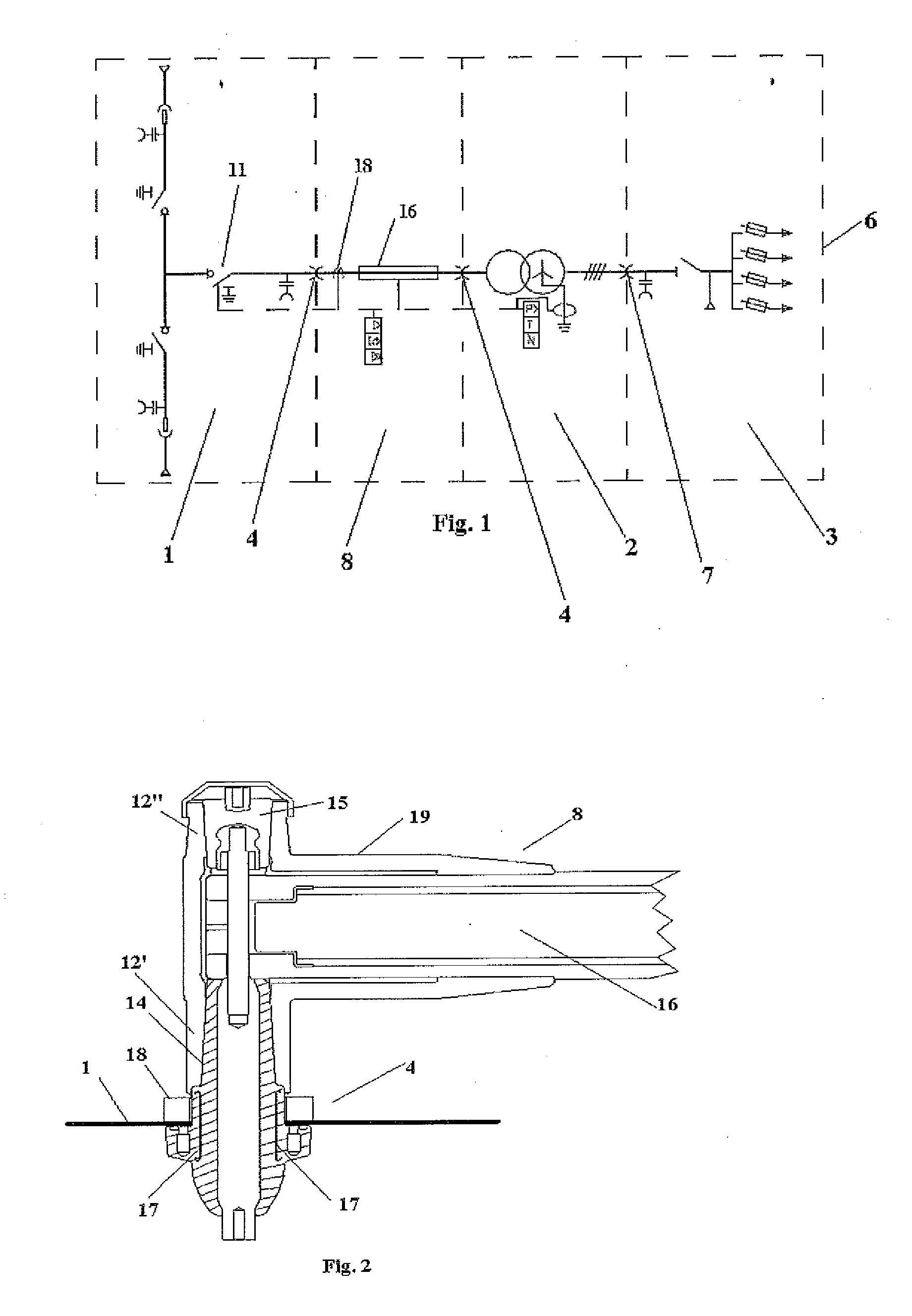
Connection device for transformer substation modules
InactiveUS20130182355A1Prevent be disturbSafety protectionSwitchgear arrangementsEmergency protective circuit arrangementsEngineeringHigh pressure
The present invention relates to a transformer substation (6) comprising high-voltage switchgear (1), a low-voltage switchboard (3) and a transformer (2) which are electrically interconnected on the upper cover (5) of the transformer (2) through a shielded direct single-pole connection. The high-voltage electric connection (4) is carried out by means of a connection device (8) which, in combination with a control / protection device (10), allows carrying out the safe and integral protection of people and property against possible malfunctions in the transformer substation (6), limiting said malfunctions and preventing disturbances of the high-voltage and low-voltage network.
Owner:ORMAZABAL Y CIA S L U
High-efficiency intelligent high-side electronic load switch with wide voltage adaptability
ActiveCN104079276ARaise the voltage thresholdExtended working voltage rangeElectronic switchingInformation processingElectronic load
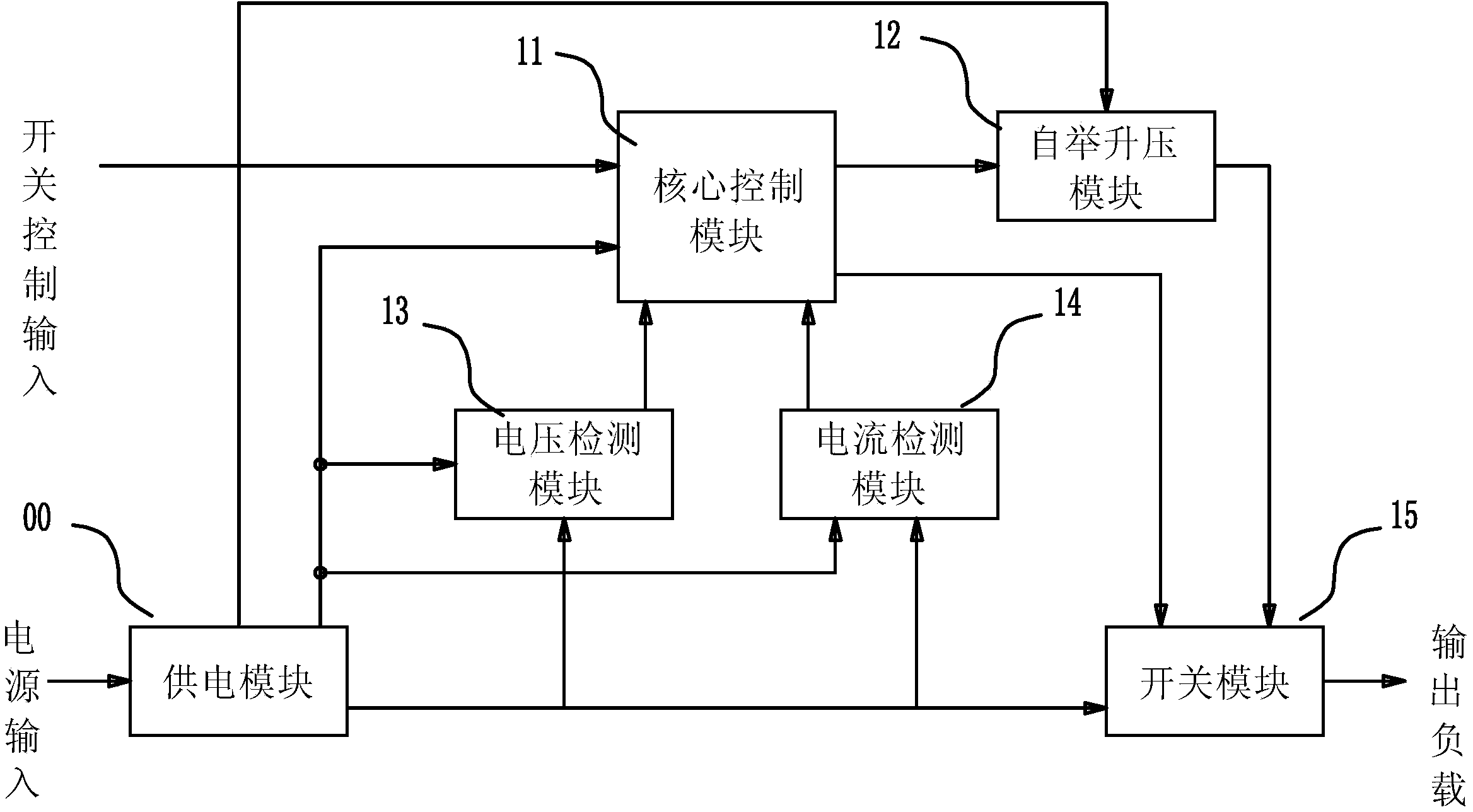
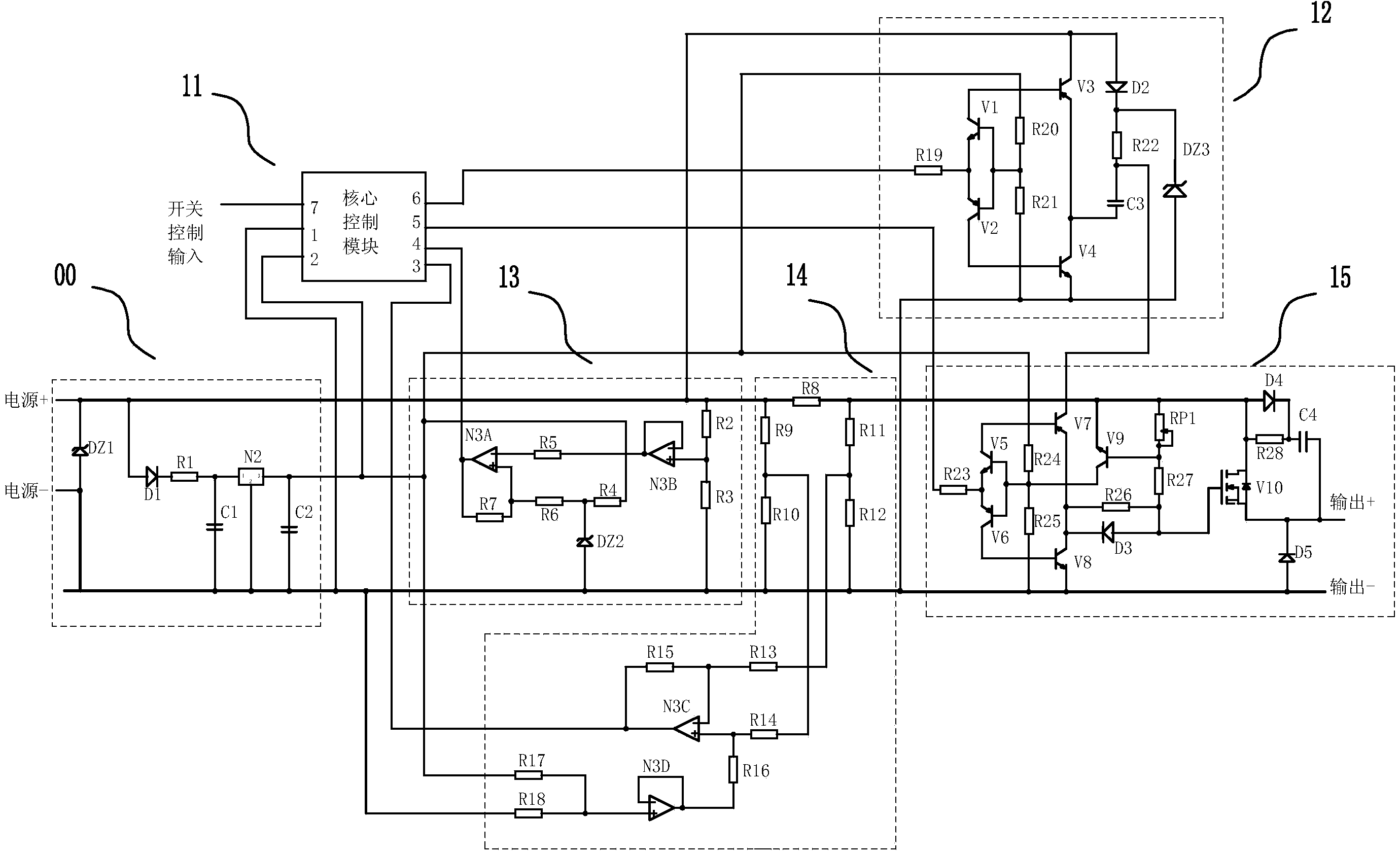
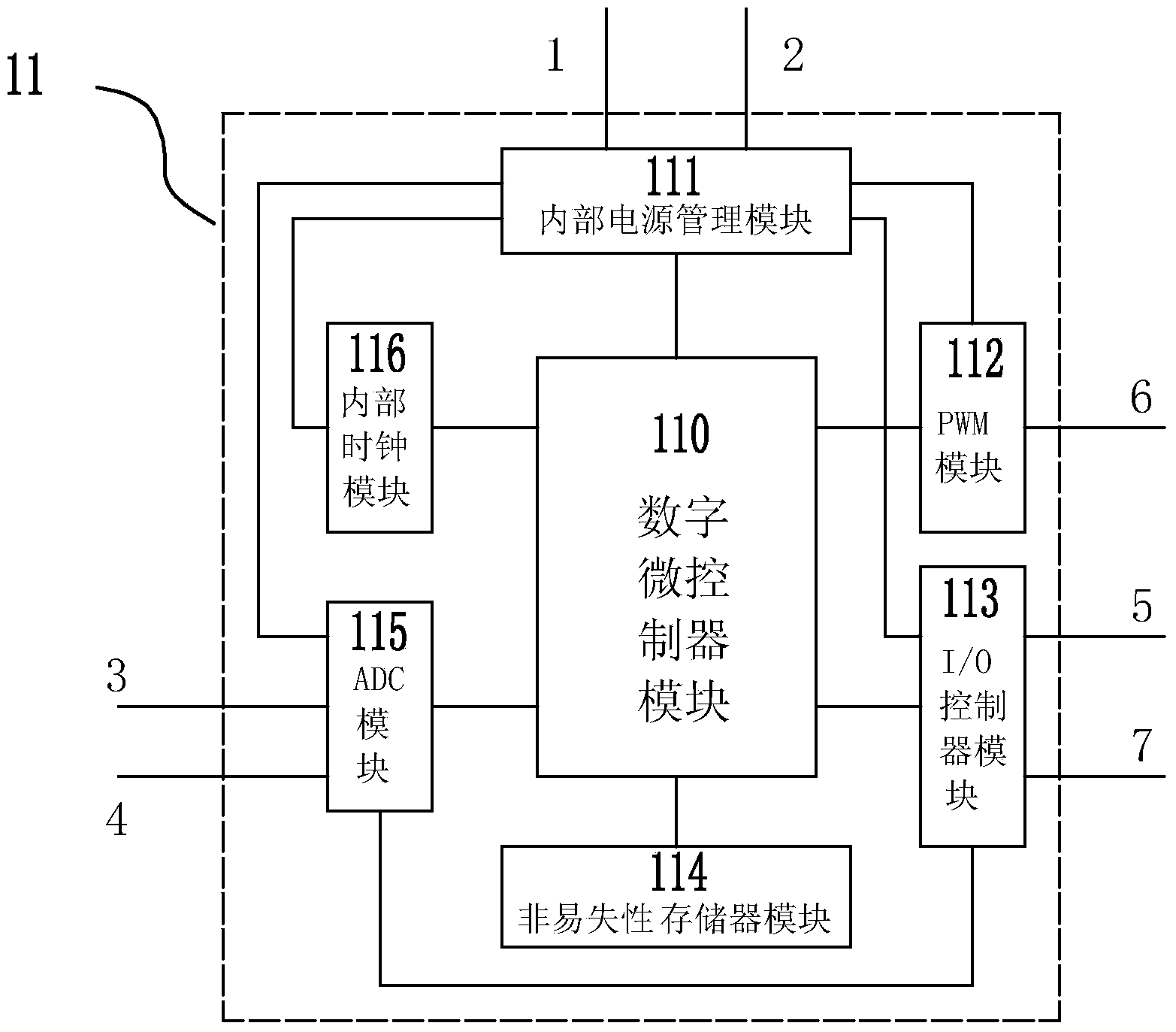
A high-efficiency intelligent high-side electronic load switch with wide voltage adaptability comprises a power supply module, a core control module, a self-boosting module, a voltage detection module, a current detection module and a switching module. The core control module is used for signal acquisition, information processing and storage and logic control; firstly, the core control module receives an external switch control input signal and detection signals output by the current detection module and the voltage detection module and processes and analyzes monitoring data according to an internally stored program to control the switching module to complete corresponding actions; secondly, the core control module provides a PWM control signal for the self-boosting module. The voltage detection module and the current detection module are used for detecting the real-time operating voltage and current of the switching module and transmitting data to the core control module for processing and analysis. The self-boosting module is used for providing a driving voltage for a switching tube in the switching module. The switching module is used for executing the on-off actions of a load. The high-efficiency intelligent high-side electronic load switch is wide in operating voltage range, high in operating frequency, high in efficiency, low in loss, safe, reliable and programmable.
Owner:LIUZHOU CHANGHONG MACHINE MFG
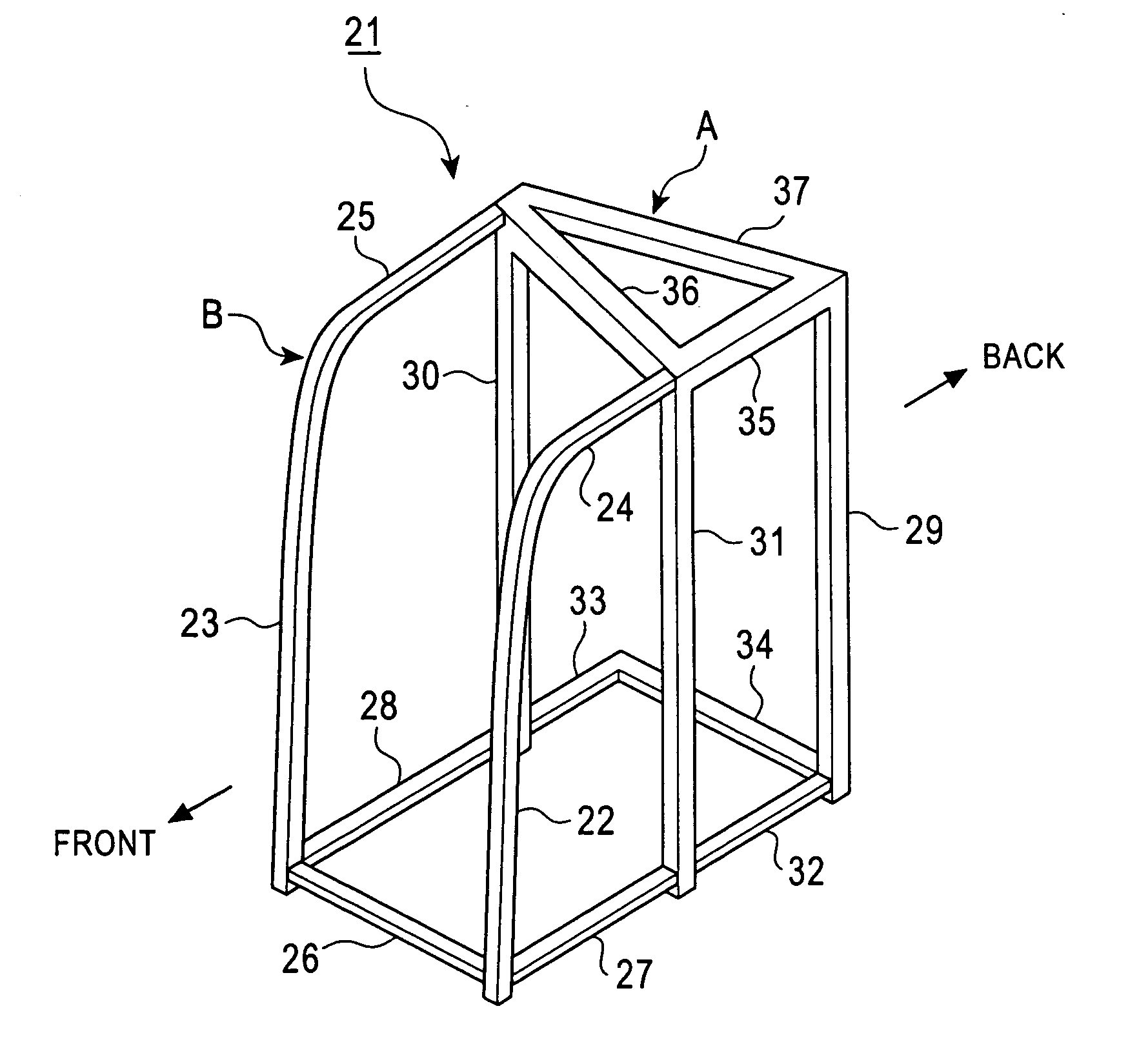
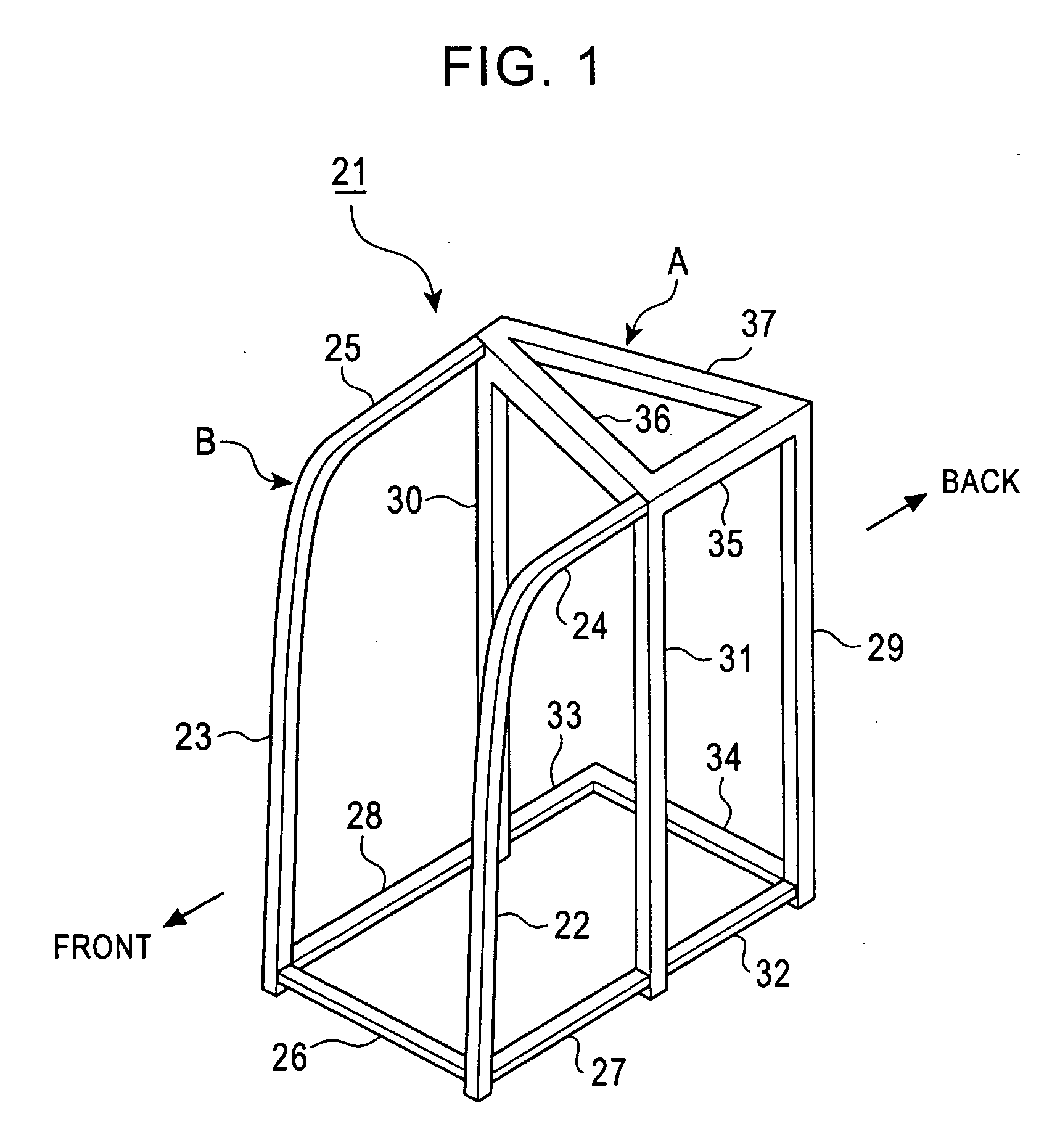
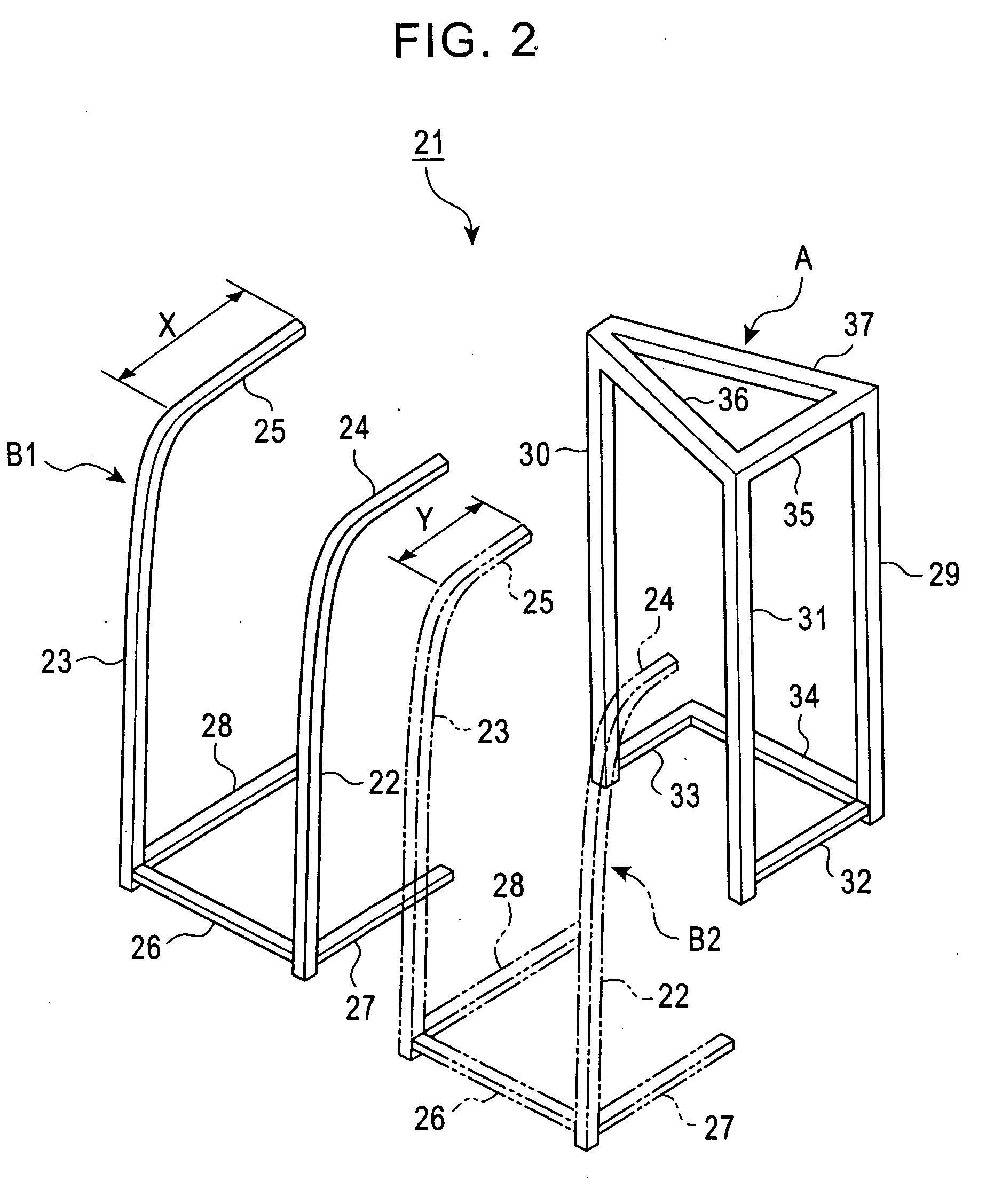
Driver's cabin of construction machine
InactiveUS20060017308A1Safety protectionAppropriate strengthVehicle seatsPedestrian/occupant safety arrangementNacelleEngineering
A cabin frame for a cabin of a construction machine includes a combination of a posterior frame body having a predetermined strength and an anterior frame body disposed in front thereof. The posterior frame body defines a common element that is used in common between different machine models, whereas the anterior frame body defines an adjustment element such that its dimension in a front-back direction of the construction machine is determined according to the corresponding machine model. Another cabin frame includes a combination of an anterior frame body defining a common element used in common between three machine models, namely, a model with an operator-protecting function, a low-tare model with an operator-protecting function, and a high-tare model with an operator-protecting function; and a posterior frame body defining a replaceable element having a predetermined strength selected from a plurality of strengths set for the corresponding machine models.
Owner:KOBELCO CONSTR MASCH CO LTD
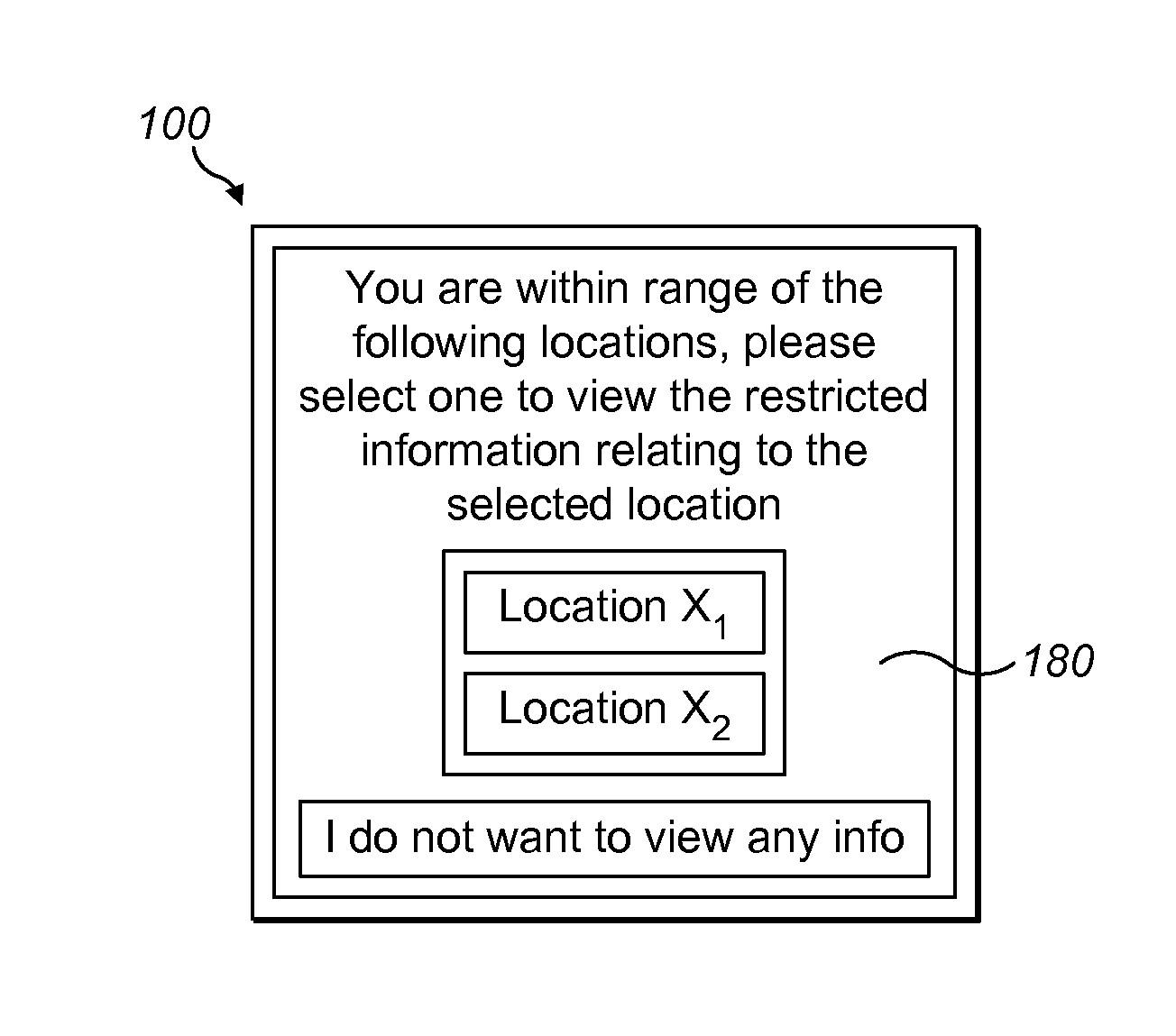
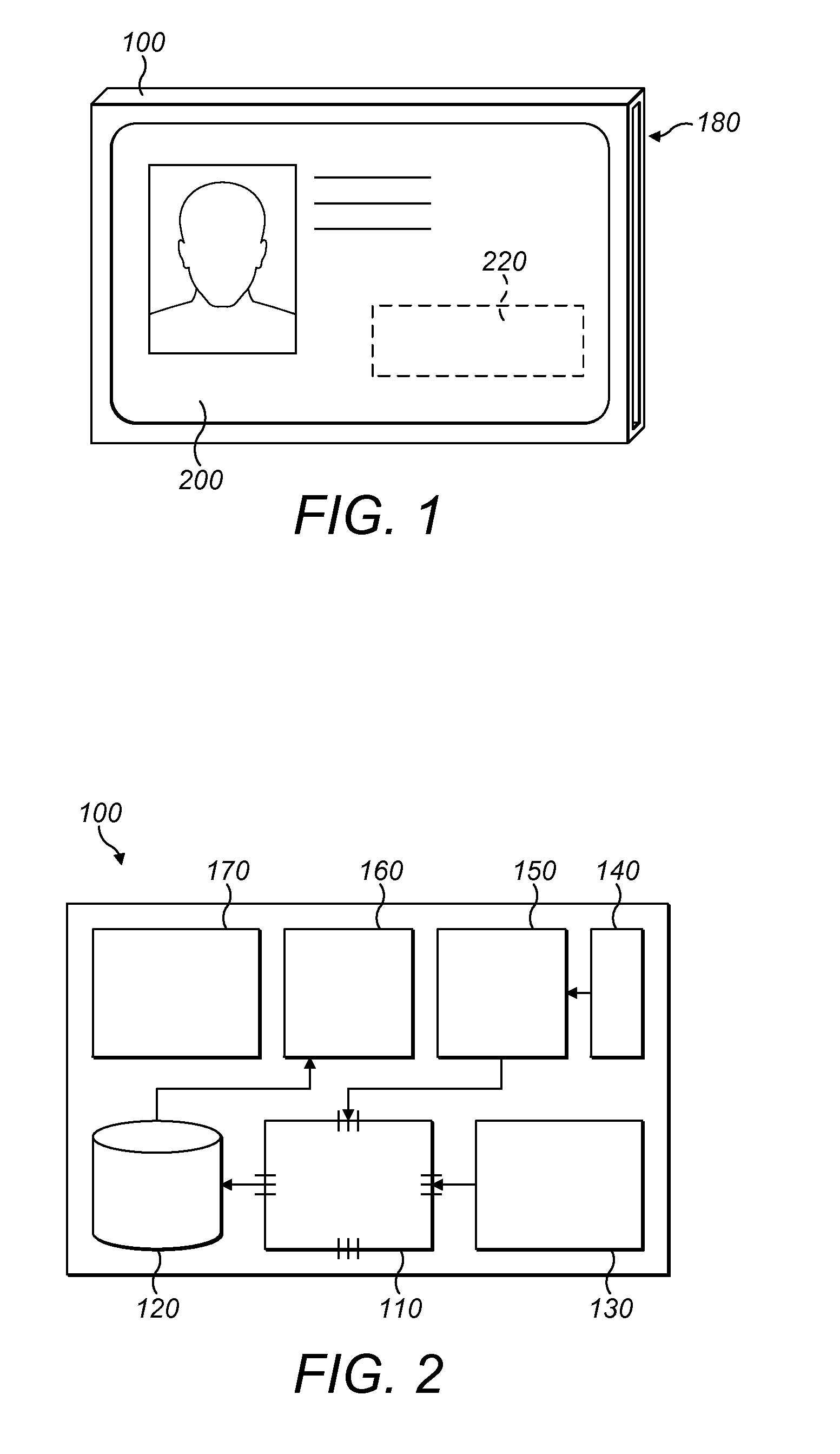
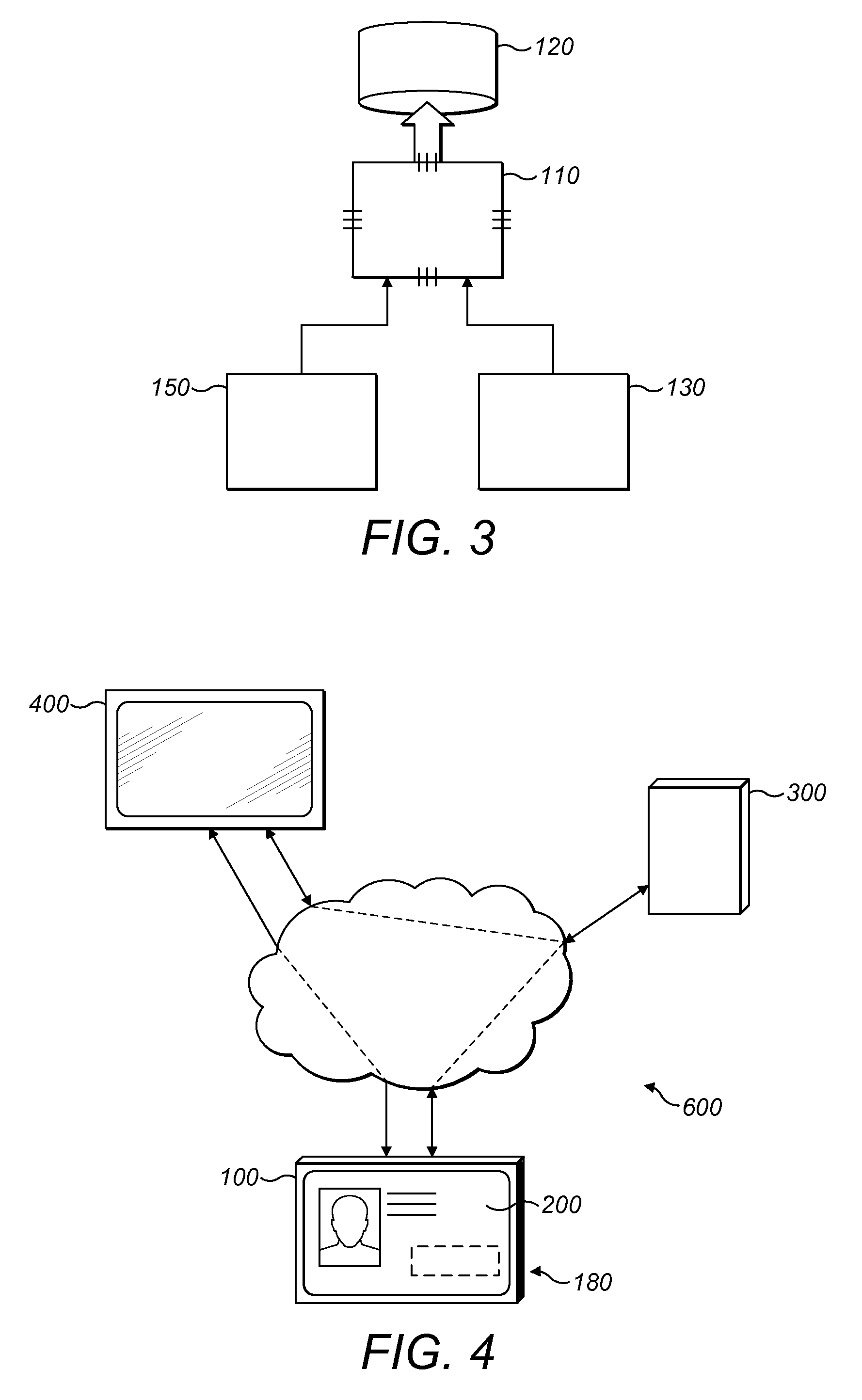
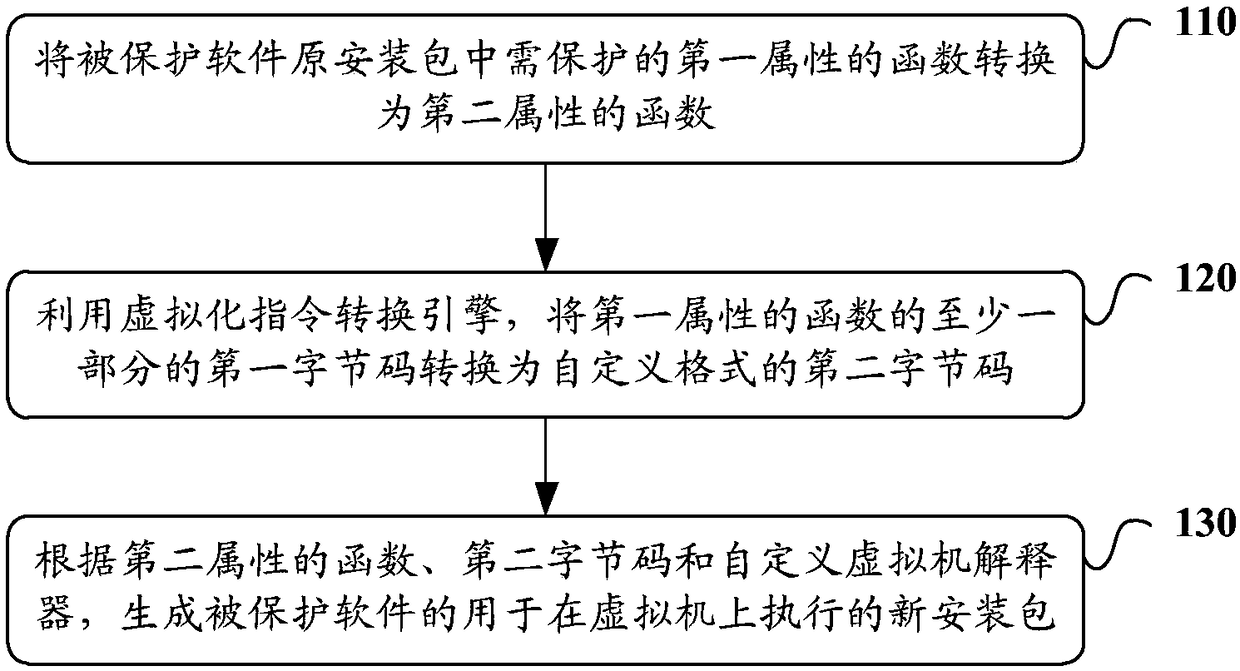
Identity card holder and system
InactiveUS20160050202A1Improve safetySafety be ensureDigital data processing detailsMultiple digital computer combinationsServer applianceCard holder
An identity card holder with a processor, a memory, an antenna, an interface for communicating with an identity card, positioning circuitry for obtaining position data of the identity card holder and communications circuitry for communicating with a remote server apparatus. The processor being configured to receive identification data from the identity card via the interface to identify a user, to cause a credential of the user associate with the identity card to be determined, to obtain position data of the identity card holder from the positioning circuitry and to cause restricted information related to a location to be provided to the user, where the restricted information has an access requirement related to the credential of the user and wherein the restricted information is provided to the user only if the user credential meets the access requirement and the position of the identity card holder is proximate the location.
Owner:SOLOPROTECT
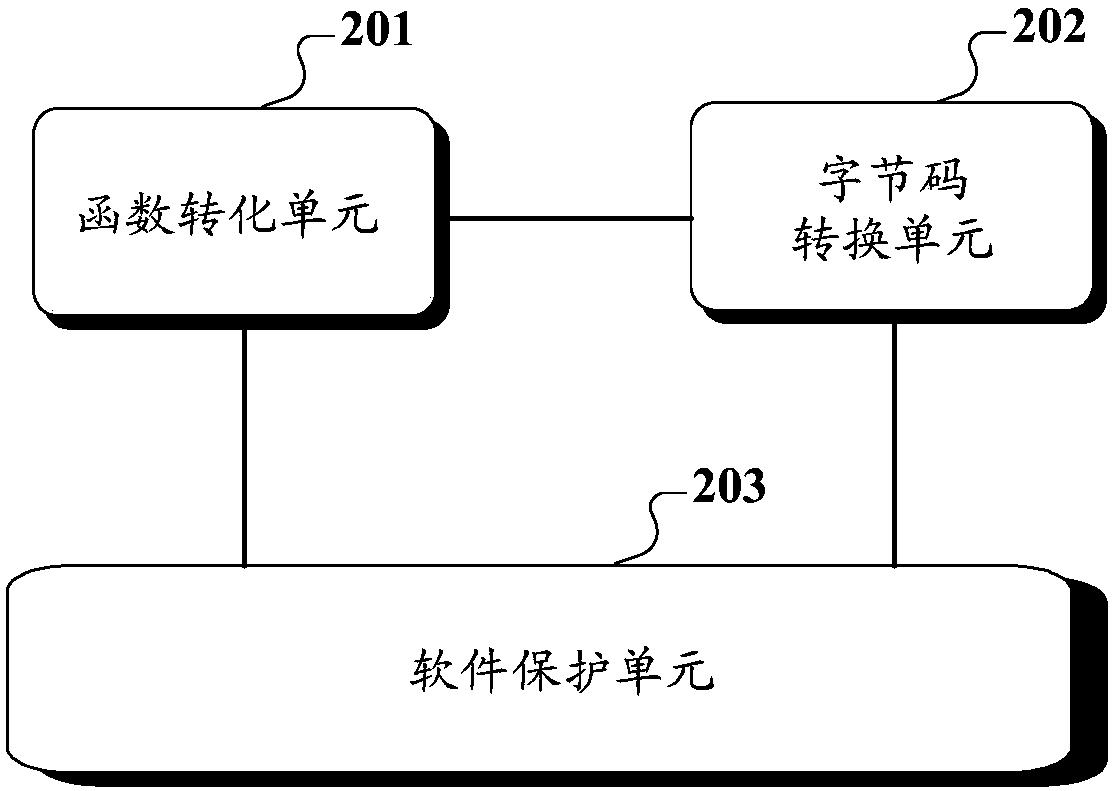
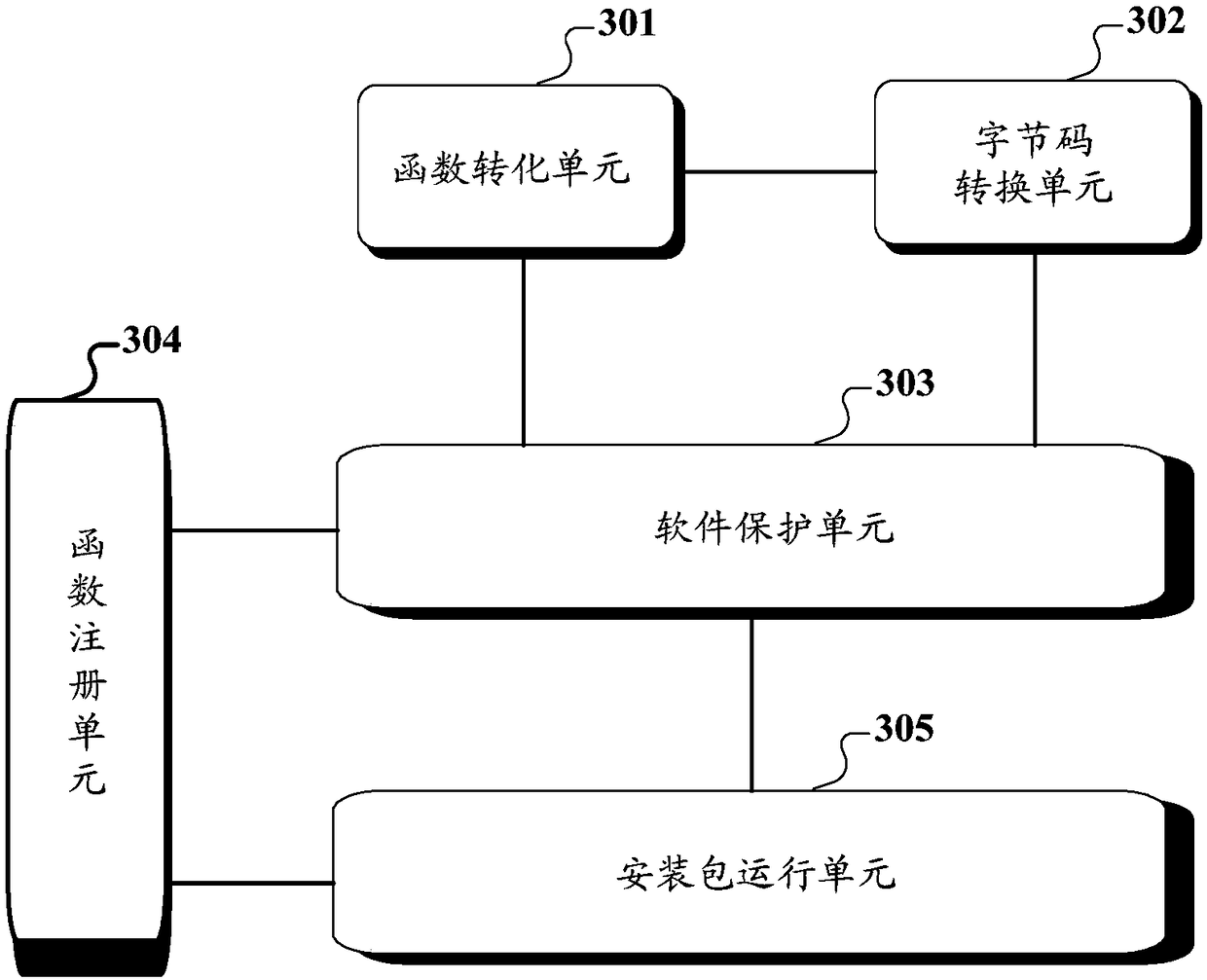
A protection method and device for virtualization software
ActiveCN108932406AIncrease the difficultySafety protectionProgram/content distribution protectionSoftware simulation/interpretation/emulationVirtualizationUser defined
The application discloses a protection method and device for virtualization software. The method includes the following steps: a function of a first attribute which requires to be protected in an original installation package of protected software is converted into a function of a second attribute; a virtualization command conversion engine is utilized, at least a part of a first byte code of thefunction of the first attribute is converted into a second byte code in a user-defined format; a new installation package used for executing on the virtual machine of the protected software is generated according to the function of the second attribute, the second byte code and a user-defined virtual machine explainer; and the user-defined virtual machine explainer is used for reading the second byte code while executing the new installation package and for performing interpretation execution on meaning of the second byte code. According to a scheme, and the safety of the protected software can be effectively guaranteed.
Owner:BEIJING BANGCLE TECH CO LTD
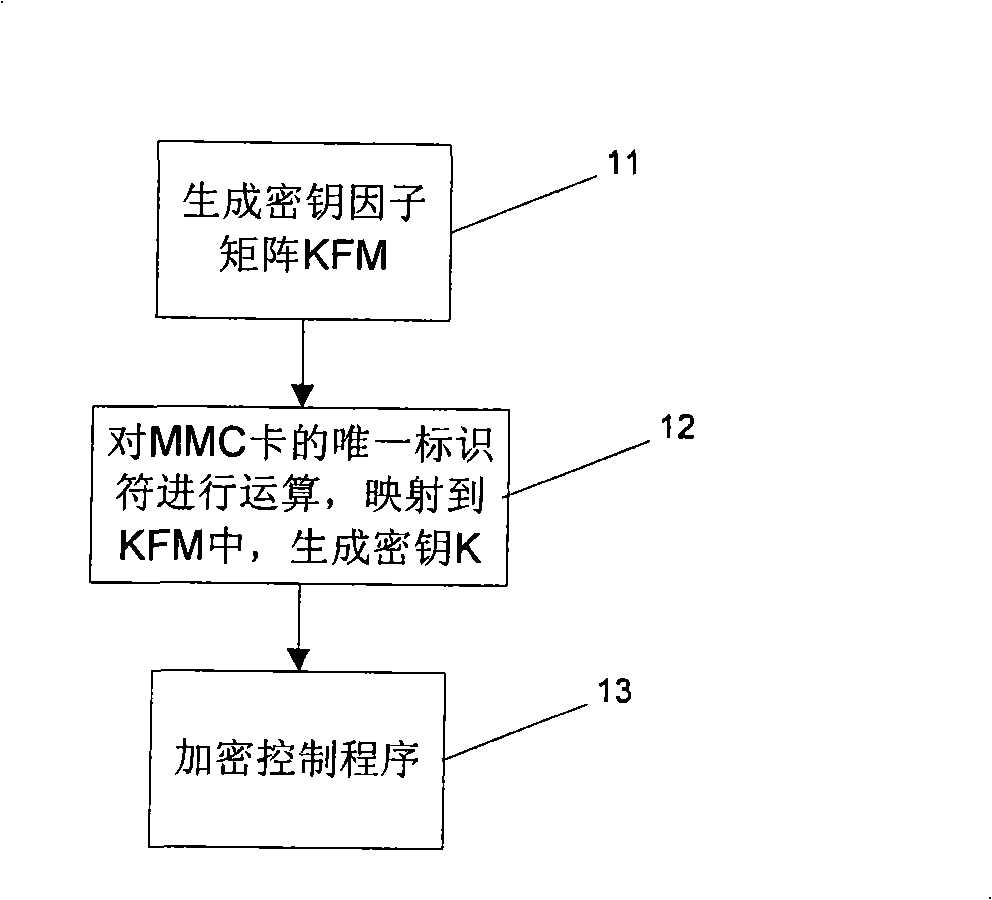
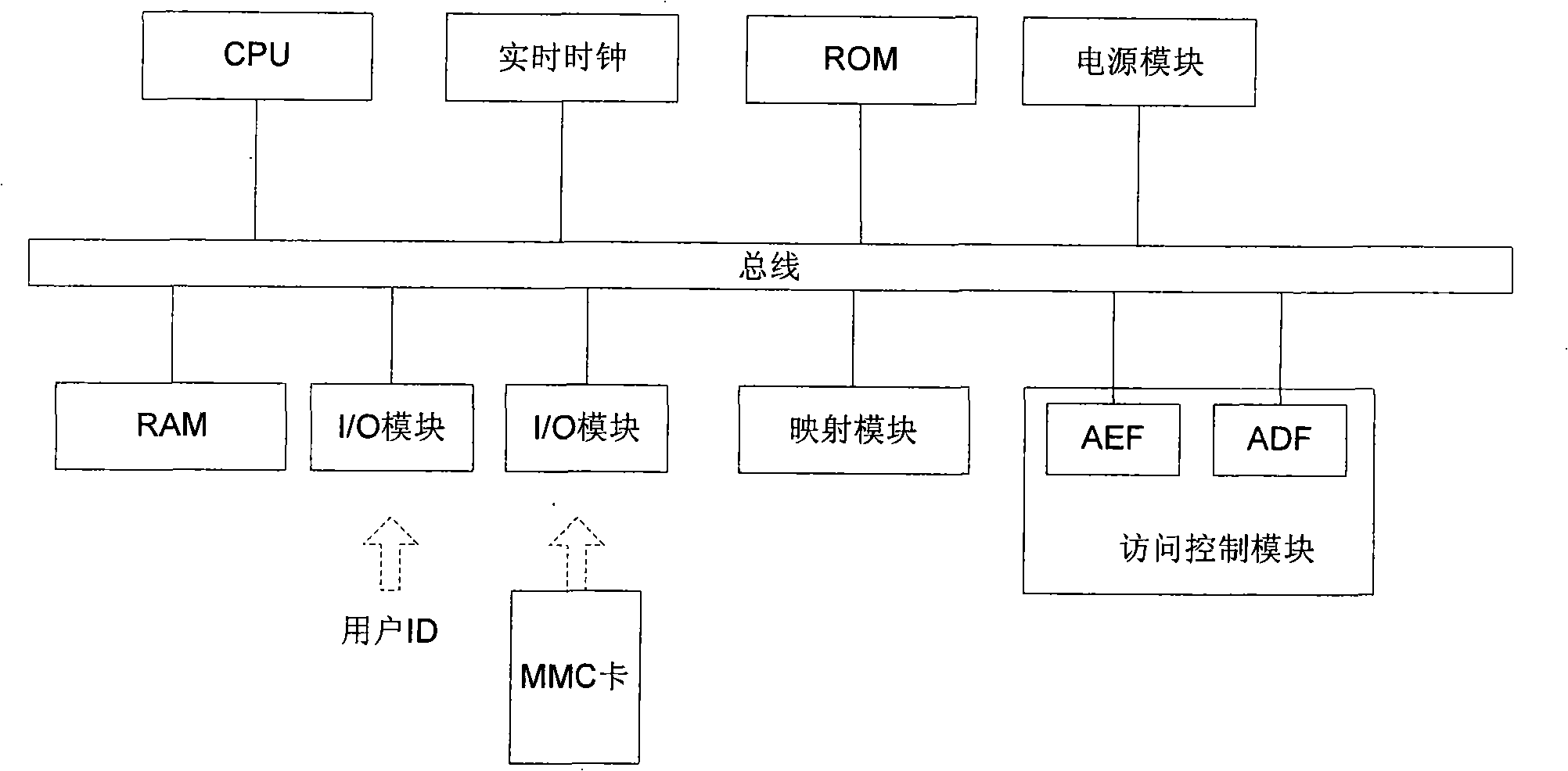
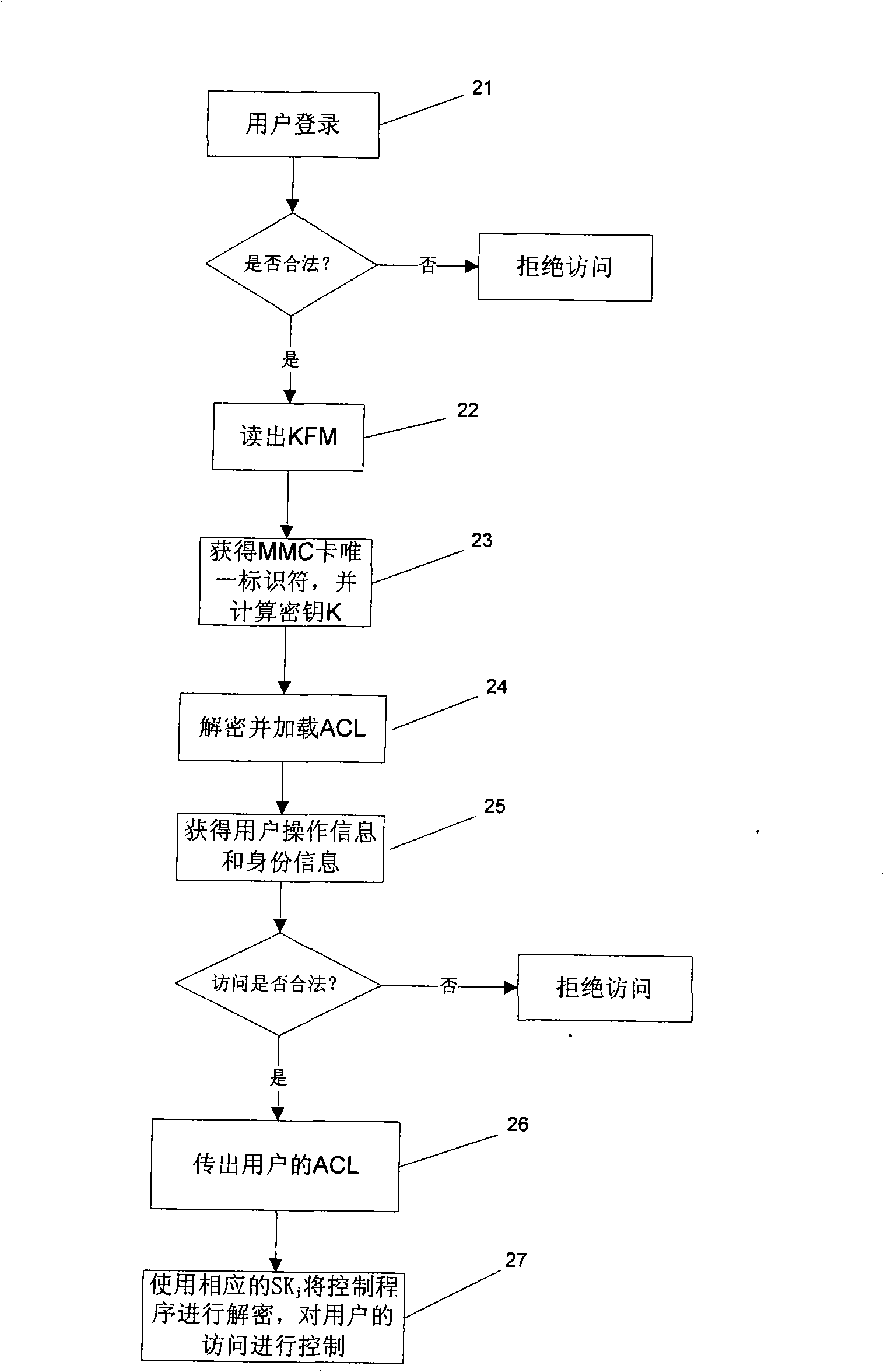
Encryption and decryption method, and PLC system using the same
ActiveCN101329658ASafety protectionImprove protectionUnauthorized memory use protectionDigital data protectionUnique identifierComputer software
The invention relates to the field of industrial computer software safety, in particular to a method for encrypting and decrypting information in a memorizer and a PLC system for applying the method. The encrypting method of the invention comprises the following steps of storing an algorithm F()in the system; mapping the unique identifier of the memorizer into a cipher key K; encrypting the information stored in the memorizer by utilizing the cipher key K based on a symmetric encryption algorithm; and predefining the access strategy based on the user identity in order to control the user's access to the information stored in the memorizer; and storing the access strategy in the memorizer by utilizing the cipher key K based on the symmetric encryption algorithm. During the decryption process, decrypting, information stored in the memorizer is decrypted by utilizing the cipher key K based on the symmetric encryption algorithm, and the access strategy is decrypted by utilizing the cipher key K based on the symmetric encryption algorithm. Then the user's access to the information stored in the memorizer is controlled based on the user identity. The method and the system of the invention have the advantage of being capable of enhancing the safety of software codes.
Owner:SIEMENS CHINA
Memory encryption method, apparatus and system
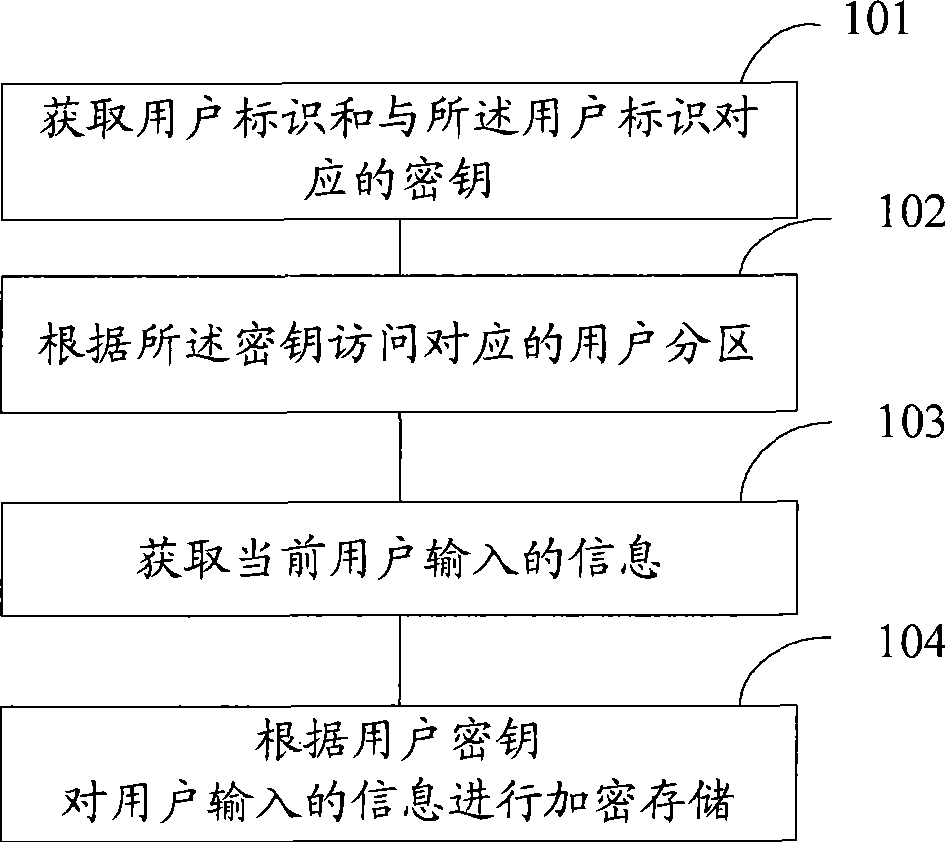
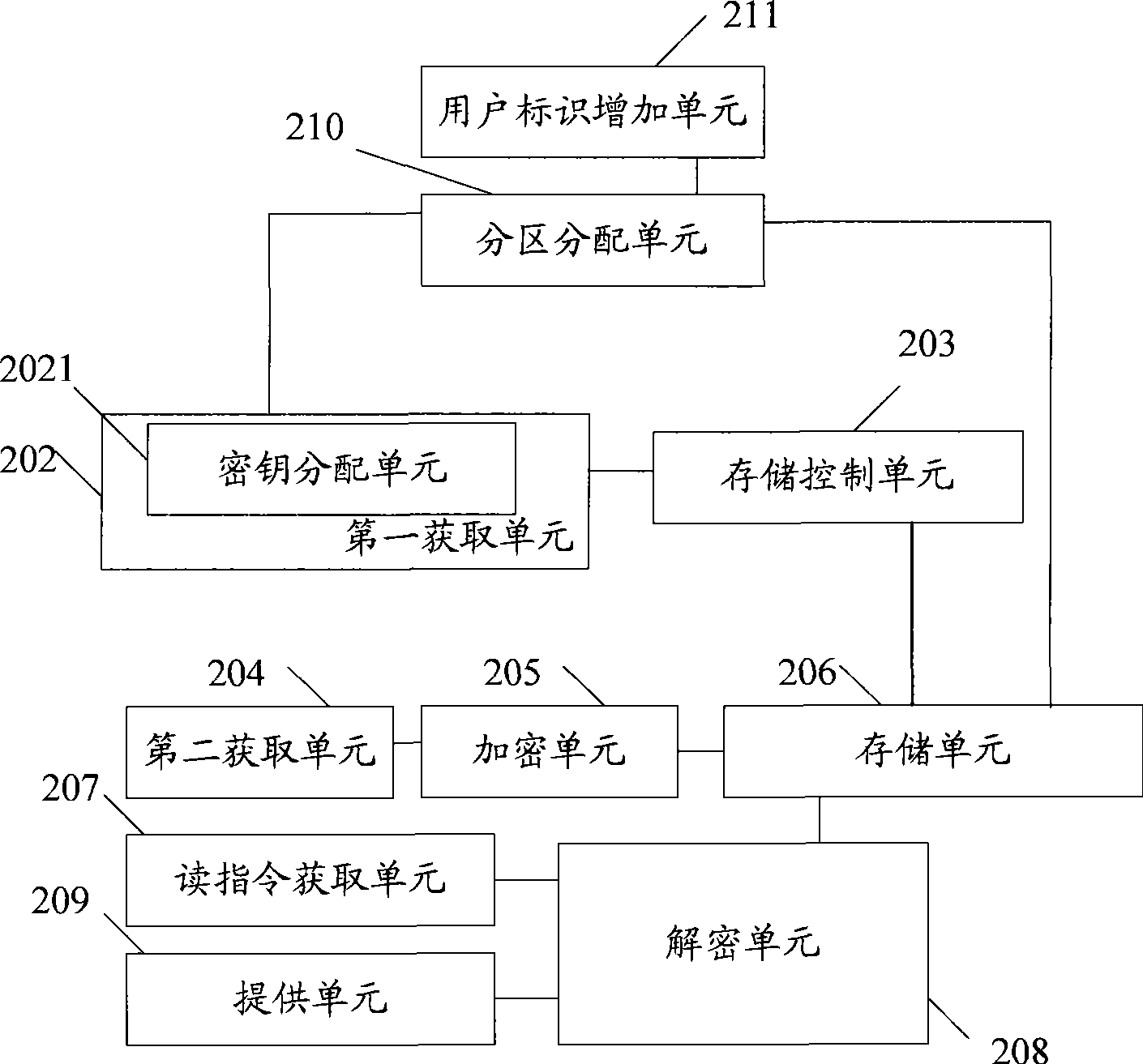
InactiveCN101488110AEnable secure sharingSafety protectionUnauthorized memory use protectionComputer hardwareEncryption
The embodiment of the invention discloses an encryption storage method and comprises the steps as follows: a user identification and a key corresponding to the user identification are obtained; and a user partition corresponding to the user identification is accessed with the key. The embodiment of the invention also provides a corresponding encryption storage device. Different users of the same storage device own respective different keys, and each key only can decrypt a corresponding encryption partition, so that the technical proposal of the invention can carry out safer protection towards a storage medium. Different keys are used for realizing the safety share of different users for different encryption partitions on the same medium.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
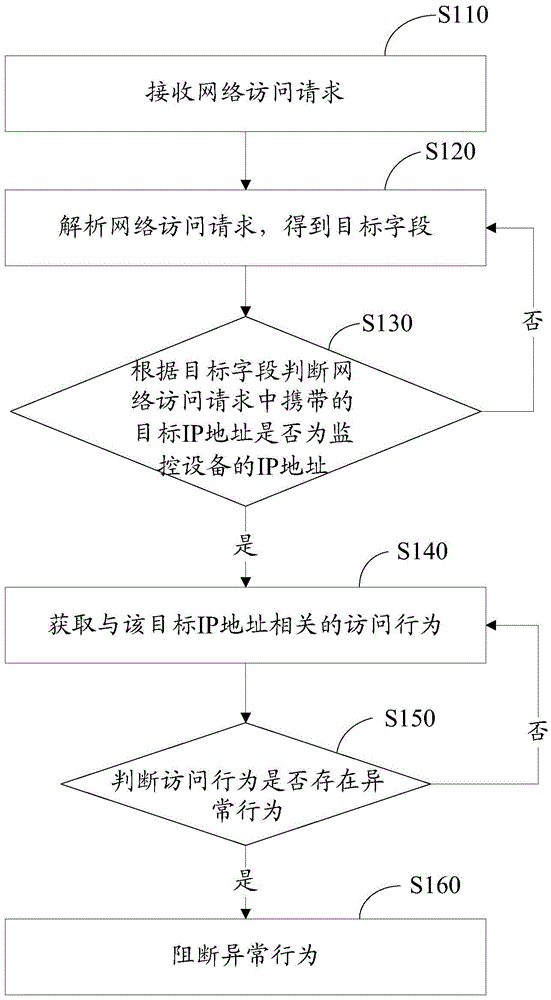
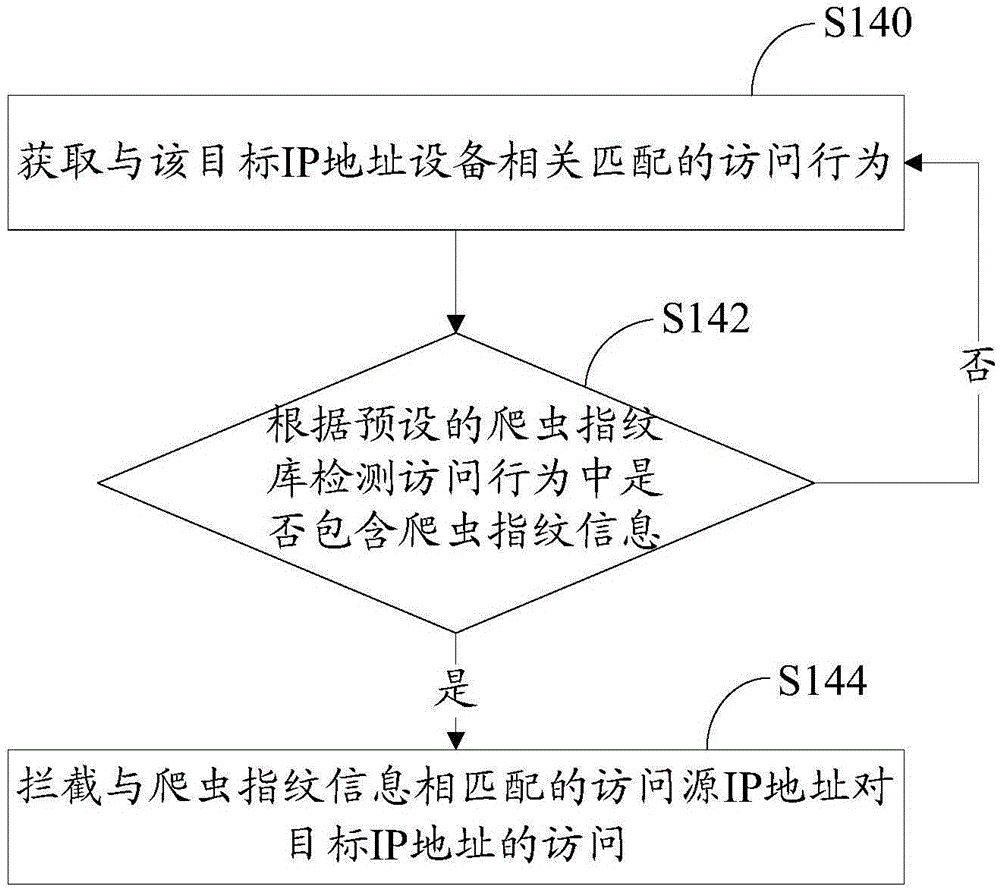
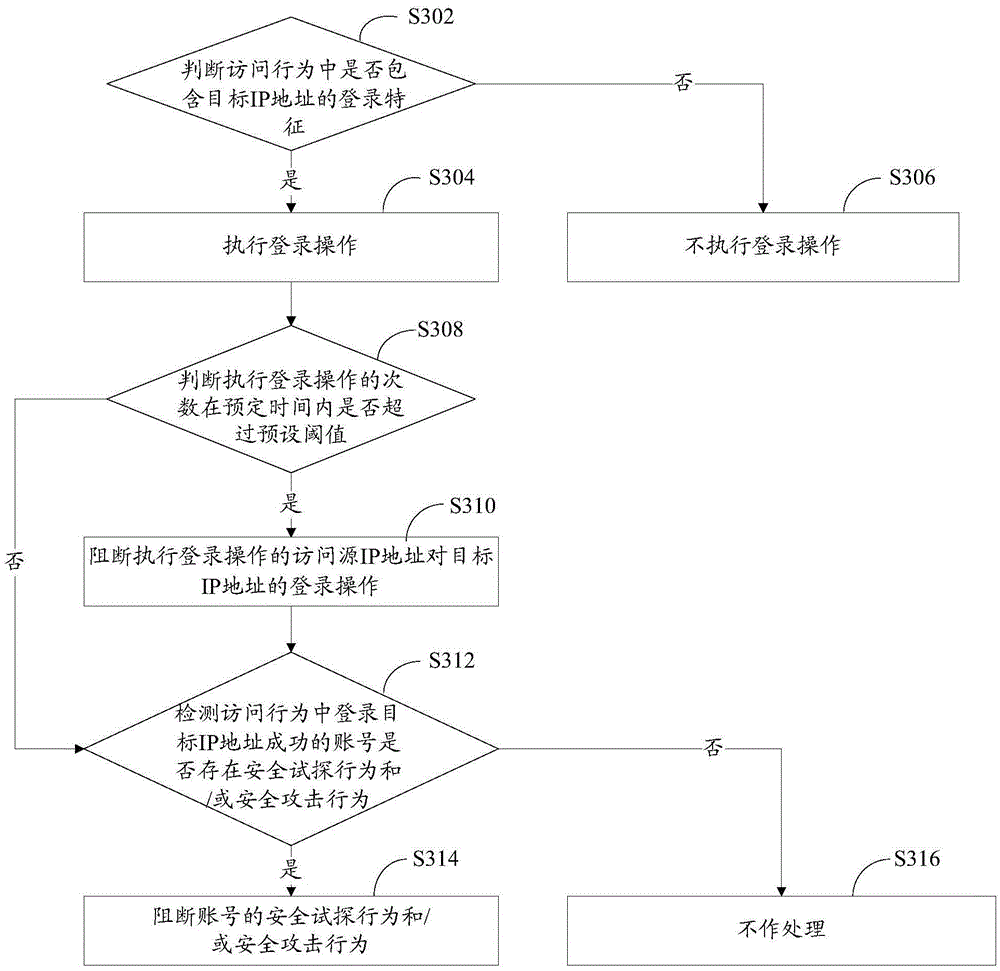
Security defense method and system of monitoring system
The invention relates to a security defense method and system of a monitoring system. The method comprises the following steps: receiving a network access request; analyzing the network access request to obtain a target field; judging whether a target IP address carried in the network access request is the IP address of a monitoring device according to the target field; if the target IP address is the IP address of the monitoring device, acquiring an access behavior related to the target IP address; judging whether the access behavior has abnormal behavior, if so, blocking the behavior. Through the adoption of the security defense method and system of the monitoring network, the abnormal behavior of an attracter to the monitoring device can be blocked, the security of the monitoring network is protected, and the security defense is performed on the monitoring network.
Owner:SANGFOR TECH INC
A double wheel arm locking type inspection robot mechanism
ActiveCN102263389AWalk fastImprove protectionMechanical energy handlingApparatus for overhead lines/cablesPressure transmissionLocking mechanism
The invention relates to an inspection robot and in particular relates to a double-wheel-arm locking type inspection robot mechanism which is capable of walking in a high pressure / ultrahigh pressure transmission line and is used for automatically inspecting and detecting transmission line facilities. The double-wheel-arm locking type inspection robot mechanism comprises front and back wheel arms which are mounted on a guide rail base and are of a same structure, wherein each wheel arm is composed of a walking obstacle-detouring mechanism, a lifting mechanism and a rotating mechanism; the walking obstacle-detouring mechanisms are located at the tops of the lifting mechanisms; the top ends of the rotating mechanisms are connected to the lower ends of the lifting mechanisms; the lower ends of the rotating mechanisms are fixedly connected to the guide rail base; a mass center adjusting mechanism is mounted on the guide rail base; a space, which is enclosed by the walking obstacle-detouring mechanisms, is used for enclosing a lead, thereby achieving a safe protective function; and at the obstacle-detouring moment, the walking obstacle-detouring mechanisms are lifted by the lifting mechanisms, the connecting rods of the walking obstacle-detouring mechanism rotate respectively under the action of an opening and closing motor, and the connecting rods are opened left and right so as toavoid an obstacle and pass by the side face of the obstacle, thereby realizing obstacle detouring. The double wheel arm locking type inspection robot mechanism is suitable for obstacles in different sizes and has the advantages of strong obstacle-detouring capacity, high safety, and the like.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Electronic equipment, and identification system and decryption method thereof
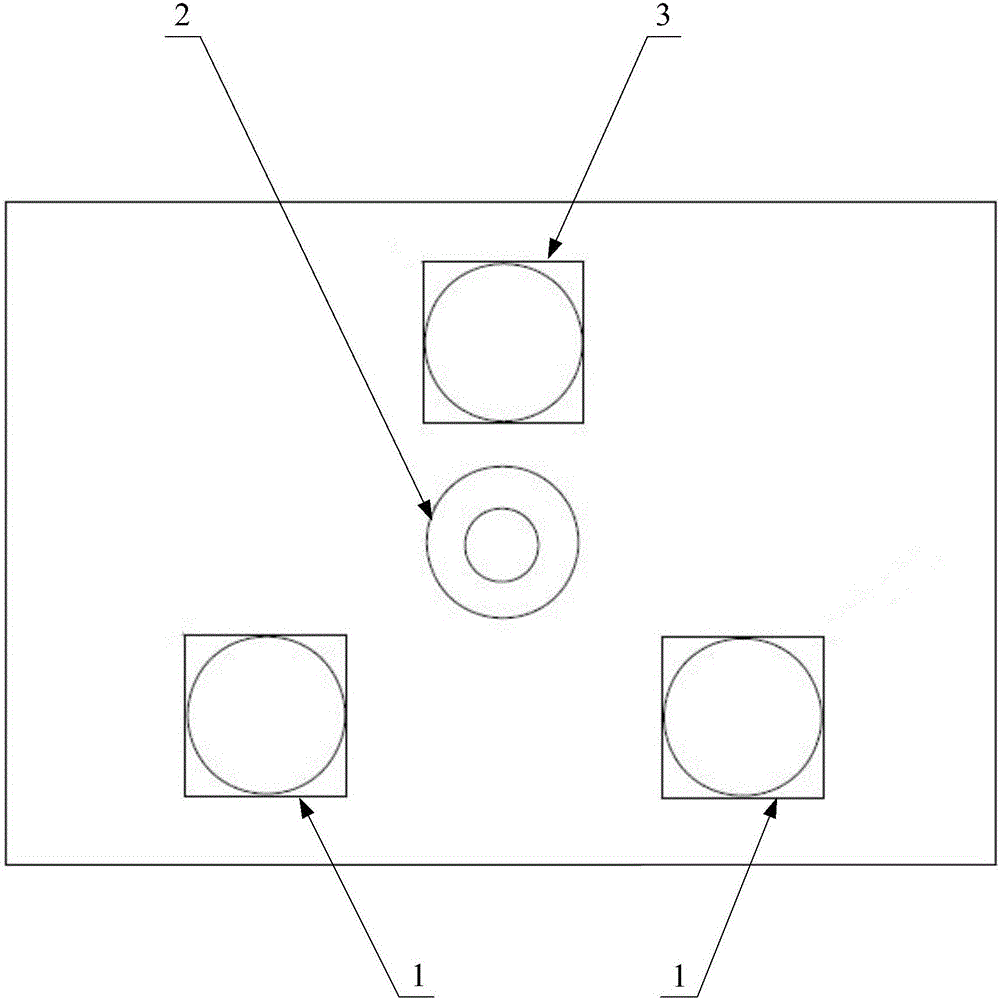
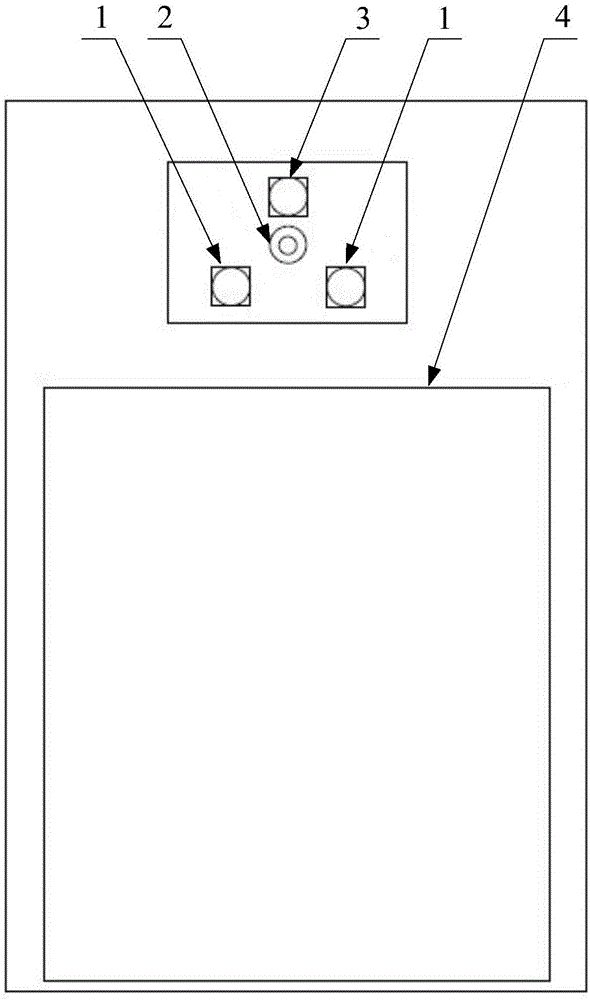
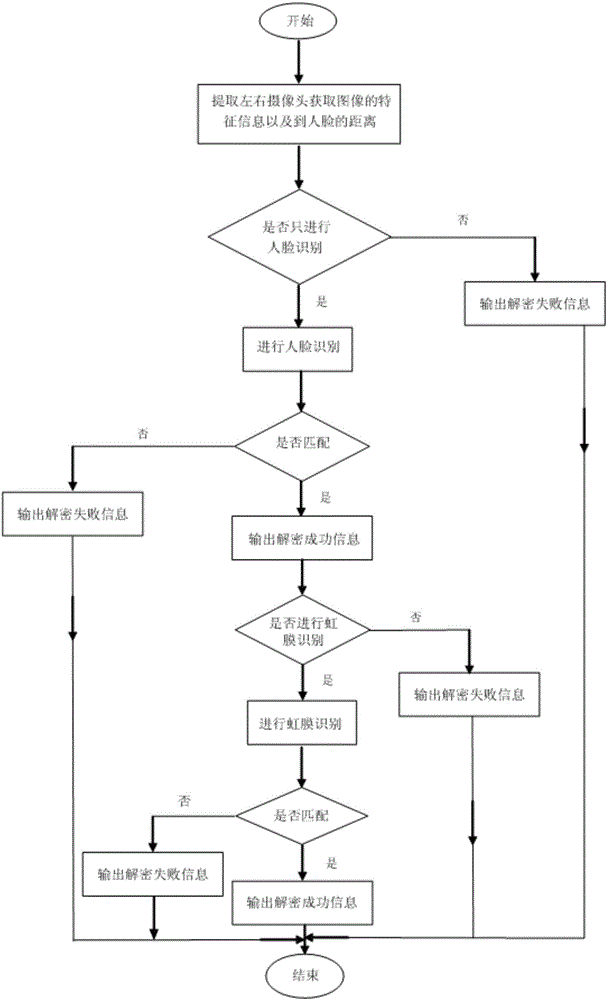
InactiveCN106485118ARealize 3D modelingImplement encryptionCharacter and pattern recognitionDigital data authenticationInfraredIris recognition
The invention discloses an identification system, which is used for being matched with a central processing unit of electronic equipment, so that three-dimensional modelling of a human face is realized. The identification system comprises multiple face shooting modules, an infrared light emitting device and an eye shooting module; the multiple face shooting modules are in signal connection with the central processing unit, and used for respectively shooting different parts of the human face, so that different facial information is obtained; the infrared light emitting device can emit infrared ray; and the eye shooting module is matched with the infrared light emitting device, and used for shooting eyes of a human, so that iris information is obtained. By means of the identification system provided by the invention, acquisition of three-dimensional information of a face can be realized through the multiple face shooting modules 1; furthermore, an iris identification manner is combined; compared with the manner of only acquiring two-dimensional information of the face by using a single camera, the security reliability and the robustness of the electronic equipment are relatively high; and the privacy of users can be protected more safely. The invention further relates to the electronic equipment having the identification system, and a decryption method for decrypting the electronic equipment.
Owner:TRULY OPTO ELECTRONICS
Variable magnetic flux motor drive system
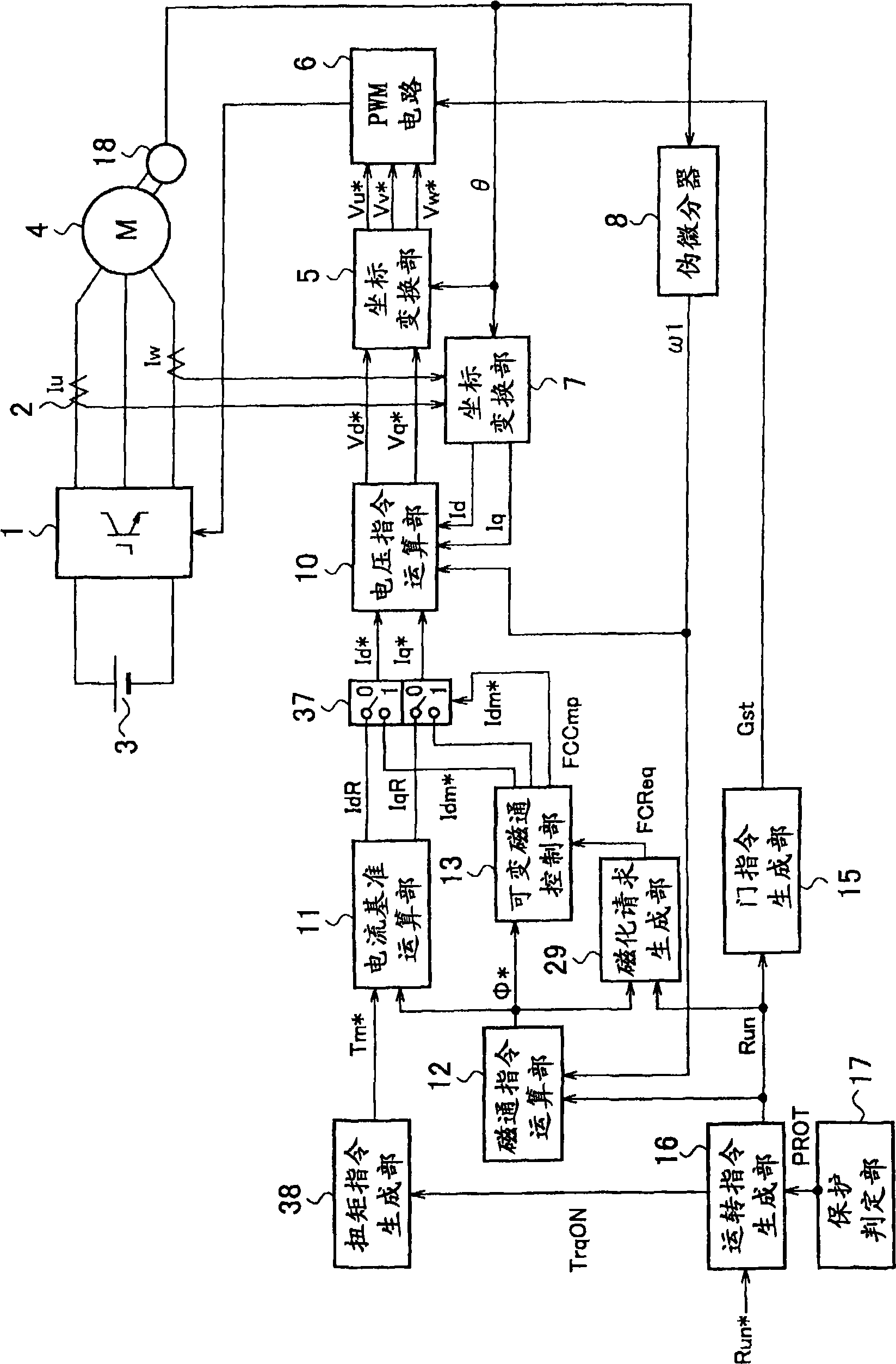
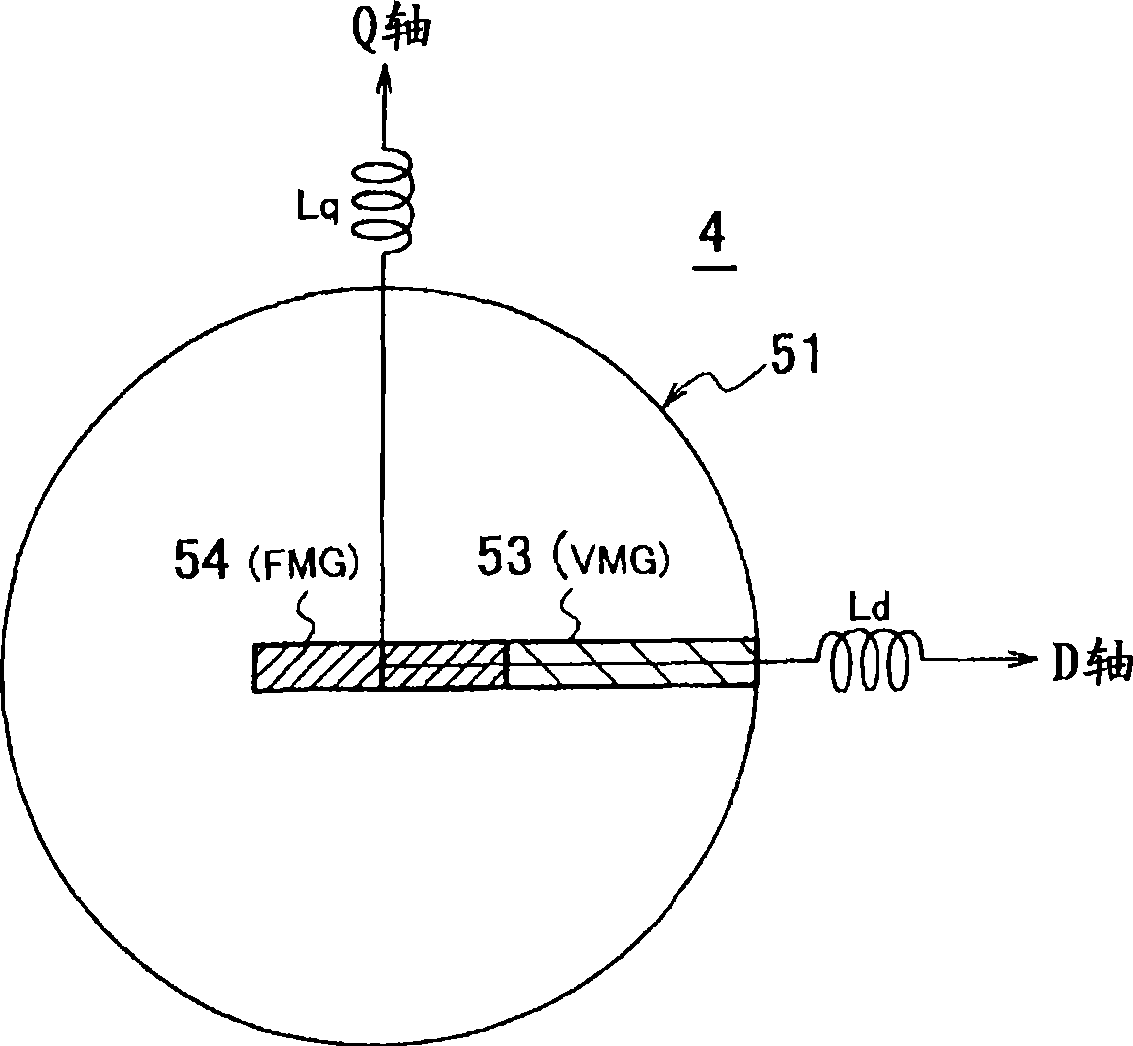
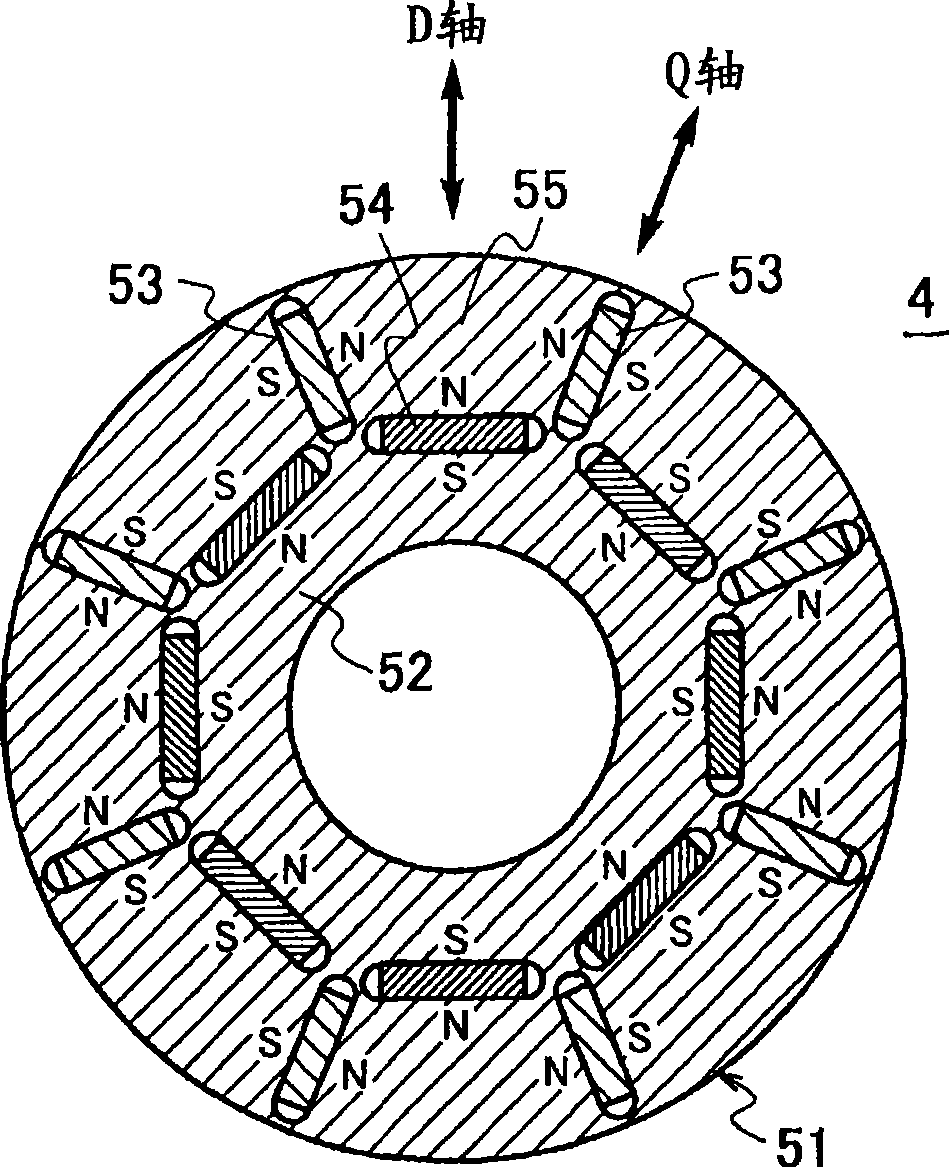
ActiveCN101490946APrevent application of braking forceSafety protectionMotor control for low load efficiencyMagnetic circuit rotating partsMotor drivePermanent magnet motor
The present invention provides a variable-flux motor drive system including a permanent-magnet motor 4 having a permanent magnet, an inverter 1 to drive the permanent-magnet motor, and a magnetize means to pass a magnetizing current for controlling the flux of the permanent magnet. The permanent magnet is a variable magnet whose flux density is variable depending on a magnetizing current from the inverter 1. The magnetize means passes a magnetizing current that is over a magnetization saturation zone of magnetic material of the variable magnet. This system improves a flux repeatability of the variable magnet 53 and a torque accuracy.
Owner:KK TOSHIBA
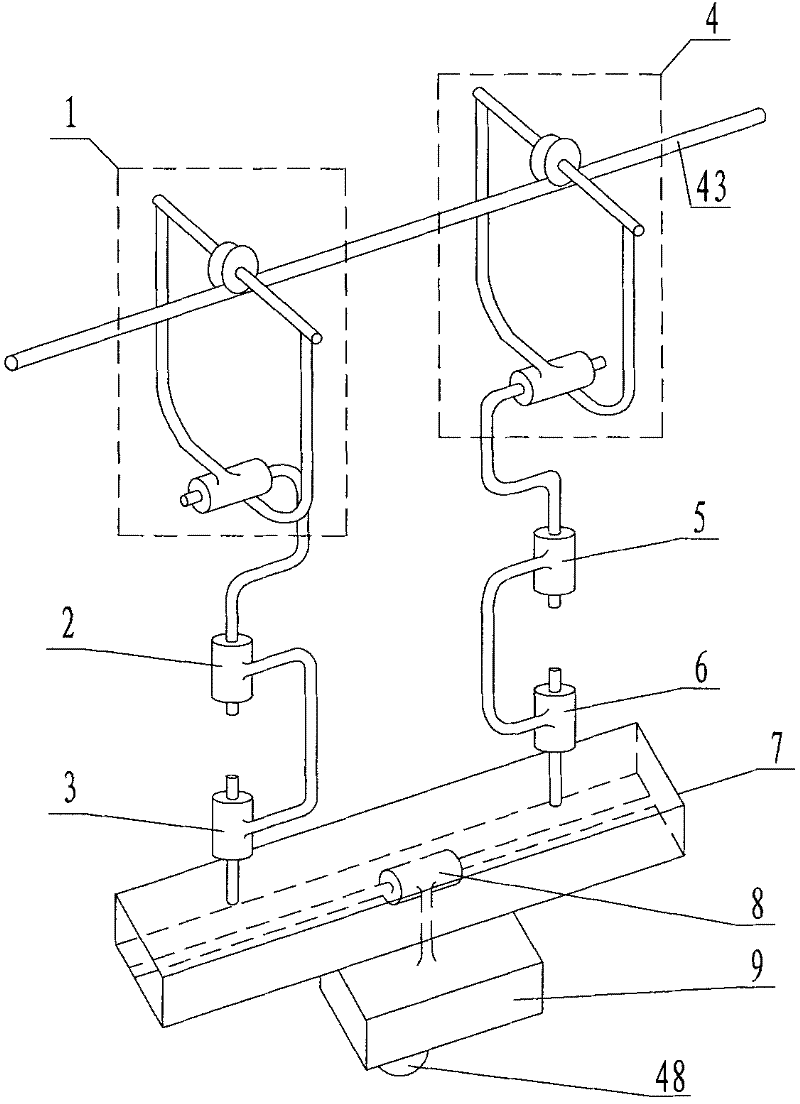
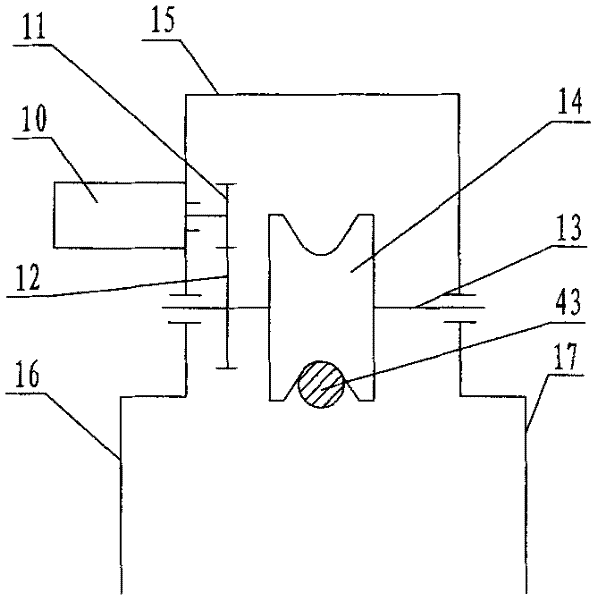
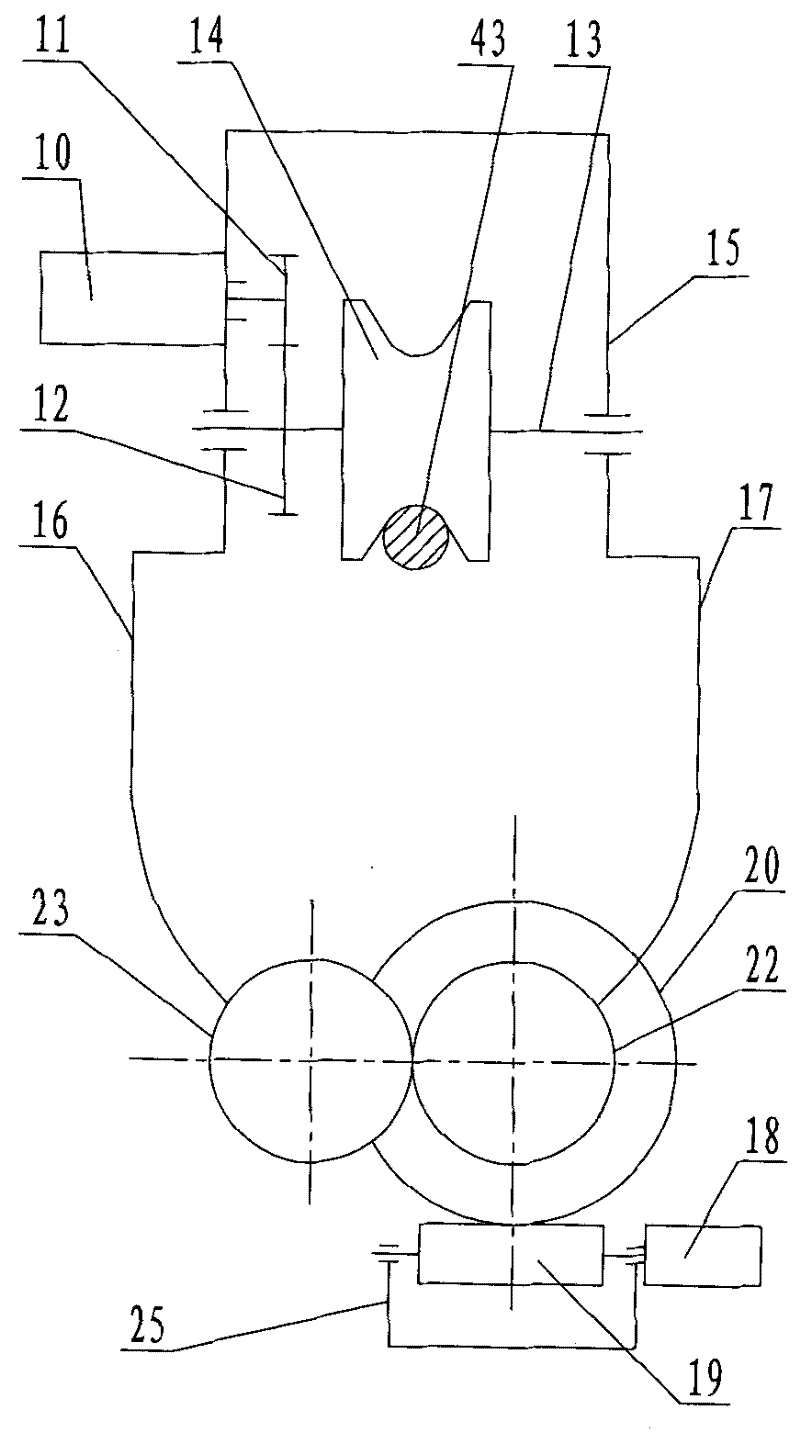
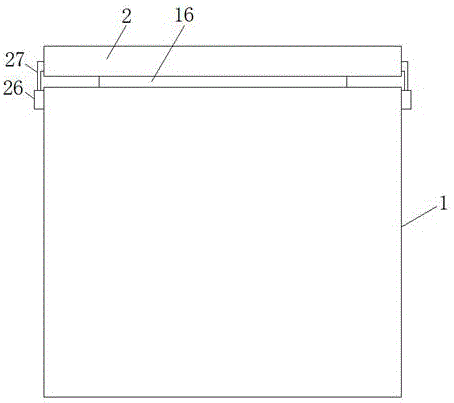
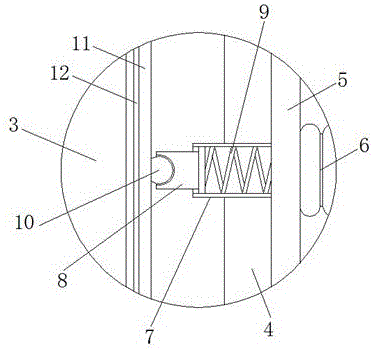
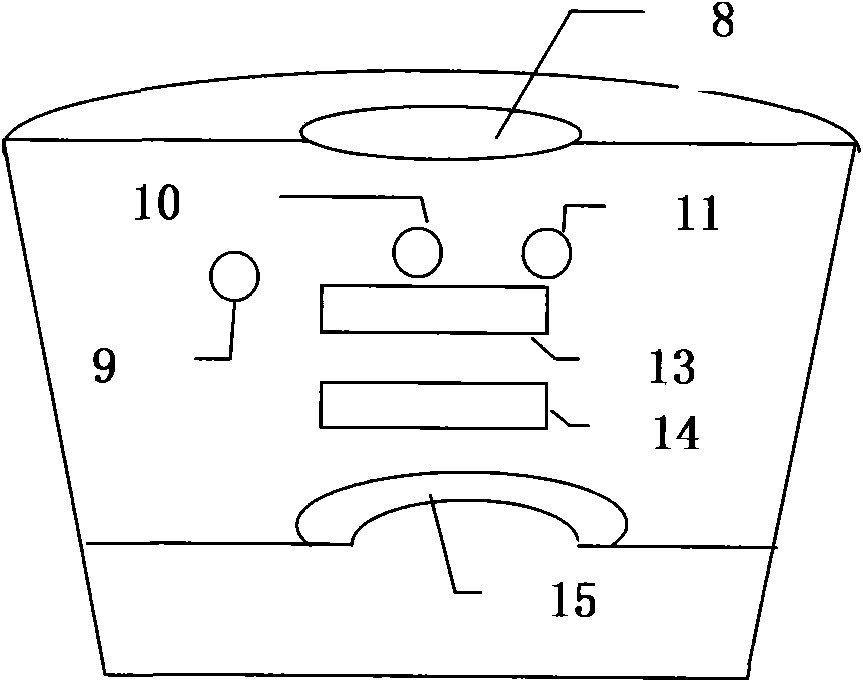
Intelligent protection method for automobile battery
The invention discloses an intelligent protection method for an automobile battery. Grooves (4), shock absorption protection plates (5), air springs (6), telescopic main pipes (7), telescopic support rods (8), horizontal shock absorption springs (9), positioning balls (10), positioning plates (11) and horizontal positioning shock absorption pads (12) can cooperate to effectively reduce impact force generated in the horizontal direction, thereby achieving the effect of effectively protecting a battery (3) and more effectively protecting the battery (3). According to the method, the impact force generated in the horizontal direction can be effectively reduced, so that the effect of effectively protecting the battery is achieved, and the battery can be protected more effectively; impact force generated in the vertical direction can be effectively reduced, thereby more effectively protecting the battery.
Owner:知运保(亳州)技术开发有限公司
Vacuum ejector pumps
Disclosed herein is a vacuum ejector pump operated by compressed air which flows in and out at high velocity, thus creating negative pressure in an outer surrounding space (S). The vacuum ejector pump includes a cylindrical nozzle body (2) and a cover (10). The nozzle body has at a predetermined position thereof an opening (3). One or more mounting nozzles (4, 5) are coaxially installed in the nozzle body and are visible through the opening (3). Holes (8) are formed in the wall of the nozzle body to allow the pump to communicate with the surrounding space (S). The cover functions to cover the opening of the nozzle body. Further, the pump includes flexible valve members (9) to open or close the holes, and fastening means (13, 14) to fasten the nozzle body to the cover.
Owner:KOREA PNEUMATIC SYST CO LTD
Switching type dc-dc converter
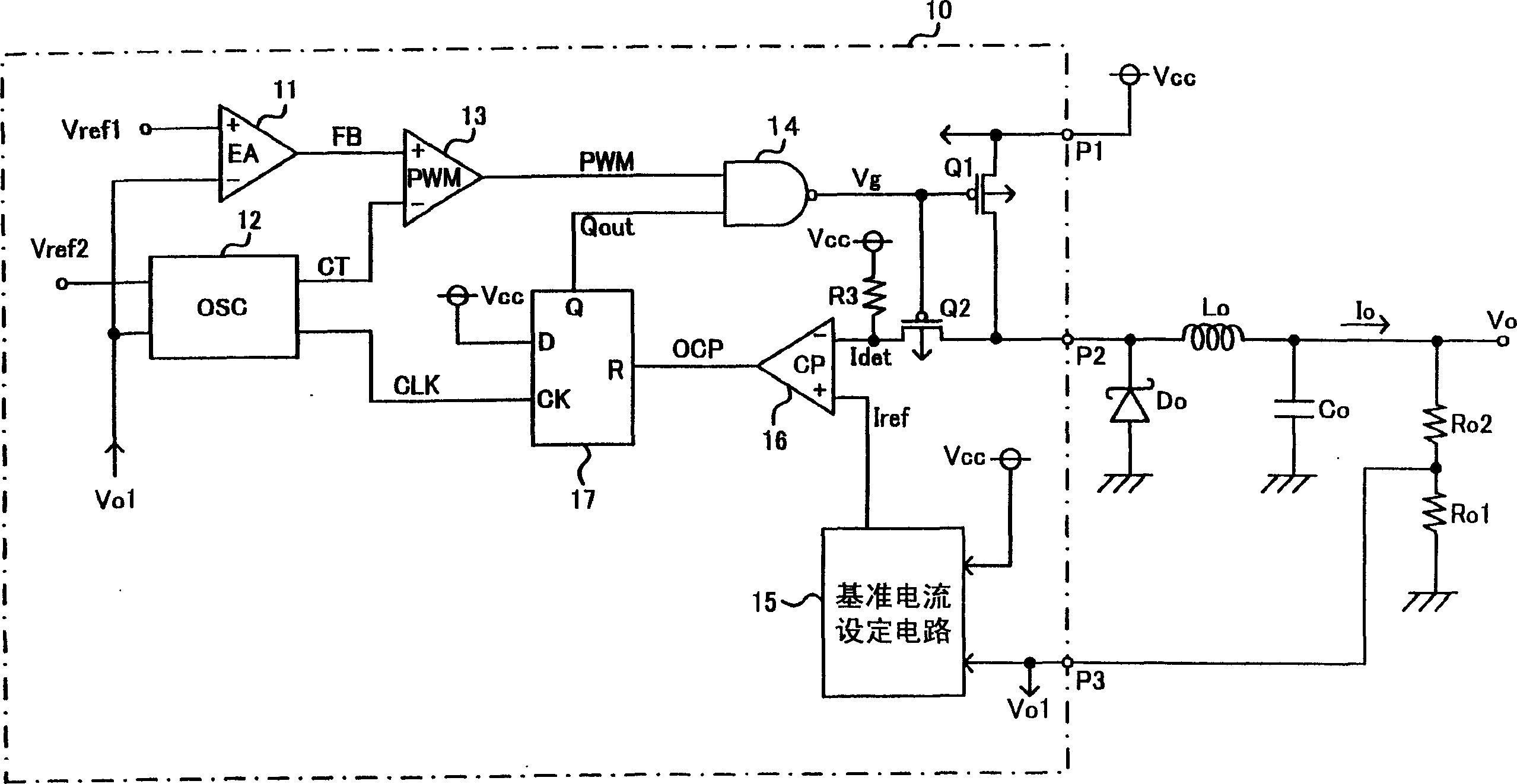
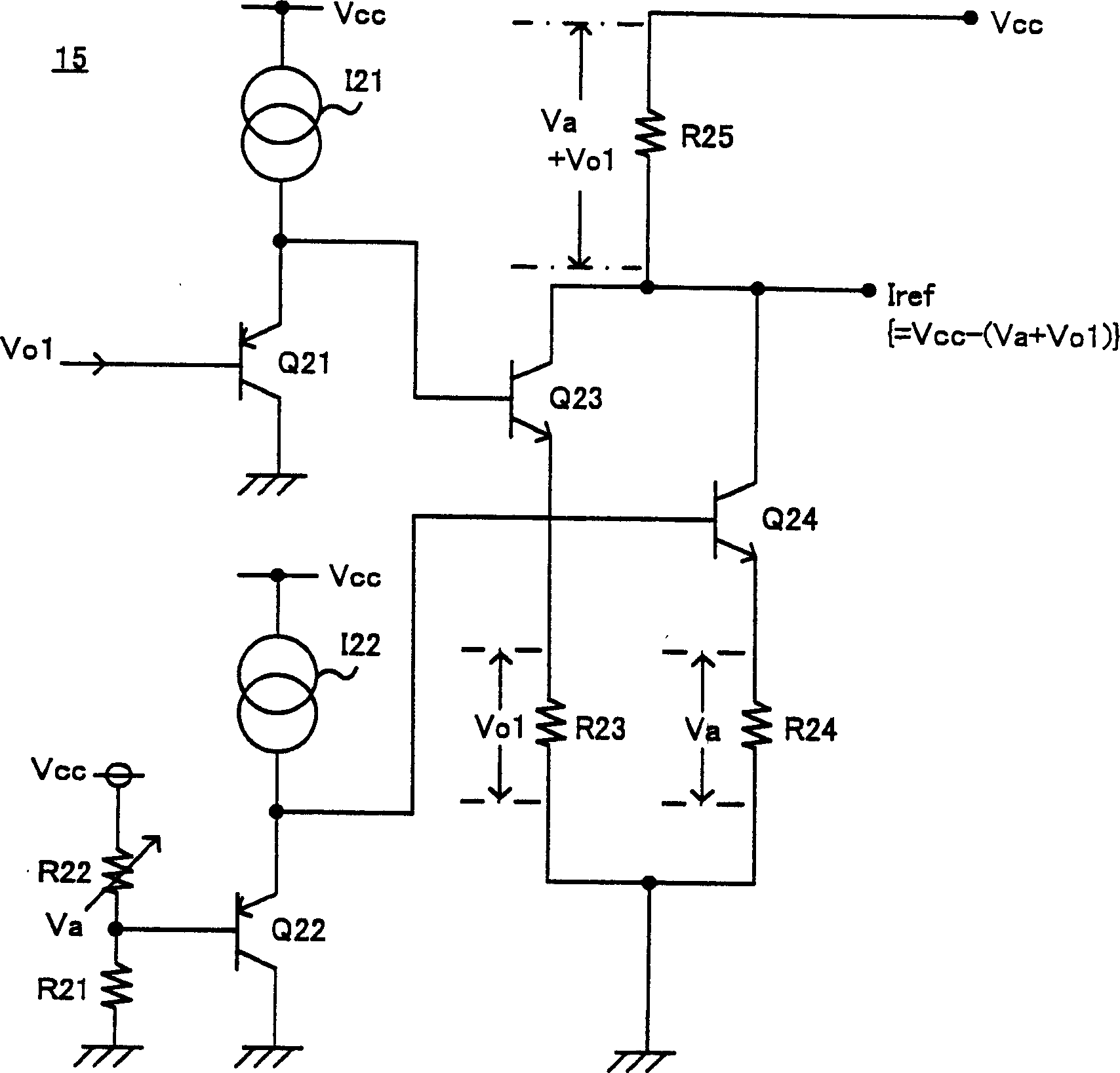
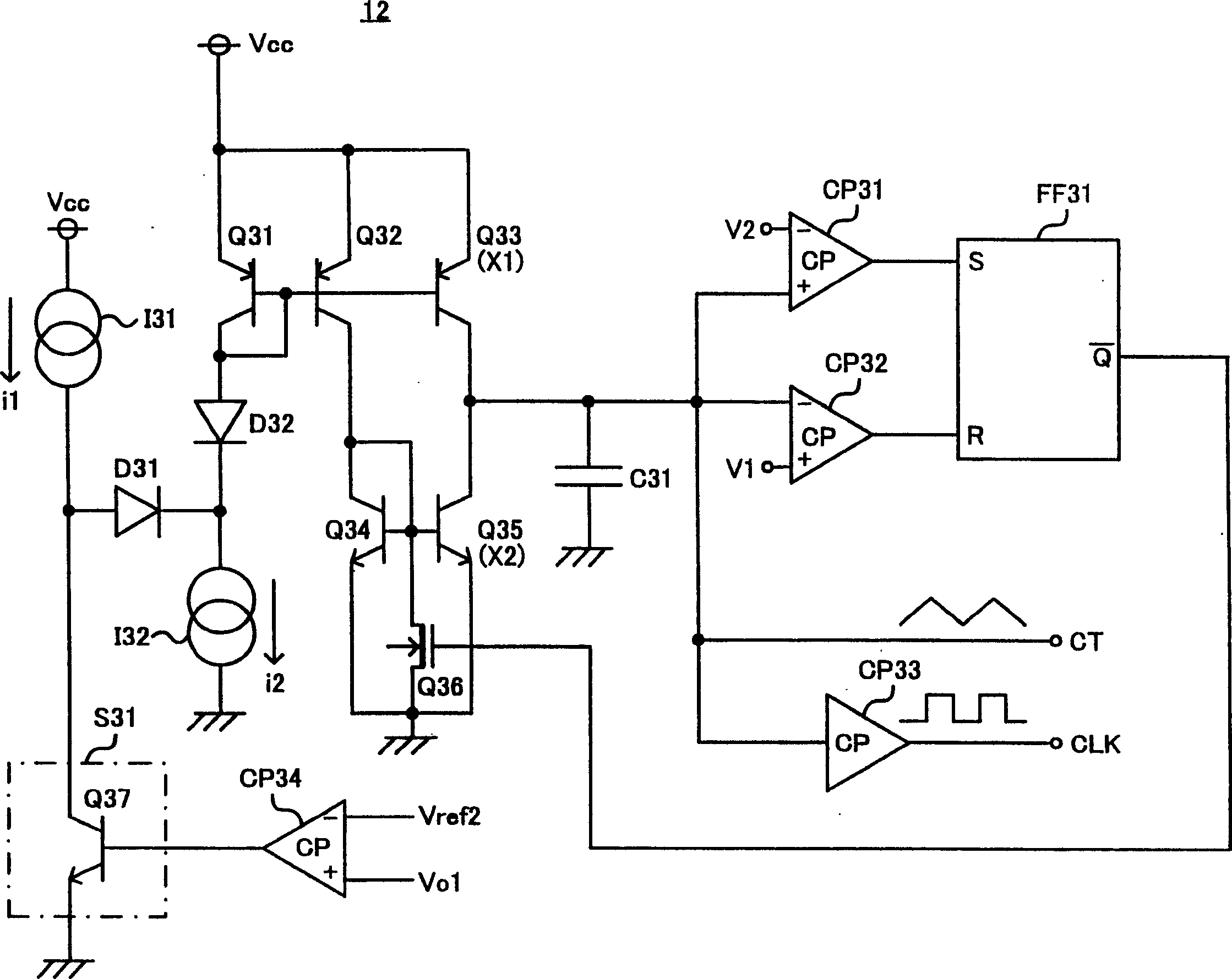
ActiveCN1574579ASafety protectionSmall currentApparatus with intermediate ac conversionEmergency protective arrangements for limiting excess voltage/currentCurrent limitingDc dc converter
Switching type DC-DC converter. To safely protect a power transistor or the like by realizing an overcurrent protection circuit of foldback current limiting characteristics with a simple configuration, related to a DC-DC converter which controls a DC input voltage by on / off switching of a power transistor for outputting a prescribed DC constant voltage. An inventive switching type DC-DC converter is adapted to set a protective reference current level lower for a decreased output voltage, and stop the switching control signal supplied to a switching transistor circuit when the detected current level exceeds the protective reference current level. In addition, in case where the output voltage declines due to, for example, a circuit failure such as short-circuiting, the switching period of the switching transistor circuit is extended. Thus, the switching type DC-DC converter is provided with a foldback current limiting type protection characteristic through reduction of the protective reference current level and extension of the switching period of cycle.
Owner:ROHM CO LTD
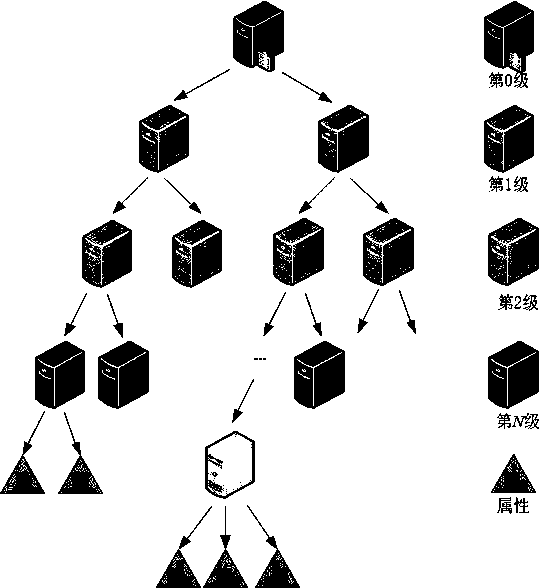
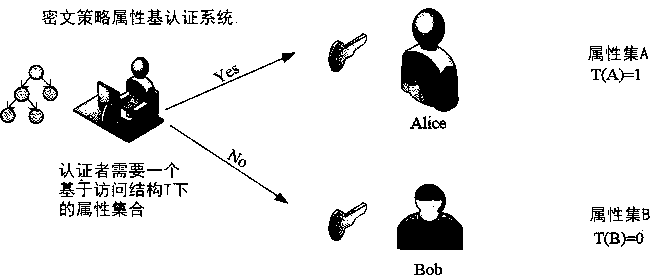
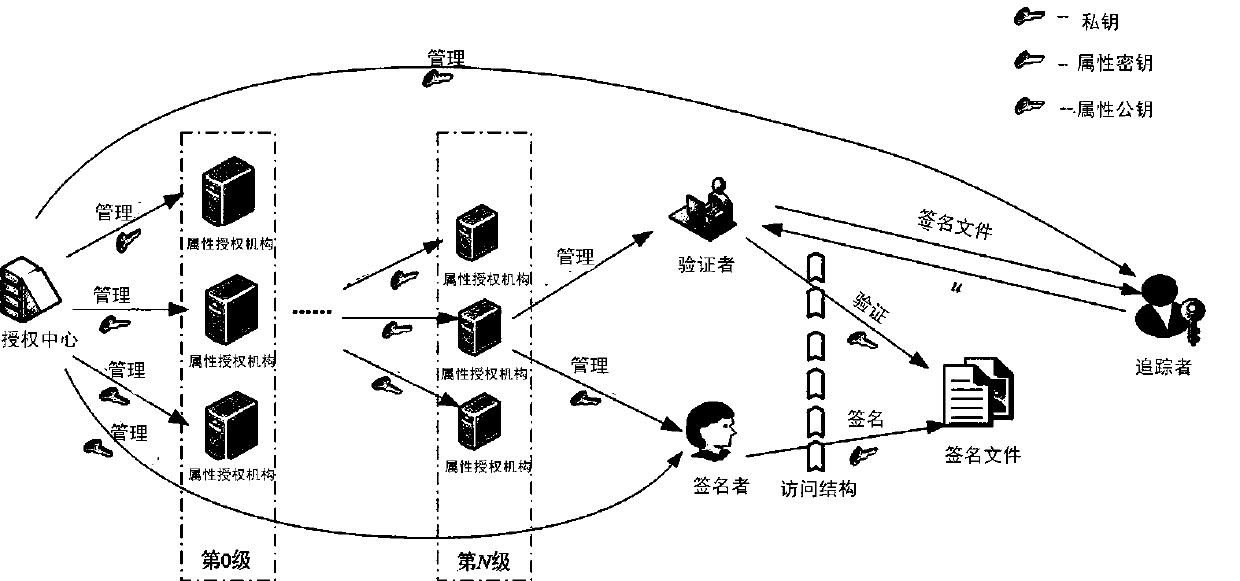
Traceable layered multi-authorization ciphertext policy attribute base authentication method
ActiveCN110113156AWon't leakSafety protectionKey distribution for secure communicationUser identity/authority verificationUser privacyAuthorization
The invention relates to a traceable layered multi-authorization ciphertext policy attribute base authentication method. A central authorization mechanism generates a main public / private key of a system, a private key of a zero-level authorization mechanism and a private key of a signer; the upper-level attribute authorization mechanism authorizes the next-level attribute authorization mechanism,and the attribute authorization mechanisms of different levels can generate attribute keys for signers according to the managed attribute sets and then send the attribute keys to the signers; a signerin the system owns a private key and an attribute key, signs a message by using the attribute key of the signer, and sends signature information of the message to a verifier; the verifier verifies whether the signature is valid or not by using the attribute public key of the signer; when there is a dispute in the system, the tracker is responsible for recovering the identity information of the signer from the signature. According to the method, the privacy of the user can be protected, collusion attacks of multiple authorization mechanisms can be resisted, and the method is safe and efficient.
Owner:FUJIAN NORMAL UNIV
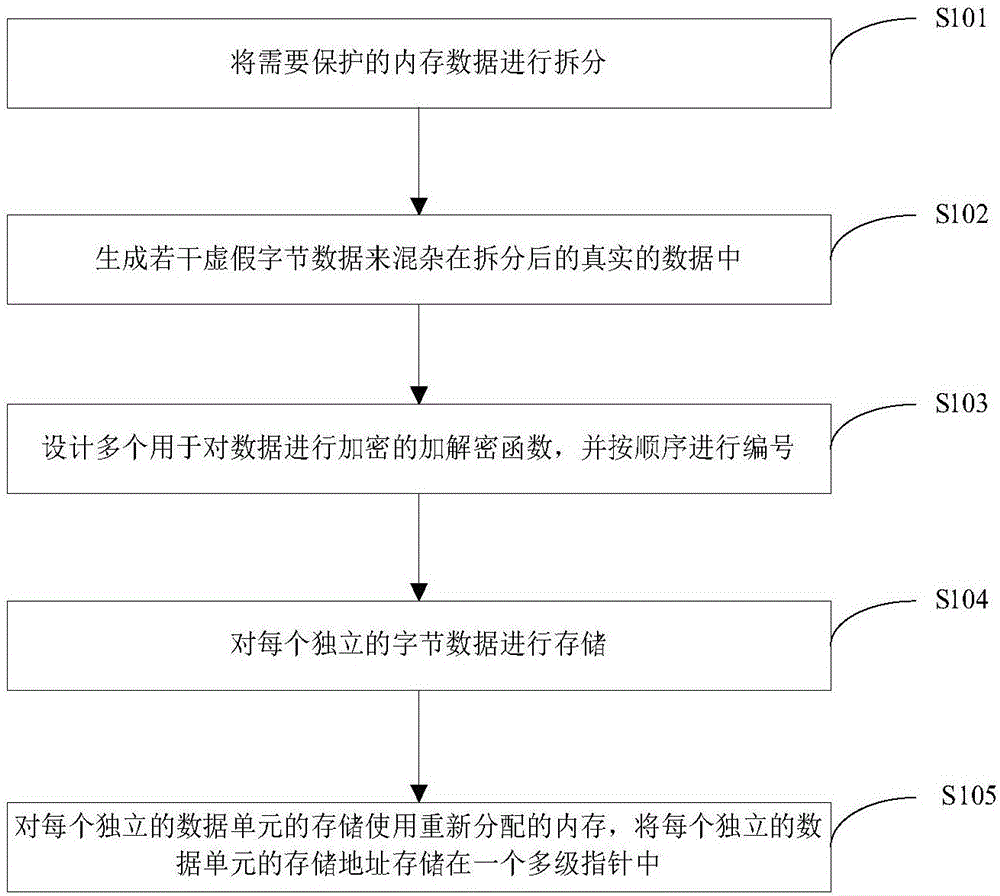
Secure memory data protection method and device
ActiveCN106598882ASafety protectionPlay a role in confusingUnauthorized memory use protectionDigital data protectionReverse analysisByte
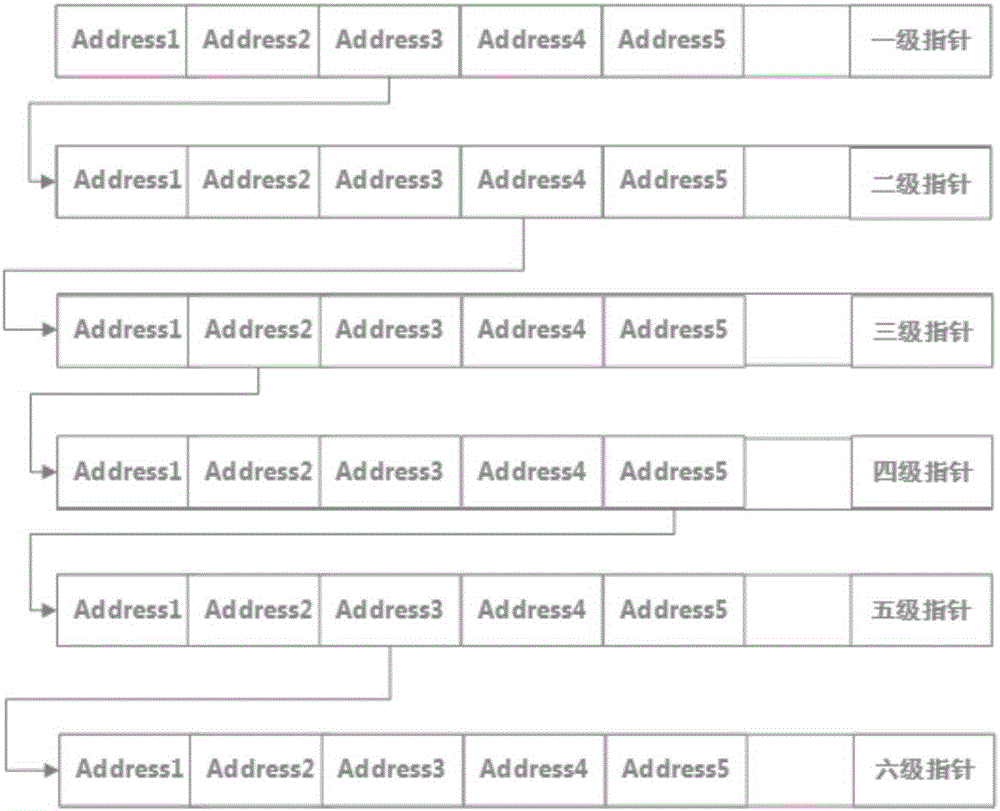
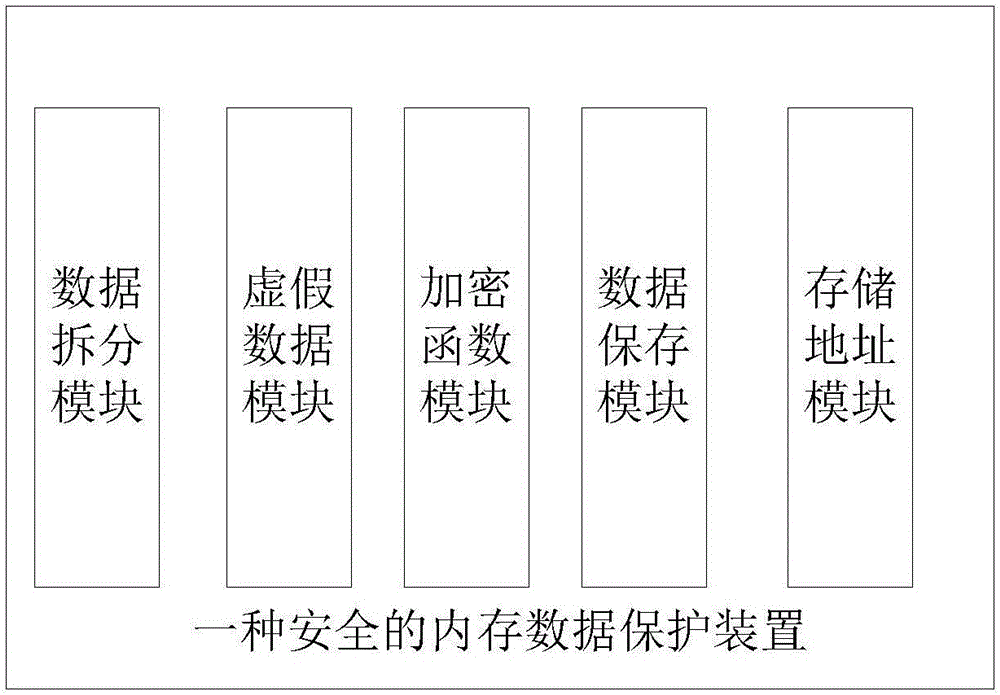
The invention discloses a secure memory data protection method and device. The method comprises the following steps: (1) splitting memory data to be protected into independent byte data one by one; (2) generating a plurality of false byte data, and mixing into split real data; (3) designing a plurality of encryption and decryption functions for encrypting the data, and numbering the functions in sequence; (4) storing each independent byte data, wherein a storage format includes the following field information; and (5) storing each independent data unit with a redistributed memory, and storing a storage address of each independent data unit into a multilevel pointer. The secure memory data protection method is designed under the consideration of data encryption from an angle of inconvenient HACK reverse analysis, so that the data can be protected more securely, and the method is easy to implement.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Interface control method, electronic device and computer readable storage medium
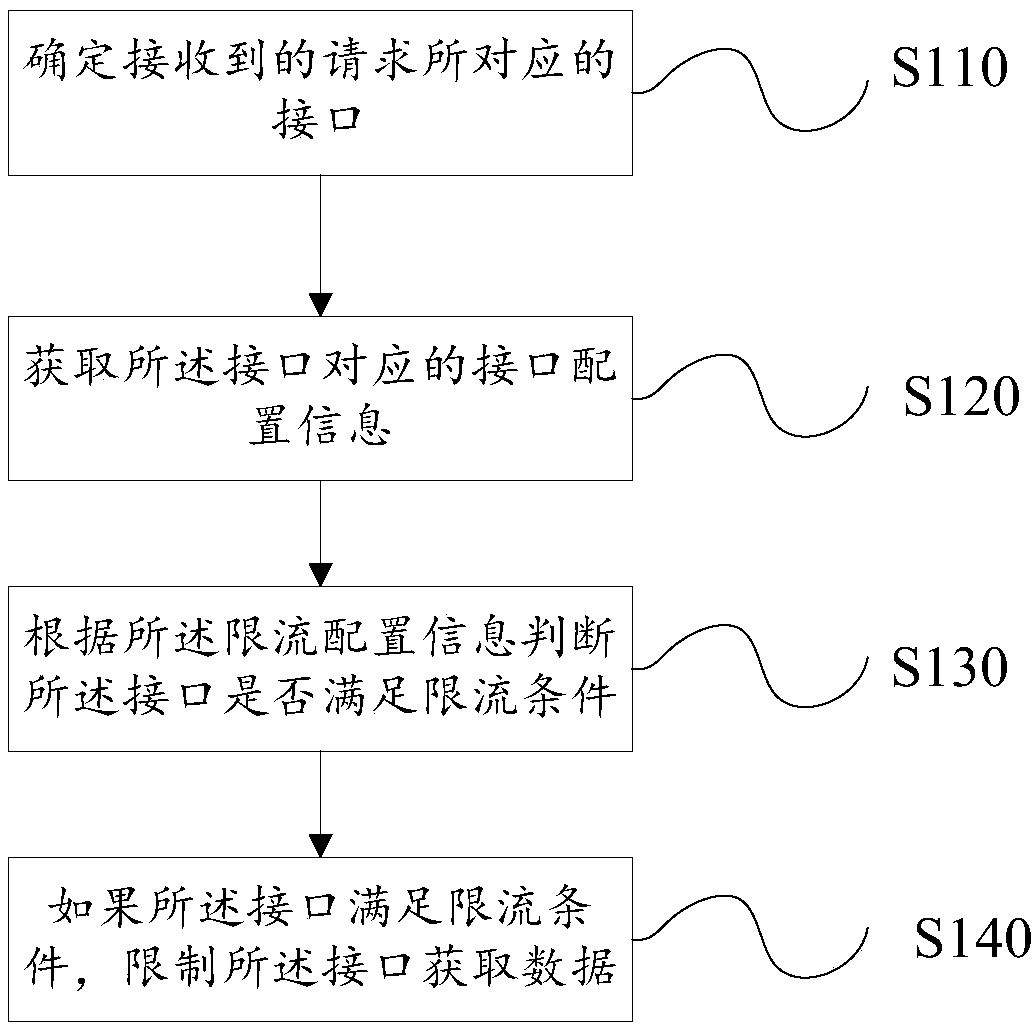
InactiveCN108566304ASolve the technical problem that flexible custom current limit control cannot be performedFlexible and convenient interface current limiting functionData switching networksCurrent limitingSystem protection
The present invention provides an interface control method, an electronic device, and a computer readable storage medium. The interface control method comprises the following steps: determining an interface corresponding to a received request; obtaining the interface configuration information corresponding to an interface, the interface configuration information at least includes current limitingconfiguration information; judging, according to the current limiting configuration information, whether the interface meets a current limiting condition or not; if the interface meets the current limiting condition, limiting the interface to obtain data, which solves the technical problem that the existing system cannot meet the multi-interface unified current control and cannot carry out flexible custom current limiting control, realizes the more flexible and convenient multi-interface current limiting function, and effectively provides a technical effect of more secure system protection.
Owner:NUBIA TECHNOLOGY CO LTD
Identification presentation device as well as identification recognition method and identification recognition system based on same
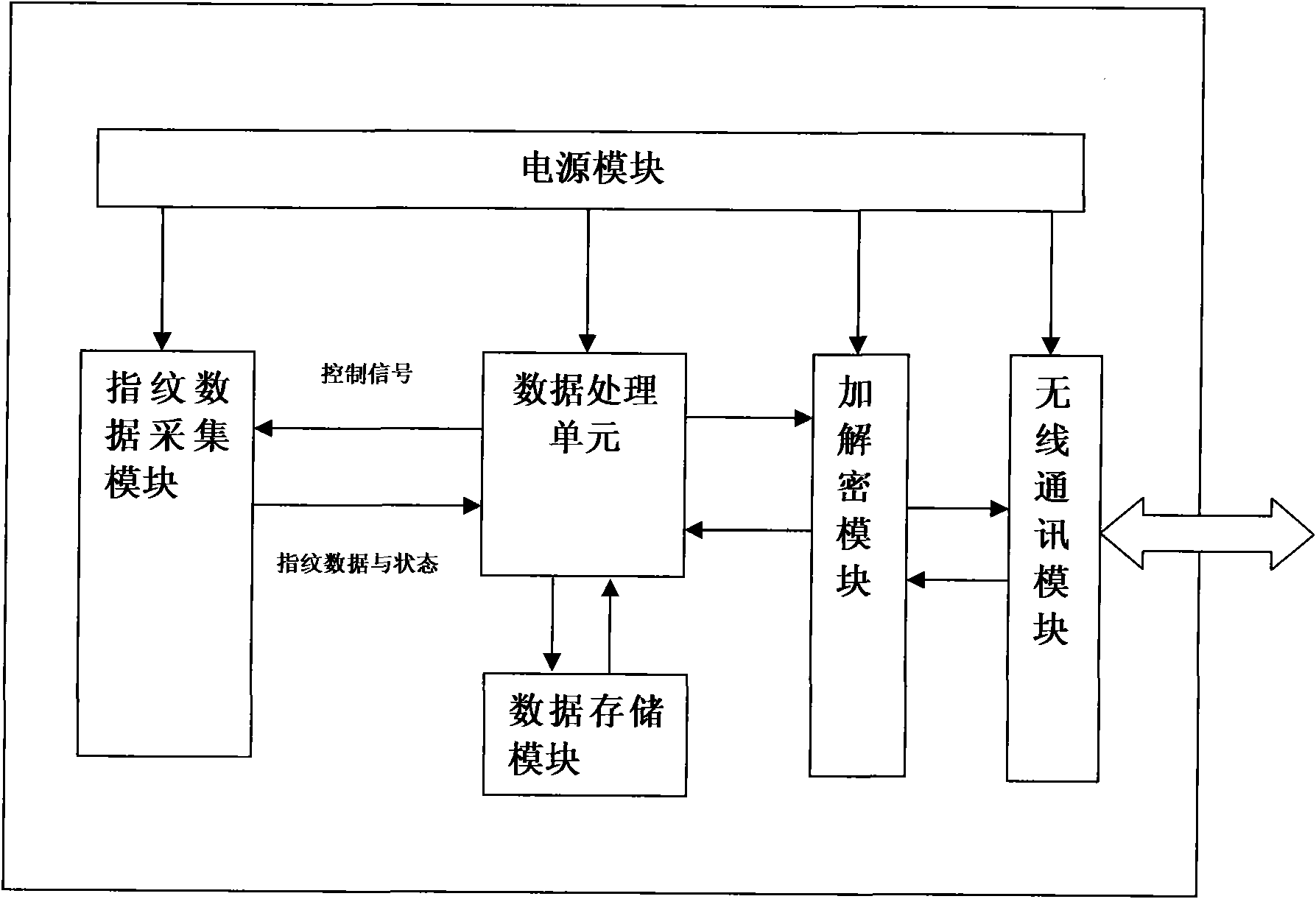
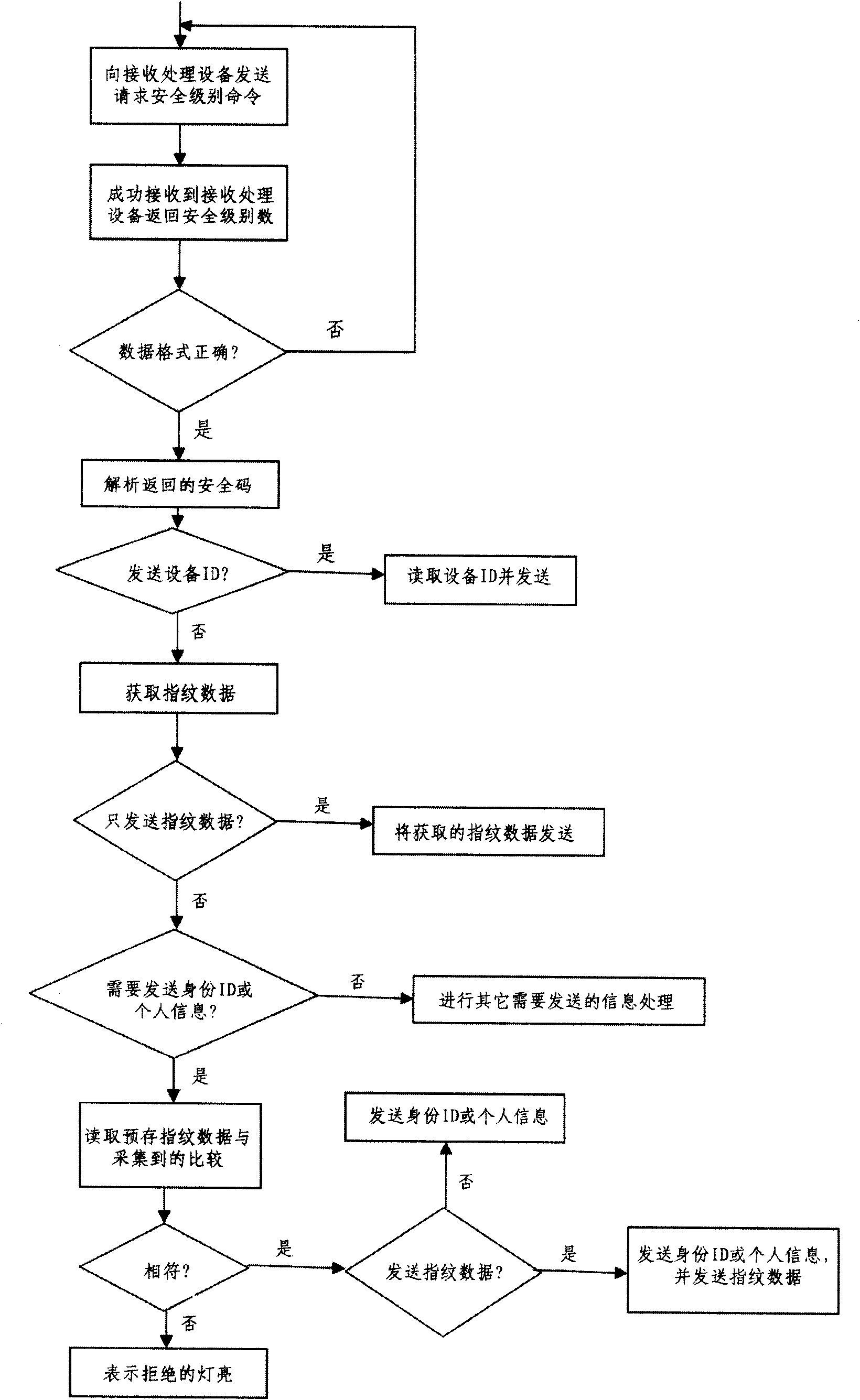
InactiveCN101615309ASafety protectionEasy to operateIndividual entry/exit registersTransmissionData acquisitionData acquisition module
The invention discloses an identification presentation device which is simultaneously suitable for different identification presentation occasions, is more convenient to operate and comprises a power supply module, a wireless communication module, a fingerprint data acquisition module, a data storage module and a data-processing unit. The invention also discloses an identification recognition method which is based on the identification recognition device, simultaneously satisfies different identification presentation occasions and has high recognition efficiency and good safety. The invention also discloses an identification recognition system for realizing the identification recognition method. The technical scheme of the invention can remotely operate identification recognition and selectively confirm identification information needed for recognition so that the same equipment can be used for the same operation on various occasions needing identification recognition, the operation is more convenient and rapider, the protection of the identification information is safer, and the recognition efficiency is greatly improved on an occasion when more people are on the scene.
Owner:张小鹏
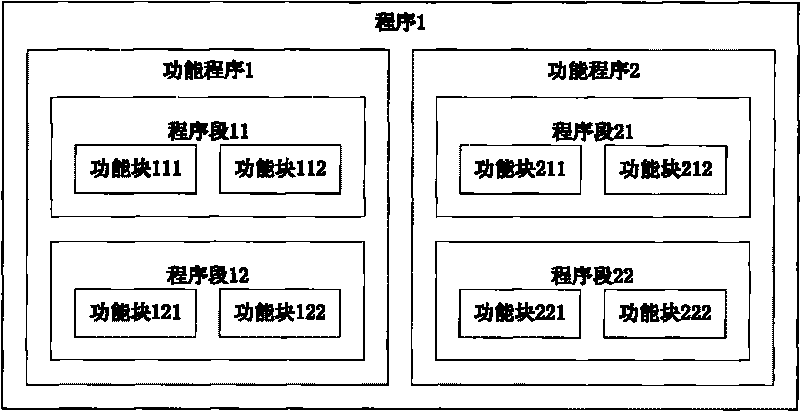
PLC program protection method, access method and device thereof
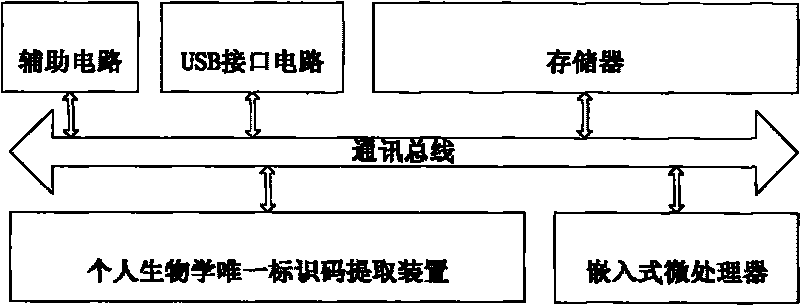
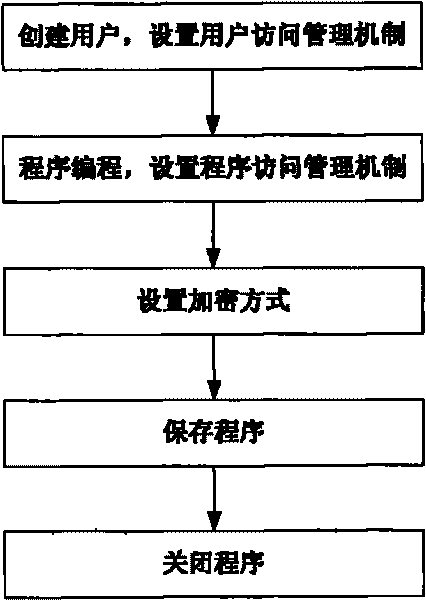
InactiveCN101697188ASafety protectionImprove protectionDigital data authenticationProgramme control in sequence/logic controllersAccess methodEncryption decryption
The invention discloses a PLC program protection method, an access method and a device thereof. The PLC program protection method comprises the following: step A, creating users and setting user access management mechanisms; step B, programming and setting program access management mechanisms; step C, setting encryption modes; and step D, saving programs. The invention also discloses a device for implementing the PLC program protection method. The device comprises an embedded microprocessor connected with a communication bus, a memory, an extraction device for personal biological unique identification codes, a USB interface circuit and an auxiliary circuit. The invention can provide security protection for PLC programs and prevent the illegal access of unauthorized people to the programs. Due to hardware devices and symmetric encryption-decryption algorithms, the programs are not easy to crack and can be further protected.
Owner:CISDI ENG CO LTD
Safety anti-vibration bed
The invention relates to a safety anti-vibration bed, which comprises two head cylinders respectively mounted at the center of each head support, wherein, the outer ends of piston rods of cylinders are connected with lifting sliding plates; two bed supports are divided into left and right parts symmetry via the cylinders, while each part comprises upright track, half part of lifting sliding plate, arc plate lifting turnover device and bed lifting device; the upright track is fixed at the bed support near the cylinder; the block of lifting sliding plate can move up and down along the upright track; the arc plate lifting turnover device comprises a U-shaped swing arm and an axle sheath fixed on the upright track; the bed lifting device comprises a drawing rod, a small swing arm, a bed lifting swing arm, and a bed frame. The left and right arc plates can form arc protection above the bed, when the bed plate falls to the bottom, the people can be hurt little.
Owner:王树庆
Technology for dyeing textile by means of plant dyes
The invention belongs to the technical field of printing and dyeing and particularly relates to a technology for dyeing textiles by means of plant dyes. The textiles can be yarn or fabrics and can be made of cotton fiber, bamboo fiber, viscose and chemical fiber modified fiber. The textiles with impurities removed through pretreatment are washed with water and then subjected to normal-temperature dip dyeing and modification, then the plant dyes are used for dip dyeing, and then after-treatment is conducted to obtain dyed textiles. Original plant resources are used for dyeing textile fabrics, so that the fabrics completely get rid of damage of toxic chemical dyes, can be recycled and do no harm to the environment and human beings, the production process is short, and products are stable. Compared with chemical products, cost is low. Compared with other plant dye dyeing technologies, colors are more uniform and dyeing defects are not likely to happen in dyeing application of most plants, color fastness is higher, and accordingly the technology has a very wide prospect in actual application.
Owner:杨江源
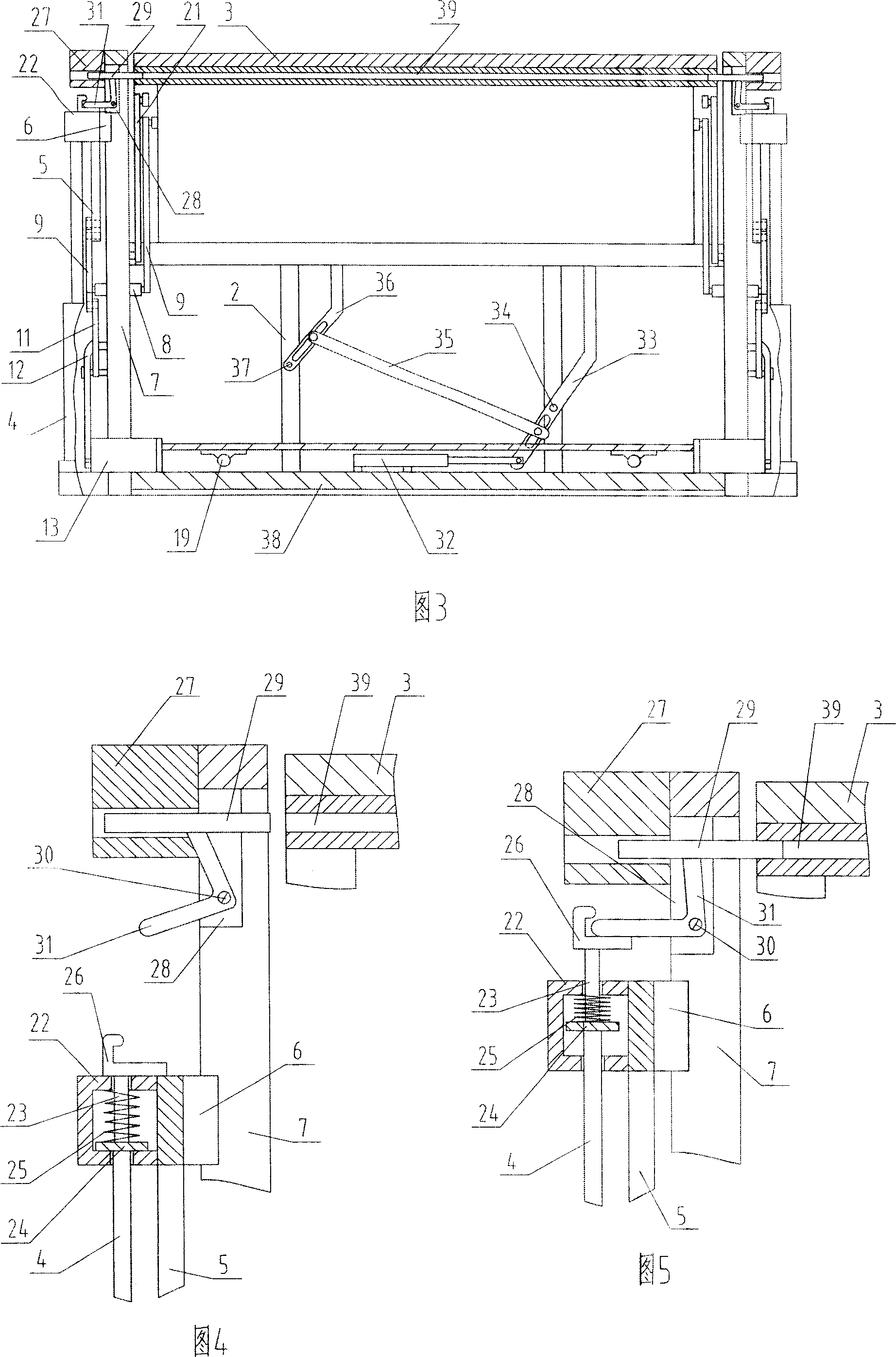
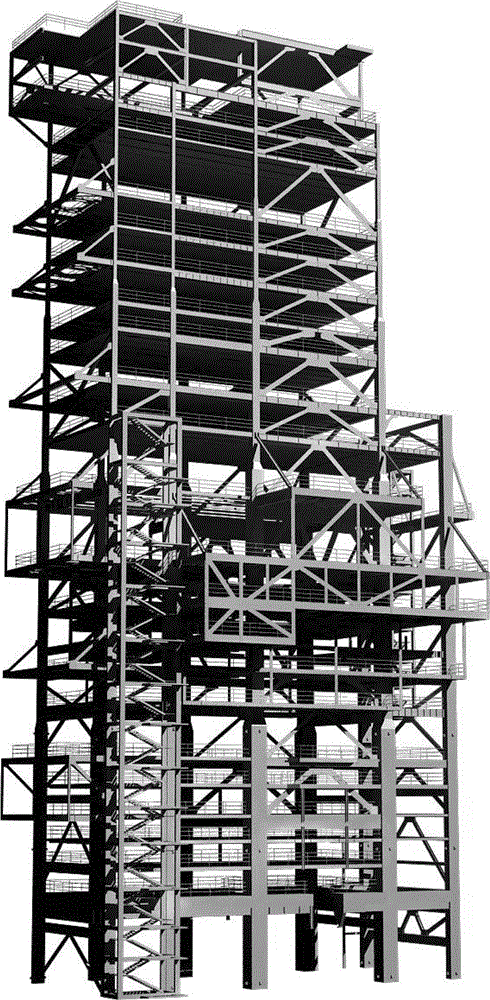
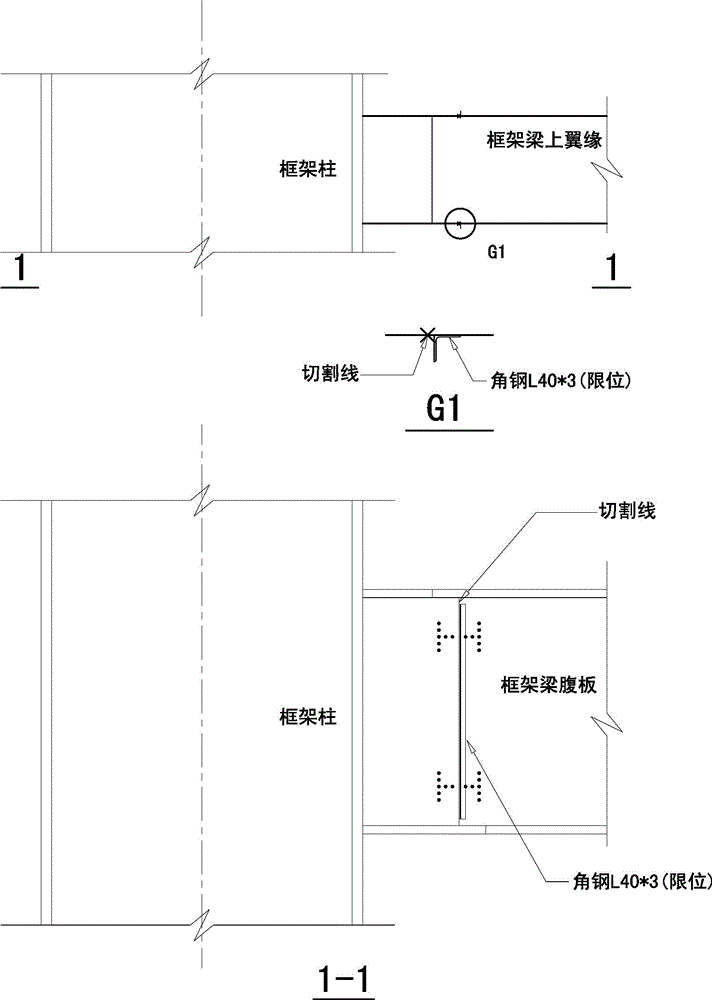
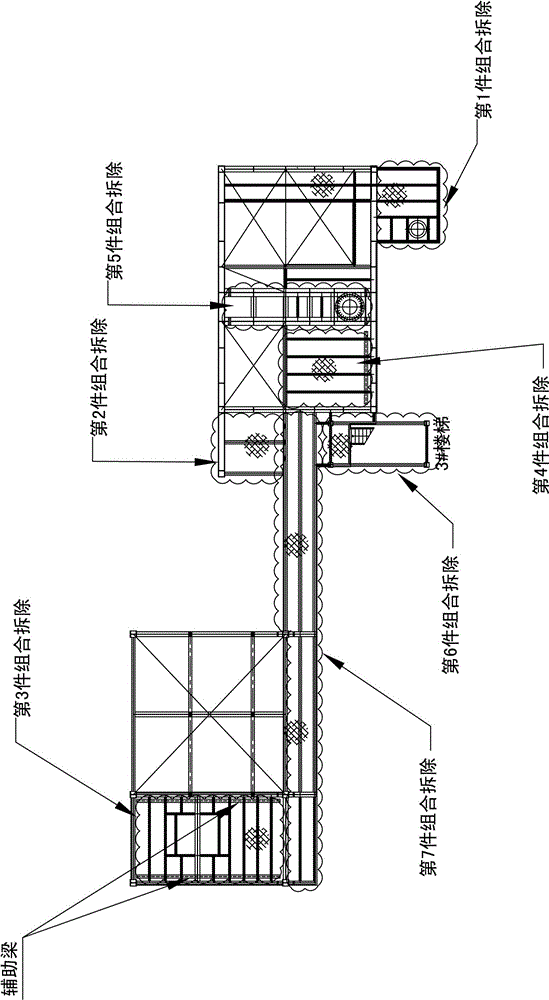
Protective dismantle and assembly method for large-scale towering steel structures
The invention relates to the field of hoisting and hauling operations and especially relates to a protective dismantle and assembly method for large-scale towering steel structures. The protective dismantle and assembly method for large-scale towering steel structures is characterized by following steps which are carried out sequentially: A. dismantling segment by segment; B. marking by drawing lines; C. numbering; D. lifting lug assembling; E. operating by two combined operation modes; F. pre-hoisting; G. cutting segment by segment; H. combined dismantling piece by piece; I. dismantling integrally. The operation by the invention is safe and reliable and the device utilization rate is high.
Owner:SHANGHAI BAOYE GRP CORP
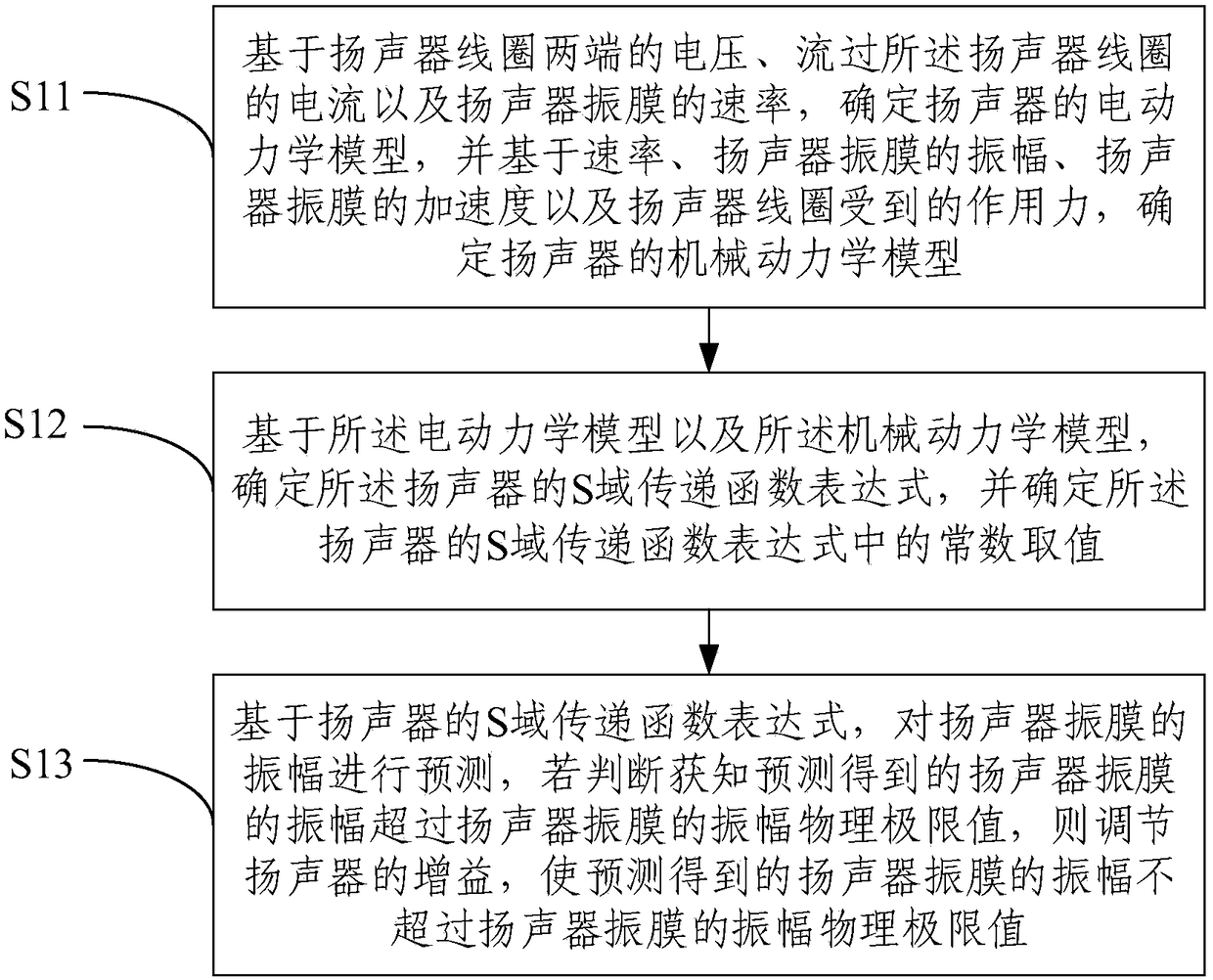
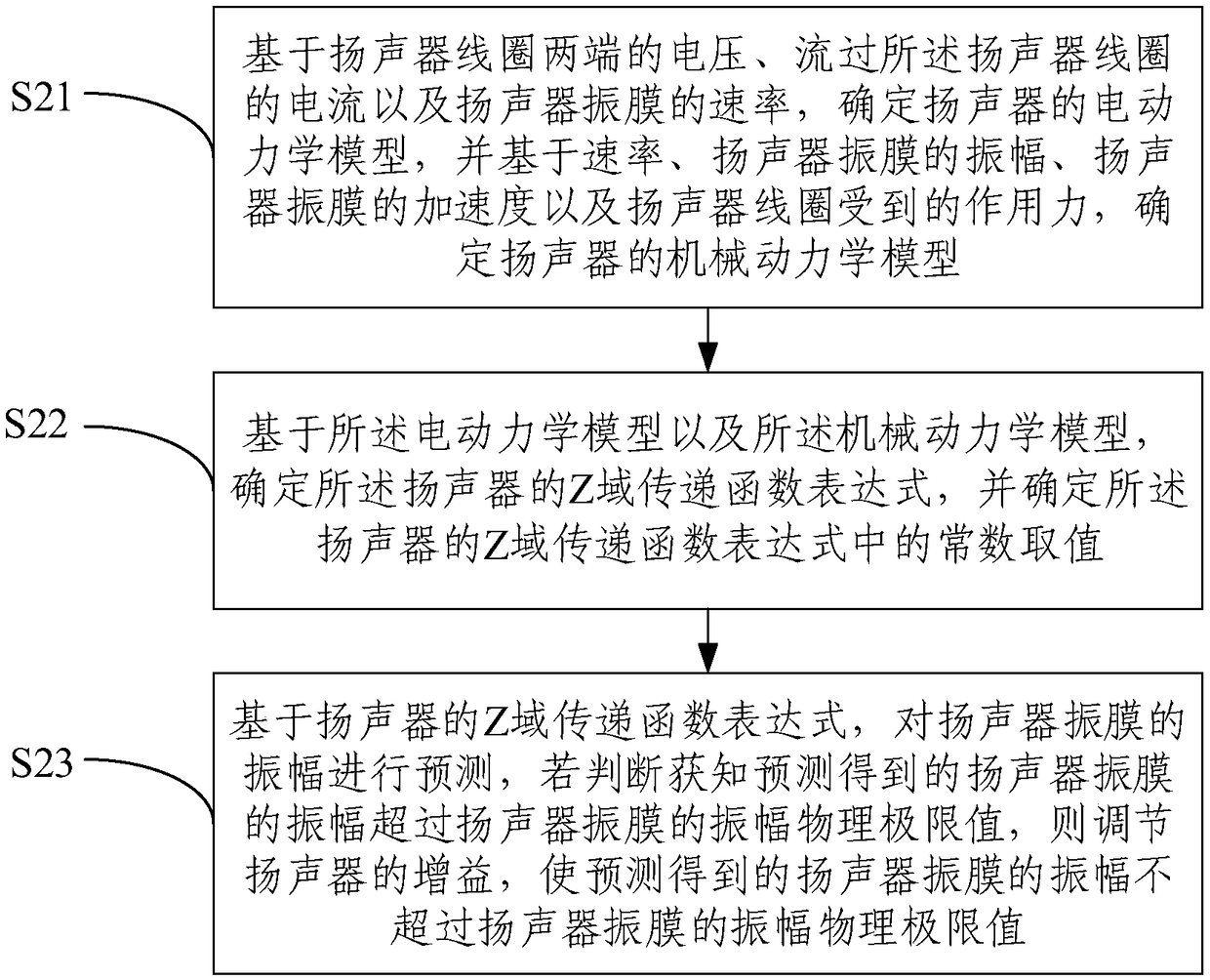
Method and system for adjusting amplitude of speaker diaphragm
ActiveCN109495820AIncrease volumeStrong impact resistanceElectrical transducersLoudspeakersDynamic modelsLimit value
The embodiment of the invention provides a method and system for adjusting the amplitude of a speaker diaphragm. The method comprises the steps of: first determining an electrodynamic model and a mechanical dynamic model of a speaker through relevant parameters of the speaker; determining the expression of a S domain / Z domain transfer function of the speaker according to the electrodynamic model and the mechanical dynamic model; predicting the amplitude of a speaker diaphragm through the expression of the S domain / Z domain transfer function of the speaker; and adjusting the gain of the speakersuch that the predicted amplitude of the speaker diaphragm does not exceed a physical limit value of the speaker diaphragm. The method and the system adjust the gain of the speaker in advance by predicting the amplitude of the speaker diaphragm, thereby preventing the amplitude of the speaker diaphragm from exceeding the physical limit value, and ensuring that the speaker obtains the largest possible volume without being damaged. Moreover, there is no need for additional processing of the speaker, no need to measure current in real time, so the method and the system have advantages of low cost and lower speaker battery loss.
Owner:WUHAN JUXIN MICROELECTRONICS CO LTD
Production method for sunscreen cream with plant extracts as main functional components
InactiveCN103356442APlay a coordinating roleGood sun protectionAntibacterial agentsCosmetic preparationsBiotechnologySkin sensitization
The invention provides a production method for a sunscreen cream with plant extracts as main functional components. The production method comprises the following steps: 1, extraction of alcohol-soluble components in the shuck of mangosteen; 2, extraction of water-soluble polysaccharides in the shuck of mangosteen; 3, preparation of a chinaroot greenbrier cream; 4, manufacture of fine kudzu vine root powder; and 5, preparation of a matrix cream. The sunscreen cream prepared by using the method prevents symptoms like obstruction of pores and skin allergic diseases, exerts substantial effects on anti-inflammation, sterilization, skin nourishing, improvement of wrinkle resistance of the skin and effective delaying of skin ageing and has the advantages of enhanced safety and reduced cost; the sunscreen cream can effectively restore damaged skin, wherein the restoration effect of the sunscreen cream is incomparable with restoration effects of antioxidant substances like vitamin E; and the sunscreen cream enables synergy of ultraviolet ray absorbers to be performed, so a minimum usage amount of the sunscreen cream can exert a maximum protection effect.
Owner:珠海丽阳生物科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com