PLC program protection method, access method and device thereof
A program protection and program technology, applied in the direction of electrical program control, computer security device, program control in sequence/logic controller, etc., can solve the problems of no access record, multi-user simultaneous access hierarchical encryption, etc., so that it is not easy to crack, Prevent illegal access and improve the effect of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
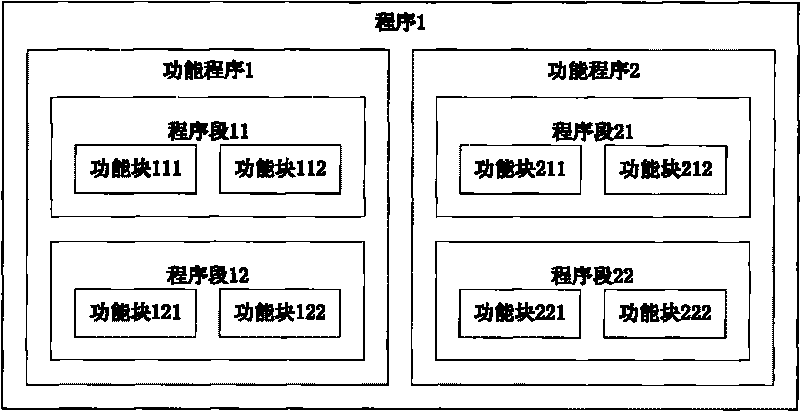
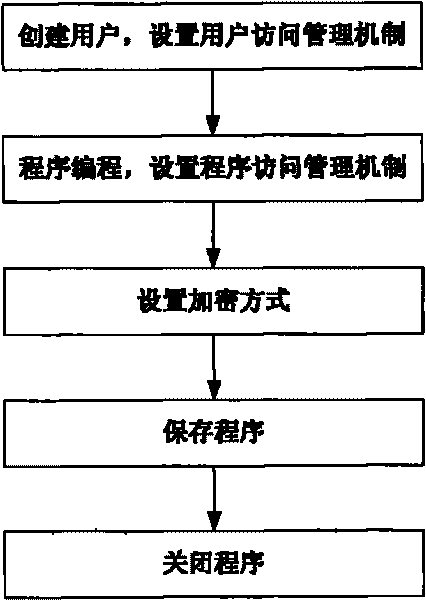
[0021] Embodiment 1: as figure 1 , image 3 Shown, a kind of PLC program protection method comprises the following steps:
[0022] Step A: Create a user and set up a user access management mechanism;
[0023] The user access management mechanism refers to a user management mechanism that establishes individual users or user groups, and adopts access strategies such as autonomous access control strategies, mandatory access control strategies, and role access mechanism strategies. Discretionary Access Control Policy is an access control service that enforces a security policy based on the identity of system entities and their authorization to access system resources. The mandatory access control policy is "imposed" on the access subject, that is, the system forces the subject to obey the access control policy. The role access mechanism strategy is to grant different permissions according to the division of roles.
[0024] Step B: Program programming, setting program access m...
Embodiment 2
[0031] Embodiment 2: as Figure 4 Shown: a method for accessing a PLC program protected using the above-mentioned protection method, comprising the following steps:
[0032] Step A': open program request;
[0033] Step B': User identity authentication, if valid, allow to open the program, otherwise refuse to open the program;
[0034] Step C': access program request;
[0035] Step D': compare the program access rights, if they match, then allow access to the program, otherwise deny the access;
[0036] Step E': Access the program, and perform operations such as reading, modifying, uploading, downloading, and authorizing the program;
[0037] Step F': Save the program, set permissions and encrypt according to the set user and program access management mechanism and encryption method, otherwise it will not be saved; the encryption method here is the encryption method described above, and will not be repeated here .
[0038] turn off an app.
Embodiment 3
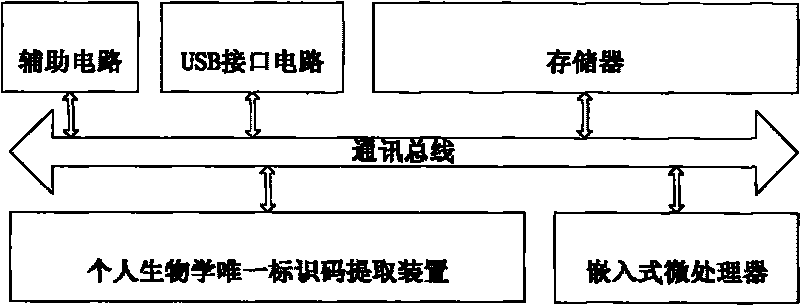
[0039] Embodiment 3: as figure 2 Shown: a kind of device that is used to realize PLC program protection method, adopts the following technical scheme: the device includes embedded microprocessor connected with communication bus, memory, personal biological unique identification code extracting device, USB interface circuit and auxiliary circuit; the embedded microprocessor is used to realize the calculation of encryption and decryption algorithms, and the management of user access mechanism and program access mechanism; the memory is used to store temporary data, user access management mechanism information, program access management mechanism information, keys, encryption The decryption algorithm and the PLC program involve memories such as EPROM, RAM, ROM, flash memory, etc.; the personal biological unique identification code extraction device is used to extract the personal biological unique identification code; the personal biological unique identification code can be sele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com