JAVA program anti-obfuscation method and terminal
A program and index technology, applied in the field of anti-obfuscation, can solve problems such as analysis obstacles, logical errors, and a lot of time and energy, and achieve the effect of promoting development and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
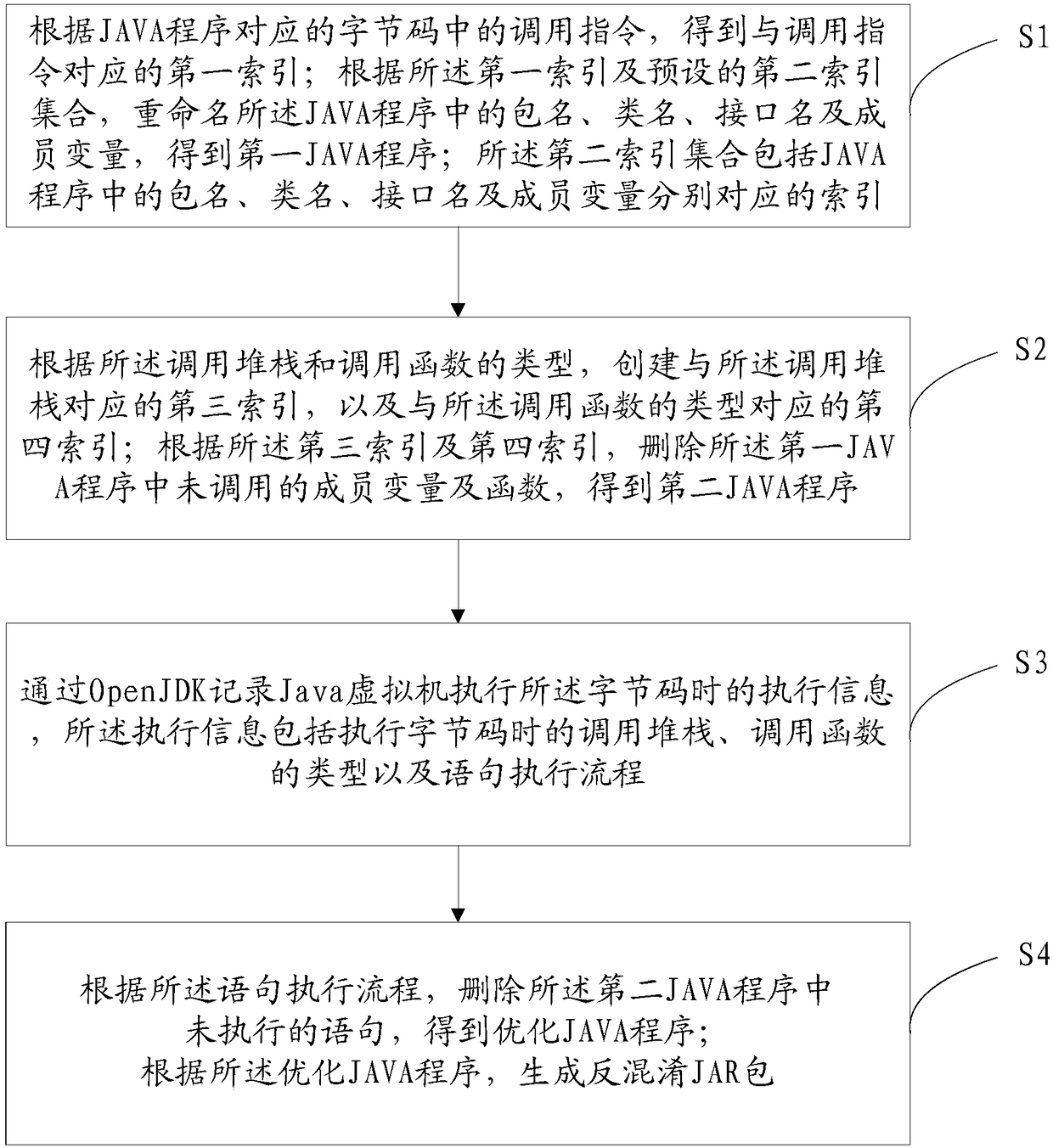
[0076] Please refer to figure 1 , Embodiment 1 of the present invention is:
[0077] A kind of JAVA program anti-obfuscation method provided by the present invention comprises the following steps:
[0078] S1: Obtain the first index corresponding to the call instruction according to the call instruction in the bytecode corresponding to the JAVA program; rename the package name in the JAVA program according to the first index and the preset second index set , class name, interface name and member variables, to obtain the first JAVA program; the second index set includes indexes corresponding to package name, class name, interface name and member variables in the JAVA program;
[0079] The S1 is specifically:
[0080] Obtain the JAVA program and the bytecode corresponding to the JAVA program according to the preset JAR package;
[0081] According to the obfuscation rules of the JAVA program, rename the package name, class name, interface name and member variables in the JAVA ...
Embodiment 2
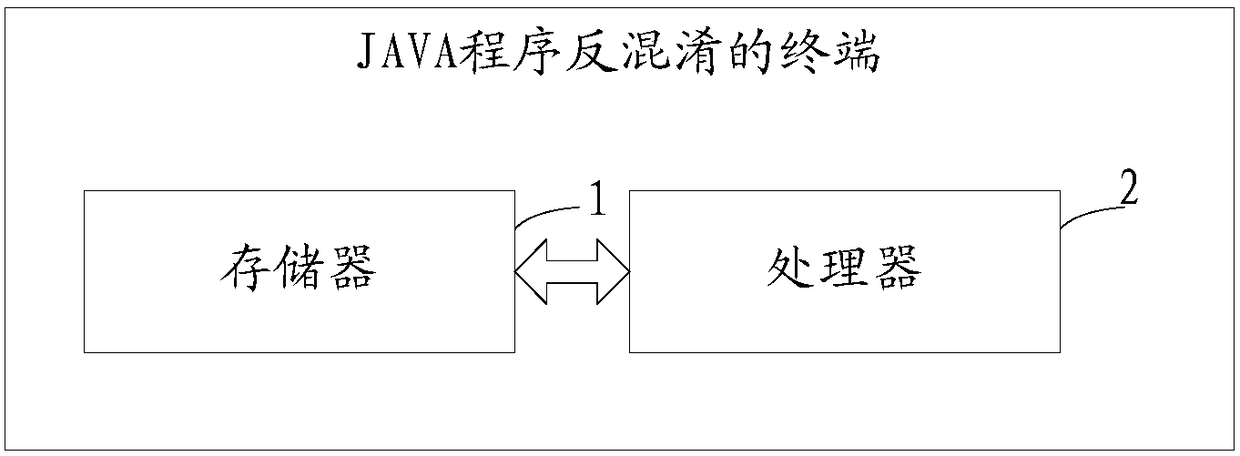
[0108] Please refer to figure 2 , the second embodiment of the present invention is:
[0109] A JAVA program anti-obfuscation terminal provided by the present invention includes a memory, a processor, and a computer program stored on the memory and executable on the processor, and the processor implements the following steps when executing the program:
[0110] S1: Obtain the first index corresponding to the call instruction according to the call instruction in the bytecode corresponding to the JAVA program; rename the package name in the JAVA program according to the first index and the preset second index set , class name, interface name and member variables, to obtain the first JAVA program; the second index set includes indexes corresponding to package name, class name, interface name and member variables in the JAVA program;
[0111] The S1 is specifically:
[0112] Obtain the JAVA program and the bytecode corresponding to the JAVA program according to the preset JAR p...
Embodiment 3
[0133] The symbols in this embodiment refer to: package name / class name / interface name / member variable;
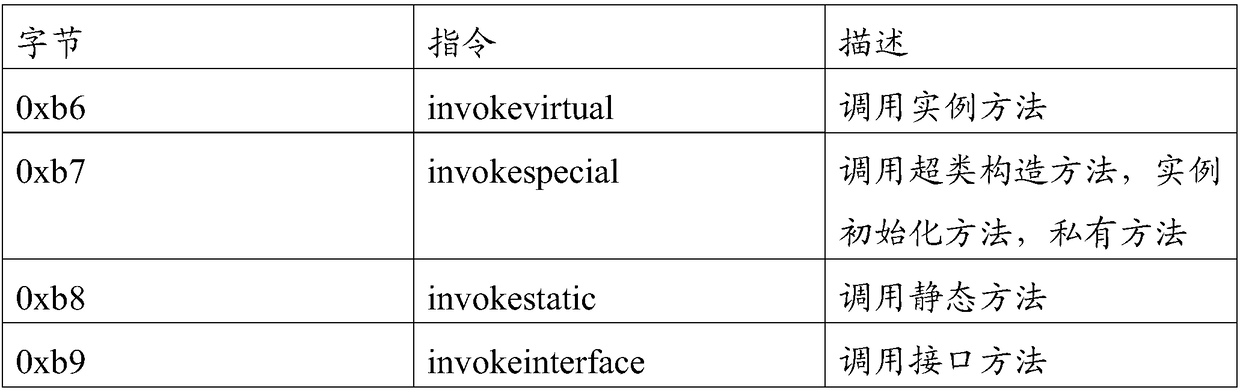
[0134] The anti-obfuscation scheme of the present invention is analyzed on the basis of Java bytecode. The tool javap provided by the JDK used will decompile the java bytecode into JVM instructions similar to assembly instructions.
[0135] Renaming includes static renaming and dynamic renaming.
[0136] Static renaming refers to analyzing JVM instructions without running them. Mainly by analyzing the class name, interface, and method used in the instruction, a call index is initially established for each class, and then all objects referenced to the symbol are replaced according to the records of the index when renaming.
[0137] Dynamic renaming refers to executing Java bytecode in a customized JVM virtual machine, and improving the call index generated in static analysis through reflection and call stack. According to the execution process in the JVM to simplify and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com