An Android malicious software detection method based on a sensitive calling path
A technology of malware and detection methods, applied in the field of information security, can solve the problems of low accuracy and insufficient granularity, and achieve the effect of high precision, easy expansion, and improvement of the degree of intelligent detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
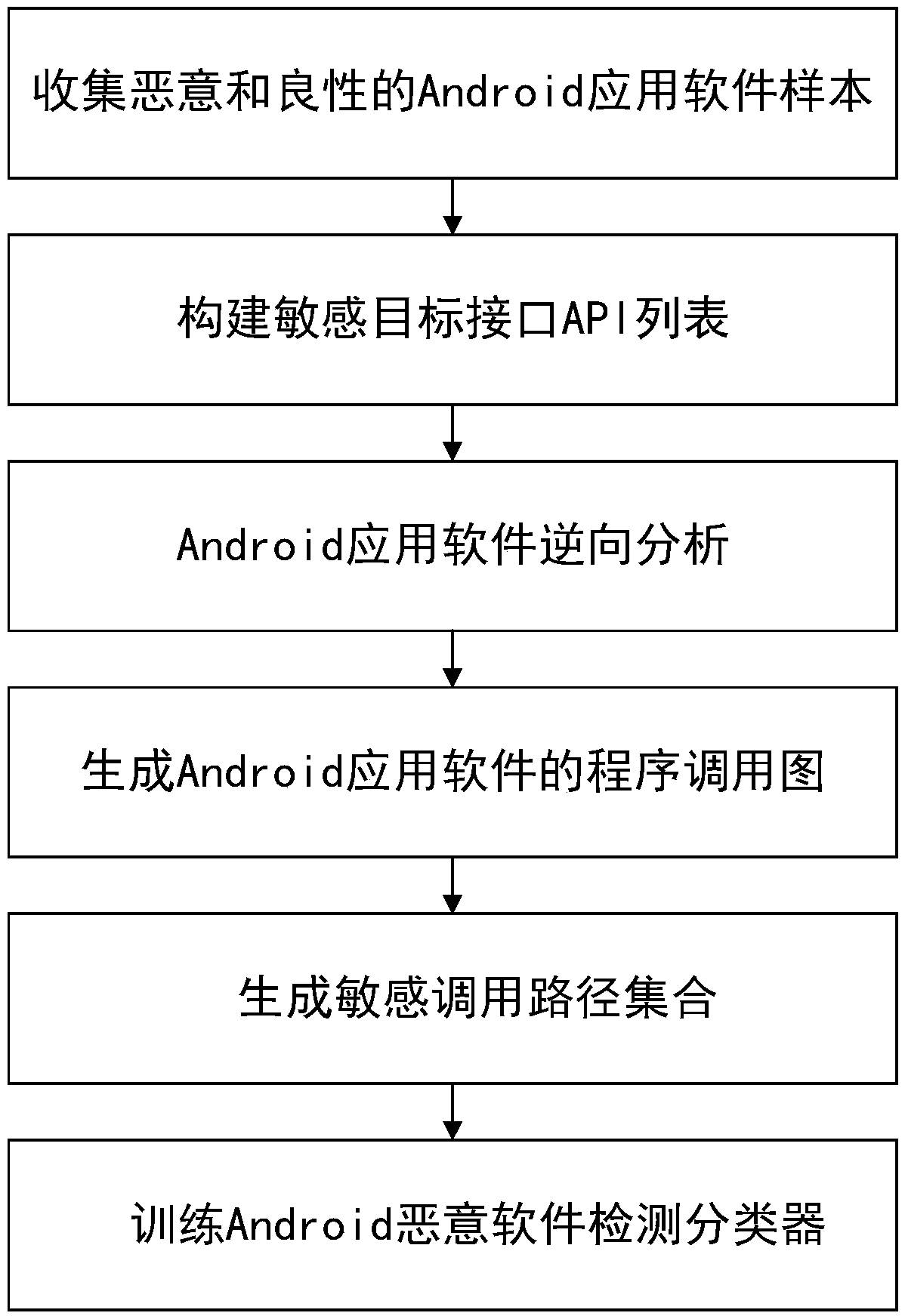
[0032] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0033] refer to figure 1 , the implementation steps of the present invention are as follows:
[0034] Step 1, collect malicious and benign Android application software samples.
[0035] Download and collect known malicious and benign Android application software samples from domestic and foreign mainstream application markets and public data sets, among which malicious samples and benign samples account for half each, and the number of each sample is not less than B, and B is greater than or equal to 1 positive integer;
[0036] This embodiment downloads and collects 16,300 Android malicious software and 16,300 Android benign software from Google Play, Drebin data set, and VirusShare sample library.
[0037] Step 2, build a sensitive target interface API list.
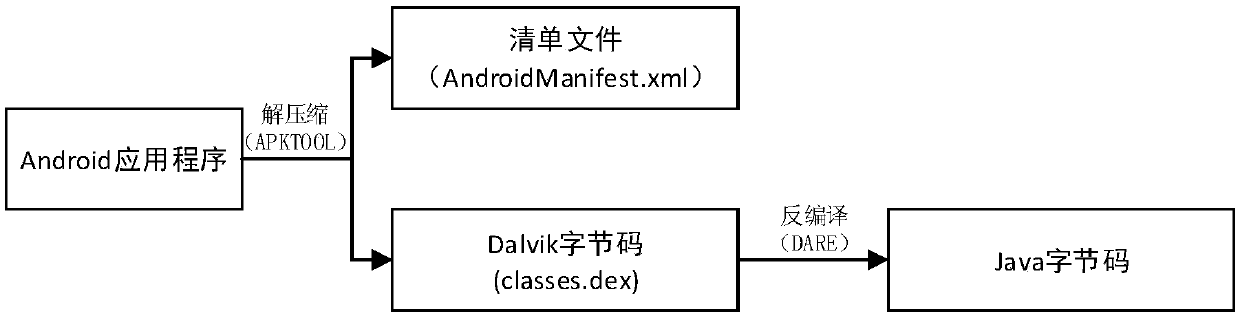
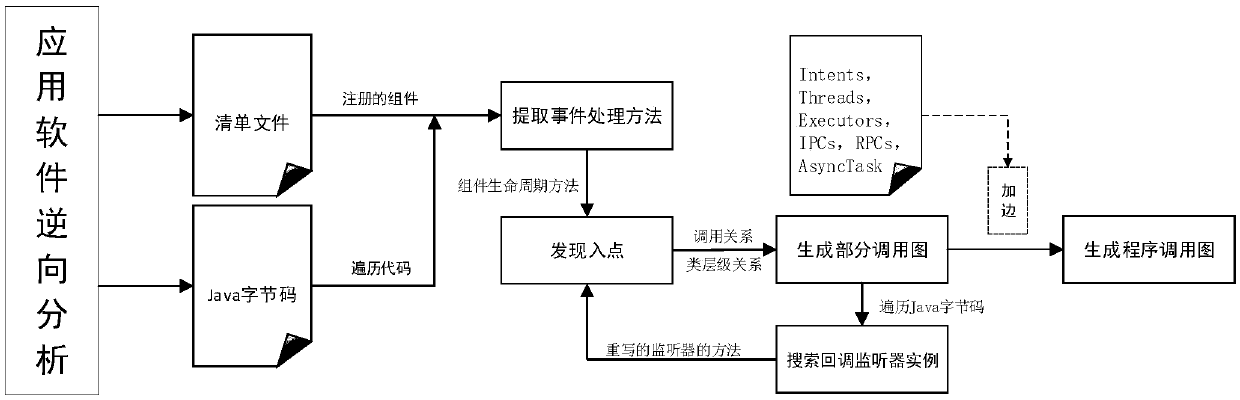
[0038] The sensitive target interface API list refers to a series of sensitive target interfac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com