Patents
Literature
60results about How to "Avoid authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
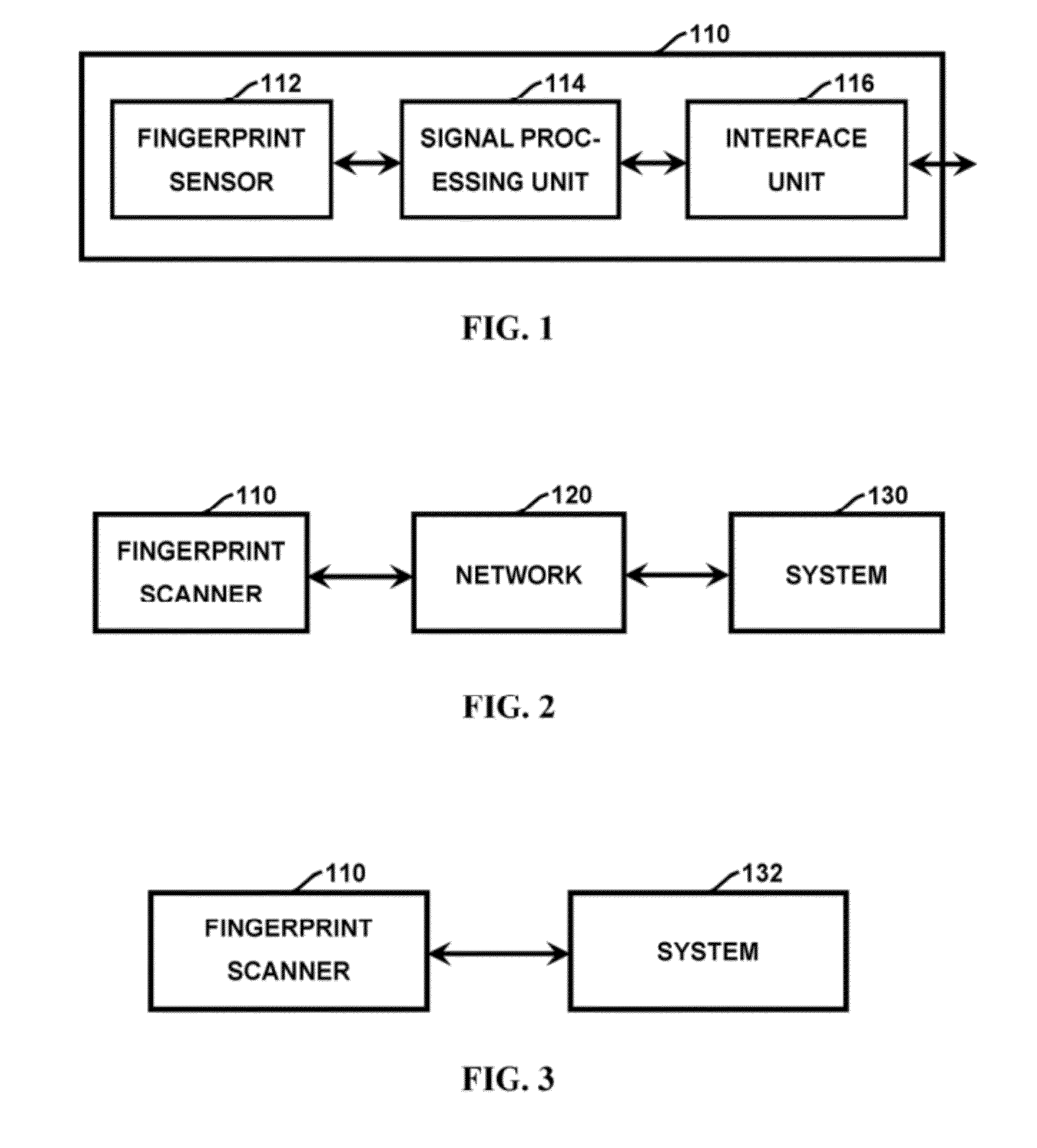
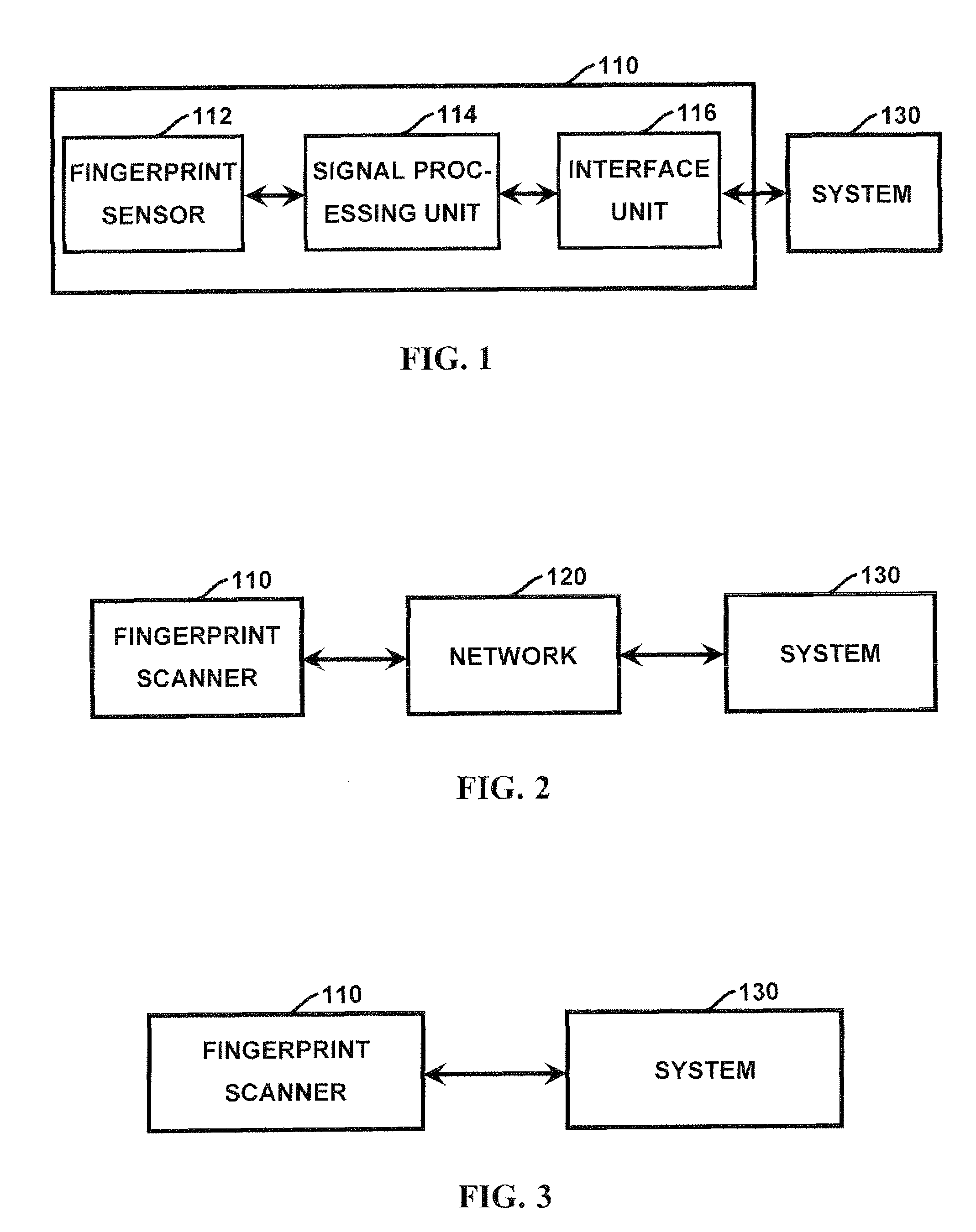
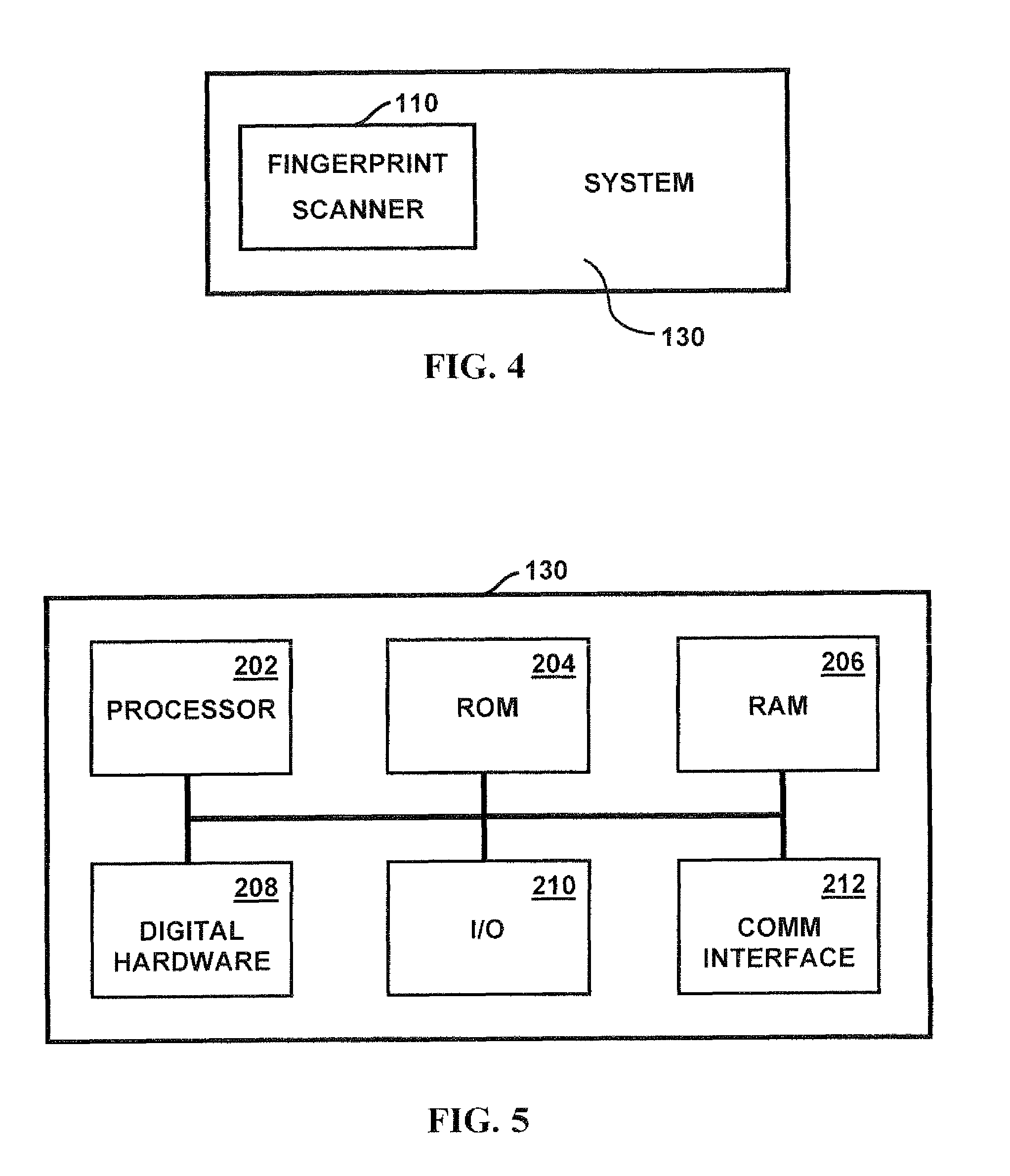
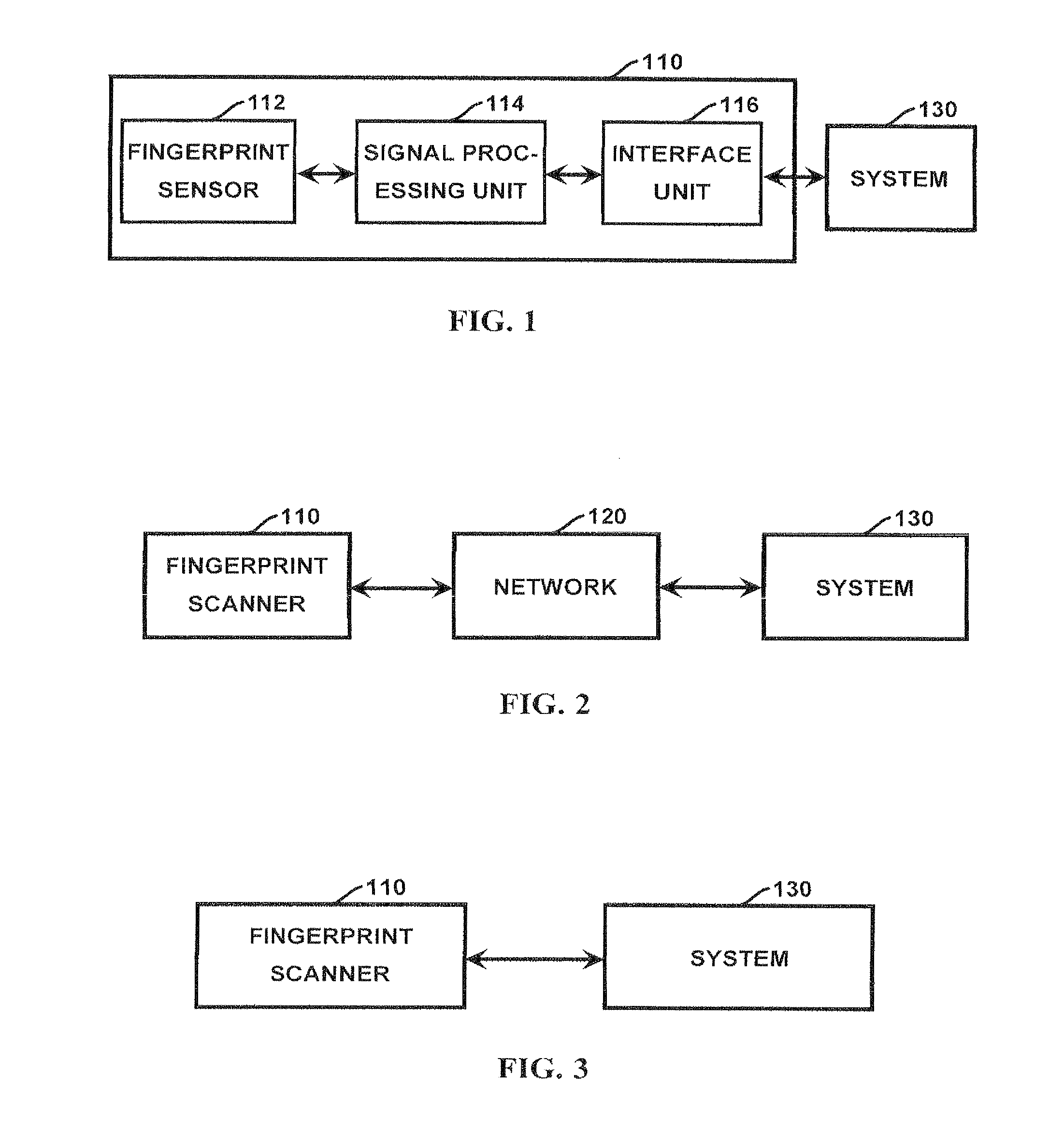
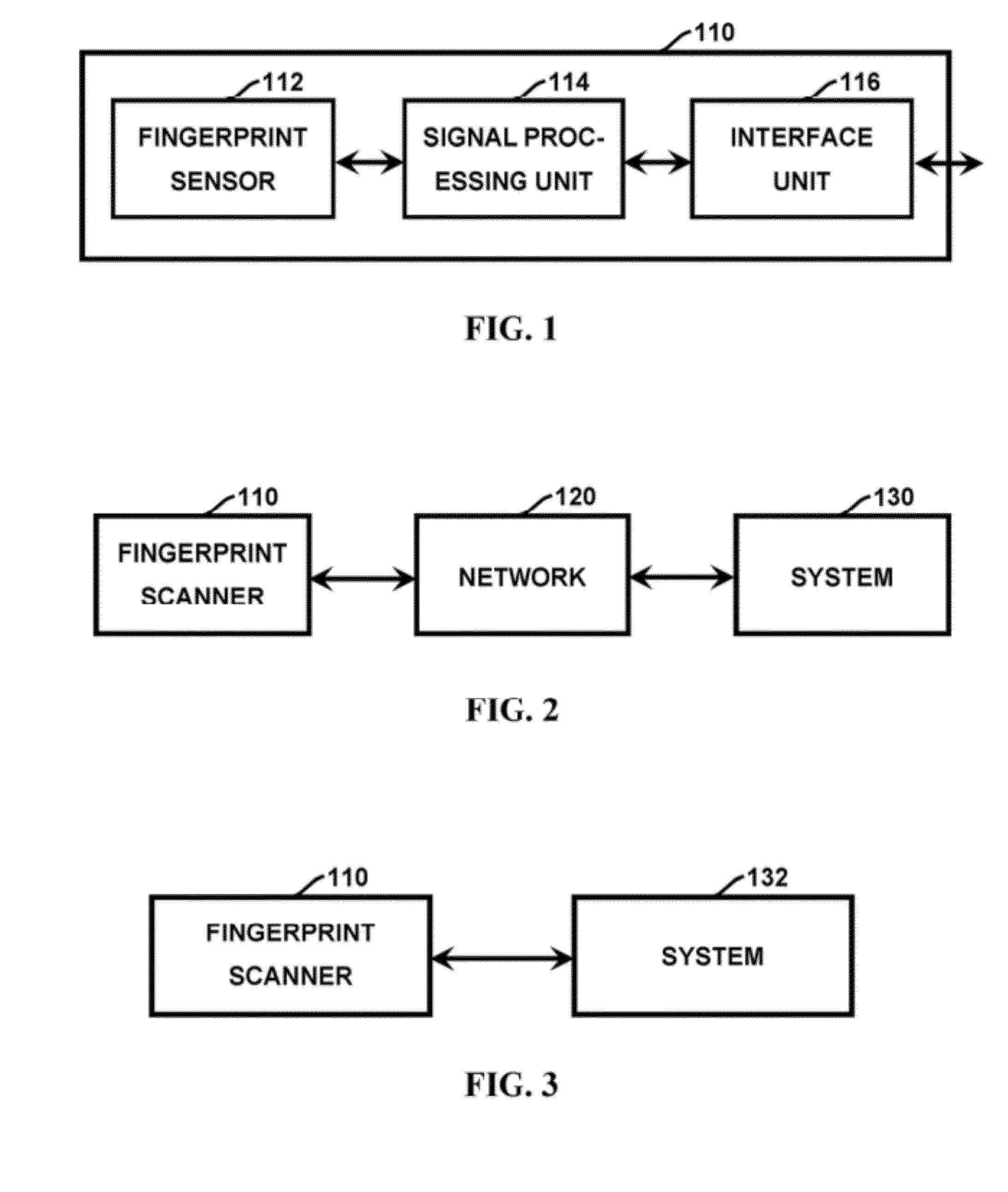
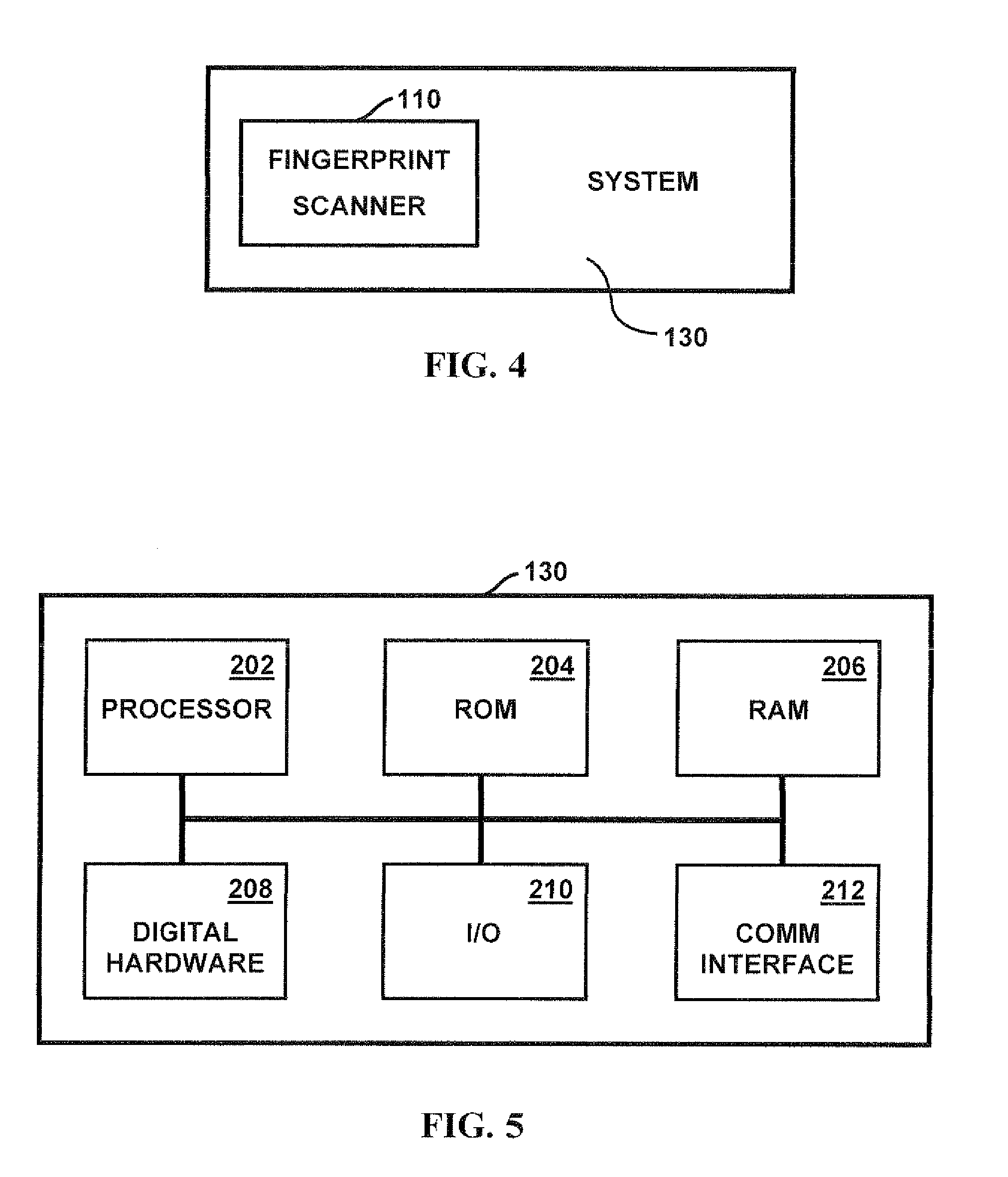
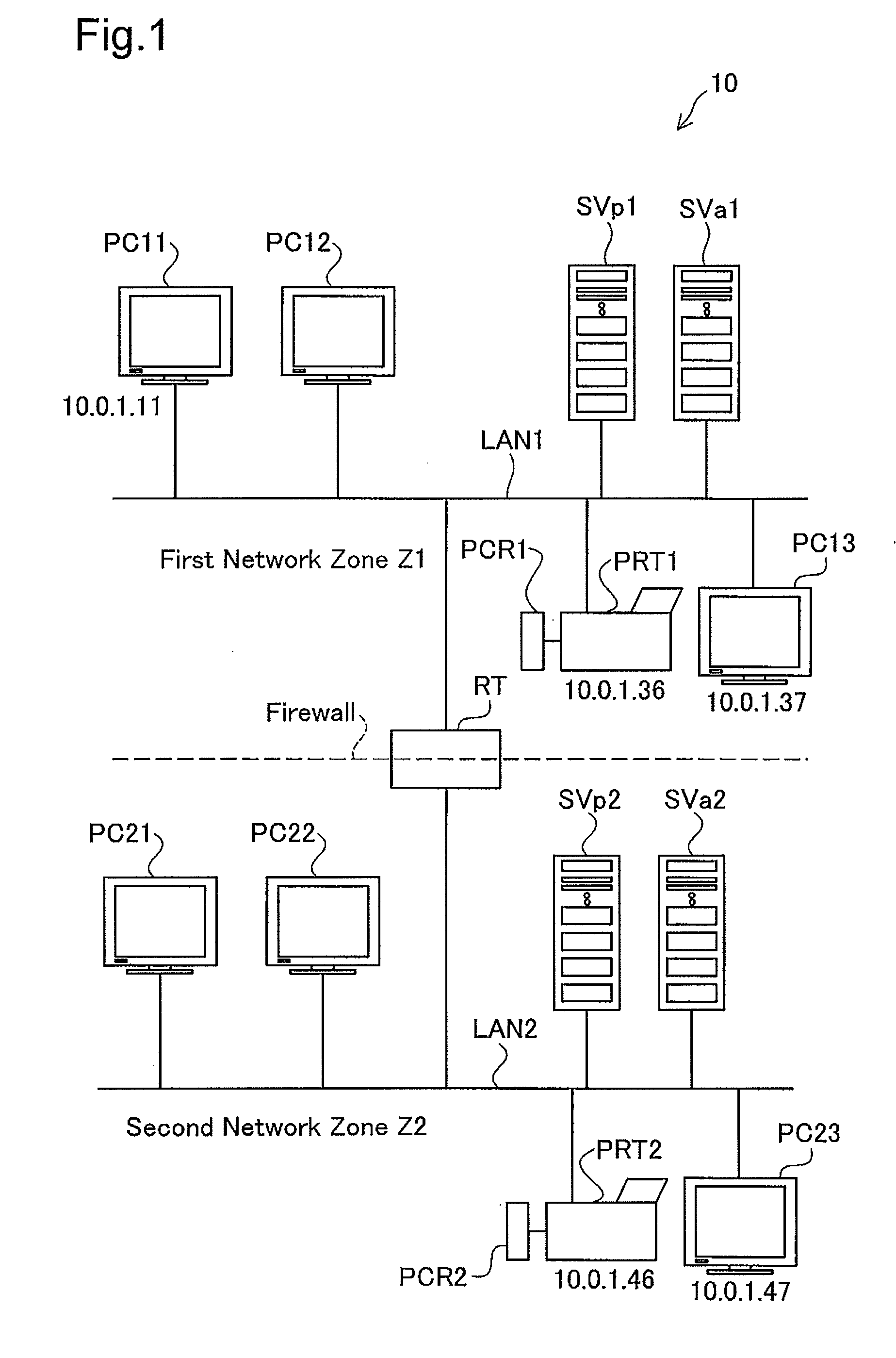
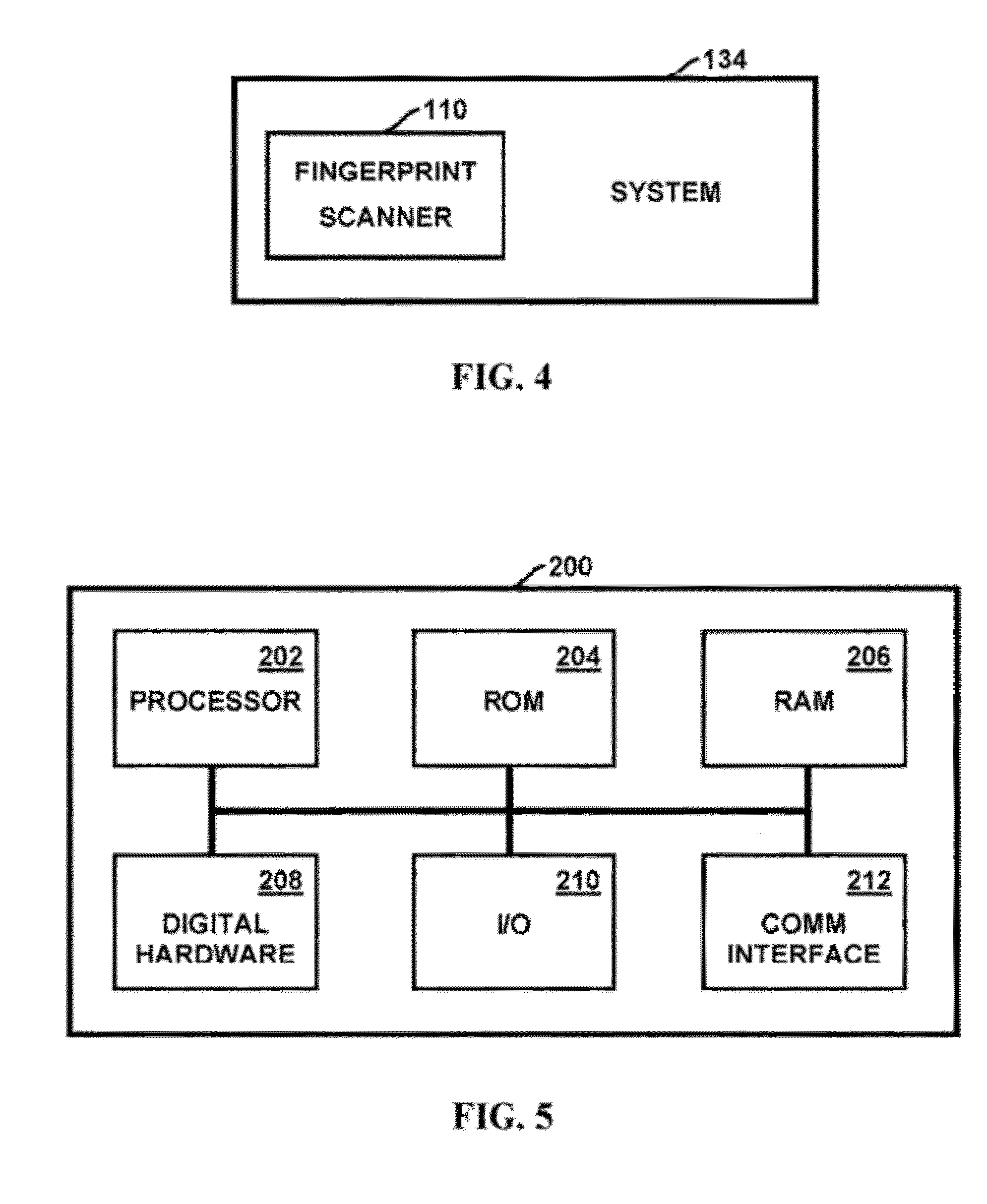
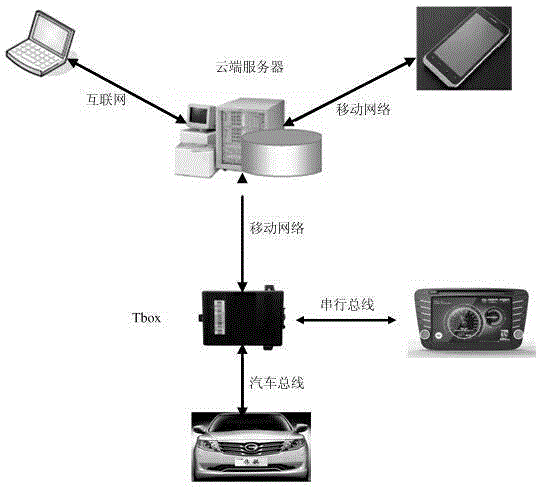
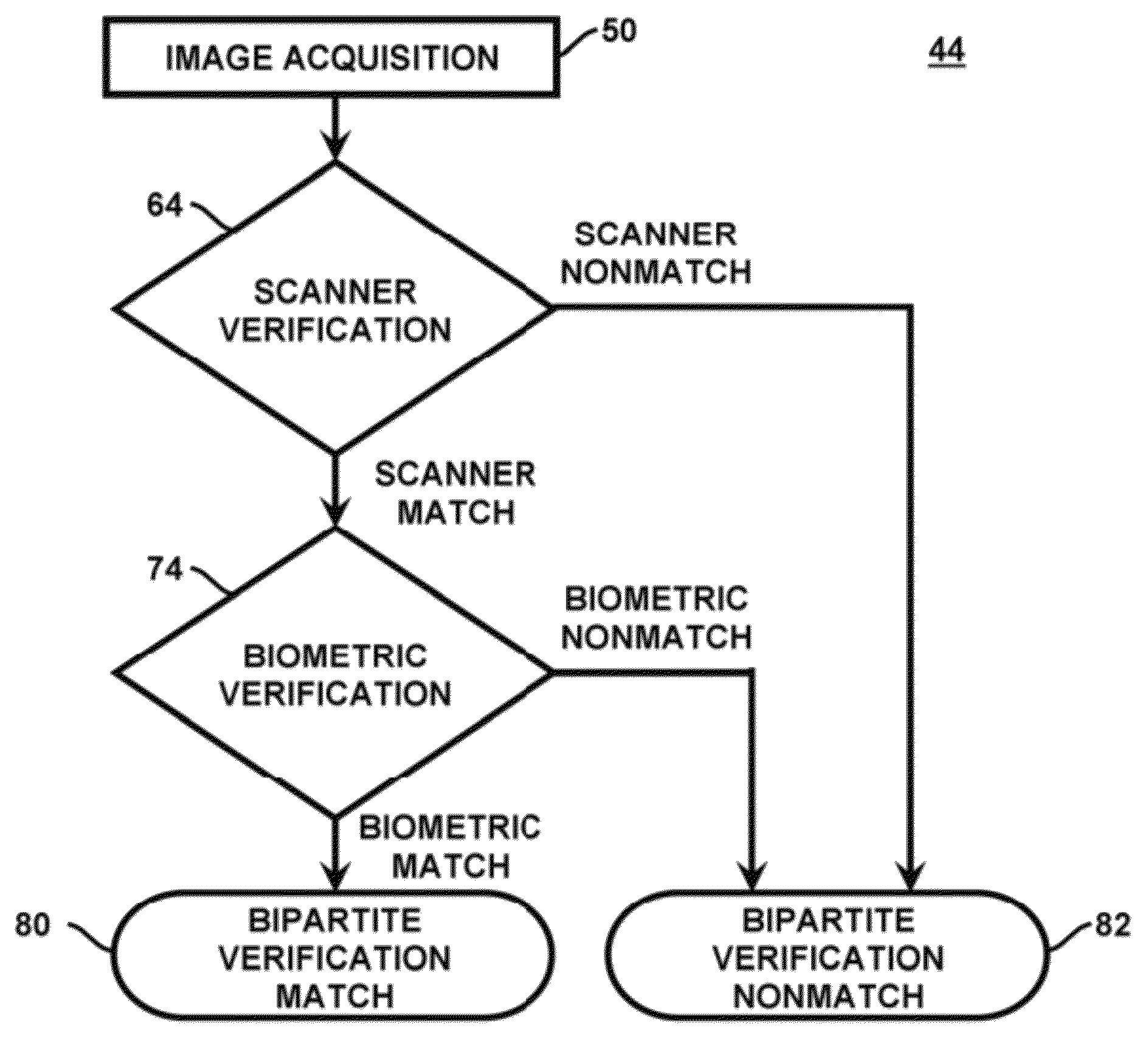
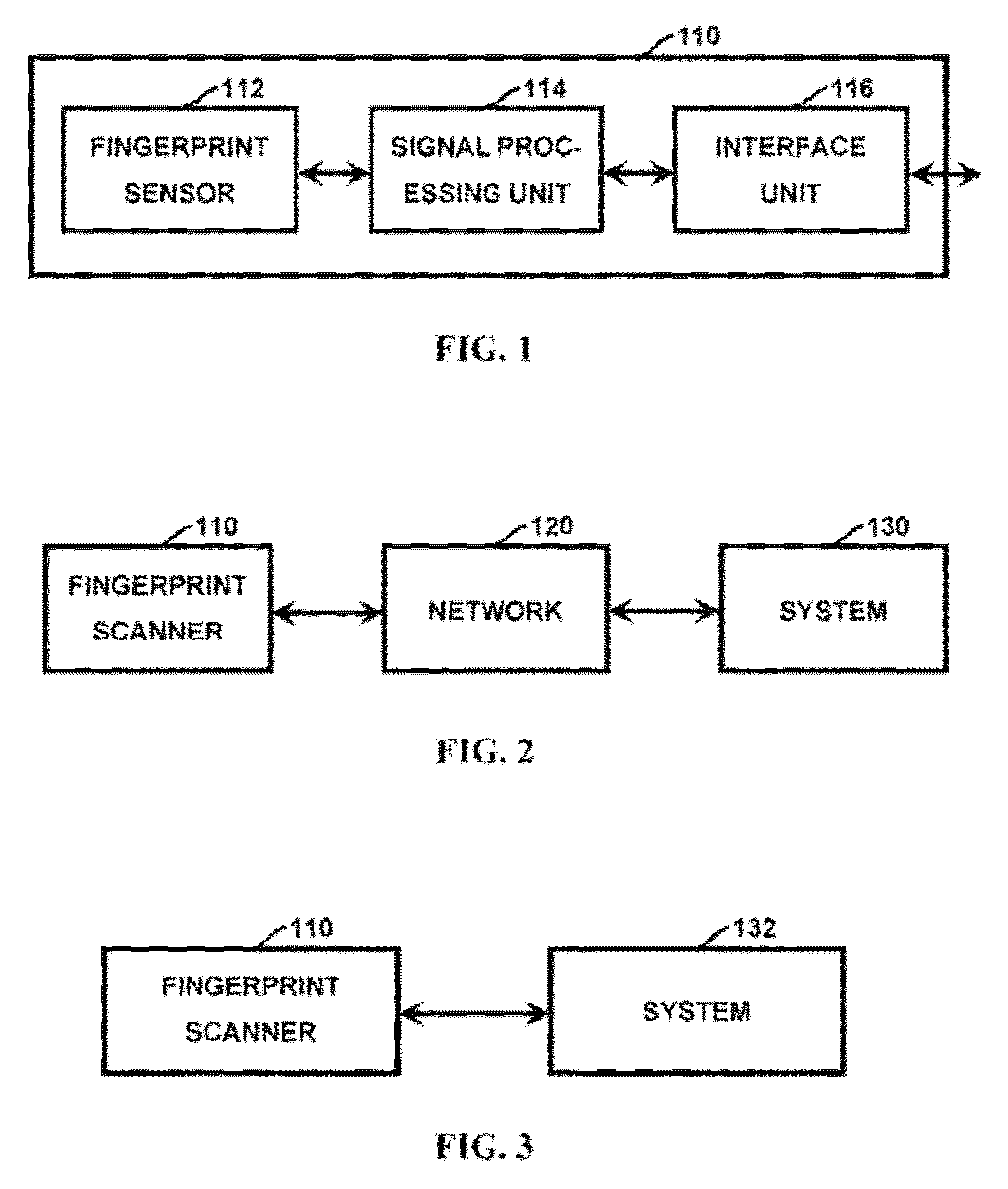
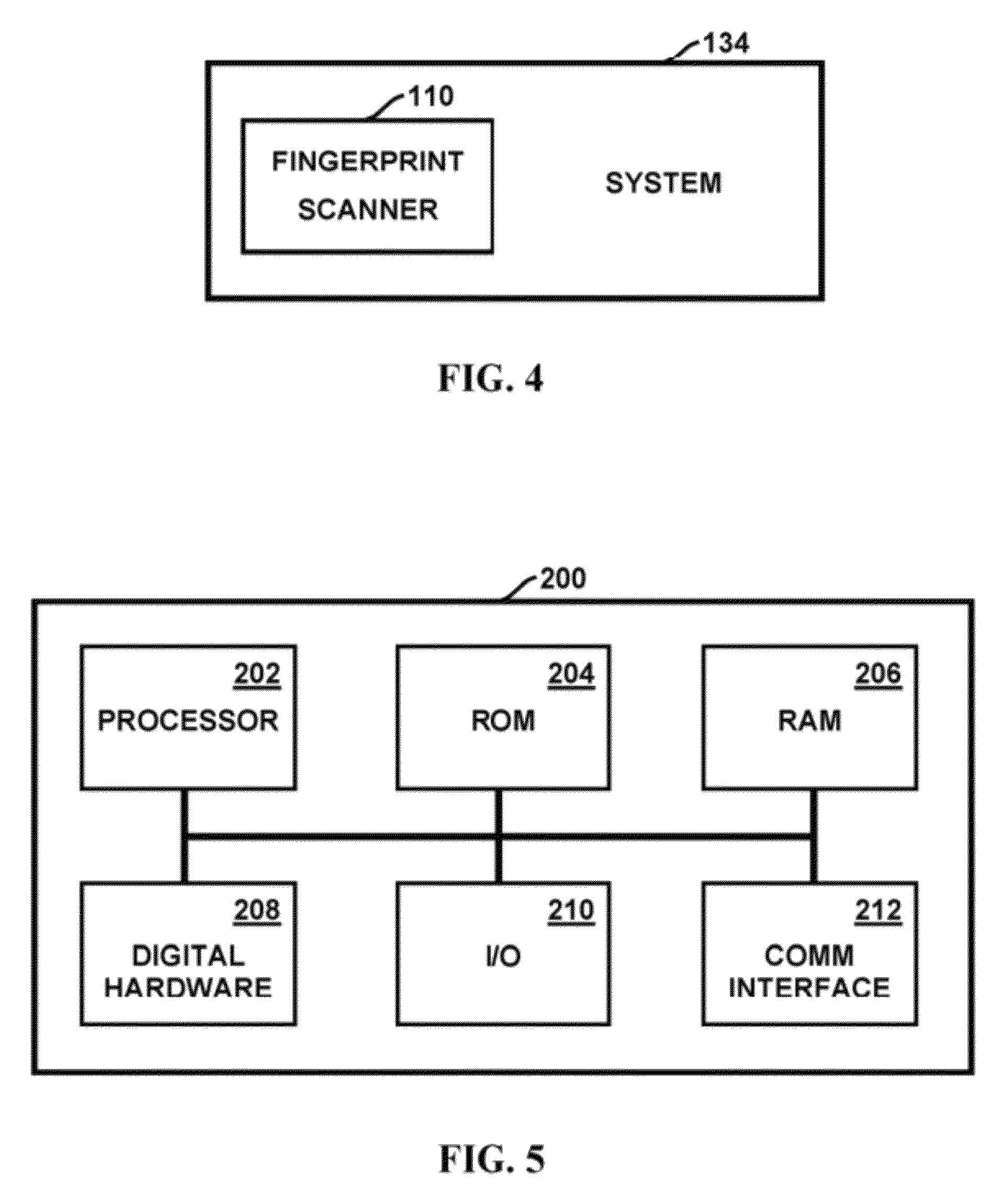
Method and apparatus for authenticating area biometric scanners
ActiveUS20120300988A1Improve security levelEasy to be stolenImage enhancementPrint image acquisitionImaging processingUser authentication
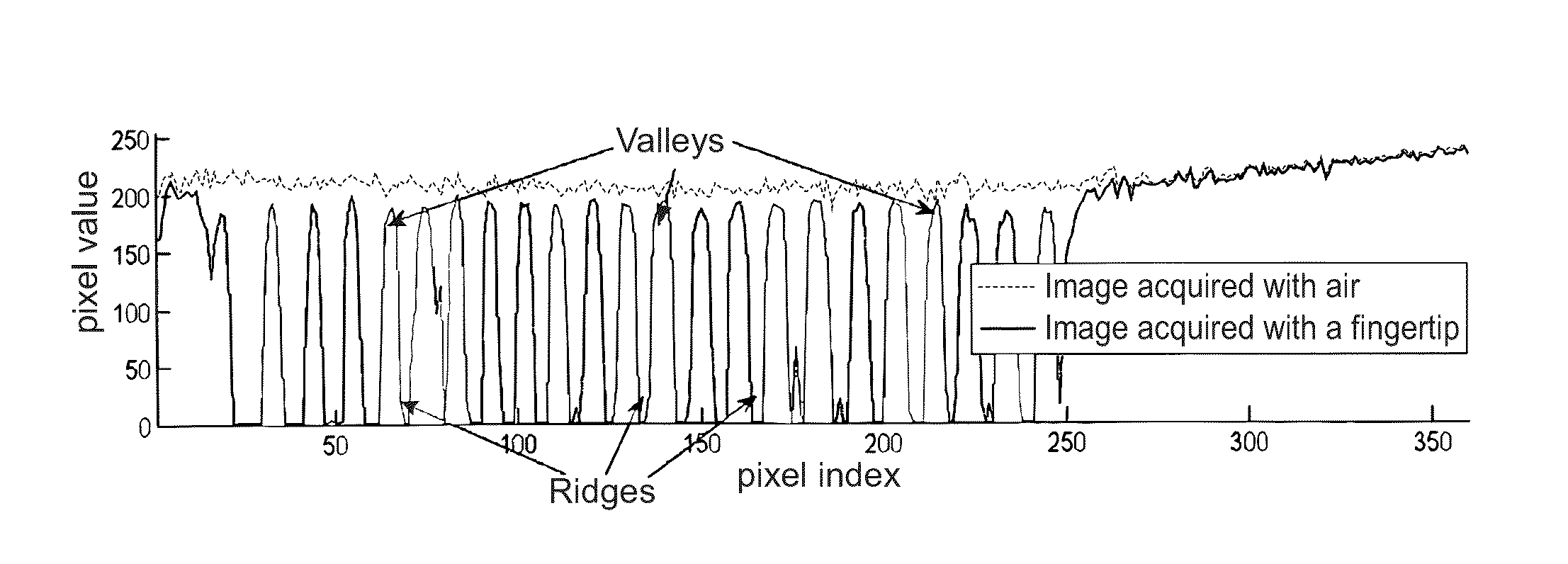
Methods and apparatuses for authenticating a biometric scanner, such as area type finger print scanners, involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeit biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND BALTIMORE
Method and apparatus for authenticating biometric scanners
ActiveUS8577091B2Improve security levelAvoid attackCharacter and pattern recognitionImaging processingUser authentication
A method and apparatus for authenticating a biometric scanner involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeited biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND
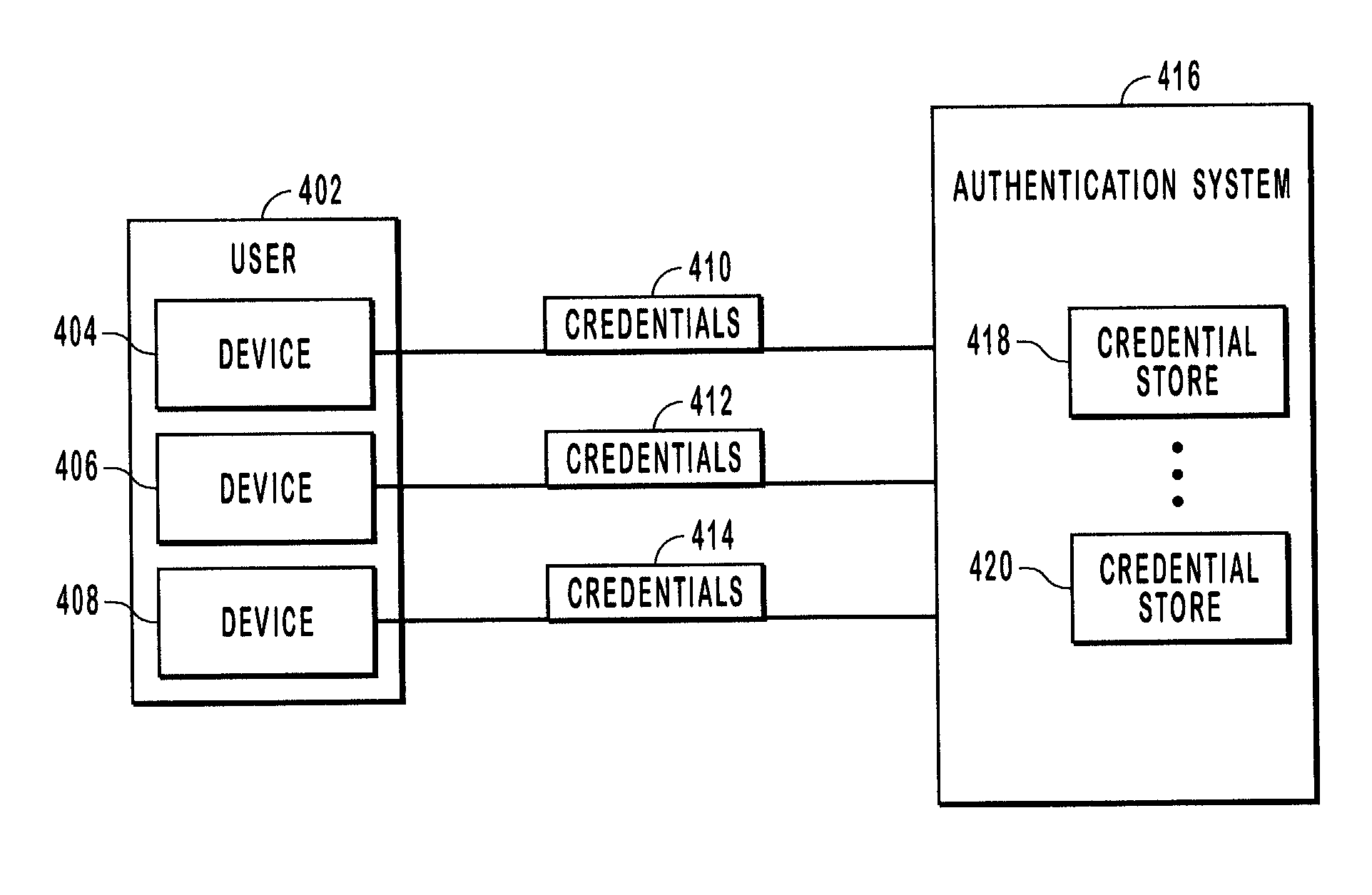
Multiple credentials in a distributed system
InactiveUS7676829B1Improve securitySufficient securityDigital data processing detailsMultiple digital computer combinationsAuthentication systemComputer security
Systems and methods for associating multiple credentials with a single user account in a distributed authentication system. A user can be authenticated to a service by providing any one of the multiple credentials to the authentication system. Thus, a user can provide credentials that are more easily entered or supplied on a given device. All of the credentials are associated with a single user account. The credentials can be associated symmetrically, where the user account is independent of each credential, or asymmetrically, where the user account is stored with a primary credential and the other credentials are secondary credentials that reference the primary credential.
Owner:MICROSOFT TECH LICENSING LLC
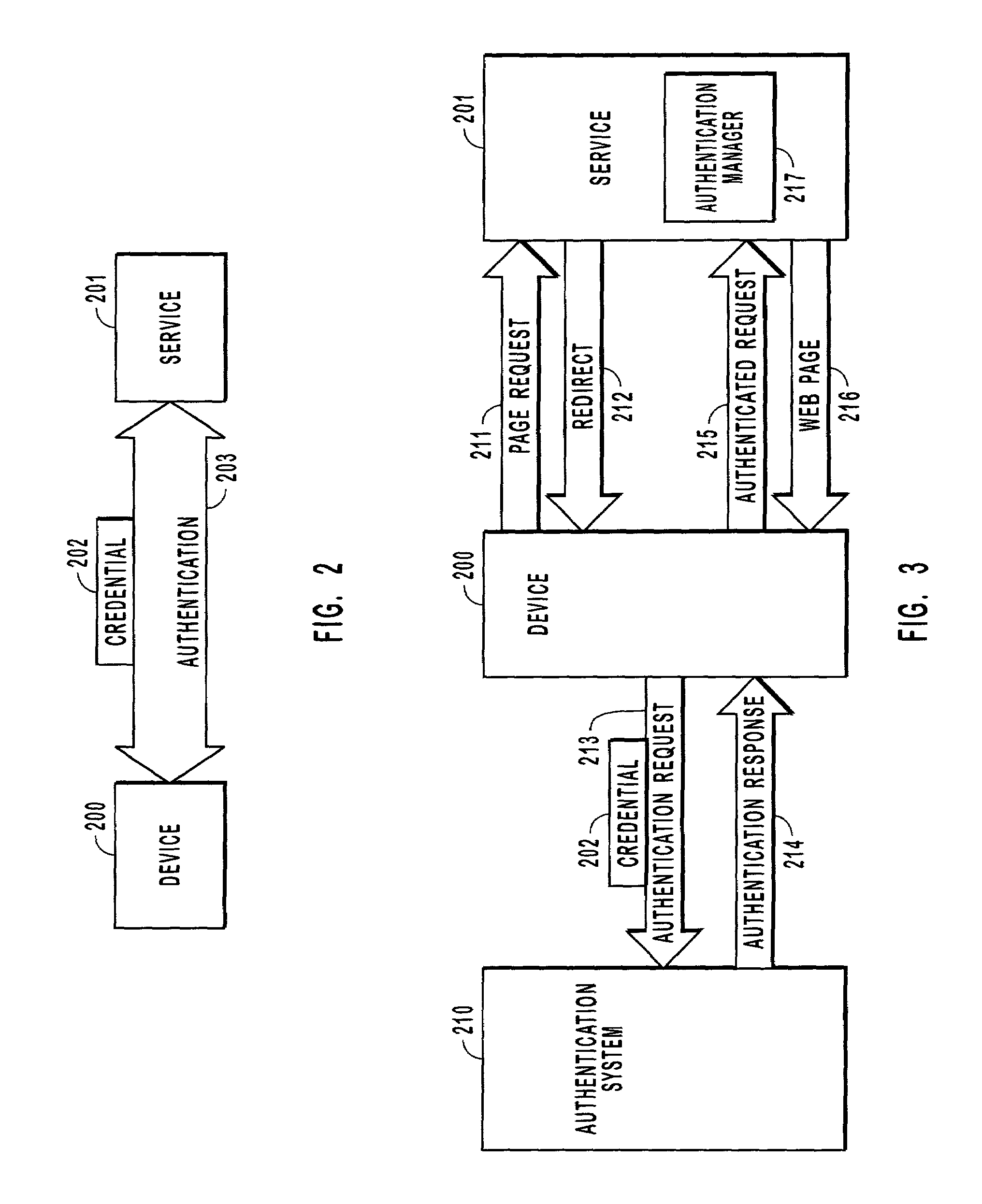
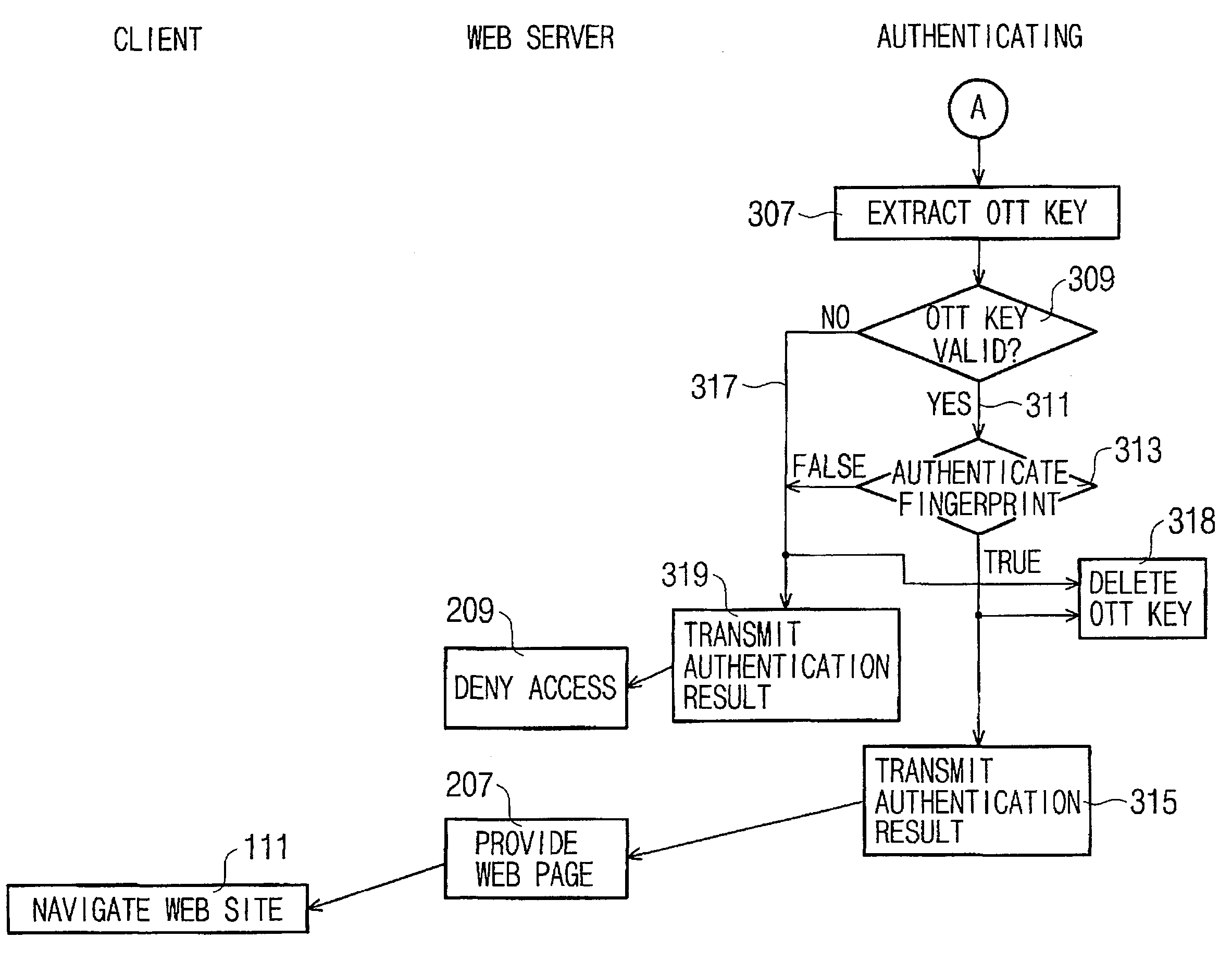
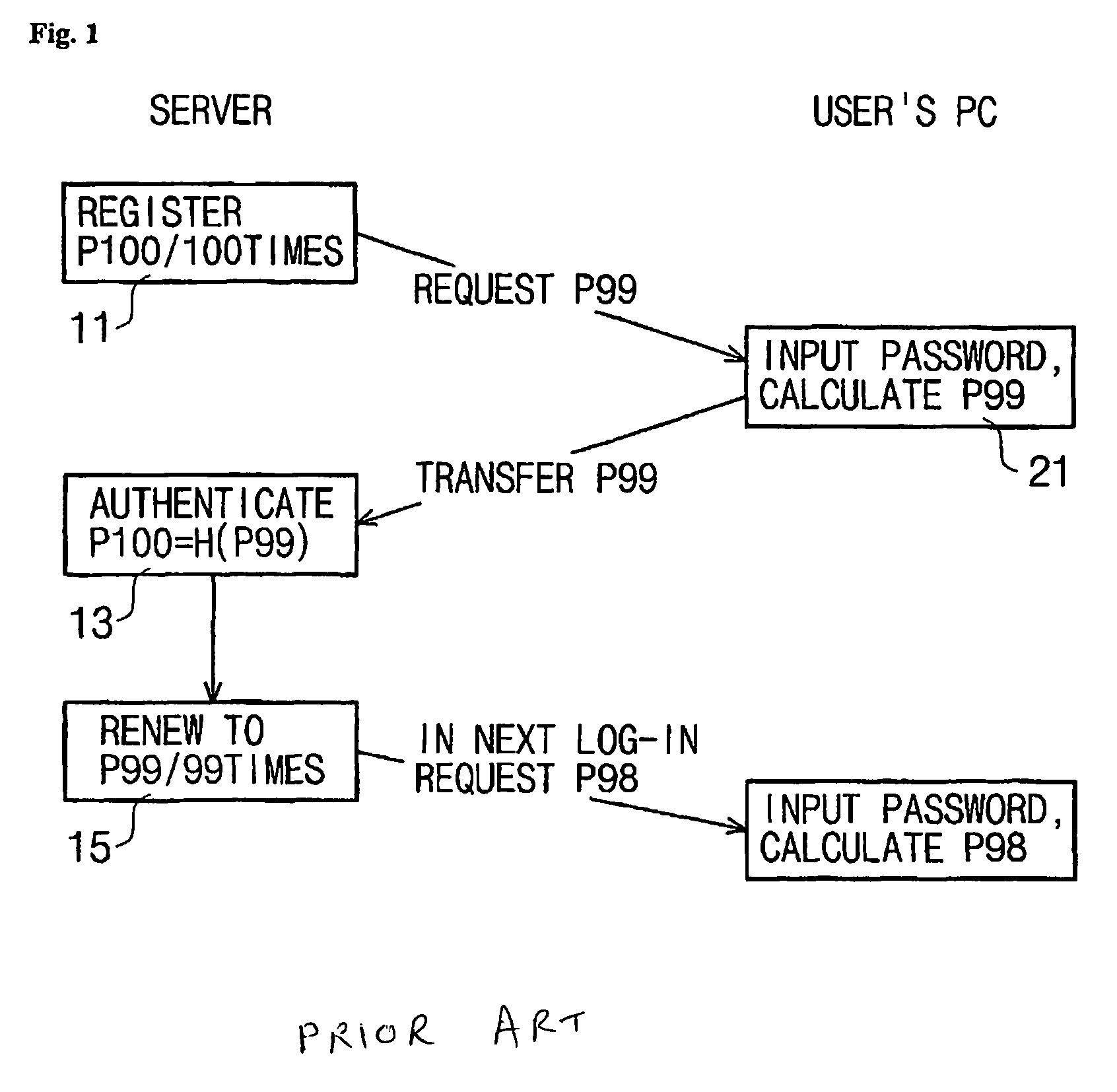
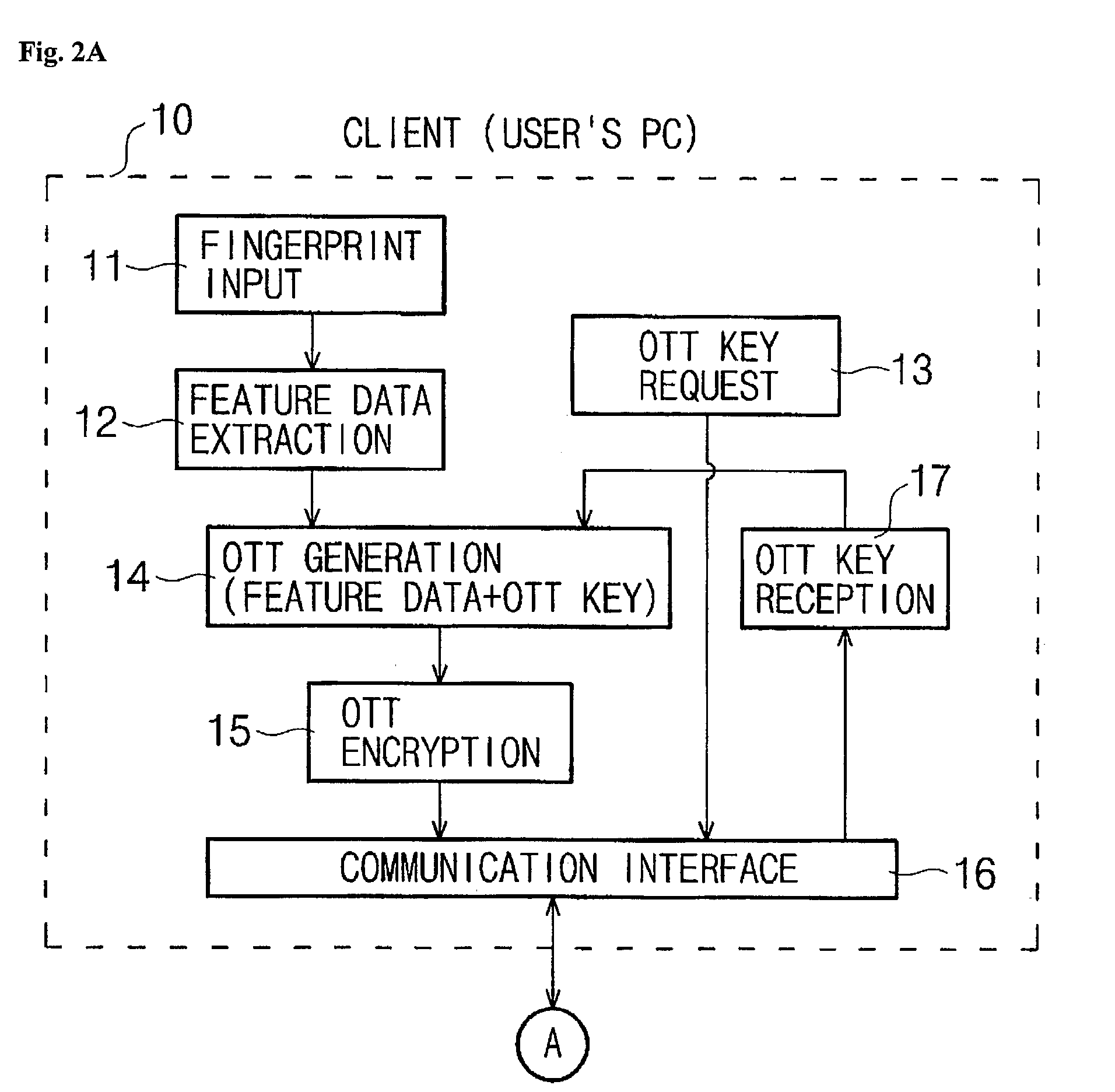
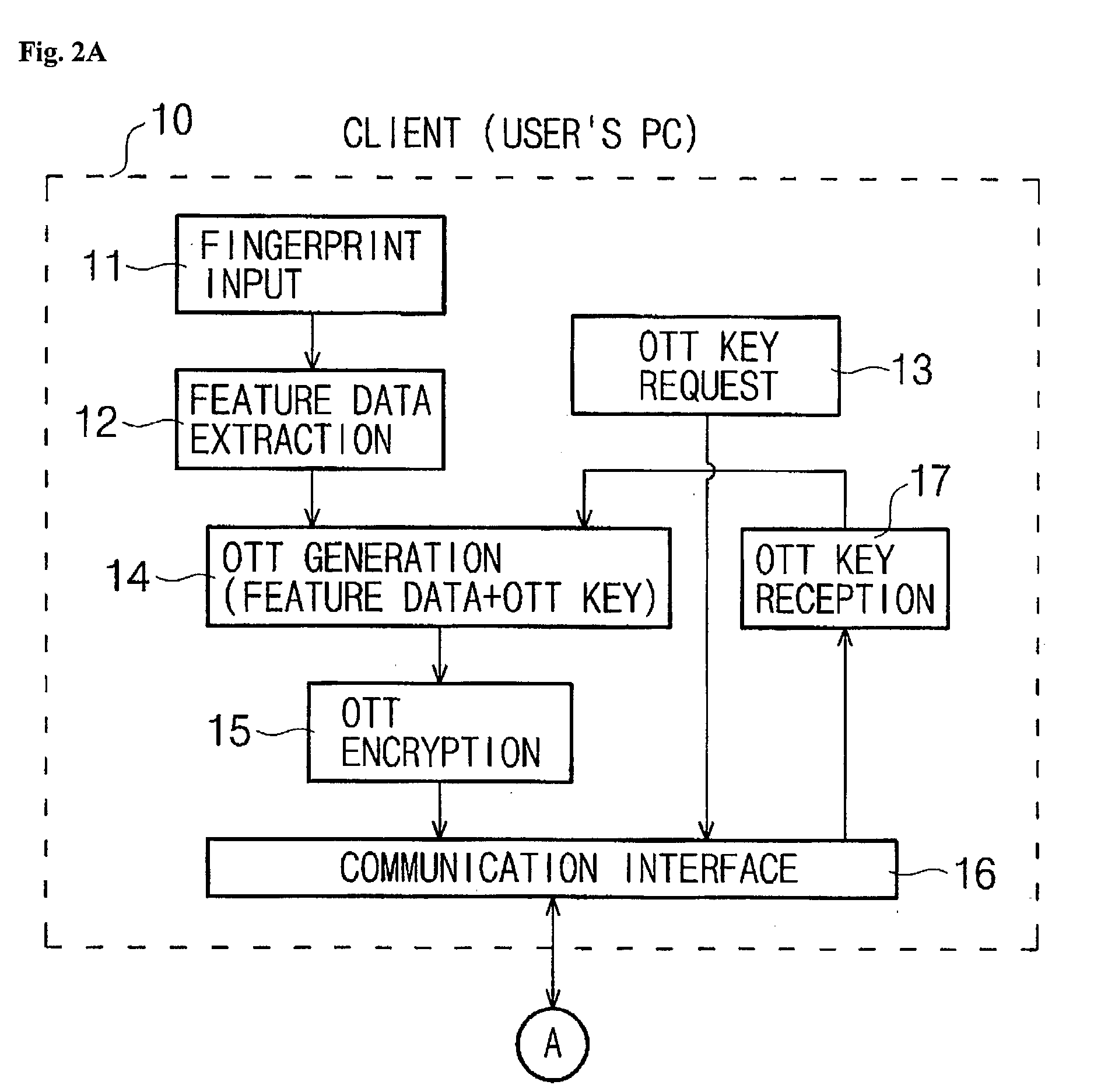
User authenticating system and method using one-time fingerprint template
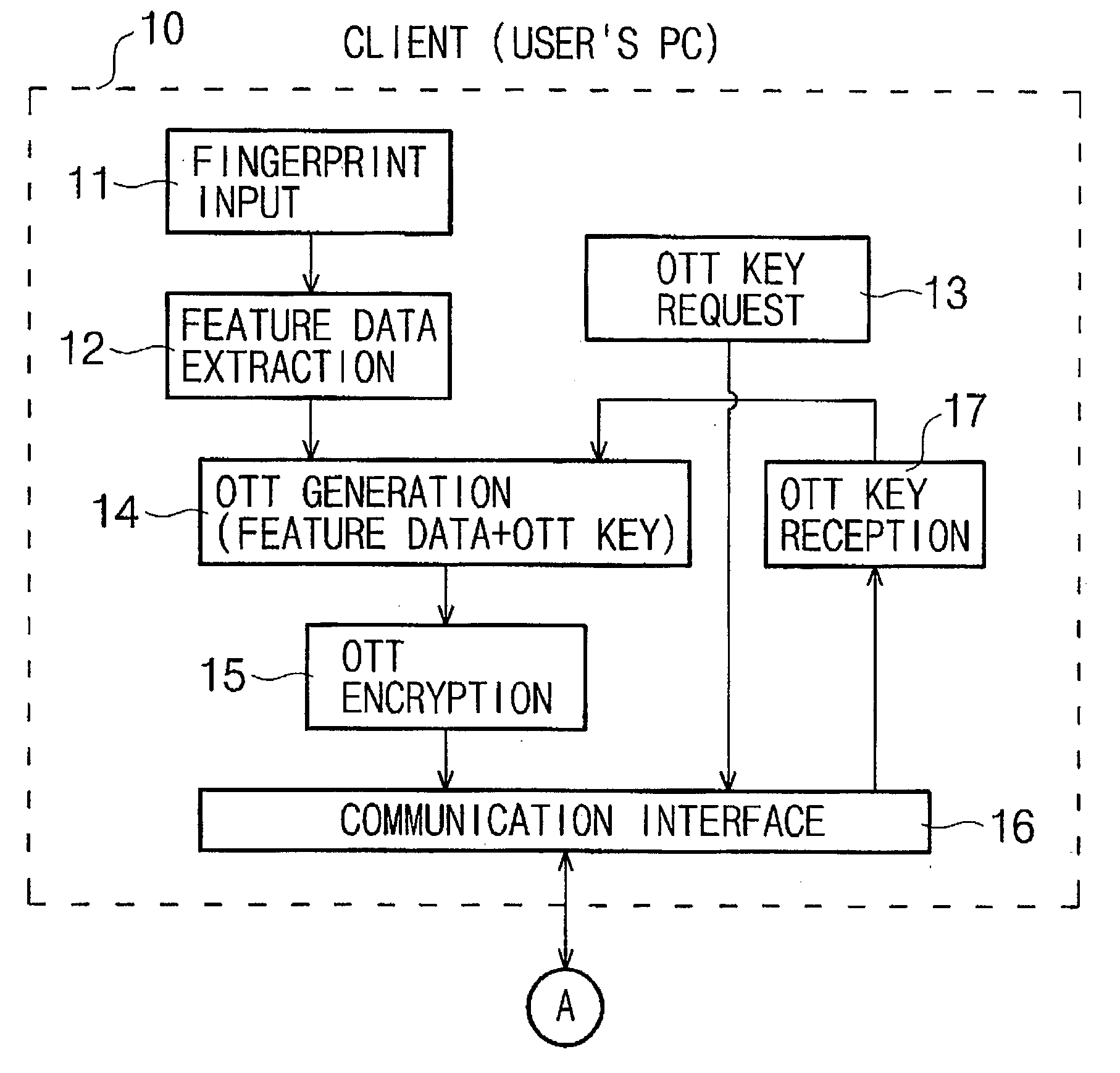
InactiveUS7035442B2Avoid authenticationElectric signal transmission systemsKey distribution for secure communicationUser authenticationFeature data
This invention relates to a user authenticating system and a method using aone-time fingerprint template. The system and the method according to the invention are improvements of the conventional user authentication based on the manner of comparing the fingerprint feature data only, for the purpose of preventing a false authentication by misusing fingerprint feature data, if exposed in the course of transfer thereof. In the system and the method according to the invention, fingerprint feature data of a user are combined with an OTT key transferred from a server. The combined result is encoded and transferred to an authenticating server. The authenticating server then confirms validity of the OTT key and authenticates the user based on the fingerprint. Thus, the present invention has an advantage of preventing a false authentication through hacking, etc., even if the OTT key is exposed to a network, because the OTT key is used only once for authentication.
Owner:SECUGEN CORP
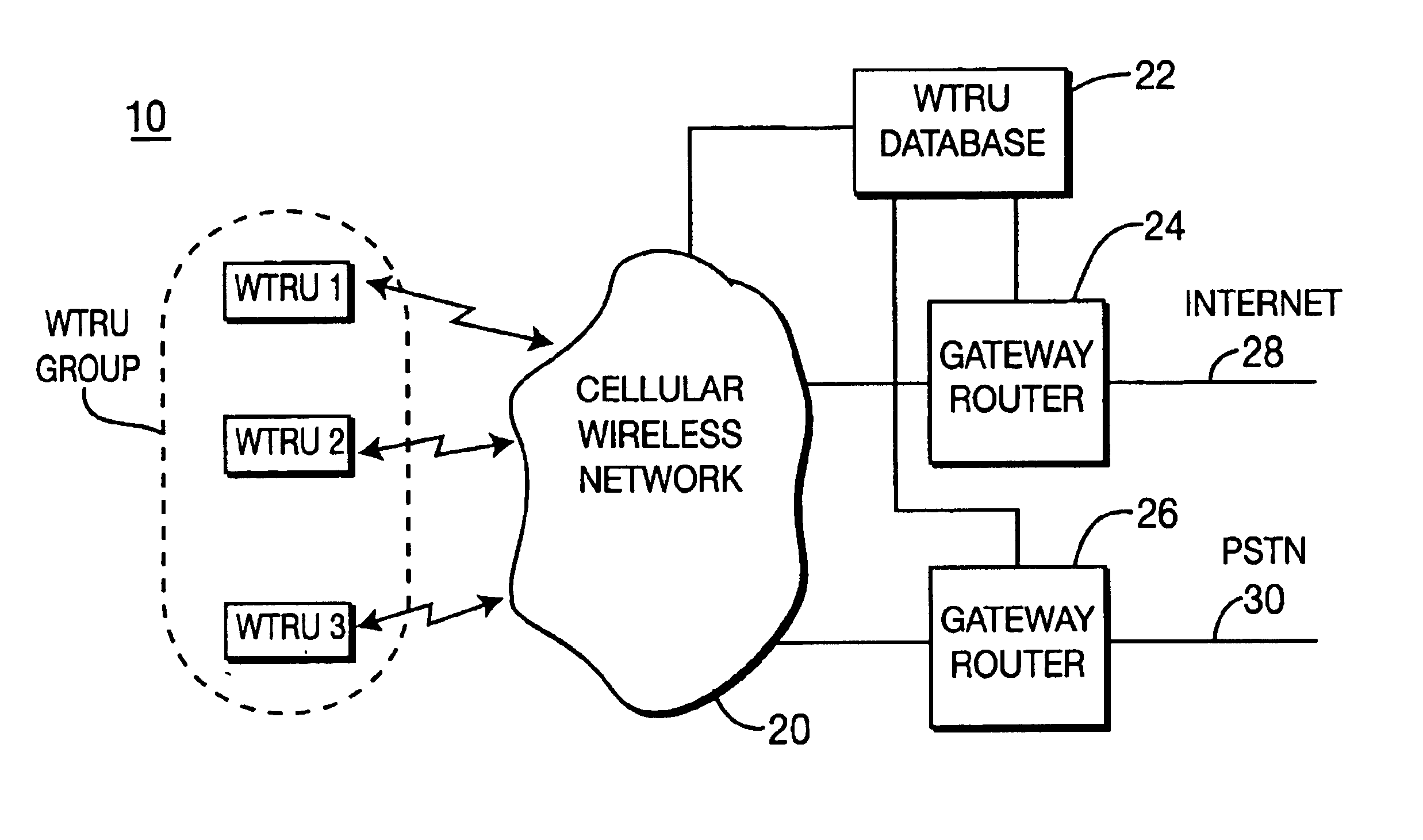
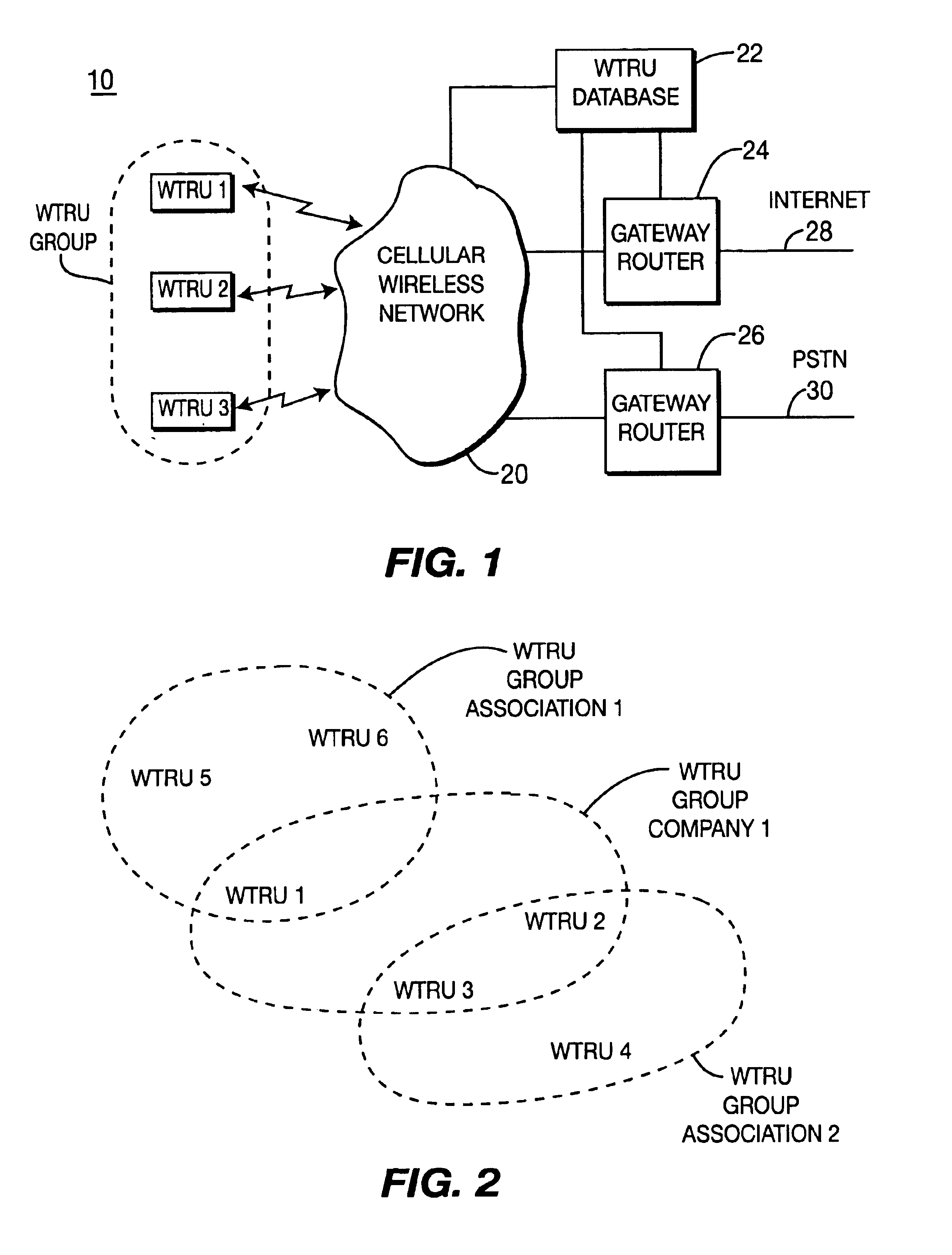
System for facilitating personal communications with multiple wireless transmit/receive units
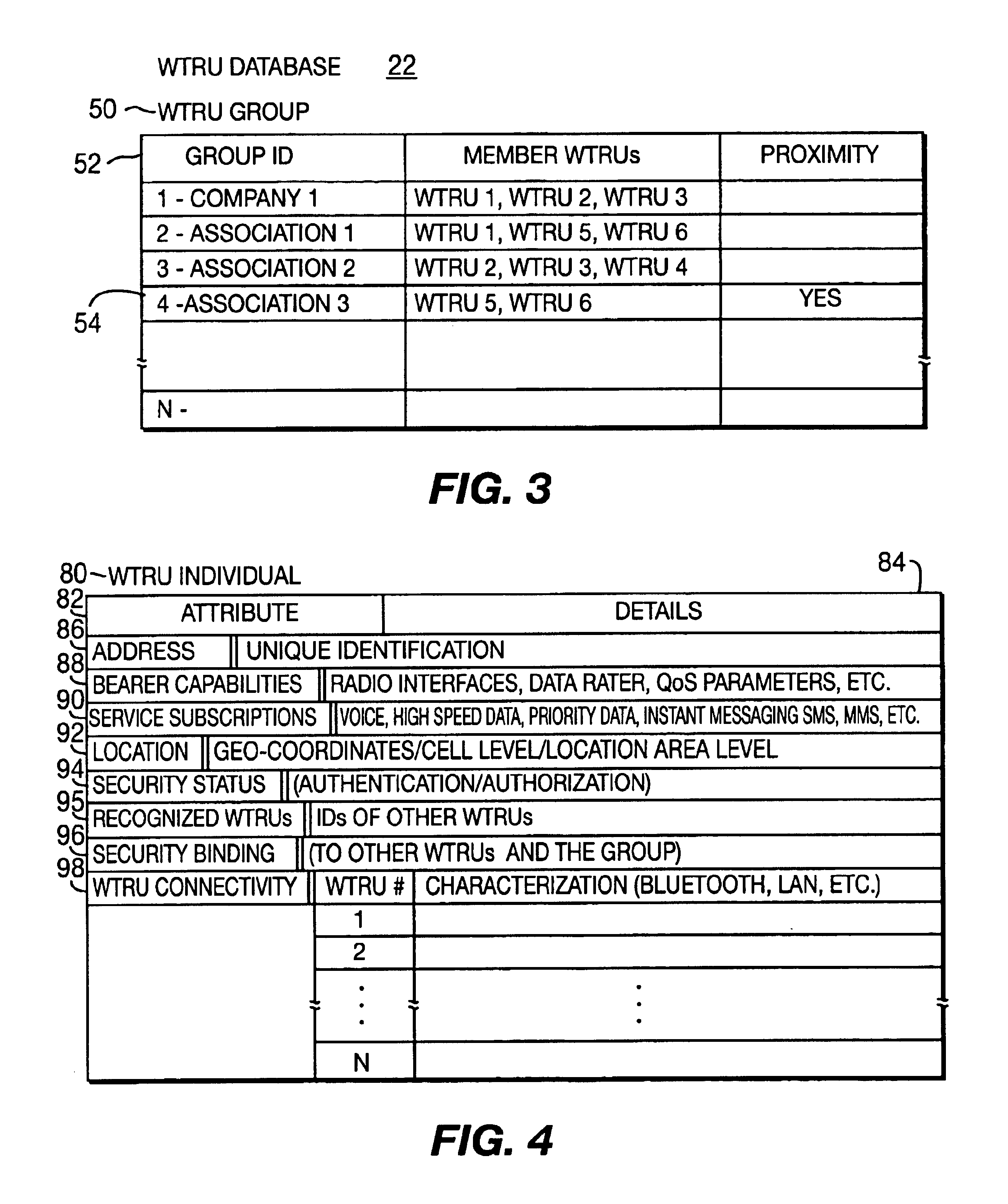
InactiveUS6853628B2Facilitating personal communicationGuaranteed normal transmissionNetwork traffic/resource managementTime-division multiplexMobility managementWireless
A system for supporting security and mobility management of wireless communications to multiple wireless transmit / receive units (WTRUs) includes a first database having a listing of each of the WTRUs along with their capabilities, and a second database having a listing of the location of each of the WTRUs. The second database has at least one subgroup which corresponds to at least two WTRUs which are co-located. The WTRUs in the subgroup are treated as a single WTRU for security and mobility management.
Owner:INTERDIGITAL TECH CORP
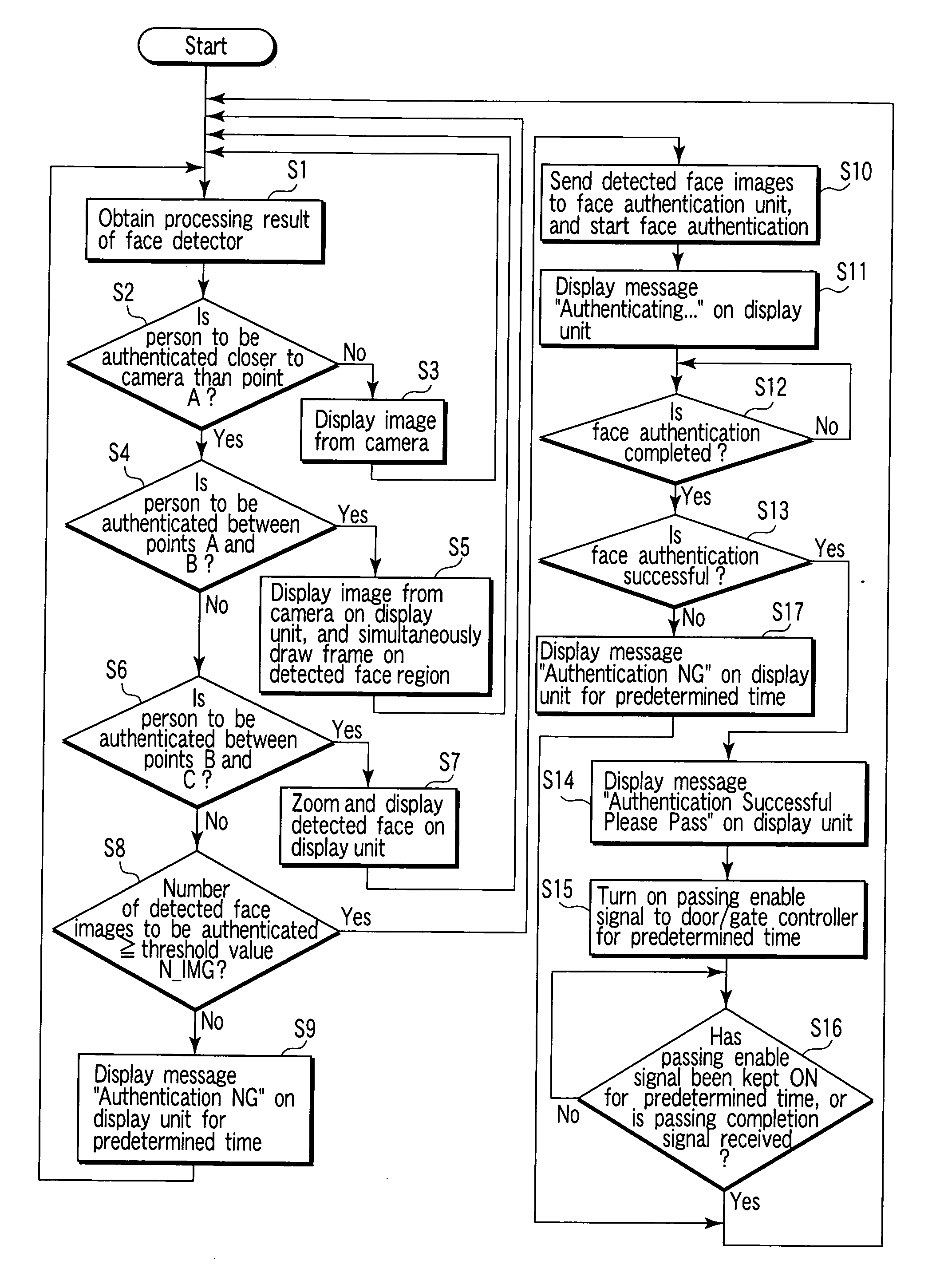
Face authentication system and gate management system
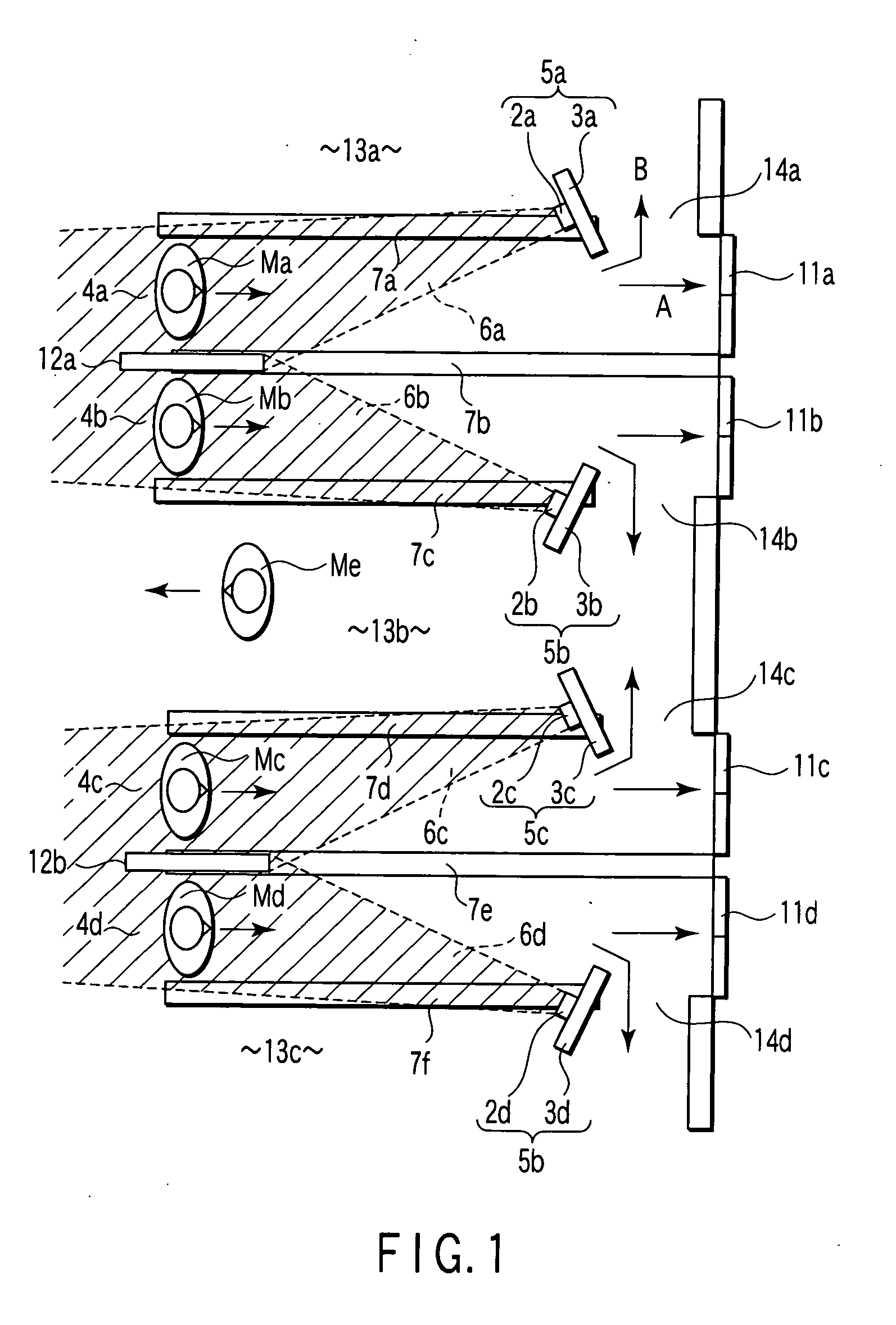
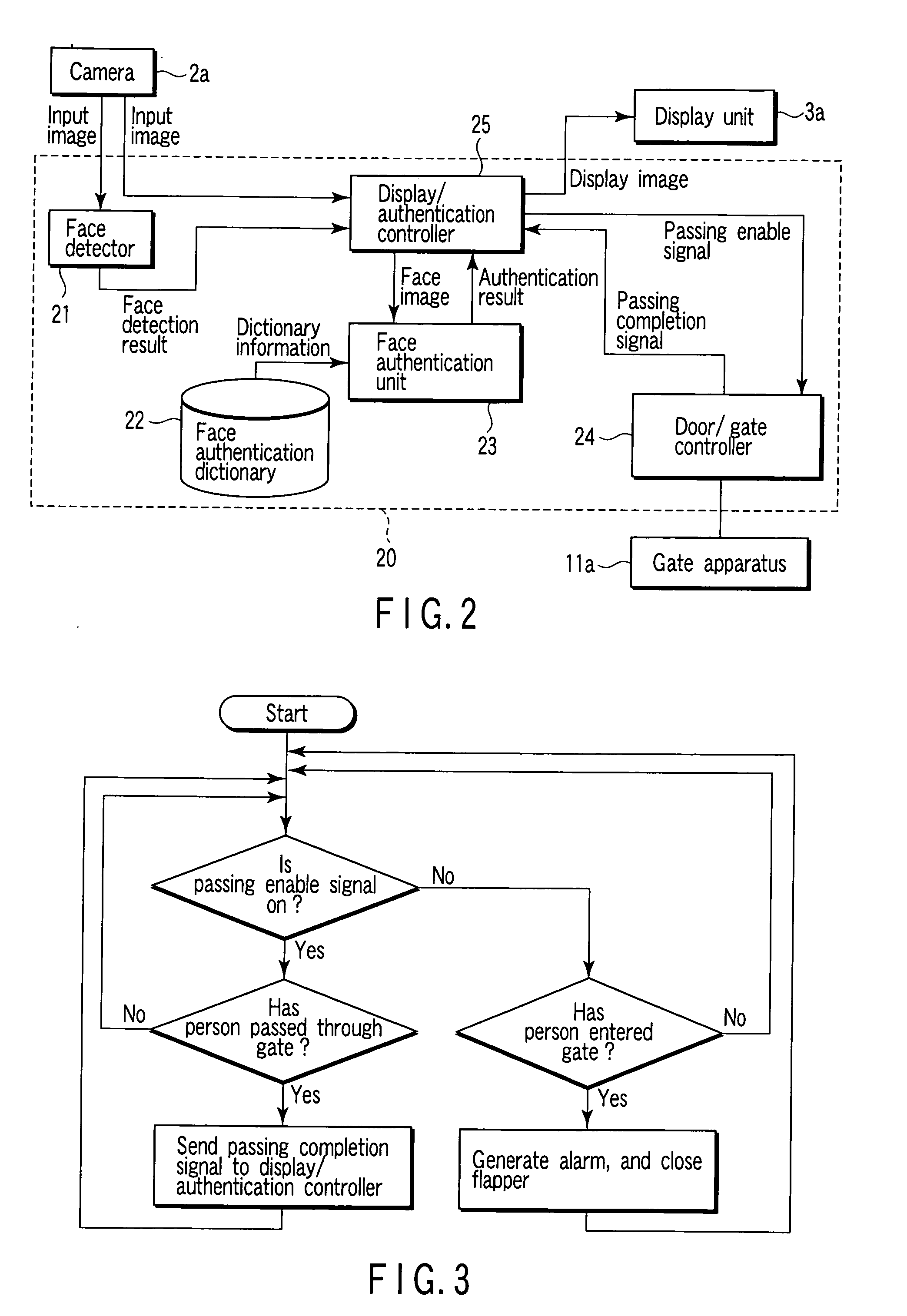
InactiveUS20070122011A1Avoid authenticationImprove accuracyTicket-issuing apparatusCharacter and pattern recognitionAuthentication systemManagement system
A face authentication system which authenticates the faces of persons passing through at least two parallel passages before the persons reach predetermined positions includes a plurality of image sensing units arranged in the predetermined positions of the plurality of passages to record images of persons passing through the passages, a plurality of face authenticating units for checking whether the persons are preregistered persons, on the basis of the images obtained from the plurality of image sensing units, and a blind plate installed between every two adjacent passages making a pair among the plurality of passages to prevent the image sensing unit installed in one passage to record a person passing through the passage from recording a person passing through the other passage. The recording direction of the image sensing unit installed in one passage points to the other passage.
Owner:KK TOSHIBA
Development method and system based on mobile terminal application program security application
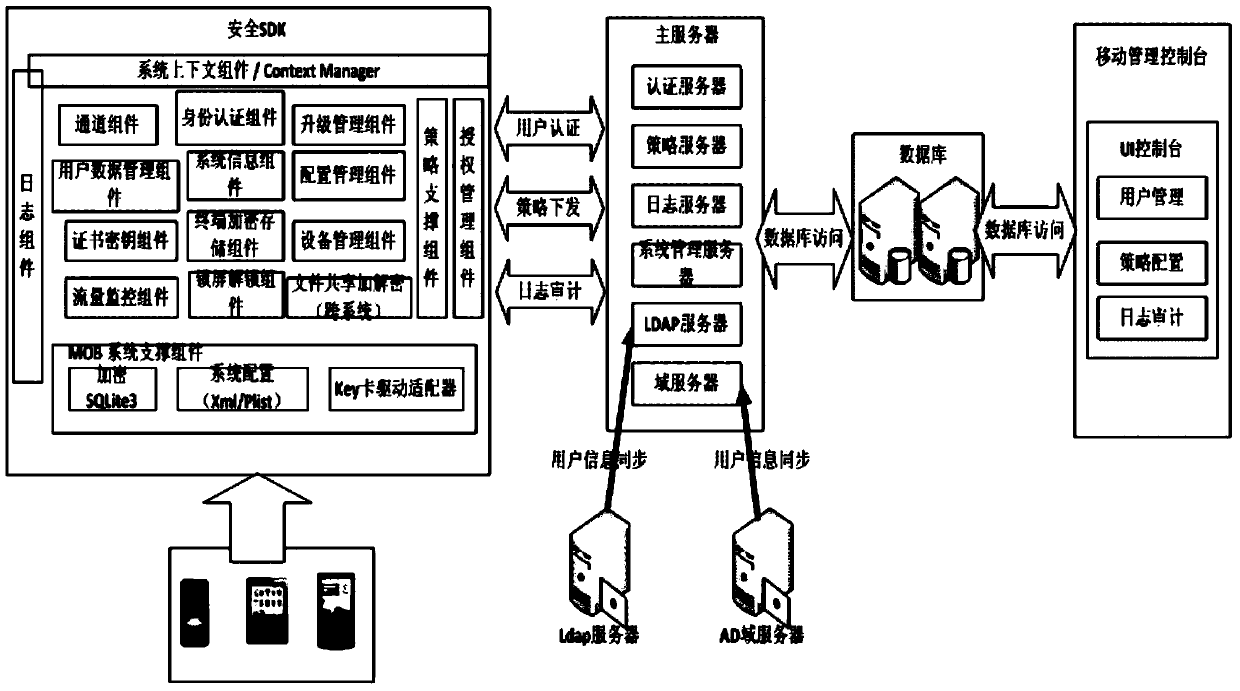
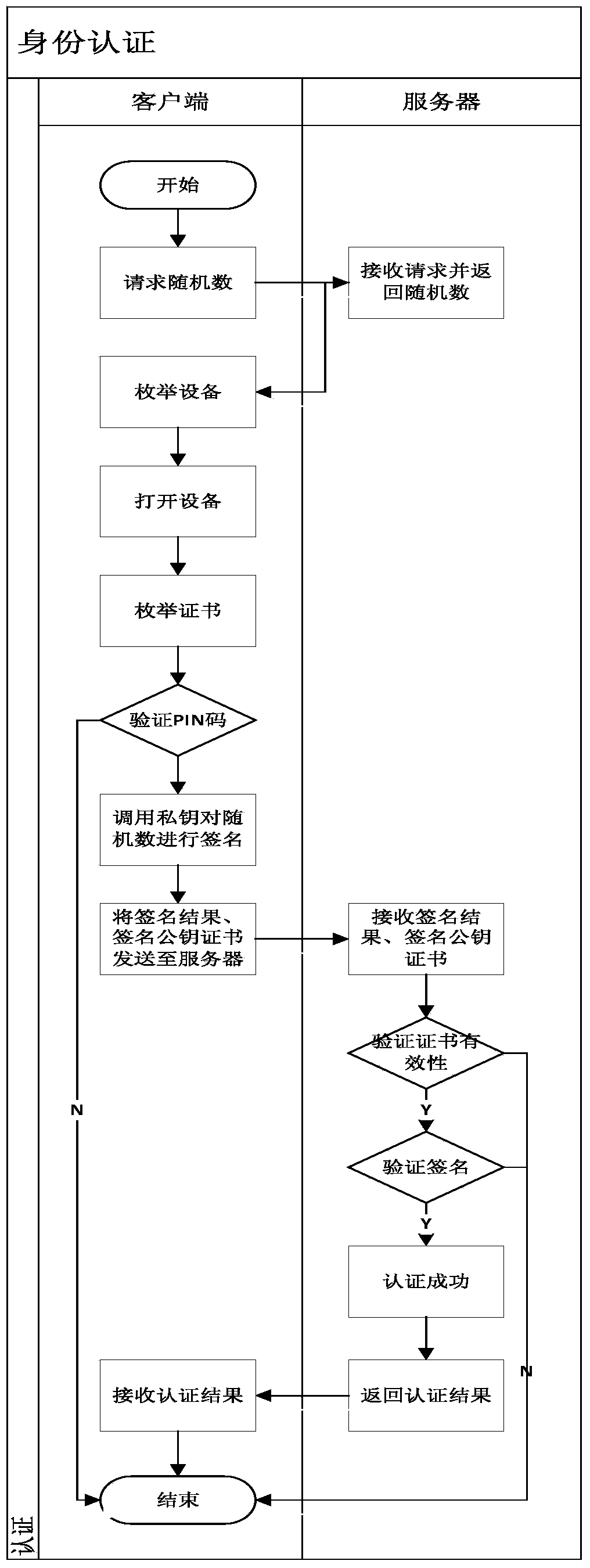
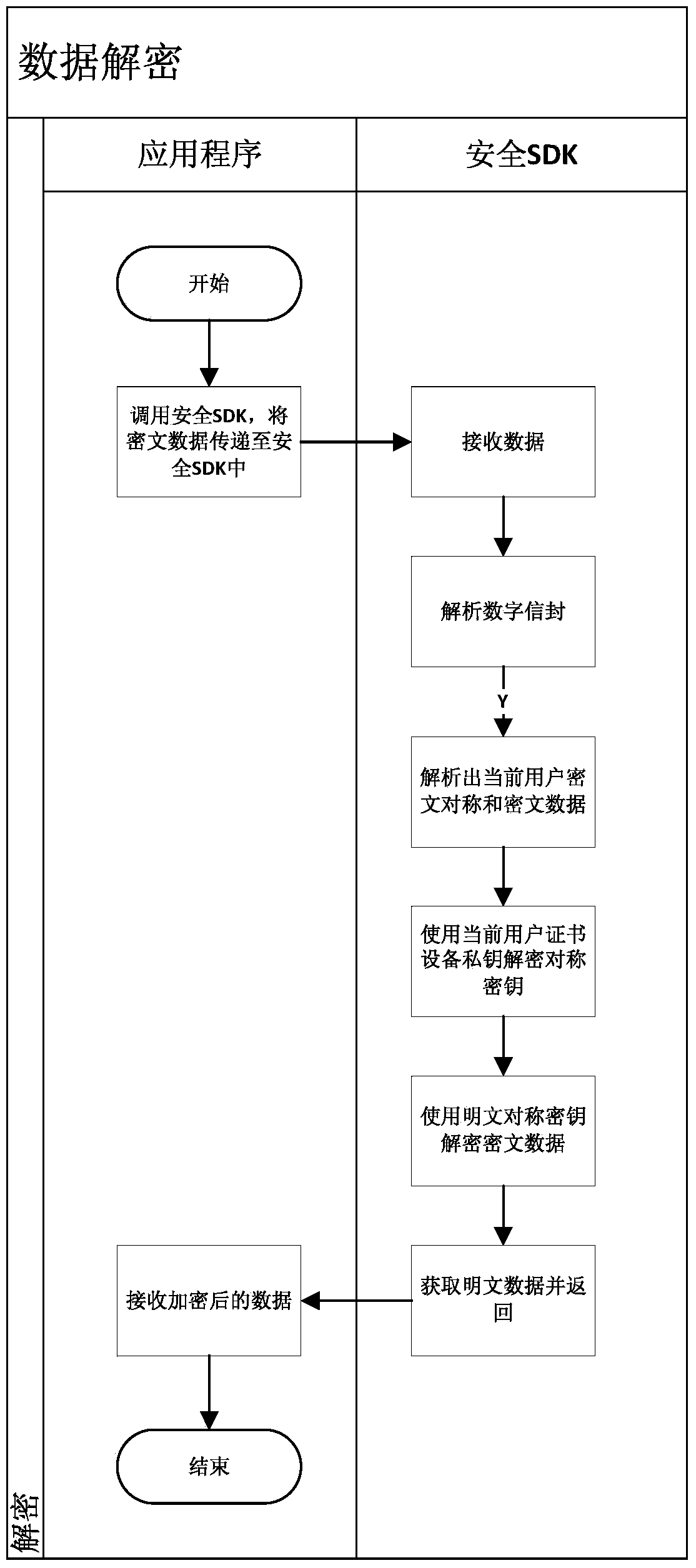
ActiveCN103812871AAvoid security issuesAvoid authenticationPublic key for secure communicationUser identity/authority verificationData informationCiphertext
The invention discloses a development method and system based on mobile terminal application program security application. The system comprises a sending terminal, a safe software development kit (SDK), a server and a receiving terminal. The method includes that the sending terminal requests a random number from the server, after the requested random number is received, a private key of the sending terminal is called to perform signing on the random number, and a signing result and a signing public key certificate are sent to the server; after the success of identity authentication, the safe SDK is called, received data information is encrypted through symmetric keys, the symmetric keys are encrypted by a public key of the receiving terminal, and encrypted symmetric keys and data information are sent to the receiving terminal; the receiving terminal calls the safe SDK to decrypt encrypted data. By means of the development method and system based on mobile terminal application program security application, related problems such as identity authentication, data breach and equipment controlling of data information safety are avoided.
Owner:北京明朝万达科技股份有限公司
User authentication apparatus, method of user authentication, and storage medium therefor
InactiveUS7114075B1Simplify manipulationSimplifying useDigital data processing detailsUser identity/authority verificationUser inputUser authentication
Apparatus of the present invention comprises a control unit controlling comparison of identifying information input by a user with identifying information stored in a storage medium, which also stores authentication information for applications corresponding to the stored identifying information. The apparatus also comprises a set unit setting, as input information for authentication system of one of the applications, the authentication information the storage medium sends to the set unit responsive to a result of the comparison.
Owner:FUJITSU LTD
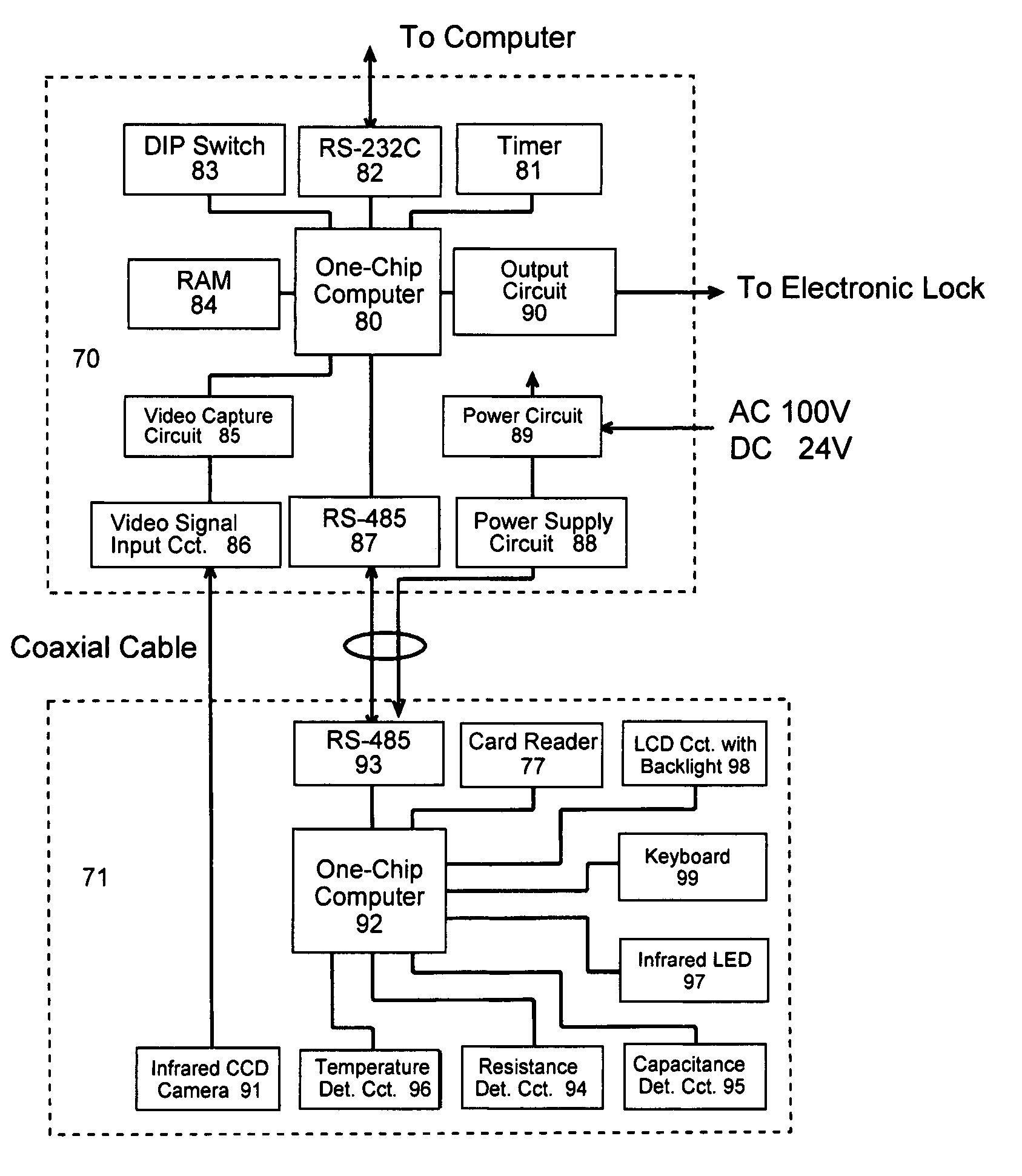
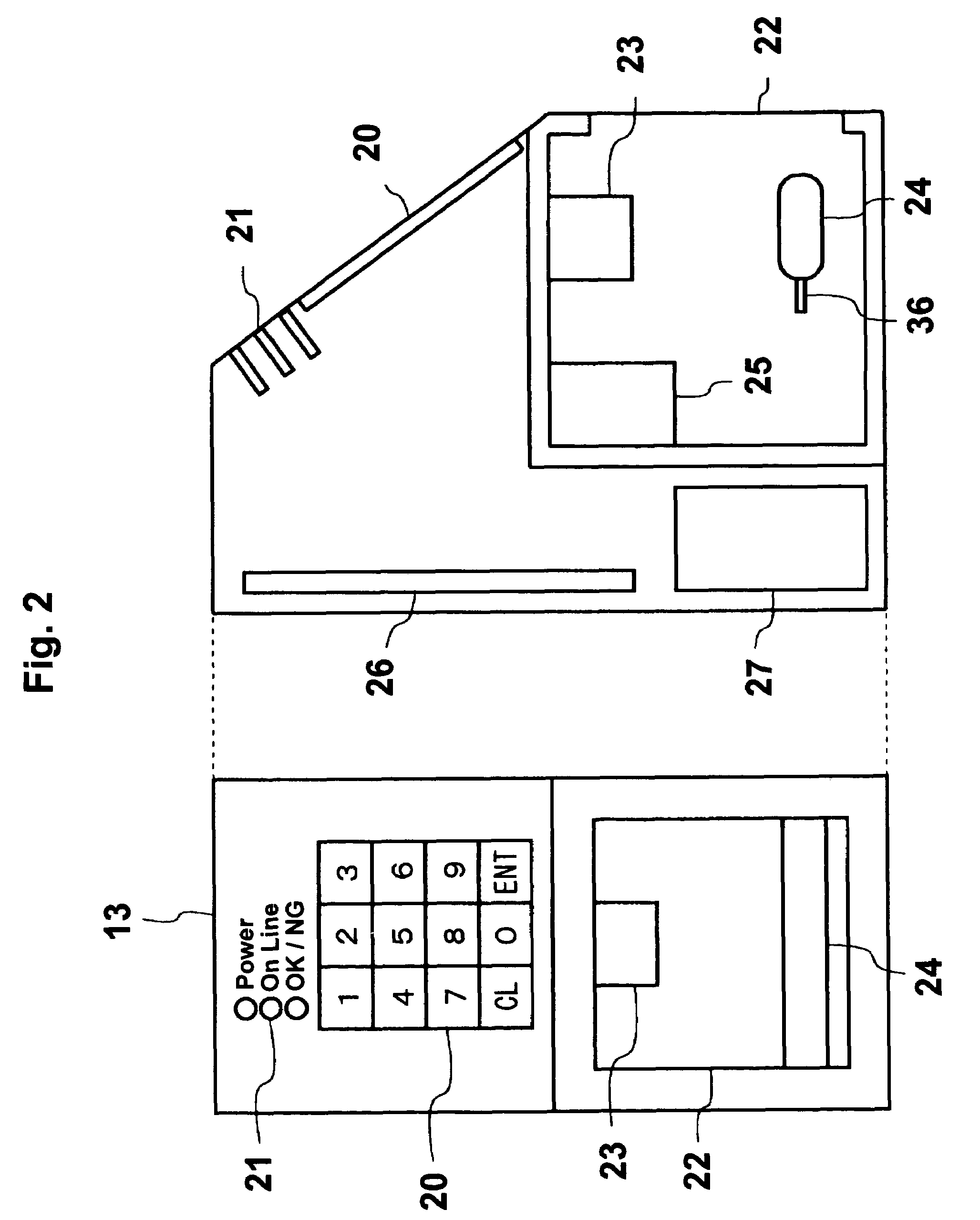
Organism authenticating apparatus
InactiveUS7327861B2Improve accuracyAvoid authenticationImage analysisDiagnostics using lightBiological bodyInfrared
The organism authenticating apparatus 71 of this invention comprises a means that fixes the position of a hand or a finger of a hand, an infrared ray radiating means 97 that radiates infrared rays, an infrared ray image input means 91 that is placed at the opposite side of said hand or said finger of a hand with regard to said infrared ray radiating means, an organism recognizing means that recognizes that the organism is live, a processing means that processes data that are inputted by said infrared ray image input means so that it collates them with image data that are registered in advance and an output means that outputs the result of processing carried out by said processing means. By using this invention, it becomes possible to obtain a clear blood vessel pattern image by a compact size apparatus by using an infrared ray source and by capturing the passed-through infrared ray image of the organism, and it becomes possible by using an organism recognizing means to prevent false authentication.
Owner:BIONICS
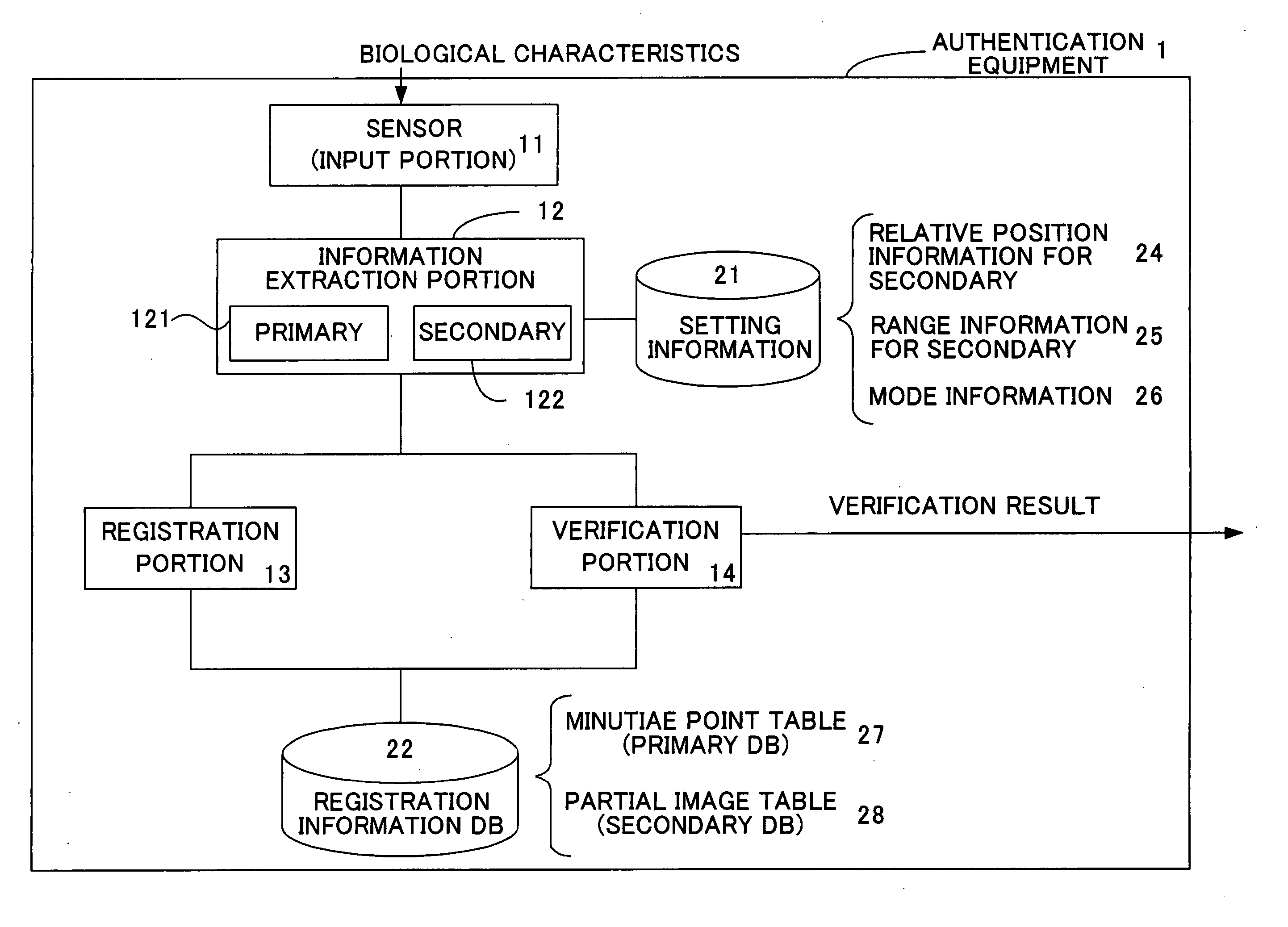
Authentication method based on biological characteristic information
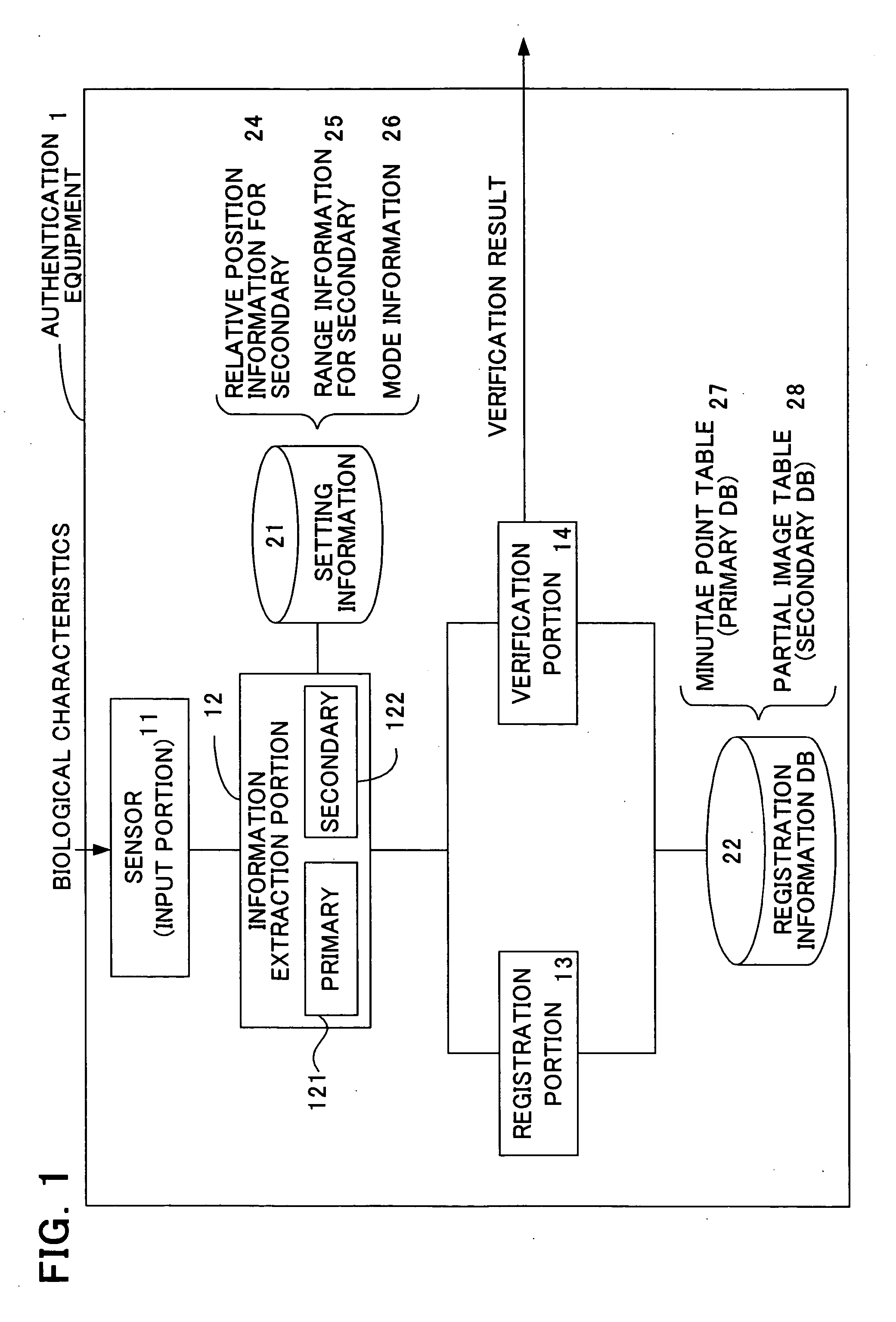
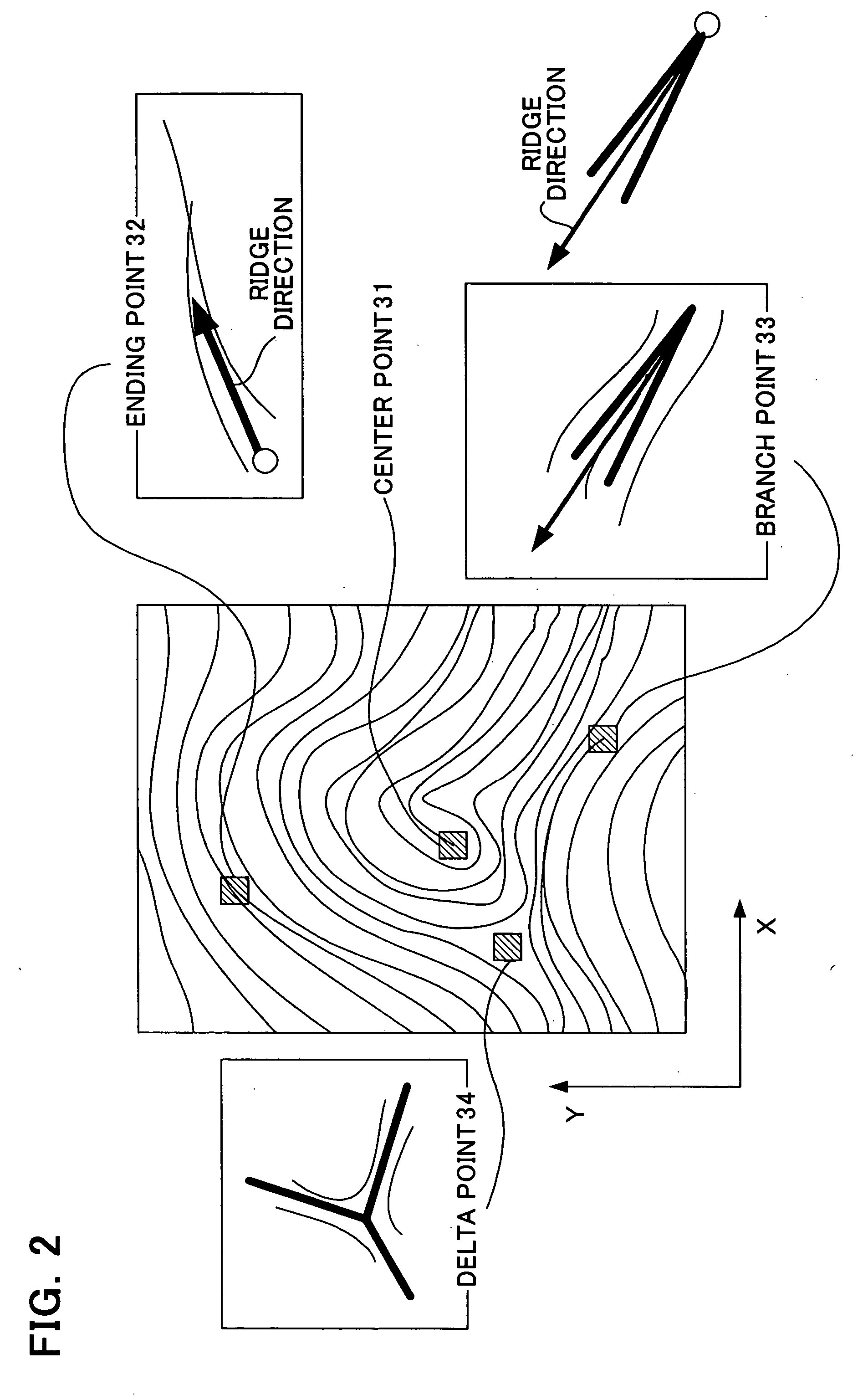
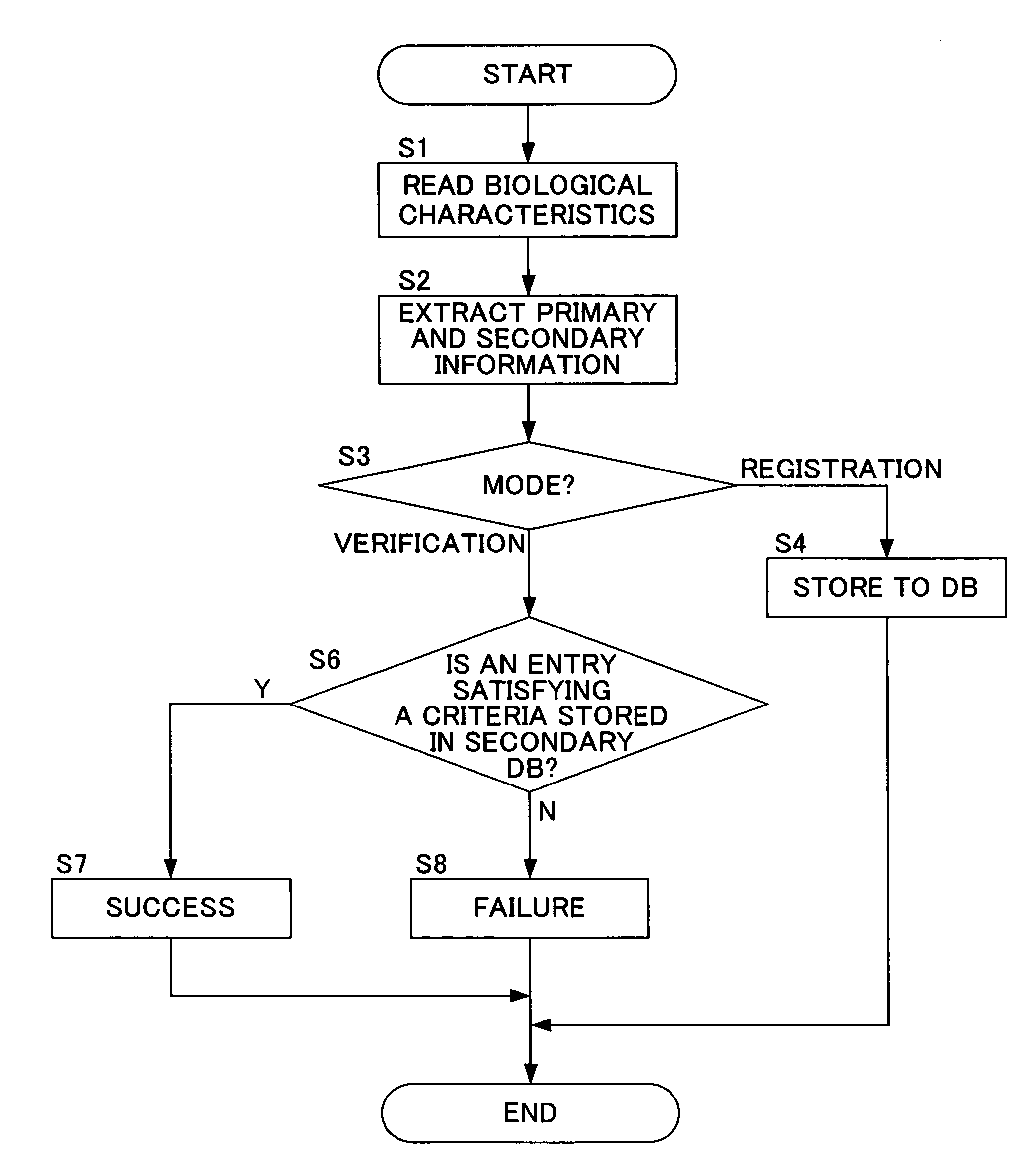
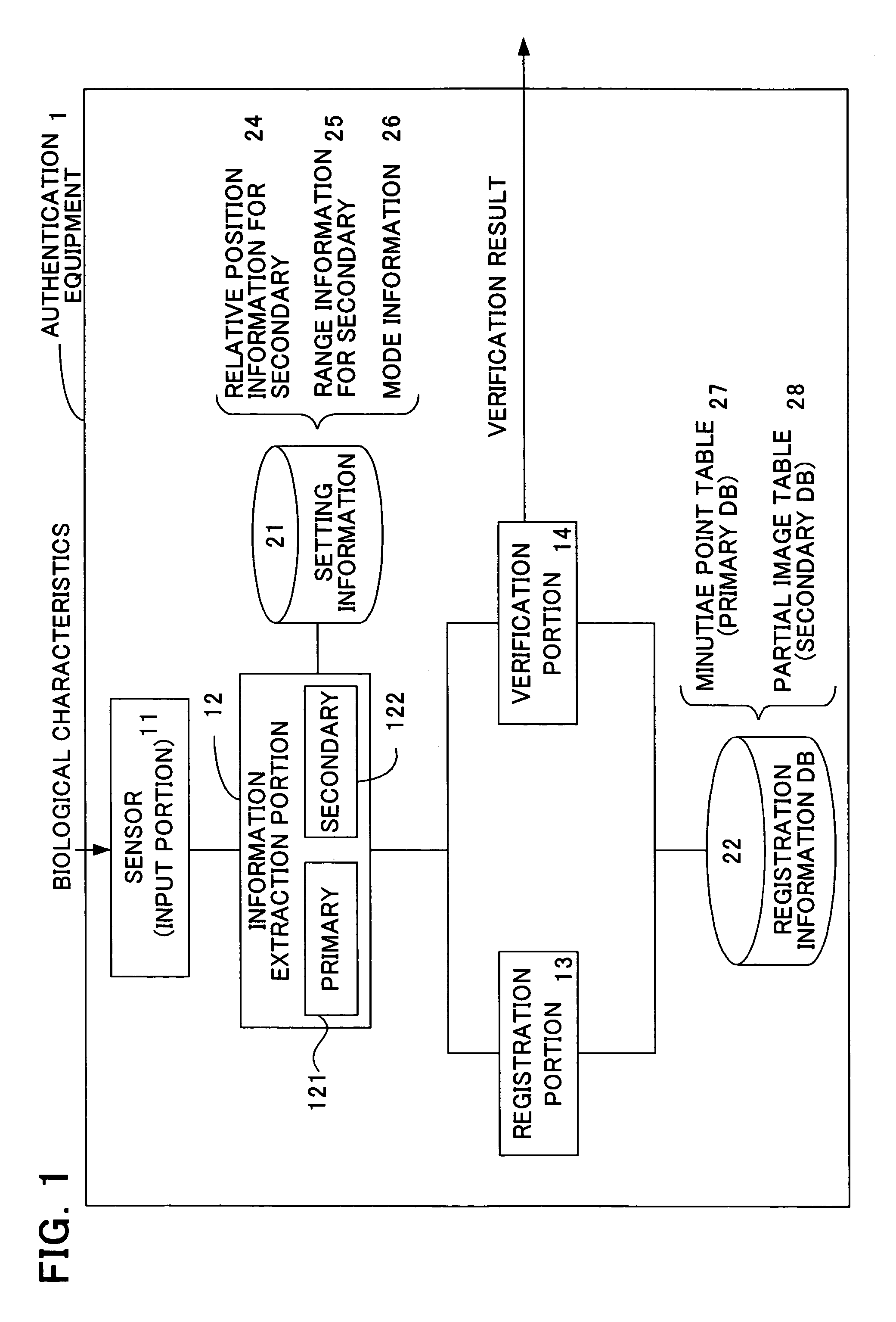
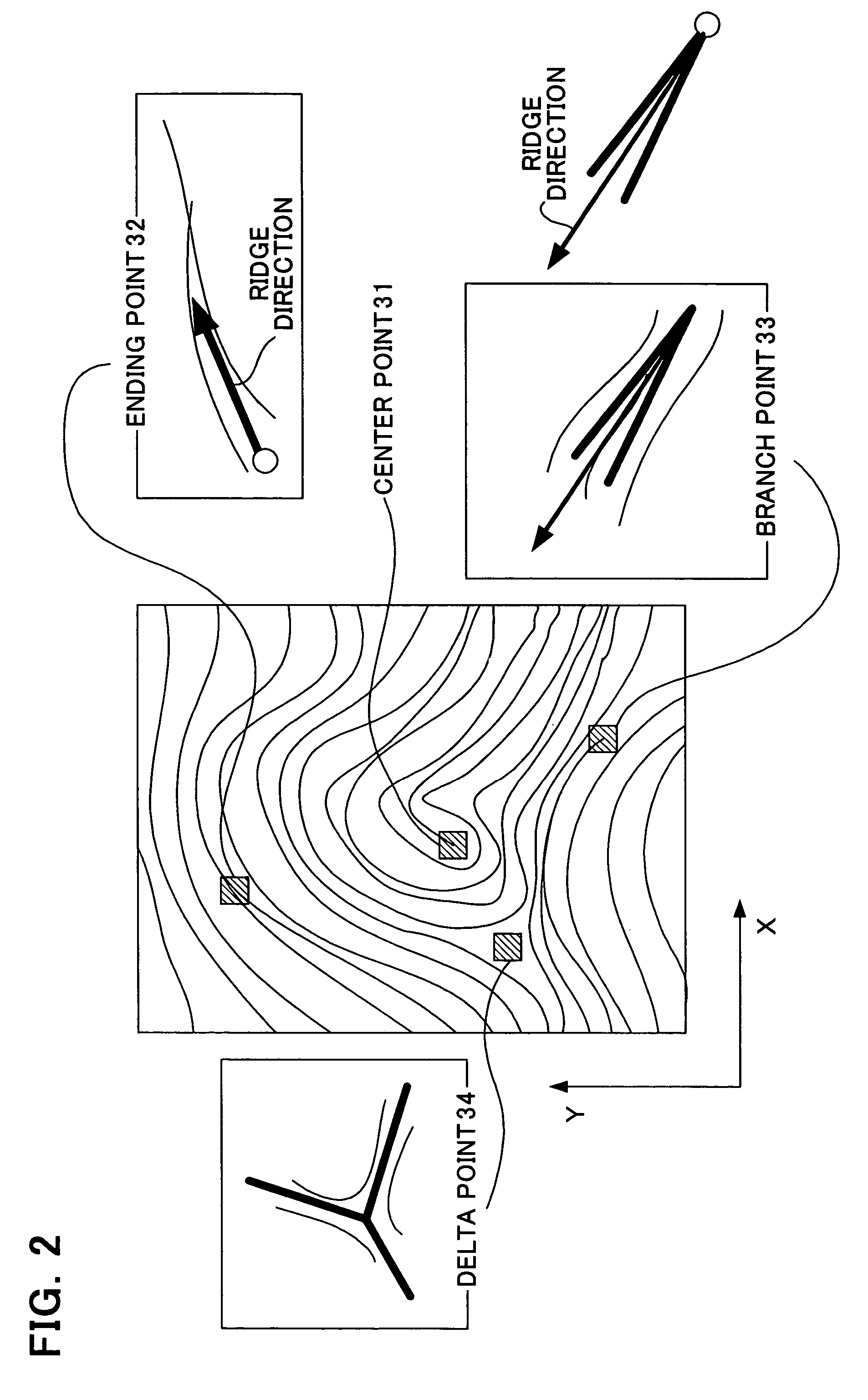
InactiveUS20060047970A1Reduce the burden onImprove authentication accuracyDigital data authenticationSecret communicationBiometricsAuthentication
The present invention provides authentication equipment having functions for prevention of erroneous authentication using biometrics data, and which can reduce the burden of registration placed on users. The authentication equipment is characterized in comprising an input portion, which generates primitive-format information of biological characteristics based on biological characteristics specific to individuals; a primary information extraction portion, which extracts primary information identifying the biological characteristics from the primitive-format information; a secondary information extraction portion, which extracts, as secondary information, a part of the primitive-format information using the primary information; a registration portion, which stores in a storage portion the secondary information extracted by the secondary information extraction portion; and a verification portion, which compares the secondary information extracted by the secondary information extraction portion with secondary information stored in the storage portion, and judges whether authentication has been successful.
Owner:FUJITSU LTD
User authenticating system and method using one-time fingerprint template
InactiveUS20030152254A1Avoid authenticationKey distribution for secure communicationElectric signal transmission systemsUser authenticationFeature data
This invention relates to a user authenticating system and a method using aone-time fingerprint template. The system and the method according to the invention are improvements of the conventional user authentication based on the manner of comparing the fingerprint feature data only, for the purpose of preventing a false authentication by misusing fingerprint feature data, if exposed in the course of transfer thereof. In the system and the method according to the invention, fingerprint feature data of a user are combined with an OTT key transferred from a server. The combined result is encoded and transferred to an authenticating server. The authenticating server then confirms validity of the OTT key and authenticates the user based on the fingerprint. Thus, the present invention has an advantage of preventing a false authentication through hacking, etc., even if the OTT key is exposed to a network, because the OTT key is used only once for authentication.
Owner:SECUGEN CORP
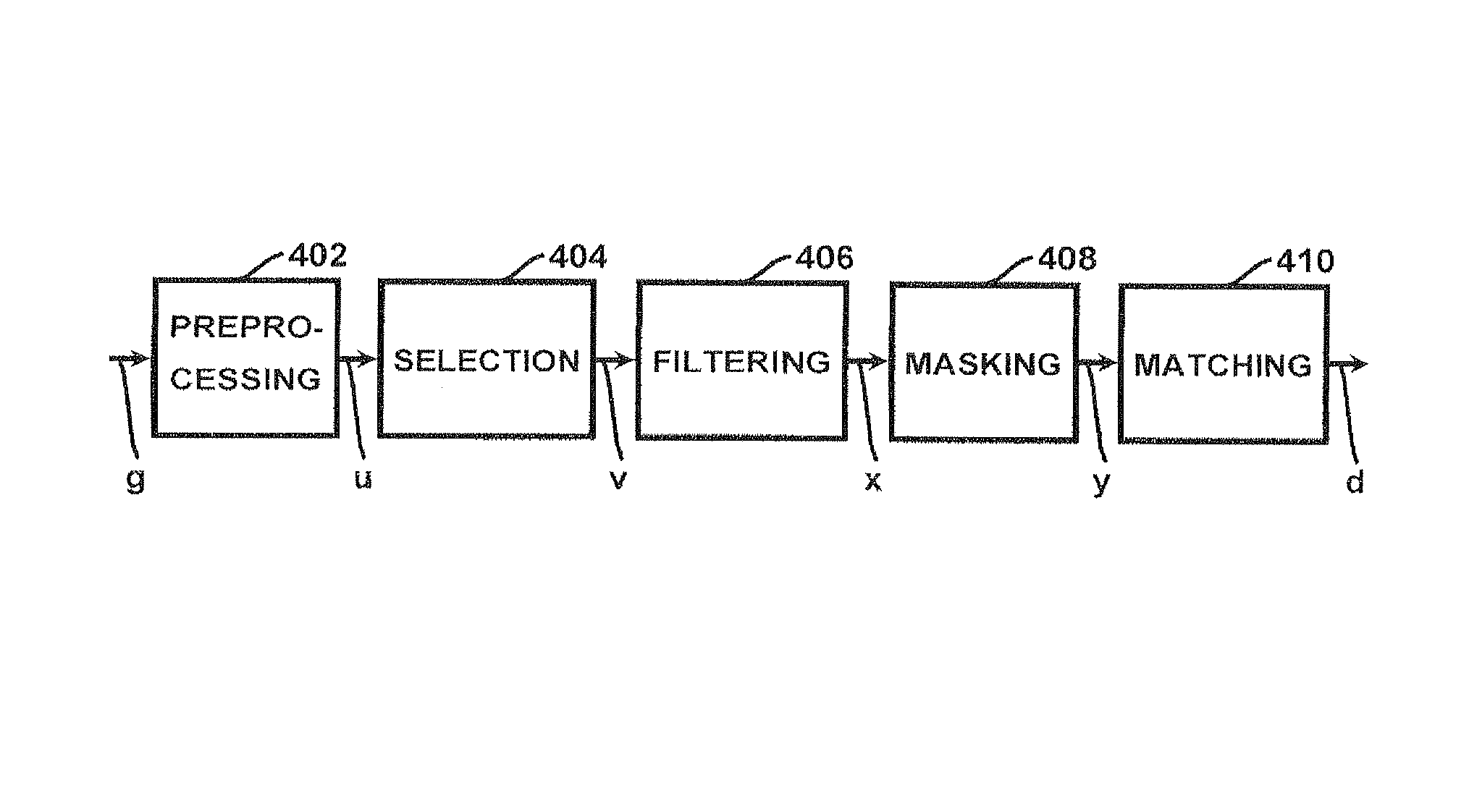
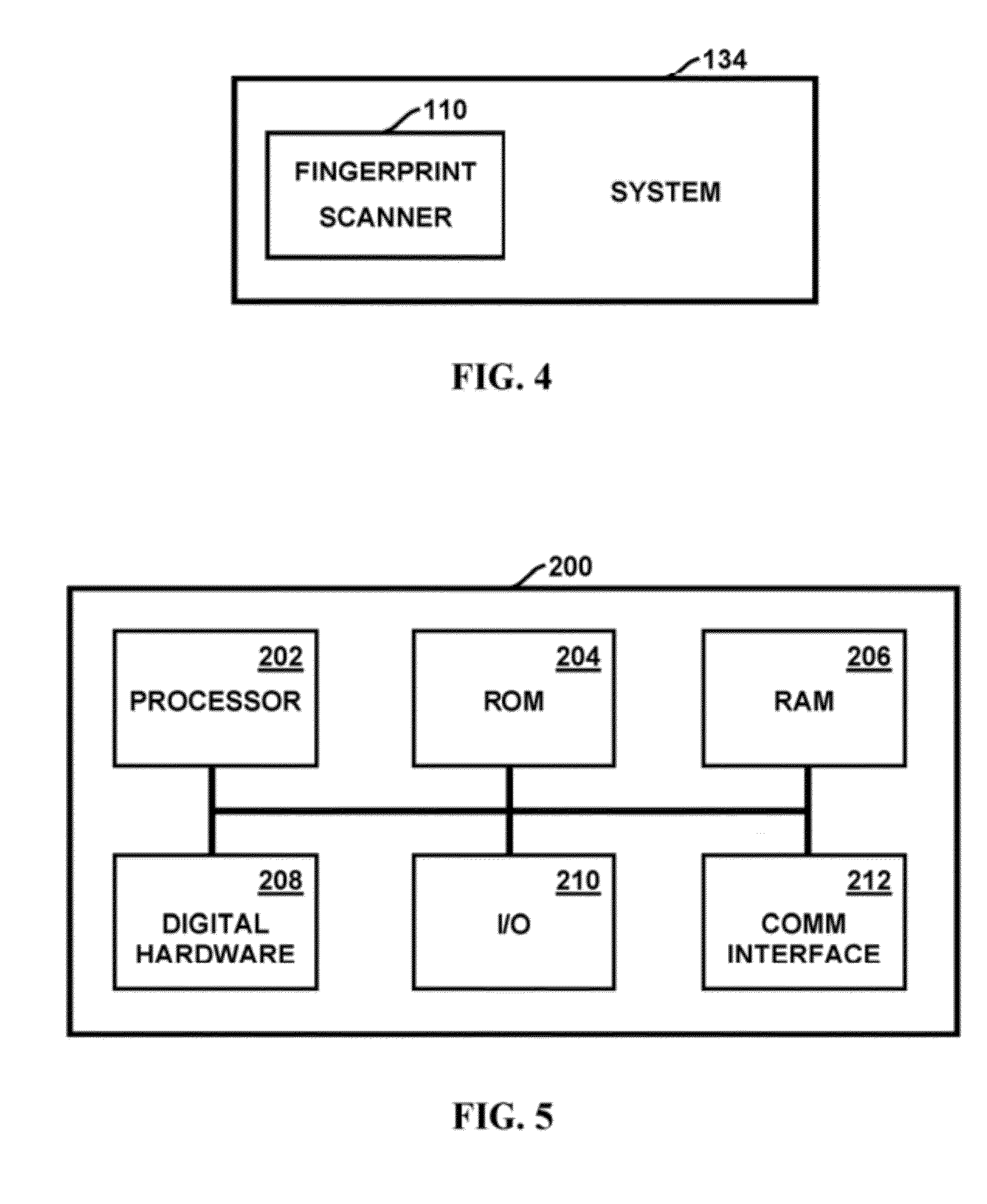
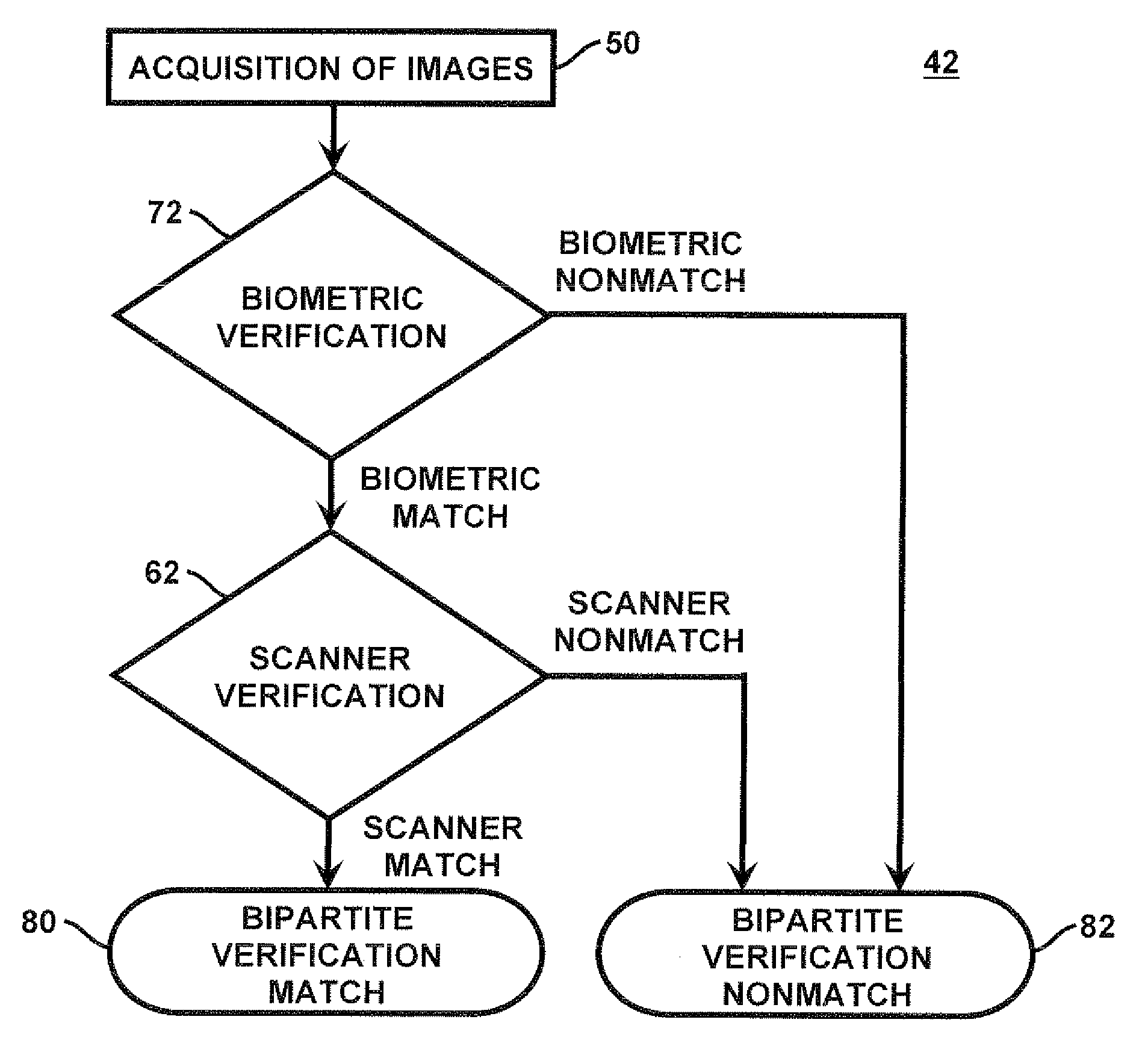
Method and apparatus for authenticating biometric scanners
ActiveUS8953848B2Improve security levelAvoid attackMatching and classificationPattern recognitionImaging processing
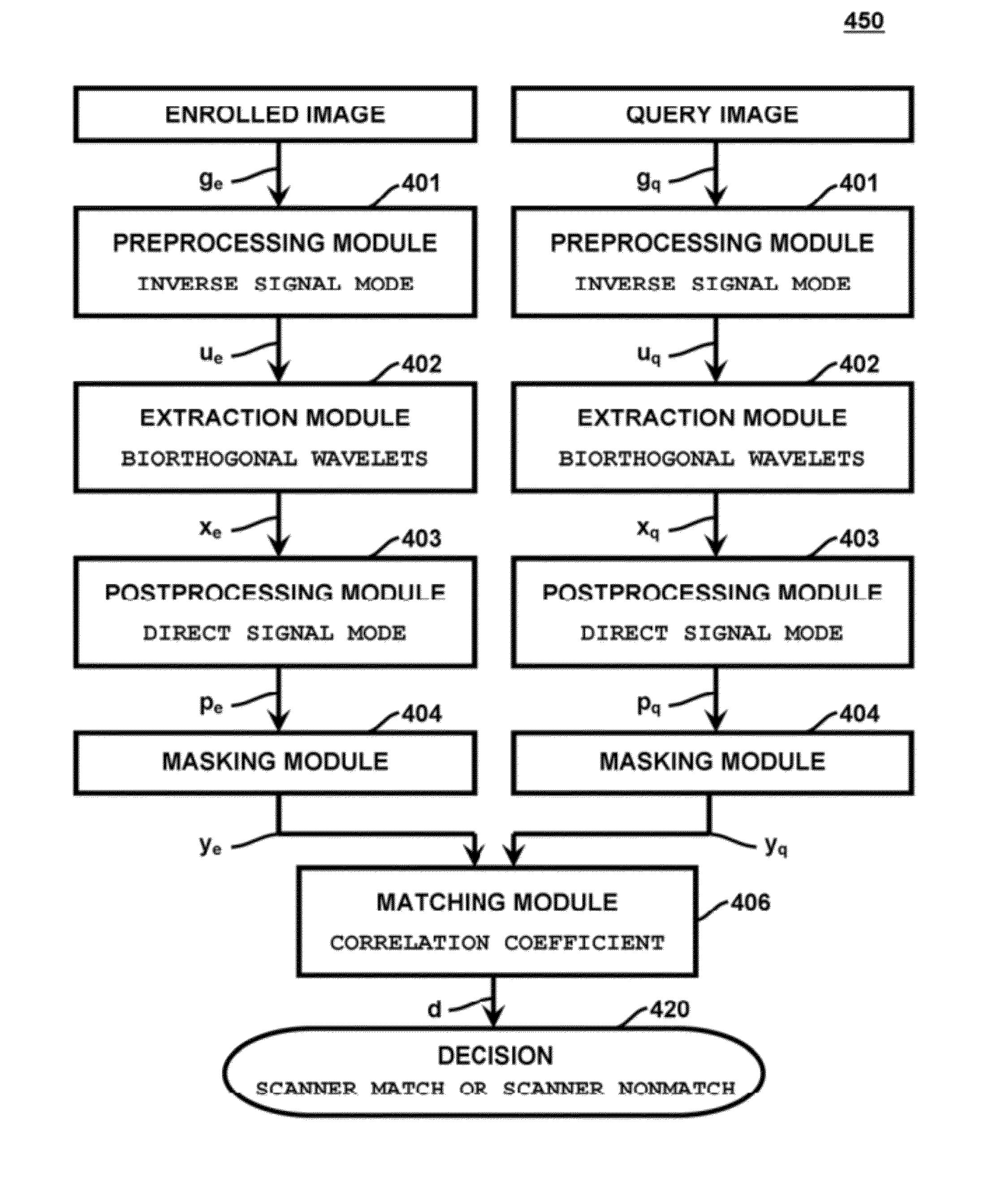
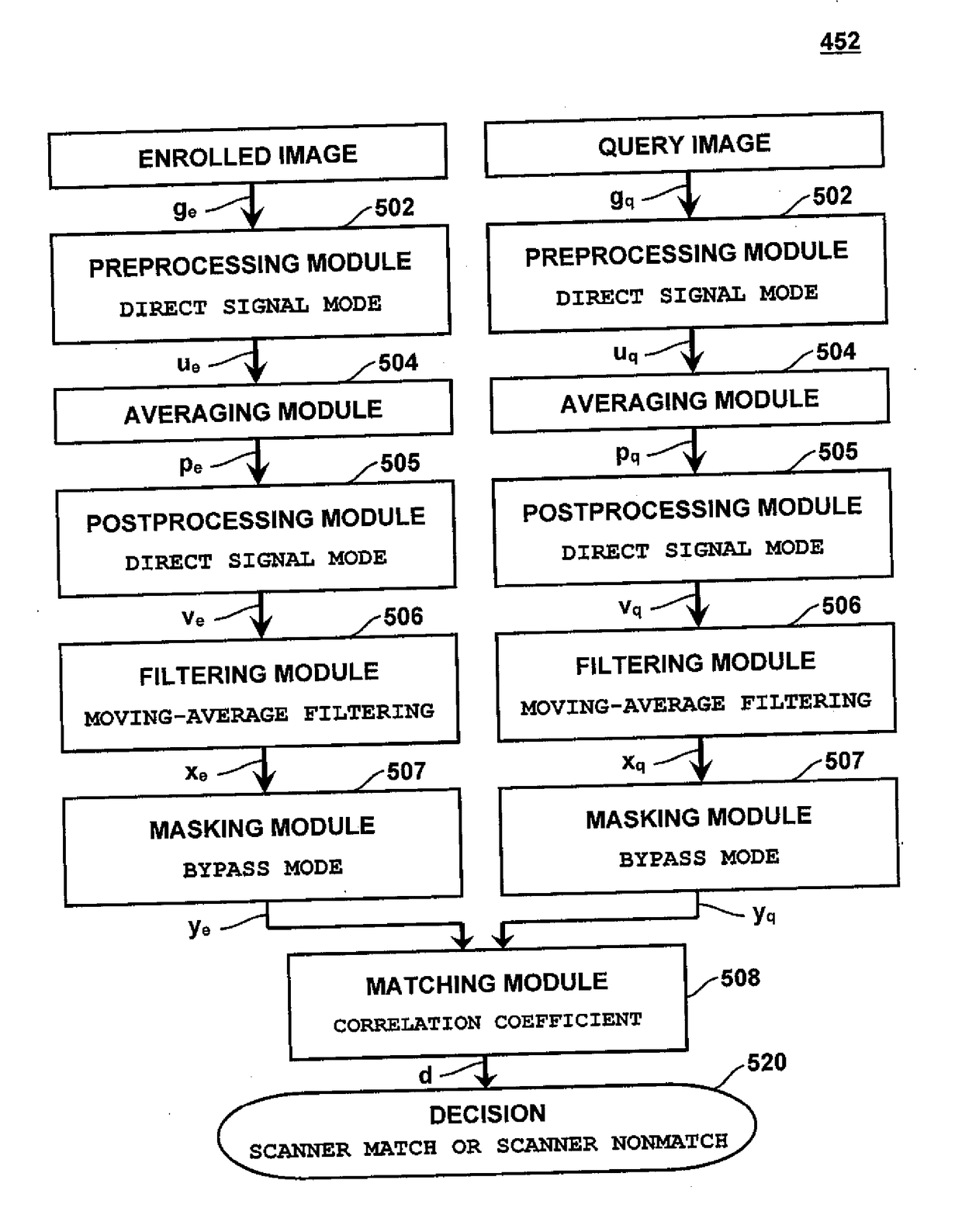
Methods and systems involving image processing extract from an image and estimate unique intrinsic characteristics (scanner pattern) of a biometric scanner, such as area type fingerprint scanner. The scanner pattern is permanent over time, can identify a scanner even among scanners of the same manufacturer and model, and can be used to verify if a scanner acquired an image is the same as the scanner used for biometric enrollment, i.e., to authenticate the scanner and prevent security attacks on it. One method comprises selecting pixels from an enrolled and query image, masking useful pixels from the images, computing a similarity score between the common pixels of the enrolled and query useful pixels, and comparing this score with a threshold to determine whether the query image has been acquired by the same scanner as the enrolled image. The method can further comprise inverting the pixel values and / or filtering the selected pixels.
Owner:UNIV OF MARYLAND
Method and apparatus for authenticating biometric scanners
ActiveUS20140133714A1Avoid authenticationImprove security levelMatching and classificationPattern recognitionImaging processing
Methods and systems involving image processing extract from an image and estimate unique intrinsic characteristics (scanner pattern) of a biometric scanner, such as area type fingerprint scanner. The scanner pattern is permanent over time, can identify a scanner even among scanners of the same manufacturer and model, and can be used to verify if a scanner acquired an image is the same as the scanner used for biometric enrollment, i.e., to authenticate the scanner and prevent security attacks on it. One method comprises selecting pixels from an enrolled and query image, masking useful pixels from the images, computing a similarity score between the common pixels of the enrolled and query useful pixels, and comparing this score with a threshold to determine whether the query image has been acquired by the same scanner as the enrolled image. The method can further comprise inverting the pixel values and / or filtering the selected pixels.
Owner:UNIV OF MARYLAND
Method and apparatus for authenticating swipe biometric scanners
ActiveUS8942438B2Improve securityAvoid attackImage enhancementPrint image acquisitionImaging processingUser authentication
Methods and apparatuses for authenticating a biometric scanner, such as swipe type finger print scanners, involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeit biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND BALTIMORE
Method and apparatus for authenticating biometric scanners
ActiveUS20110013814A1Improve security levelAvoid attackImage analysisCharacter and pattern recognitionImaging processingUser authentication
A method and apparatus for authenticating a biometric scanner involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeited biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND
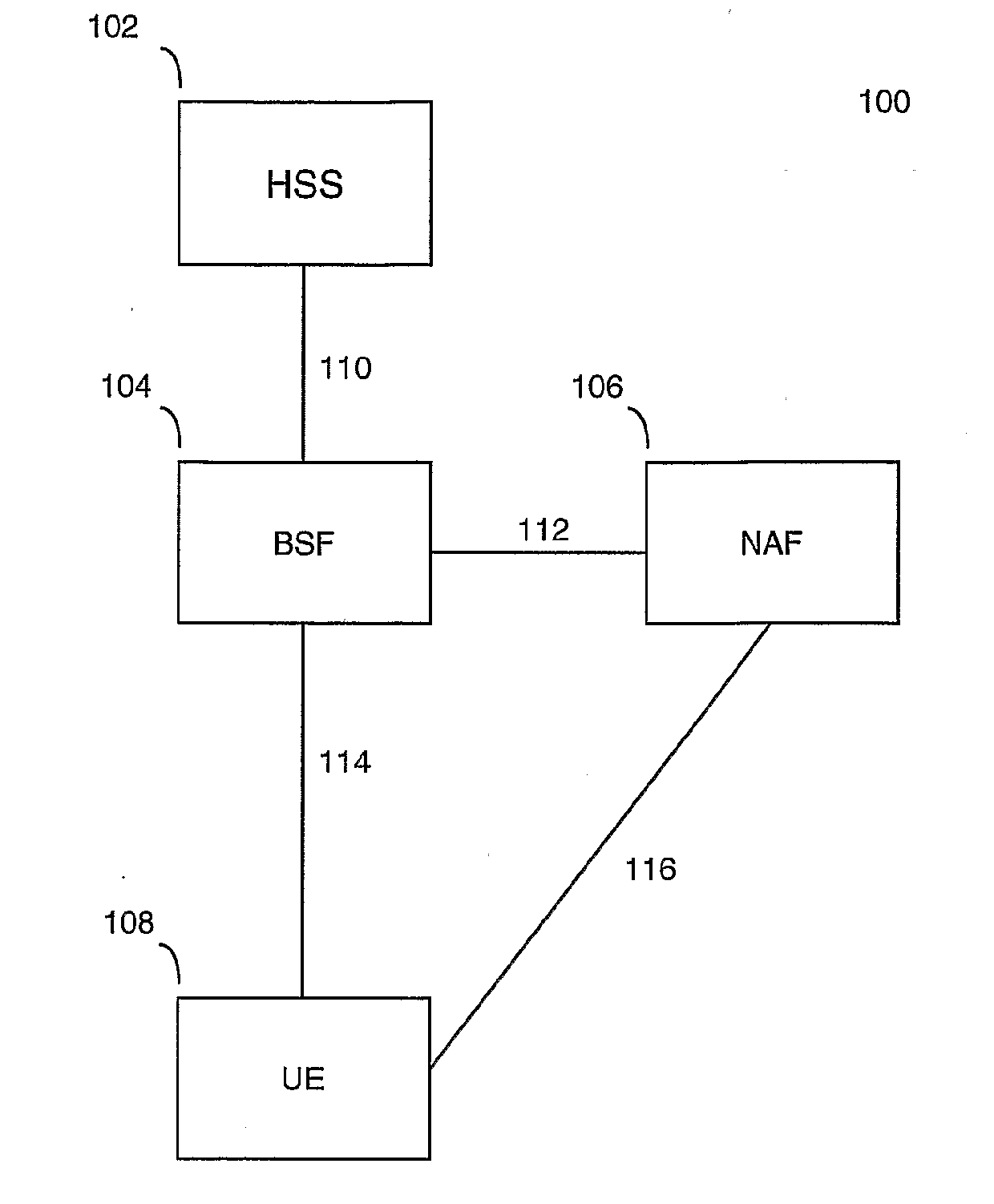
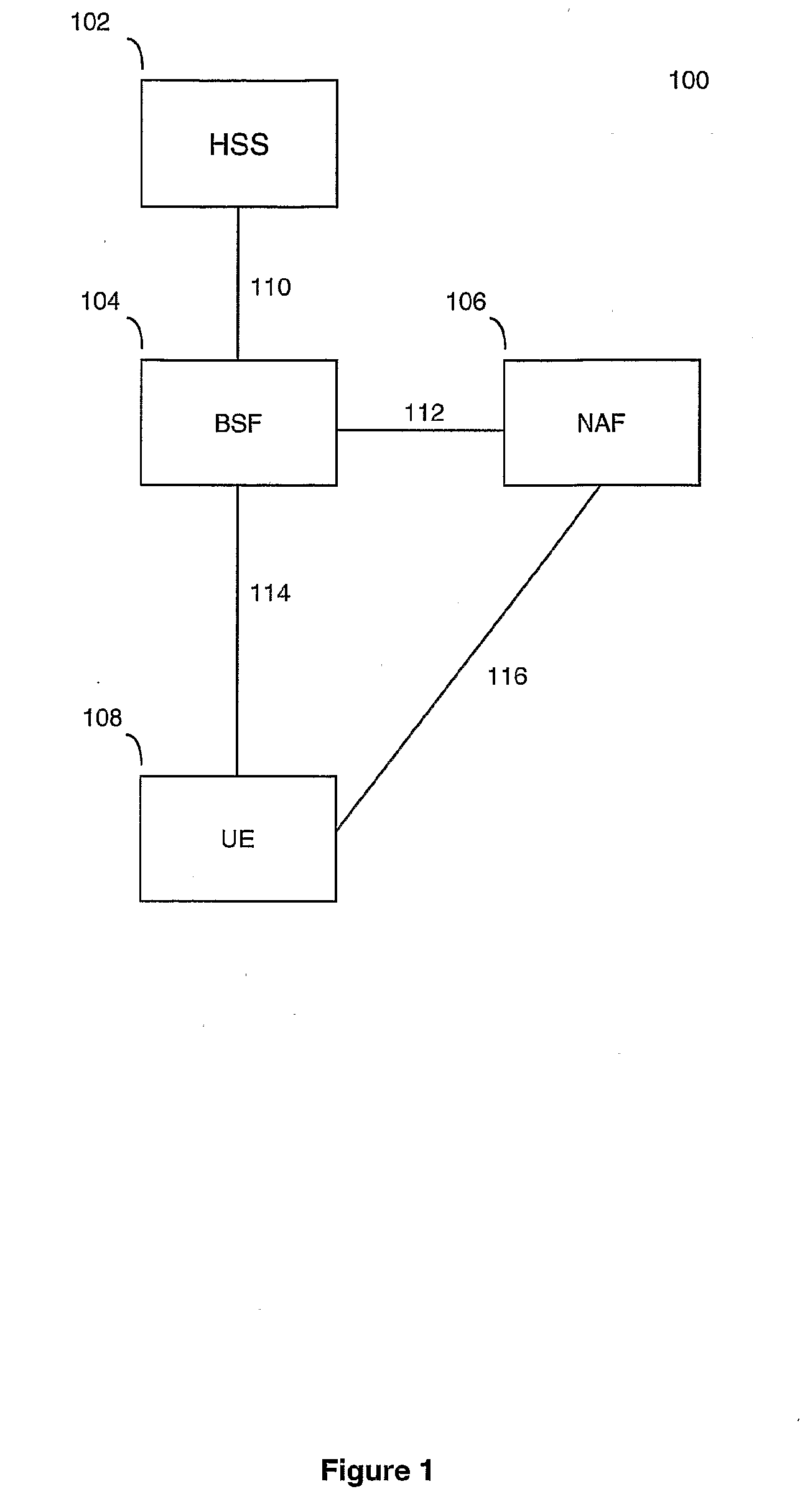
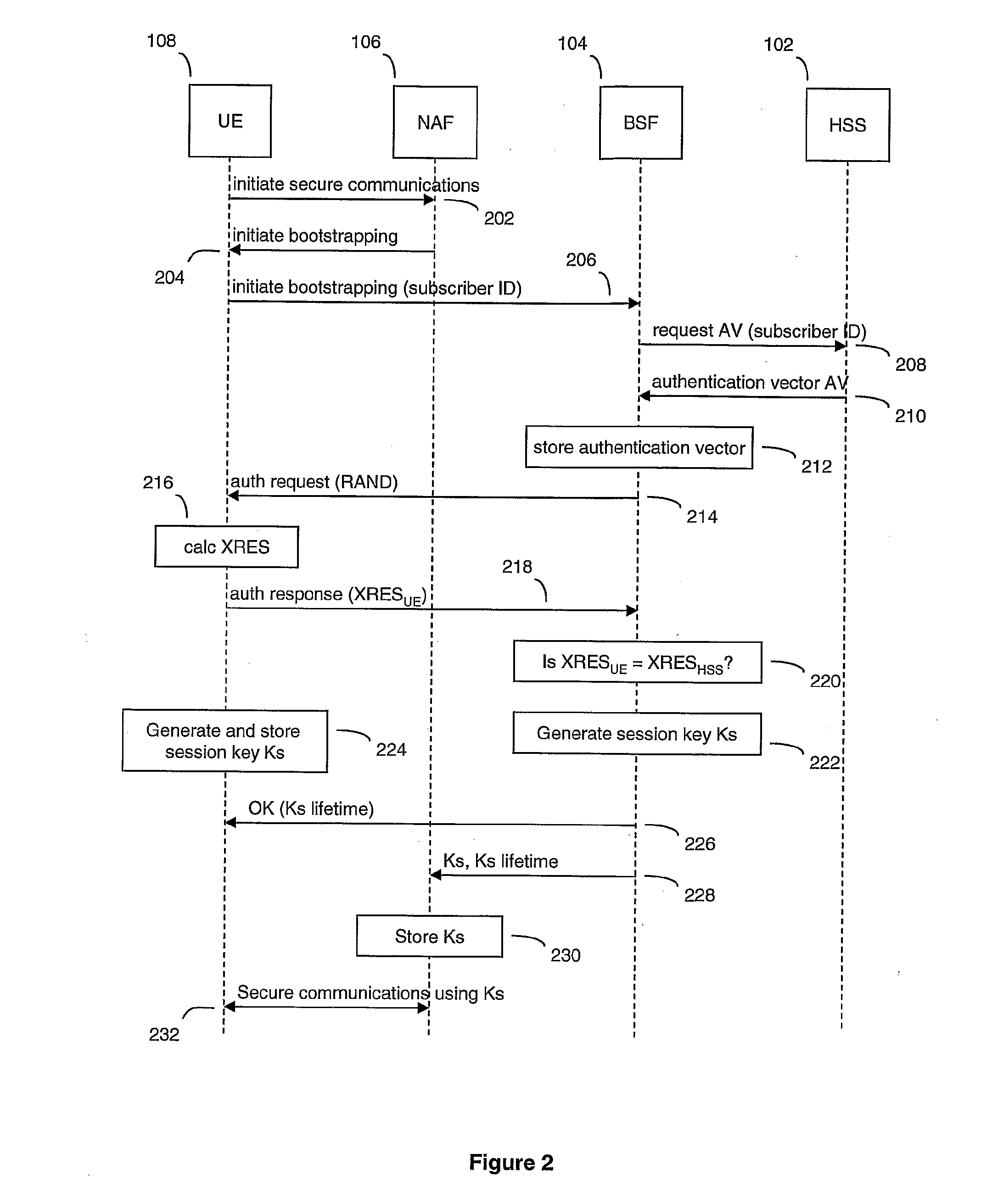
Recursive authentication
ActiveUS20110045799A1Avoid authenticationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsHome subscriber serverTraffic volume
Under a system referred to as GAA in the 3G protocol, authentication of devices in a network that is usually performed by a home subscriber server can be transferred to a third party element known as a bootstrapping server function. However, the use of a bootstrapping server function does not completely address the problem of reducing authentication traffic at the home subscriber sever. The present invention alleviates such a problem by utilising the original session key generated under GAA and using that key in a recursive process to authenticate and generate further session keys at other network elements. This generation of further keys can be performed independently of the home subscriber server, and thus reduces traffic at the home subscriber server.
Owner:BRITISH TELECOMM PLC
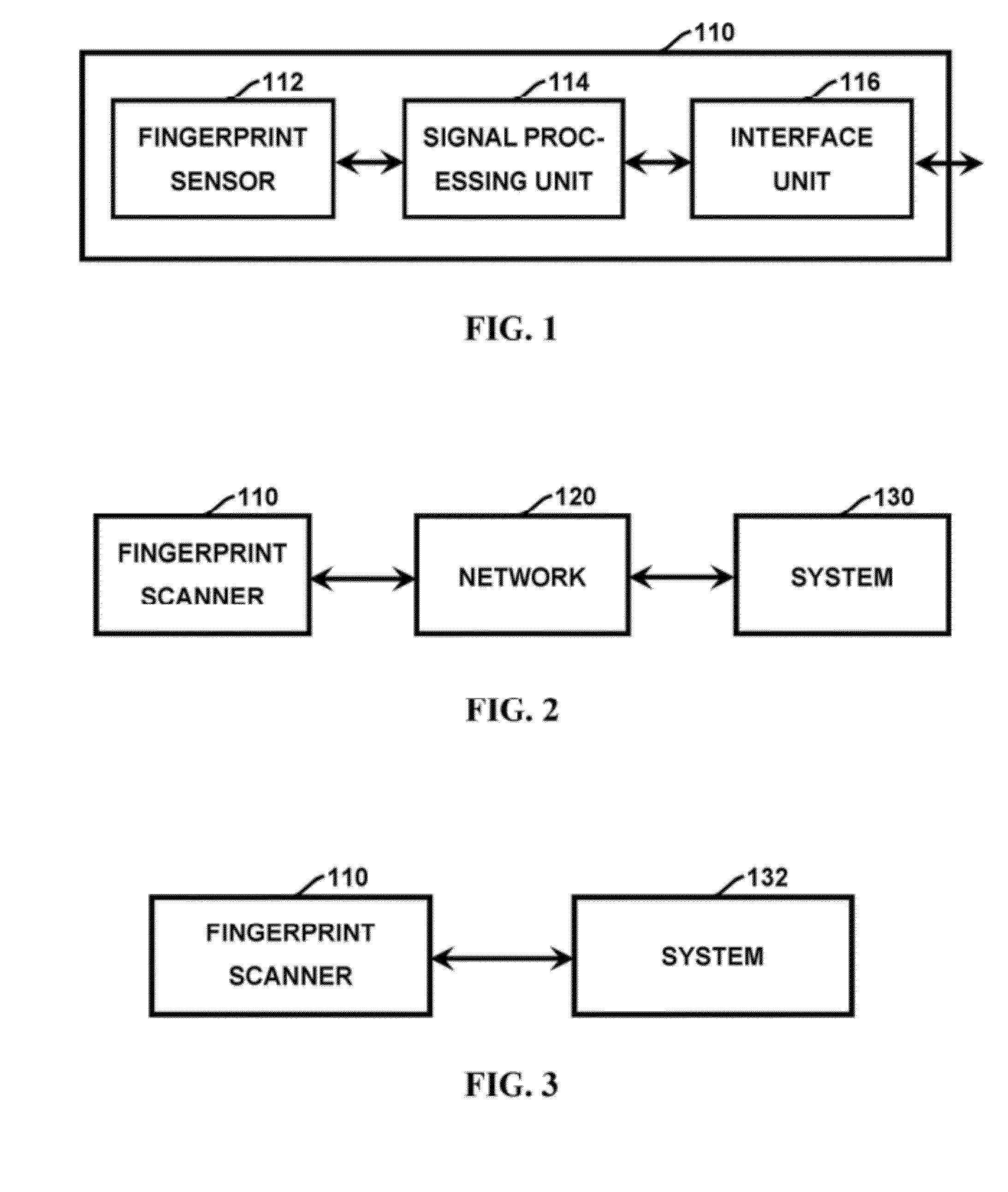
Method and apparatus for authenticating device and for sending/receiving encrypted information
ActiveUS20170295014A1Improve safetyGreat securityKey distribution for secure communicationAcquiring/reconising fingerprints/palmprintsFingerprintData information
Methods and apparatuses for authenticating communication devices and securely transmitting and / or receiving encrypted voice and data information. A biometric scanner, for example a fingerprint scanner, is utilized for authenticating the communication device and for generating the encryption key. The fingerprint scanner can be an area or swipe type of scanner is registered to a particular user and has unique intrinsic characteristics (the scanner pattern) that are permanent over time and can identify the scanner even among scanners of the same manufacturer and model. The unique scanner pattern of the scanner generates a unique encryption key that cannot be reproduced using another fingerprint scanner.
Owner:UNIV OF MARYLAND
Authentication apparatus, authenticated printing system, and authentication method
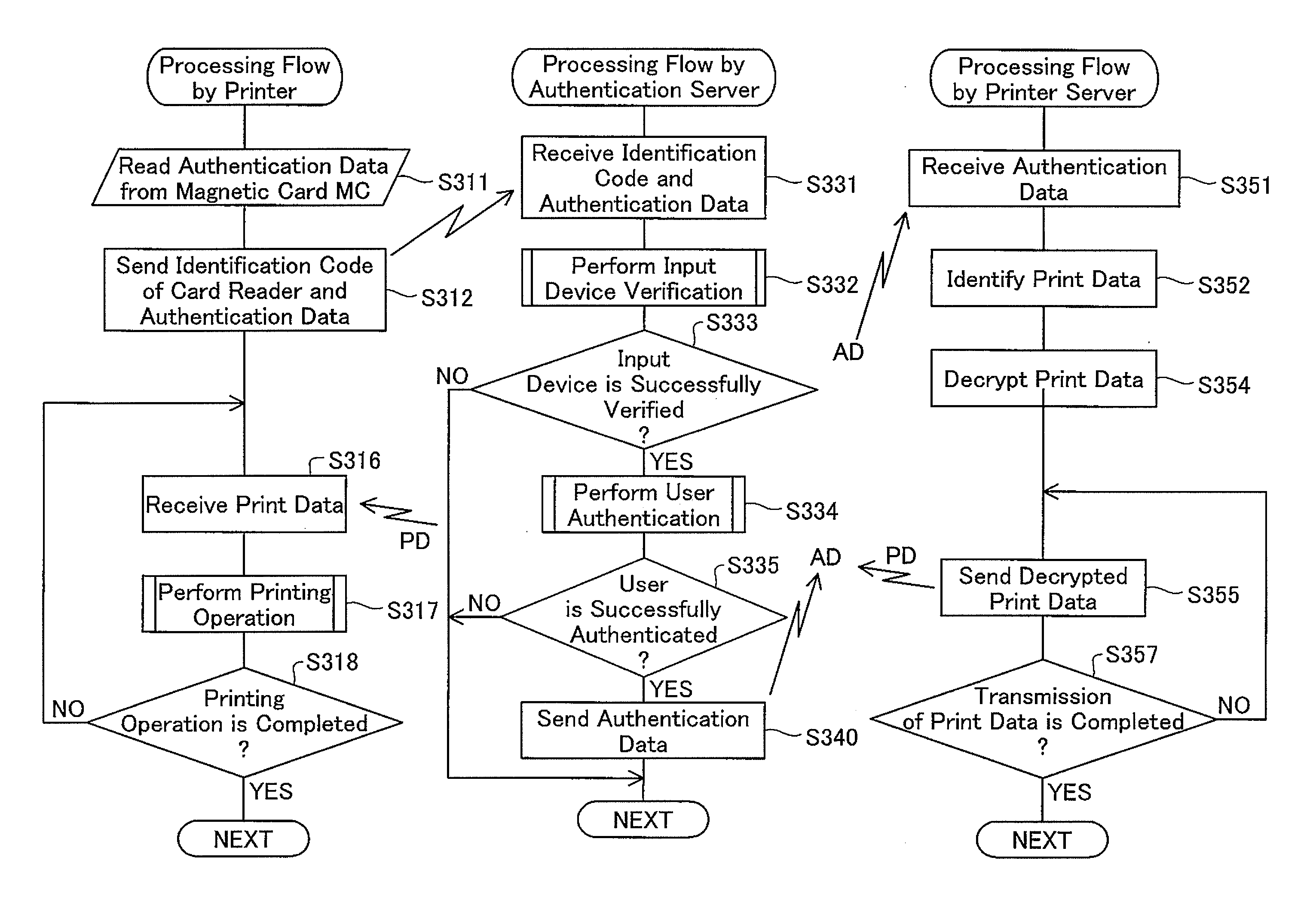
InactiveUS20090210927A1Avoid authenticationEasy to identifyDigital data processing detailsUser identity/authority verificationData inputAuthentication protocol
An authentication apparatus of the invention performs an authentication process based on authentication data input from a device used for data entry. The authentication apparatus receives device identification information for identifying the device and matches the received device identification information against authentication-authorized device identification information representing that the device is authorized to be used for authentication. In the case of failed matching of the received device identification information with the stored authentication-authorized device identification information, the authentication apparatus restricts the authentication process. This arrangement ensures the high security in an authenticated printing system including a printing apparatus connectable with at least one device used for entry of authentication data.
Owner:SEIKO EPSON CORP
Method and apparatus for authenticating swipe biometric scanners
ActiveUS20120300992A1Improve security levelEasily stolenImage enhancementPrint image acquisitionUser authenticationFingerprint
Methods and apparatuses for authenticating a biometric scanner, such as swipe type finger print scanners, involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeit biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND BALTIMORE
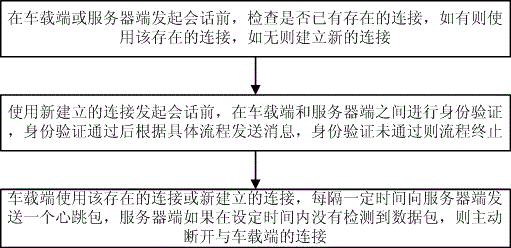
Vehicular remote communication method
InactiveCN106612313AAvoid wastingEnsure safetyNetwork topologiesWireless commuication servicesNetwork packetRemote communication
The invention provides a vehicular remote communication method comprising the following steps: before a session is initiated at a vehicle side or at a server side, whether there is an existing connection is checked, an existing connection is used if there is an existing connection, and a new connection is established if there is no existing connection; before a session is initiated through the newly established connection, authentication is carried out between the vehicle side and the server side, a message is sent according to a specific process after authentication, and the process is stopped if authentication fails; and the vehicle side sends a heartbeat packet to the server side at regular intervals through the existing connection or the newly established connection, and the server is actively disconnected from the vehicle side if the server detects no data packet in a set time. According to the embodiment of the invention, through a short connection method, frequent identity authentication is avoided, traffic is saved, and the connection efficiency is improved. Authentication is needed for a newly established connection, and the safety of communication is ensured. Moreover, waste of server resources caused by long-time occupation of server resources is avoided.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
Printing system, printout apparatus, and recording medium
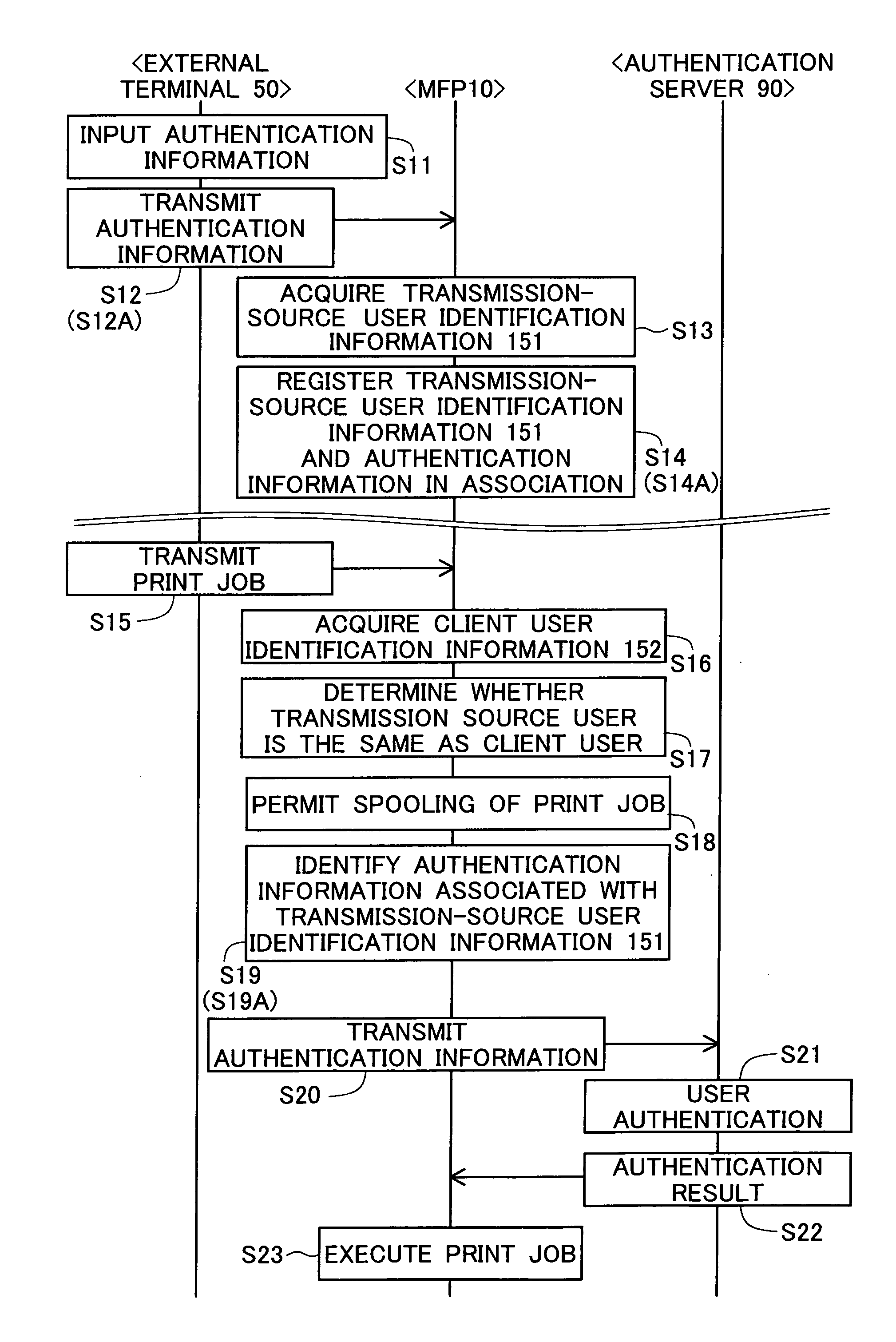
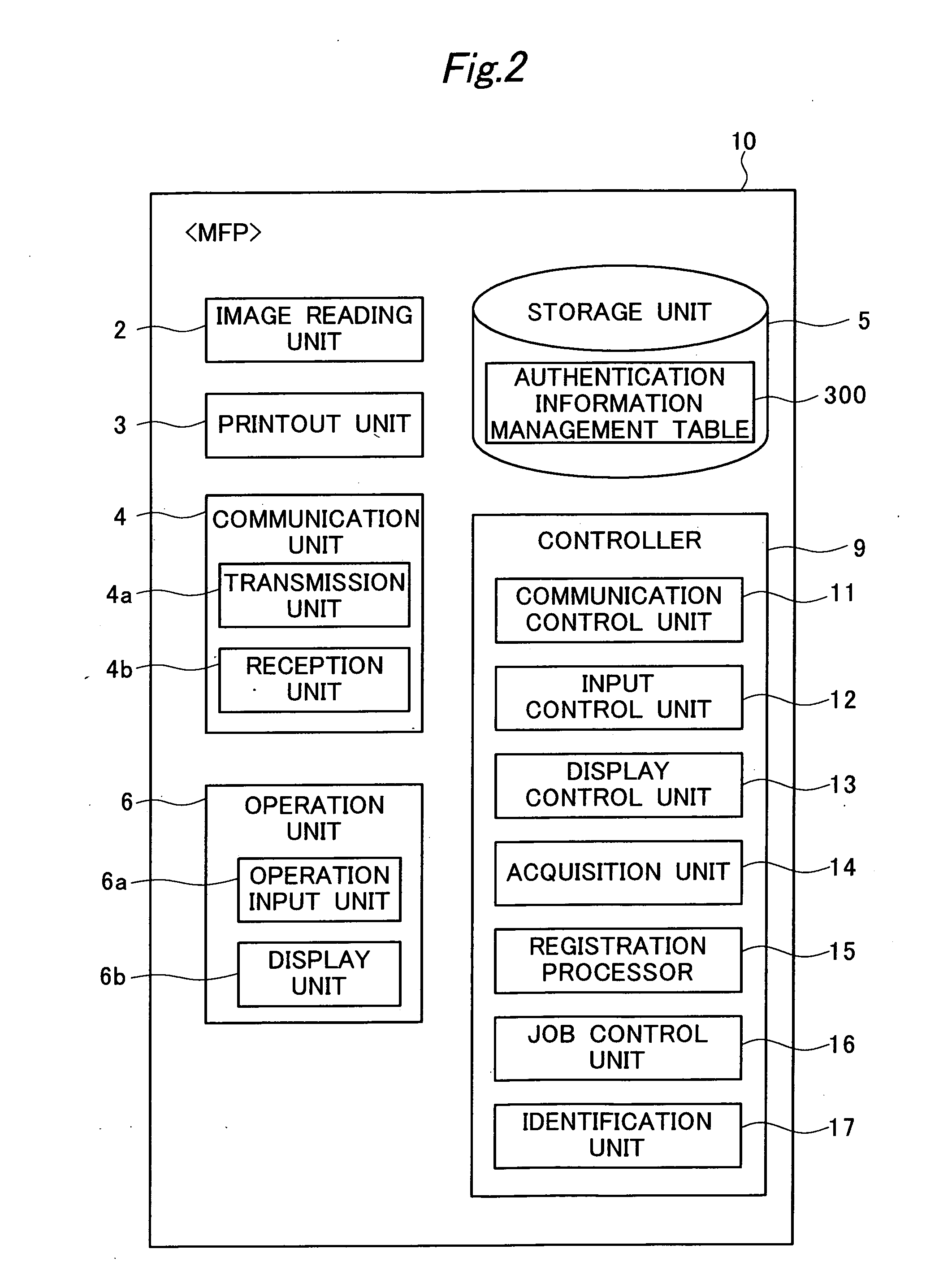
ActiveUS20160212297A1Avoid authenticationComputer security arrangementsVisual presentationOutput deviceComputer terminal
An external terminal transmits a print job to a printout apparatus and also transmits authentication information required for user authentication in printing that involves authentication to the printout apparatus at one time or a plurality of times and at a different time from the transmission of the print job. The printout apparatus identifies the authentication information received from the external terminal as information to be used for the user authentication when a transmission source user of the authentication information and a client user of the print job are determined to be the same on the basis of transmission-source user identification information for identifying the transmission source user and client user identification information for identifying the client user.
Owner:KONICA MINOLTA INC
Authentication method based on biological characteristic information
InactiveUS7685432B2Reduce the burden onAvoid authenticationDigital data authenticationSecret communicationError preventionBiometrics
The present invention provides authentication equipment having functions for prevention of erroneous authentication using biometrics data, and which can reduce the burden of registration placed on users. The authentication equipment is characterized in comprising an input portion, which generates primitive-format information of biological characteristics based on biological characteristics specific to individuals; a primary information extraction portion, which extracts primary information identifying the biological characteristics from the primitive-format information; a secondary information extraction portion, which extracts, as secondary information, a part of the primitive-format information using the primary information; a registration portion, which stores in a storage portion the secondary information extracted by the secondary information extraction portion; and a verification portion, which compares the secondary information extracted by the secondary information extraction portion with secondary information stored in the storage portion, and judges whether authentication has been successful.
Owner:FUJITSU LTD
User authentication system and method for controlling the same
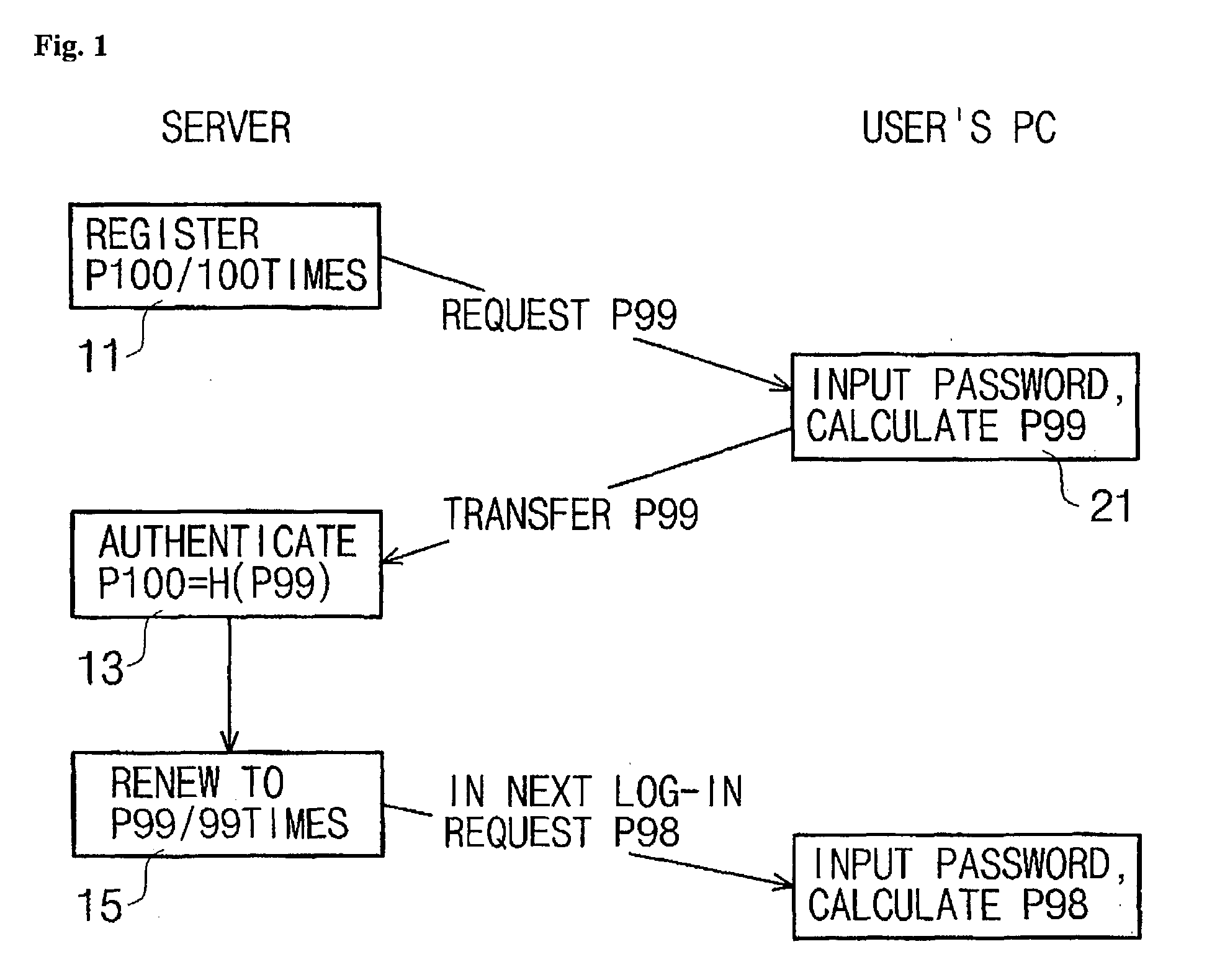
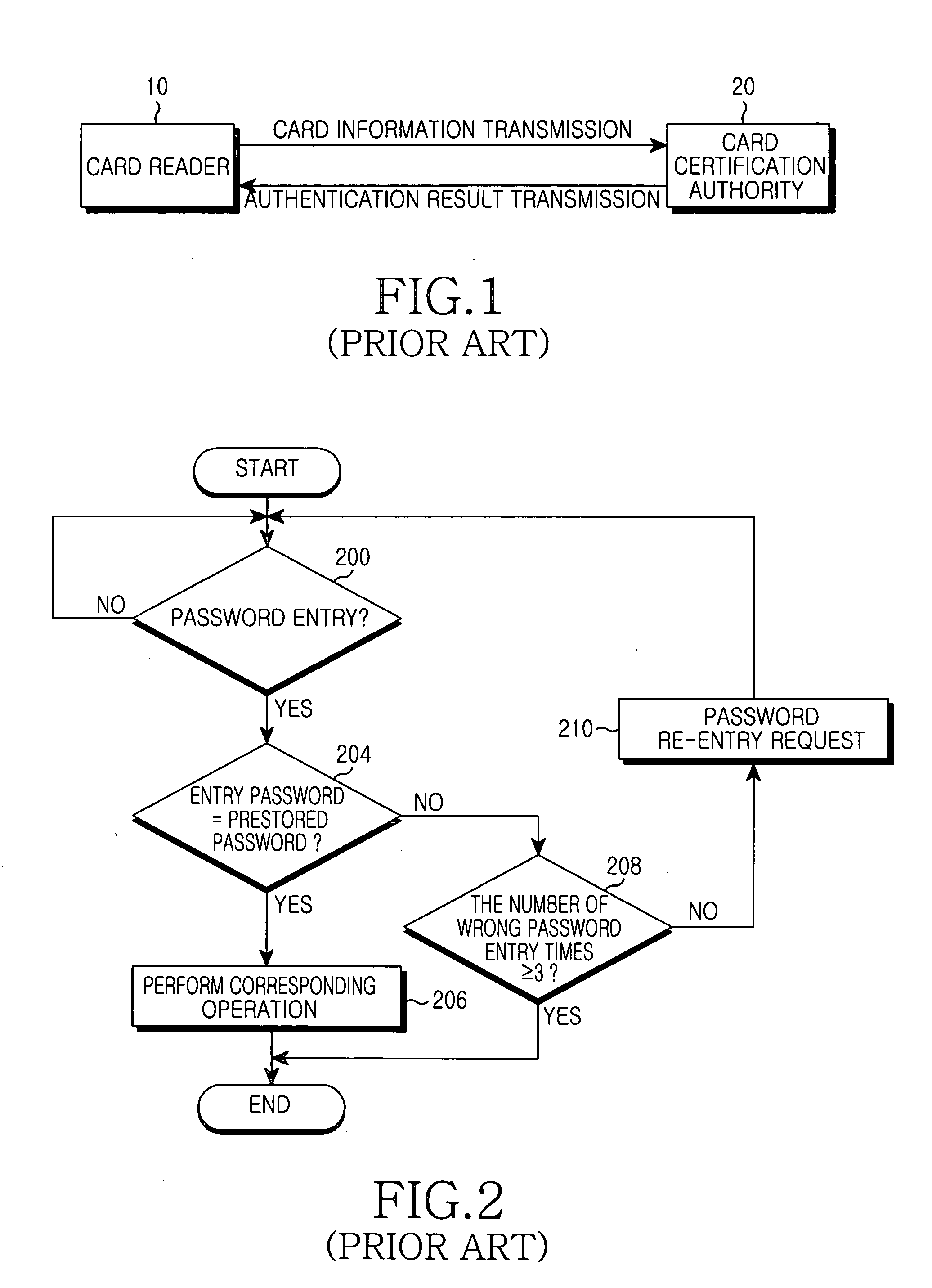
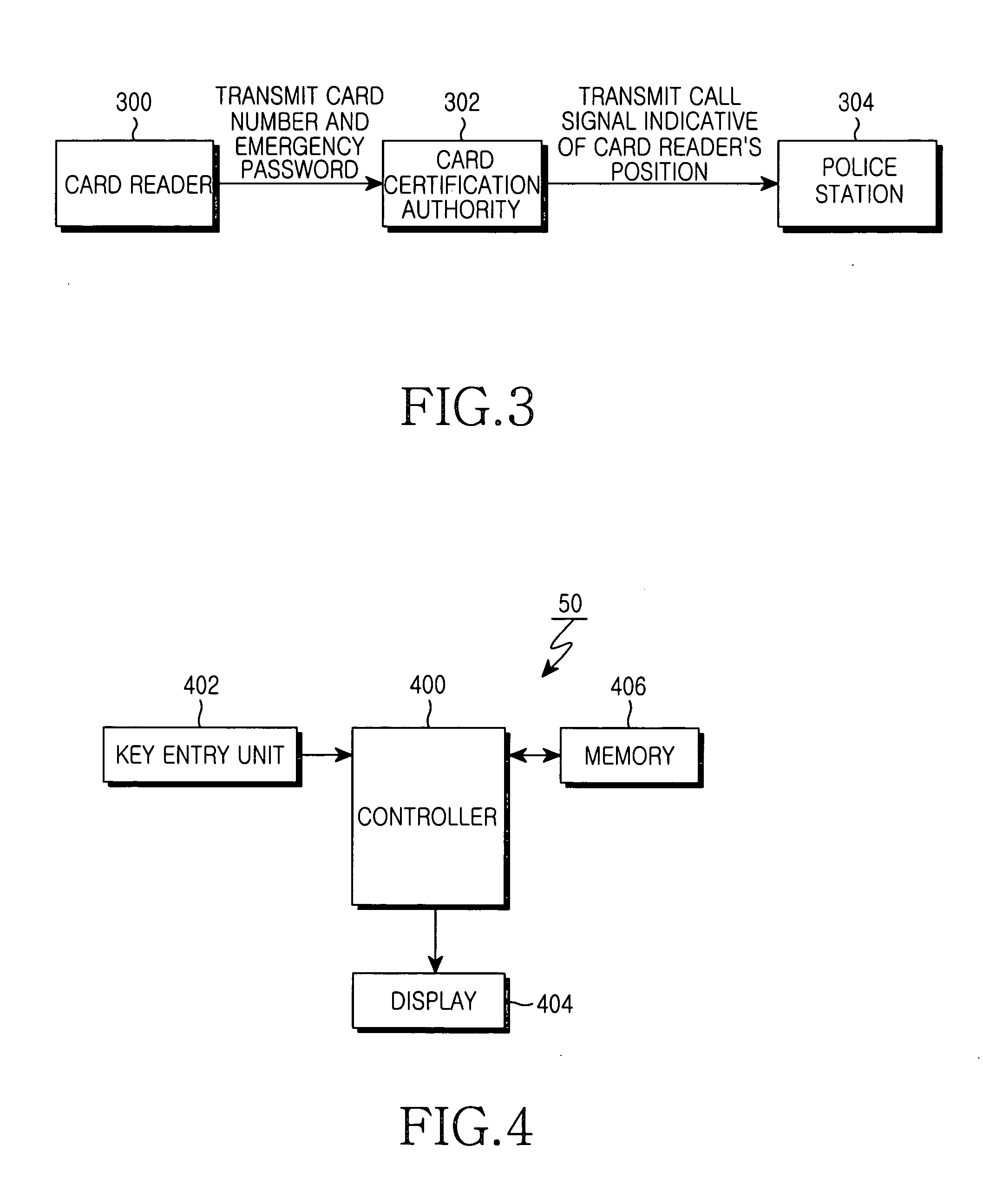
ActiveUS20050097261A1Avoid authenticationDigital data processing detailsUser identity/authority verificationPasswordOperation mode
A user authentication system and method using a password. A method for performing an operation mode associated with a password in the system having a password setup function, includes the steps of setting up a general password for normal user authentication and an emergency password needed for an emergency operation mode, and storing them in a memory; and upon receiving a password from a user, performing the normal user authentication when the user-entry password matches the general password, and performing the emergency operation mode when the user-entry password matches the emergency password.
Owner:SAMSUNG ELECTRONICS CO LTD
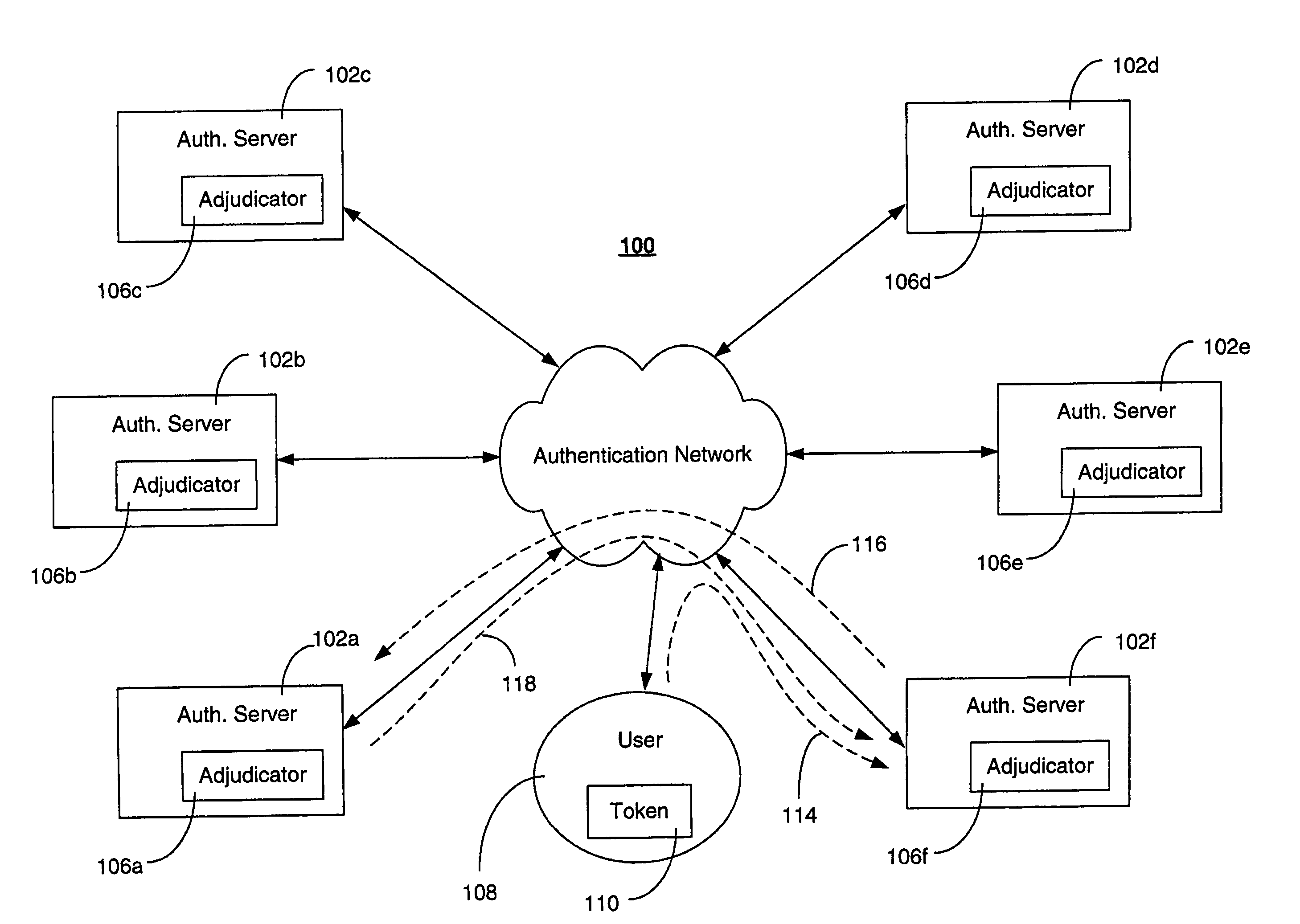
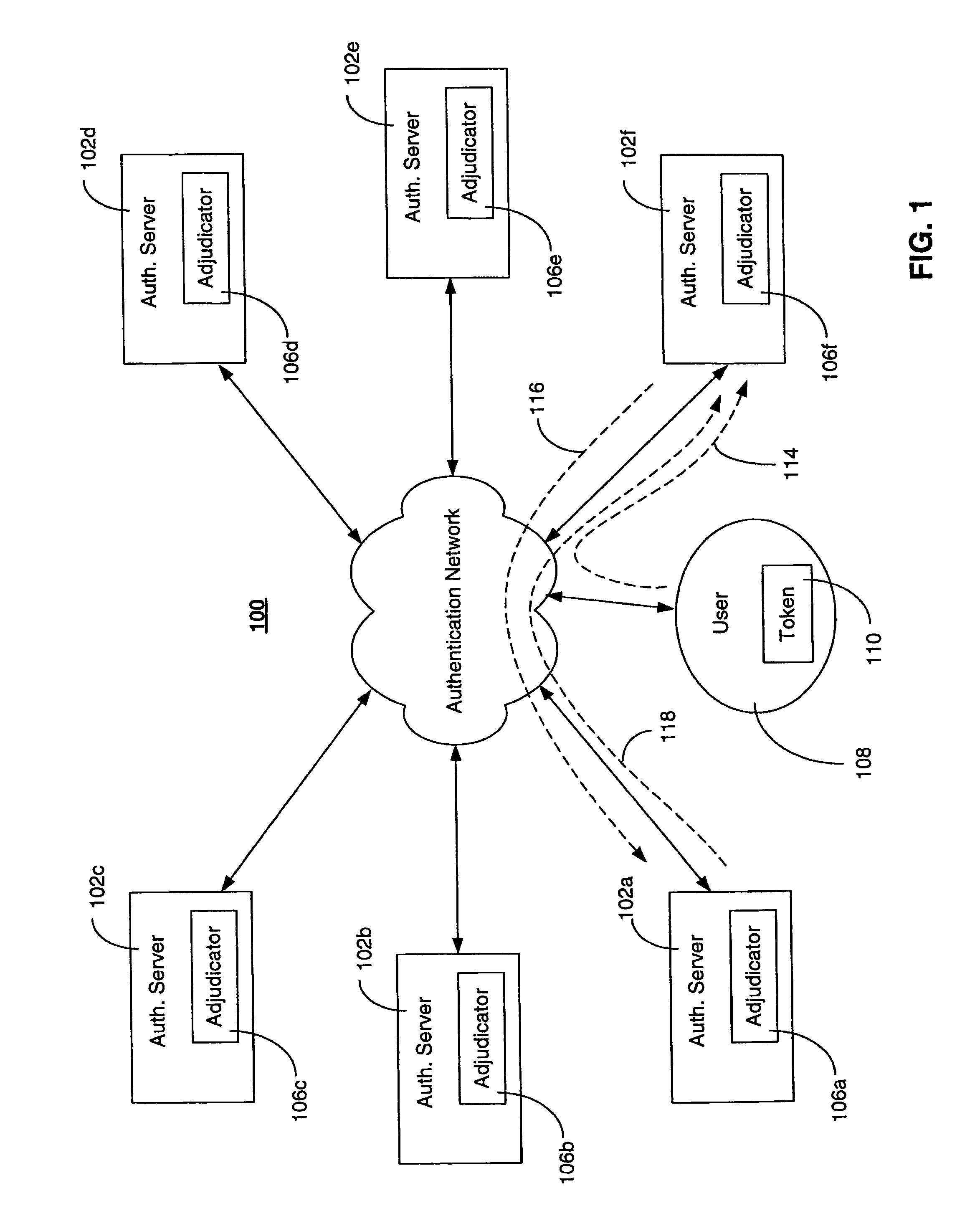
Detecting and preventing replay in authentication systems
ActiveUS7810147B2Avoid authenticationDigital data processing detailsUser identity/authority verificationAuthentication serverOne-time password
A system for detecting and preventing replay attacks includes a plurality of interconnected authentication servers, and one or more tokens for generating a one-time passcode and providing the one-time passcode to one of the authentication servers for authentication. The system includes an adjudicator function associated with each authentication server. The adjudicator evaluates a high water mark value associated with a token seeking authentication, allows authentication to proceed for the token if the high water mark evaluation indicates that the one-time passcode was not used in a previous authentication, and prevents authentication if the high water mark evaluation indicates that the one-time passcode was used in a previous authentication. The token is associated with a home authentication server that maintains a current high water mark of the token. The home authentication server validates the current high water mark on behalf of the adjudicator function evaluating the token for authentication.
Owner:RSA
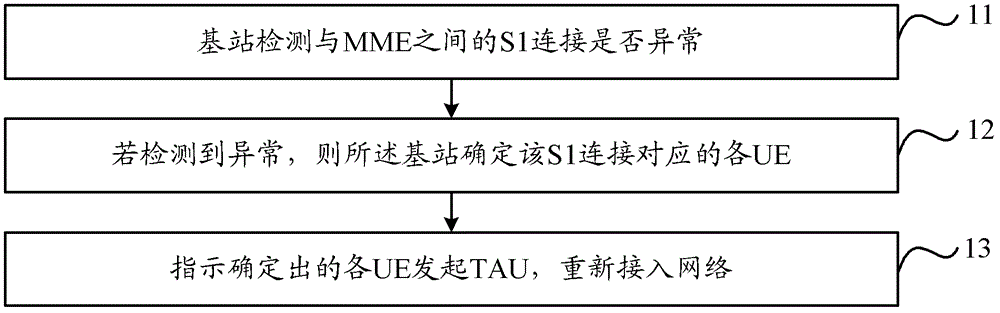
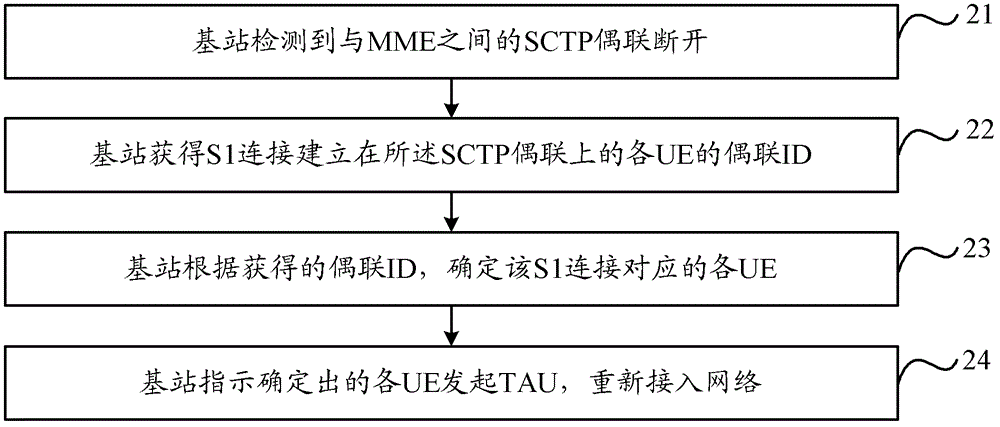
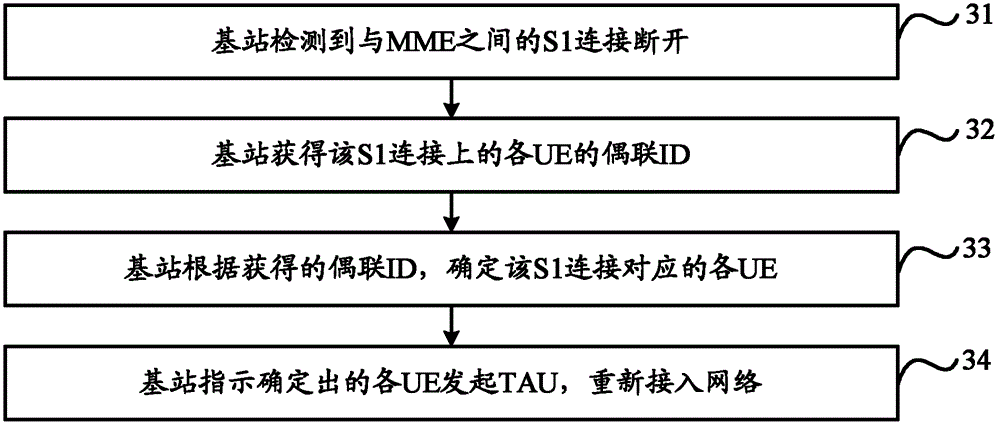
Network access method, base station and user equipment
InactiveCN102802273AAvoid authenticationShorten the timeConnection managementAccess methodMobility management
The invention discloses a network access method, a base station and user equipment. The method comprises the following steps that: the base station detects whether an S1 connection which is between the base station and a mobility management entity (MME) is abnormal; if the S1 connection is abnormal, the base station determines each piece of user equipment (UE) corresponding to the S1 connection; and the base station instructs the determined UE to initiate tracking area update (TAU) for reaccess to a network. By the technical scheme, the problems that long time is required by the reaccess of the UE to the network in the prior art and much signaling interaction is required to be performed between the UE and a network side are solved.
Owner:ZTE CORP
Method and apparatus for authenticating area biometric scanners
ActiveUS8942430B2Improve securityAvoid attackImage enhancementPrint image acquisitionImaging processingUser authentication
Owner:UNIV OF MARYLAND BALTIMORE
Method and system for safely receiving and sending mails
ActiveCN103428077AEnsure safetyImplement encryptionUser identity/authority verificationData switching networksSecure transmissionClient-side
The invention discloses a method and a system for safely receiving and sending mails. Mail receiving and sending safety authentication and safety transmission of the mails are realized. The method includes the steps: connecting a mail client with a login platform to perform identity authentication; returning a token message to the mail client after authentication success; accessing a first address in the token message by the mail client; receiving a first message including a second address by the mail client; calling an interface of a safety management platform and transmitting the first message to the safety management platform by the mail client; generating a second message and transmitting the second message to the mail client and a mail gateway by the safety management platform; acquiring a user policy message from the safety management platform through the second message by the mail client; carrying the second message by the mail client and authenticating the second message at the mail gateway; connecting the mail gateway with a mail server and starting receiving and sending the mails after passing authentication.
Owner:北京明朝万达科技股份有限公司
Array password authentication system and method thereof
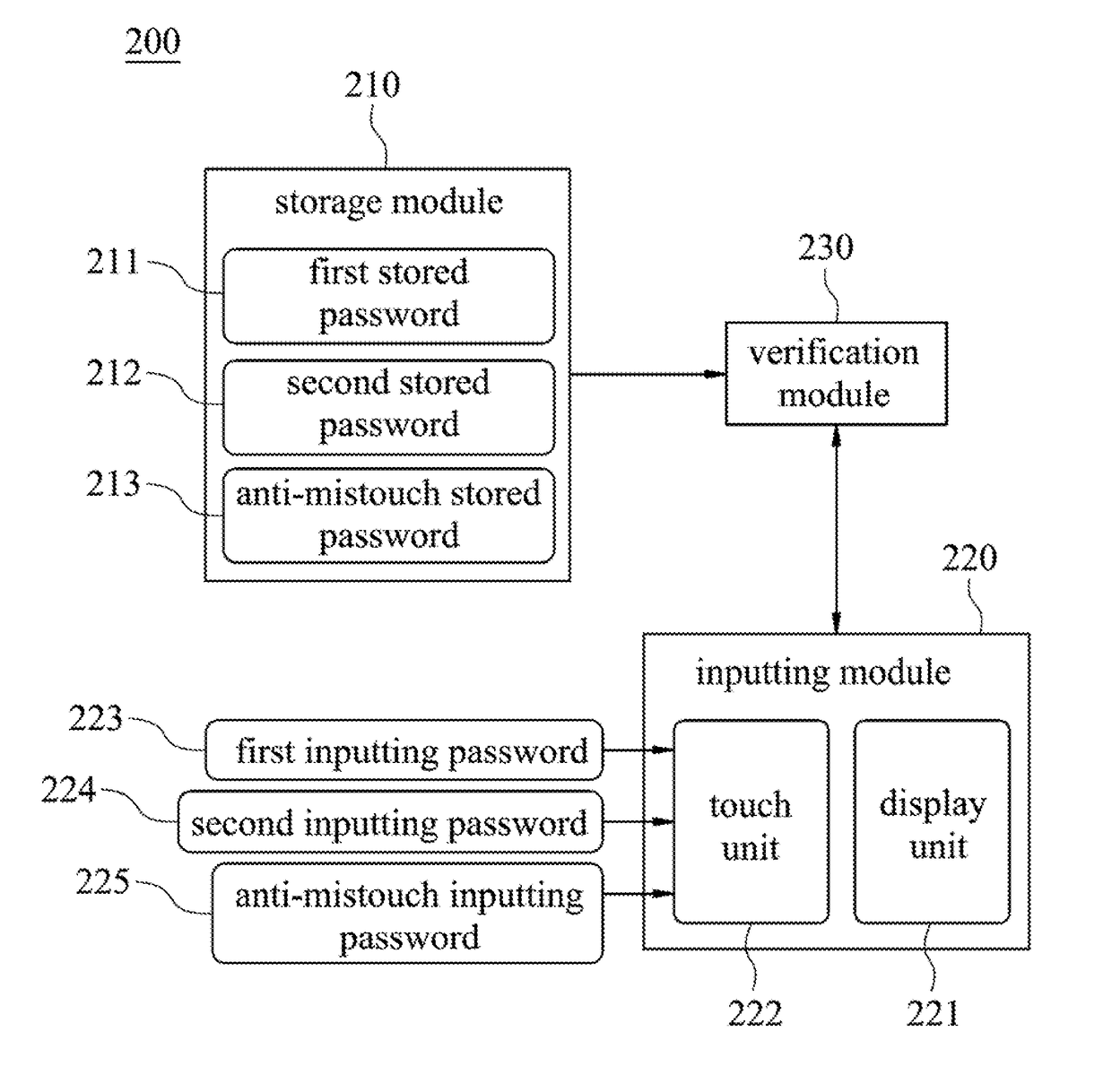
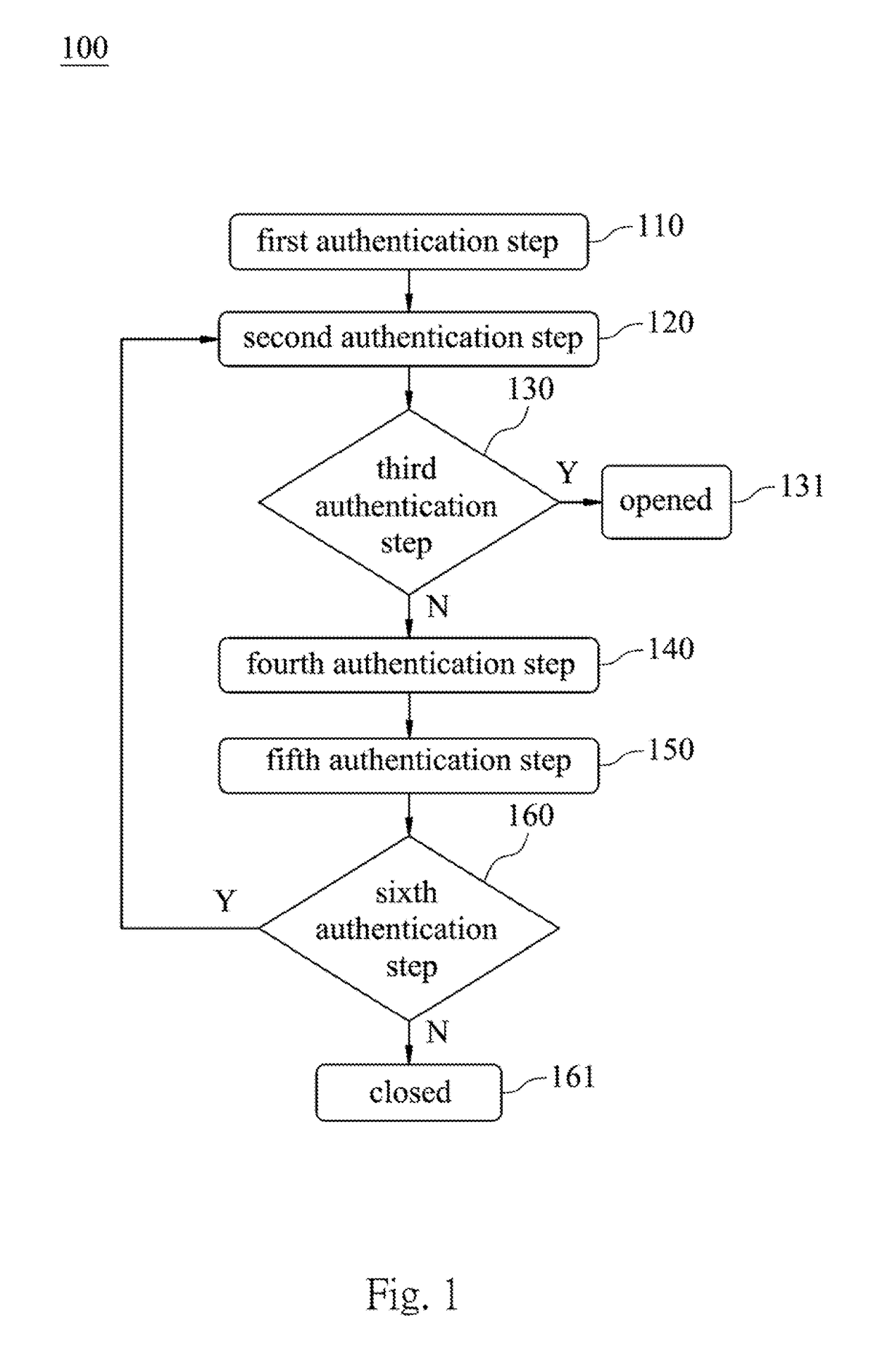
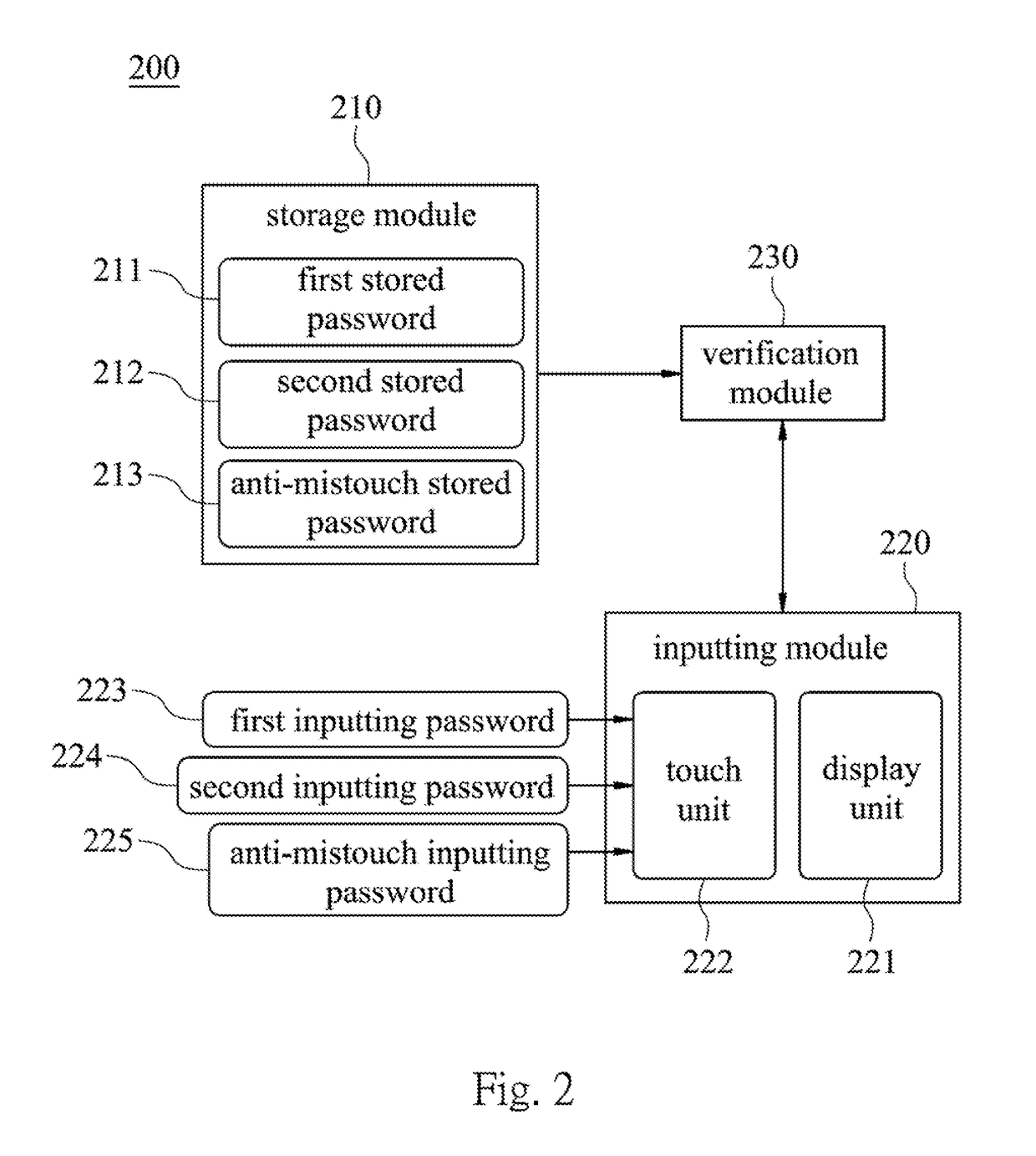
InactiveUS20170154173A1Improve safetyReduce riskDigital data authenticationAuthentication systemComputer hardware
An array password authentication method includes six authentication steps. The first authentication step is for inputting stored passwords into a system. The second authentication step is for displaying a plurality of first random codes arranged to form a first square matrix. One of the first random codes, is selected as a first inputting password. The third authentication step is for comparing the first stored password with the first inputting password. The fourth authentication step is for executing an anti-mistouch verification. The fifth authentication step is for displaying a plurality of second random codes arranged to form a second square matrix. One of the second random codes is selected as a second inputting password. The sixth authentication step is for comparing the second stored password with the second inputting password. If the second stored password and the second inputting password are different, the system is locked.
Owner:WANG CHAO HUNG
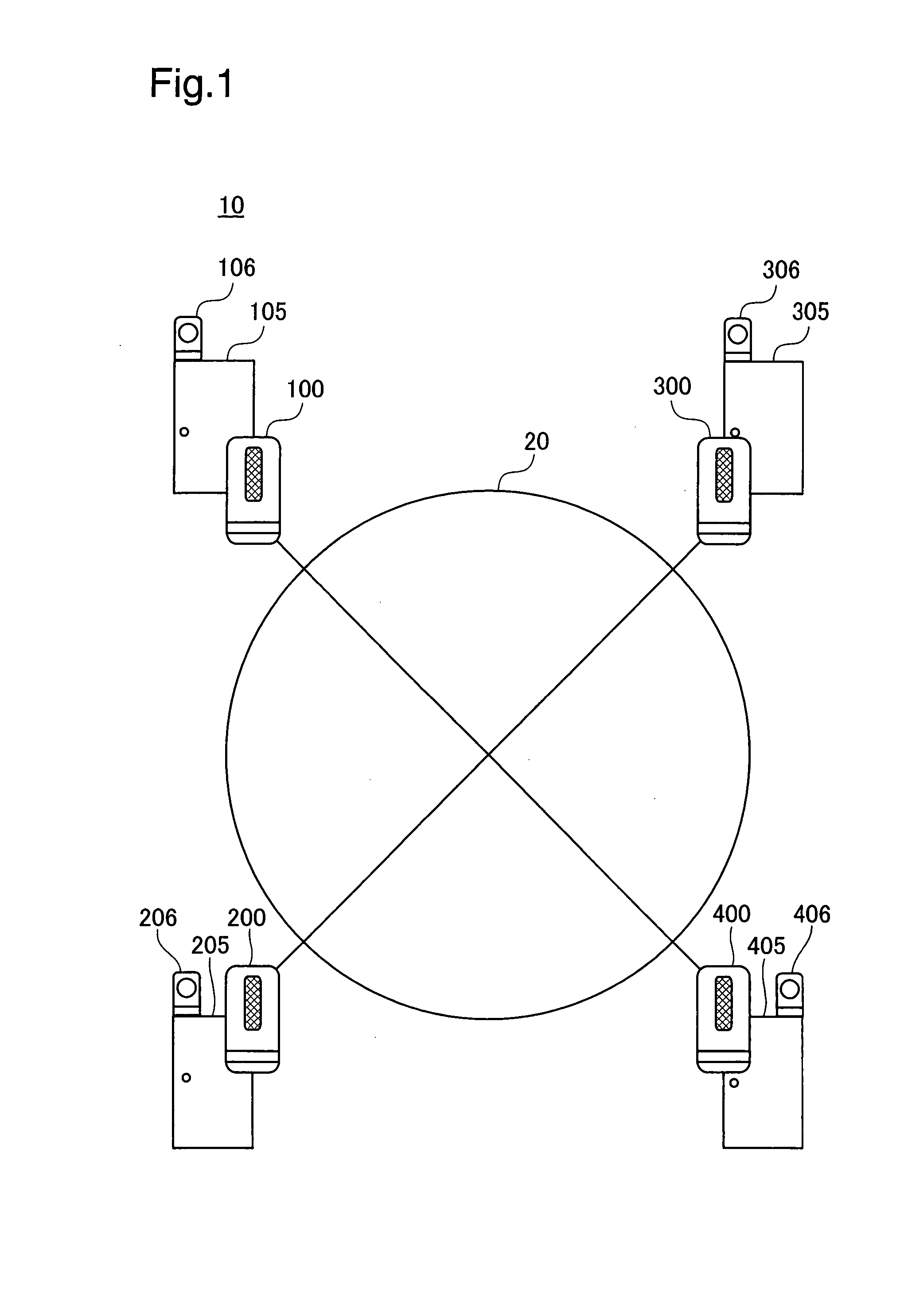
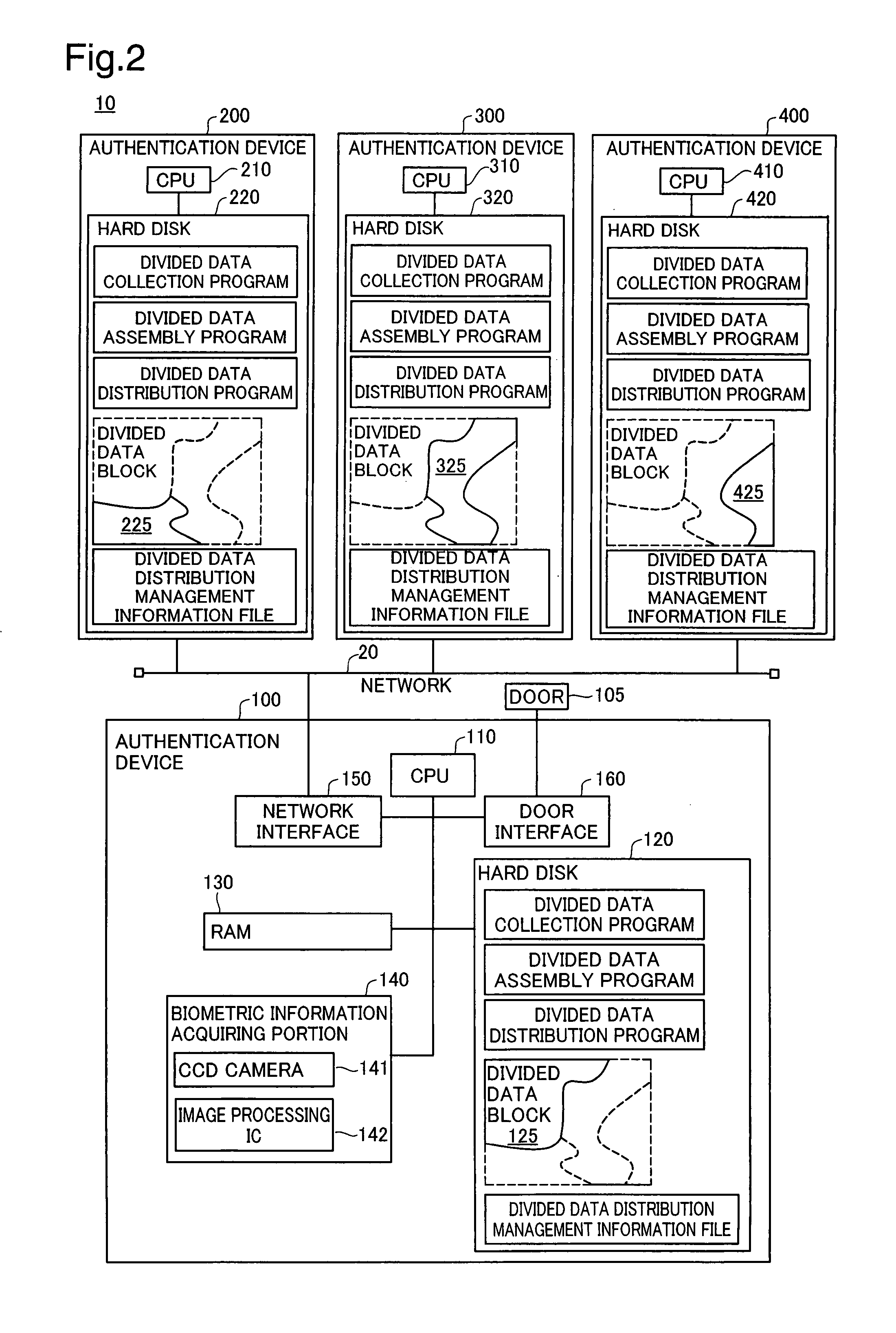
Authentication device, authentication system, and verification method for authentication device
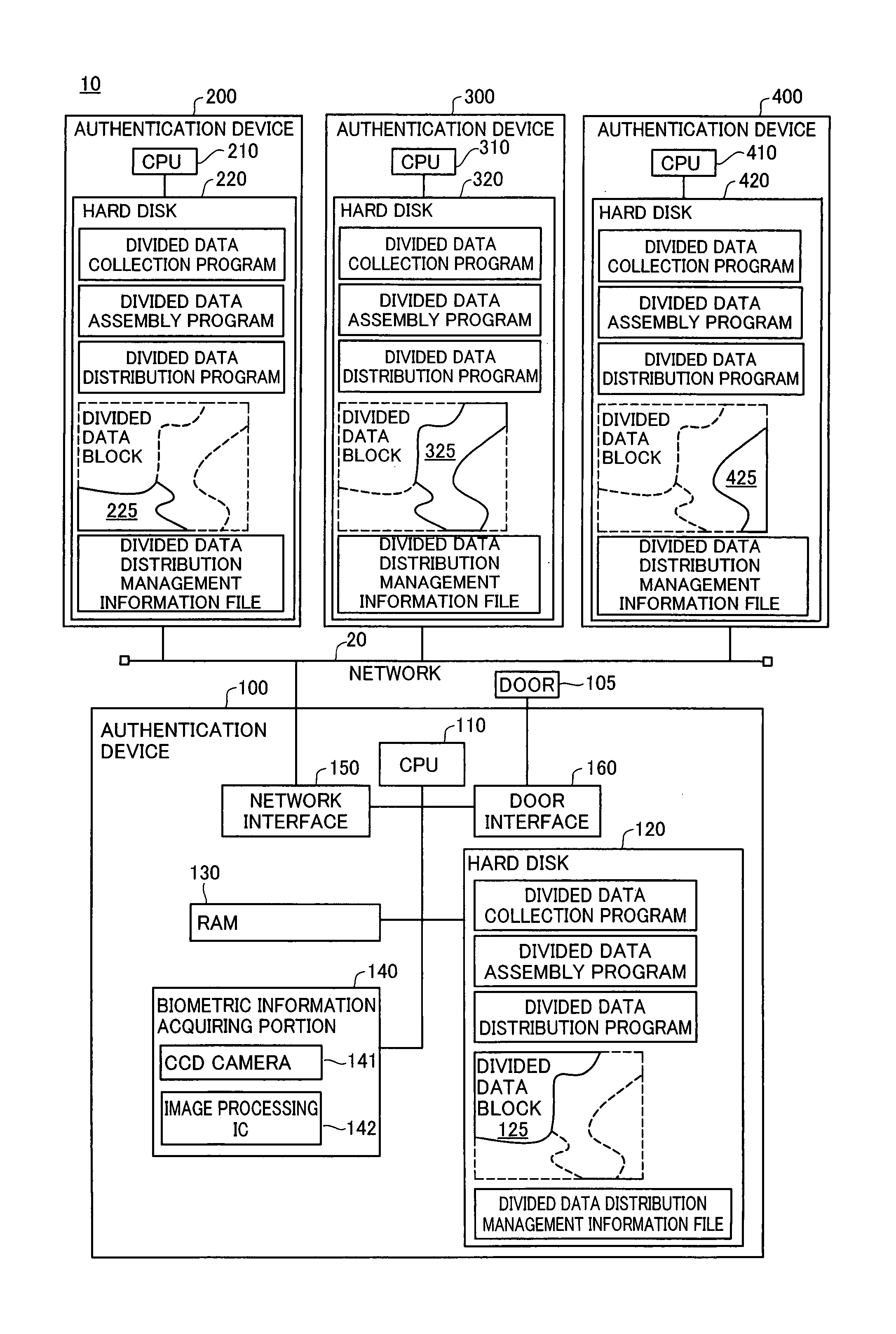
InactiveUS7941832B2Avoid analysisAvoid authenticationSpecial service provision for substationDigital data processing detailsValidation methodsAuthentication system
At startup, divided data blocks are received from other authentication devices and are assembled together with the local divided data block to reconstitute first authentication data. After a prescribed time interval, divided data blocks are again received from other authentication devices and are assembled together with the local divided data block to reconstitute second authentication data. The first authentication data and the second authentication data are cross-checked, and the legitimacy of the other authentication devices is decided; in the event that the other authentication devices are legitimate devices, one authentication device among the multiplicity of authentication devices re-divides the second authentication data into a multiplicity of divided data blocks for re-distribution, and a process of reconstituting the authentication data from the divided data, cross-checking the reconstituted data with the first authentication data, and deciding whether the other authentication devices are legitimate devices is repeated at prescribed intervals.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
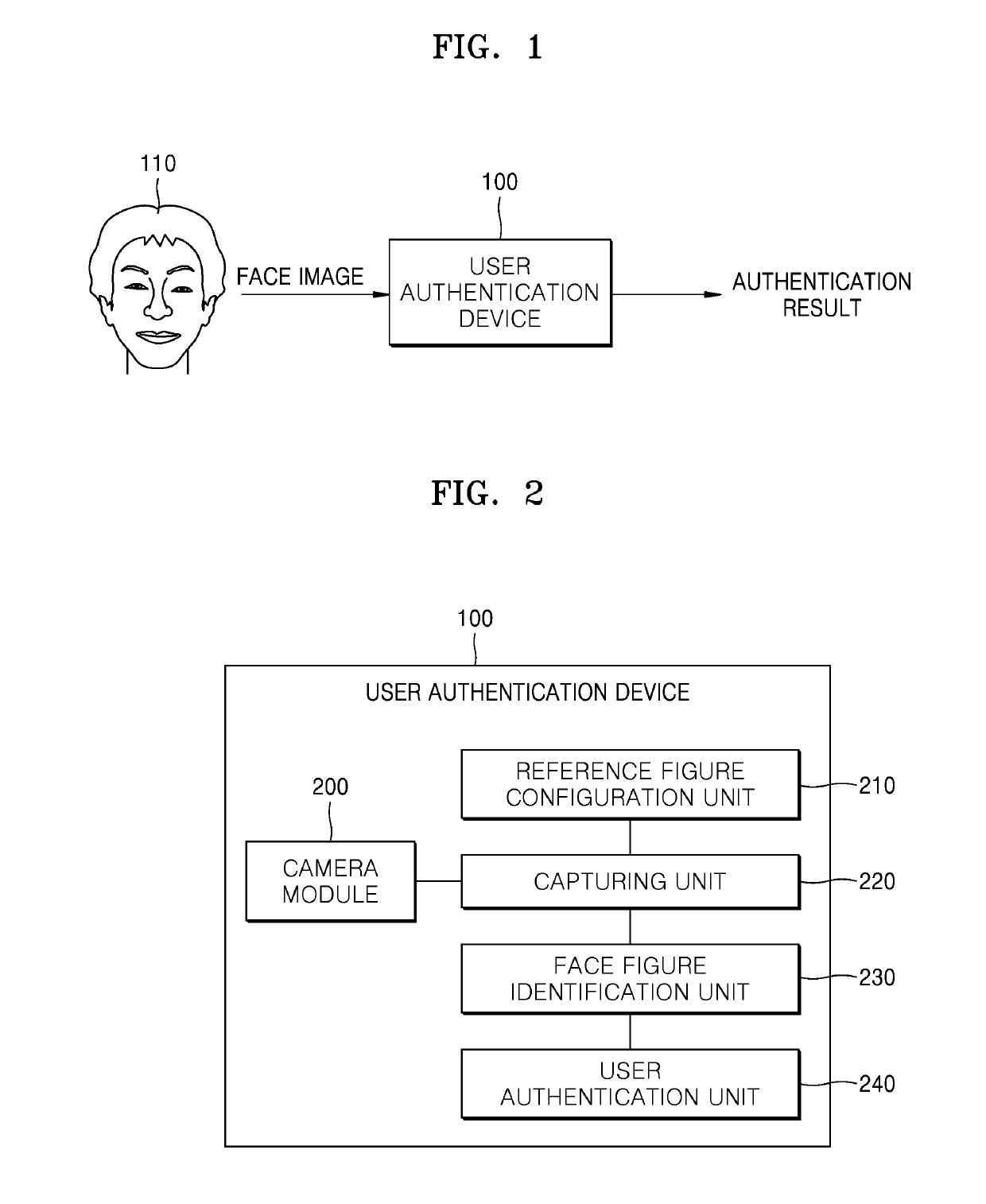
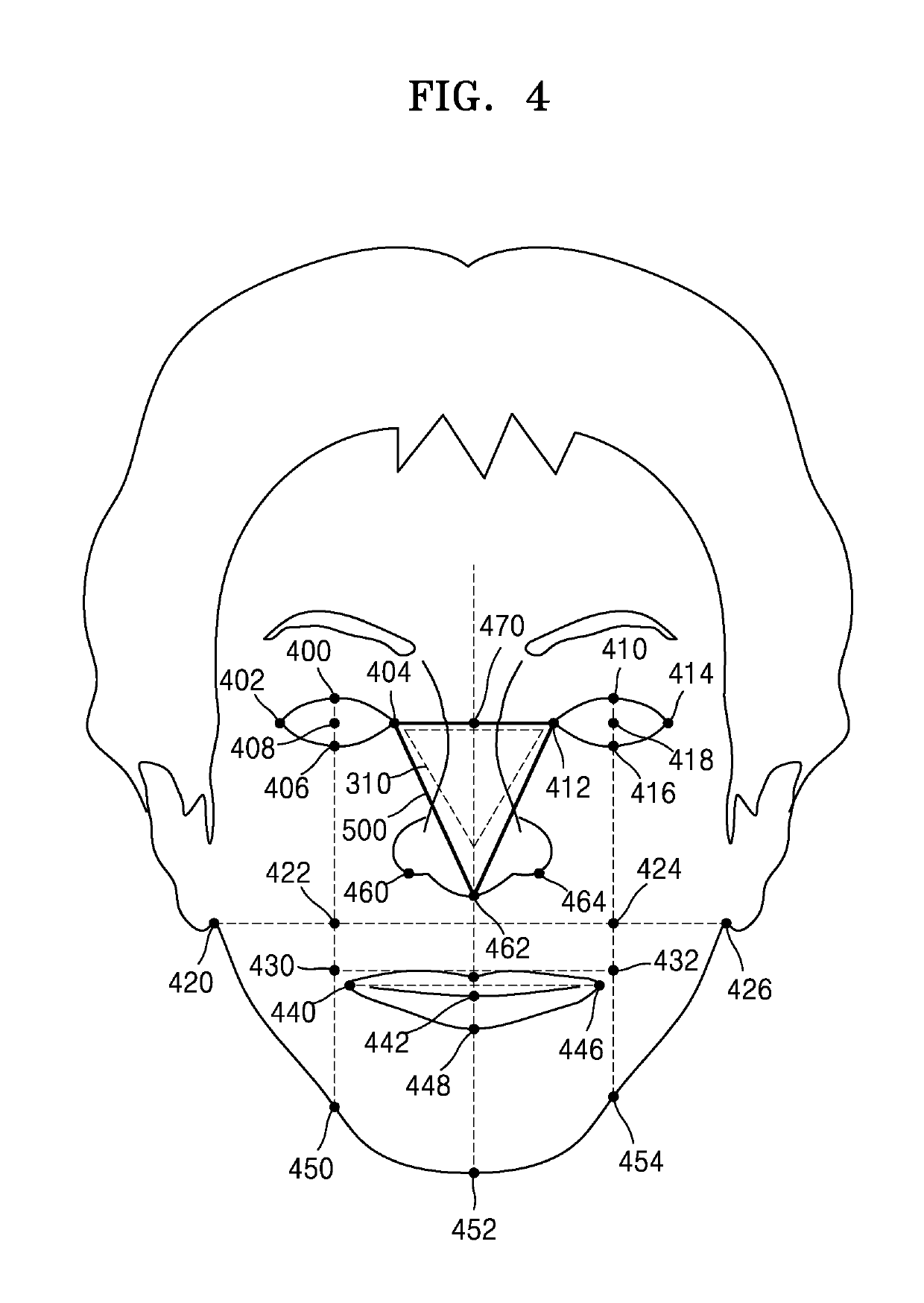
User authentication method using face recognition and device therefor
InactiveUS20190286798A1Easy authenticationSimplify the authentication processCharacter and pattern recognitionDigital data authenticationPattern recognitionGraphics
Provided is a user authentication method using face recognition and a device therefor. The user authentication method in a user authentication device includes capturing a face image of a user by using a camera module, identifying a plurality of figures based on positions of an eye, a nose, a mouth or an ear of the face image, and approving user identity based on the plurality of figures.
Owner:KIM YONG SANG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com