Method and system for safely receiving and sending mails
An e-mail system and e-mail technology, applied in the field of safe e-mail sending and receiving methods and systems, can solve the problems that the SMTP server cannot verify MAILFROM, lack of strict identity authentication mechanism, etc., and achieve the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
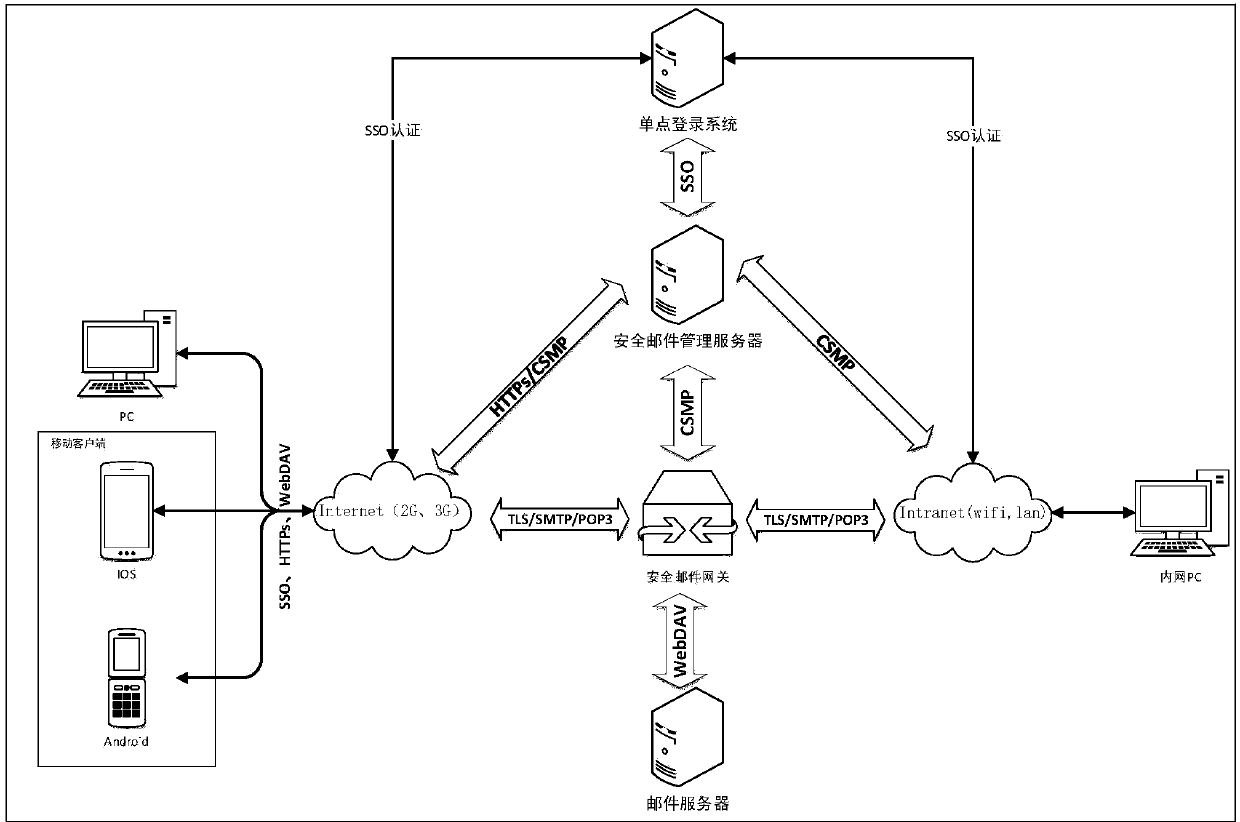
[0098] Embodiment 1 provides an overall architecture diagram for sending and receiving secure emails. attached image 3 The system framework of the present invention includes an external mail client for sending and receiving mail, an intranet mail client for sending and receiving mail, a single sign-on (SSO) system, a security management platform, a secure mail gateway, and a mail server.
[0099] The external mail client can be a mobile mail client, such as a smart phone (such as a common Andriod mobile phone in the prior art, an IPHONE mobile phone of Apple's IOS system), a tablet computer, a PDA and other mobile terminal devices that have the function of sending and receiving mail. The email client can also be various computer terminals with the function of sending and receiving emails, such as PC / notebook based on Windows operating system and PC / notebook based on MAC OS. The mail client of the present invention includes but is not limited to the above-mentioned terminal e...
Embodiment 2
[0108] Embodiment 2 provides a method for sending and receiving emails by a mobile terminal on an external network. Figure 4 It is the working sequence diagram of the external network mobile terminal. The external network mobile terminal is a mobile email client, which includes a single sign-on (SSO) application component (APP), a mobile security management component (APP), and a mobile security software development kit (SDK).
[0109] The specific working sequence of the mobile mail client to send and receive emails is as follows:
[0110] 1) The single sign-on APP connects to the single sign-on platform for identity authentication.
[0111] 2) After the authentication is successful, the token token is returned to the single sign-on APP.
[0112] 3) The single sign-on APP starts the mobile mail client and passes the token to the mobile mail client.
[0113] 4) The mobile mail client accesses the URL1 address in the token.
[0114] 5) During the access process, the SSO se...
Embodiment 3
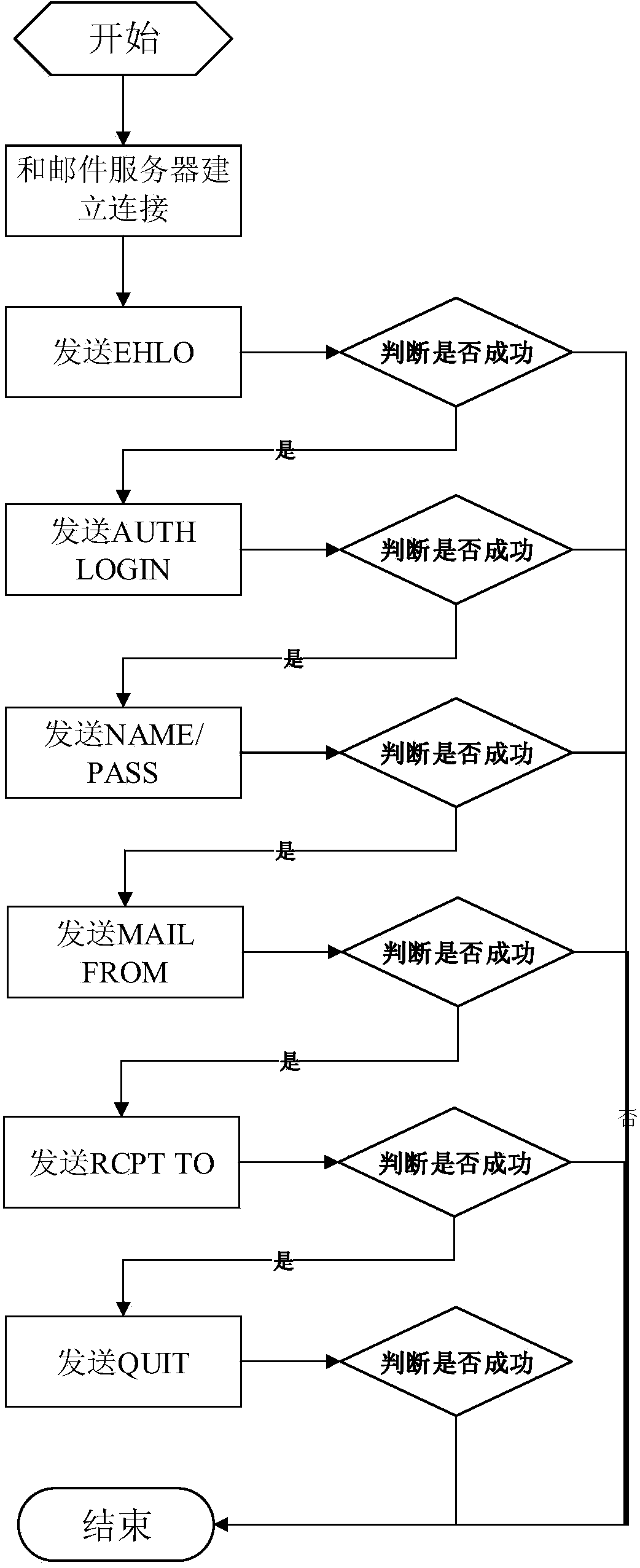
[0124] Embodiment 3 provides a method for a mobile terminal to encrypt sent mail data. Figure 5 It is a flow chart of encrypting mail data when the mobile terminal of the present invention sends mail. The method includes:
[0125] 1) The mobile email client starts sending emails.
[0126] 2) The mobile mail client first inquires whether the recipient's public key exists in the local encrypted database.
[0127] 3) If the recipient's public key exists in the local encrypted database, obtain the recipient's public key directly in the local encrypted database.
[0128] 4) If not found, go to the security management platform to use the email address to obtain the receiver's public key, and cache a copy in the local database.
[0129] 5) Encrypt the symmetric key used to encrypt the email with the receiver's public key.
[0130] 6) The mobile mail client accesses the secure mail gateway to obtain the gateway public key returned by the secure mail gateway.
[0131] 7) Encrypt ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com