Development method and system based on mobile terminal application program security application
A mobile terminal and application technology, applied in the direction of public keys, security devices, transmission systems, etc. of secure communication, can solve the problems of inability to ensure identity security, being stolen, and not doing permission control document life cycle management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
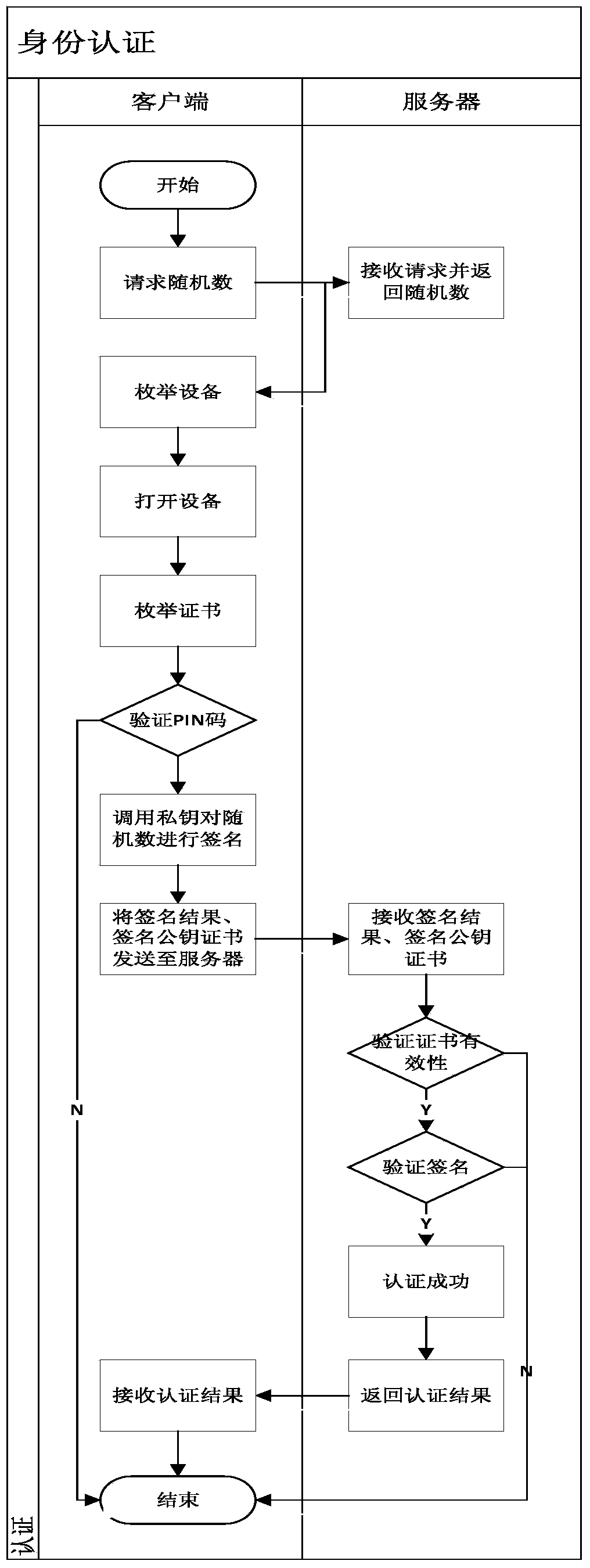
[0079] Embodiment 1 provides a secure communication method between mobile terminals.
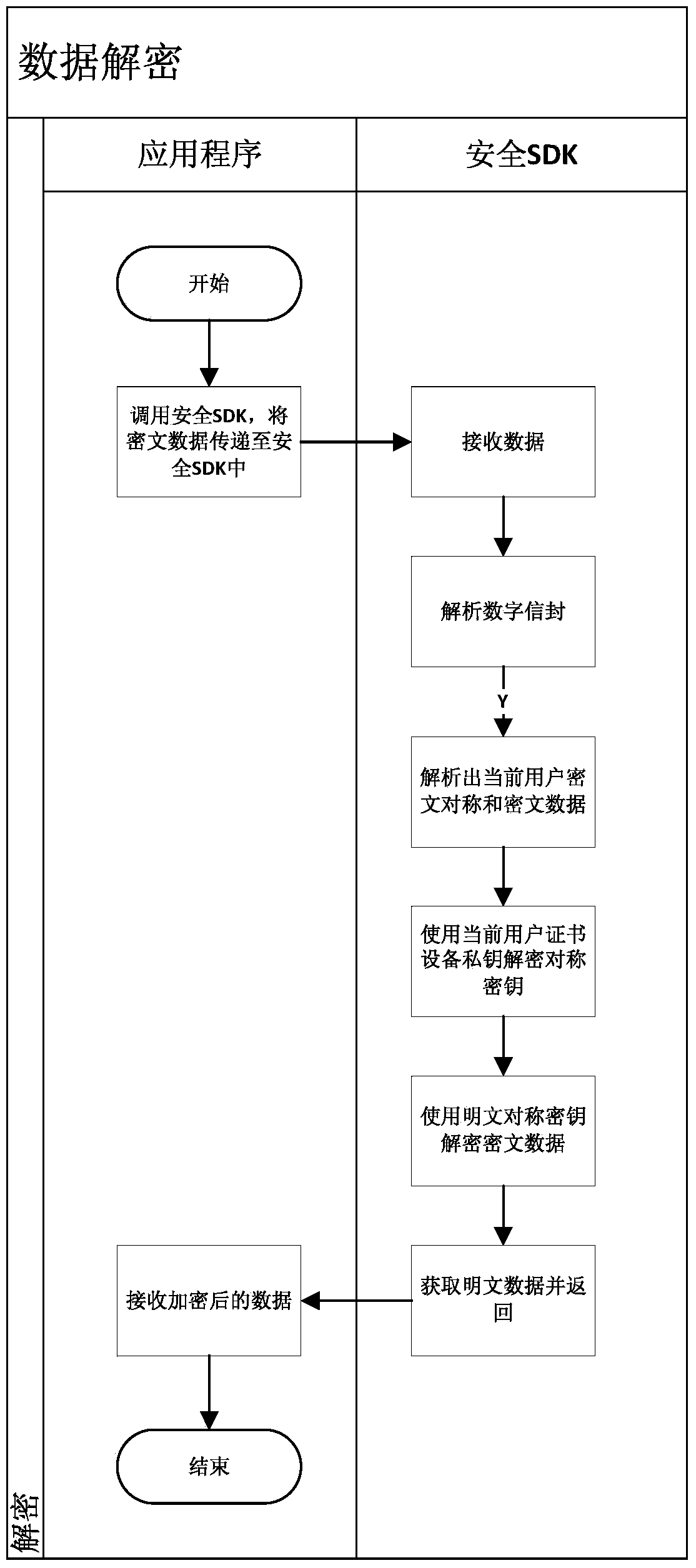
[0080] like Figure 5 As shown, it shows the process of encrypting data information of the mobile terminal of the present invention. The data encryption process specifically includes the following steps: the upper layer application of the mobile terminal calls the security SDK to encrypt data, and after passing in the user information and data information, the security SDK will find the user's public key according to the user information (if it does not exist locally, then Request the user's public key from the server), then generate a symmetric key locally, use the symmetric key to encrypt the data, use the user's public key to encrypt the symmetric key, and combine the encrypted symmetric key and the encrypted data Assemble into a digital envelope, and finally return the digital envelope to the upper application program of the mobile terminal.
[0081] like Image 6 As shown in , it sho...
Embodiment 2
[0083] Embodiment 2 provides a secure email communication method between mobile terminals.
[0084] Place Figure 7 As shown in , it shows the overall framework of the mobile terminal securely sending emails through the SDK.
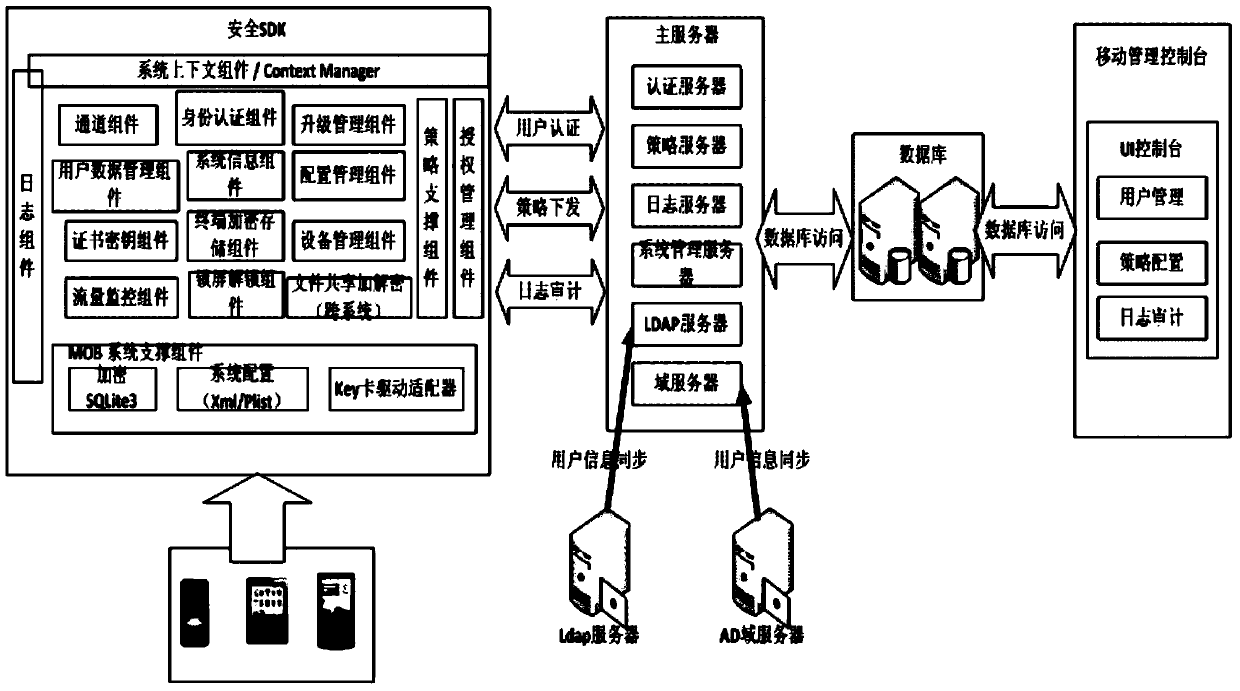
[0085] It includes mail server, mail client, security management platform and database. The mail server realizes the sending and receiving of mails. The client can be either a fixed PC client or a mobile andriod / IOS client. The client integrates the basic SDK, which realizes the functions of email identity authentication and data encryption / decryption, obtains the KEY of data encryption through network communication, and the client realizes identity authentication, policy and encryption public key acquisition through communication with the security management platform. The security management platform includes security services Processing service components and WEB service components, which respectively include identity authentication components, certif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com