Patents
Literature
101results about How to "Easy to be stolen" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
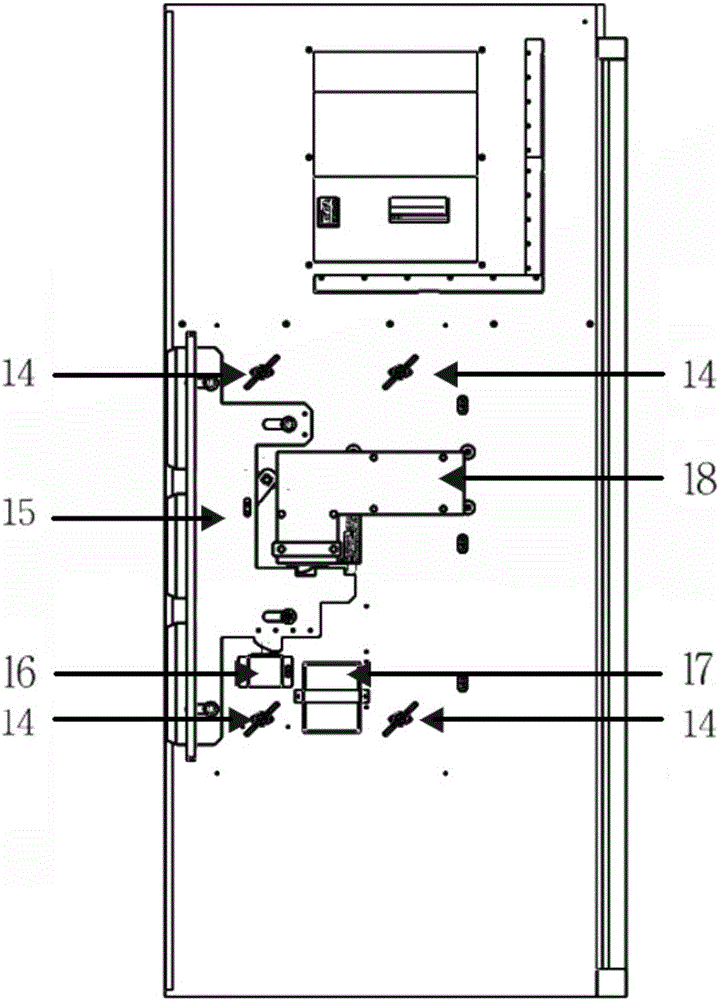
Inventor
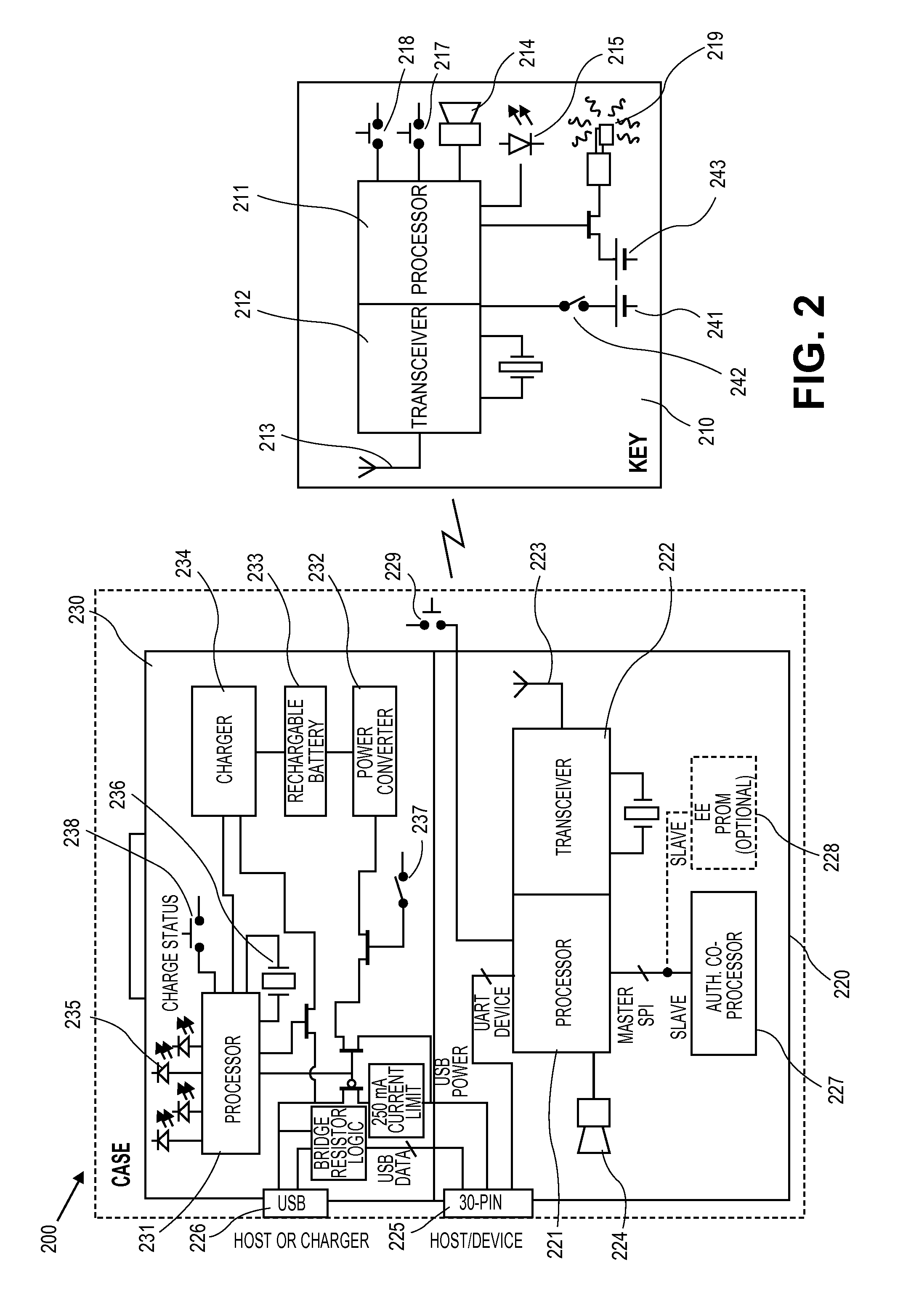
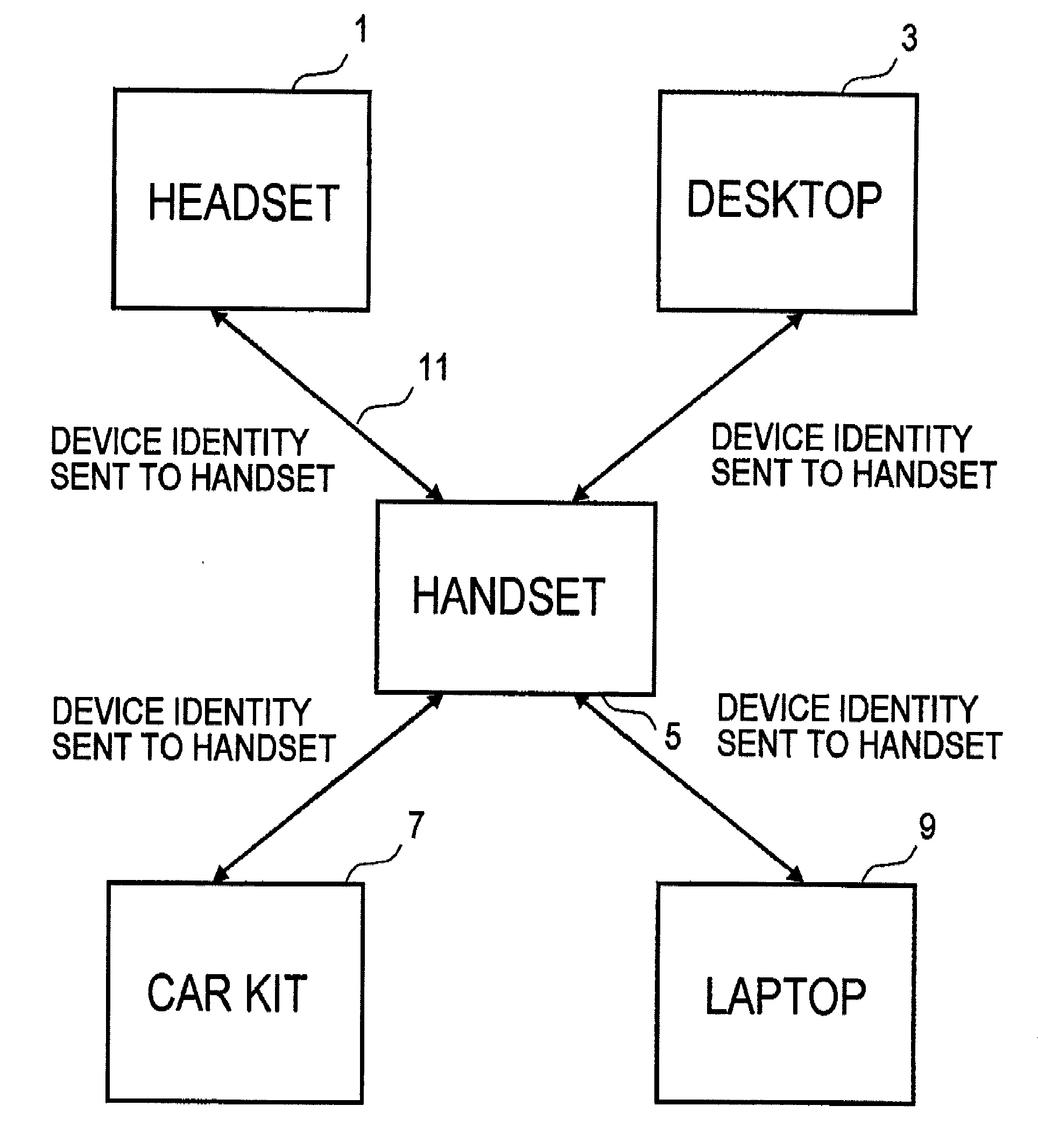
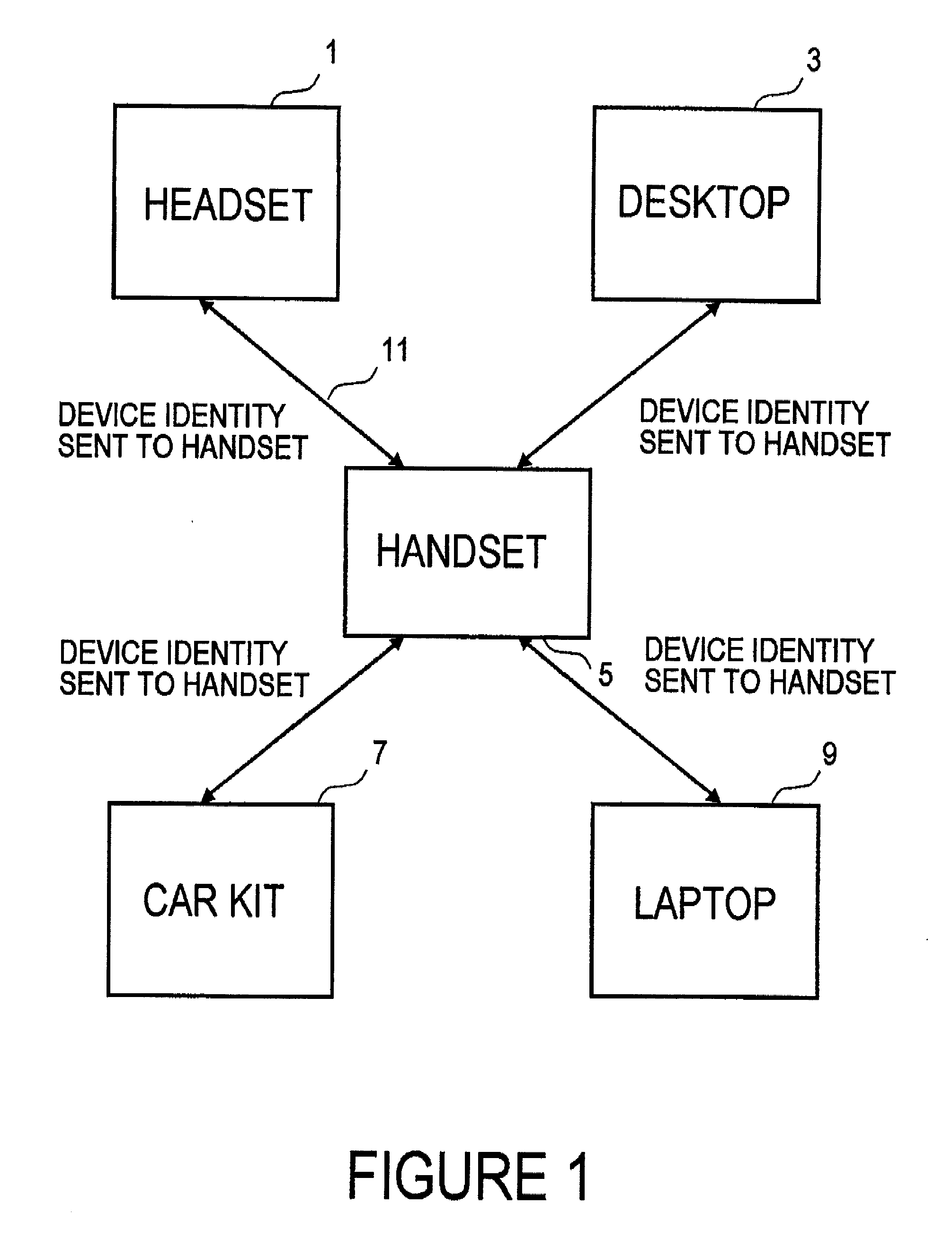
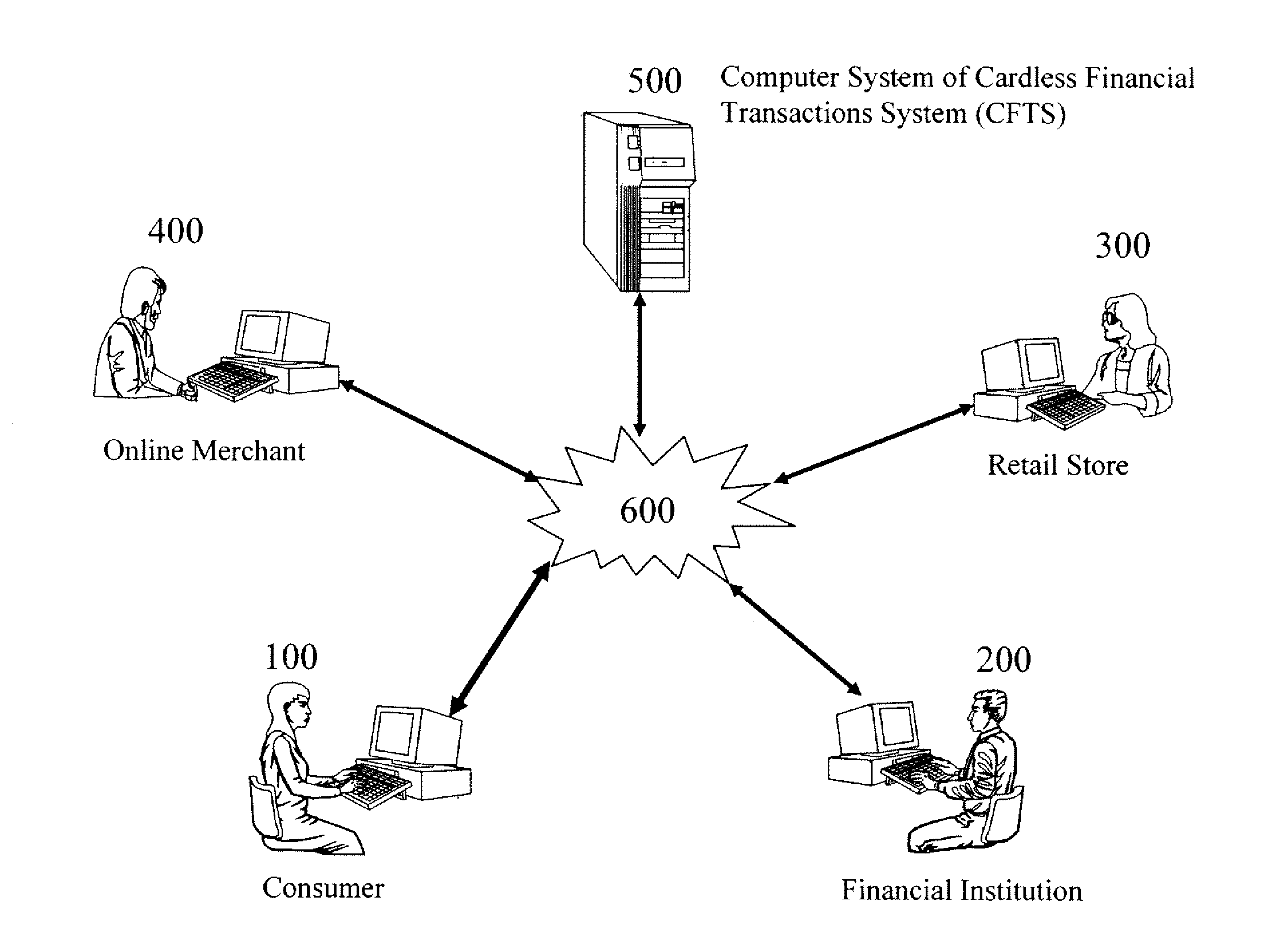
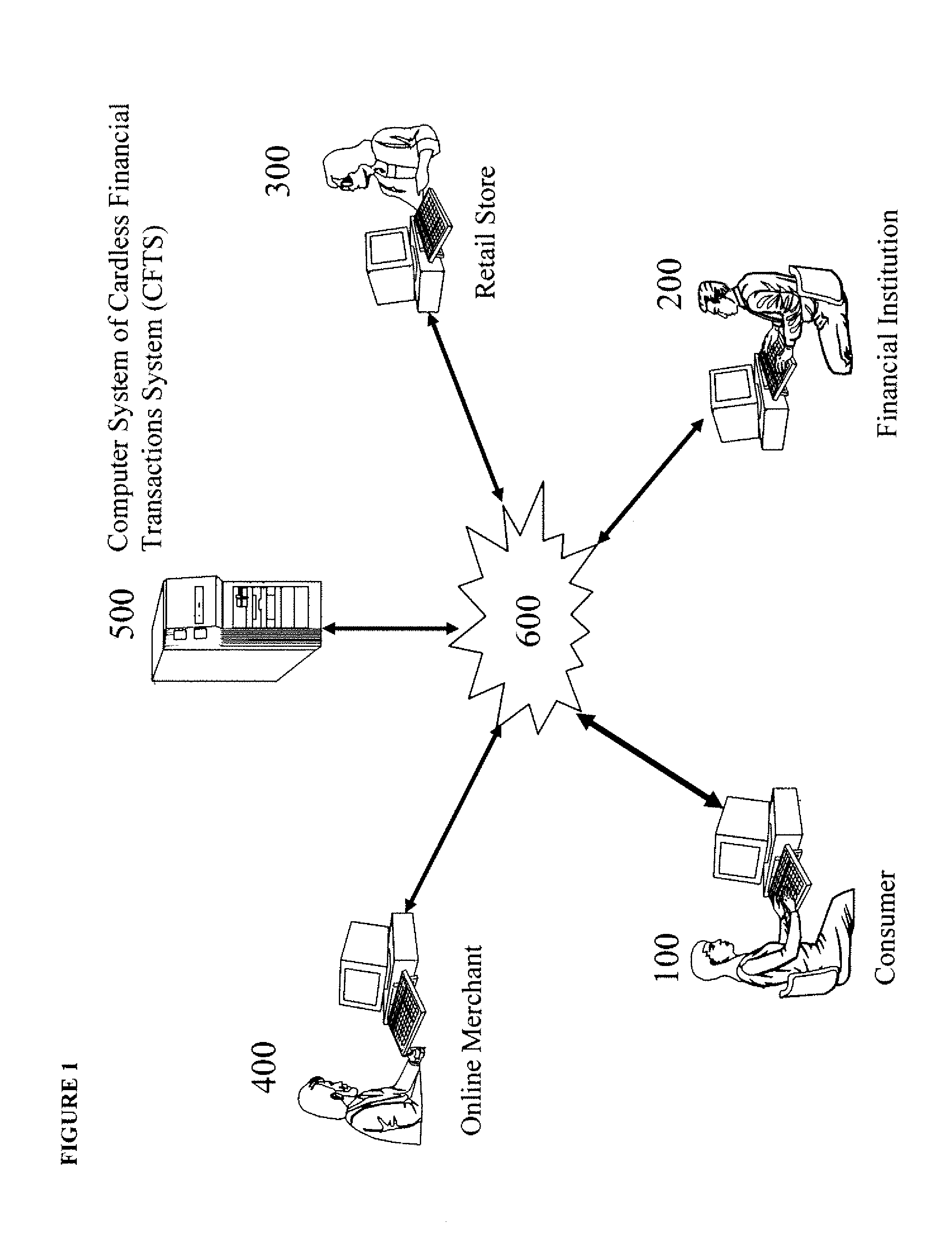
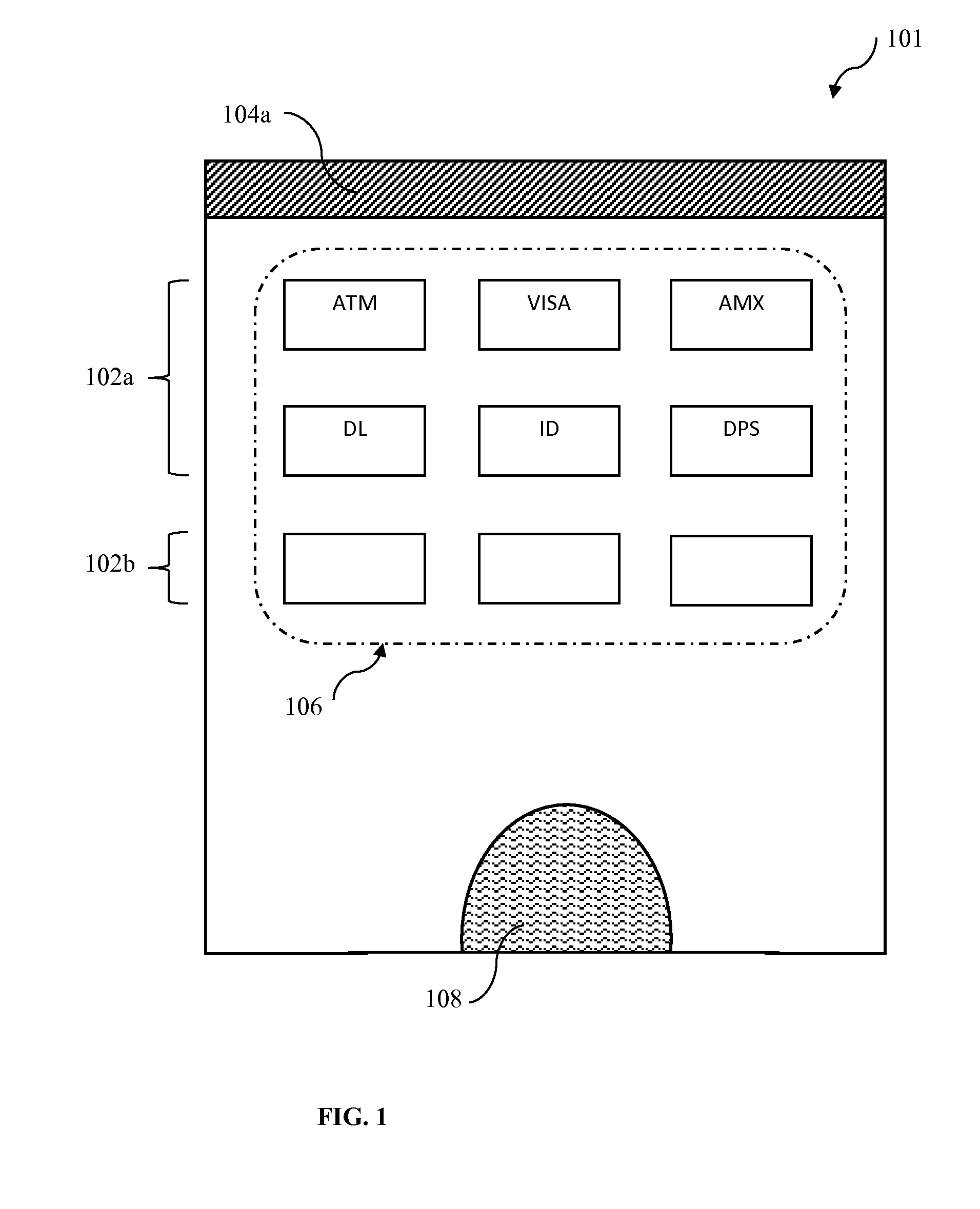
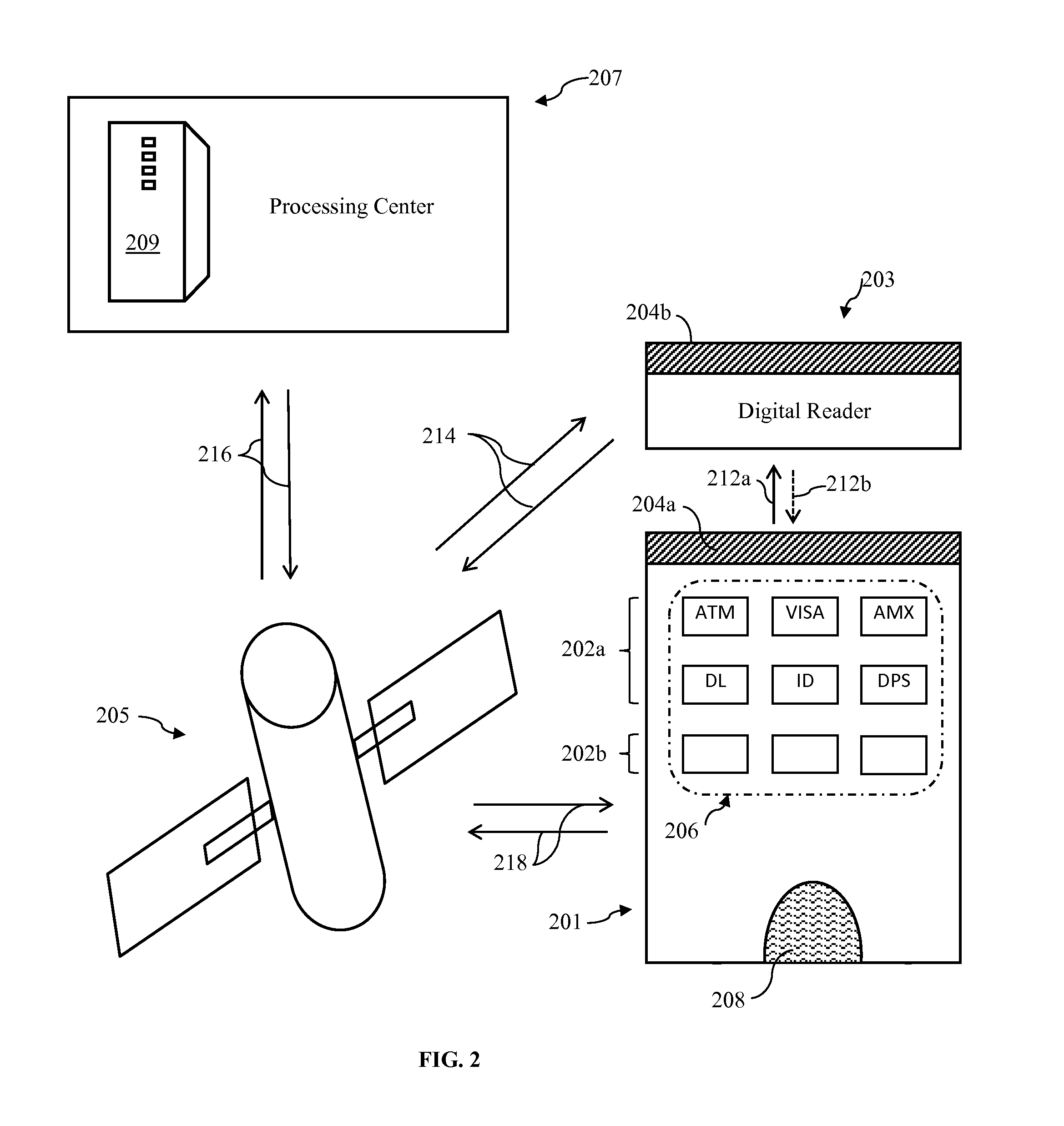
Wireless communications apparatus and method
InactiveUS7146191B2Easy to be stolenProcess safetyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInterconnectivityDisplay device
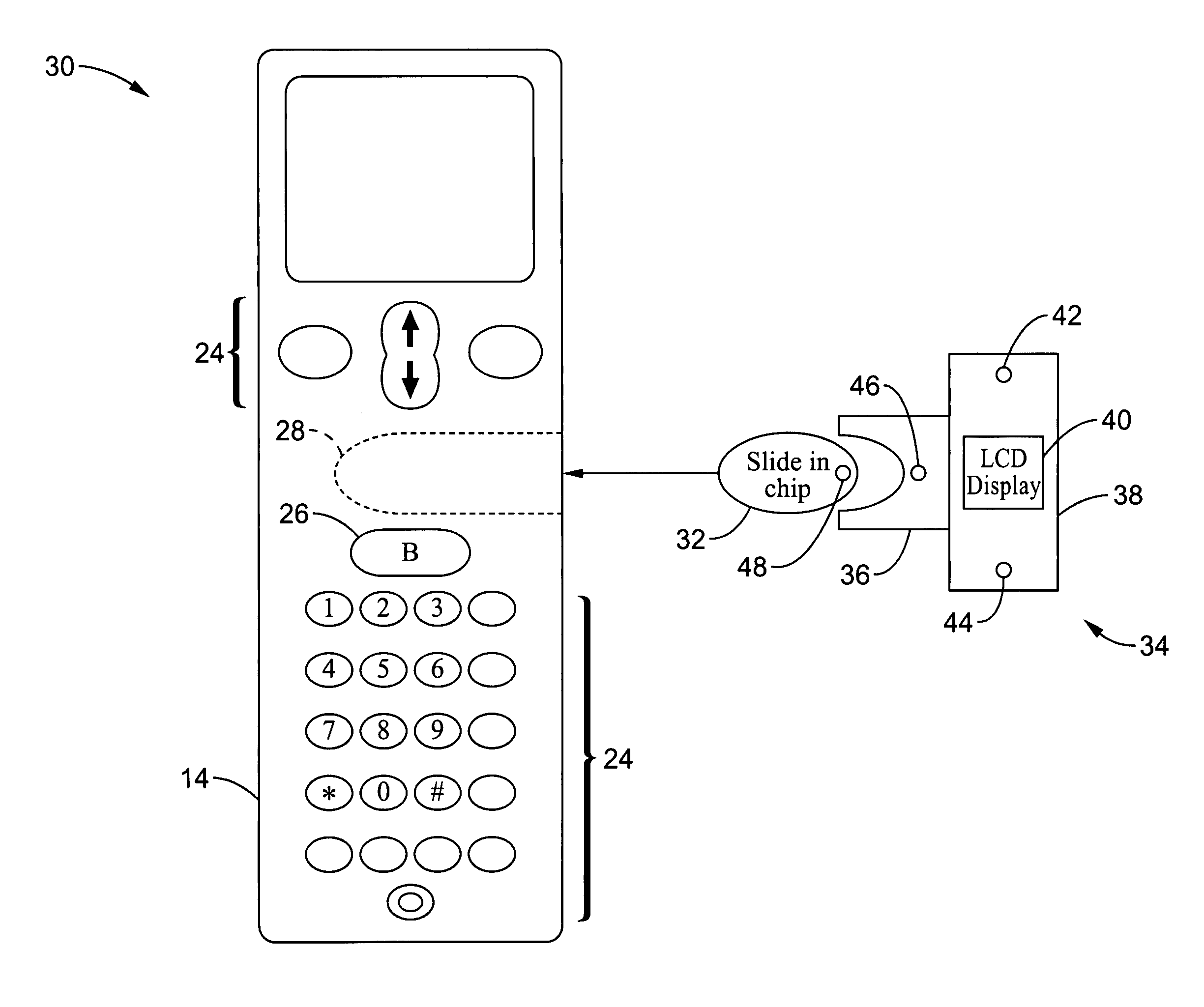
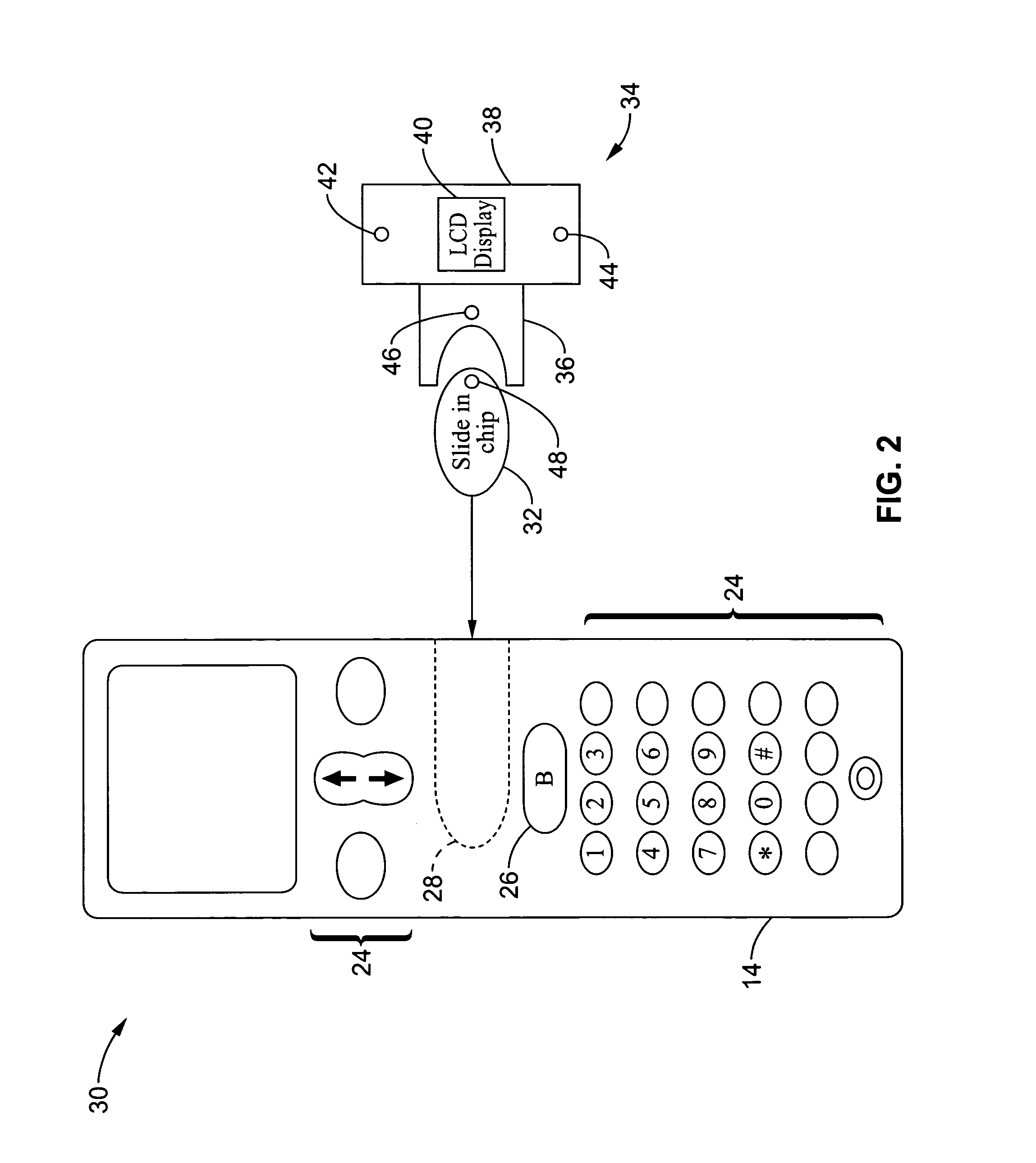
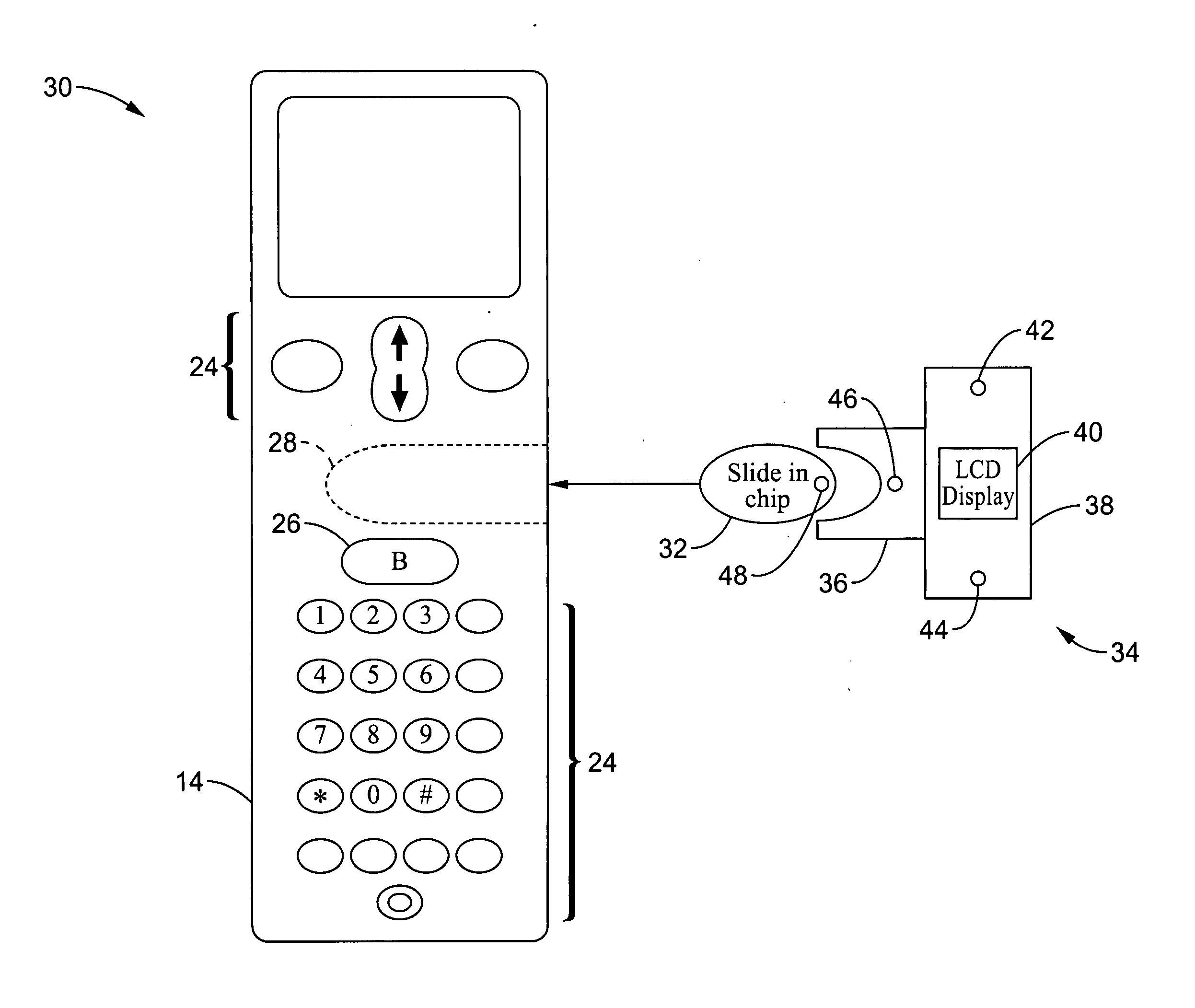
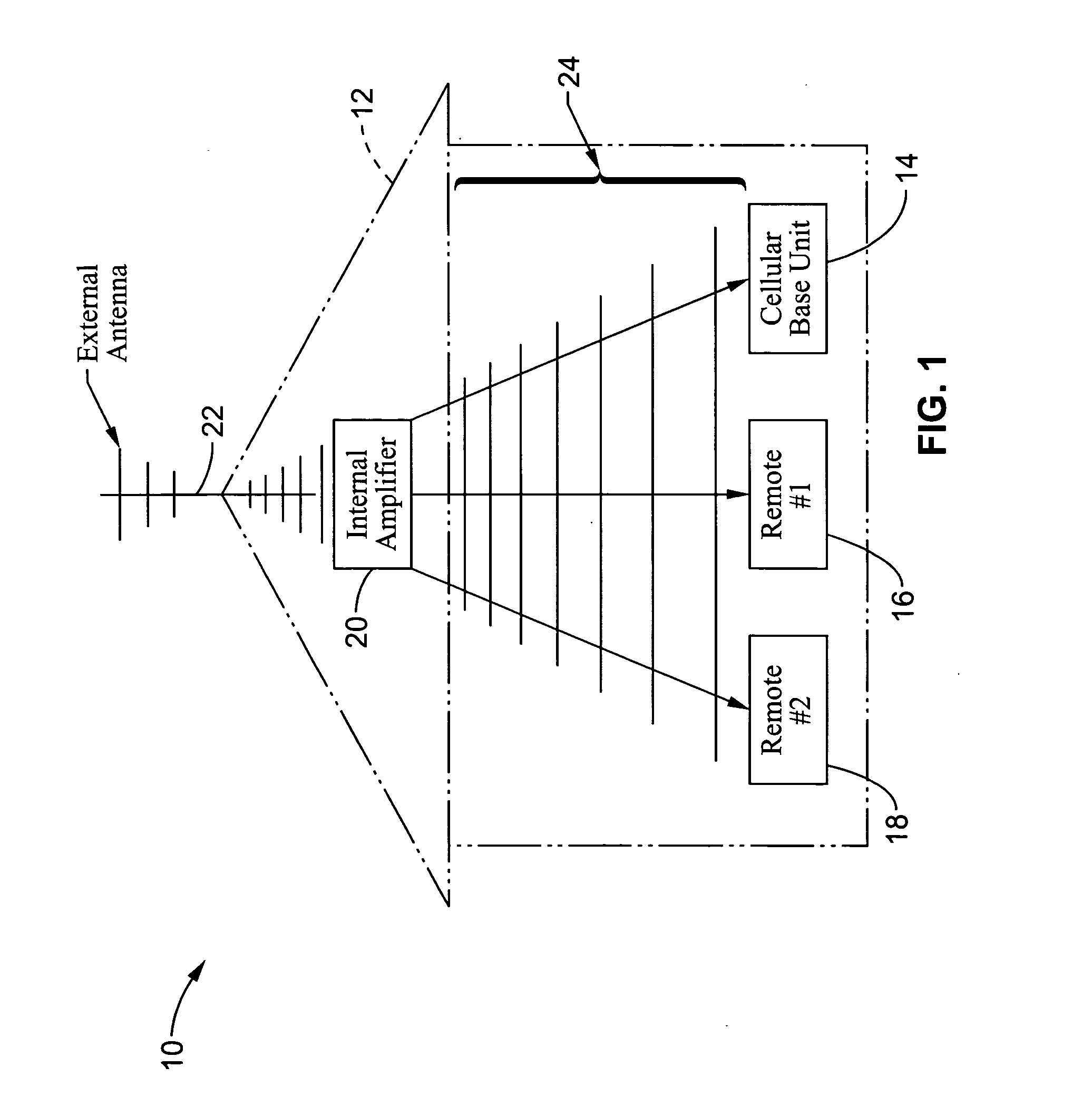
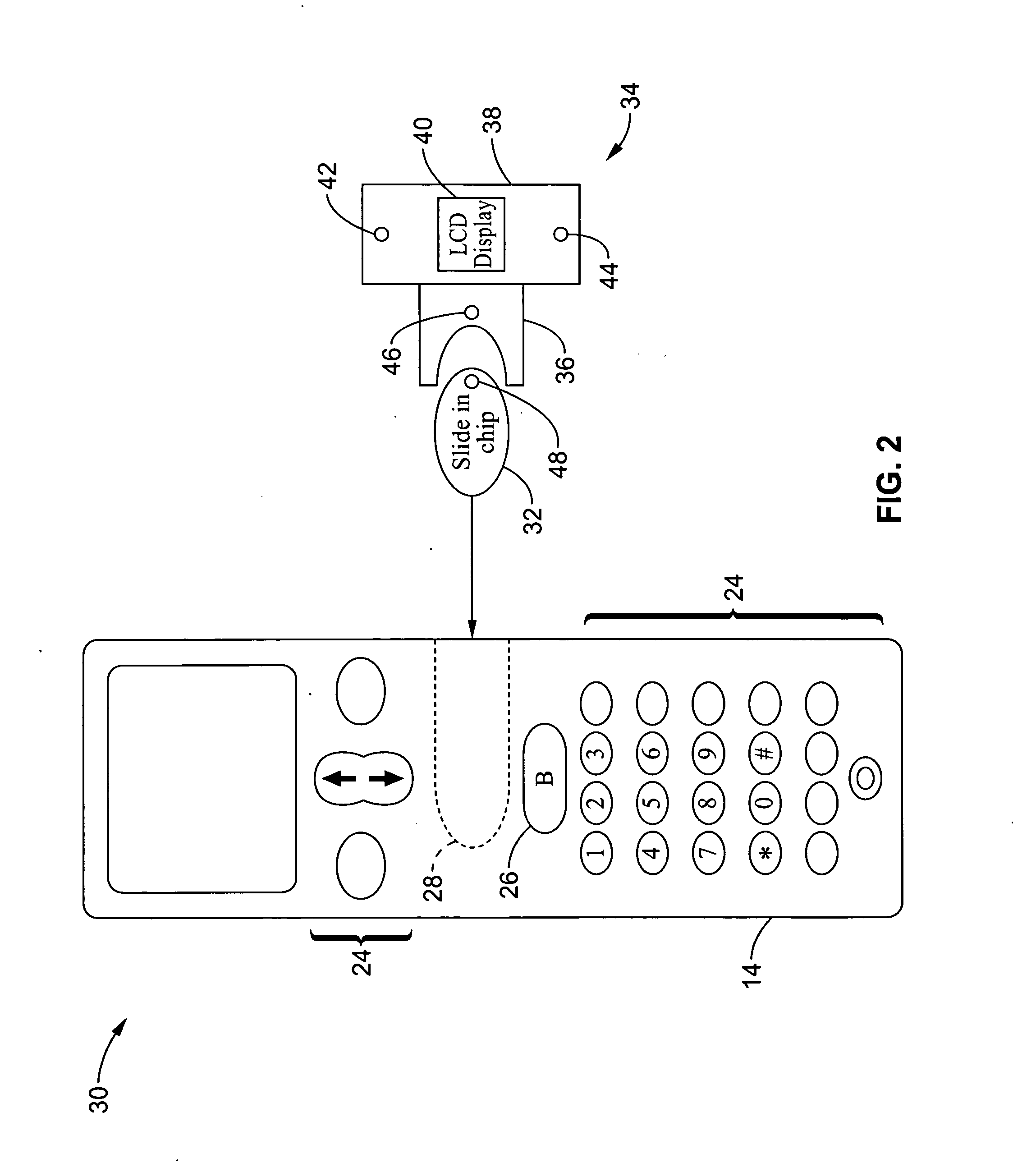
A wireless communication method and apparatus are described for increasing security for communication devices utilizing identification chips for accessing wireless networks and the associated billing for services. One aspect of the invention is an enhanced phone chip and a communications device adapted to engage the enhanced phone chip, which then cannot be installed or removed from the wireless communications device by unauthorized users. In one embodiment a security key mates to the identification chip and is utilized for installing and removing the enhanced phone chip. The security key preferably has a display upon which information about the communication device is displayed prior to removing the security key after installing the enhanced phone chip. Other aspects of the invention include wireless base station communication devices which support wired (dedicated and non-dedicated), and more preferably wireless extensions, while providing sharing of wireless network resources and interconnectivity between base station and extensions.
Owner:US THERMOELECTRIC CONSORTIUM
Wireless communications apparatus and method
InactiveUS20050159184A1Security and flexibility of systemEasy to be stolenUnauthorised/fraudulent call preventionEavesdropping prevention circuitsBase stationDisplay device
A wireless communication method and apparatus are described for increasing security for communication devices utilizing identification chips for accessing wireless networks and the associated billing for services. One aspect of the invention is an enhanced phone chip and a communications device adapted to engage the enhanced phone chip, which then cannot be installed or removed from the wireless communications device by unauthorized users. In one embodiment a security key mates to the identification chip and is utilized for installing and removing the enhanced phone chip. The security key preferably has a display upon which information about the communication device is displayed prior to removing the security key after installing the enhanced phone chip. Other aspects of the invention include wireless base station communication devices which support wired (dedicated and non-dedicated), and more preferably wireless extensions, while providing sharing of wireless network resources and interconnectivity between base station and extensions.
Owner:US THERMOELECTRIC CONSORTIUM
Proximity tag
InactiveUS20130225127A1Maximize utilizationEasily misplacedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsSecurity system
A system and method for securing a portable consumer device is disclosed. One embodiment of the present invention may be directed to a security system comprising a first wireless apparatus for use with a mobile communication device and a second wireless apparatus configured to removably and electrically couple to the mobile communication device. The second wireless apparatus comprising a second processor, a mobile communication device interface element, and a second computer readable medium coupled to the second processor and comprising code executable by the second processor to implement a method comprising determining whether the second wireless apparatus is within a particular distance from the first wireless apparatus, and locking the mobile communication device from use if the second wireless apparatus is not within the particular distance from the first wireless apparatus. Some embodiments may lock the mobile communication device from use if a tamper switch has been triggered.
Owner:ACCO BRANDS CORP
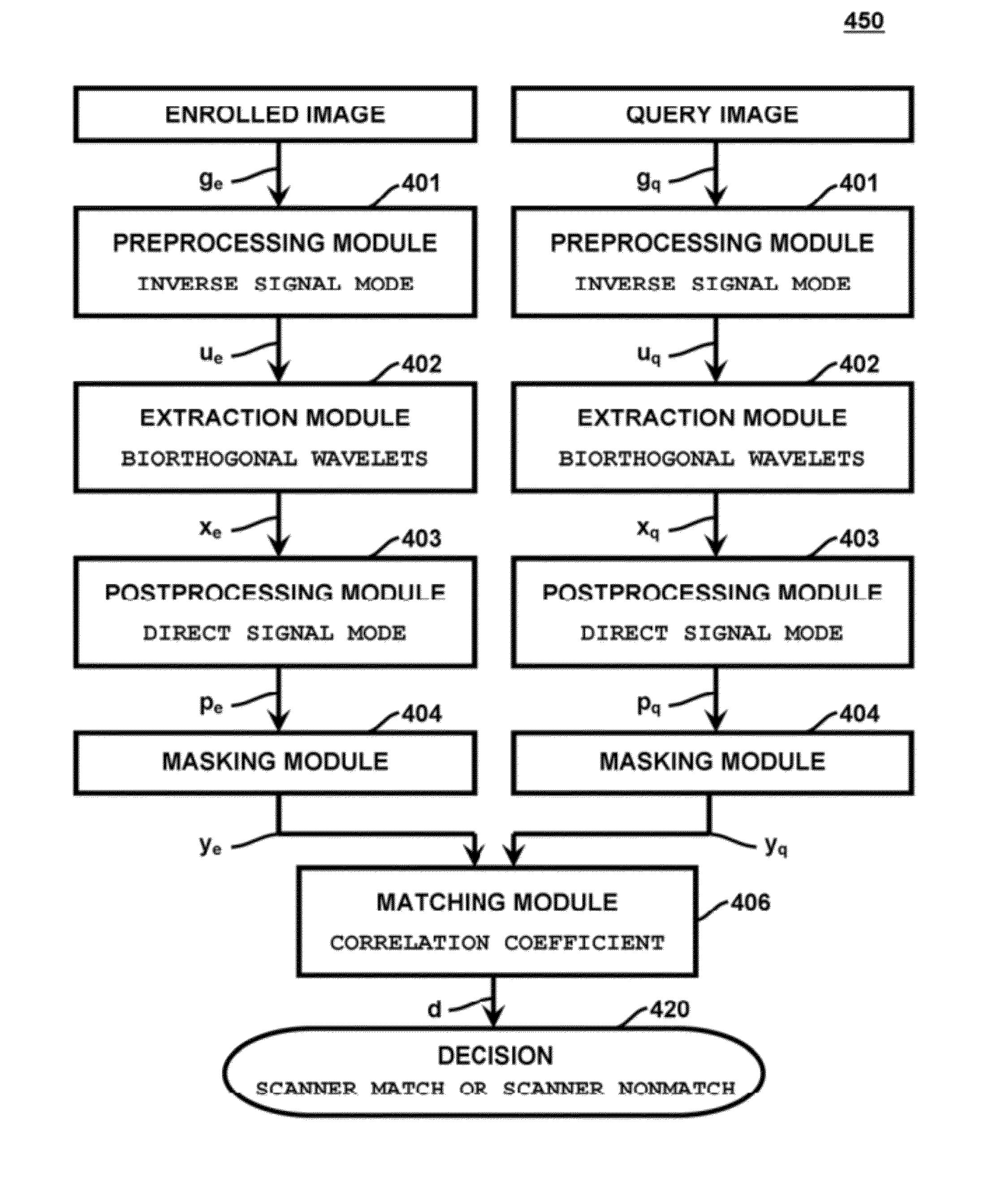
Method and apparatus for authenticating swipe biometric scanners
ActiveUS8942438B2Improve securityAvoid attackImage enhancementPrint image acquisitionImaging processingUser authentication
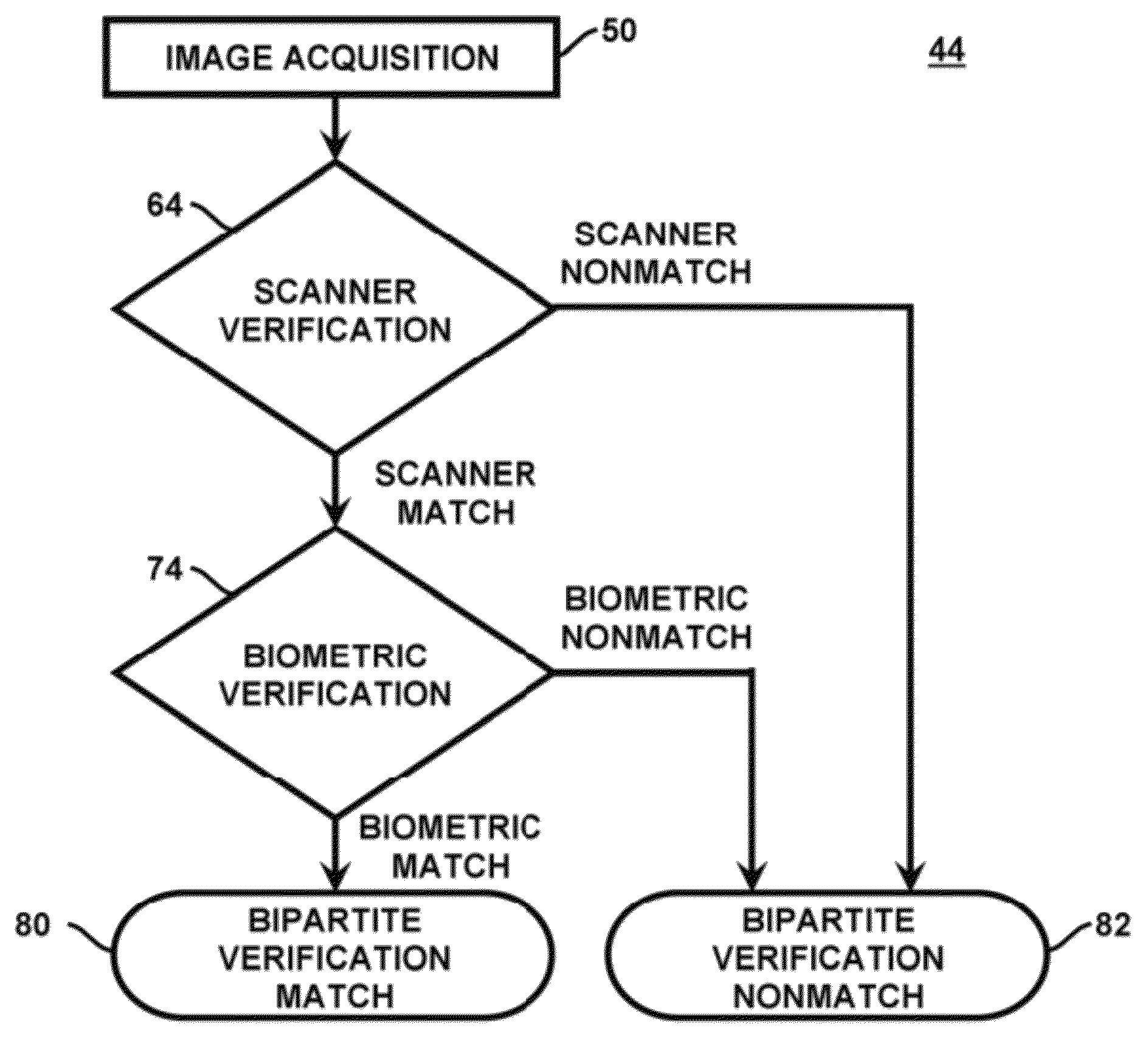
Methods and apparatuses for authenticating a biometric scanner, such as swipe type finger print scanners, involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeit biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND BALTIMORE
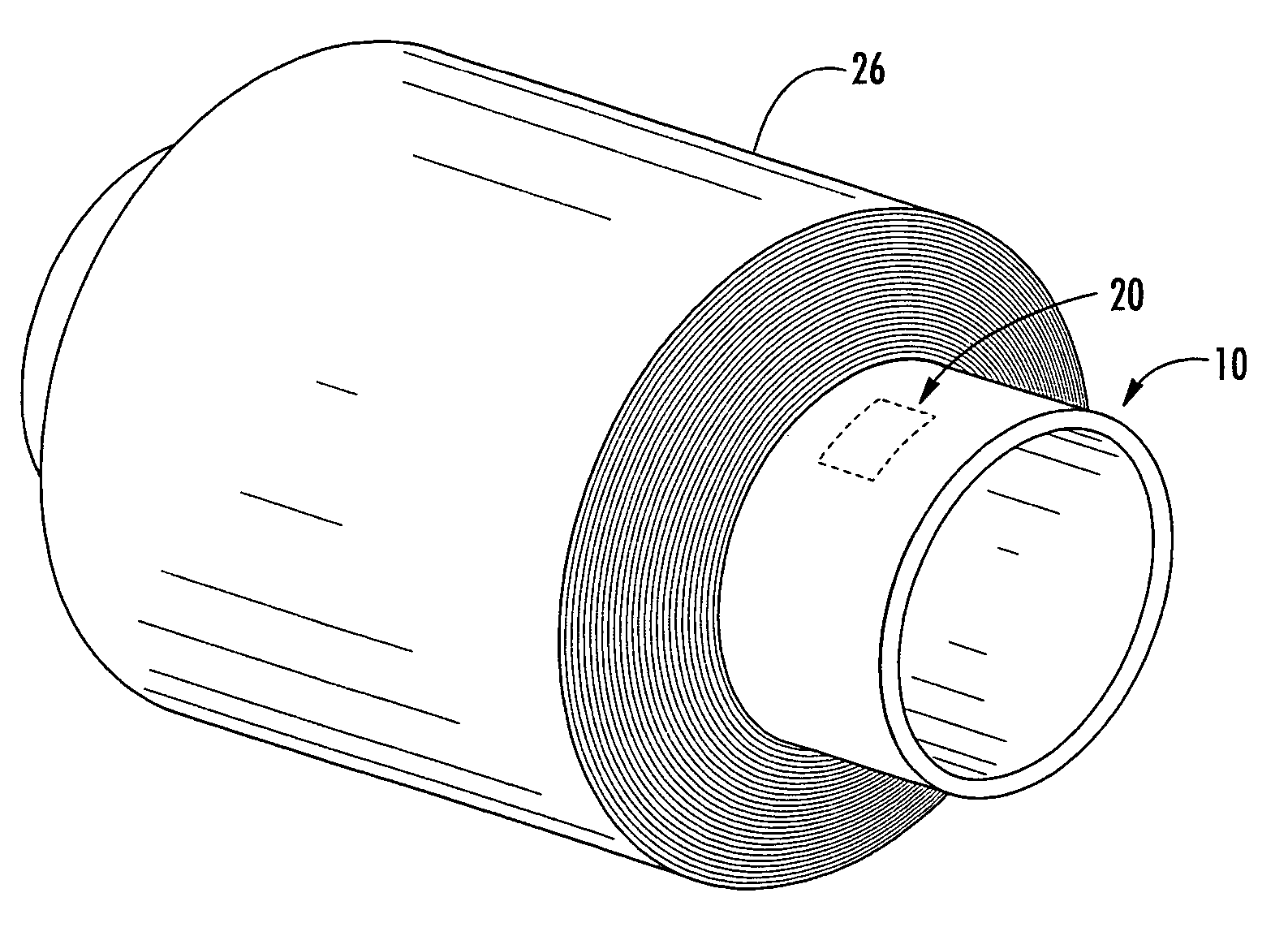
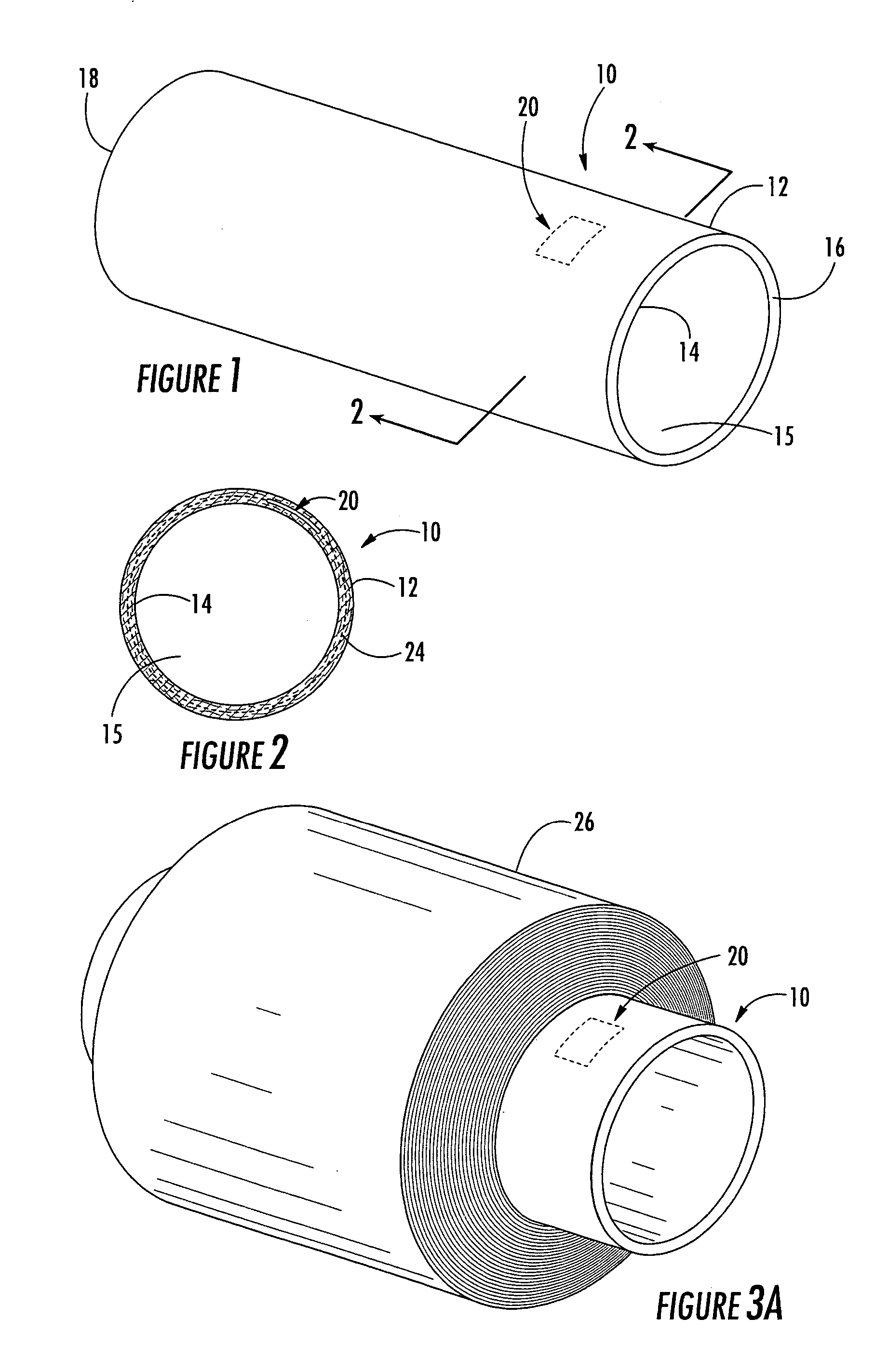
Identification device for multilayer tubular structures
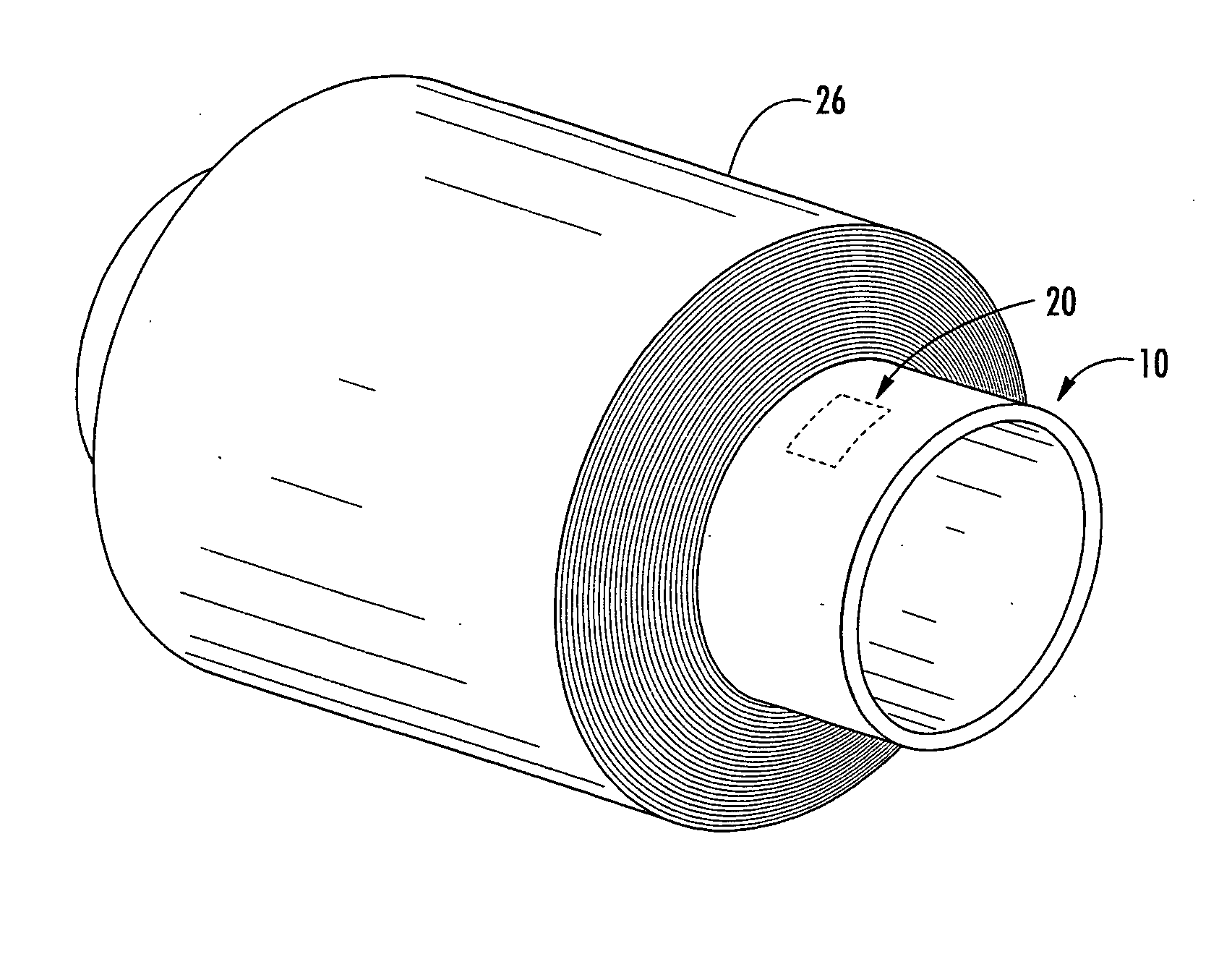
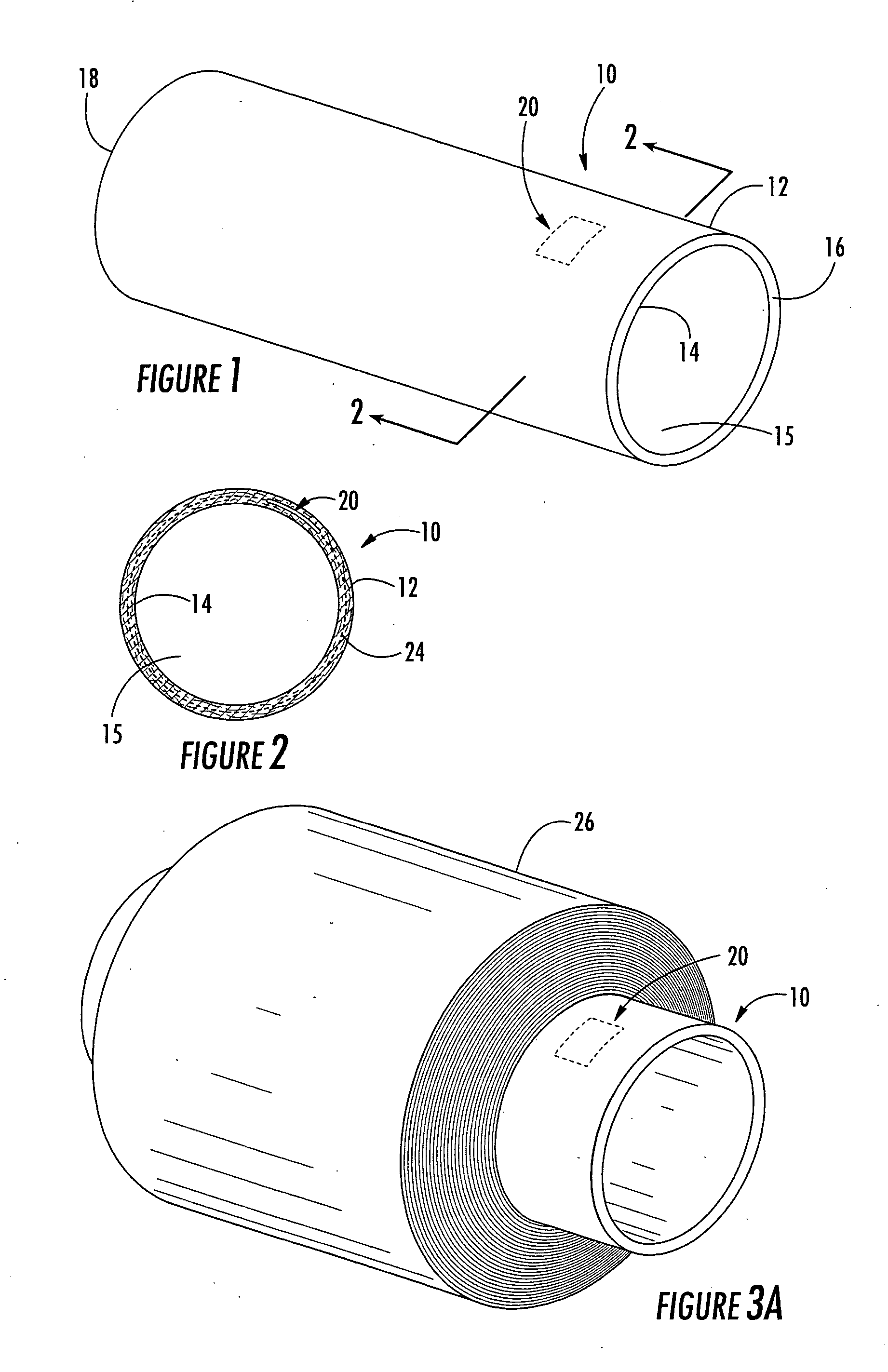
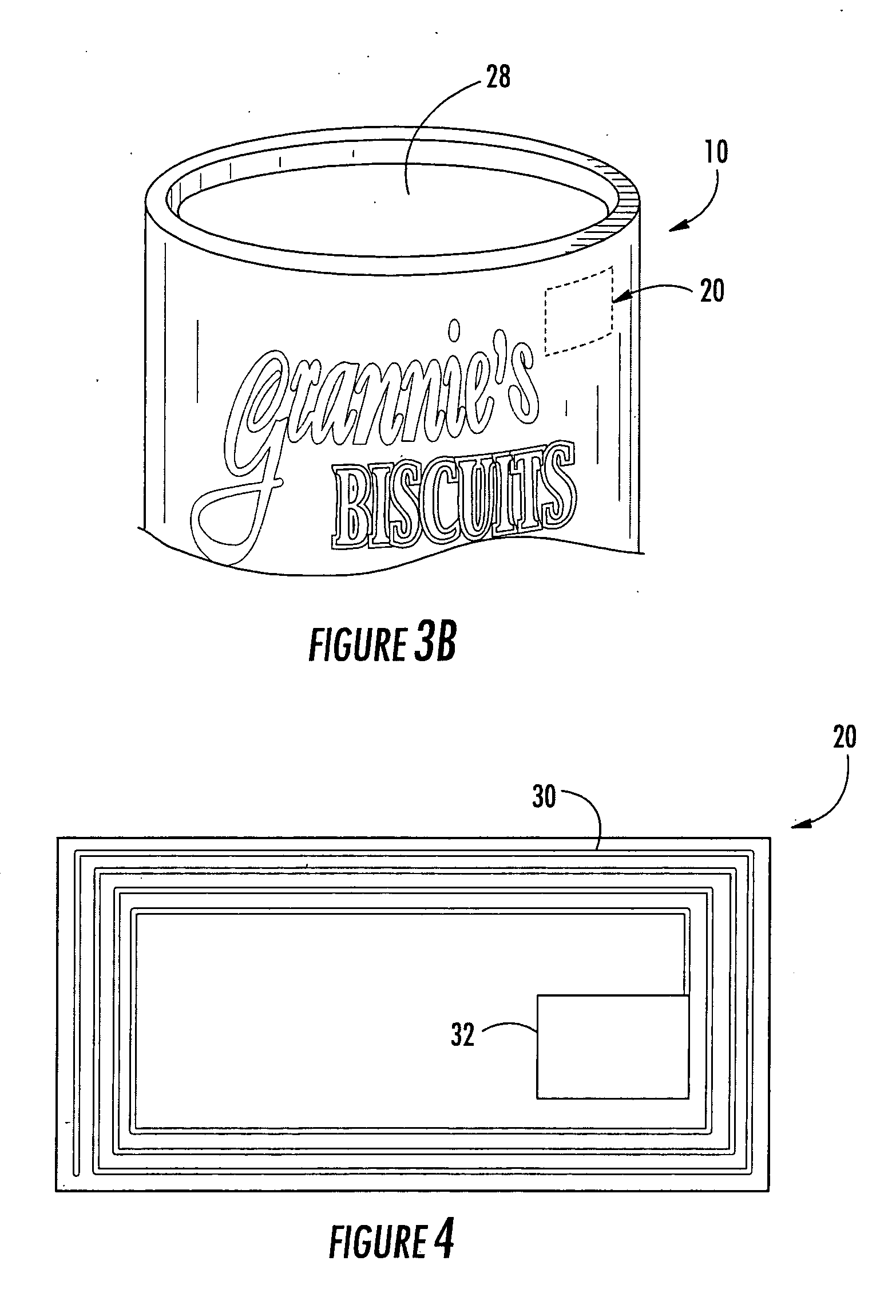
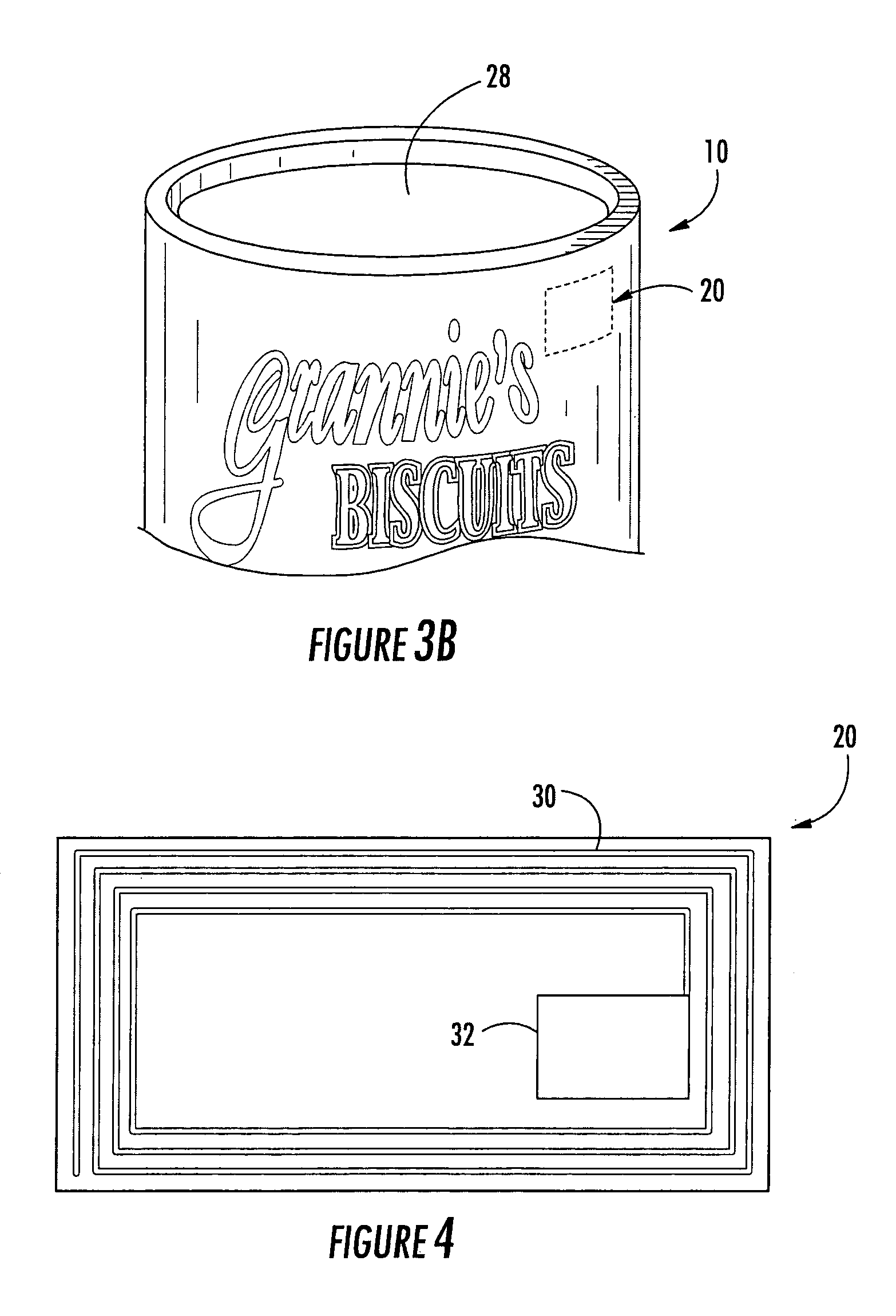
ActiveUS20050237200A1Less likely be possibly removedEasy to useContainer decorationsLevel indicationsEngineeringIdentification device
A multilayer tubular structure for products with an identification device being embedded or interposed between two of the multiple layers of the tubular structure. The identification device is responsive to radio frequencies and is able to store and transmit information about the multilayer tubular structure, the products, and processes that have been performed on same. A method is provided for manufacturing a multilayer tubular structure by embedding a radio frequency identification device between two of the multiple layers.
Owner:SONOCO DEV INC
Two-party distributed SM9 digital signature generation method and system
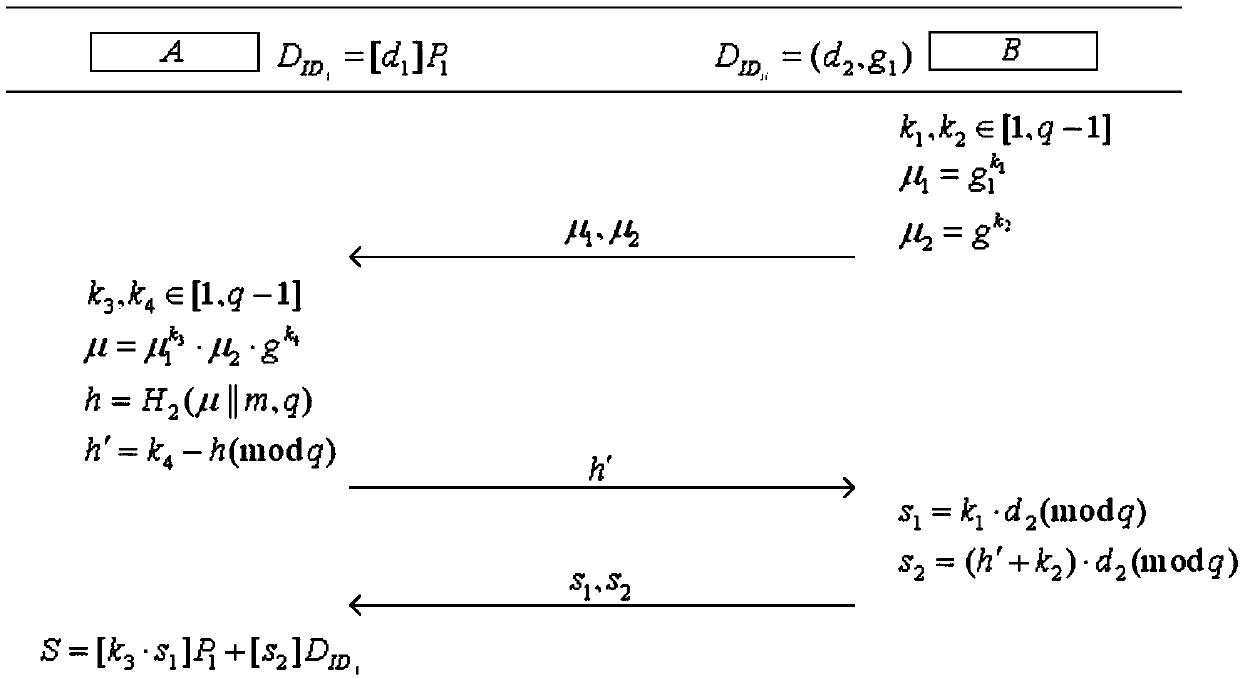
InactiveCN107566128AEasy to be stolenPrevent theftKey distribution for secure communicationUser identity/authority verificationComputer securityDigital signature
The invention discloses a two-party distributed SM9 digital signature generation method and a two-party distributed SM9 digital signature generation system. In the method, a KGC generates a corresponding private key for two communication parties A and B participating in an SM9 digital signature, and the party A sends a signing request to the party B after a signing key is received. The party B selects random numbers k1, k2 which belong to [1, q-1], computes [mu]1=g1<k1> and [mu]2=g<k2>, and returns [mu]1 and [mu]2 to the party A. At the moment, the party A randomly selects k3 and k4, computesa first part h of the signature, and returns h'=k4-h(modq) to the party B. The party B computes s1 and s2 by using the own private key and sends s1 and s2 to the party A. After receiving s1 and s2, the party A uses the own private key to compute a second part S of the signature, and after verification of the signature is passed, the party A publishes the complete SM9 digital signature (h, S). Themethod and the system provided by the invention have the advantages of being high in security and execution efficiency and prone to verify; during a digital signature generation process, the SM9 digital signature can only be generated in a distributed manner under the condition that the two communication parties participate in jointly, the signature sub-key can be effectively prevented from beingstolen by external attackers and counterfeiting of internal participators can be effectively avoided, and generation security and fairness of the SM9 digital signature the two parties participate in are improved.
Owner:WUHAN UNIV
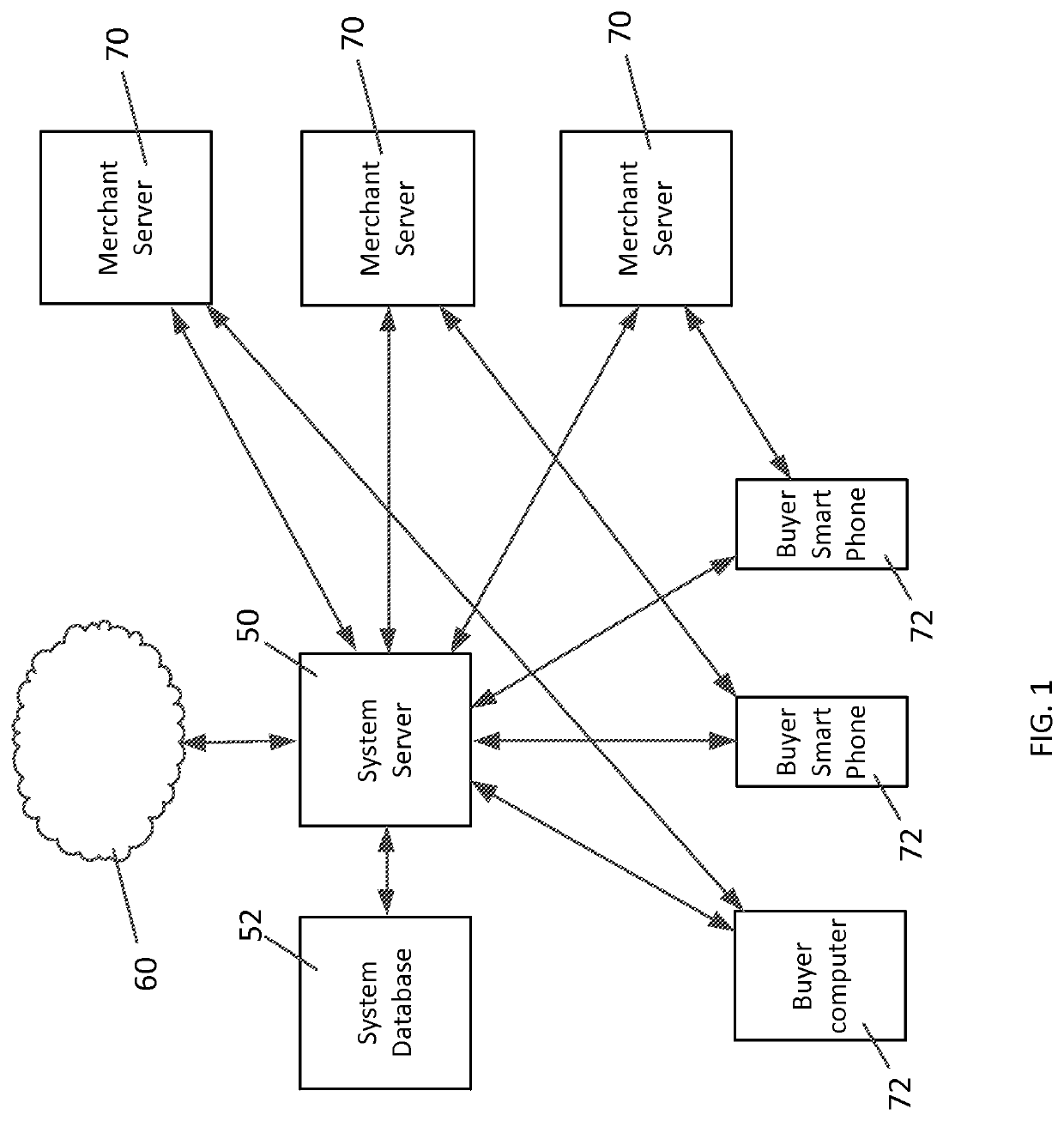
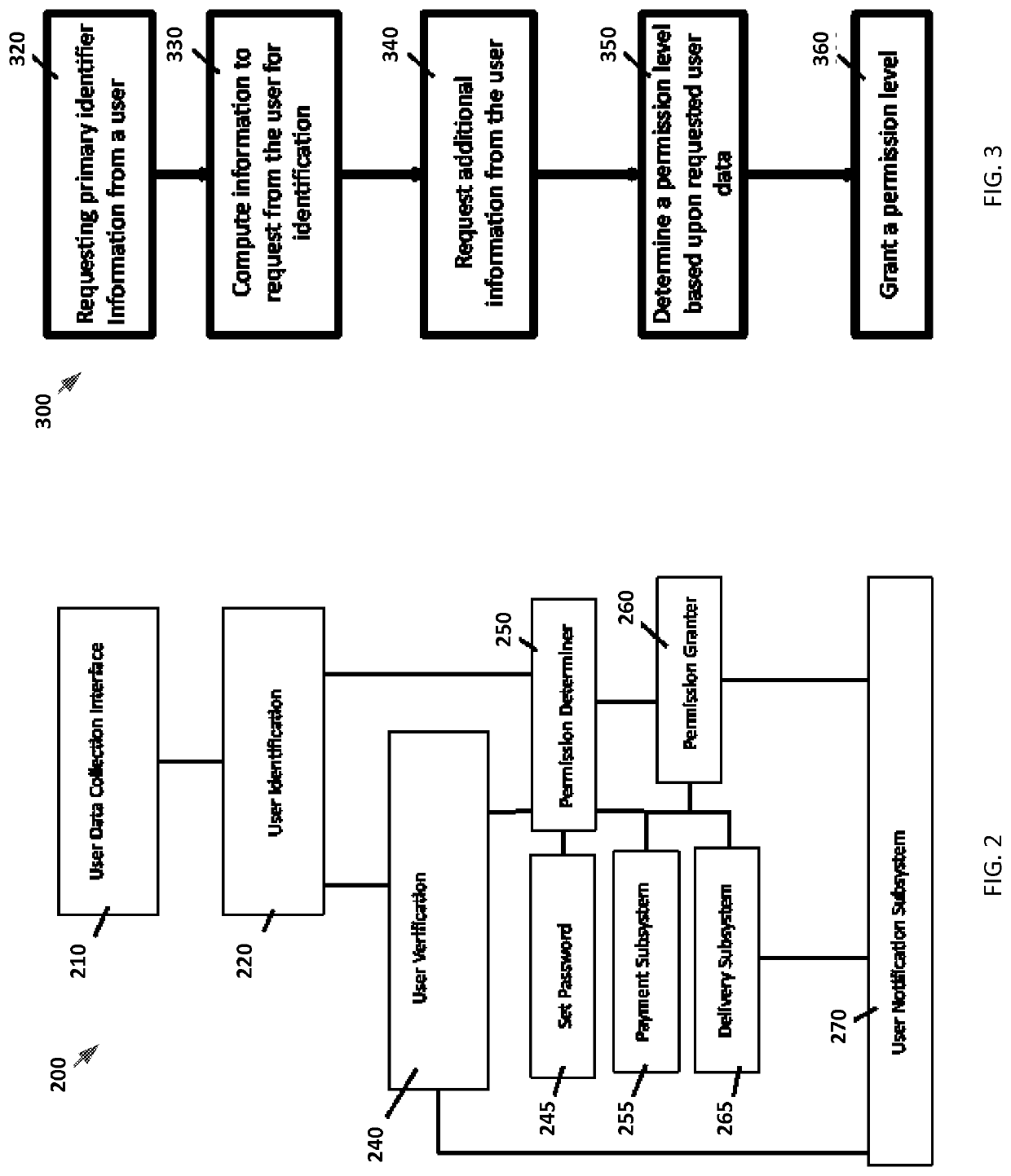
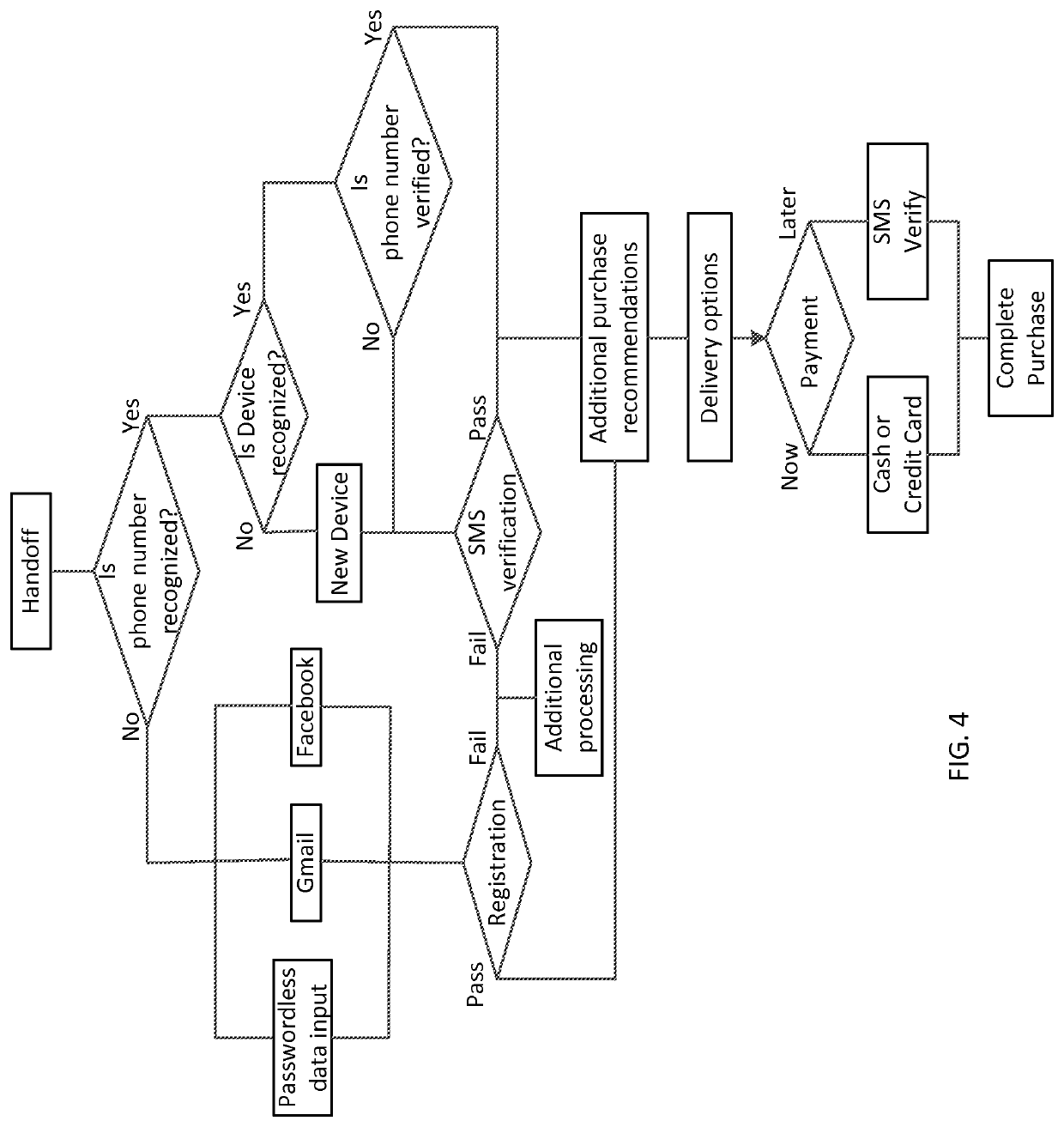
System and method for passwordless logins
ActiveUS10686781B1Significant comprehensive benefitsStrong indicationDigital data authenticationTransmissionPasswordEngineering
A login system allows users to access computer systems without using a password. The passwordless system and method can use other information to securely and reliably identify true authorized system users. The identity of a user can be associated with their mobile device. The login can be based upon a minimal amount of information such as a name and a phone number which can be stored as an identification record for each of the users in a database.
Owner:AFFIRM INC
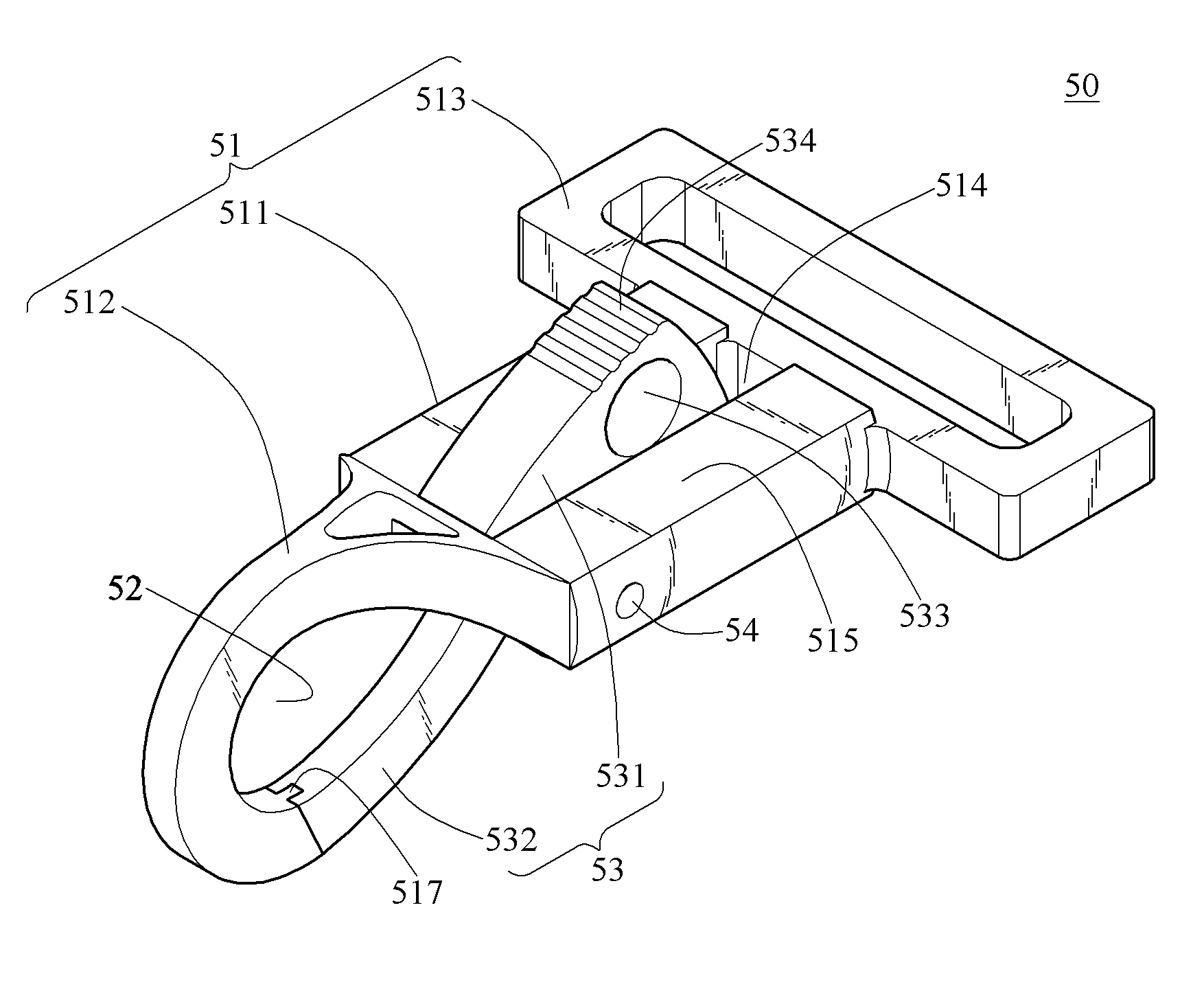
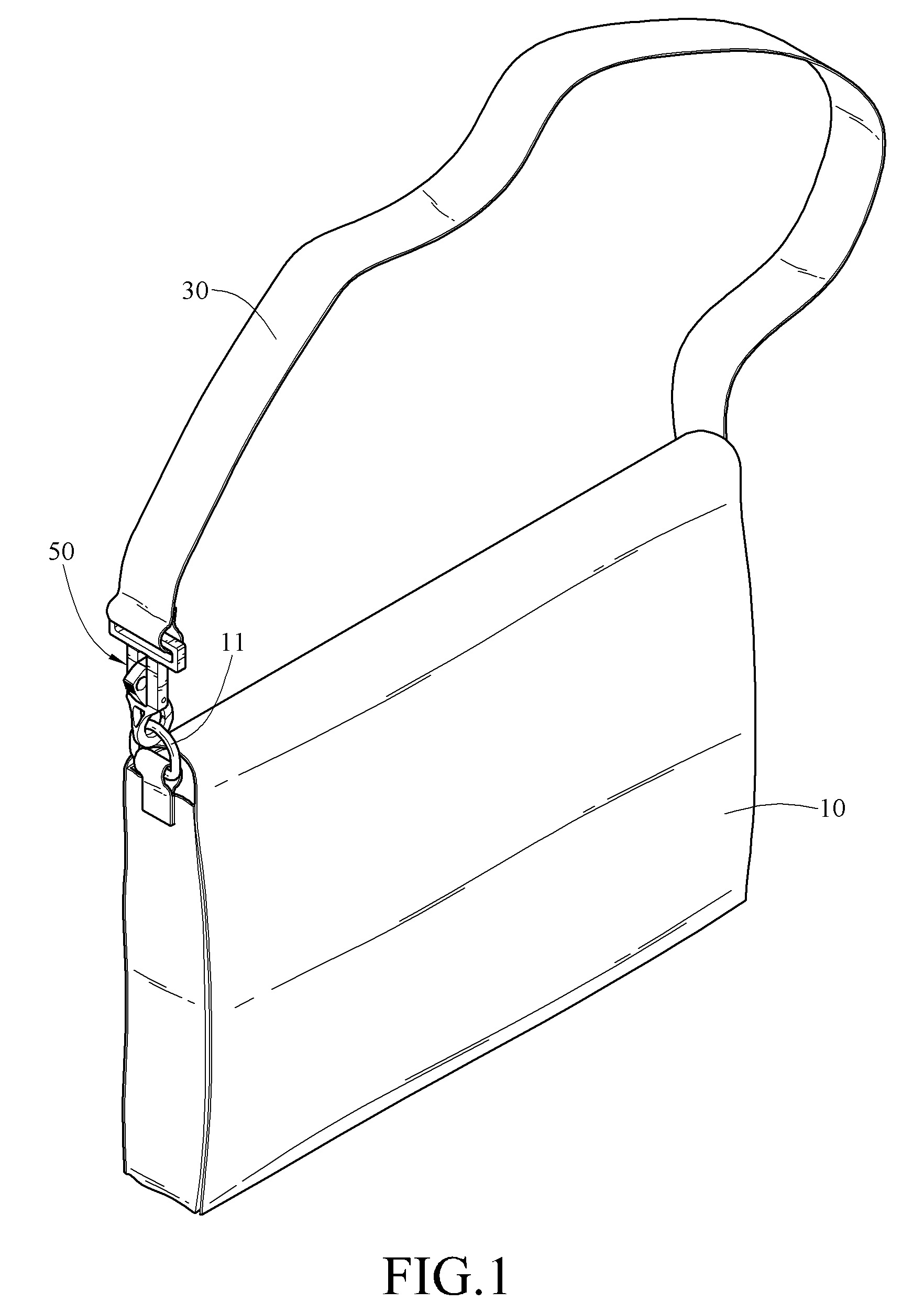
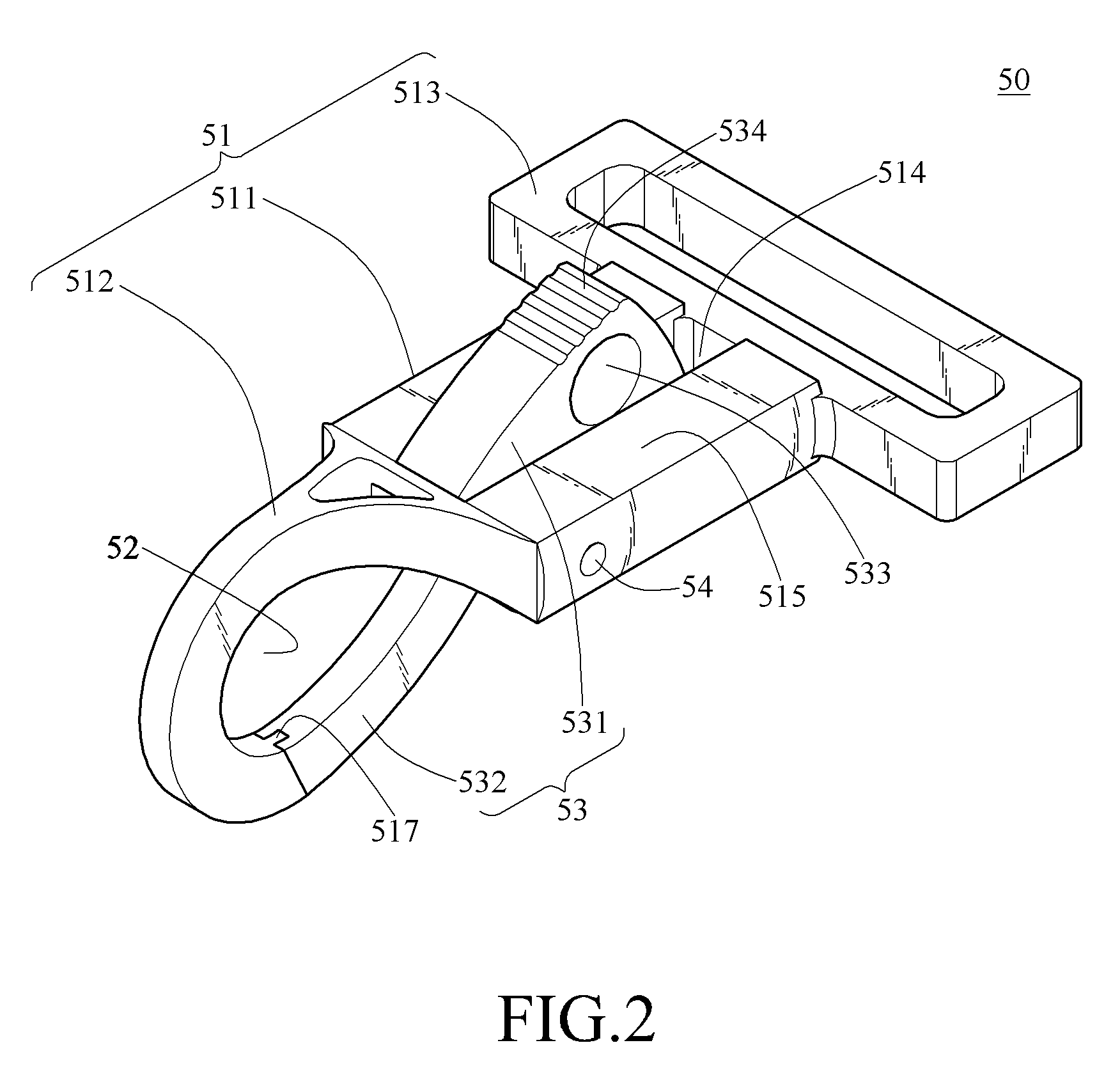
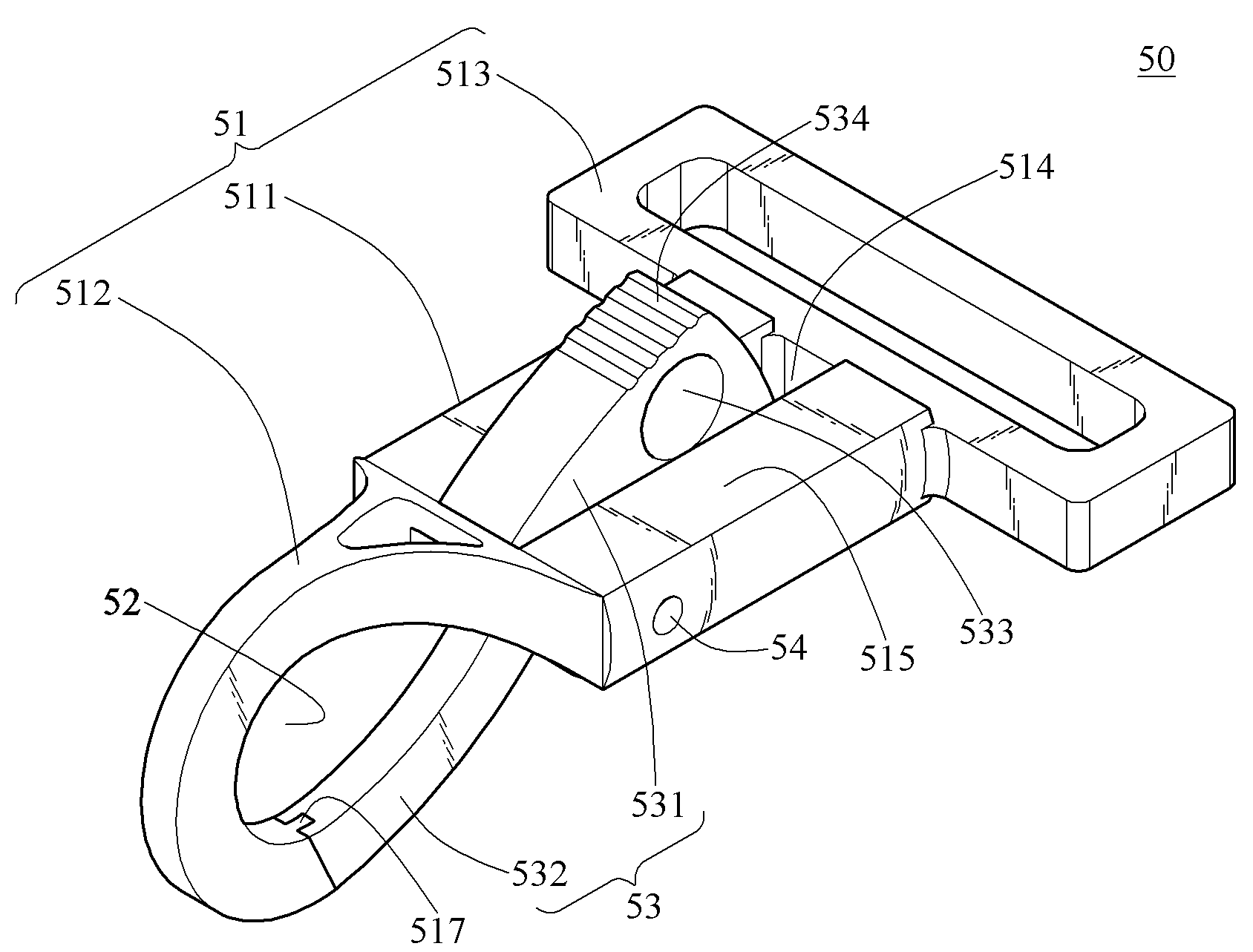
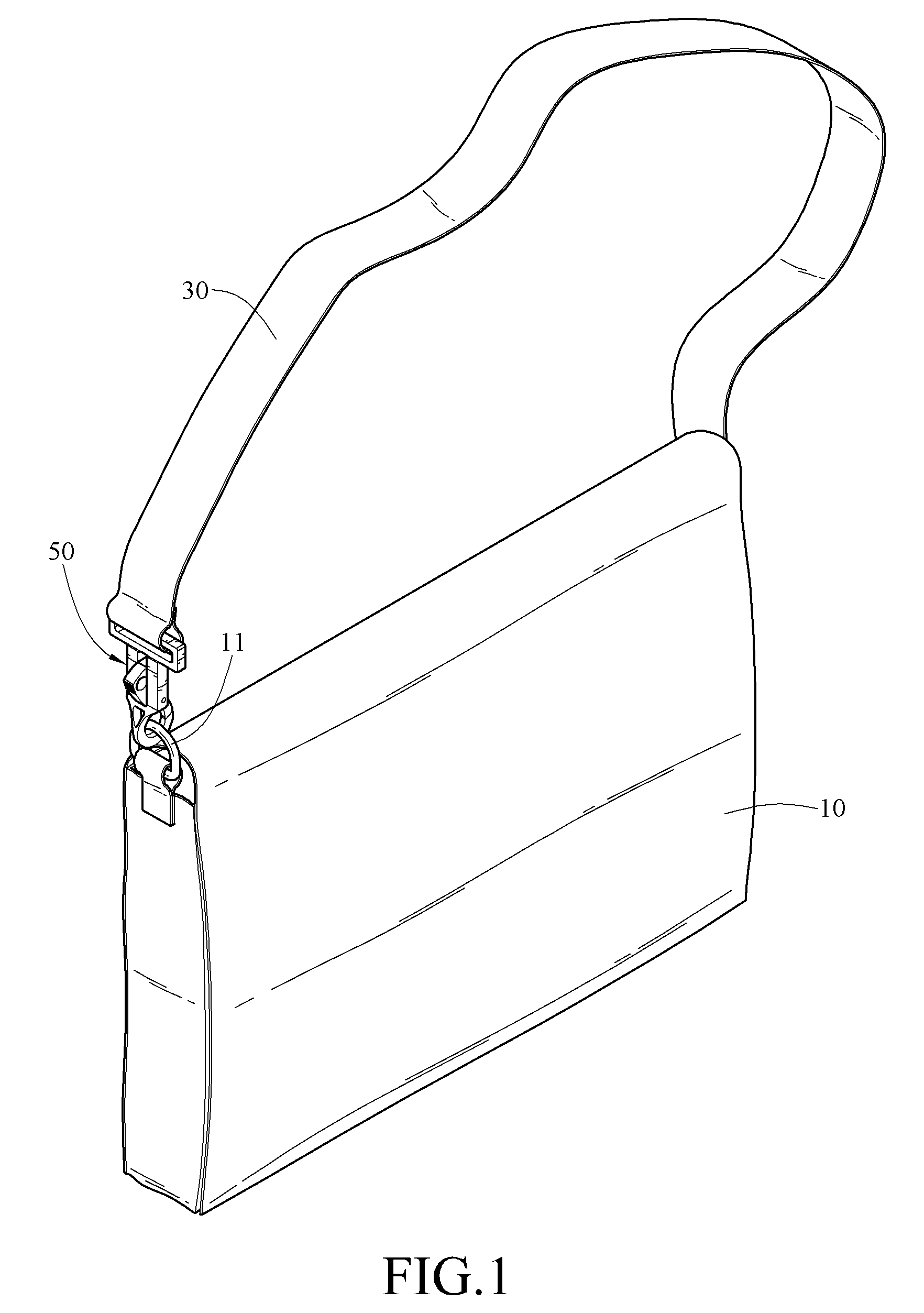
Shoulder strap assembly and snap hook structure thereof
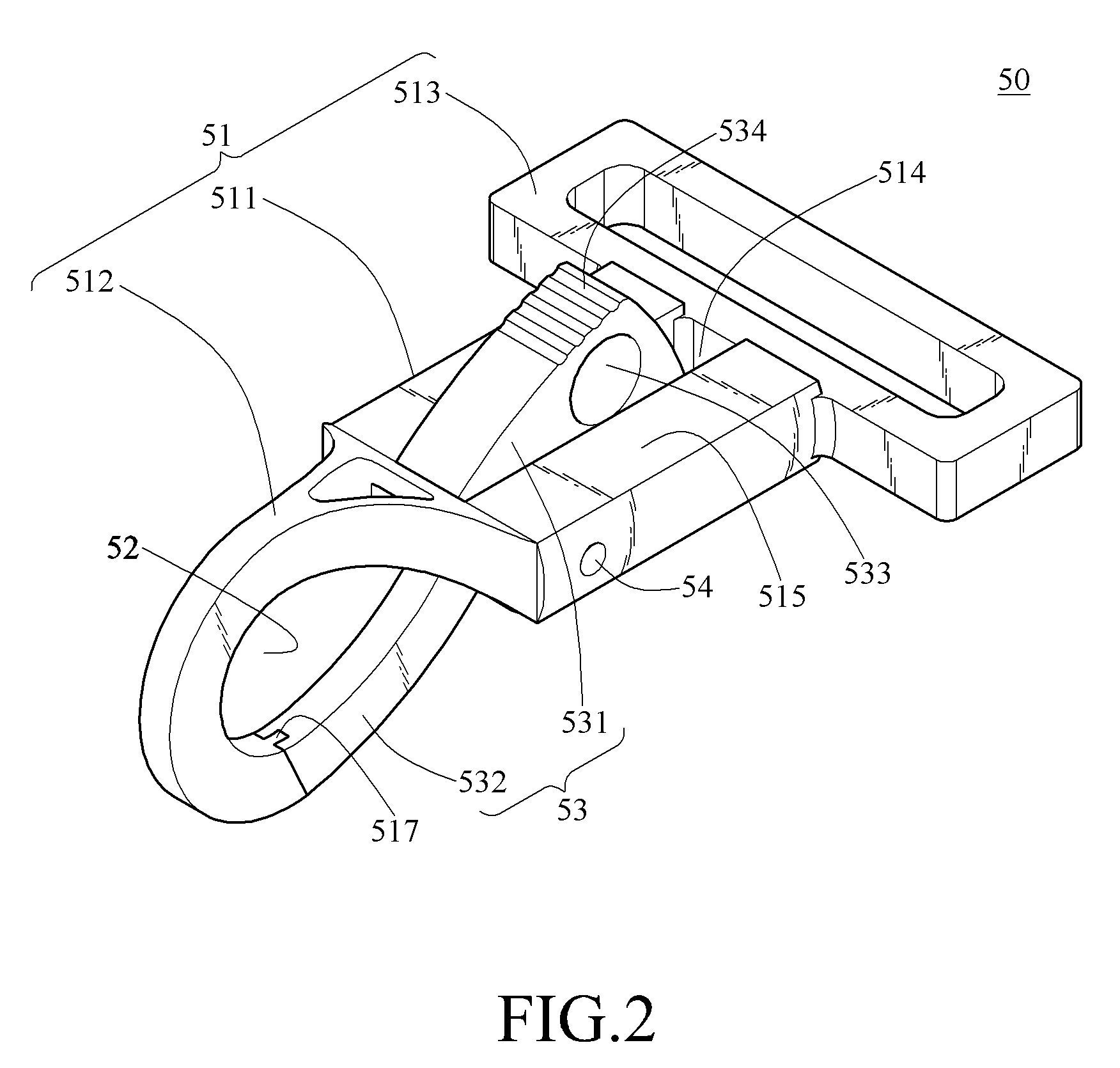
InactiveUS8234758B2Easy to be stolenAvoid separationSnap fastenersTravelling sacksEngineeringMechanical engineering
A shoulder strap assembly and a snap hook structure thereof are presented. A strap of the shoulder strap assembly is combined with a first article through the snap hook structure. The snap hook structure includes a main body and a keeper member. The main body hooks the first article, and the keeper member ensures the main body to keep hooking the first article. The keeper member has a perforation. The user can wind the strap around a second article, and use a lock to pass through the perforation so as to lock the first article with the second article, thereby preventing the first article from being stolen.
Owner:SINOX CO LTD
Shoulder strap assembly and snap hook structure thereof
InactiveUS20090193631A1Avoid separationEfficient mechanismSnap fastenersTravelling sacksMechanical engineeringMaterial Perforation
A shoulder strap assembly and a snap hook structure thereof are presented. A strap of the shoulder strap assembly is combined with a first article through the snap hook structure. The snap hook structure includes a main body and a keeper member. The main body hooks the first article, and the keeper member ensures the main body to keep hooking the first article. The keeper member has a perforation. The user can wind the strap around a second article, and use a lock to pass through the perforation so as to lock the first article with the second article, thereby preventing the first article from being stolen.
Owner:SINOX CO LTD
Method and apparatus for authenticating swipe biometric scanners
ActiveUS20120300992A1Improve security levelEasily stolenImage enhancementPrint image acquisitionUser authenticationFingerprint
Methods and apparatuses for authenticating a biometric scanner, such as swipe type finger print scanners, involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeit biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND BALTIMORE
Mobile handset security system
InactiveUS20090011796A1Easy to be stolenBroaden applicationUnauthorised/fraudulent call preventionSubstation speech amplifiersControl electronicsEngineering
A system and method if provided for controlling an electronic device, the system comprising means associated with a master electronic device for storing at least one identifier associated with a slave electronic capable of being linked to the master device and means for controlling the operation of one of the electronic devices in dependence on detection of the master device and at least one slave device being linked when operation of that device is to take place. The system is advantageously used for a mobile telephone handset security system.
Owner:NEC CORP
Intelligent handover storage equipment, system and method
InactiveCN105931388AIncrease brightnessImprove accuracyApparatus for meter-controlled dispensingSafesState variationIdentification device
The invention relates to intelligent handover storage equipment, system and method. The intelligent handover storage equipment comprises a handover teller machine provided with safe box doors, and electronic locks are arranged in the safe box doors and are opened through biological identification devices; bolts of the electronic locks are equipped with sensors I, state change signals are sent to a main unit when the electronic locks are opened or restored, and the main unit learns whether the locks of safe boxes are opened; sensors II are arranged on inner sides of door frames of the safe boxes, state change signals are sent to the main unit when the doors are opened or closed, and the main unit learns whether the safe box doors are opened; the safe boxes are arranged in the safe box doors. The intelligent handover storage equipment has higher biological identification safety by arranging the biological identification devices for faces, fingerprints, irises, palm veins and the like on the safe box doors.
Owner:邢德智 +1
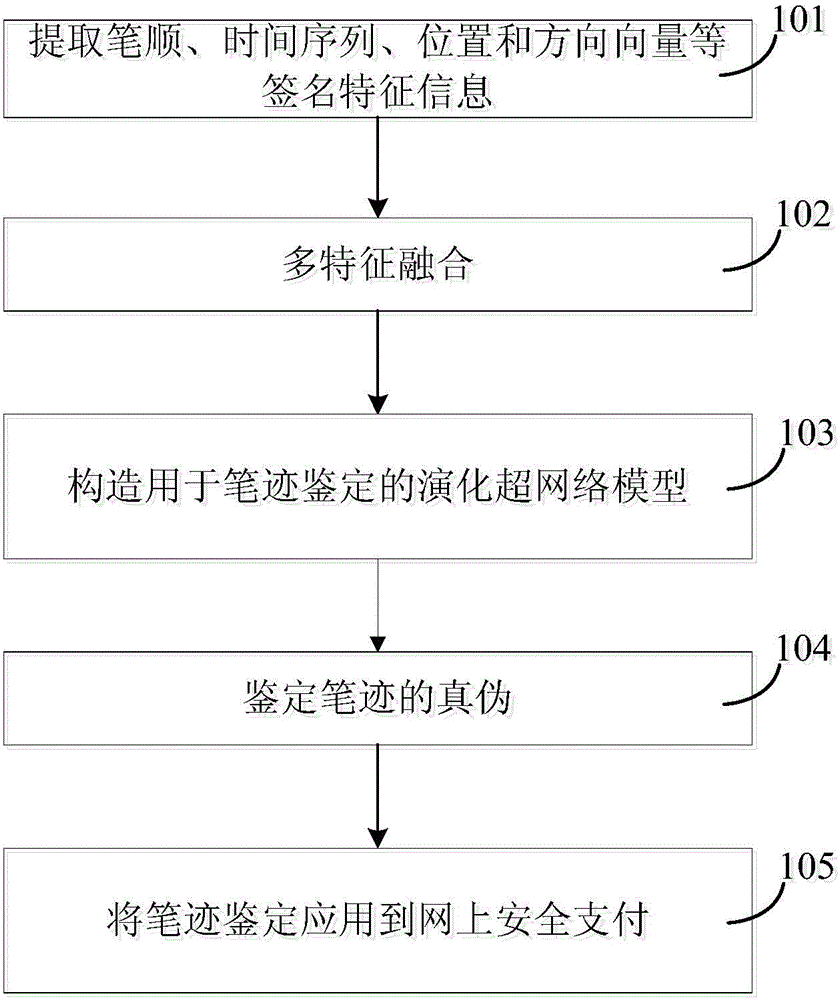
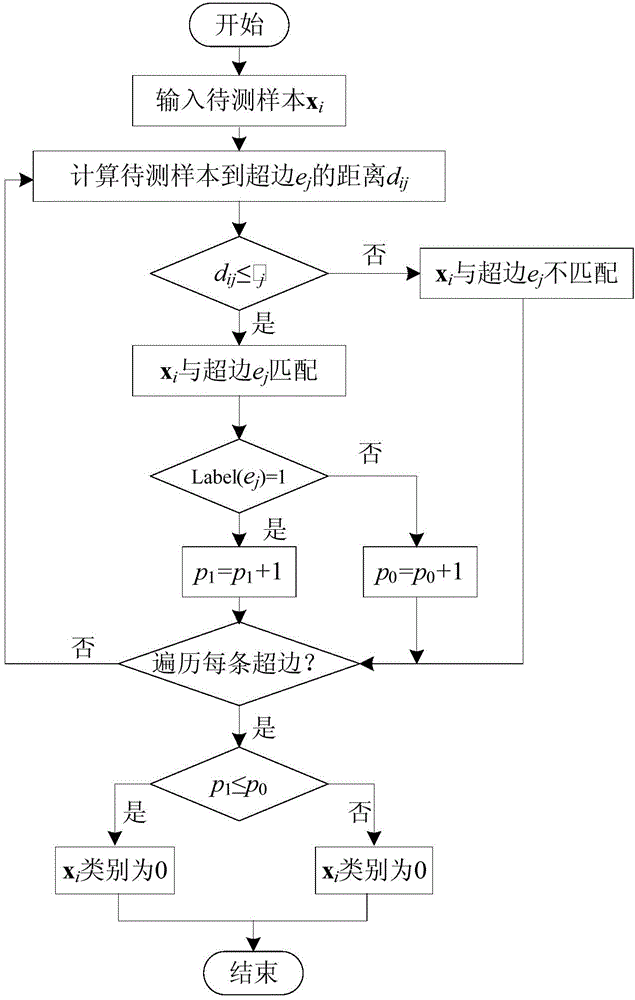
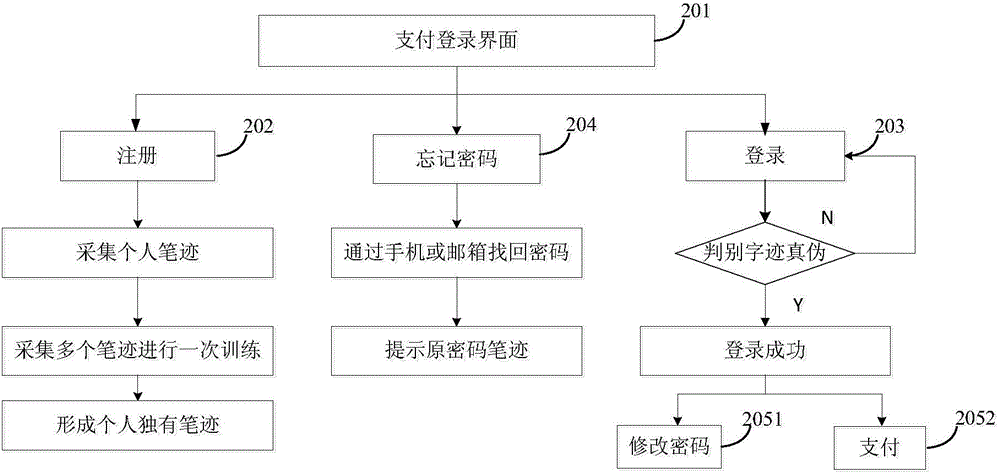
Online safe payment system based on handwriting authentication
ActiveCN104820924AImprove stabilityImprove recognition efficiencyPayment protocolsCharacter recognitionHandwritingOptimal weight
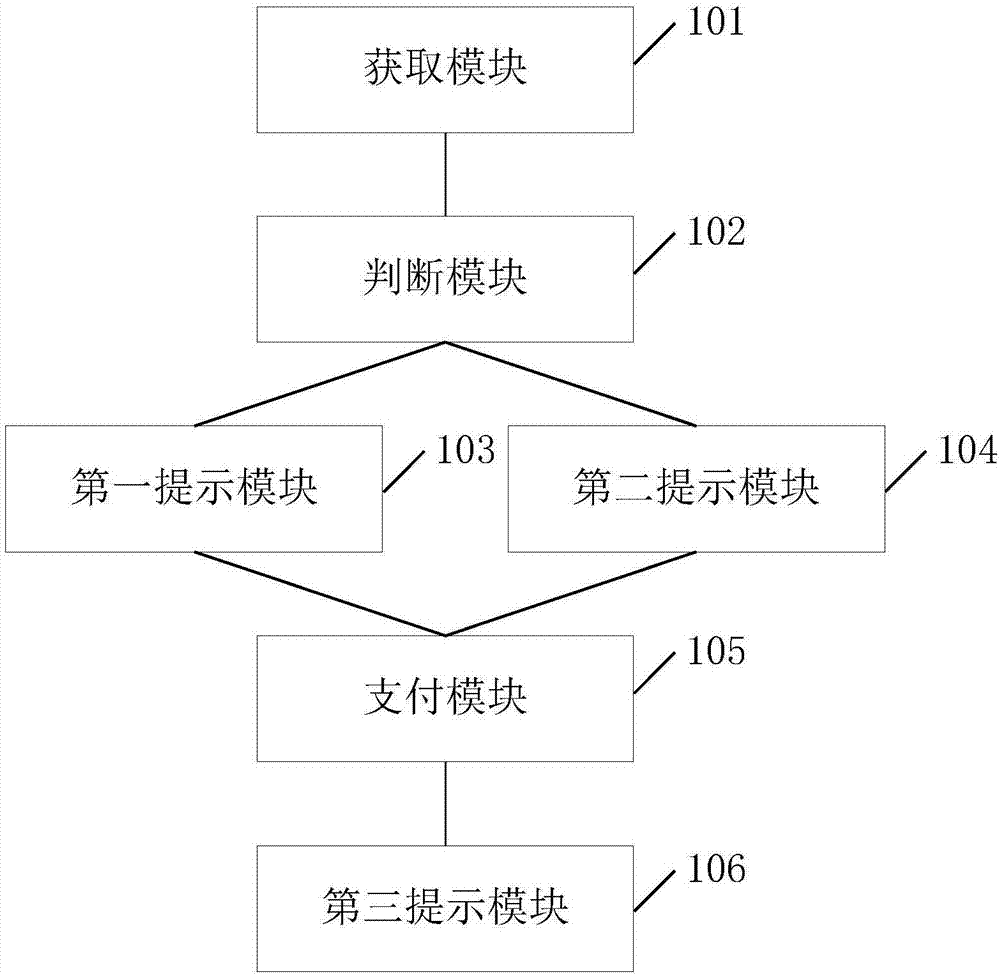
Provided is an online safe payment system based on handwriting authentication. The system comprises a 101 user registration module; a 102 reception module; a 103 learning and training module; a 104 authentication module, and a 105 payment module. The 102 reception module is used to receive any to-be-identified signature sample input by a user, perform multi-feature fusion to use various attribute characteristic values as the characteristic values of the sample, excavate contribution degree of each attribute characteristic value on correct identification of the signature, perform descending sort, and select a group of optimal weights according to contribution value rank ordering to fuse various characteristics. The 103 learning and training module converts the combined multi-feature set to data of 1 to 8, and the data is used as input based on a neighbourhood-hypernetwork sorter, so as to perform training and tests. A user inputs a signature, and the 104 authentication module compares a to-be-identified hyperedge with hyperedges in a hyperedge library to authenticate authenticity of user handwriting. The 105 payment module applies the handwriting authentication to online safe payment. The system has higher stability, security, and convenience. The system combines with a multi-feature fusion technology, and can improve identification efficiency and accuracy of signature samples.
Owner:CHONGQING AOXIONG INFORMATION TECH
Paperless Coupon Transactions System
PendingUS20110225045A1Easily fabricatedEasy to be stolenFinanceDigital data authenticationInternet privacyFinancial transaction
Owner:SONG YUH SHEN +3
Payment method, payment system, novel POS machine and payment core system
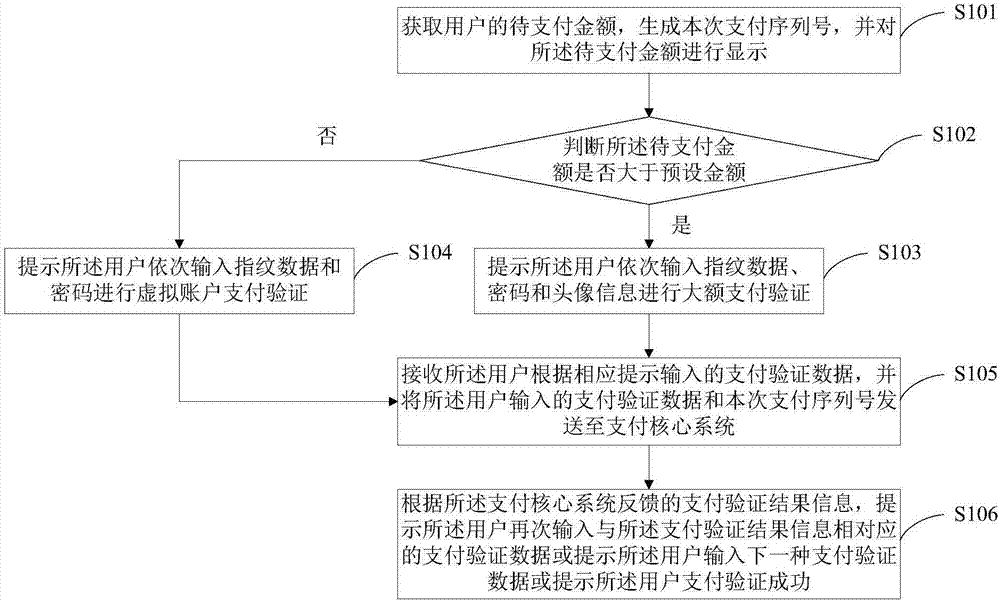
InactiveCN107274168AImprove payment experienceImprove securityPoint-of-sale network systemsProtocol authorisationUser inputPassword
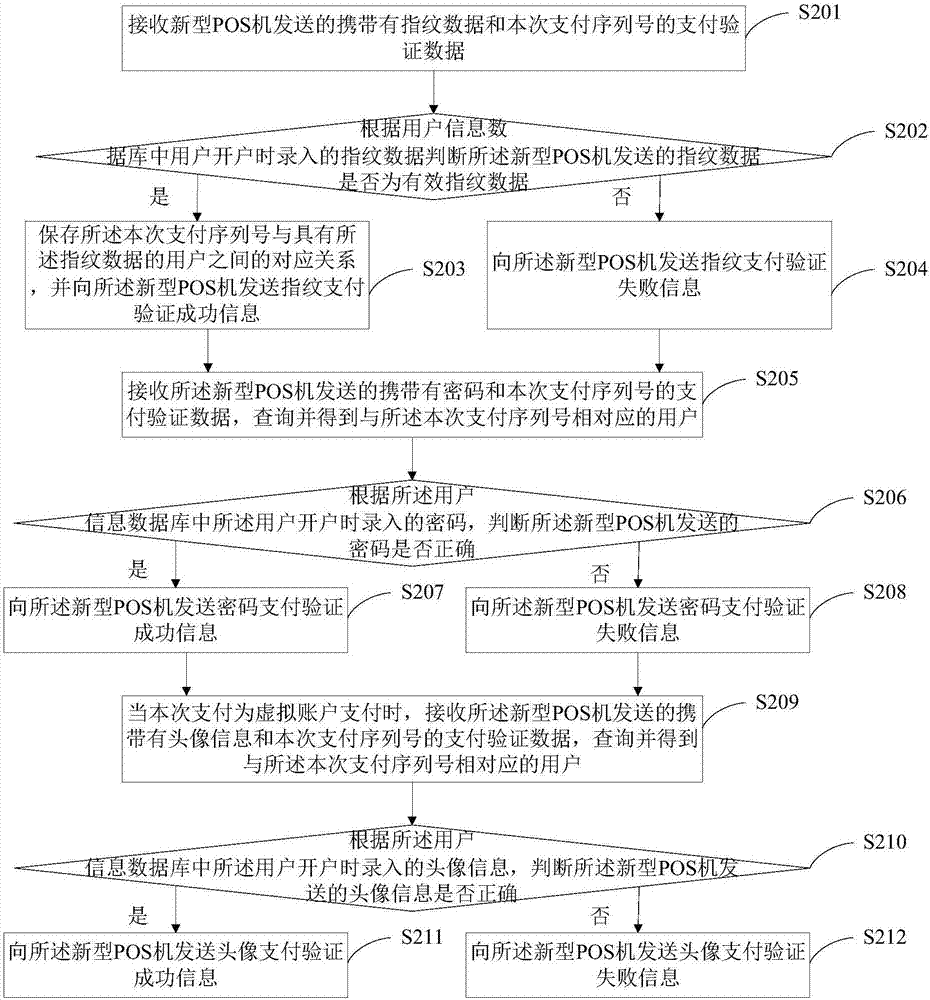
The invention provides a payment method and a payment system which support payment verification of a virtual account. According to the invention, a user does not need to carry an IC card, the user is prompted to adopt different payment verification modes according to the amount money to be paid, payment verification data inputted by the user and a serial number of the current payment are sent to a payment core system, and the payment core system is enabled to perform verification according to account opening information inputted by the user when the account is opened. For large-amount payment, the user is prompted to sequentially input fingerprint data, a password and head portrait information, and the payment security of the user is improved; and for small-amount virtual account payment verification, the user is prompted to sequentially input fingerprint data and a password, and small-amount fast payment is realized. The invention further discloses a novel POS machine which further provides a fingerprint input function and a picture taking function while supporting traditional password input, takes a picture for the user when the user performs payment so as to be used for large-amount payment verification or act as a payment record of virtual account payment verification, thereby being convenient for acting as unauthorized payment evidence when unauthorized payment occurs in a later period.
Owner:BANK OF CHINA
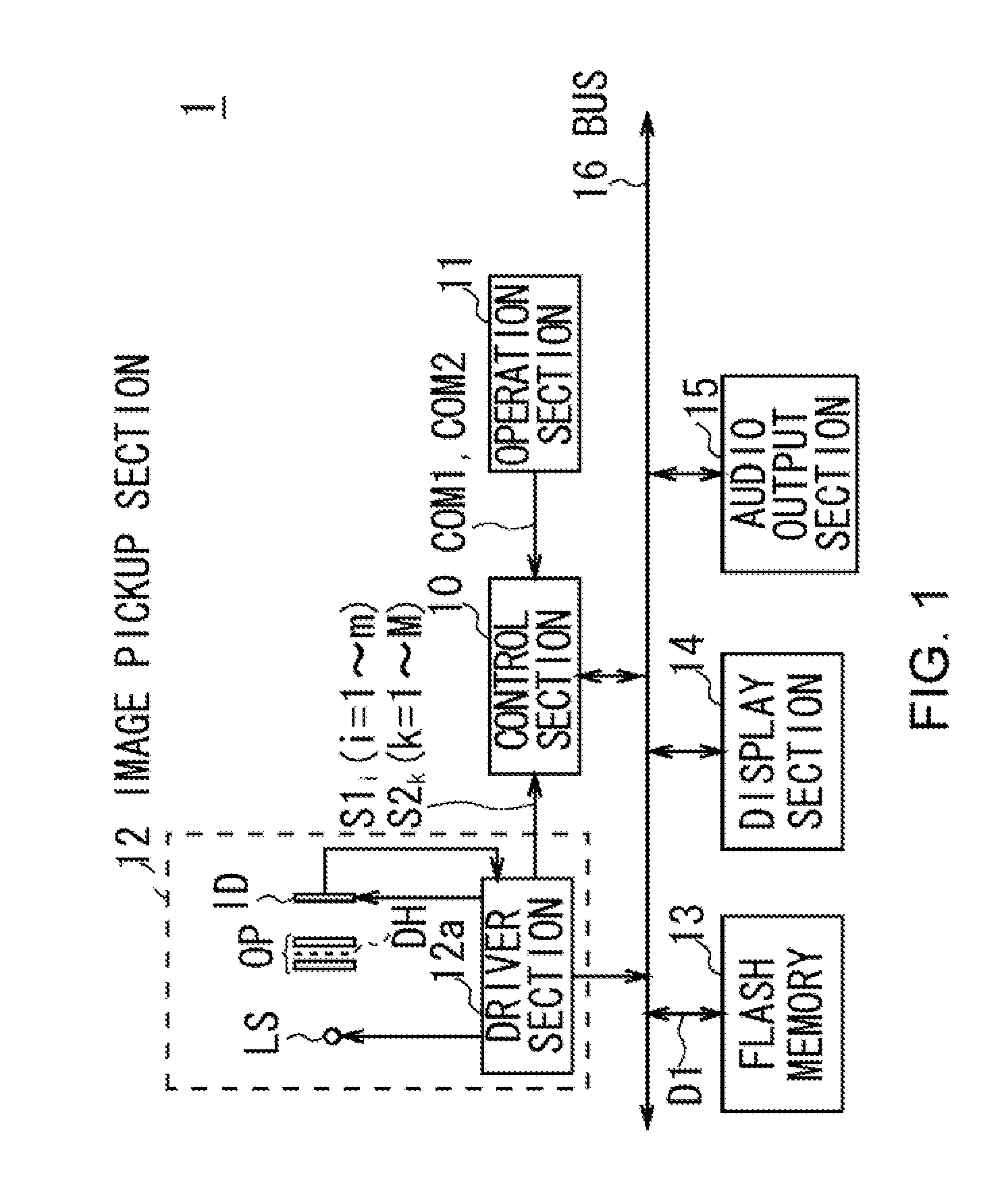
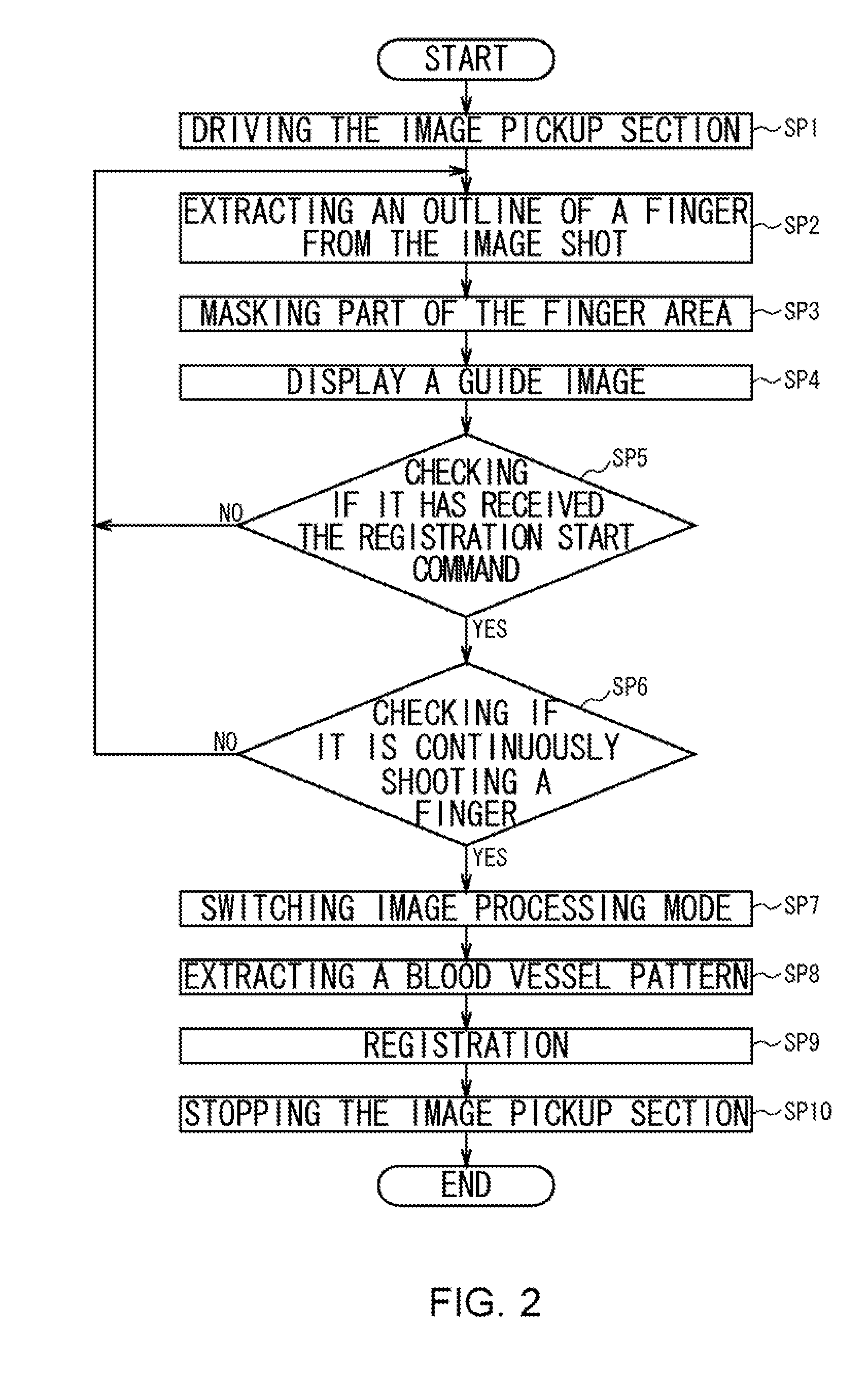
Registration Apparatus, Verification Apparatus, Registration Method, Verification Method and Program
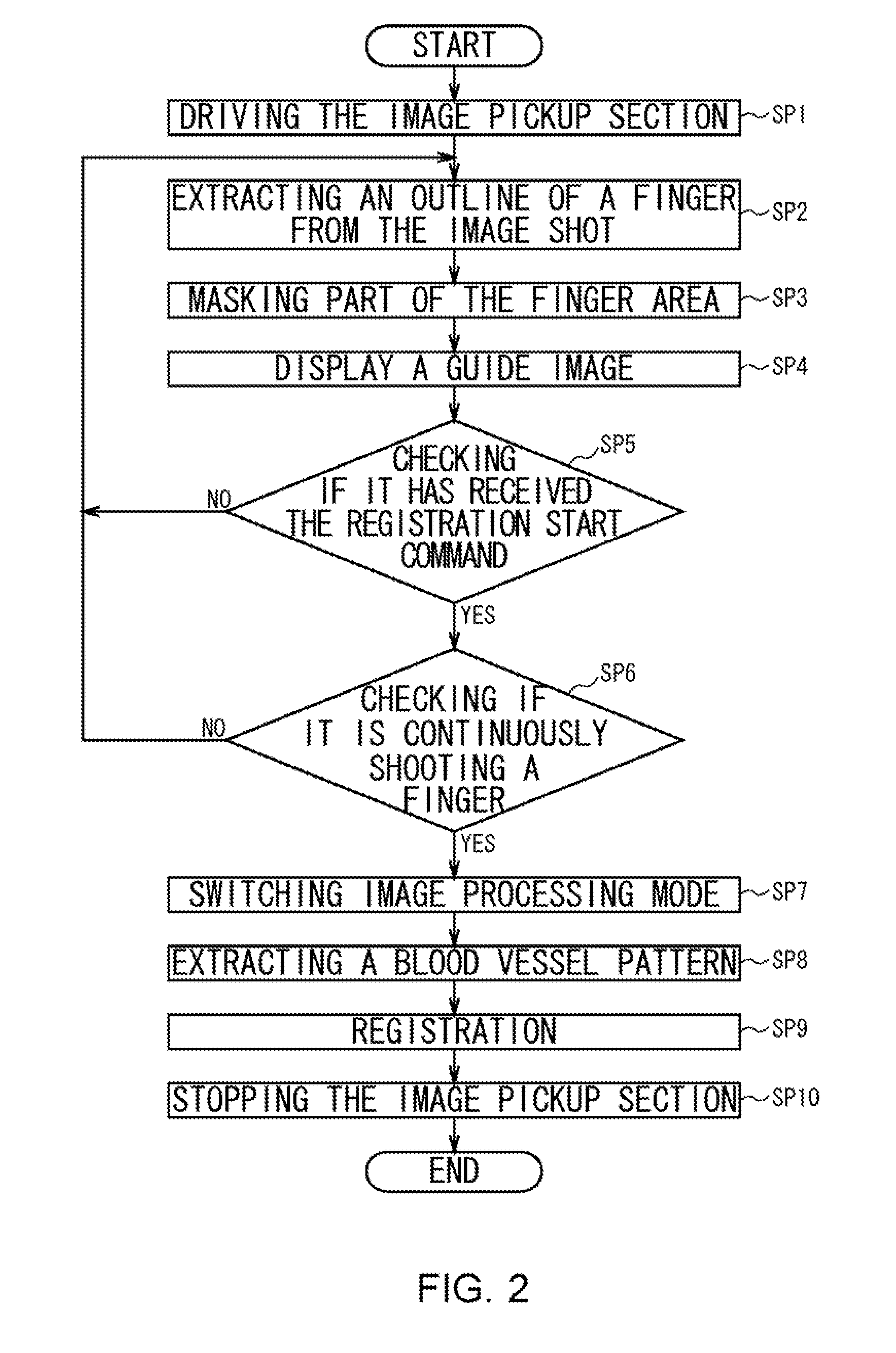
InactiveUS20080112597A1Easy to be stolenPrevent leakageSubcutaneous biometric featuresBlood vessel patternsValidation methodsComputer science
A registration apparatus includes: display control means for controlling display means to display a body part reflected on an image pickup surface and where the body part should be placed on the image pickup surface; driver means for driving a light source to emit light specific to a verification object inside the body part, the verification object being used for verification; extraction means for extracting a pattern of the verification object reflected on the image pickup surface as a result of emitting the light; and registration means for registering in storage means the pattern extracted by the extraction means.
Owner:SONY CORP
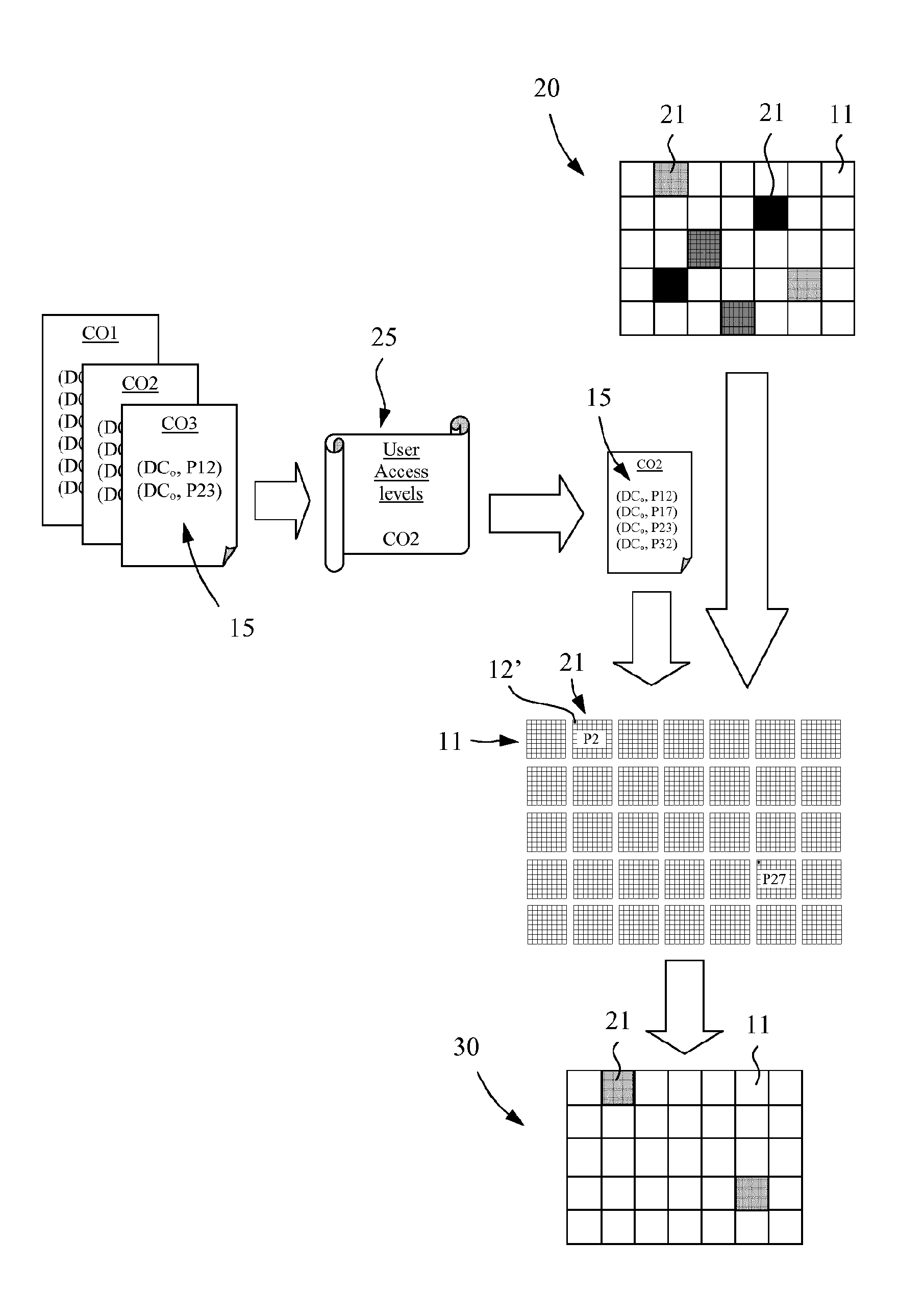
Method for controlling access to visual media in a social network
InactiveUS20130254843A1Avoid complicationsEasy to be stolenData processing applicationsDigital data processing detailsWeb siteVisual Objects
A method for controlling access to a visual medium in a social network comprising user units connected to a social network site server associated to a database and a to a distorted visual medium server storing visual media posted by users of the social network. A visual medium is selected by a posting user on a user unit and made available to at least one entitled user of said social network. The posting user defines a list of entitled users to be entitled to access the visual medium, said list of entitled users comprising at least one identifier identifying at least one entitled user, said identifier being associated to a parameter defining an access level to the selected visual medium. The selected visual medium is uploaded to the distorted visual medium server in association with the list of entitled users. The distorted visual medium server stores the visual medium in a memory and applies a distortion effect so as to obtain at least one distorted visual medium degraded according to a predefined degradation level. An entitled user iden tified on the list receives, from the distorted visual medium server, the visual medium distorted according to a degradation level corresponding to the parameter defining the access level associated to the identifier of the entitled user. The distortion effect applied on the original visual medium preferably consists of a scrambling operation performed on the original visual medium to obtain a scrambled visual medium. The access level defines the rights of a user for descrambling the scrambled visual medium into a reconstructed visual medium. Depending on the user access level, the reconstructed visual medium can be a partially descrambled visual medium or a fully descrambled visual medium according to the user access level.
Owner:PRIVATELY
Locked Asset Rental System
ActiveUS20170337622A1Facilitates commercial rentalImmune to theftReservationsApparatus for meter-controlled dispensingTablet computerEngineering
The invention is a system allowing for the commercial rental of physical assets that are locked and secured at specific locations, including, without limitation, bicycles, motorcycles, automobiles, tools, machines, computers, smart phones, or tablet computers.
Owner:DENAIS VINCE +1
Digital card device and method
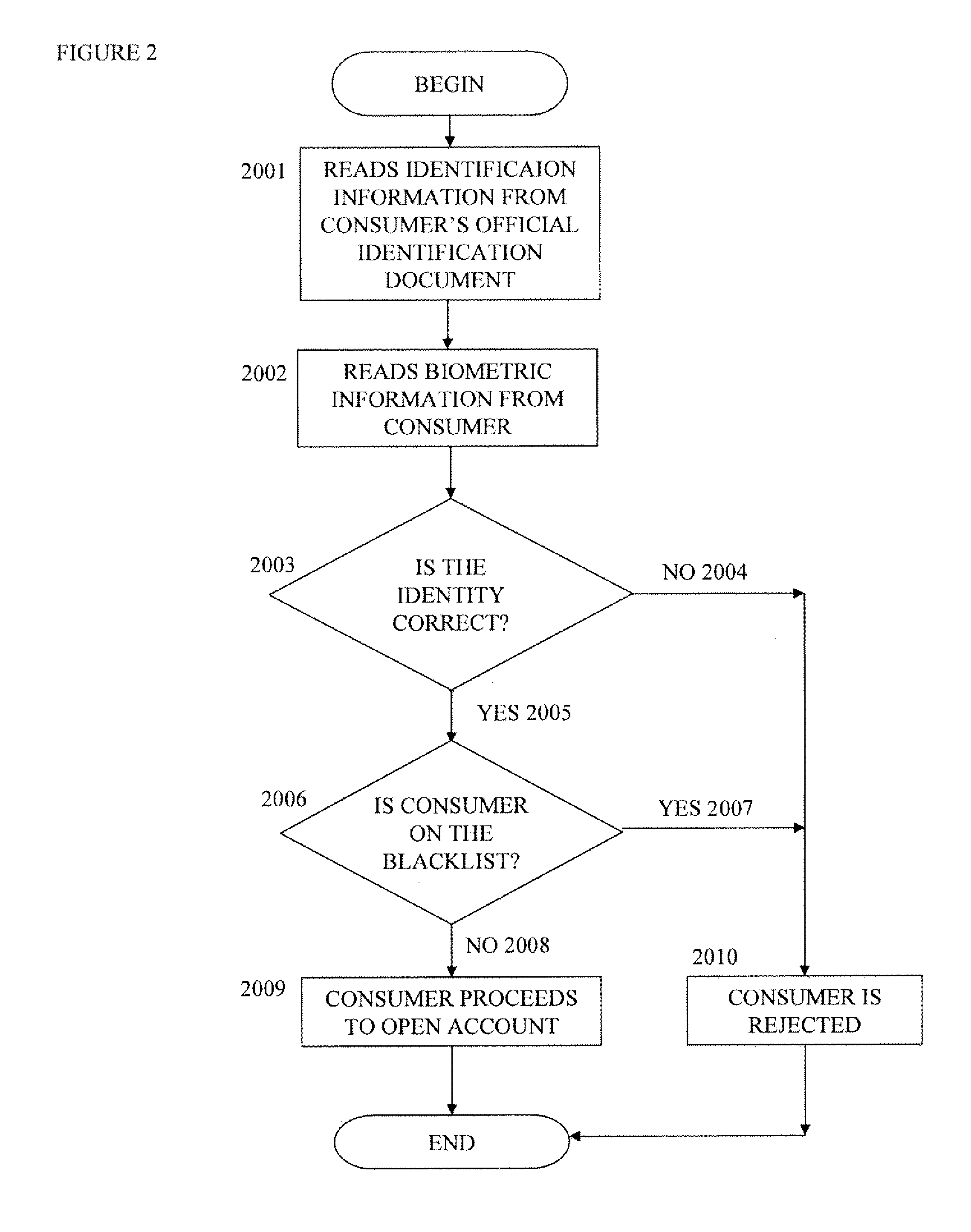
InactiveUS20140122267A1Easy to loseEasy to be stolenFinancePayment architectureComputer hardwareMobile device
A mobile device configured to replace physical card(s) of a user, the mobile device being capable of performing a process including in any order the steps of: receiving from the card issuer card data necessary for performing cardless transactions; storing the card data; receiving from the user instructions for initiating a cardless transaction; authenticating the user before the cardless transaction is initiated; and, initiating the cardless transaction by transmitting the card data to a card data reader.
Owner:TAYEBI RAY
Identification device for multilayer tubular structures
ActiveUS7038587B2Less likely can be seen and possibly removedSafe breakageContainer decorationsLevel indicationsIdentification deviceRadio frequency
A multilayer tubular structure for products with an identification device being embedded or interposed between two of the multiple layers of the tubular structure. The identification device is responsive to radio frequencies and is able to store and transmit information about the multilayer tubular structure, the products, and processes that have been performed on same. A method is provided for manufacturing a multilayer tubular structure by embedding a radio frequency identification device between two of the multiple layers.
Owner:SONOCO DEV INC
Method and apparatus for authenticating area biometric scanners
ActiveUS8942430B2Improve securityAvoid attackImage enhancementPrint image acquisitionImaging processingUser authentication
Owner:UNIV OF MARYLAND BALTIMORE
Locked Asset Rental System
InactiveUS20160055575A1Facilitates commercial rentalImmune to theftApparatus for meter-controlled dispensingBuying/selling/leasing transactionsTablet computerEngineering
The present invention relates to a system for the commercial rental of physical assets locked and secured at a specific location, including, without limitation, of bicycles, motorcycles, automobiles, tools, machines, computers, smart phones, or tablet computers.
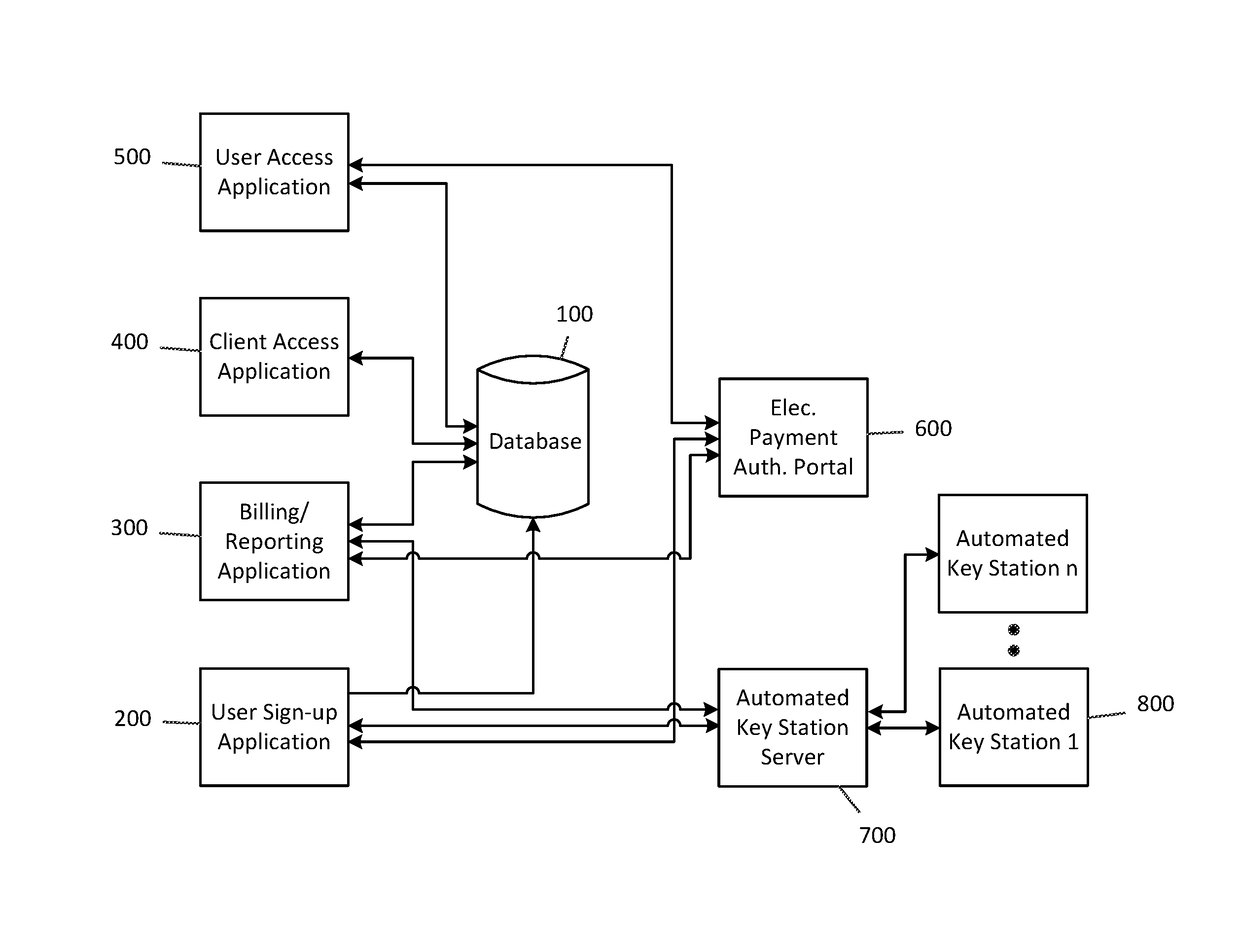
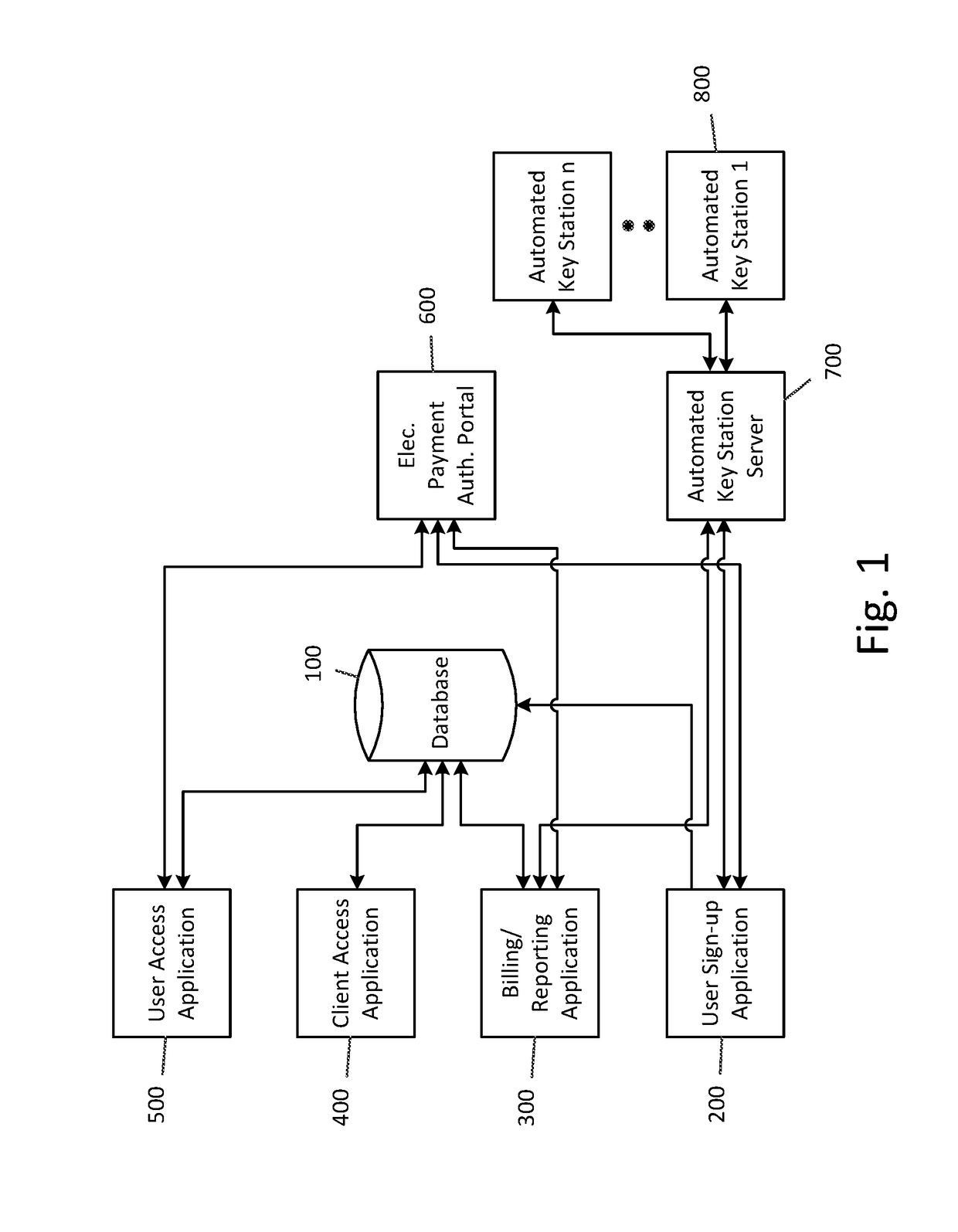
Owner:DENAIS VINCE +1
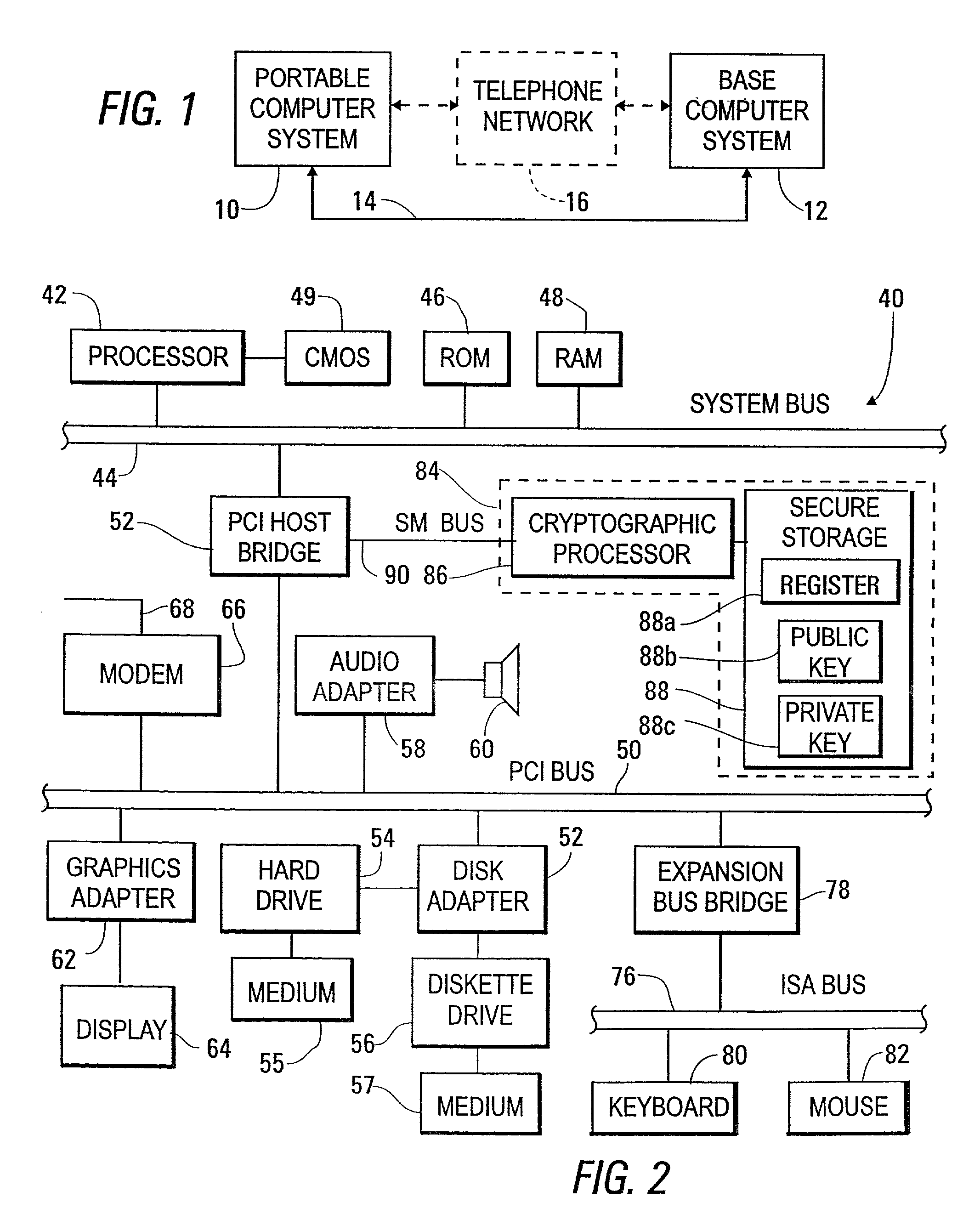
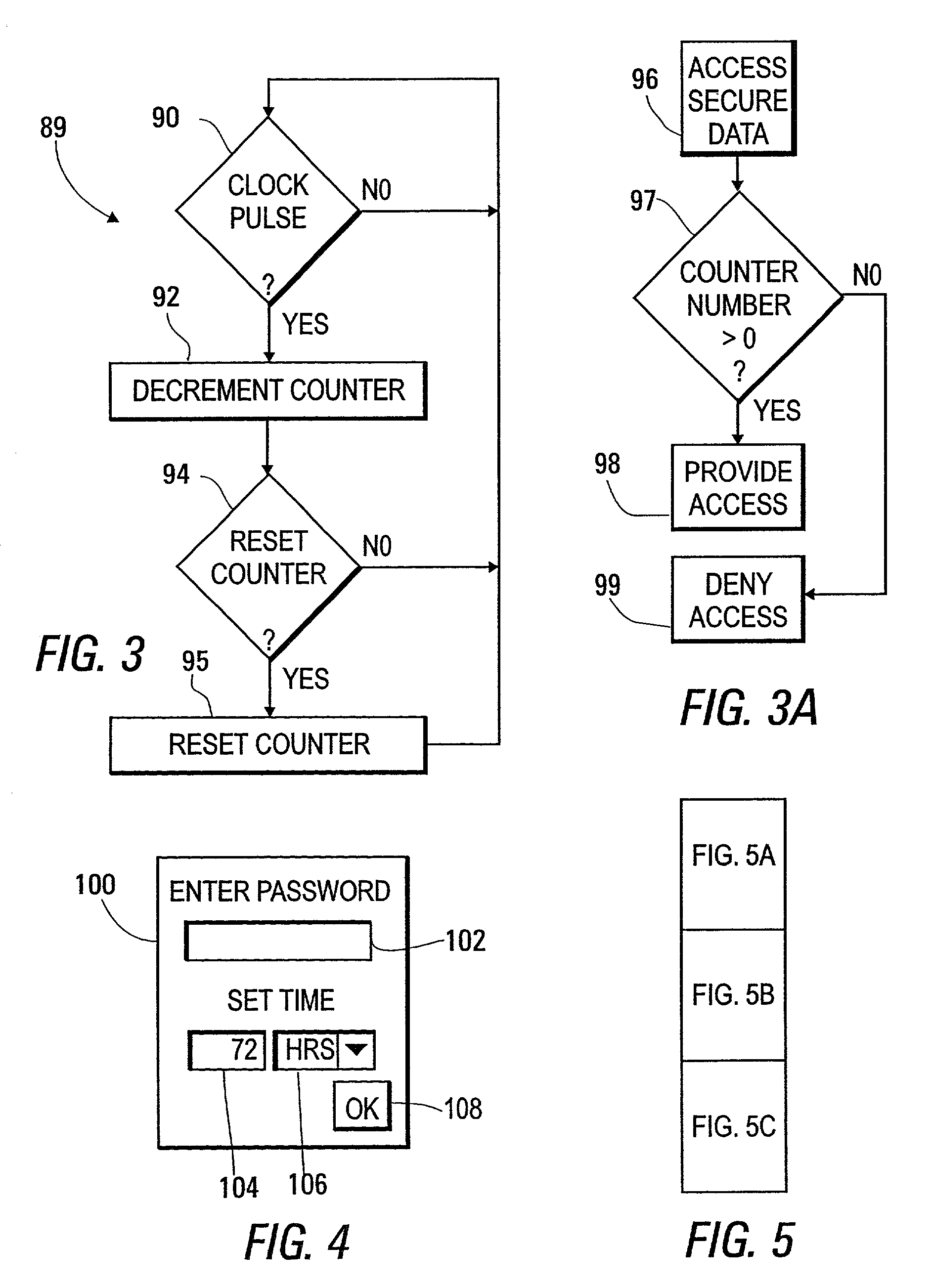
System and apparatus for limiting access to secure data through a portable computer to a time set with the portable computer connected to a base computer
ActiveUS7389536B2Light weightSmall sizeMemory loss protectionError detection/correctionPasswordSecret code
Access to secure data through a portable computing system is provided only when a timer within the system is running. The timer is reset with the portable system connected to a base system, either directly, as by a cable, or indirectly, as through a telephone network. In an initialization process, the portable and base systems exchange data, such as public cryptographic keys, which are later used to confirm that the portable system is connected to the same base system. In one embodiment, the initialization process also includes storing a password transmitted from the portable system within the base system, with this password later being required within the reset process.
Owner:LENOVO PC INT
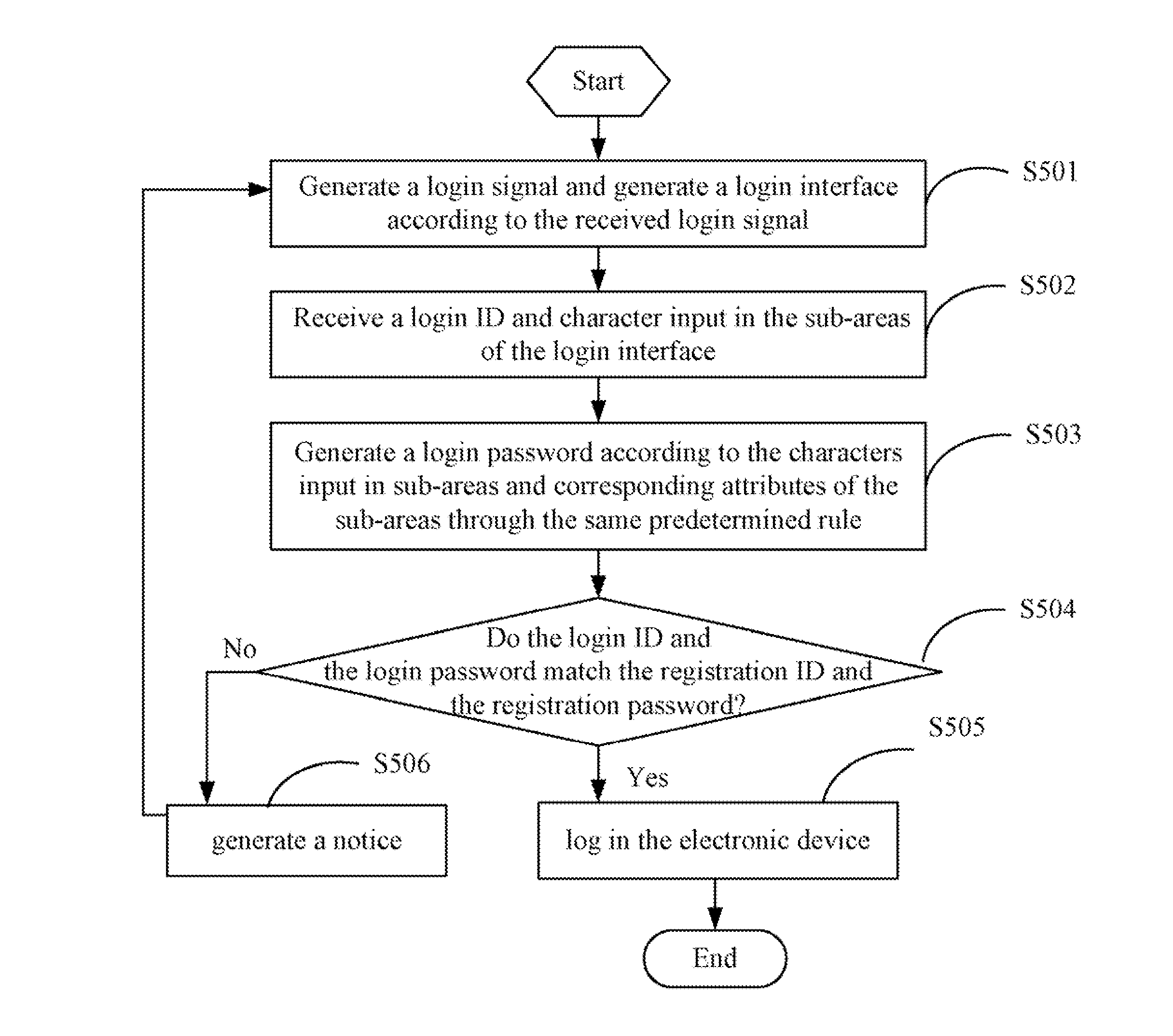
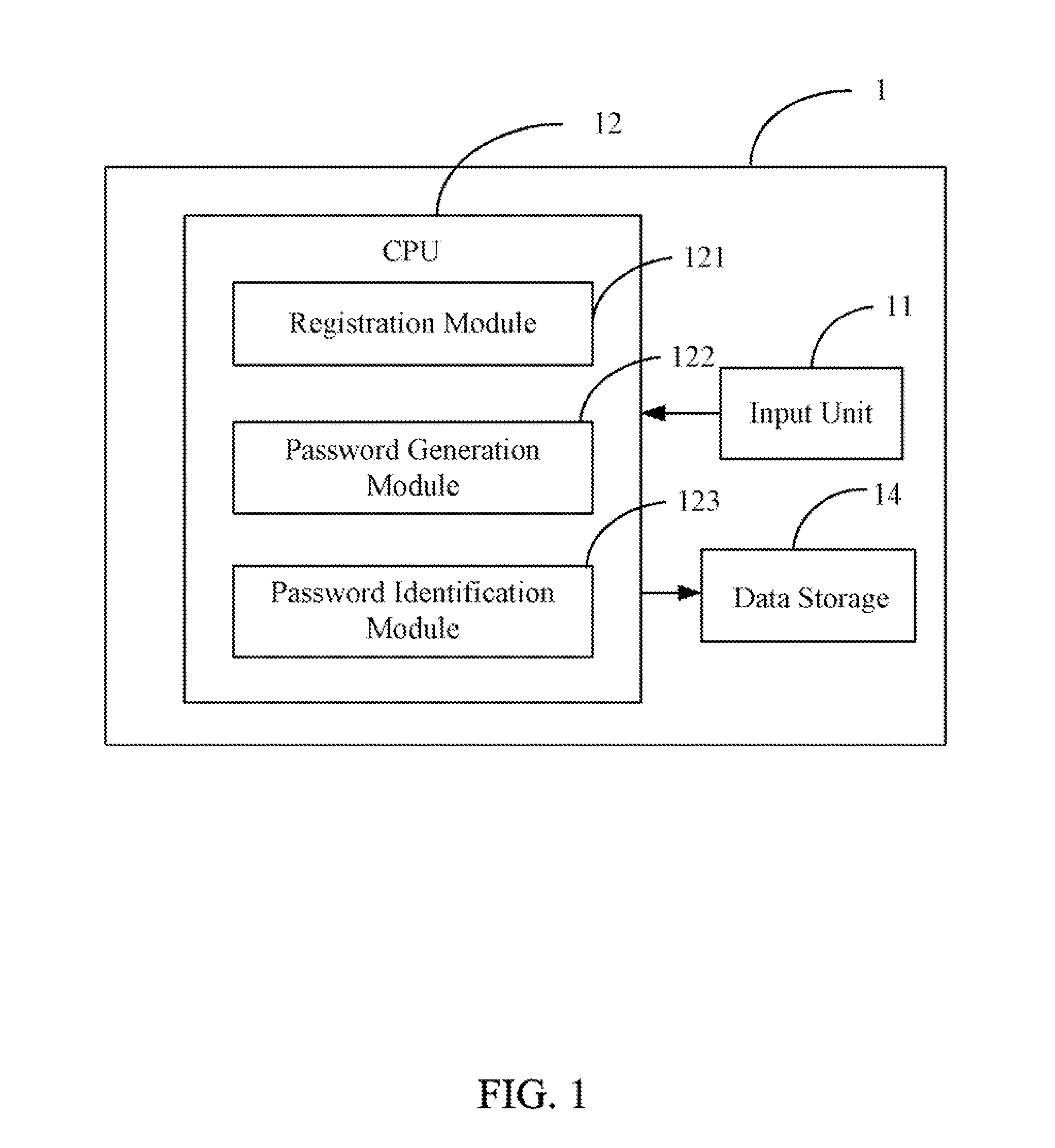
Electronic device with password protection function and method thereof
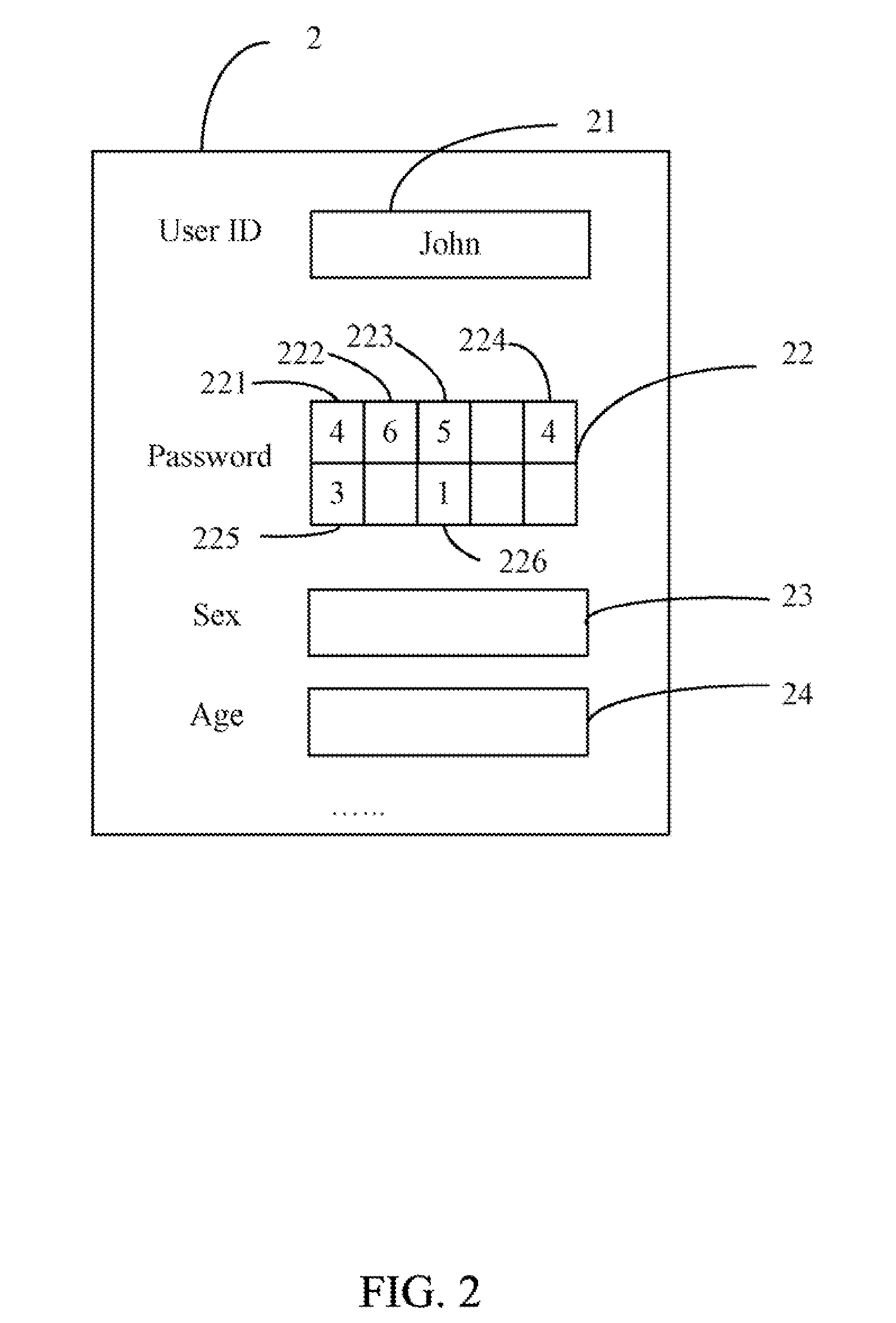
InactiveUS20110154483A1Easy to be stolenMake up for information lossDigital data processing detailsUser identity/authority verificationPasswordElectronic equipment
An electronic device with a password protection function is provided. The electronic device provides a password input area, which includes a number of sub-areas. Each of the sub-areas is designated a distinctive attribute, and is provided for inputting a single character. The characters and the attributes of the sub-areas are used to generate a login password according to a predetermined rule, thus the security of the login password is strengthened.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Automatic authentication method, apparatus and system of wireless local area network (WLAN)
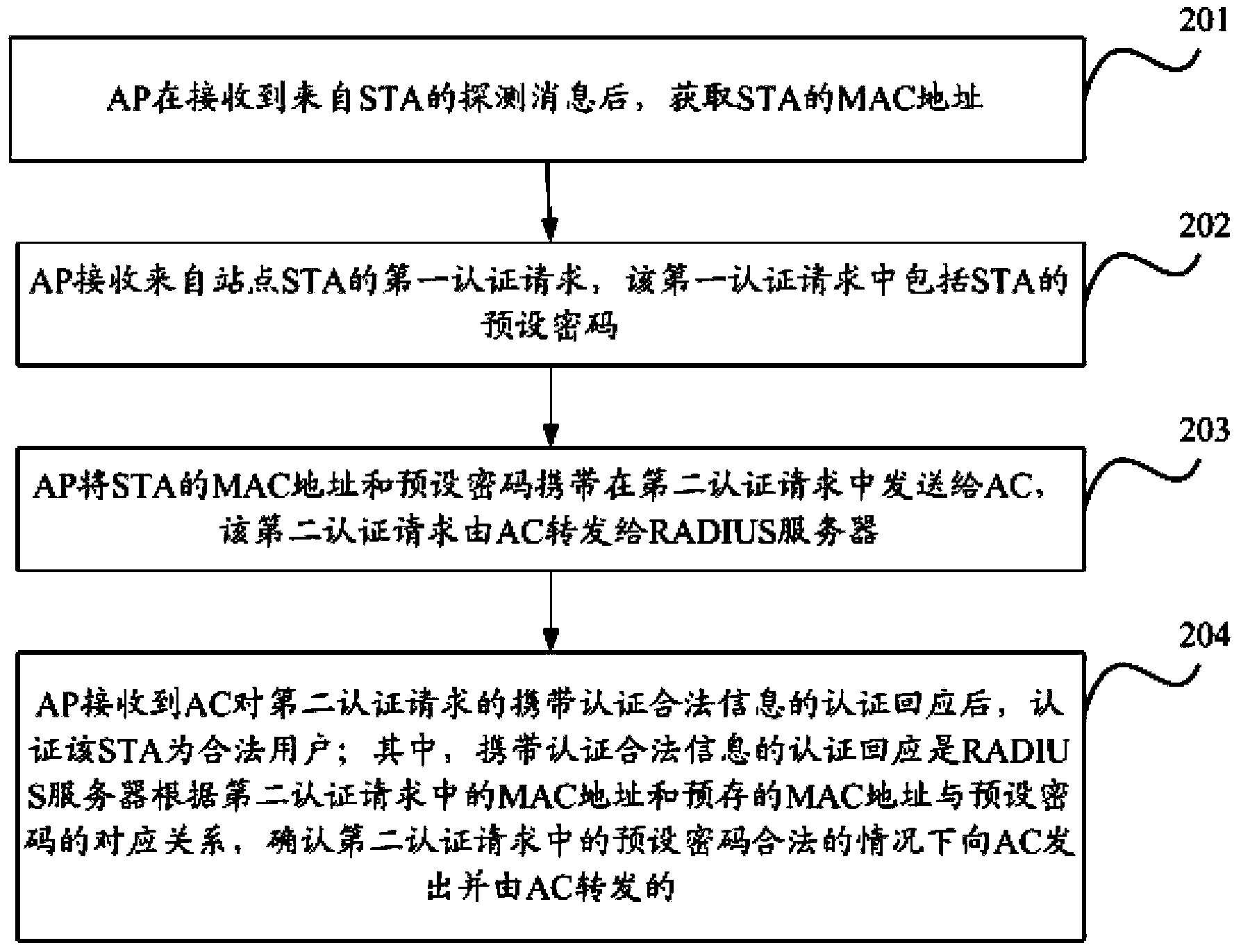
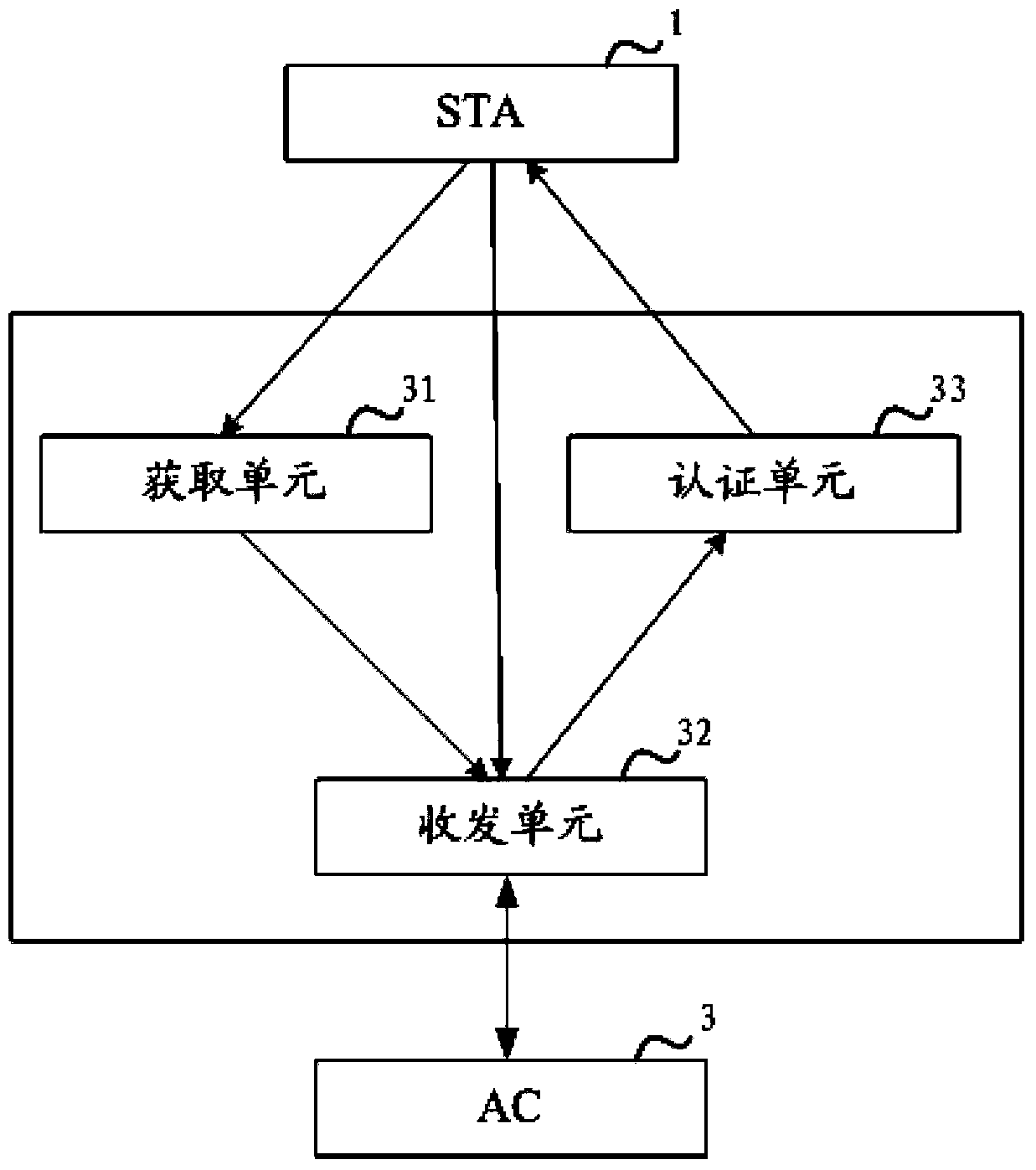
ActiveCN104349318AEasy to be stolenReduce the risk of obtaining preset passwordsNetwork topologiesTransmissionPasswordMAC address
The invention discloses an automatic authentication method, apparatus and system of a wireless local area network (WLAN), for solving the problem of illegal registration due to easy stealing of authentication information by use of a conventional WLAN automatic authentication technical scheme. According to the method, an AP obtains the MAC address of an STA and carries a second authentication request carrying the MAC address and a password from a first authentication request of the STA to an AC, the AC forwards the second authentication request to an RADIUS server, under the condition that the RADIUS server confirms that a corresponding relation between the MAC address in the second authentication request and a preset password exists in a corresponding relation between a prestored MAC address and the preset password, it is determined that the preset password in the second authentication request is valid, an authentication response carrying authentication validity information is sent to the AP through the AC, and the AP authenticates that the STA is an illegal user in case that the authentication response carrying the authentication validity information is received.
Owner:CHINA MOBILE GROUP SHANDONG
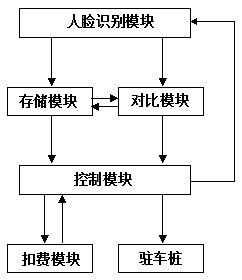
Non-motor vehicle parking and fetching system based on human face identification
InactiveCN105469505ASolve disorderly parkingEasy to be stolenApparatus for meter-controlled dispensingMotor vehicle partComputer module
The invention discloses a non-motor vehicle parking and fetching system based on human face identification. During non-motor vehicle parking, a human face identification module collects human face information and storing the information to a storage module; a control module controls a parking pile to open; after a user parks the non-motor vehicle and confirms the state, the control module controls the parking pile to close; a charging module starts to charge according to time; during non-motor vehicle fetching, the control module gives a signal collection order to the human face identification module; the human face identification module collects human face information and transmits the information to a comparison module; the comparison module and the storage module conduct information matching and then send the matching result to the control module; if the information is matched, the charging module displays charge fares and charges; and after the user pay the charge, the control module controls the parking pile to open and non-motor vehicle parking and fetching service is finished. Each system operates independently and a server is unnecessary, so low cost is required and safe and convenient vehicle parking and fetching service can be provided for non-motor vehicles of a user; and problems of casual parking and loss of non-motor vehicle can be solved.
Owner:童领
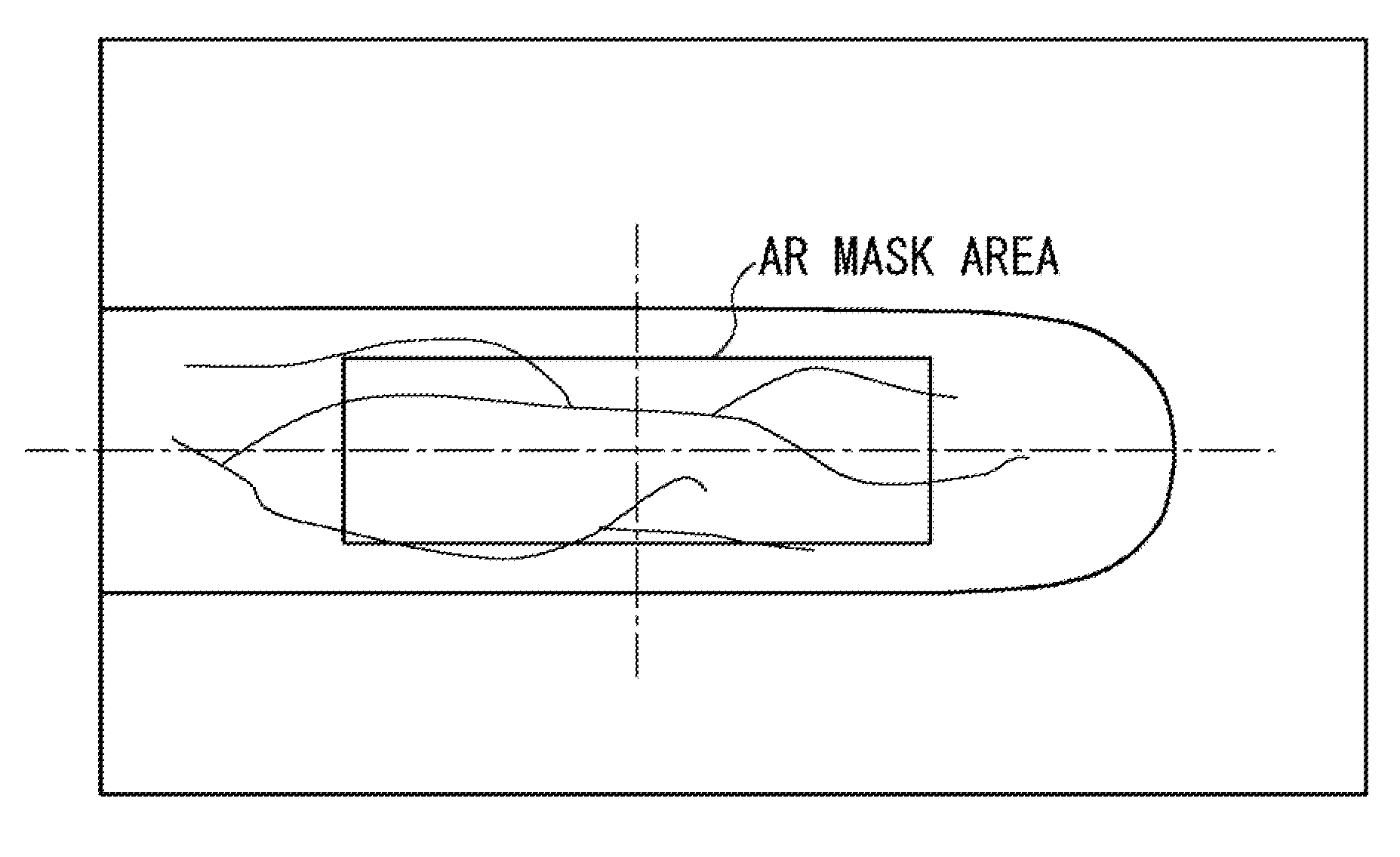
Registration Apparatus, Verification Apparatus, Registration Method, Verification Method and Program
ActiveUS20080112645A1Easy to be stolenPrevent leakageSubcutaneous biometric featuresBlood vessel patternsValidation methodsBody region
A registration apparatus includes: concealing means for concealing a part or whole of a verification area of an image generated by shooting a body part, the verification area being used for verification; production means for producing data for registration, the data representing a part or whole of a pattern of the verification area; display control means for controlling display means to display an image in which a part or whole of the verification area is concealed; and output switching means for outputting the image to the display control means or the production means.
Owner:SONY CORP
Anti-theft anti-shielding alarm system for power tower
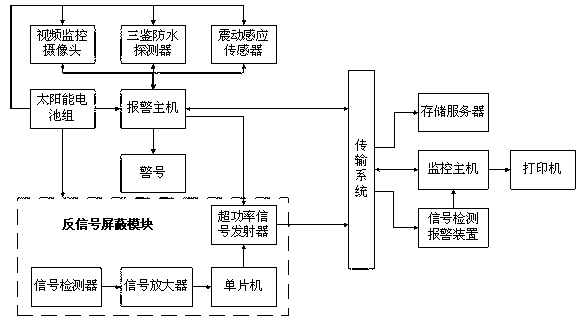
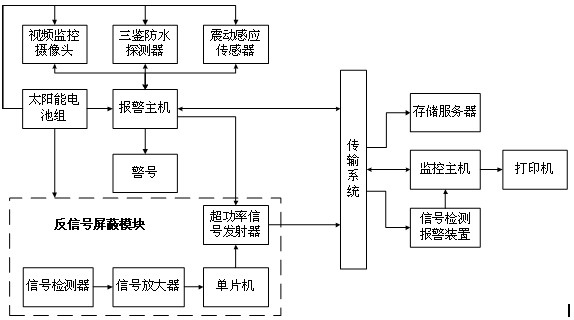
InactiveCN102708636AKeep the evidenceImprove stability and securityBurglar alarmMicrocontrollerVideo monitoring
The invention discloses an anti-theft anti-shielding alarm system for a power tower, which comprises an alarm host, a solar battery pack, a three-technology waterproof detector, a video monitoring camera, an alarm signal, a transmission system, a monitoring host, a storage server and a printer, wherein a shock sensor is installed at the tower foot, the front end also comprises an inverted signal shielding module, the inverted signal shielding module comprises a singlechip, a signal amplifier, a signal detector and a superpower signal transmitter, a signal detection and alarm device is installed at the monitoring center and can give alarm information if no signal is received within set time, and the transmission system adopts the transmission mode of combining wireless 3G network transmission and GSM transmission. In the invention, the inverted signal shielding function is added, so that a thief can be prevented from finding opportunities to steal by shielding alarm transmission signals, the security and the stability of the system are increased, and the two-channel transmission is convenient for management.
Owner:毛振刚
Anti-stealing 3D liquid crystal display, anti-stealing 3D glasses, liquid crystal display system and implementation method
InactiveCN103576386AImprove securityEasy to be stolenNon-linear opticsOptical elementsLiquid-crystal displayMaterials science
The invention discloses an anti-stealing 3D liquid crystal display, anti-stealing 3D glasses, a liquid crystal display system and an implementation method. The anti-stealing 3D liquid crystal display comprises an upper glass substrate and a lower glass substrate and a polaroid, wherein the polaroid is attached to the upper glass substrate, or the polaroid is attached to the lower glass substrate. The anti-stealing 3D glasses comprise lenses, wherein the lenses are polarized lenses, and the polarization direction of the polarized lenses is perpendicular to the polarization direction of the 3D liquid crystal display. According to the anti-stealing 3D liquid crystal display, the anti-stealing 3D glasses, the liquid crystal display system and the implementation method, only an operator who wears the 3D glasses can see the content displayed by the 3D liquid crystal display, the problem that the content displayed by the 3D liquid crystal display can be stolen easily is solved, and the safety of liquid crystal displaying is enhanced.
Owner:QINGDAO GOERTEK
Direct-current distribution box of charging pile
ActiveCN106451129AEasy to be stolenAvoid damageSubstation/switching arrangement detailsCleaning apparatus for vehicle exteriorsMechanical engineeringDirect current
The invention discloses a direct-current distribution box of a charging pile. The direct-current distribution box comprises a base, a shell with an opening in one side, and a box door. The shell is mounted at the top end of the base, the opening of the shell is connected with the box door through a hinge, and a buckle is mounted on the box door. The base comprises a bottom plate and fixed columns, the fixed columns are arranged on the two sides of the bottom end of the bottom plate, and a first rotary shaft and an annular sliding rail are arranged at the top end of the bottom plate. The first rotary shaft is located in the middle of the annular sliding rail, and the two ends of the first rotary shaft are connected with the bottom plate and the shell respectively. Bearings are arranged at the joints of the first rotary shaft, the bottom plate and the shell, and sliding blocks are arranged on the two sides of the bottom end of the shell. A water pump and a cleaning chamber are arranged in the shell, therefore, a vehicle can be cleaned while being charged, time is saved, work efficiency is improved, and the distribution box of the charging pile has diversified functions. The base is arranged at the bottom of the shell, the sliding blocks and the annular sliding rail are arranged between the base and the shell, and vehicles in different directions can be conveniently charged and cleaned.
Owner:天津筋斗祥云网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com