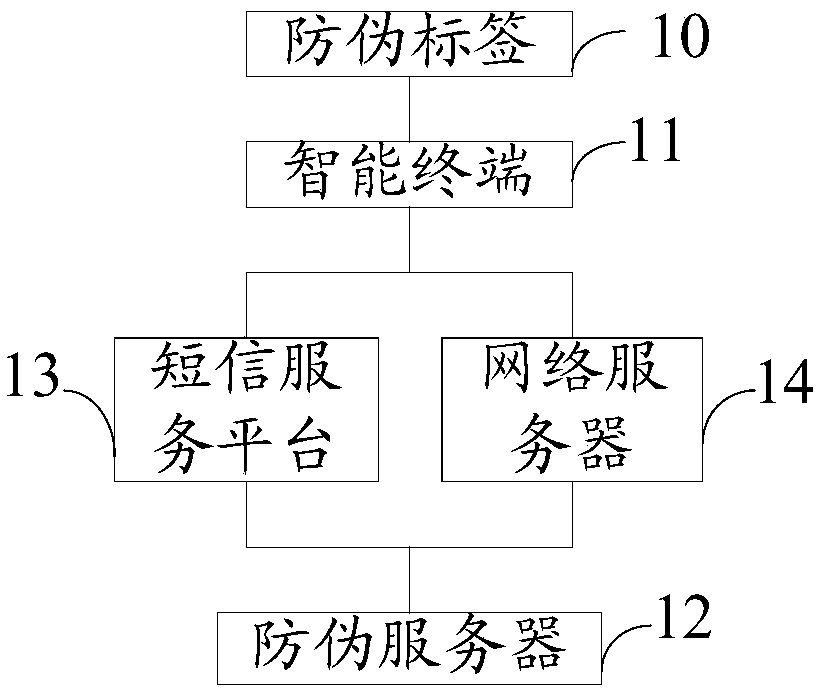
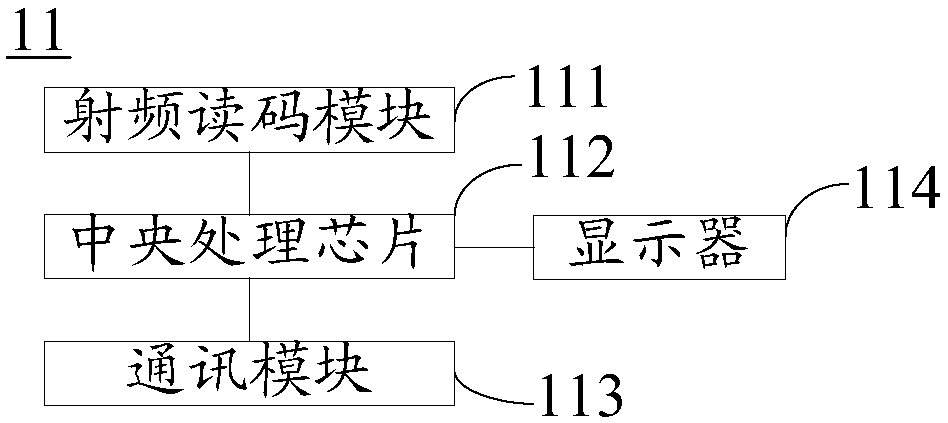
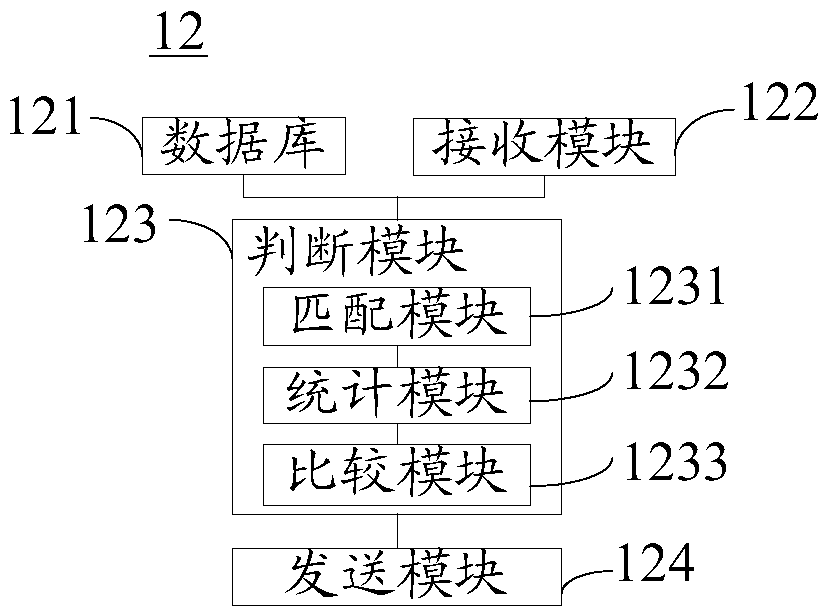
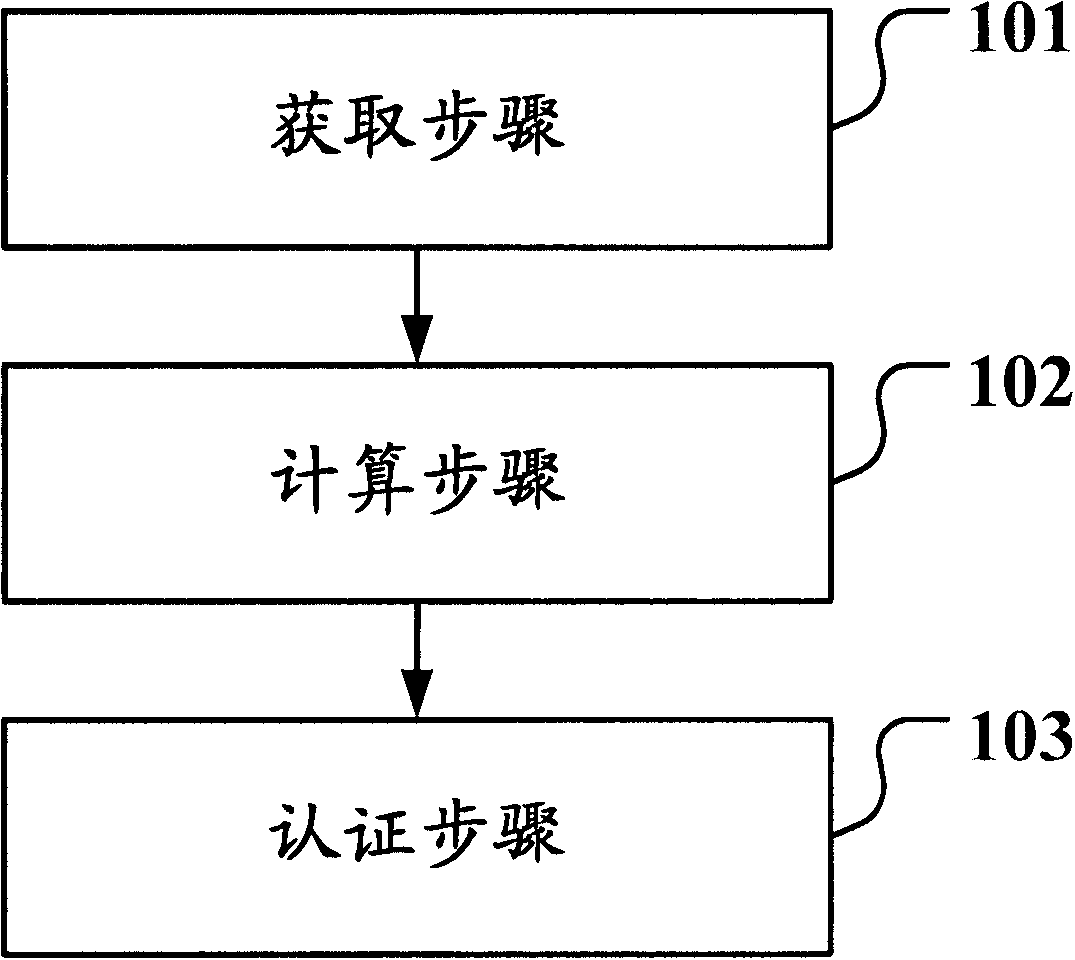
Patents
Literature
147results about How to "Prevent imitation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
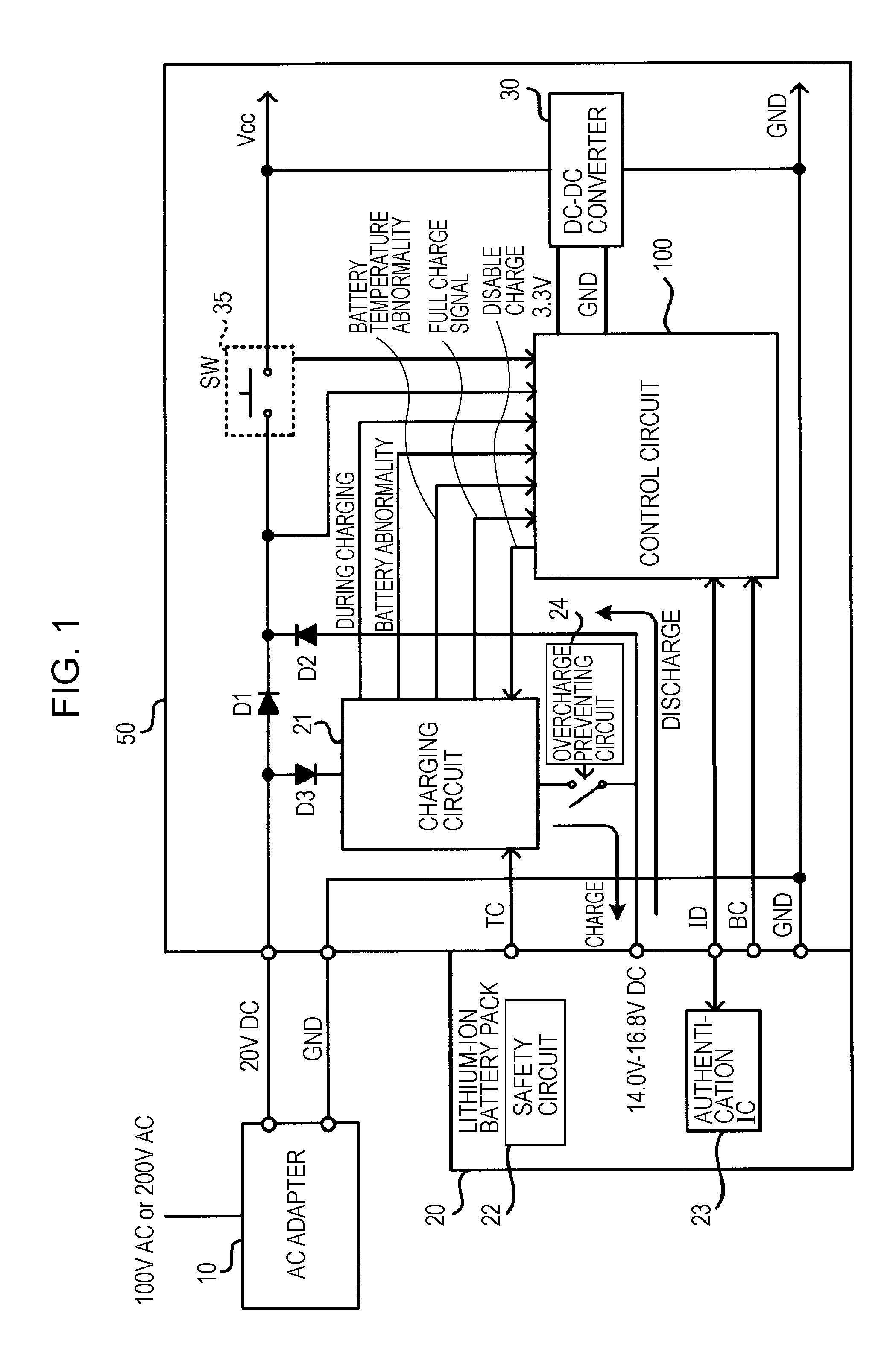
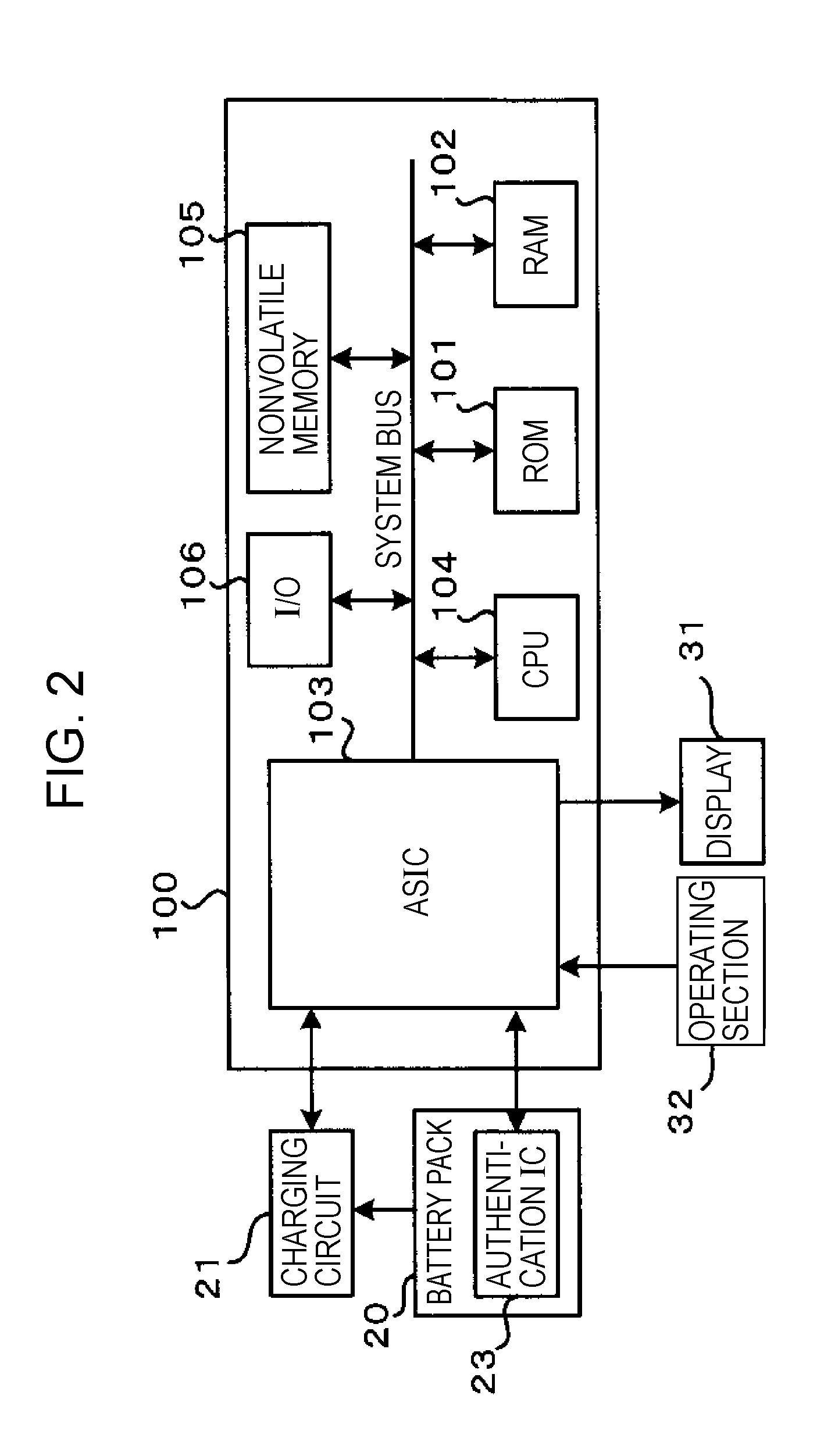
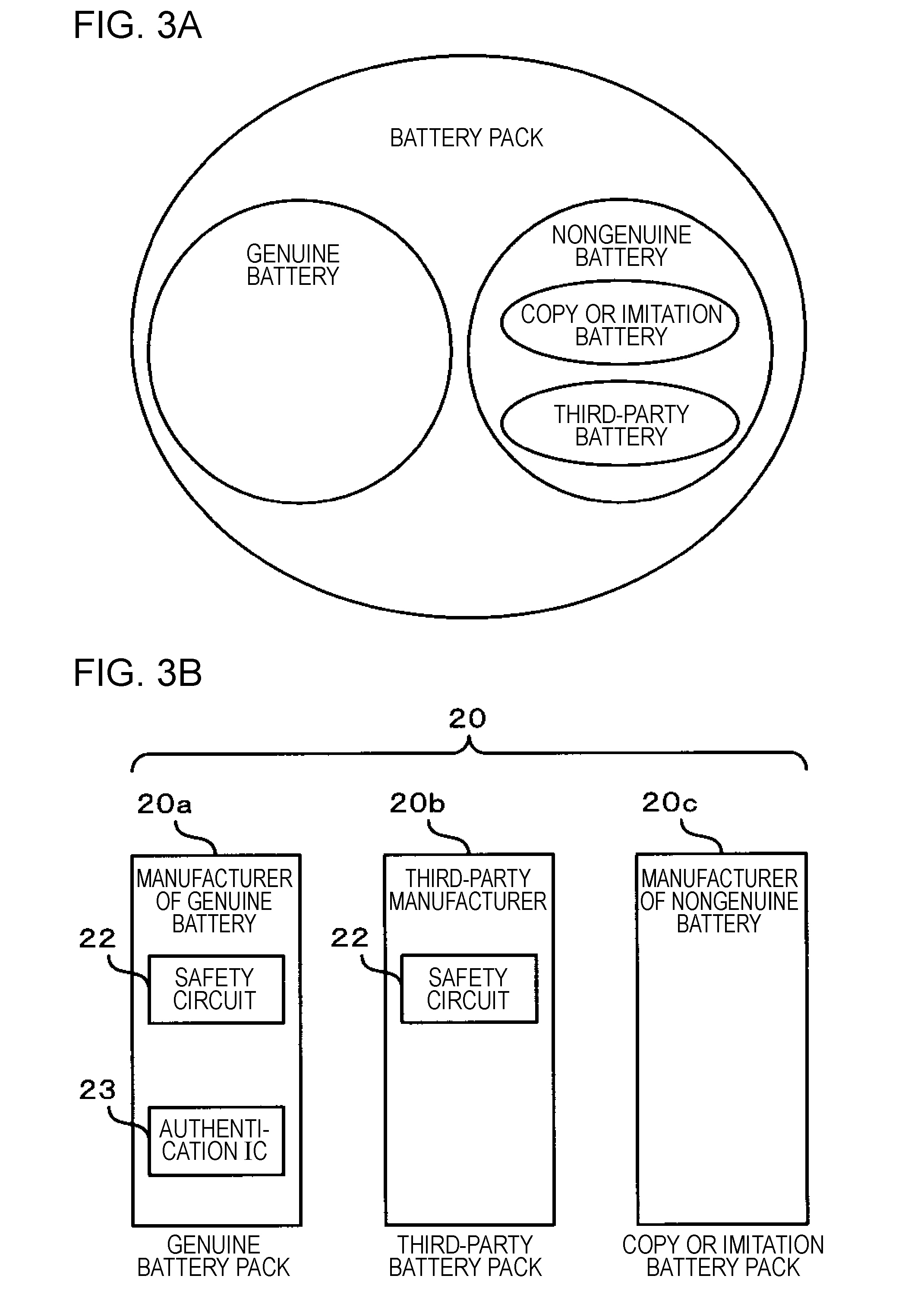
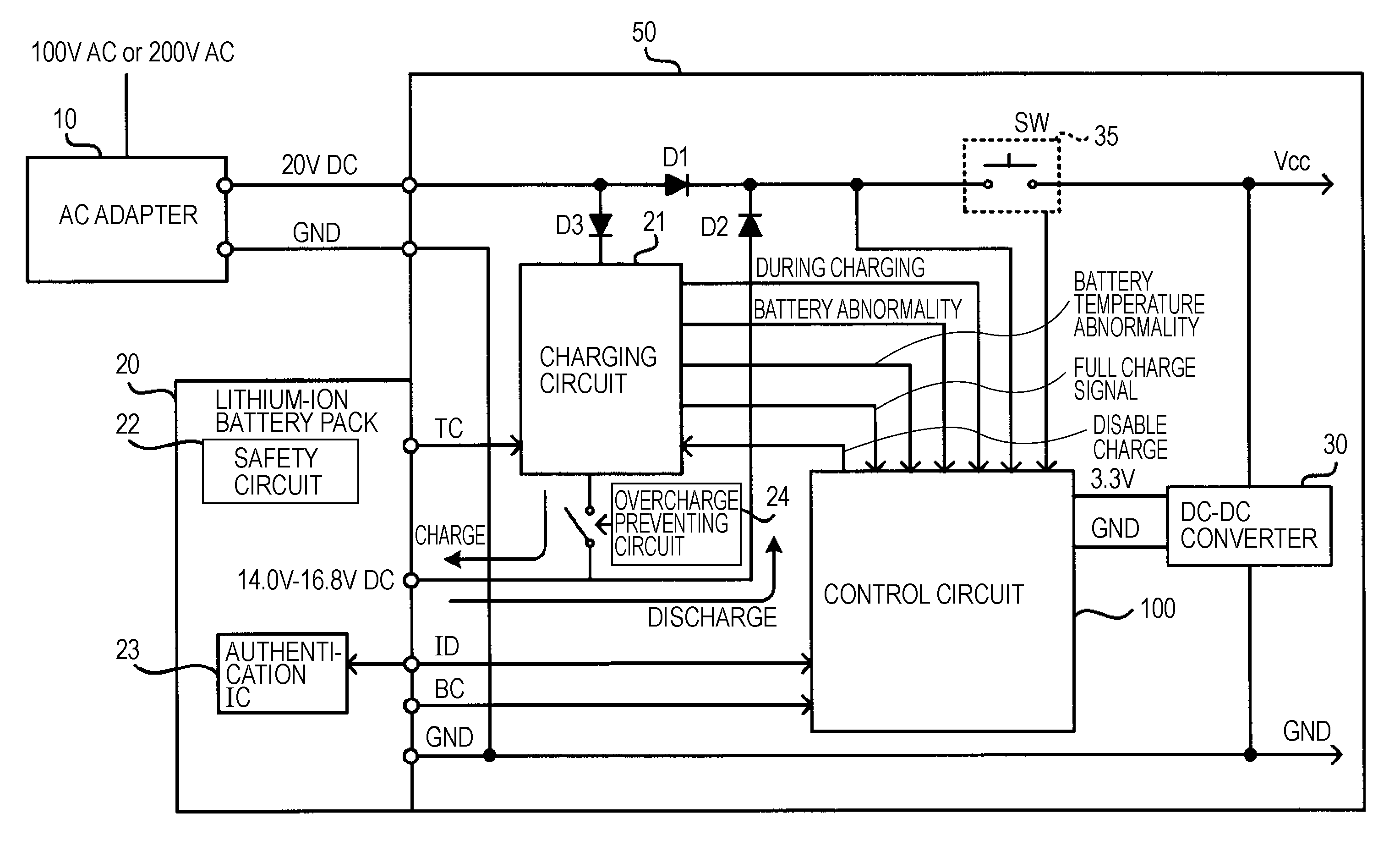
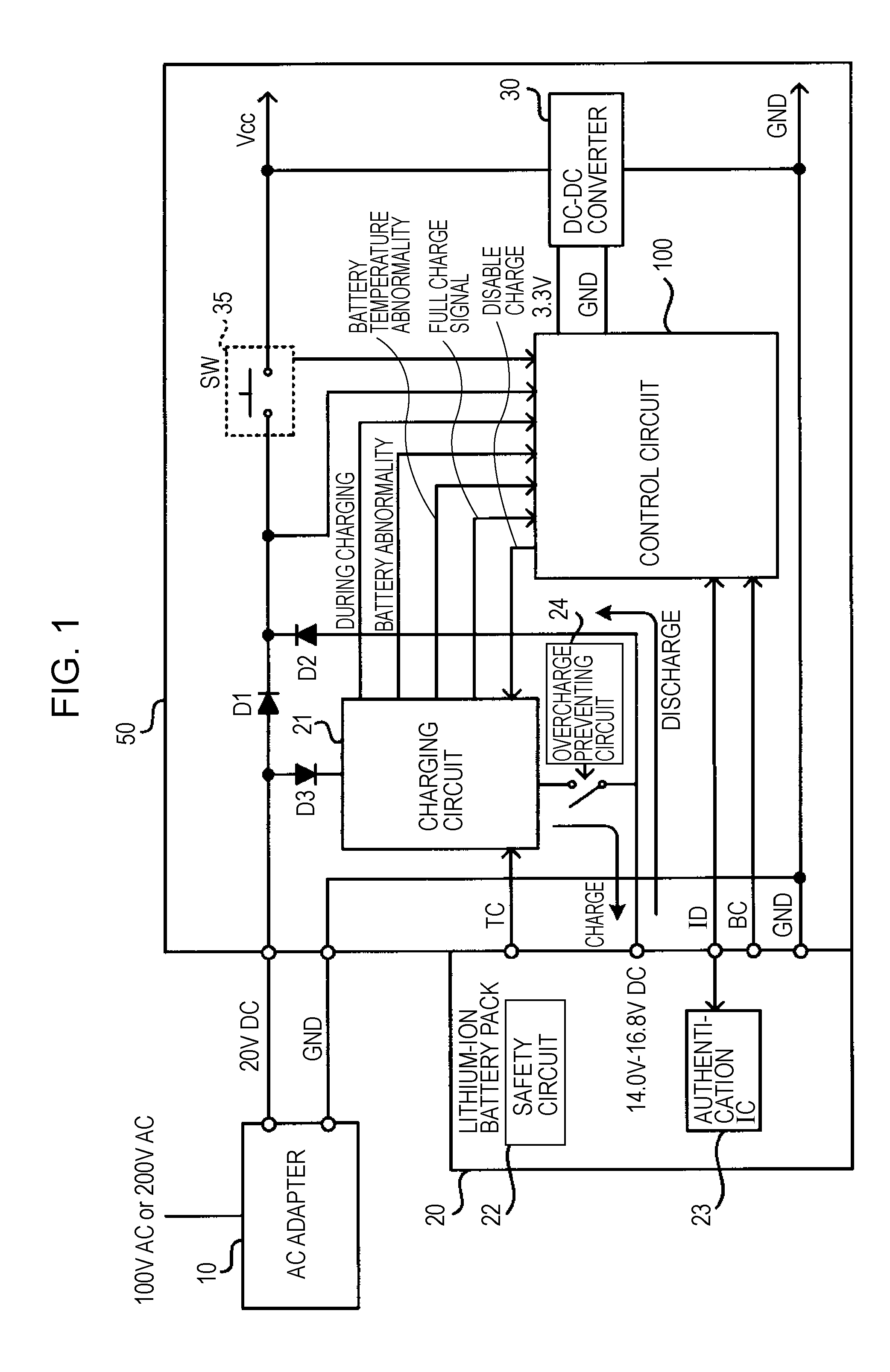
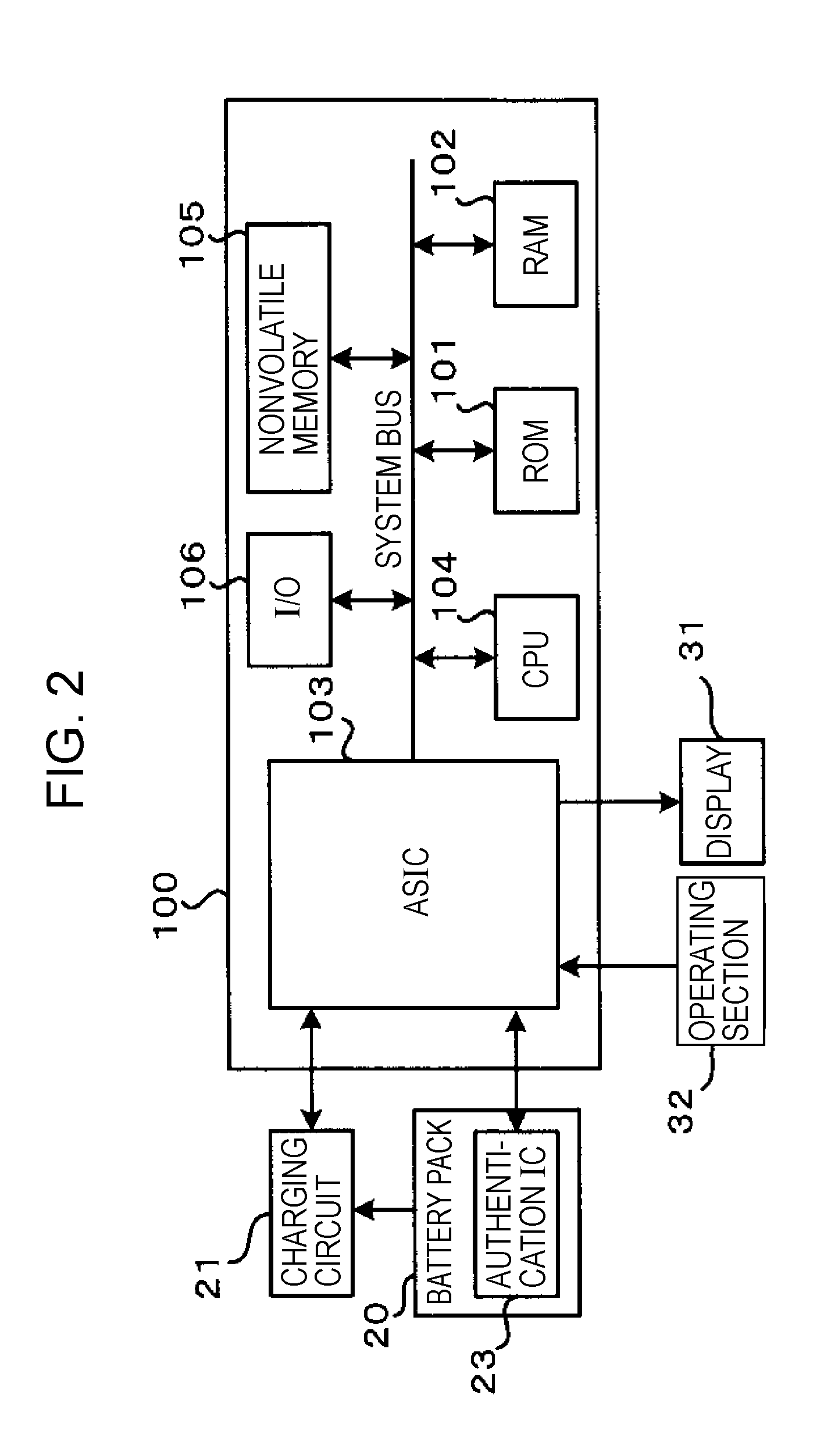
Electronic device, method for controlling the same, and program for the same
ActiveUS20070214296A1Quality be determineDisabled dischargeCircuit monitoring/indicationDifferent batteries chargingControl electronicsEngineering
The invention provides an electronic device having a structure operable by the power of a battery pack. The electronic device includes: an authenticating section that authenticates a battery pack connected so as to supply power to determine whether the battery pack is a genuine product; a user interface; and a controller for controlling the electronic device. The controller tries authentication of the battery pack connected so as to supply power with the authentication section. When the battery pack has been authenticated, the discharging of the battery pack is enabled. When the battery pack has not been authenticated, the controller requests the user to input recognition whether the battery pack is a genuine product through the user interface, and changes the control for the battery pack between when the user inputs, in response to the request, the recognition that the battery pack is a genuine product and when the user inputs the recognition that the battery pack is not a genuine product.
Owner:SEIKO EPSON CORP
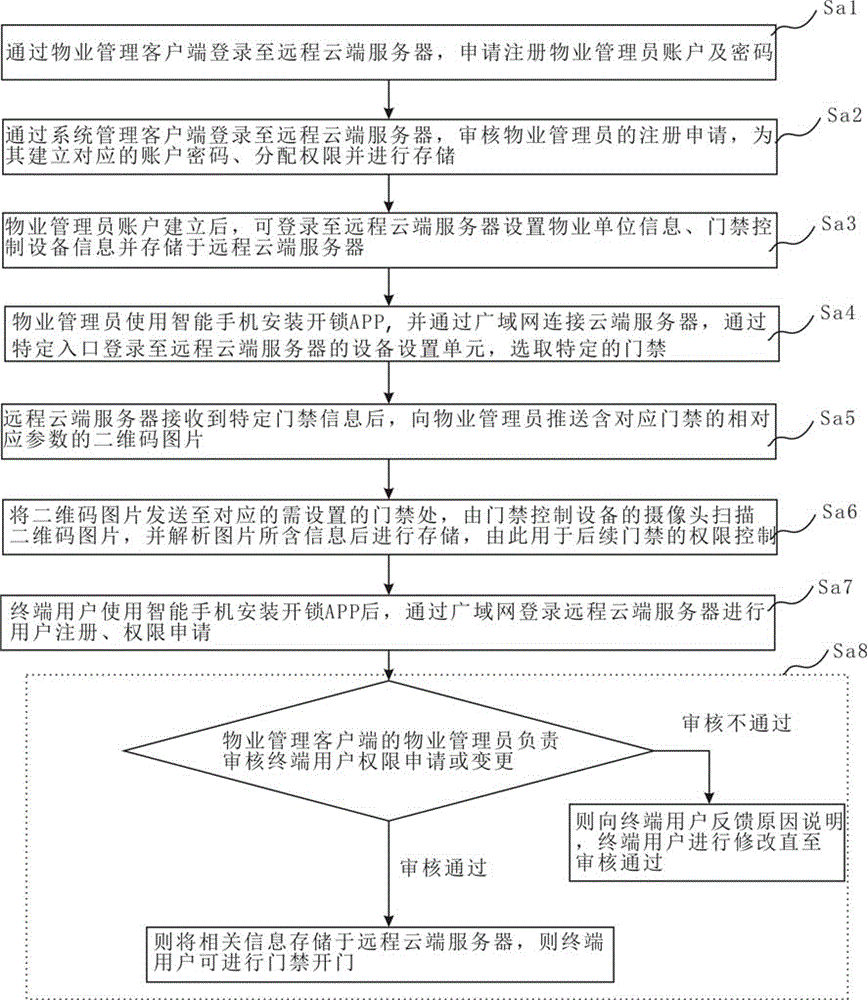
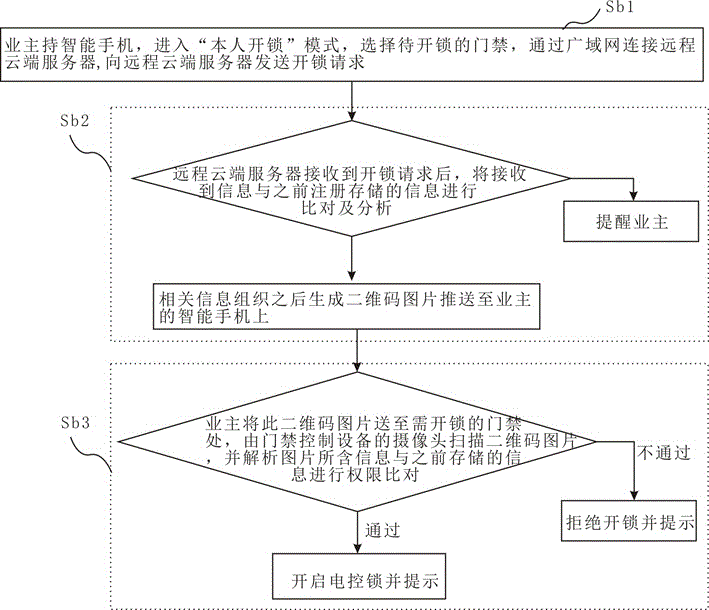
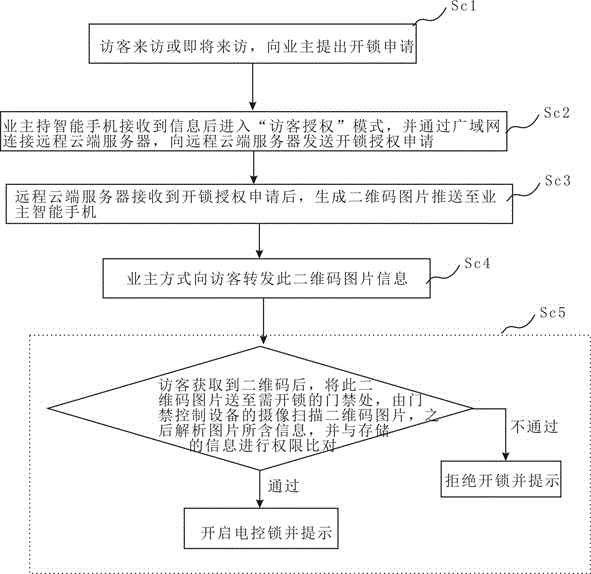
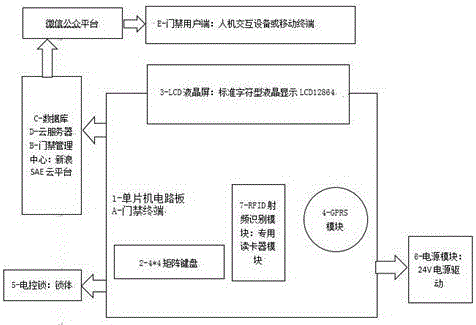
Access control method and system based on cloud technology and two-dimensional code technology
ActiveCN106652135AUnlock implementationReduce overheadIndividual entry/exit registersSystems managementElectric control
The invention discloses an access control method and system based on a cloud technology and a two-dimensional code technology. The system comprises a remote cloud server, a system management client, a property management client, a plurality of user intelligent terminals and access control equipment, wherein the access control equipment is internally provided with an electric control lock; information management is carried out through logging in the remote cloud server via the system management client; the property management client is in communication connection with the system management client through a wide area network and personnel information of corresponding units is managed by the property management client; each user intelligent terminal requires a two-dimensional code picture from the remote cloud server in a utilization process and then sends a two-dimensional code to the access control equipment to carry out authority verification; after a camera of the access control equipment scans the two-dimensional code picture, data analysis is carried out and then authority judgment is carried out; if an authority passes, the electric control lock is controlled to be unlocked and a prompt is given; otherwise, the system reminds that the electric control lock is not successfully unlocked and a prompt is given.
Owner:SHENZHEN MICHOI SECURITY TECH
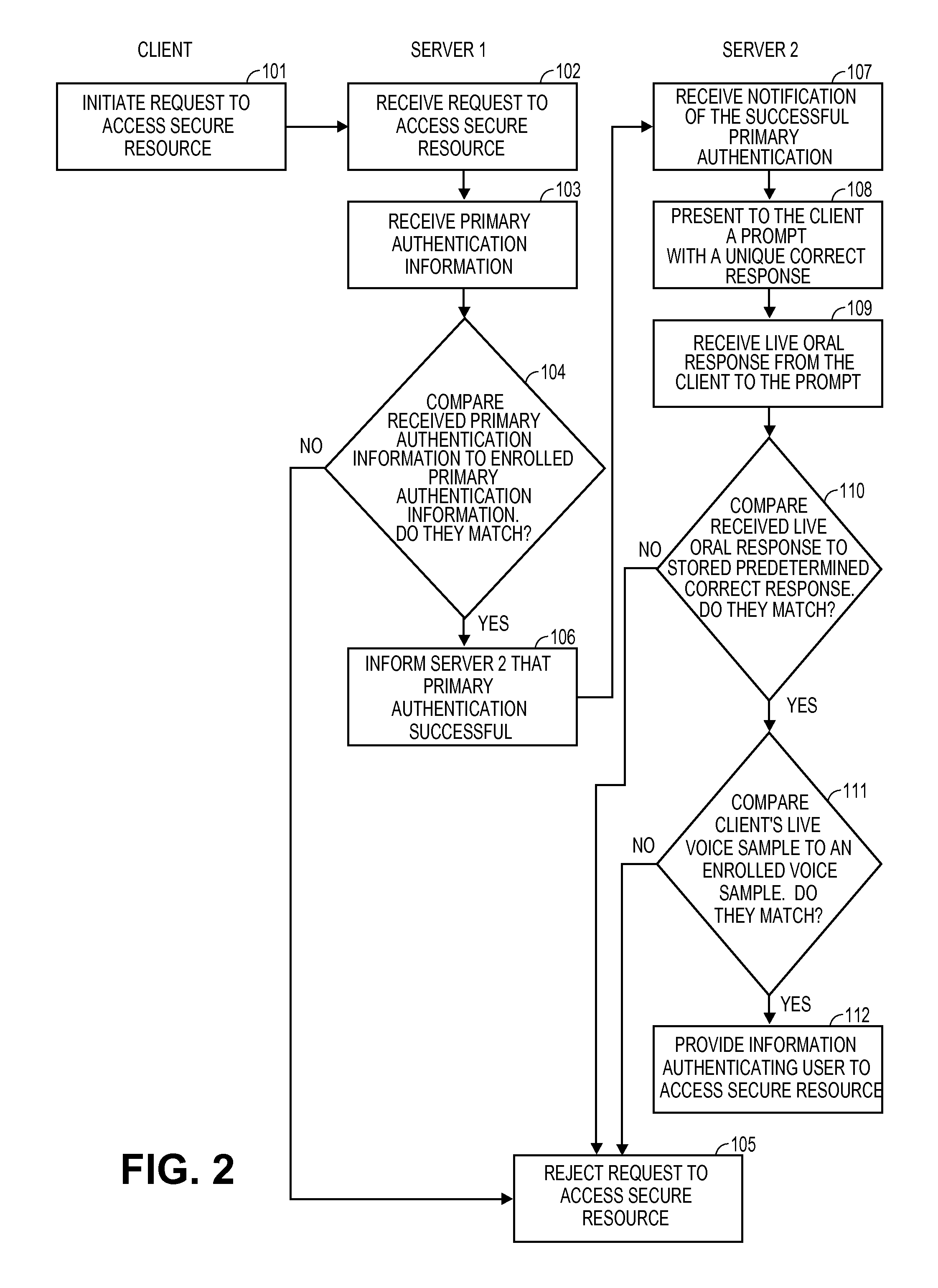
Computer program, method, and system for voice authentication of a user to access a secure resource
InactiveUS20120253810A1Prevent imitationDigital data authenticationSpeech recognitionLive voiceCorrect response
Authenticating a purported user attempting to access a secure resource includes enrolling a user's voice sample by requiring the user to orally speak preselected enrollment utterances, generating prompts and respective predetermined correct responses where each question has only one correct response, presenting a prompt to the user in real time, and analyzing the user's real time live response to determine if the live response matches the predetermined correct response and if voice characteristics of the user's live voice sample match characteristics of the enrolled voice sample.
Owner:PHONEFACTOR
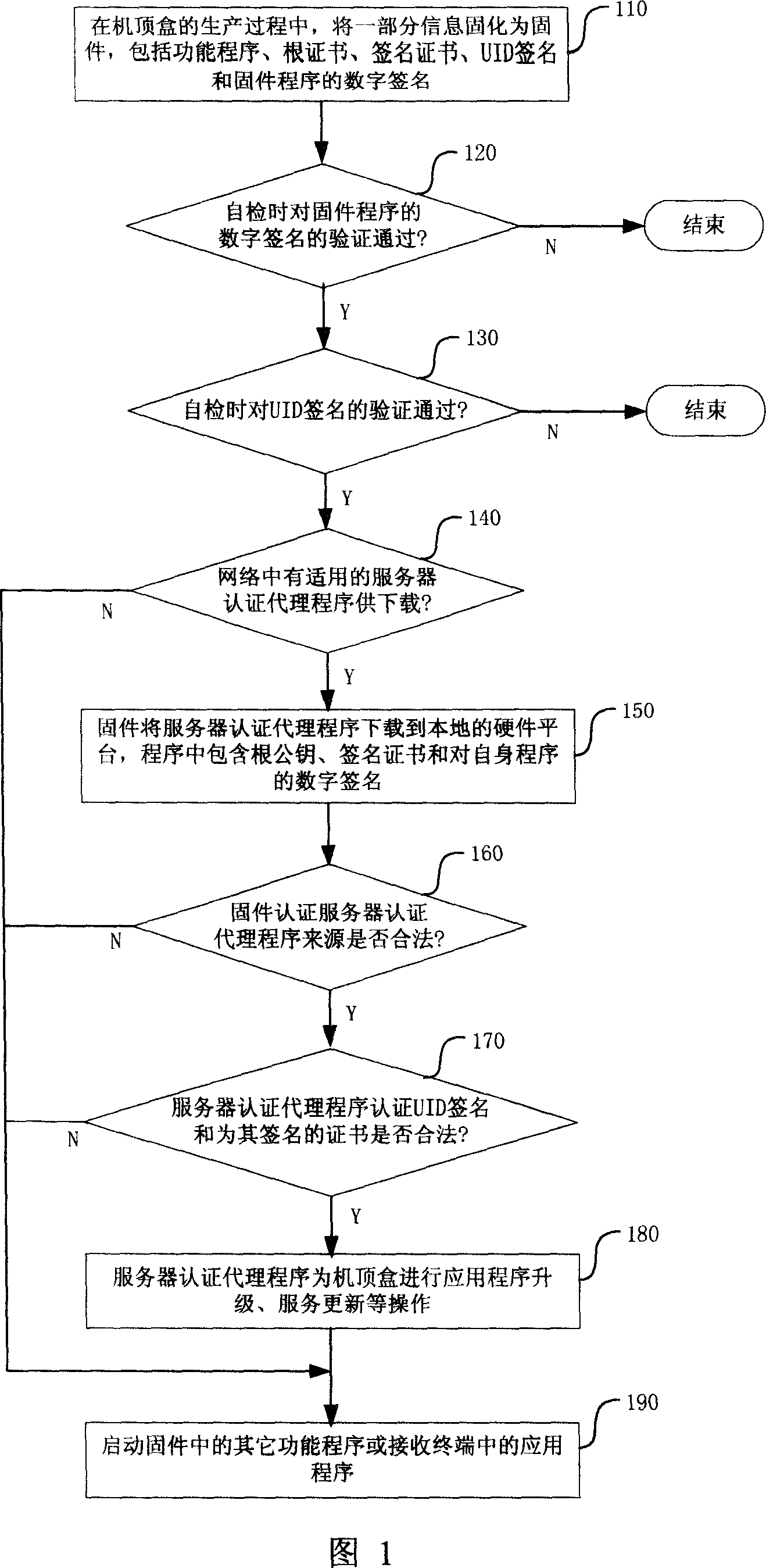
Method and system for authenticating legality of receiving terminal in unidirectional network
ActiveCN101145906ARealize the identification of legitimacyPrevent imitationUser identity/authority verificationDigital signatureTerminal equipment
The invention relates to a method and system for legality authentication of receiving terminals in a unidirectional network. The digital signature of UID of chips is written in terminal equipment, terminal firmware downloads a server authentication agent program from the network, the program runs on the hardware platform of the terminal, and UID signature is decrypted by using a built-in public key or the public key of the signature certificate acquired from the network; if the decrypted value and the abstract value of UID read out from the chips are determined to be identical and the signature certificate is in a trust chain established by the rood certificate, the terminal is legal, or the terminal is illegal. Also, in the process of self-test of the firmware, the decrypted value can be obtained by using the public key in the signature certificate to decrypt UID signature, then UID of the chips is read out and the abstract value thereof is calculated, and if the two values are identical, the self-test passes, or the work state ends. By using the self-test of the terminal firmware or the mutual authentication between the server authentication agent program and the firmware, the invention makes clone and copied set-top boxs not work normally in the network.
Owner:北京邦天信息技术有限公司
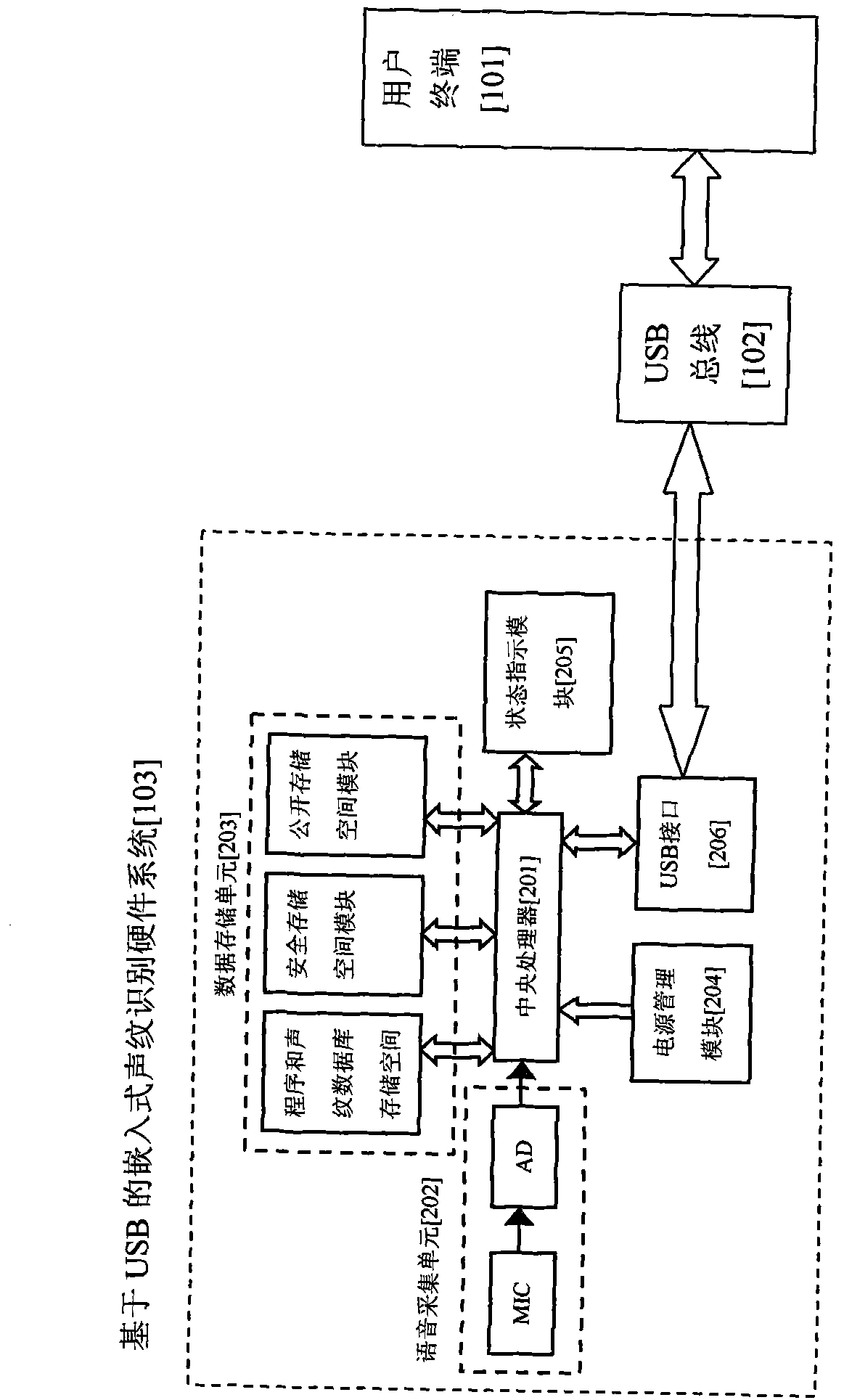
USB (universal serial bus) identity authentication method based on voiceprint recognition and system thereof
InactiveCN101997689APrevent recordingAccurate identificationUser identity/authority verificationSpeech recognitionInternet bankThird party
The invention relates to a USB (universal serial bus) identity authentication method based on voiceprint recognition and a system thereof, belonging to the technical field of computer information safety. The system comprises a user terminal and an embedded voiceprint recognition hardware system based on USB, wherein the user terminal and the embedded voiceprint recognition hardware system based on USB are connected by a USB bus; the embedded voiceprint recognition hardware system based on USB comprises a central processing unit for finishing authenticated voiceprint recognition operation, and the central processing unit is respectively connected with a voice acquisition unit, a data storage unit, a power supply management module, a state indication module and a USB interface used for connecting the user terminal. The invention has the advantage of higher safety. The invention also can provide third-party application and service voiceprint certification interface, and can expand to fields, such as internet banks, e-commerce, e-government affairs and the like.
Owner:JILIN UNIV
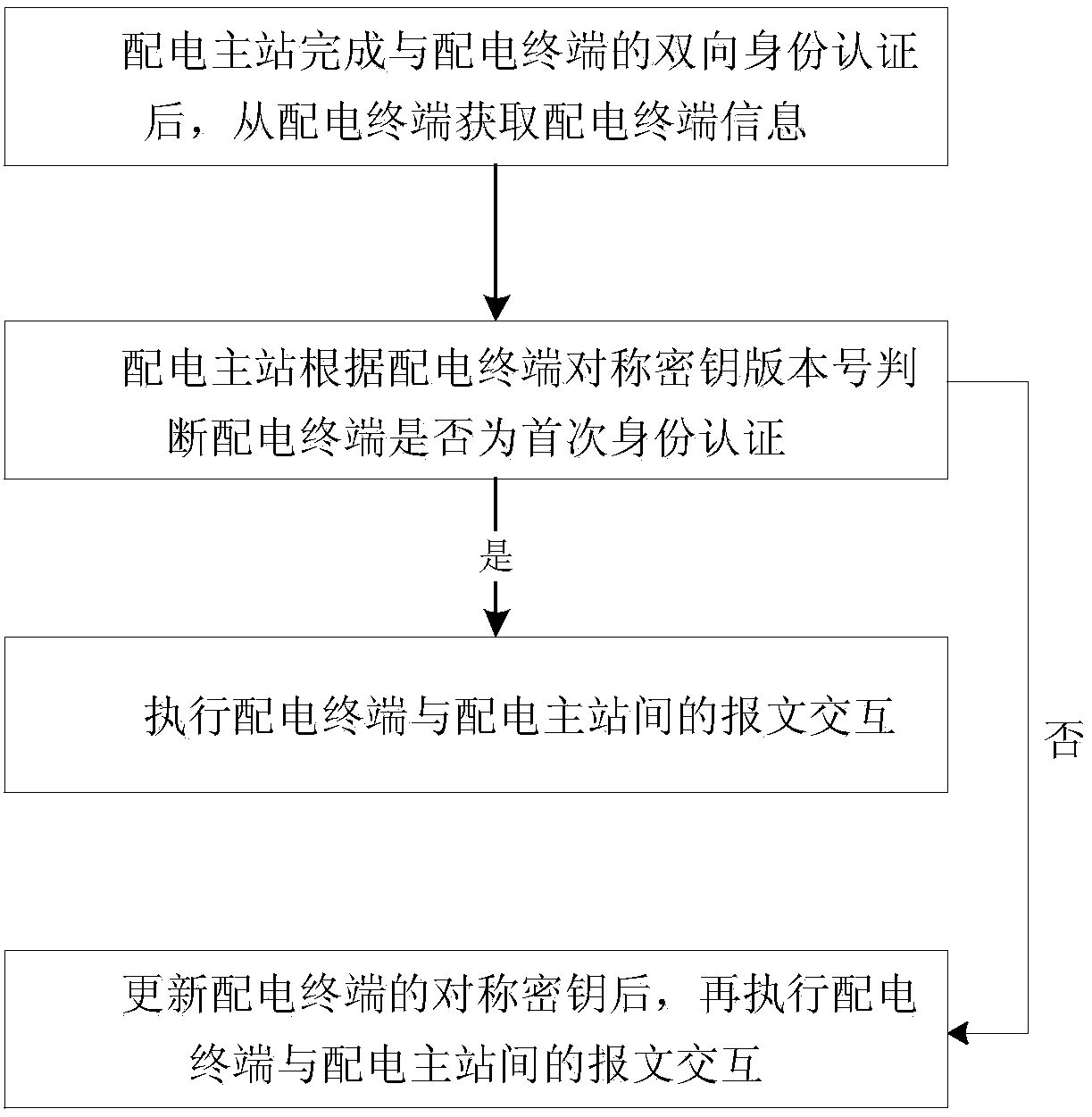
Communication message security interaction method and device of distribution automation system
ActiveCN109257327AImprove the level of security protectionAvoid safety hazardsKey distribution for secure communicationCircuit arrangementsRemote controlConfidentiality
The invention provides a communication message security interaction method and a device of a distribution automation system. After completing two-way identity authentication between a distribution master station and a distribution terminal, a main distribution station obtains distribution terminal information from the distribution terminal. The main distribution station judges whether that distribution terminal is the first identity authentication according to the version number of the symmetrical key of the distribution terminal, if not, the message exchange between the distribution terminaland the main distribution station is carried out; otherwise, after the symmetric key of the distribution terminal is updated, message exchange between the distribution terminal and the distribution master station is performed. The scheme makes up for the shortcomings that the distribution master station can not identify the distribution terminal in the distribution automation system security protection system, and the confidentiality and integrity of the communication message can not be guaranteed, and improves the security protection level of the vertical communication between the distribution master station and the distribution terminal in the distribution automation system. At that same time, the problem that the remote control / parameter set message has the hidden trouble of the replayattack and the like are sol.
Owner:CHINA ELECTRIC POWER RES INST +1
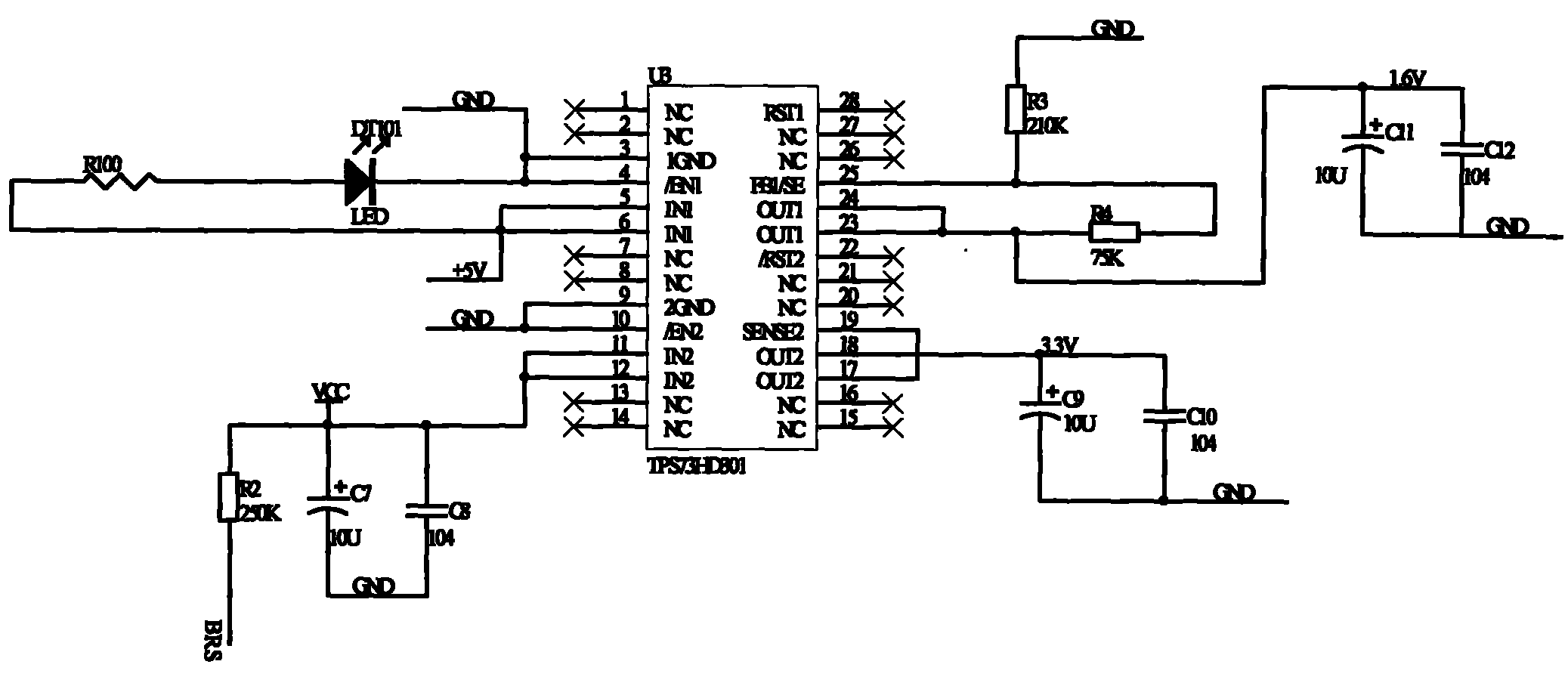
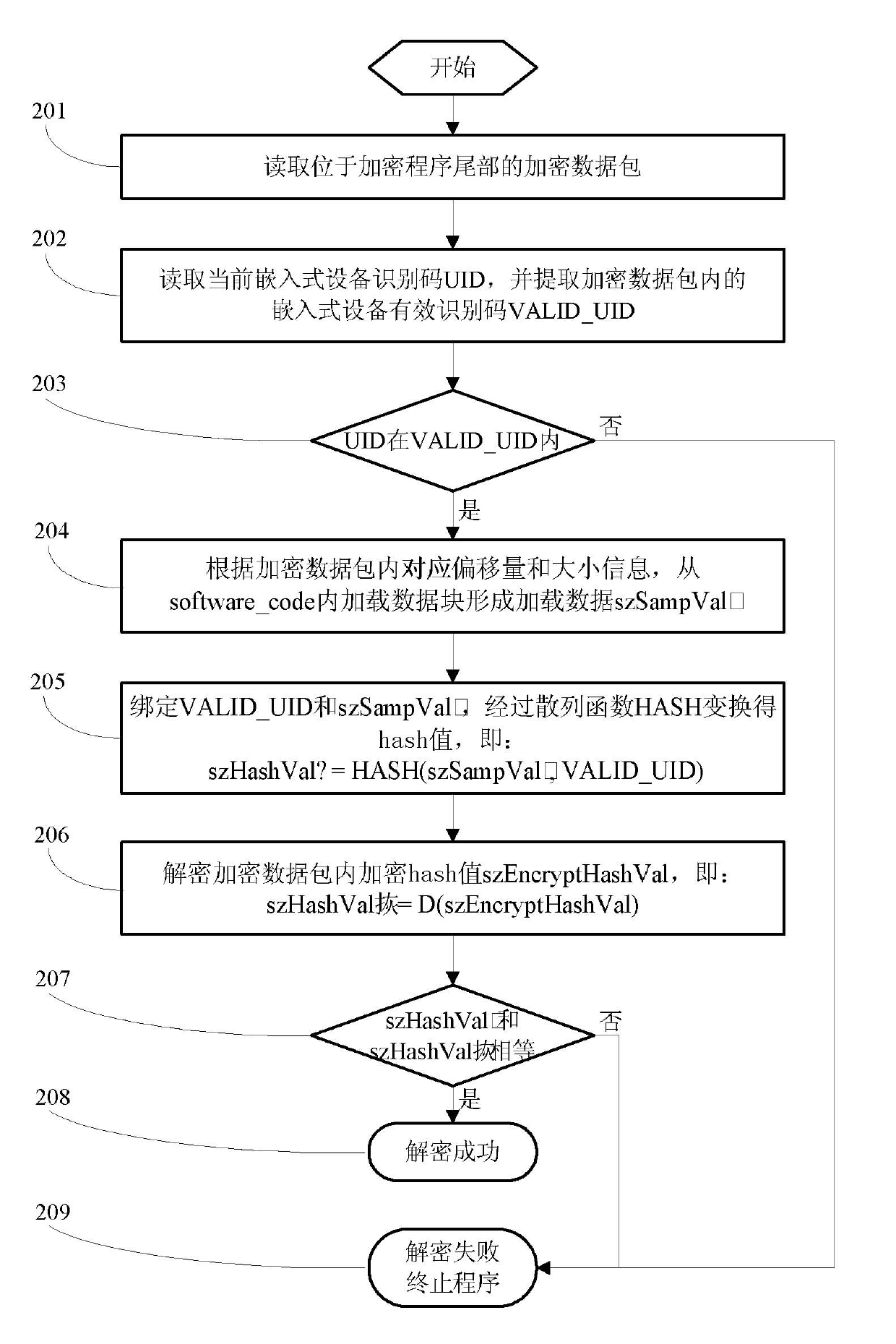
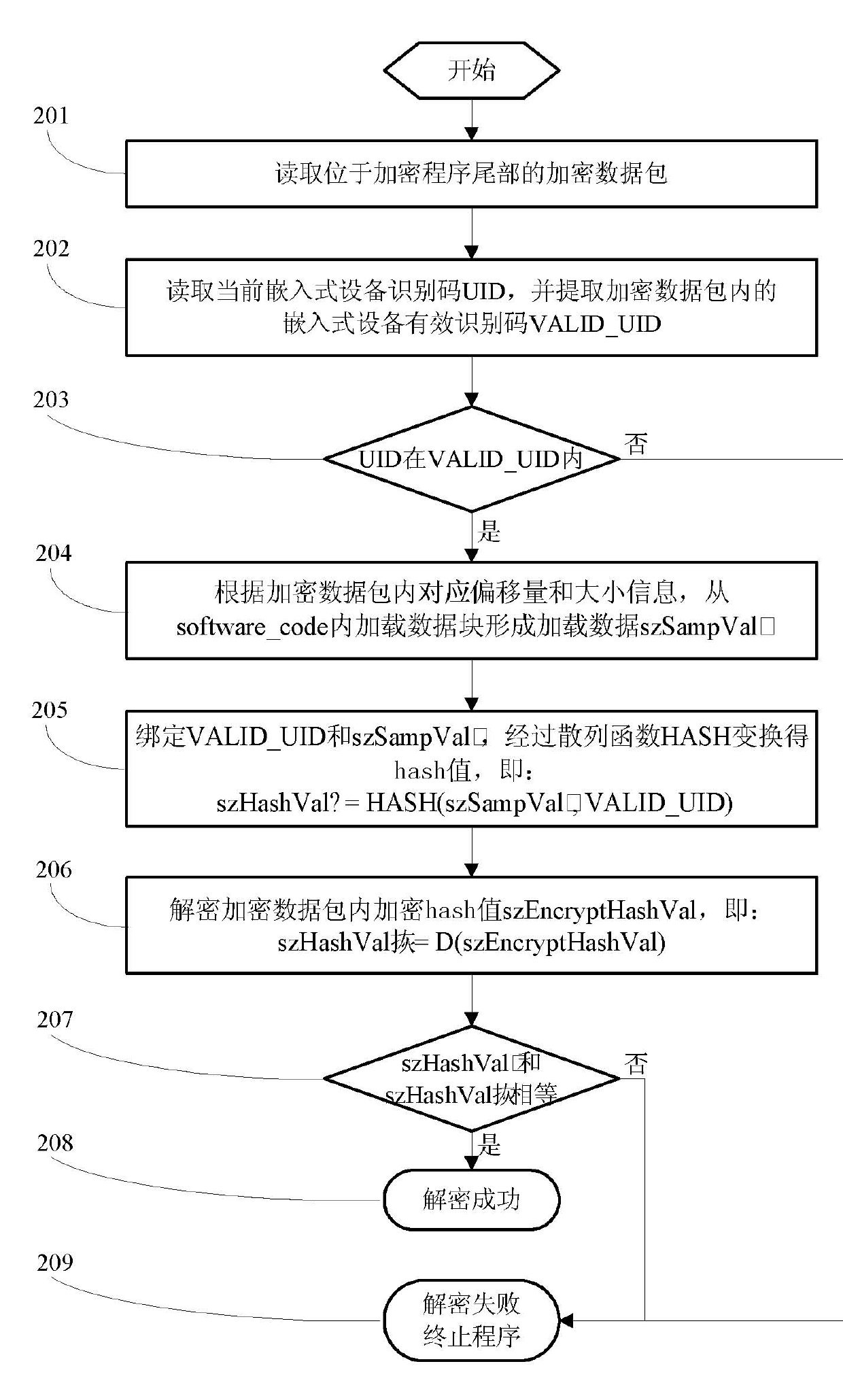
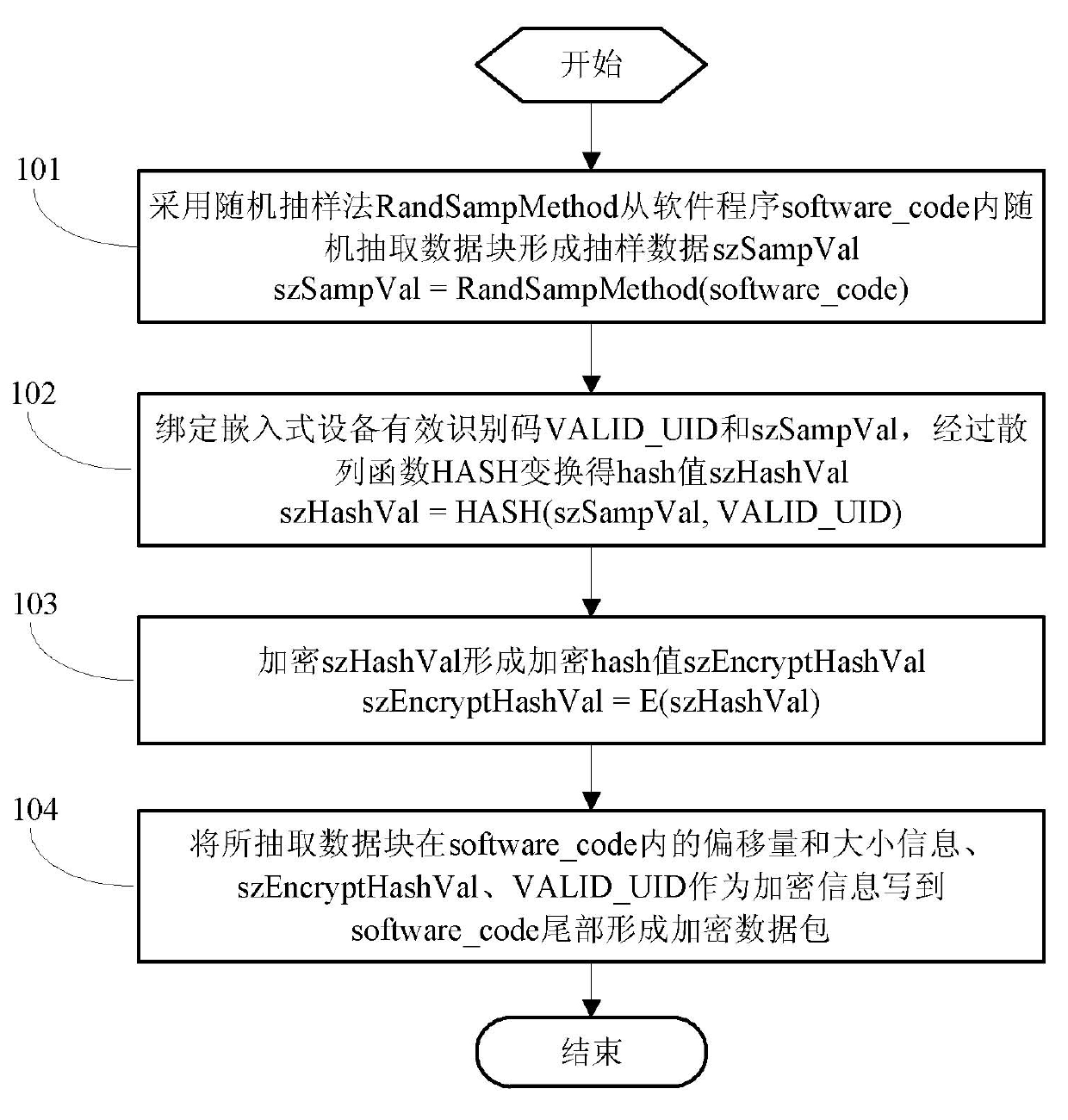
Encryption and decryption methods of embedded software program
ActiveCN101950344APrevent imitationNo additional costProgram/content distribution protectionEncryptionEmbedded software
The invention relates to encryption and decryption methods of an embedded software program. The encryption method comprises the following steps of: randomly extracting a data block from an original software program to form sampled data szSampVal; and inserting the offset and size of the extracted data block, szEncryptHashVal and a valid equipment identification code range VALID_UID into the original software program to form an encryption program. The decryption method comprises the following steps of: reading an embedded equipment identification code UID; and if the UID belongs to VALID_UID and D(szEncryptHashVal) is equal to HASH(szSampVal+VALID_UID), judging that decryption succeeds, and if the UID does not belong to VALID_UID and D(szEncryptHashVal) is equal to HASH(szSampVal+VALID_UID), judging that decryption fails. In the encryption and decryption methods of the embedded software program, after being bound with the valid equipment identification code range, codes are encrypted to be used, so that the basis is provided for anti-copying and refreshing.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
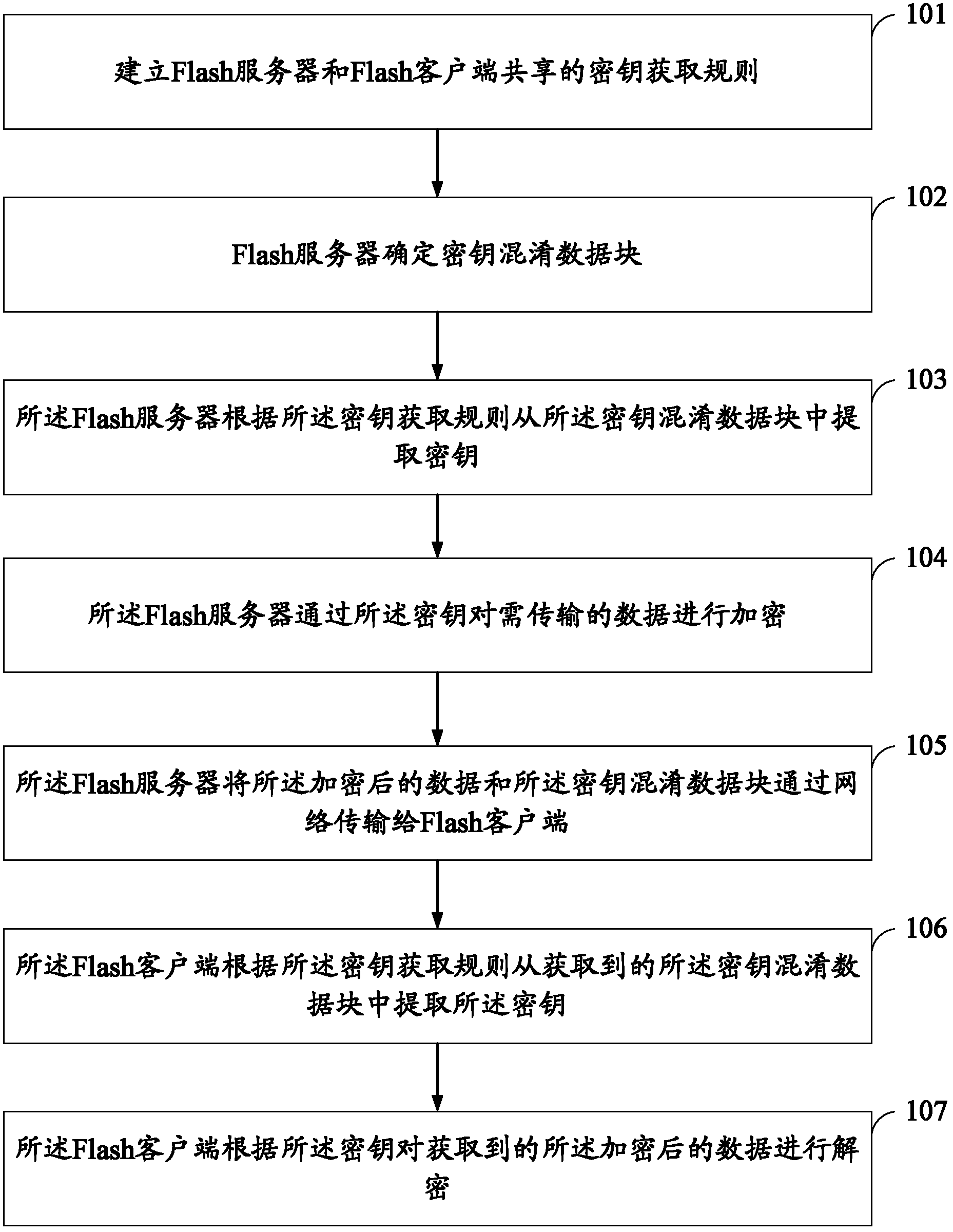
Flash data transmission method and system, as well as server and client
InactiveCN102546824AAvoid transmissionImprove securityKey distribution for secure communicationTransport systemNetwork communication
The invention relates to the field of information and particularly relates to a Flash data transmission method and system, as well as a server and a client. The Flash data transmission method comprises the following steps that: a secret key obtaining rule shared by a Flash server and a Flash client is established; the Flash server determines a secret key confusion data block; the Flash server extracts a secret key from the secret key confusion data block according to the secret key obtaining rule; the Flash server encrypts the data to be transmitted through the secret key; the Flash server transmits the encrypted data and the secret key confusion data block to the Flash client; the Flash client extracts the secret key from the secret key confusion data block according to the secret key obtaining rule; and the Flash client decrypts the obtained encrypted data according to the secret key. The Flash server, the Flash client and the Flash data transmission system transmit data after using the encryption method. According to the invention, the security in the Flash network communication is improved.
Owner:沈文策
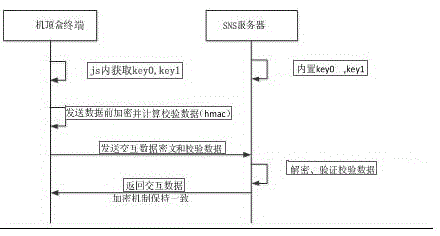
Set-top box terminal and mobile terminal binding system
PendingCN106803990APay attention to safetyIntegrity guaranteedSelective content distributionThe InternetEncryption
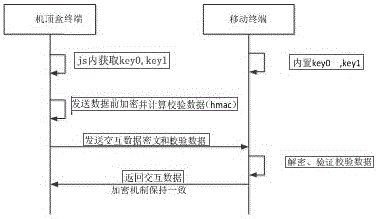
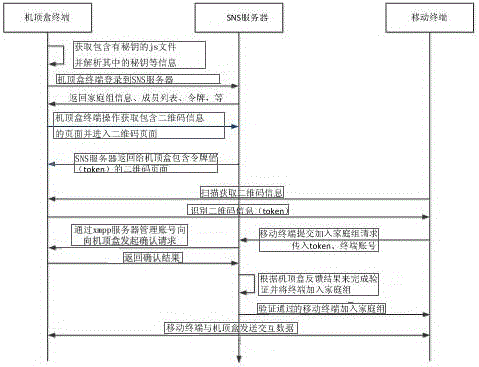
The invention provides a set-top box terminal and mobile terminal binding system comprising a set-top box terminal, an SNS server, a mobile terminal and an xmpp server. A set-top box terminal and a mobile terminal are the users of the binding system. The xmpp server provides the xmpp protocol service. The SNS server runs SNS service. A mobile terminal and set-top box terminal matching control device, in the aspect of security, adds encryption and verification messages on the basis of original interactive messages and the mobile terminal and the set-top box terminal are required to verify the integrity of the messages in order to prevent the messages from being imitated or tampered. In the Internet environment, a cell phone scans a two-dimensional code on a TV to achieve the association of the cell phone and the set-top box so as to achieve interactive functions.
Owner:中国广电山东网络有限公司
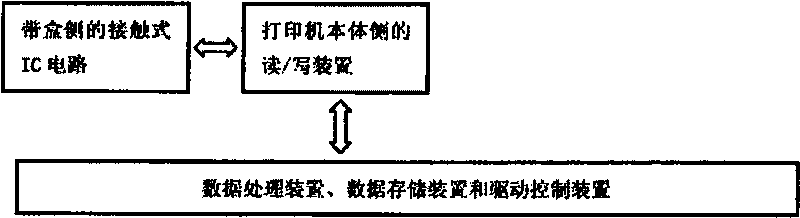
Method for identifying genuine or counterfeit printing consumable material and automatically selecting printing parameters
ActiveCN101746165ALow priceReal-time response remainingInk ribbonsSensing record carriersTime responsePassword protection
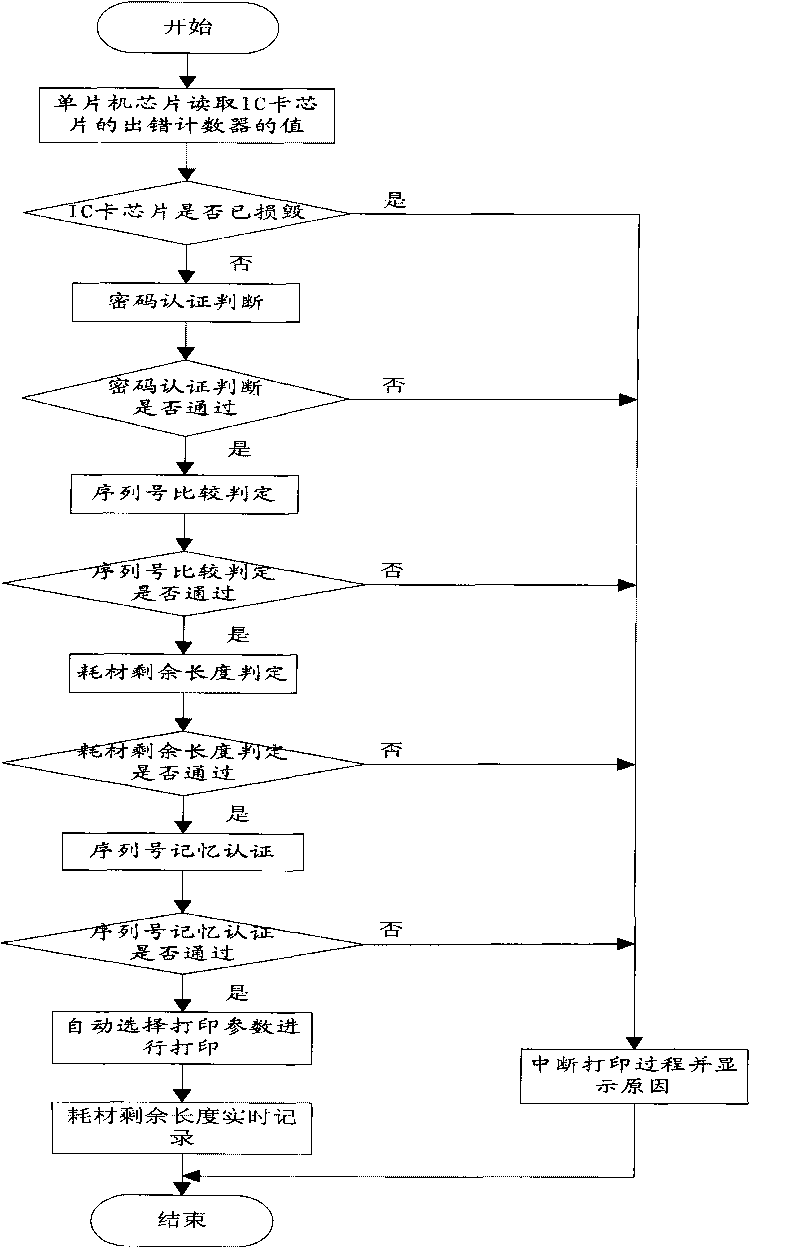
The invention discloses a method for identifying a genuine or counterfeit printing consumable material and automatically selecting printing parameters, and the method sequentially comprises the following steps: (1) authenticating and judging a password; (2) comparing and determining a serial number; (3) determining the residual length of the consumable material and recording the process in a real-time manner; (4) memorizing and authenticating the serial number; and (5) automatically selecting the printing parameters for printing; if the judgment in any step of (1), (2), (3) and (4) is no, the printing process is stopped and error information is displayed. Compared with the traditional method for identifying the printing consumable material, the method has the advantages of high imitation cost, large capacity of a storage medium, low device cost, password protection function of information, real-time response of the residual amount of the consumable material and the like.
Owner:上海威侃电子材料有限公司
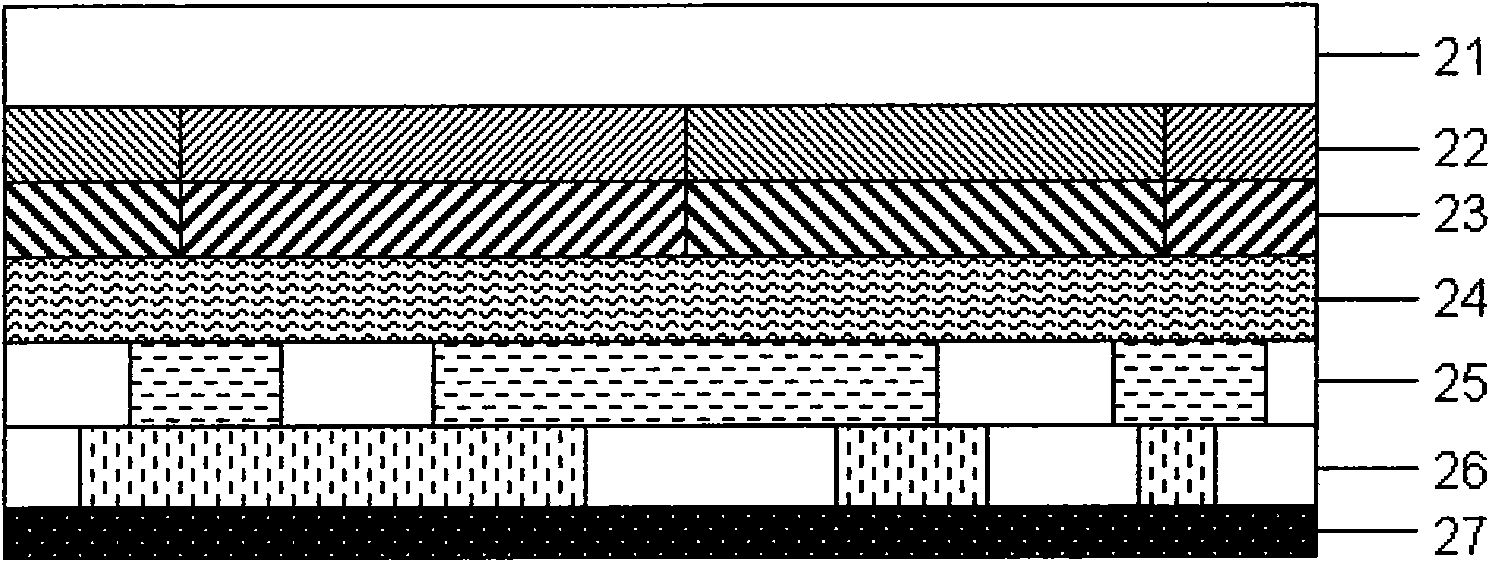
PhotoallergicPhototropic anti-fake element for protectingeventing valuable object
ActiveCN101937154ARich anti-counterfeiting featuresAbundant optical variable anti-counterfeiting featuresOther printing matterNon-linear opticsPolarizerCholesteric liquid crystal
The invention relates to a photoallergichototropic anti-fake element for protectingeventing a valuable object, at least provided with a first liquid crystal orientation layer, a first nematic liquid crystal layer, a first cholesteric liquid crystal layer, a second cholesteric liquid crystal layer and a dark background layer. The photoallergichototropic anti-fake element has the visually identifiable angle-dependantular allochroic characteristic, the visually identifiable angle-dependantular pattern change characteristic and the identifiable hidden patterns characteristic under a polaroid sheet, combines a plurality of photoallergicphototropic anti-fake characteristics in the same photoallergicphototropic anti-fake element and provides the phototropicphototropi anti-fake element which is easy for the mass to identify and hard to forge. The invention also relates to the valuable object provided with the phototropiphototropic anti-fake element.
Owner:CHINA BANKNOTE SECURITY PRINTING TECH RES INST CO LTD +1
Electronic device, method for controlling the same, and program for the same
ActiveUS7683571B2Disabled dischargePrevent imitationCircuit monitoring/indicationDifferent batteries chargingUser inputControl electronics
The invention provides an electronic device having a structure operable by the power of a battery pack. The electronic device includes: an authenticating section that authenticates a battery pack connected so as to supply power to determine whether the battery pack is a genuine product; a user interface; and a controller for controlling the electronic device. The controller tries authentication of the battery pack connected so as to supply power with the authentication section. When the battery pack has been authenticated, the discharging of the battery pack is enabled. When the battery pack has not been authenticated, the controller requests the user to input recognition whether the battery pack is a genuine product through the user interface, and changes the control for the battery pack between when the user inputs, in response to the request, the recognition that the battery pack is a genuine product and when the user inputs the recognition that the battery pack is not a genuine product.
Owner:SEIKO EPSON CORP
Method, device and system for biometrically authenticating a person
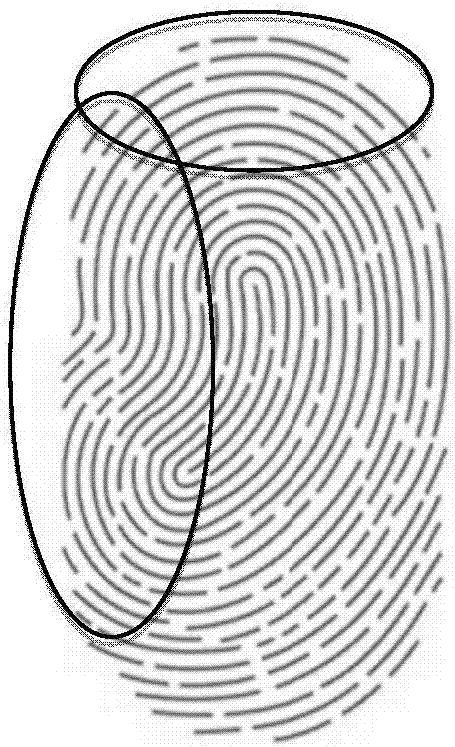
InactiveUS7165716B1Improve securityPrevent imitationComplete banking machinesFinanceBiometric dataComputer science
A method, apparatus and system for biometric authentication of a person are proposed. Since the detection of biometric data never matches 100 percent, authentication is already effected when the detected data exceed a defined threshold value in comparison to stored reference data. In order to increase security, the invention provides that information about the person's individual properties influencing the biometric data is stored and taken into account in the authentication process. For example, the threshold value is set low upon comparison of a fingerprint only if the person has exceptionally dry or moist skin. On the other hand, the sensor for detecting the biometric data of the fingerprint can also be set to be more sensitive or less sensitive depending on the stored information.
Owner:GIESECKE & DEVRIENT MOBILE SECURITY GMBH
Method and a device for safely interacting on-site operation and maintenance data
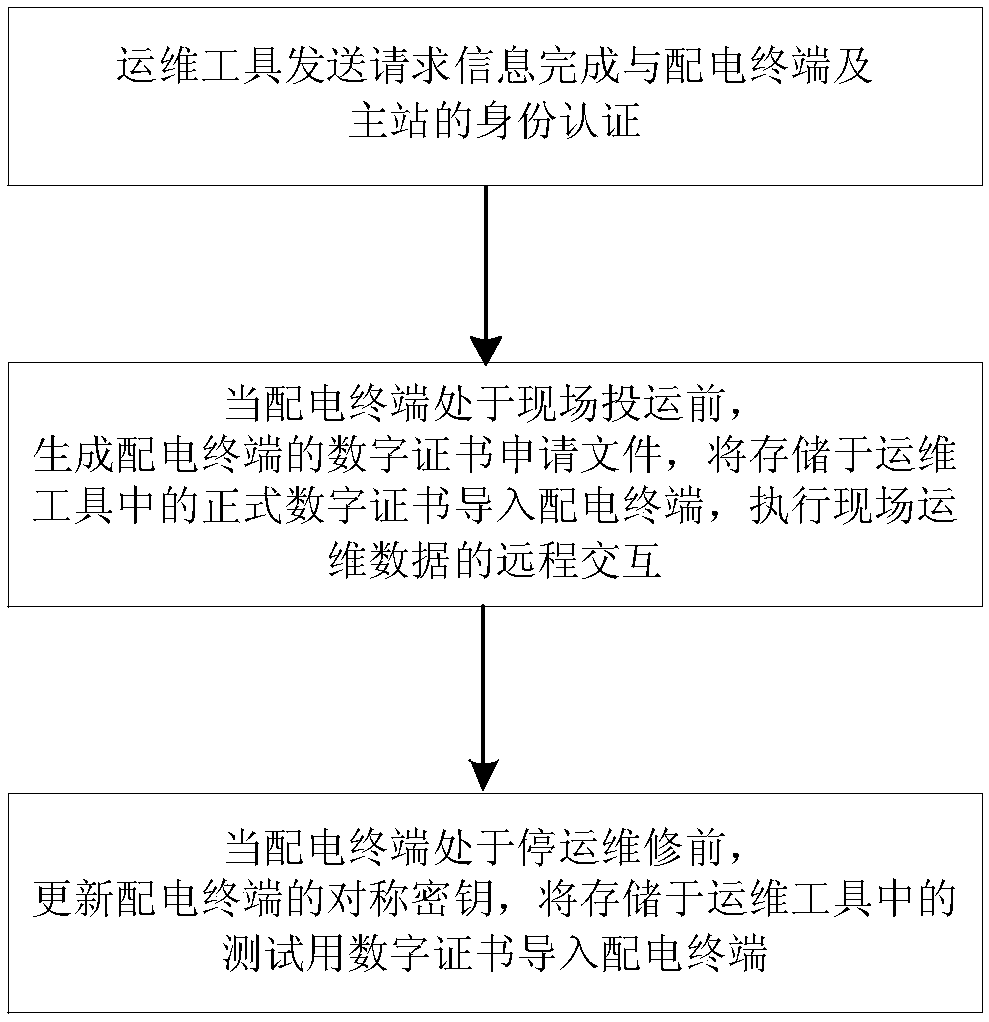
ActiveCN109257328APrevent imitationAvoid destructionKey distribution for secure communicationCircuit arrangementsMaster stationComputer terminal
The invention relates to a method and a device for safely interacting on-site operation and maintenance data, comprising the following steps: an operation and maintenance tool sends request information to complete identity authentication with a power distribution terminal and a master station; generating a digital certificate application file of the distribution terminal before the distribution terminal is put into operation on site, importing a formal digital certificate stored in an operation and maintenance tool into the distribution terminal, and performing remote interaction of the fieldoperation and maintenance data; when the distribution terminal is out of service, the symmetric key of the distribution terminal is updated, and the test digital certificate stored in the operation and maintenance tool is imported into the distribution terminal. This scheme improves the management flow of digital certificate and symmetric key, and makes up for the security loopholes in the operation and maintenance process of distribution terminals, so as to improve the security protection level of field application and operation and maintenance of distribution terminals.
Owner:CHINA ELECTRIC POWER RES INST +1
Electronic lead seal and application system
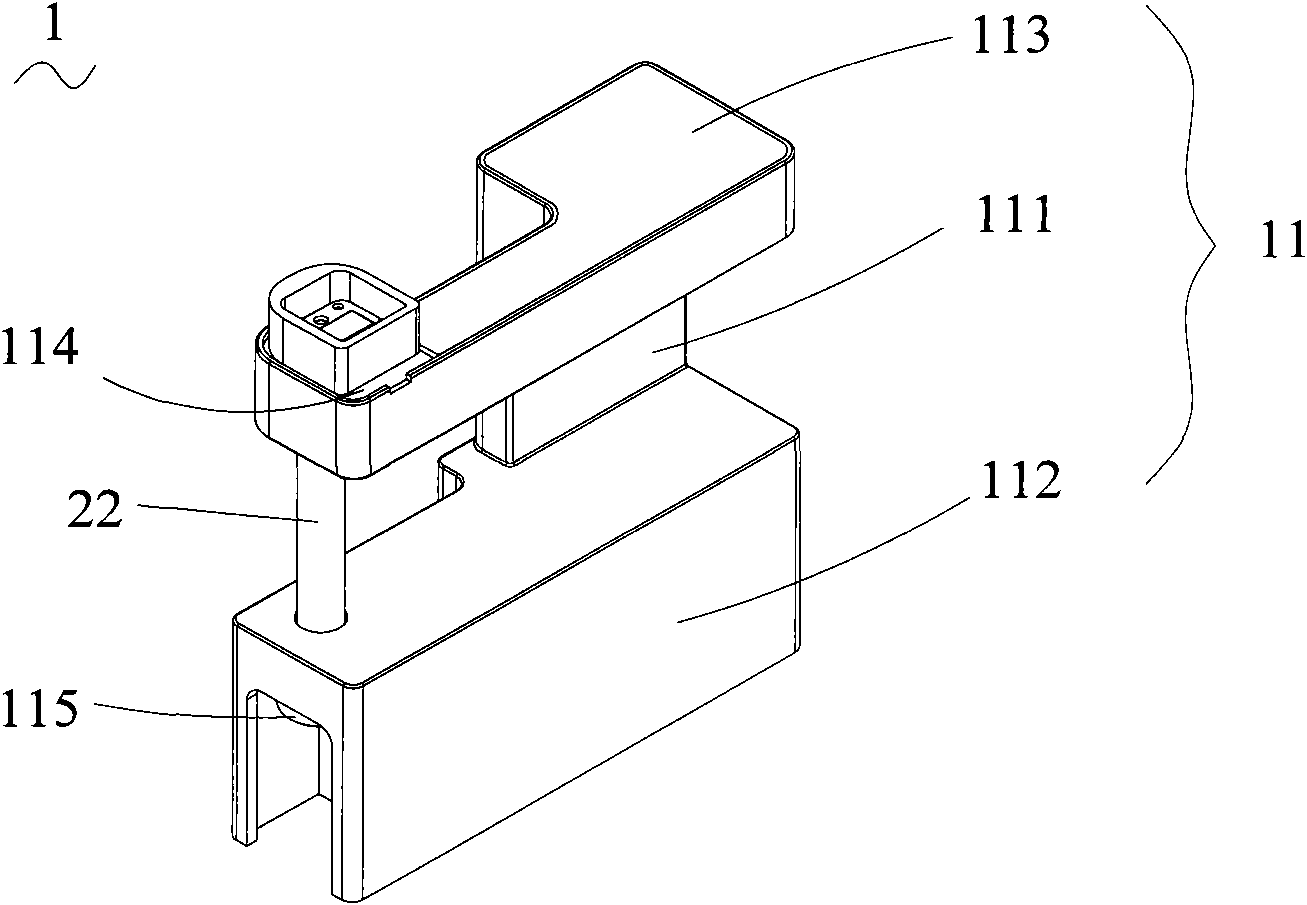
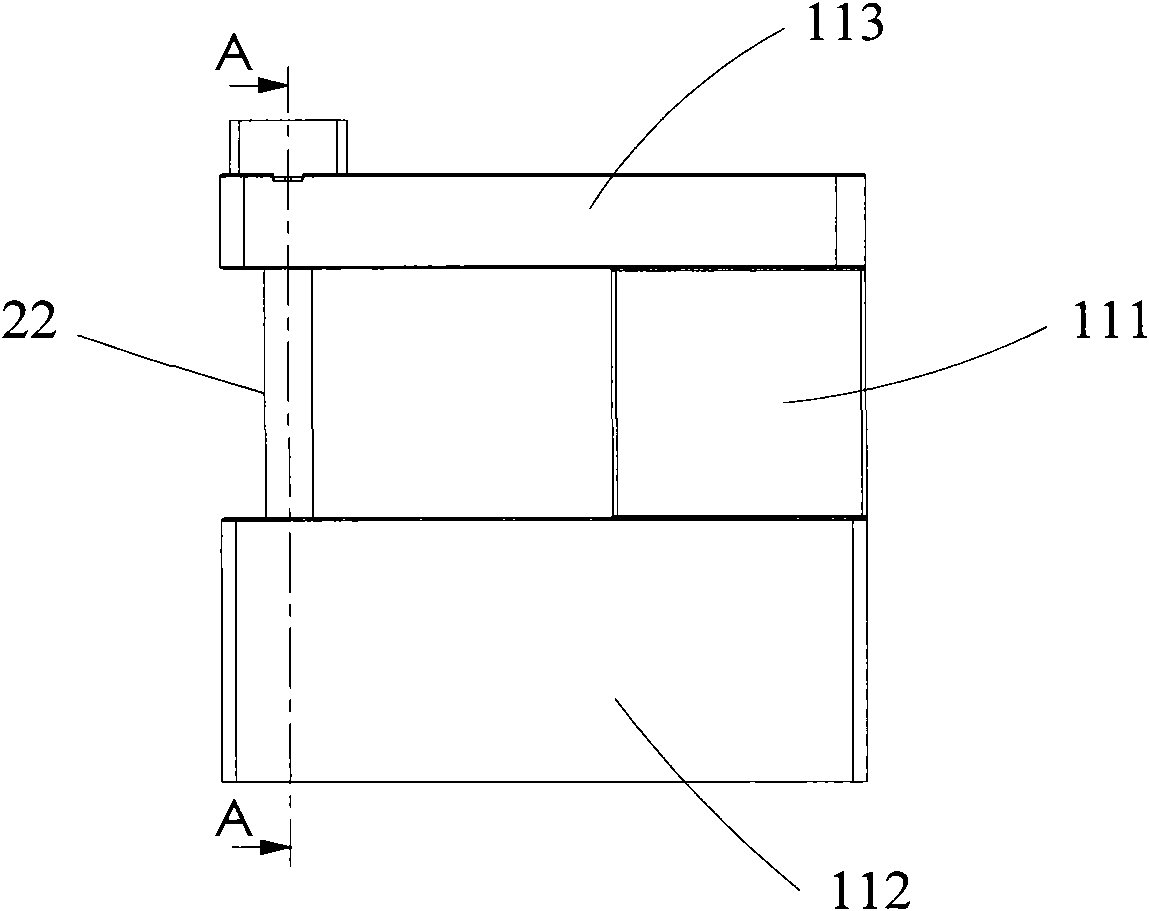
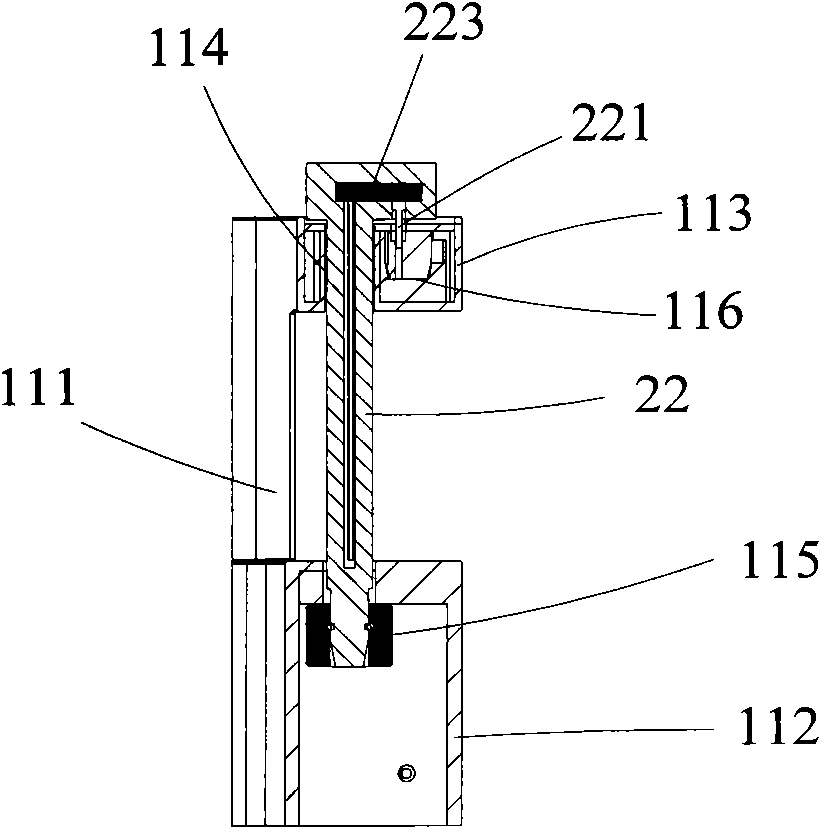
ActiveCN102140868APrevent imitationImprove securityBuilding locksLarge containersData centerComputer terminal
The invention relates to an electronic lead seal and an electronic lead seal application system, which are applied to a container. The application system comprises the electronic lead seal, a data center and a communication terminal, wherein the electronic lead seal comprises a body and a lock rod; the body comprises a vertical arm, and an upper arm and a lower arm which are connected with two ends on the same side of the vertical arm; the hanging-out end of the upper arm is provided with a positioning hole; the hanging-out end of the lower arm is provided with a lock seat; the lock rod passes through the positioning hole at the hanging-out end of the upper arm and is locked on the lock seat at the hanging-out end of the lower arm; a main body circuit is arranged in the body; a lock rod circuit for storing the identity (ID) number of the lock rod is arranged in the lock rod; and the main body circuit is connected with the lock rod circuit in a wired or wireless mode to read the ID number of the lock rod and identify the state information of inserting and cutting of the lock rod, and sends the ID number of the lock rod and the state information thereof to the data center or the communication terminal.
Owner:SHENZHEN CIMC SECURITY & SMART TECH +2
Electronic signature verification method, terminal equipment and computer readable medium
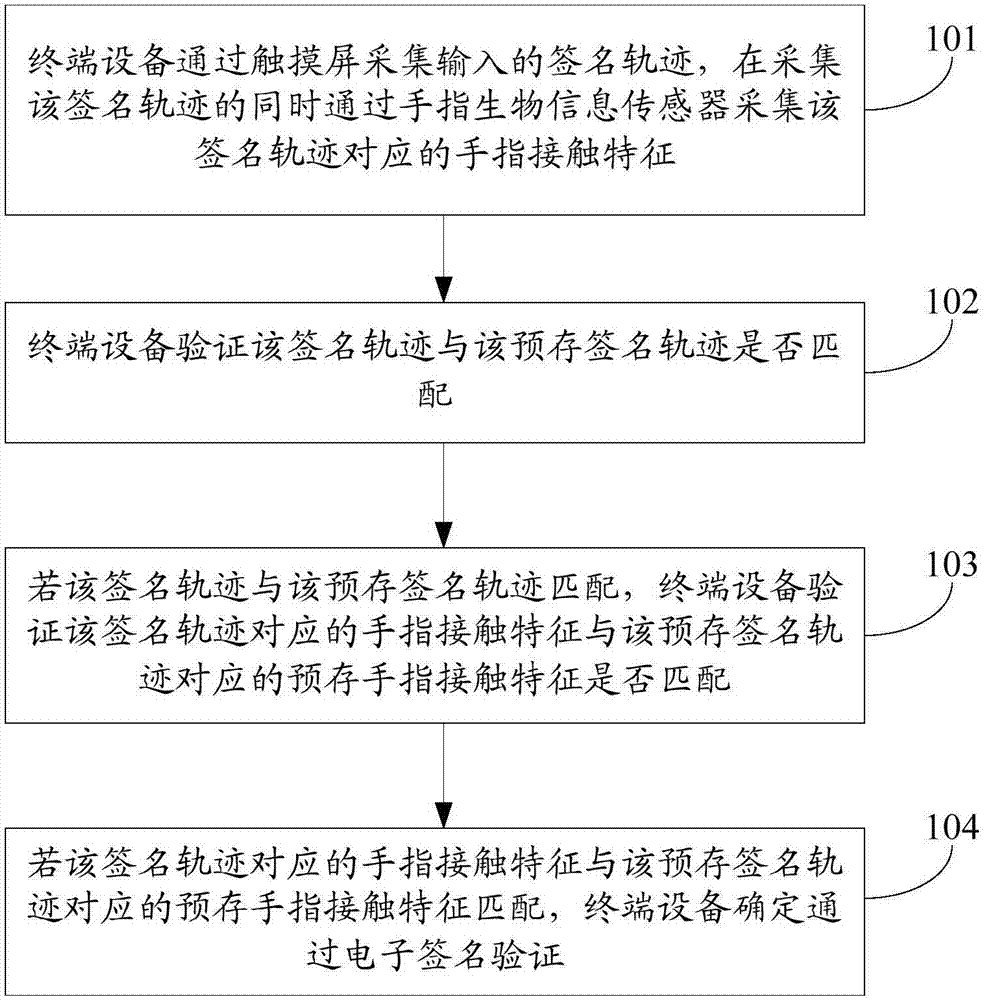
InactiveCN107992803APrevent imitationPrevent theftKey distribution for secure communicationUser identity/authority verificationValidation methodsTerminal equipment
The embodiment of the invention discloses an electronic signature verification method, terminal equipment and a computer readable medium. The method is applied to the terminal equipment which containsa finger biological information sensor in a touch screen. The method comprises the following steps that: through the touch screen, collecting an input signature trajectory, and while the signature trajectory is collected, collecting a finger contact feature corresponding to the signature trajectory through the finger biological information sensor; verifying whether the signature trajectory is matched with a pre-stored signature trajectory or not; if the signature trajectory is matched with the pre-stored signature trajectory, verifying whether the finger contact feature corresponding to the signature trajectory is matched with a pre-stored finger contact feature corresponding to the pre-stored signature trajectory or not; and if the finger contact feature corresponding to the signature trajectory is matched with the pre-stored finger contact feature corresponding to the pre-stored signature trajectory, determining the signature trajectory passes electronic signature verification. By use of the electronic signature verification method of the embodiment of the invention, the use safety of the electronic signature can be improved.
Owner:SHENZHEN GIONEE COMM EQUIP
Casino chip with antitheft and antiforgery tag circuit and manufacturing method thereof
InactiveUS20070060304A1Effectively preventing theftPrevent imitationCoin testingApparatus for meter-controlled dispensingElectronic securityTransmitter
Disclosed is a casino chip with an antitheft and antiforgery function and a method of manufacturing such chips. The casino chip is provided with an RF tag circuit which is capable of exposing an offender, by means of an electronic security system consisting of transmitters and receivers, when the offender steals authorized chips from a casino or wrongfully uses forged chips in the casino. The tag circuit (30) is not damaged because the tag circuit is protected by a preform (10, 20, 40, 50) even though the preform comprising the thin tag circuit, which is susceptible to high temperatures, is subjected to an insert-injection molding step, thereby preventing theft of the casino chip.
Owner:JEON RAN SOOK
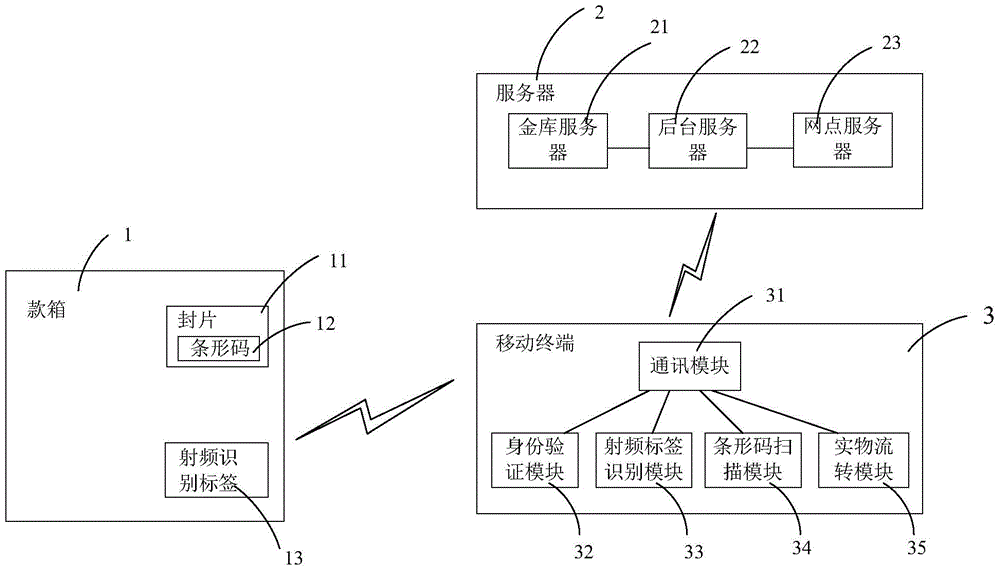
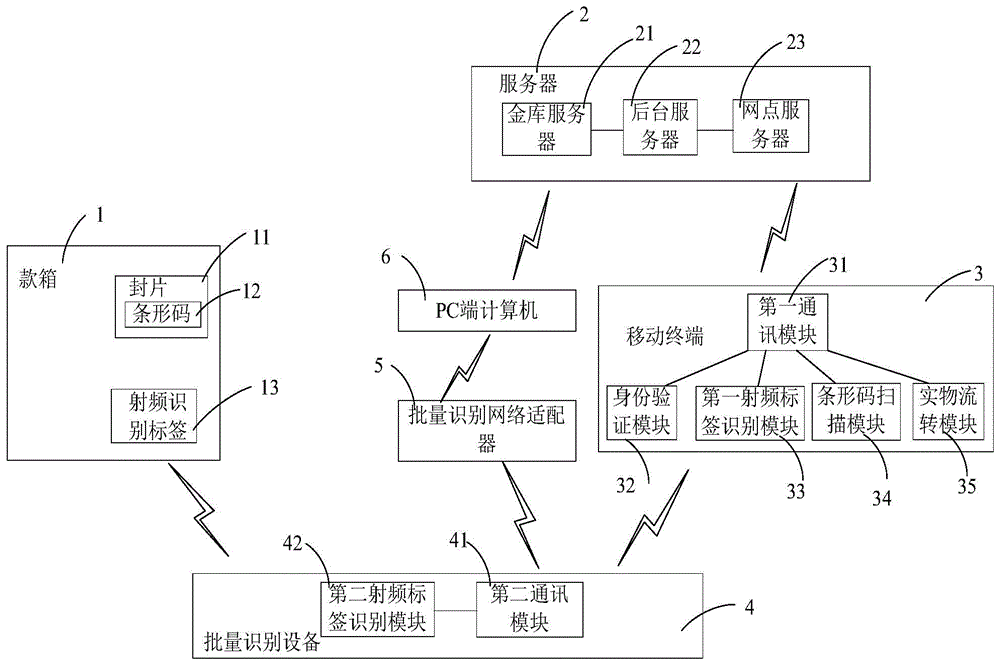
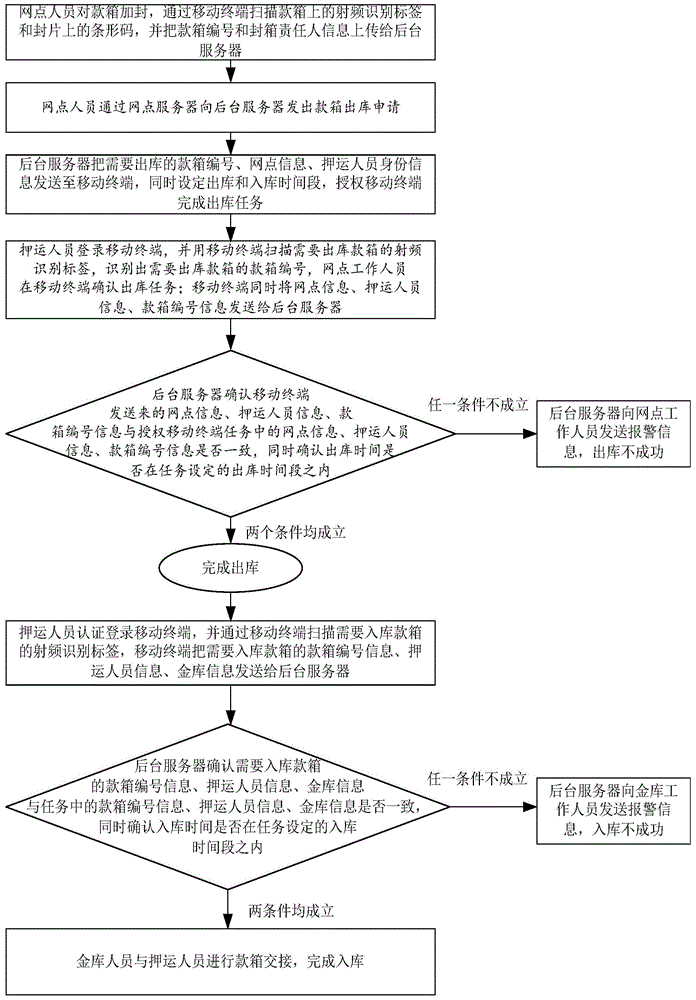
Physical flow system and physical flow method for bank cash box management
The invention discloses a physical flow system for bank cash box management. The system is mainly composed of a cash box (1), a mobile terminal (3) connected with the money box (1) through a network, and a server (2) connected with the mobile terminal (3) through the network. The system is characterized in that the cash box (1) is provided with a radio frequency identification tag (13), and a sealing piece (11) provided with a barcode (12) and used for sealing a keyhole of the cash box (1) is arranged on the keyhole. The invention further discloses a physical flow method of the physical flow system for bank cash box management. In the process of cash box transfer, people, box, lock and task binding can be realized, and a backend server carries out monitoring in a unified way. Therefore, manual record of warehousing-in and warehousing-out information is avoided, the safety is improved, and the manpower cost is reduced.
Owner:SGSG SCI & TECH CO LTD
Multifunctional distributed intelligent access control system using IC card or dynamic password
InactiveCN106600773ASimple structureImprove reliabilityIndividual entry/exit registersPasswordSecret code
The invention relates to a multifunctional distributed intelligent access control system using an IC card or dynamic password, relates to cloud intelligent Internet-of-Things household door locks, and belongs to the field of Internet of Things. The system is mainly composed of a management center server, an embedded access control terminal control module, a communication channel, an access control member mobile phone and the like. An operation method comprises the steps: a user accesses a WeChat public number through a mobile phone and submits a registration request, and after the registration is successful, the system can randomly generate a dynamic password; and then the user-obtained dynamic password is inputted to an access control host, a legal unlocking authorization is emitted, a user unlocking record is saved, and ultimately, the user unlocks the access control system. The system has the innovation that convenient standby support is provided for conditions that a card is lost and a user cannot enter a door with forgetting to take the card, and the system is convenient for daily life; on the other hand, the card can be prevented from being copied and being stolen for use, the important gateway card and code multiple authentication remote access control authorization management and control can be realized, and the access control reliability and safety are further improved.
Owner:HARBIN UNIV OF SCI & TECH
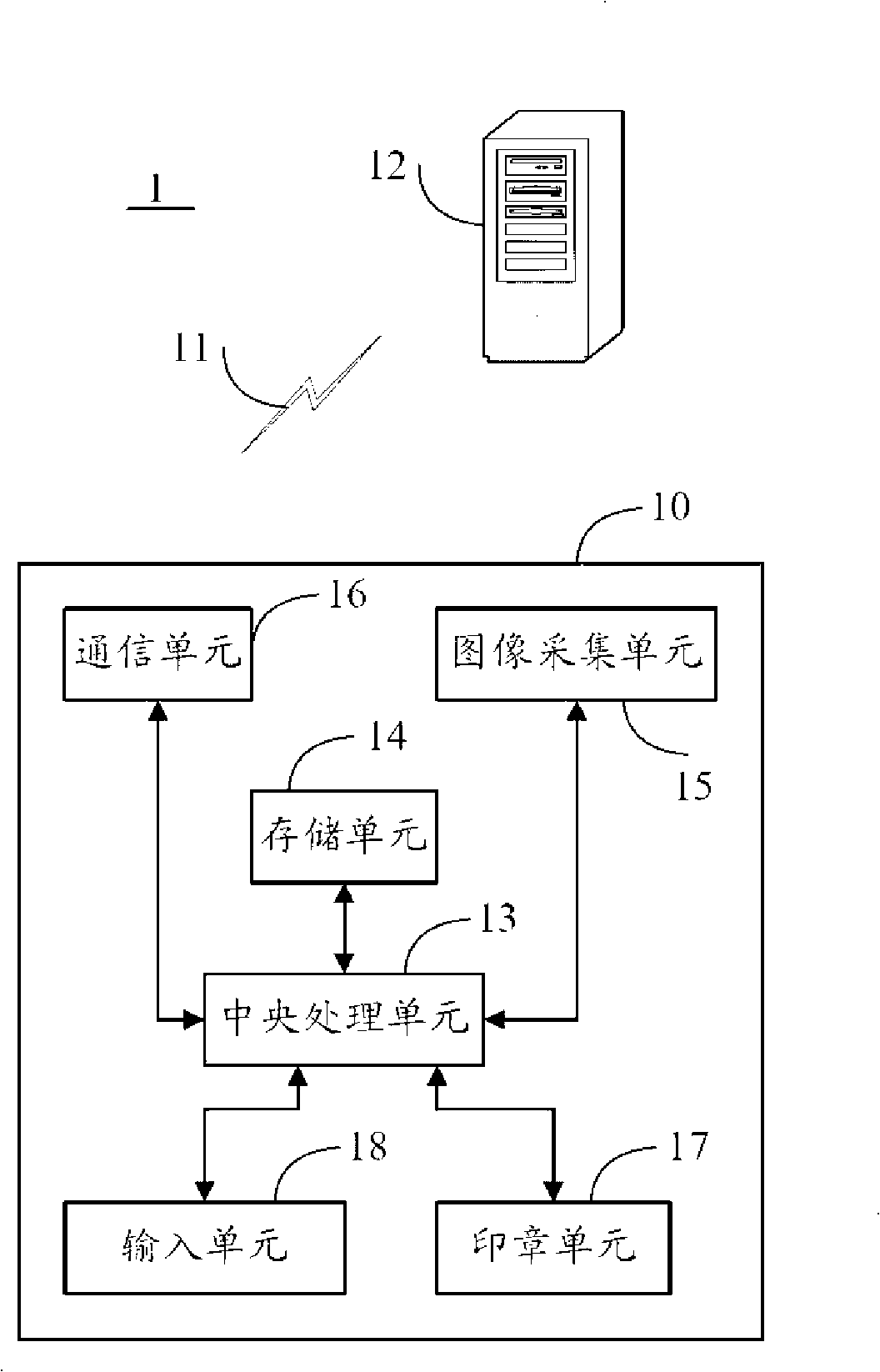
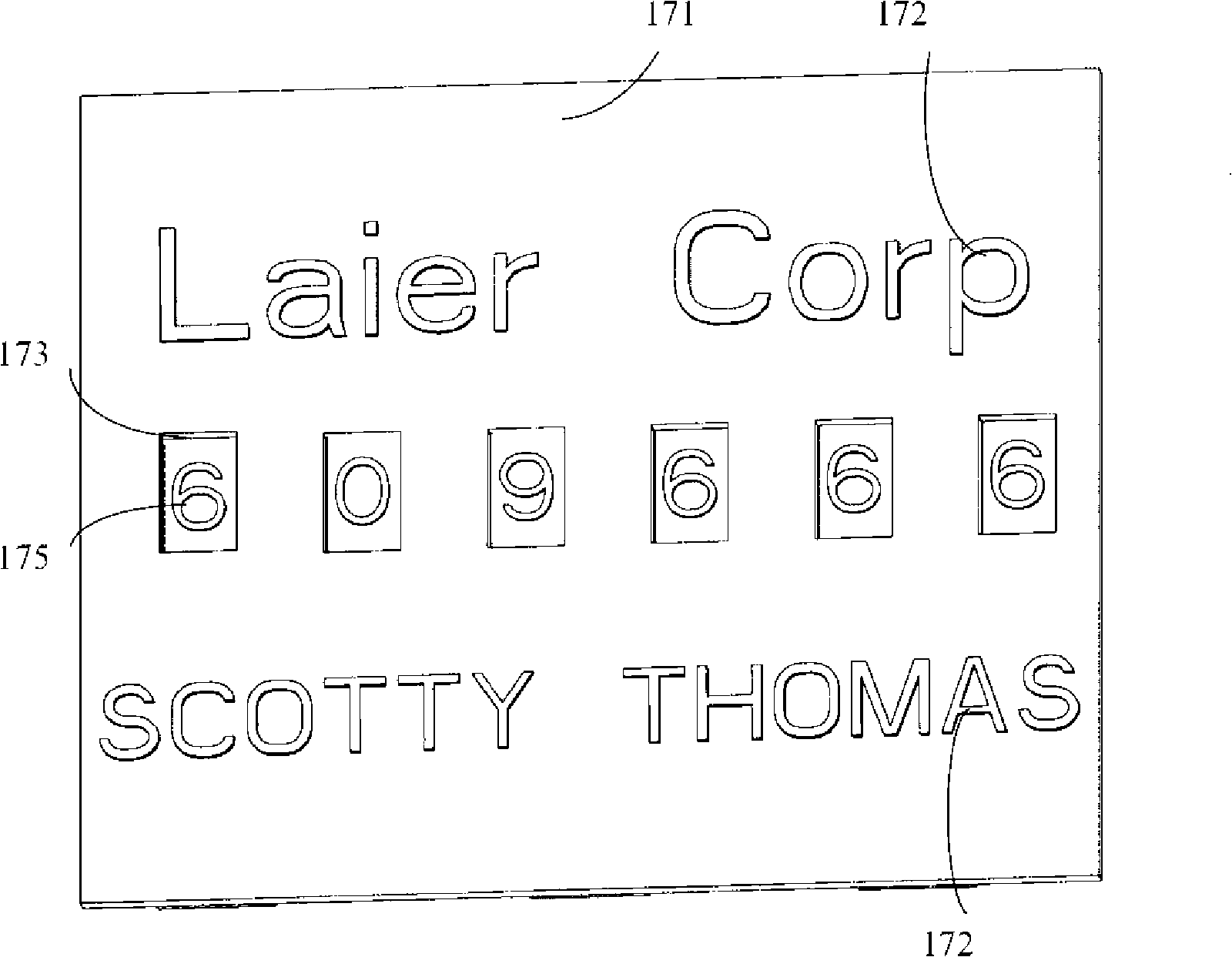
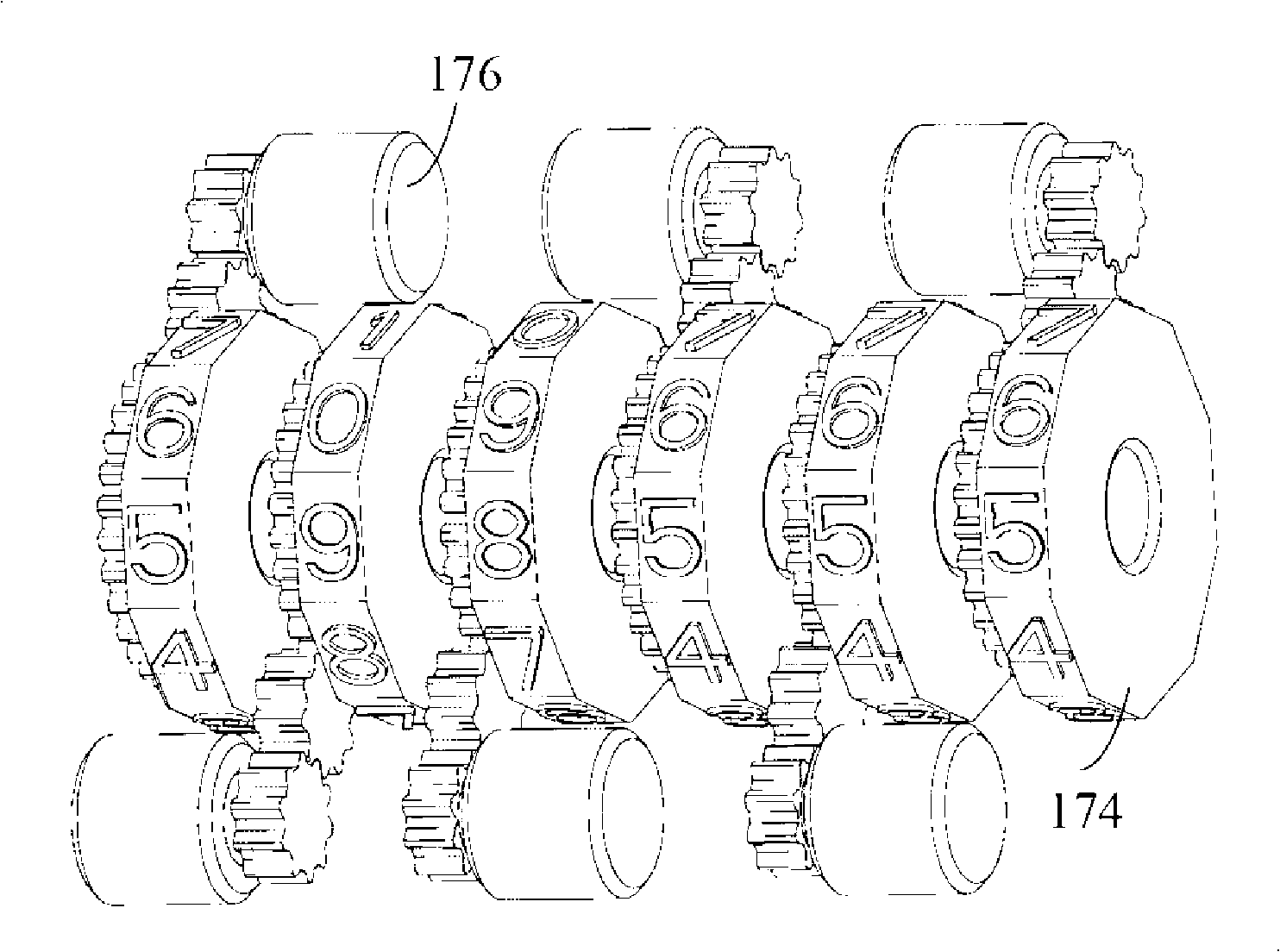
Handhold apparatus with signature function and method for signing using the same
ActiveCN101329705AEasy to sign forPrevent imitationSpecial data processing applicationsStampingHand held devicesUnit response
The invention provides a handheld device with signing function, which comprises a central processing unit, a memory unit, an input unit and a signature unit. The central processing unit responses to a signing command which is input by the input unit to generate a file identification code, and generates a control command according to the file identification code which is a unique group of codes corresponding to each approved file; the signing unit responses to the control demand of the central processing unit and generates a group of codes matching with the file identification code; the central processing unit responses to the signing confirmation command which is input by a user, generates and memorizes the record of the signing information of the file signed. Simultaneously, the invention provides a method for using the handheld device to sign. The device and the method are convenient for a signing person to sign on a paper file and generate signing records.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
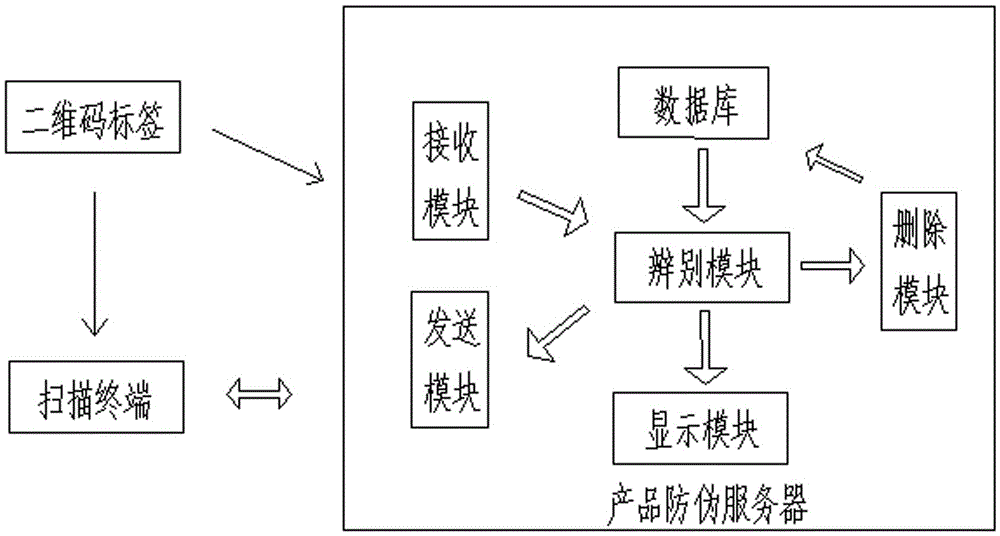
Uncopy two-dimension code anti-fake system based on one-time identification and realization method
PendingCN105528709AImprove anti-counterfeiting performancePlay the role of publicityCommerceRecord carriers used with machinesProgramming languageEncryption
The invention discloses an uncopy two-dimension code anti-fake system based on one-time identification, comprising a two-dimension code generation unit based on encryption information, a two-dimension code printing unit, a two-dimension code label, a scanning terminal and a product false proof server. The product false proof server comprises a database, a reception module, a discrimination module, a transmission module and a deleting module. The two-dimension code contains encryption information which can be randomly variable and an anti-fake function of the two-dimension code is added; the two-dimension code information stored in the database can be eliminated after the two-dimension code is scanned for one time by a scanning terminal; the two-dimension code anti-fake system can remind the consumer that the invalid information of two-dimension code, the manufacture or the advertisement of the product when scanning the two-dimension code again. The invention puts an end to the fact that the illegal vendor copies the two-dimension code, plays an important role of preventing counterfeiting and also plays a role of propagating the manufacture.
Owner:赵凯泽
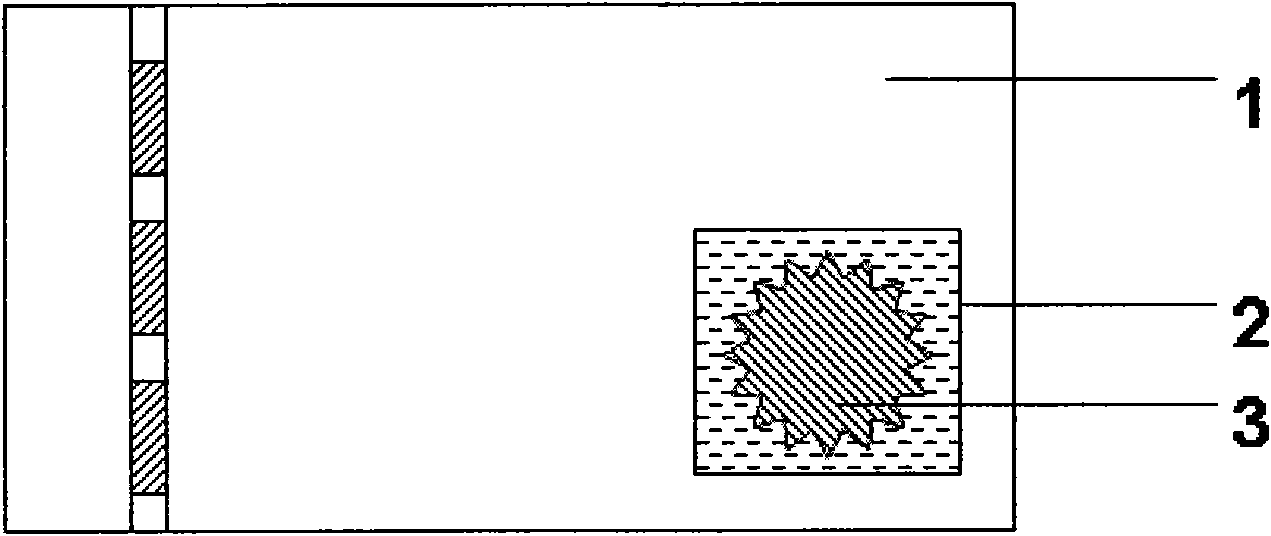
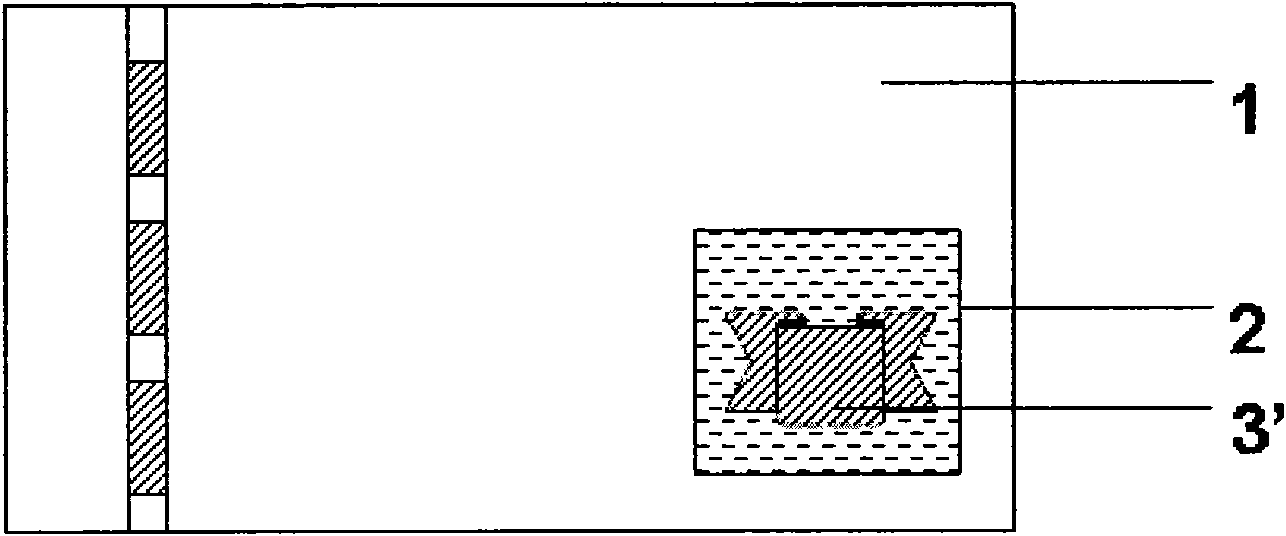
Security paper and a method for the production thereof
InactiveCN101171145AWith optical effectPaper Thickness ReductionNon-fibrous pulp additionOther printing matterPaper productionPulp and paper industry
The invention relates to a security paper for producing security or value documents such as banknotes, identity cards and the similar comprising at least two through holes (12, 16). According to said invention, the first through hole (12) is embodied during paper production and comprises characteristic irregularities on the edge area thereof (14) whereas the second hole (16) is embodied after thepaper production by cutting out or punching and is provided with a sharply outlined edge area (18).
Owner:GIESECKE & DEVRIENT CURRENCY TECHNOLOGY GMBH
Anti-counterfeiting system
InactiveCN107590663APrevent theftAvoid imitationCo-operative working arrangementsCommerceLibrary scienceCode reading
The invention discloses an anti-counterfeiting system, which comprises an anti-counterfeiting label, an intelligent terminal and an anti-counterfeiting server, wherein the anti-counterfeiting label isassociated with product information and is embedded on the package of the product and is invisible; the intelligent terminal is internally provided with a code reading module and is wirelessly sensedwith the anti-counterfeiting label, and the intelligent terminal is used for reading the product information in the anti-counterfeiting label and transmitting the product information to the anti-counterfeiting server; and the anti-counterfeiting server stores multiple items of certified product information and is in communication connection with the intelligent terminal. According to the anti-counterfeiting system provided by the invention, the anti-counterfeiting label is invisible and the anti-counterfeiting server and the intelligent terminal do not display the specific product informationor the certified product information and only display the true and false information, the anti-counterfeiting label and the product information associated with the anti-counterfeiting label can be effectively prevented from being stolen or copied, and a counterfeited or forged product can be efficiently recognized.
Owner:米格(浙江)创新科技有限公司
Method and device for authenticating terminal as well as EOC (Ethernet over Coax) terminal
InactiveCN102137074APrevent imitationLow costData switching by path configurationEthernet over coaxTerminal cost
The invention relates to a method and device for authenticating a terminal as well as an EOC (Ethernet over Coax) terminal. The method for authenticating the terminal comprises the following steps of: acquirement: acquiring characteristic domain information of the EOC terminal and first encryption control domain information which is prestored in the EOC terminal and generated according to a preset key and encryption algorithm based on the characteristic domain information; calculation: generating second encryption control domain information according to the preset key and encryption algorithm based on the characteristic domain information; and authentication: judging whether the first encryption control domain information and the second encryption control domain information accord with the preset authentication passing rule or not, allowing the EOC terminal to pass the authentication if the first encryption control domain information and the second encryption control domain information accord with the authentication passing rule; or otherwise, not allowing the EOC terminal to pass the authentication. The invention can achieve the purpose of carrying out the authentication control on the terminal on the basis of not increasing the terminal cost.
Owner:NEW H3C TECH CO LTD
Data transmission methods, terminals, storage medium and processor
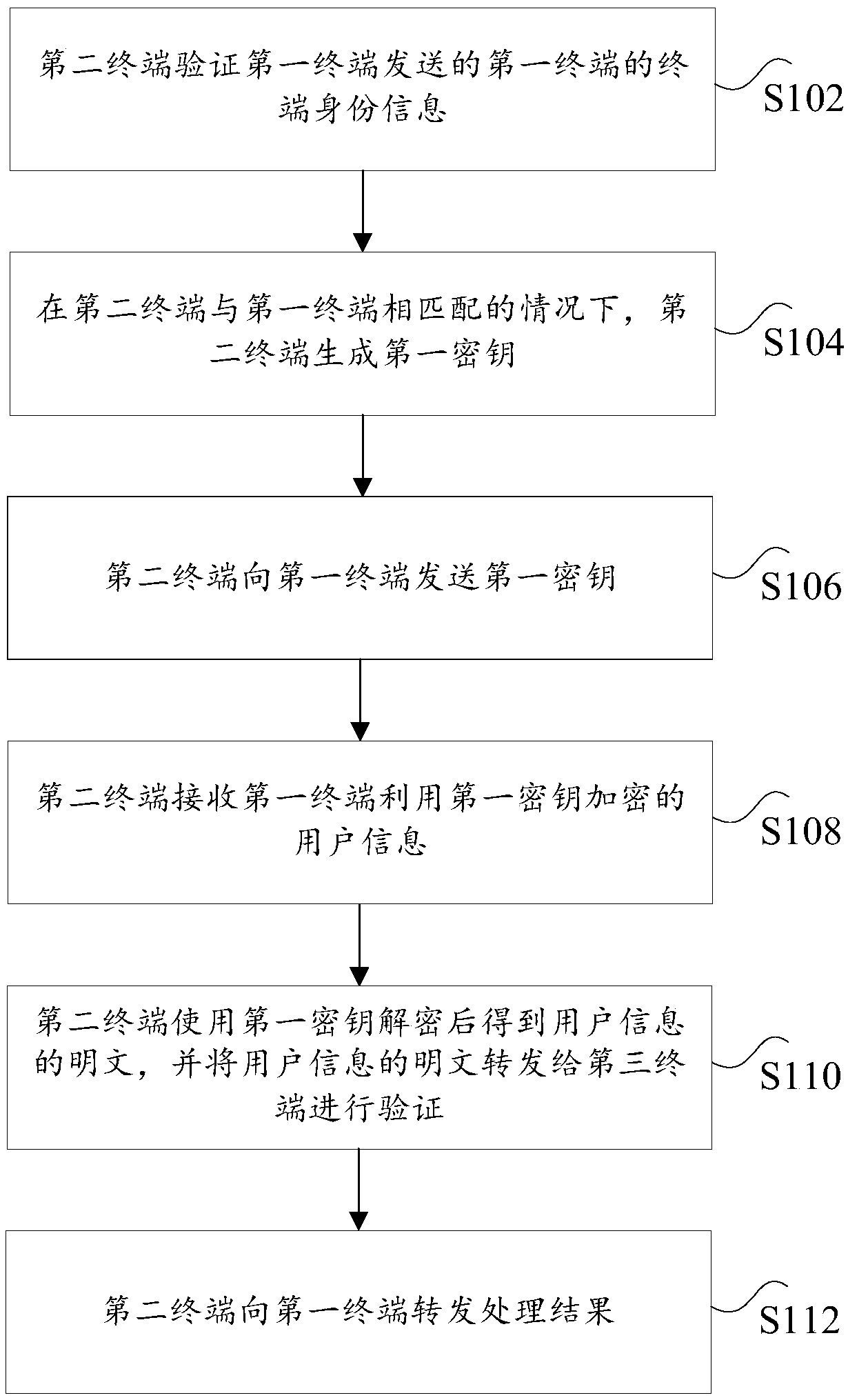
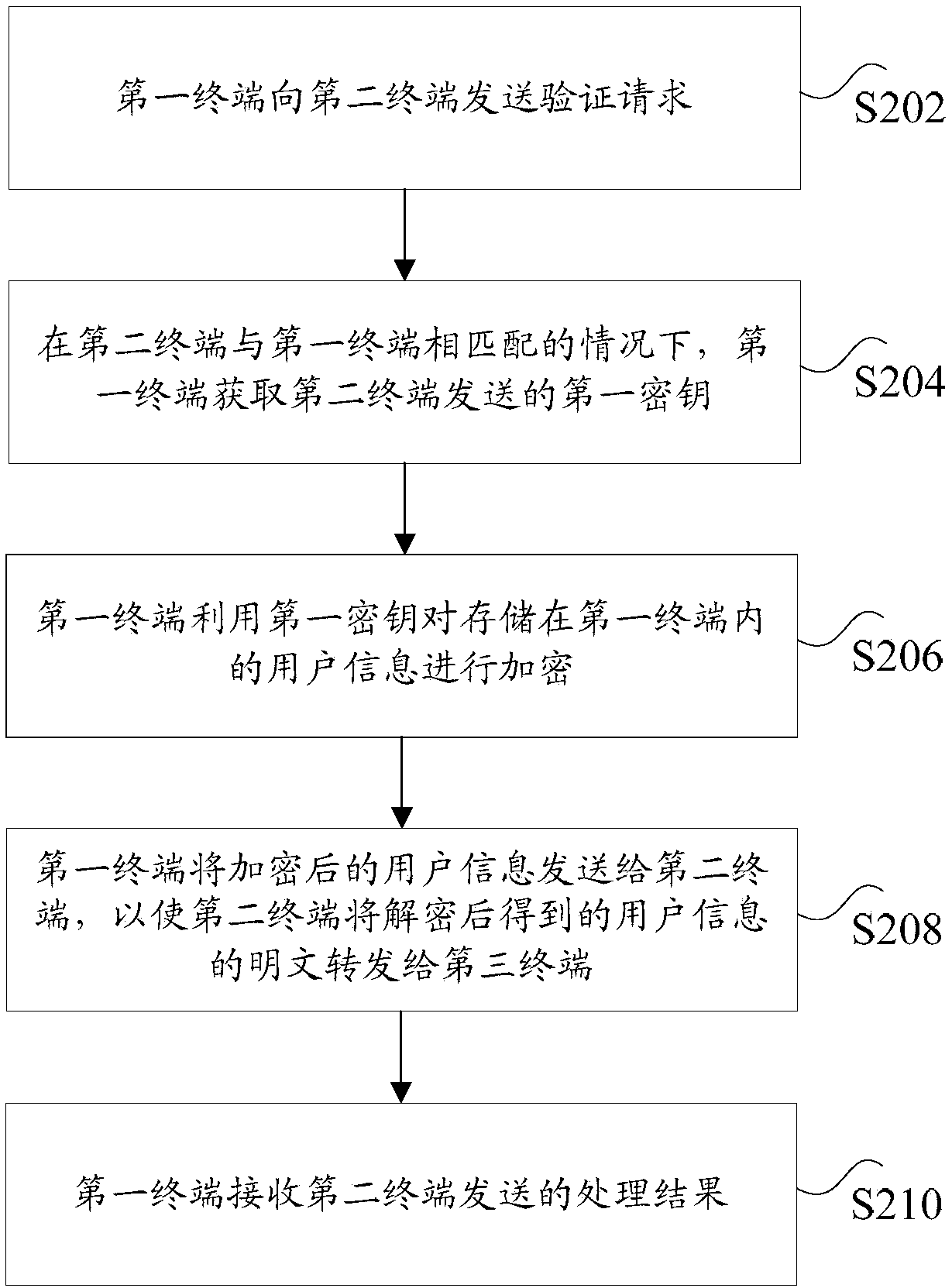
InactiveCN109429203APrevent imitationAvoid crackingIndividual entry/exit registersSecurity arrangementPlaintextComputer terminal
The invention discloses data transmission methods, terminals, a storage medium and a processor. The method includes: sending a verification request by a first terminal to a second terminal, wherein the verification request is used for verifying whether the second terminal matches the first terminal; acquiring a first key, which is sent by the second terminal, by the first terminal, in a case wherethe second terminal matches the first terminal; using the first key by the first terminal to encrypt user information stored in the first terminal; and sending encrypted user information by the firstterminal to the second terminal to enable the second terminal to forward user information plaintext, which is obtained after decrypting, to a third terminal, wherein the third terminal processes theplaintext of the user information, and then returns a processing result to the second terminal, then the second terminal sends the returned processing result to the first terminal, and the first terminal receives the processing result sent by the second terminal. The method solves the technical problem of relatively low transmission security of existing data transmission technology.
Owner:KUANG CHI INTELLIGENT PHOTONIC TECH
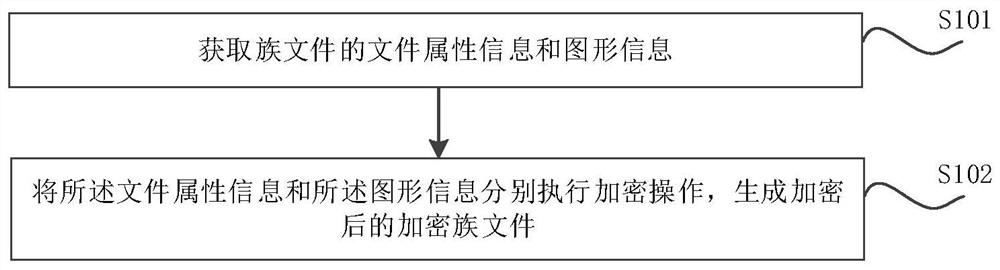
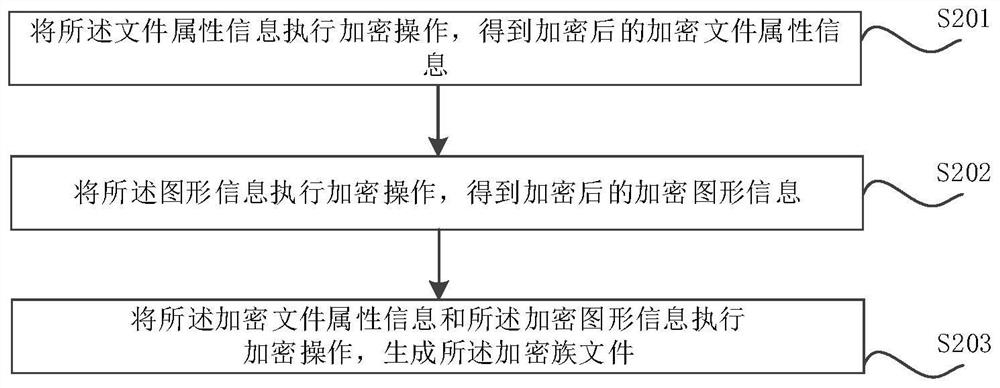
Family file processing method and device, computer equipment and storage medium
ActiveCN111832031AImprove confidentialityImprove securityDigital data protectionProgramming languageGraphics
The invention relates to a family file processing method and device, computer equipment and a storage medium. The method comprises the steps of obtaining file attribute information and graphic information of family files; and respectively executing encryption operation on the file attribute information and the graphic information to generate an encrypted encrypted family file, wherein the file attribute information is used for representing an object specification in the family file; wherein the graphic information is used for representing visual features of the family files; therefore, when the encrypted family file is loaded into the project and is in a family editing mode; the file attribute information is encrypted; therefore, information such as object specifications in the family filecannot be obtained; the confidentiality of family files is realized; in addition, due to the fact that the graphic information is encrypted, normal geometric figures of the objects cannot be displayed in the family editing mode, users who are not allowed to check the geometric figures of the family files are prevented from imitating the geometric figures of the family files, the safety of the family files is greatly improved, and the loss of labor achievements of designers is avoided.
Owner:久瓴(上海)智能科技有限公司
Valuable document
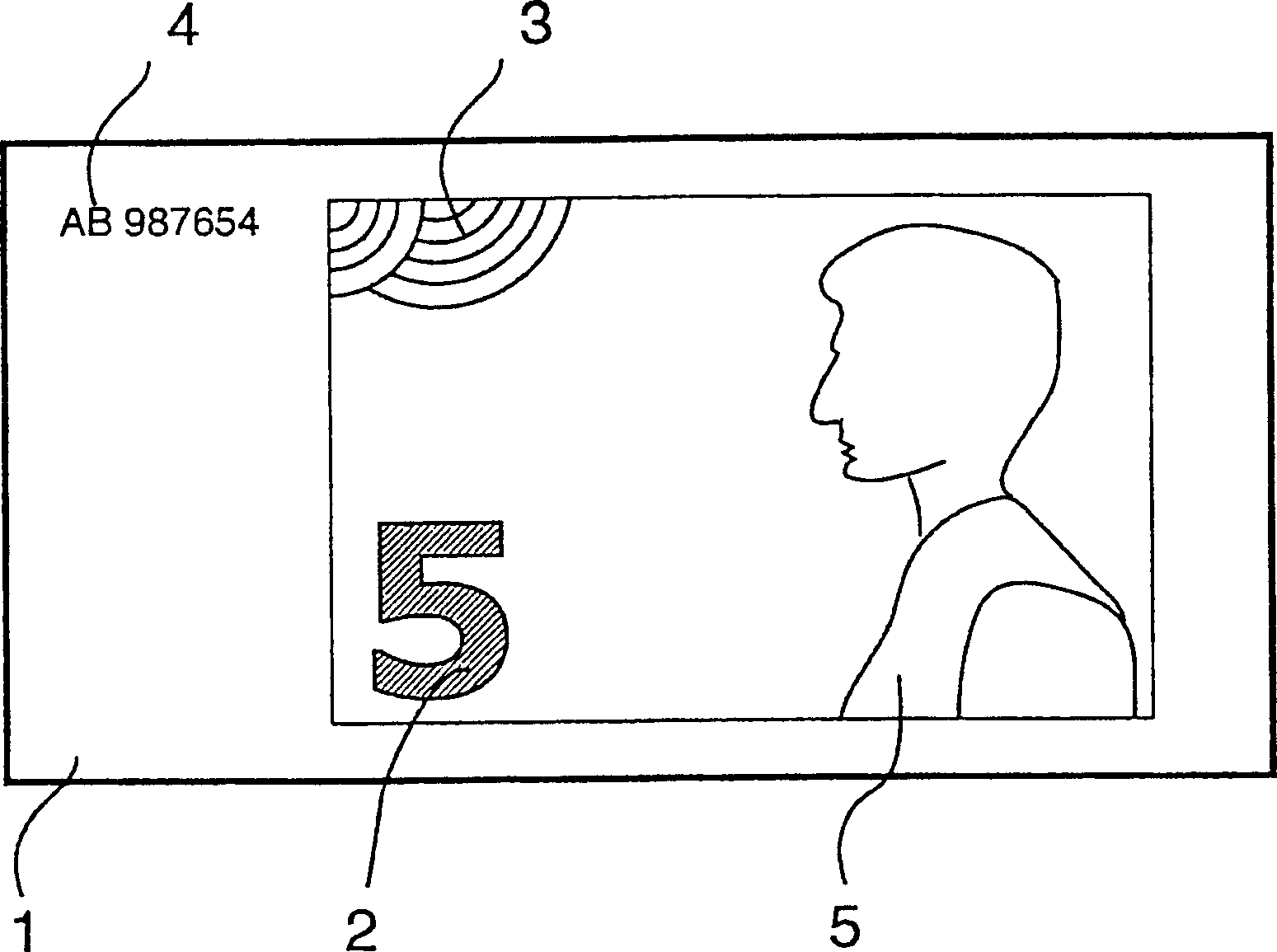
InactiveCN1605089AImprove inspection effectPalpableOther printing matterPaper-money testing devicesComputer graphics (images)Paper document
Owner:GIESECKE & DEVRIENT GMBH
Bank automated teller machine authentication method and system
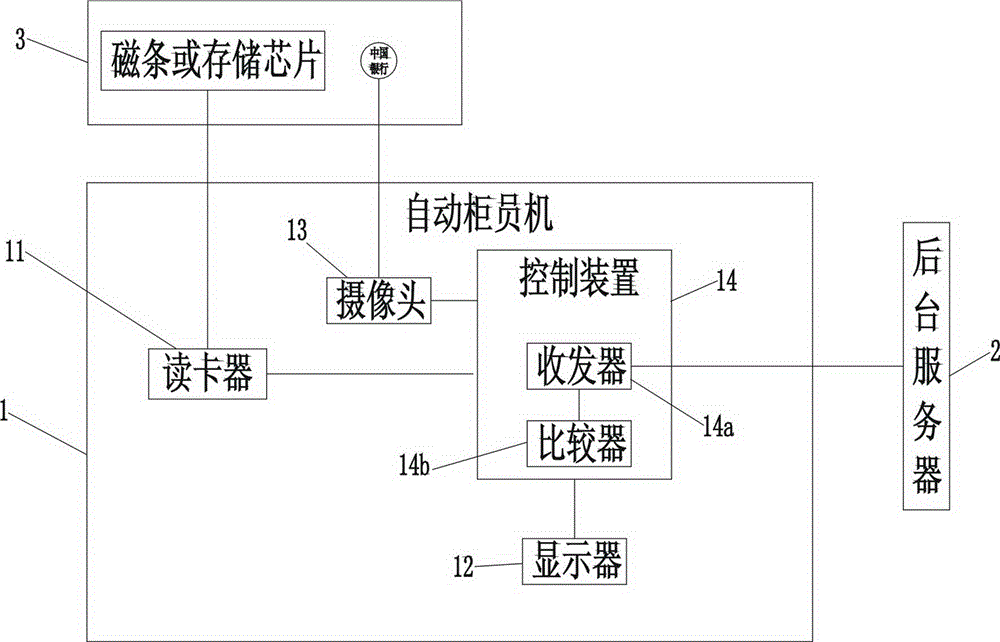
ActiveCN104574696AEliminate counterfeitingPrevent counterfeitingComplete banking machinesDigital data authenticationPressure castingTransceiver
The invention discloses a method and a system of preventing stealing by counterfeiting or copying bank cards of card holders. The system is characterized in that a bank card is provided with a recess, a lead weight is press-fitted into the recess, the surface of the lead weight is provided with a seal by pressure casting, a background server stores account information and seal image data, and an automated teller machine is internally provided with a camera, a card reader, a transceiver and a comparator; during withdrawal or transfer, the system performs operations: the card reader reads the account information of the bank card, the camera shoots the surface of the lead weight in the bank card to acquire surface image data, the transceiver reads the corresponding seal image data from the background server according to the account information, the comparator compares the surface image data with the seal image data, withdrawal or transfer is allowed if the data are consistent and is avoided if the data are inconsistent. Even after an account number and a password are stolen, a criminal is unable to steal by counterfeiting the bank card; meanwhile, a protective means of protecting capital security in case of robbery is further provided.
Owner:余炳顺
Writing handwriting identification system and method
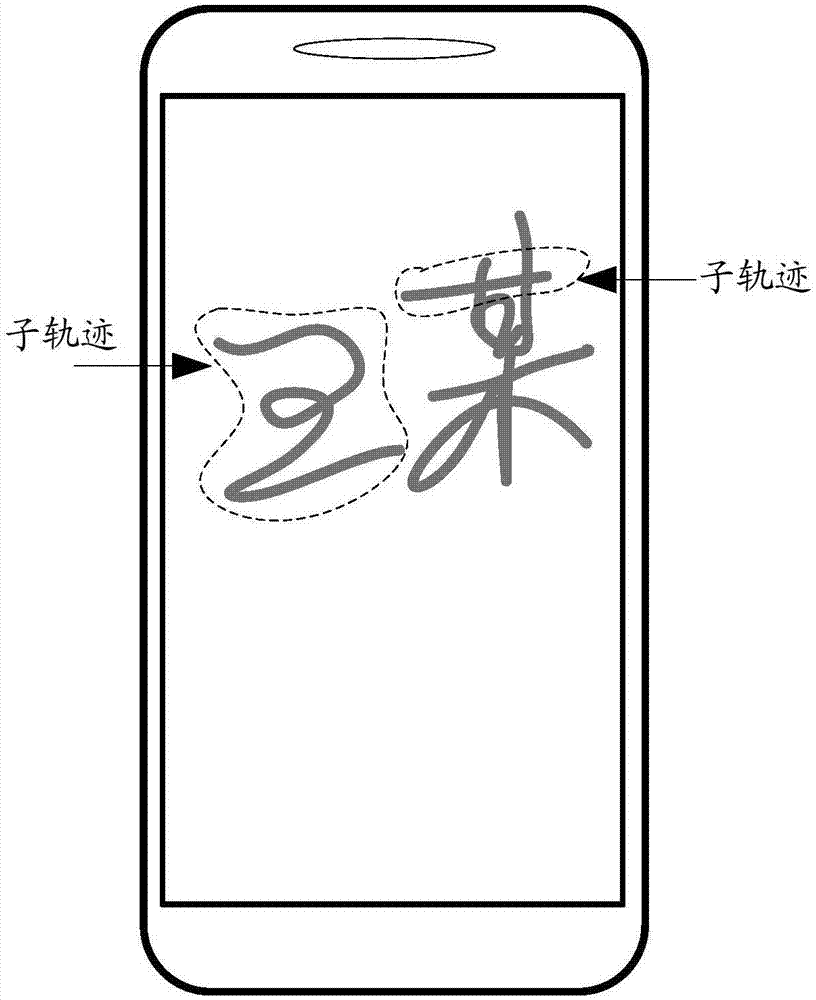
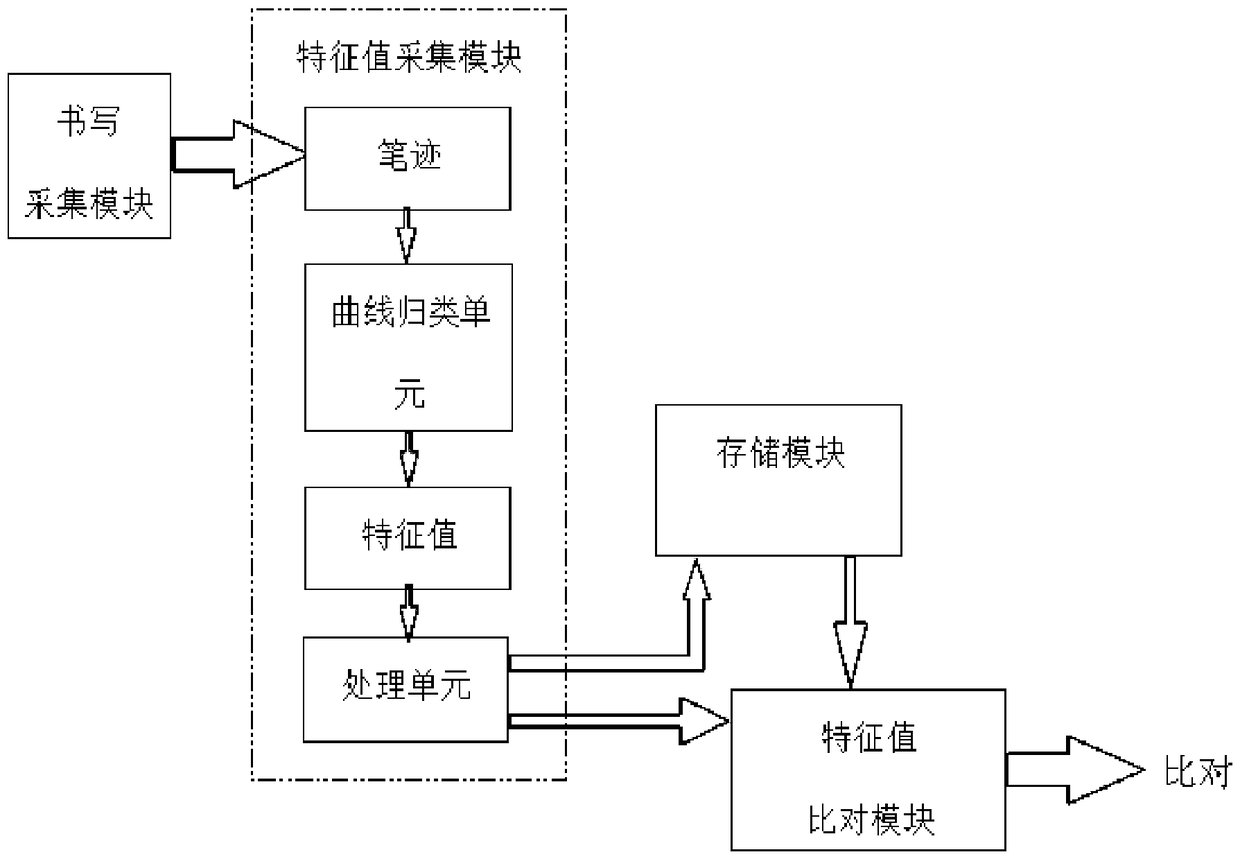
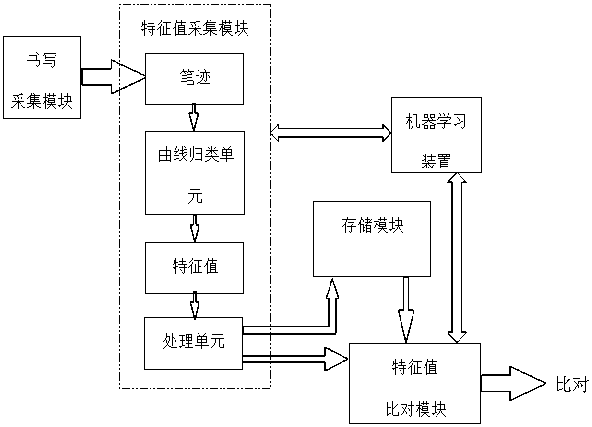
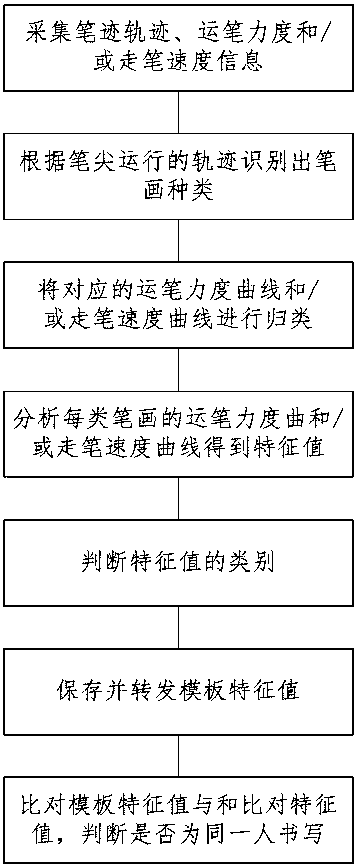
InactiveCN108416249APrevent imitationHigh identification accuracyCharacter and pattern recognitionHandwritingComputer graphics (images)
The present invention discloses a writing handwriting identification method. The method comprises the steps of: collecting brushstroke force, writing speed and a handwriting track to generate a brushstroke force curve and / or writing speed curve when a writer is writing, a handwriting identification unit is configured to distinguish the types of strokes through identification of a nib moving trackto classify the obtained brushstroke force curve and / or writing speed curve according to the types of strokes and extract feature values which can best differ from other persons, wherein the obtainedfeature values can be taken as a feature value template stored in a storage module, or can be taken a comparison feature value sent to a feature value comparison module for comparison with the featurevalue template. In the handwriting identification method, the brushstroke force and / or writing speed can be collected, and / or the brushstroke force curve and / or writing speed curve are generated in the handwriting identification method to perform analysis, because the brushstroke force and the writing speed are both writing features invisible to human eyes, and other persons cannot perform imitation, it can be prevented from imitation by other persons in any one way or both ways, and therefore, the discrimination accuracy can be improved.
Owner:肖奇
Self-contained two-dimensional code anti-fake medicine, and preparation method and identification method thereof
ActiveCN104095827APrevent imitationEnsure safetyPharmaceutical product form changePill deliveryPolyvinyl alcoholRadio frequency
The invention provides a self-contained two-dimensional code anti-fake medicine, and a preparation method and an identification method thereof, and belongs to the technical field of biological medicine preparation. According to the preparation method, a micro-processing technology is adopted to perform two-dimension code structure processing on a substrate, the polydimethylsiloxane is adopted to perform antagonizing model on a base plate with the two-dimension code structure to obtain a solid mould for preparing the medicine, the polyvinyl alcohol with the molecular weight of 80,000 to 120,000 is poured into the mould to form a medicine-contained coating, then a medicine solution is poured, and drying is carried out to obtain the self-contained two-dimensional code medicine. The self-contained two-dimensional code medicine provided by the invention can be applied to the anti-fake field of medicines, and has the advantages that firstly, the medicine can directly carry anti-fake information per se to avoid a re-imitation problem of printed paper labels; secondly, the influence of the traditional radio frequency identification (RFID) technology on safety and effectiveness of electronic tags is avoided; finally, an anti-fake process of the medicine and an identification process of the medicine are further simplified, thereby being rapid and low in cost.
Owner:TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com