Encryption and decryption methods of embedded software program
A technology of embedded software and encryption method, which is applied in the field of encryption and decryption, can solve problems such as difficult to prevent malicious refresh and decryption failure, and achieve the effect of ensuring security and strong flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] At first, explain the inventive idea:
[0041] (1) Anti-imitation:
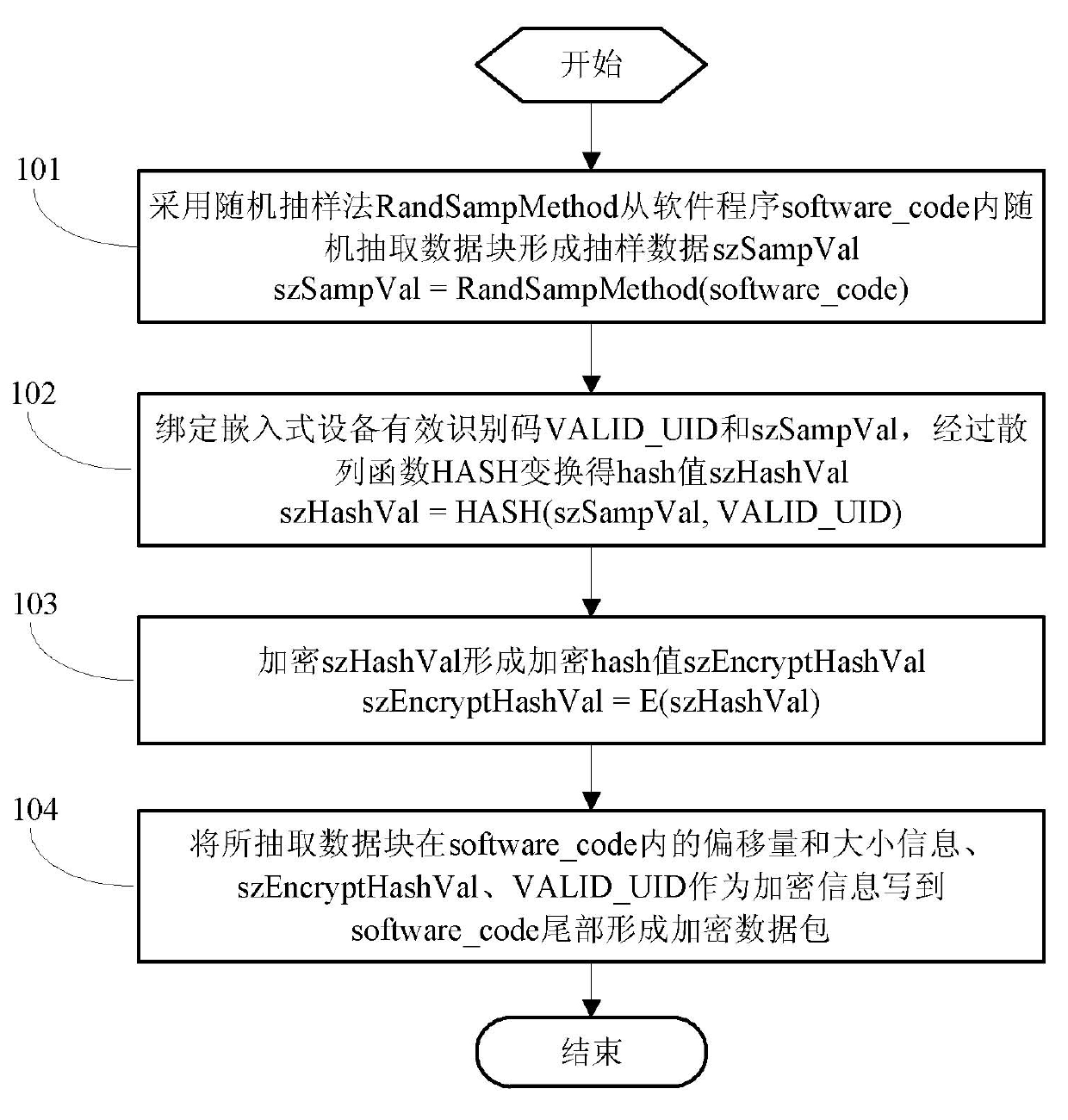
[0042] When downloading the embedded software program to the storage medium of the embedded device, execute the encryption process described in the present invention, and download the encryption program into the storage medium of the embedded device;
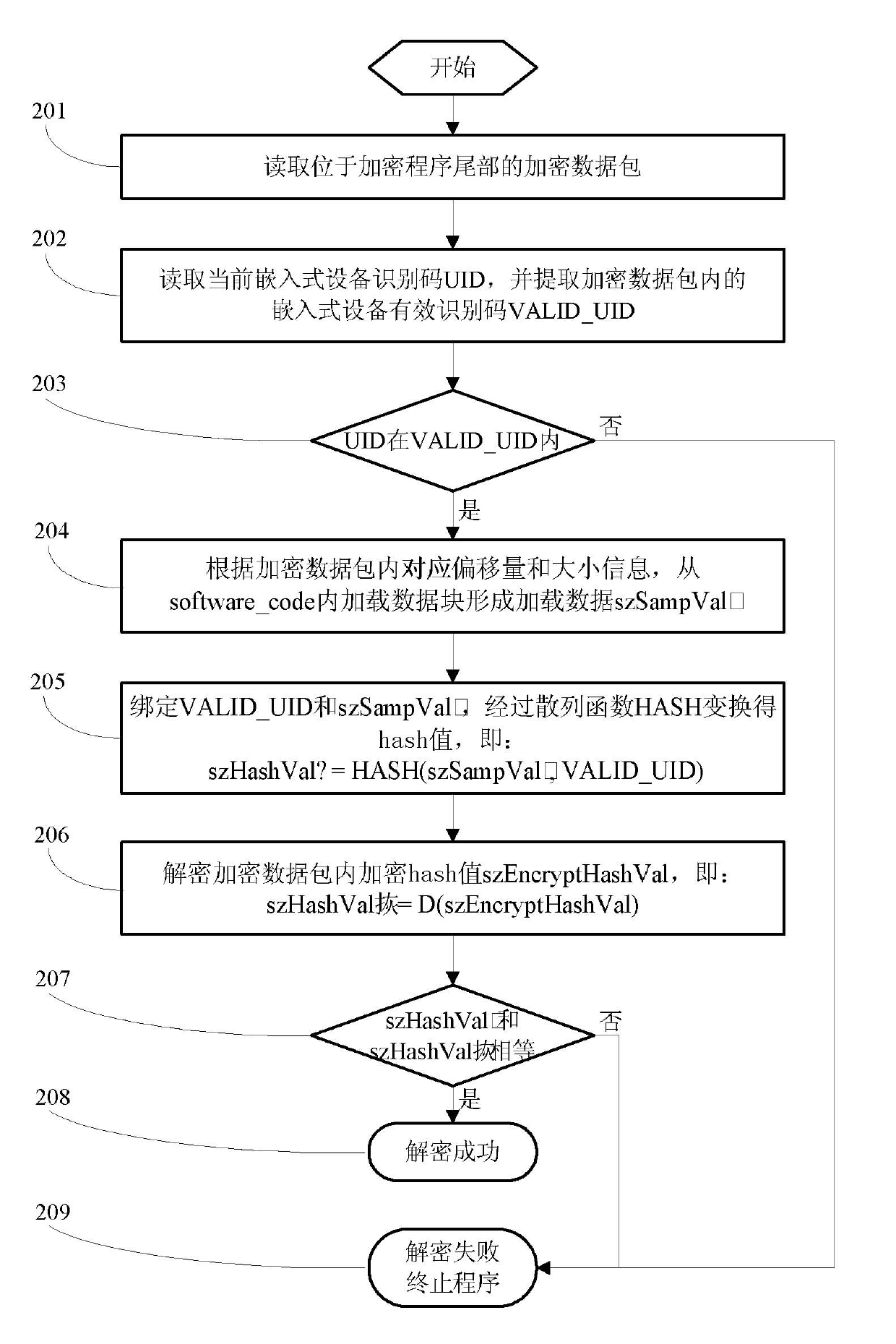
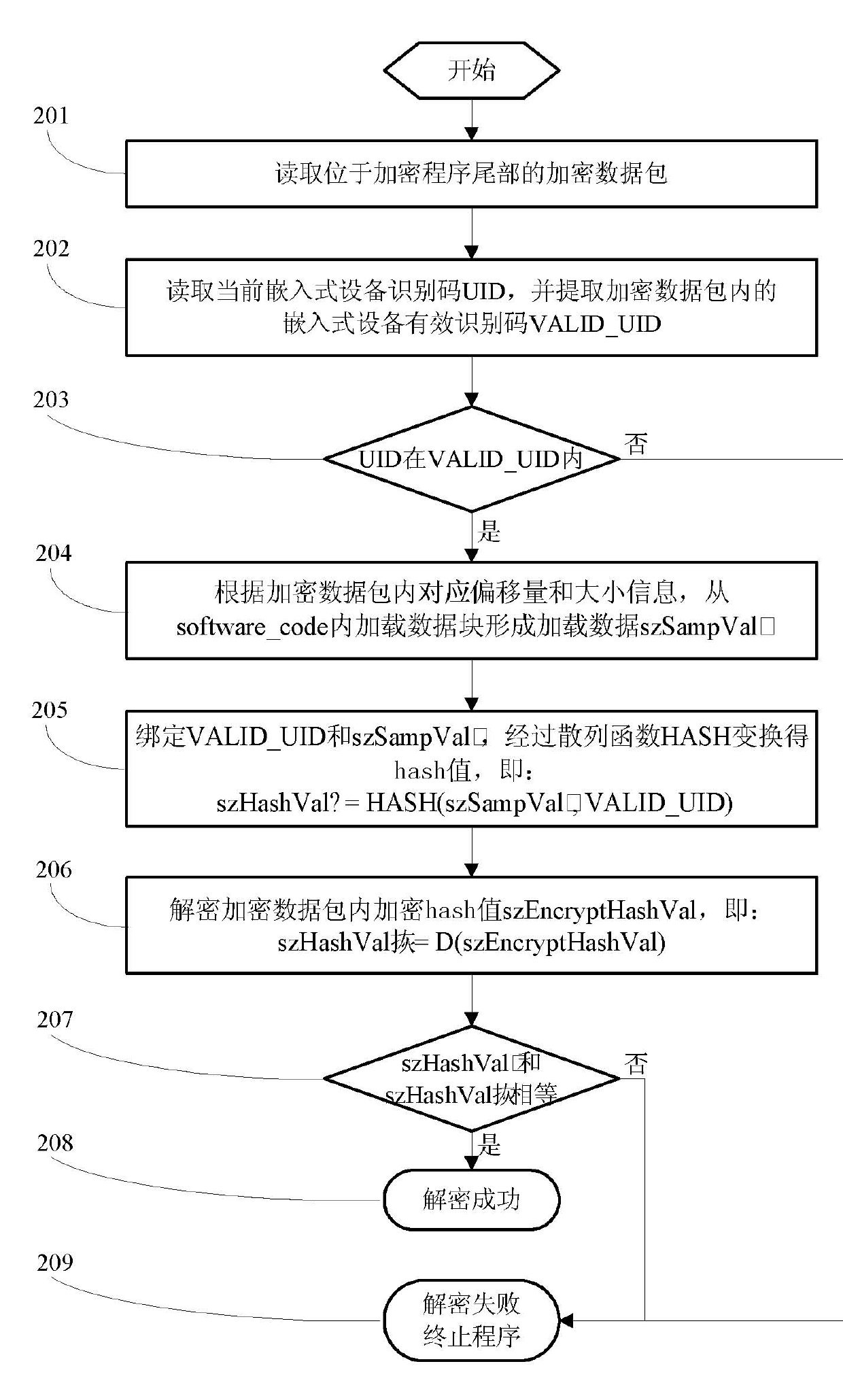
[0043] When the encryption program in the storage medium is loaded during the startup process of the embedded device, the decryption process described in the present invention is executed. If the decryption is successful (ie: the embedded device is our authorized device), continue to start, and if the decryption fails, exit Start the process.
[0044] (2) Anti-refresh:
[0045] When our embedded device downloads the program to the storage medium of our embedded device, it executes the decryption process described in the present invention. If the decryption is successful (that is, the downloaded program is our authorized encrypted program), the program ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com