Method and system for authenticating legality of receiving terminal in unidirectional network
A technology of legality authentication and receiving terminal, applied in the field of one-way digital transmission network to prevent imitation and cloning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
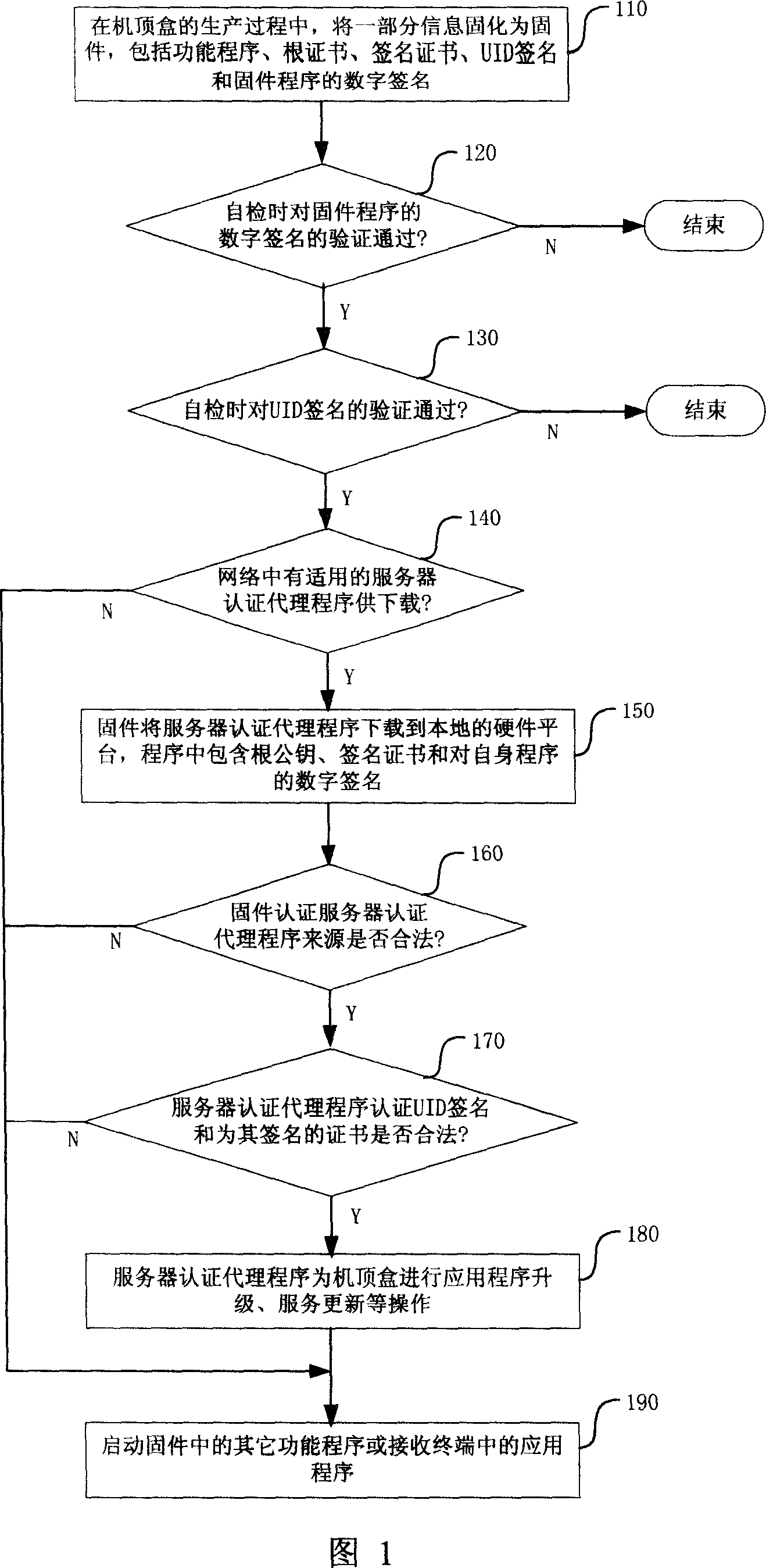
[0034] The digital signature and digital abstract technologies to be used in the present invention will be briefly introduced below.
[0035] Digital signature is a widely used digital security technology. It is based on asymmetric key algorithms and digital digests. The asymmetric key algorithm uses a pair of keys for encryption and decryption operations, public key encryption, private key solution, for confidentiality requirements; private key encryption, public key solution for non-repudiation requirements. If the information to be sent needs to be signed by the information sender, the private key of the information sender needs to be used for the signature operation, and the receiver can identify the identity of the information publisher only by verifying with the sender's public key. Commonly used public key algorithms include RSA, DSA, Diffie-Hellman, etc.
[0036] Digital digests apply a one-way mathematical function called a hash algorithm to data, and the result of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com