Dynamic encrypting device in network and its password identification method
A dynamic encryption and password technology, applied in secure communication devices, user identity/authority verification, instruments, etc., can solve problems such as stealing user passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
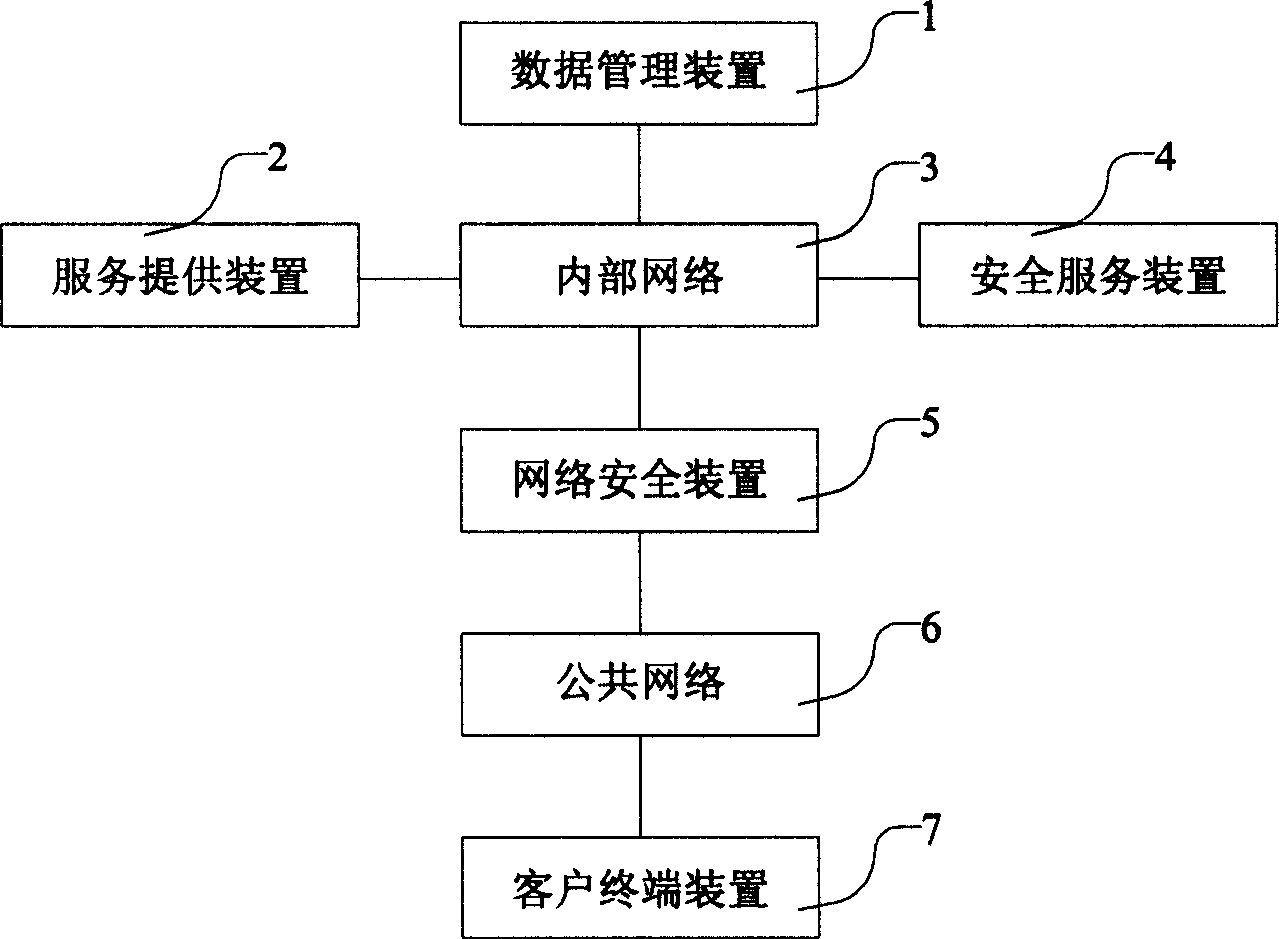
[0020] figure 1 Among them, the data management device 1 can be a PC server or a host computer, runs a database management system, stores enterprise data and customer information, such as user names, passwords, etc., and is responsible for customer access management after authentication.
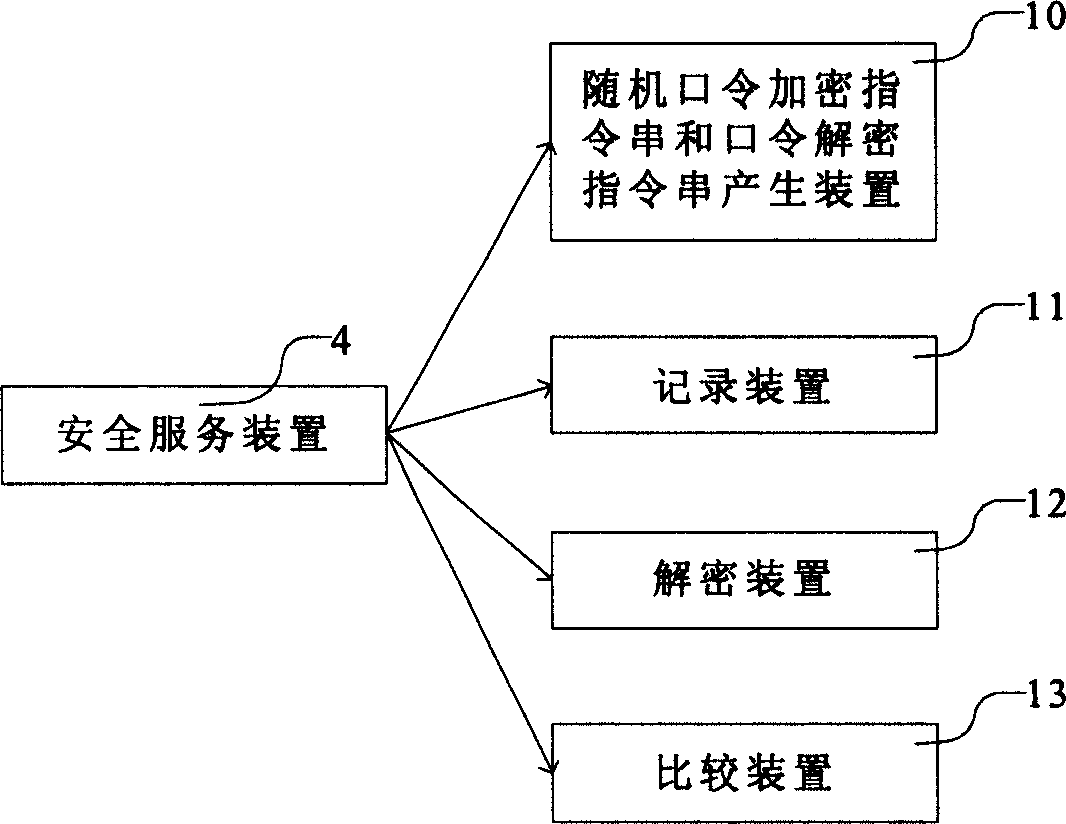
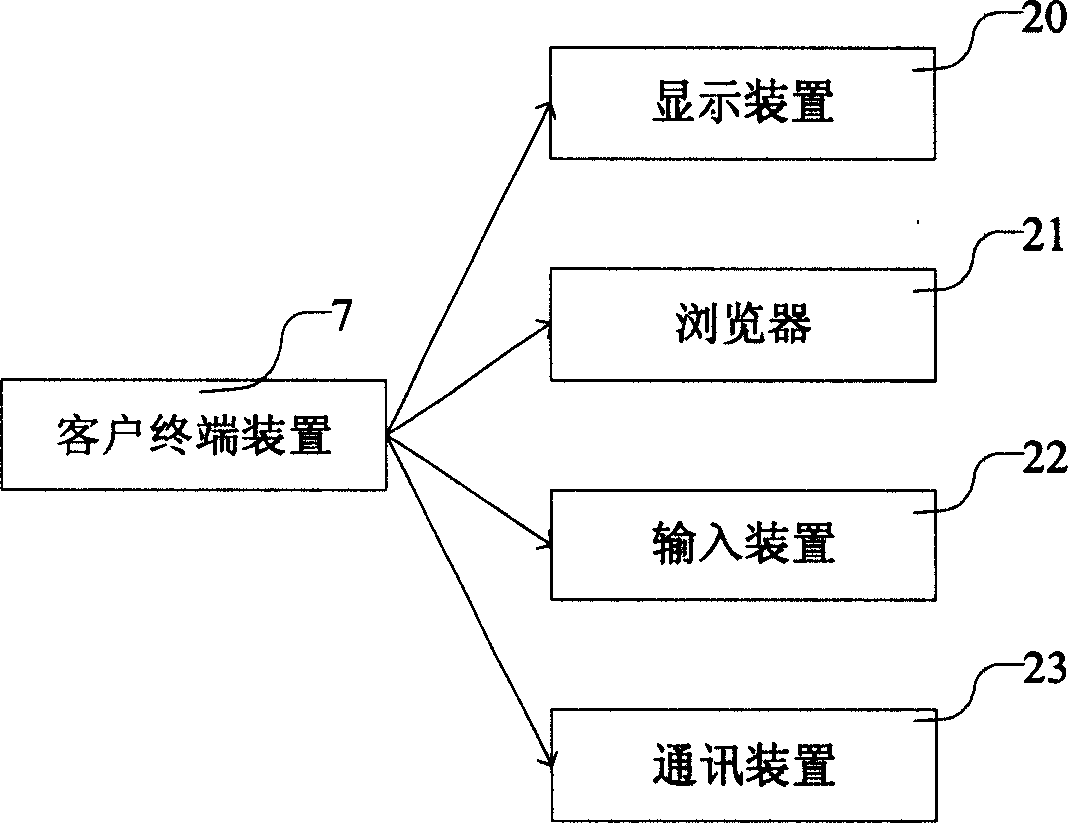
[0021] The service provider 2 can be a web server or a server providing access. Provide clients with services based on http and https protocols, dynamically generate web page files, provide them to client terminal devices, and interact with client terminal devices. When the client terminal device 7 starts to access the service related to security in the service provider 2, if the user has not passed the authentication, the service provider 2 requires user authentication, obtains a random password encrypted command string from the security service device 4, and generates a user The initial data required for authentication is sent to the client terminal device 7, and the initial data may be a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com