Method for designing domestic BMC (Baseboard Management Controller) chip trusted firmware
A technology of BMC chips and design methods, applied in computing, computer security devices, instruments, etc., can solve problems such as inability to guarantee safety and credibility, damage, and integrity of firmware program tampering, so as to improve core competitiveness and ensure credibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
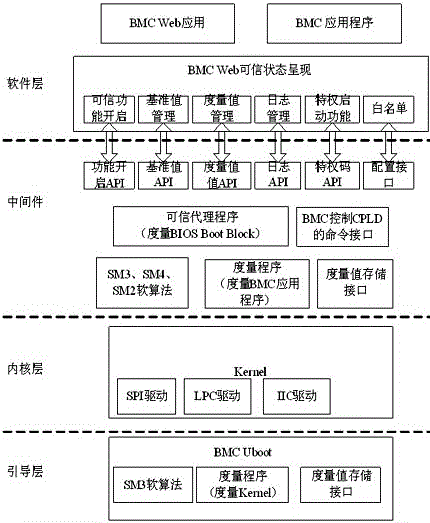
[0036] Such as figure 1 Shown, a kind of design method of domestic BMC chip trustworthy firmware, described method adds trustworthy function module in the guiding layer of BMC firmware, kernel layer, middleware and software layer, kernel program, kernel program, Integrity measurement is performed on application programs and key BIOS codes to ensure program integrity, thereby establishing a trusted execution environment for the system platform.
Embodiment 2
[0038] On the basis of Embodiment 1, the boot layer described in this embodiment is the U-boot startup code of the BMC firmware. U-boot is the first code that runs when the BMC is powered on. Function modules include measurement program, SM3 soft algorithm and measurement value storage interface, among which:
[0039] a. Measuring program: when the BMC starts, the measuring program calls the SM3 soft algorithm to measure the Linux kernel (Kernel) of the BMC;
[0040] b. SM3 soft algorithm: a national secret SM3 cryptographic hash algorithm implemented with a C program, which performs a hash operation on the input data to generate a 256-bit hash value;
[0041] c. Measurement value storage interface: save the measurement value to the safe storage space of BMC, such as Flash.
[0042] When the BMC starts, the U-boot measurement program calls the SM3 soft algorithm to measure the BMC Linux Kernel, and compares the obtained measurement value with the reference value 1 to judge th...
Embodiment 3
[0045] On the basis of embodiment 2, the kernel layer Kernel layer described in this embodiment is the ARM Linux kernel through tailoring, in order to realize trusted computing function, need to add IO driver, described IO driver comprises the interface that realizes LPC, SPI, IIC Function to complete the hardware interface timing and configuration related registers, so that the BMC and external modules can communicate normally, among which:
[0046] a. LPC interface driver: realize the communication interface between the BMC chip and the external TCM trusted password module, so that the BMC can access the TCM module through the LPC interface;
[0047] b. SPI interface driver: realize the communication interface between the BMC chip and the external BIOS chip, so that the BMC can read the Boot Block code of the BIOS through the SPI interface;
[0048] c. IIC interface driver: realize the communication interface between the BMC chip and the external CPLD chip, so that the BMC s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com