Creditability detection method of computer
A detection method and reliability technology, applied in the computer field, can solve problems such as inability to dynamically add new components, inconvenient system expansion, and increase system maintenance and update costs, so as to facilitate expansion, improve security and verification flexibility, The effect of reducing maintenance and updating costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
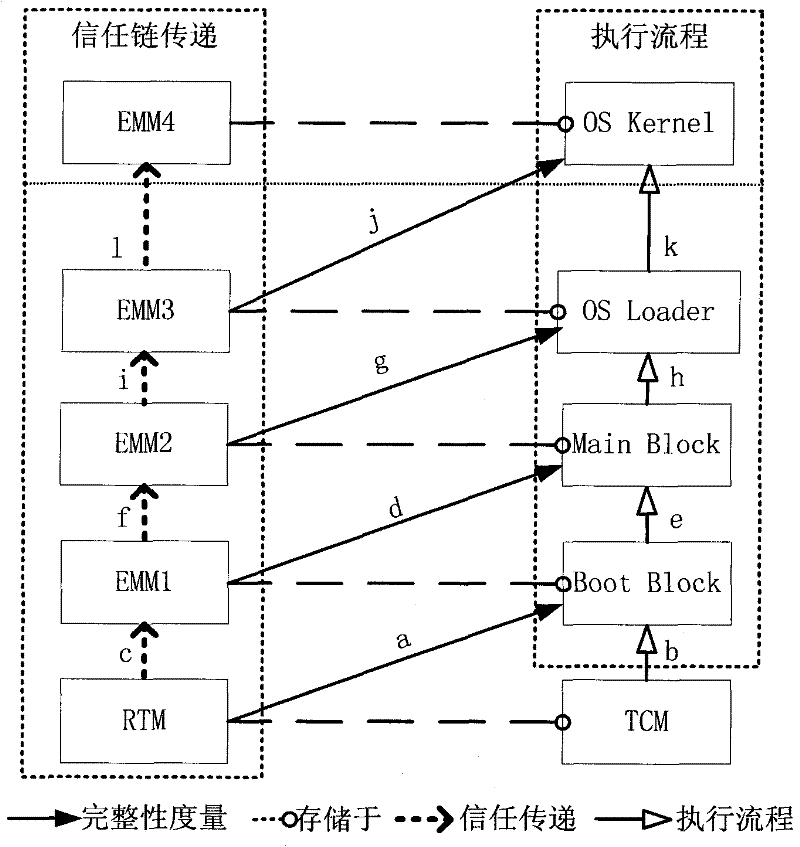
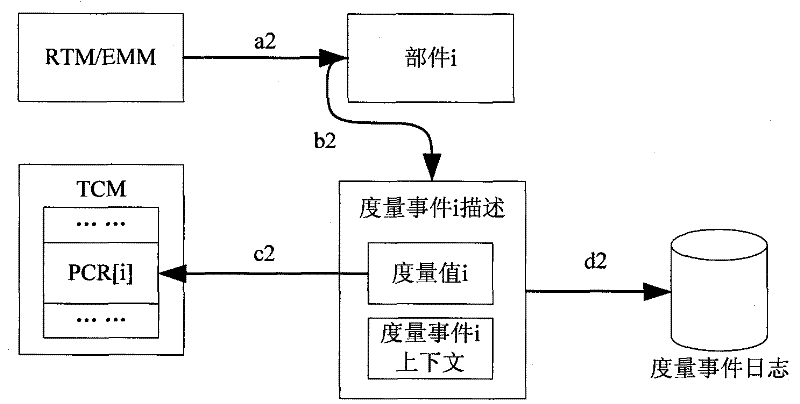
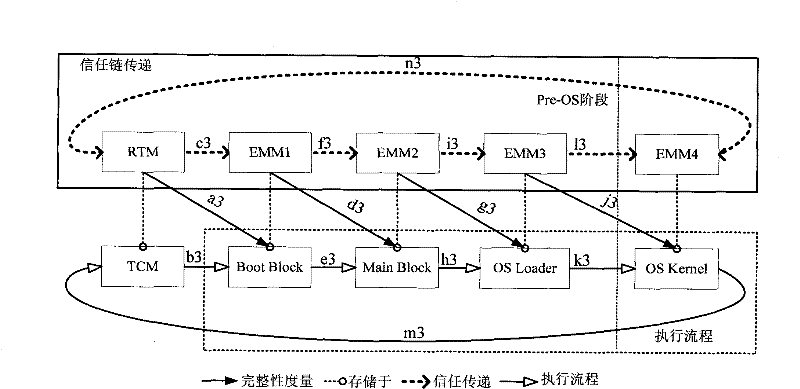
[0034] The main idea of the present invention is: the ring trust chain structure is supported, and the independent hardware TCM is used as the trusted measurement controller of the whole computer platform. TCM uses physical methods and software-assisted methods to integrate trusted computing roots, trusted storage roots and trusted reporting roots, and has the function of platform identity authentication for itself. When testing the reliability of a computer, the components (also called endpoints) on the circular trust chain use the TCM trusted computing measurement function, and the adjacent components use the cross-measurement mechanism to finally transfer the trust to the TCM, and the TCM completes the platform. reliability report. If the starting point of the measurement is the TCM, the security guidance requirements of the traditional chain trust chain platform can be fulfilled, but the last component to be measured must be required to pass the trust to the TCM, and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com