Embed type platform guiding of credible mechanism
An embedded and embedded system technology, applied in the direction of program control devices, computer security devices, instruments, etc., can solve the problems of embedded system trust root dependence, difficulty, and poor predictability of modification results, etc., to achieve reliable measurement and the effectiveness of the reporting mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
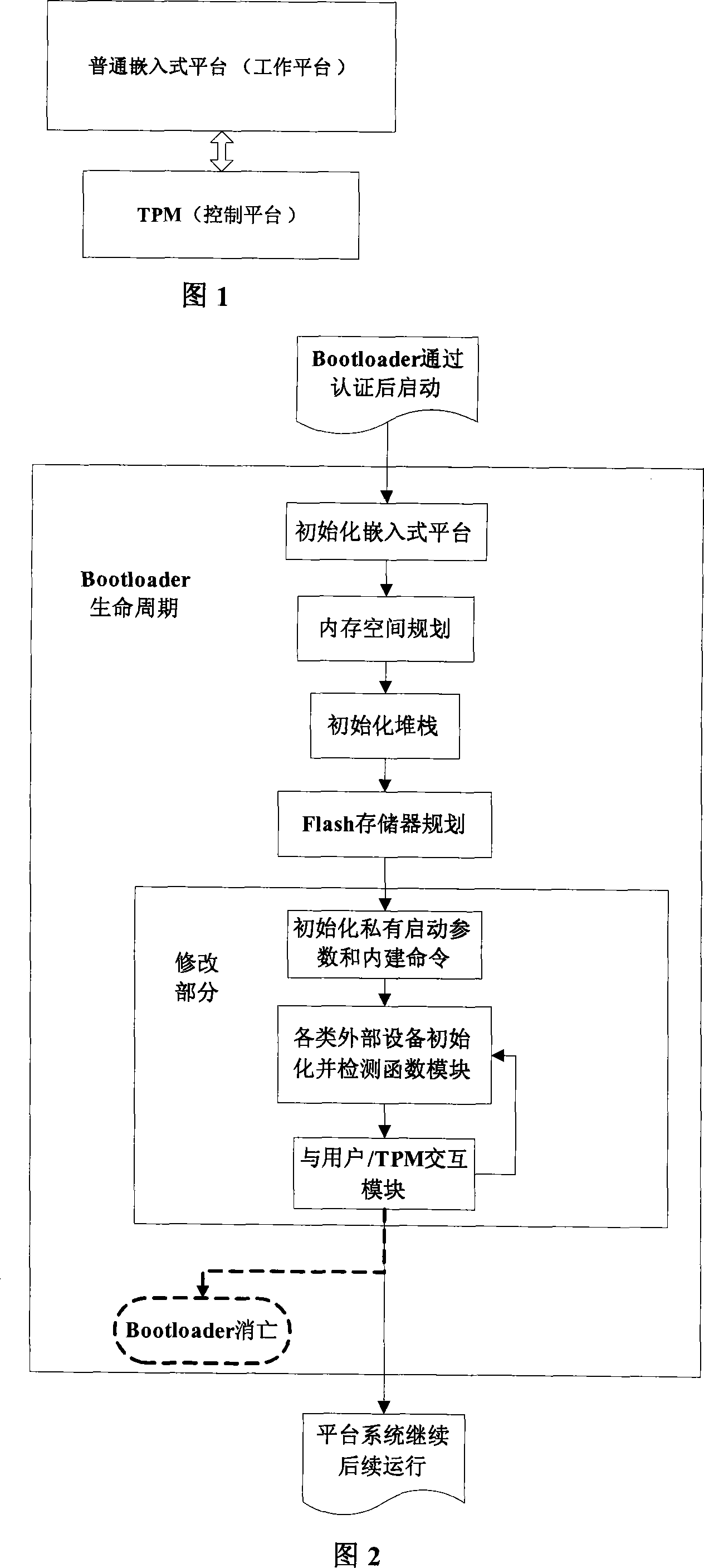
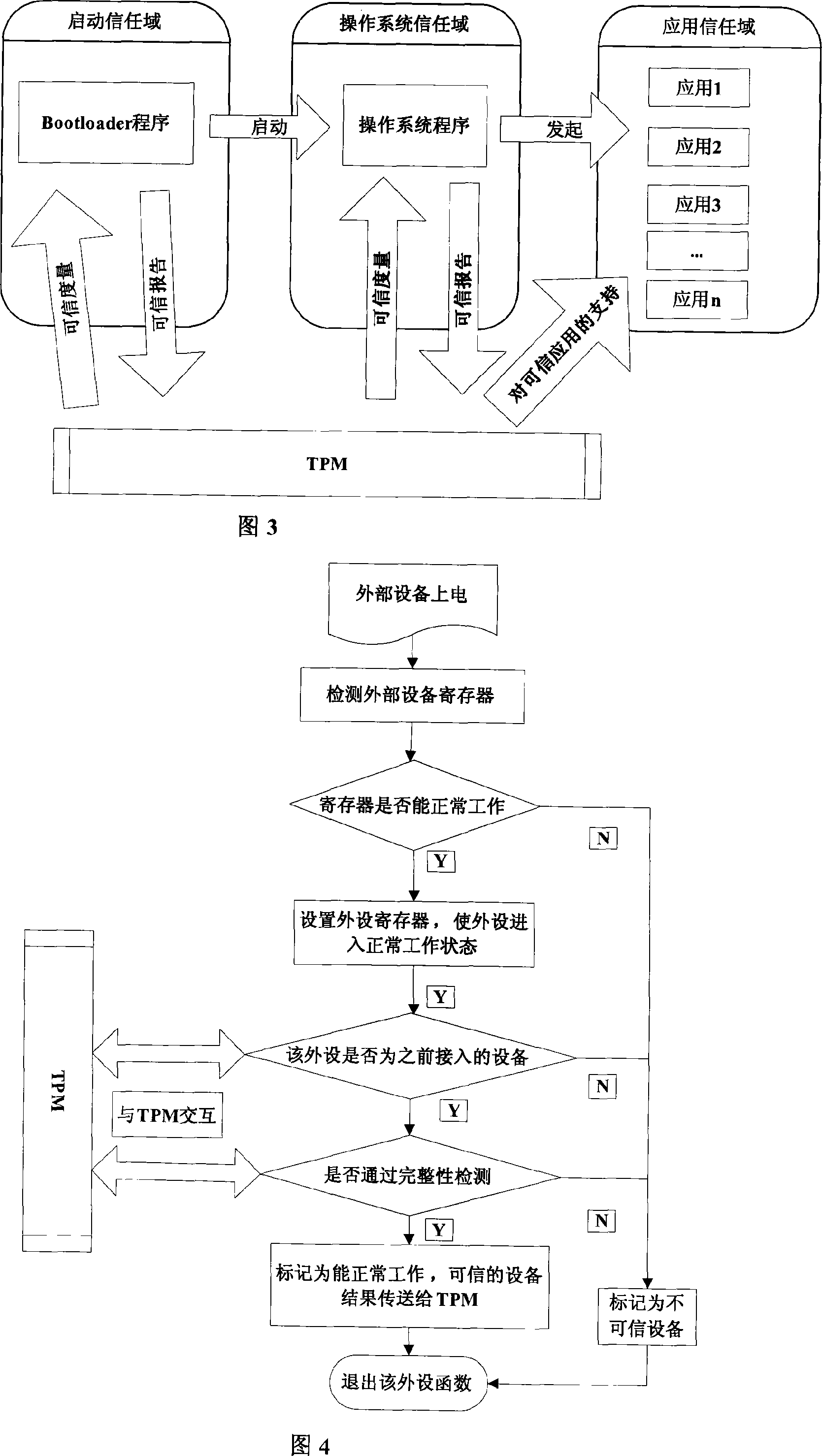
[0020] The invention discloses an embedded platform booting method based on a trusted mechanism, specifically: according to the architectural characteristics of the trusted system, the embedded platform and the TPM hardware module (wherein, the TPM hardware module includes trusted measurement root, trusted report root, and trusted storage root), and the initialization of the embedded platform uses a Bootloader with a trust chain structure that is improved on the basis of vivi (a kind of Bootloader). The Bootloader is solidified in in the platform's Flash memory. The TPM first starts from the startup of the system based on the trusted integrity measurement root, and performs integrity verification on the Bootloader, operating system, etc. to ensure that the software in the platform startup chain has not been tampered with, and then allows the CPU to read the Bootloader to start. Since the source code of the Bootloader is open, the credible Bootloader supports TPM to control ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com