Trusted computation trust root device for computer and computer
A technology of trusted computing and root devices, applied in the computer field, can solve the problem that ordinary computers cannot be installed with secure chips, trusted computing, etc., and achieve the effect of simple security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
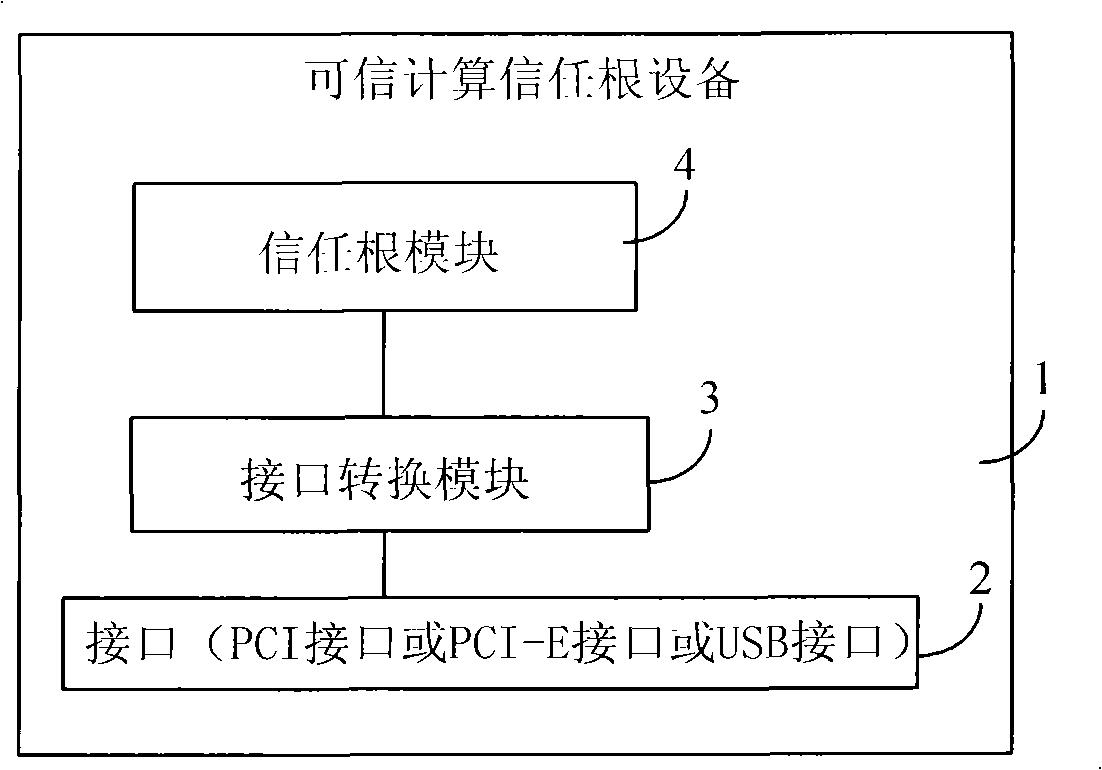
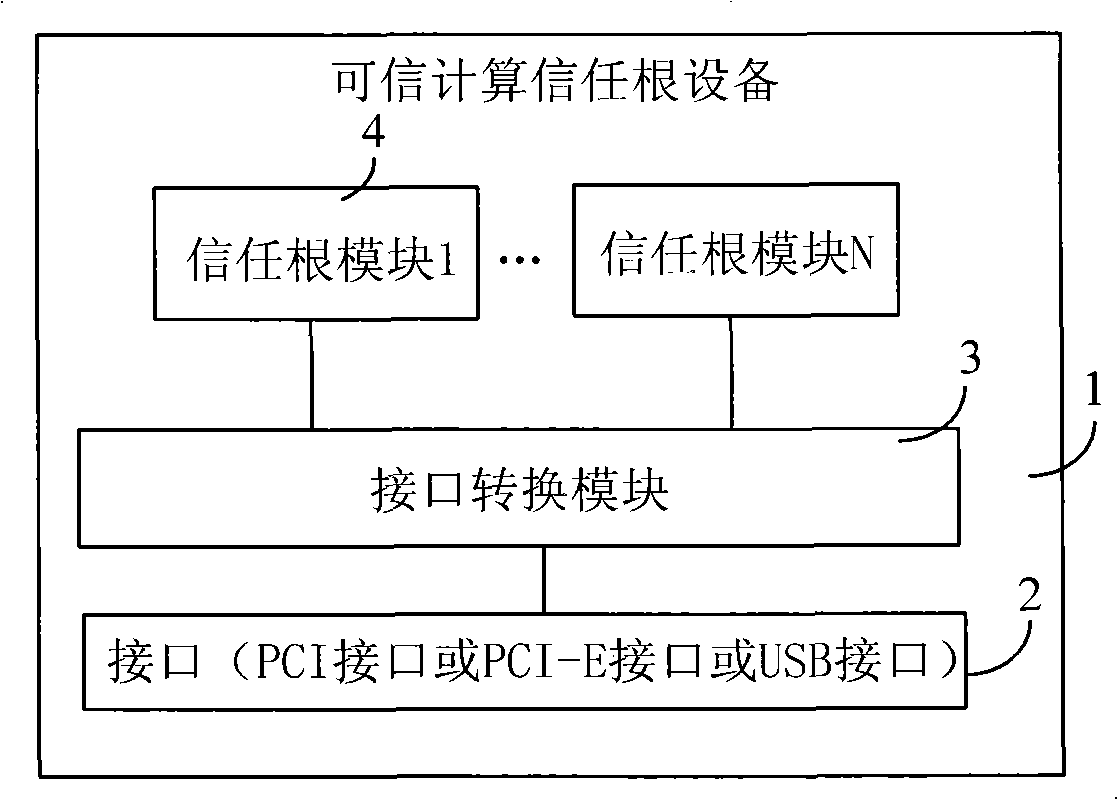
[0023] The first embodiment provides a trusted computing trust root device for computers, which is applied to ordinary computers to enable ordinary computers to have trusted computing functions, such as figure 1 As shown, the trusted computing trust root device includes:
[0024] circuit board 1, interface conversion module 3 and at least one root of trust module 4;
[0025] Wherein, the circuit board 1 is provided with an interface 2, and the interface 2 can adopt a PCI interface or a PCI-E interface or a USB interface, which is connected to the PCI interface or PCI-E interface of the computer motherboard (that is, the PCI slot on the computer motherboard or the PCI-E interface). PCI-E slot) or USB interface; when interface 2 adopts PCI interface or PCI-E interface, it is generally the PCI interface or PCI-E interface formed by the electrical connection between the interface module and the golden fingers printed on the circuit board. The golden finger on the circuit board re...
Embodiment 2
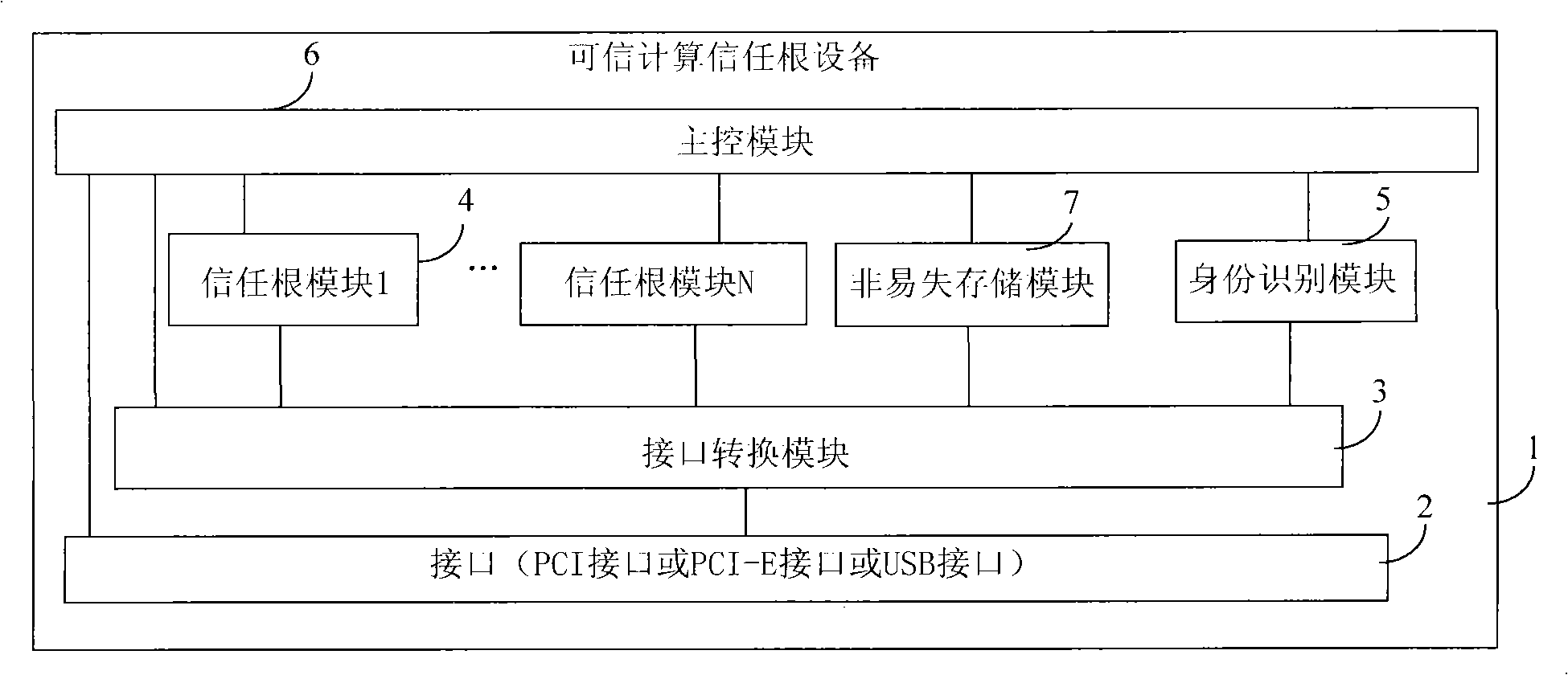
[0033] The second embodiment provides a trusted computing root of trust device for computers, which is applied to an ordinary computer to enable the ordinary computer to have a trusted computing function. The structure of the root of trust device is basically the same as the root of trust device given in the first embodiment above. The same, the difference is that the root of trust device in this embodiment is also provided with an identity recognition module 5 and a main control module 6, such as image 3 As shown, the identity recognition module 5 and the main control module 6 of the root of trust device are both arranged on the circuit board 1, the identity recognition module 5 and the main control module 6 are respectively electrically connected with the interface conversion module 3, and the main control module 6 is respectively connected with the identity Identification module 5. Each root of trust module is electrically connected;
[0034] Described identity recognition...
Embodiment 3
[0043] The third embodiment provides a computer, such as Figure 5 shown, the computer includes:
[0044] The host 21, the trusted computing trust root device 25, the storage device (not shown in the figure), the input device 22 and the output device 23; wherein the host 21 is provided with a main board 24, and the trusted computing trust root device 25 adopts the above-mentioned The trusted computing trust root device given in the first embodiment;
[0045] The storage device, the input device 22 and the output device 23 are all electrically connected to the mainboard 24 in the host 21; the trusted computing trust root device 25 is connected to the PCI slot or PCI of the mainboard 24 in the host 21 -E slot or USB interface is electrically connected with the motherboard 24.
[0046] The hardware structure of the computer is basically the same as that of an ordinary computer. The difference is that the computer also includes a trusted computing root of trust device. By connec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com