Security terminal reinforcing model and reinforcing method of tolerable non-trusted component
A secure terminal and untrusted technology, which is applied in the security terminal reinforcement model and reinforcement field that can tolerate untrusted components, can solve the problems of trusted platform application loading restrictions, lengthy, complicated process, etc., to achieve tolerant loading and operation, and guarantee confidentiality security, confidentiality and integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
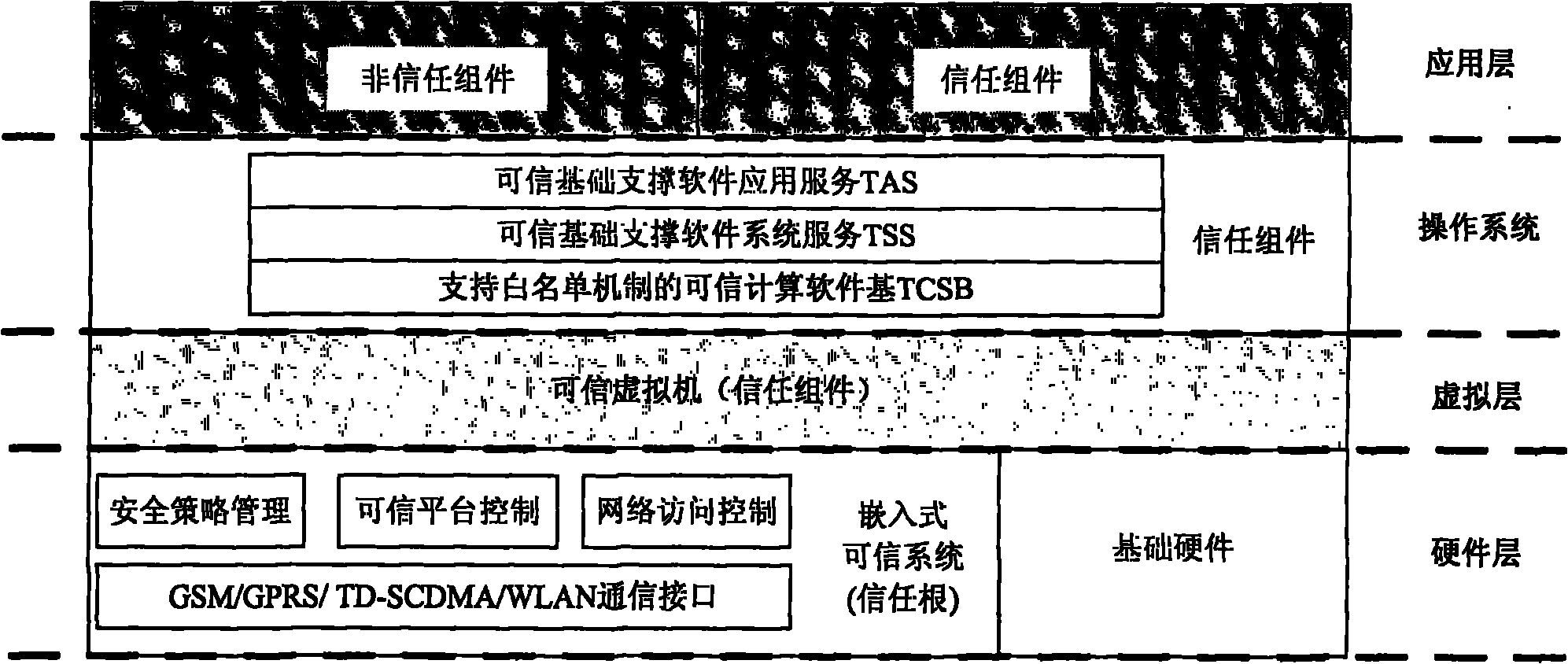
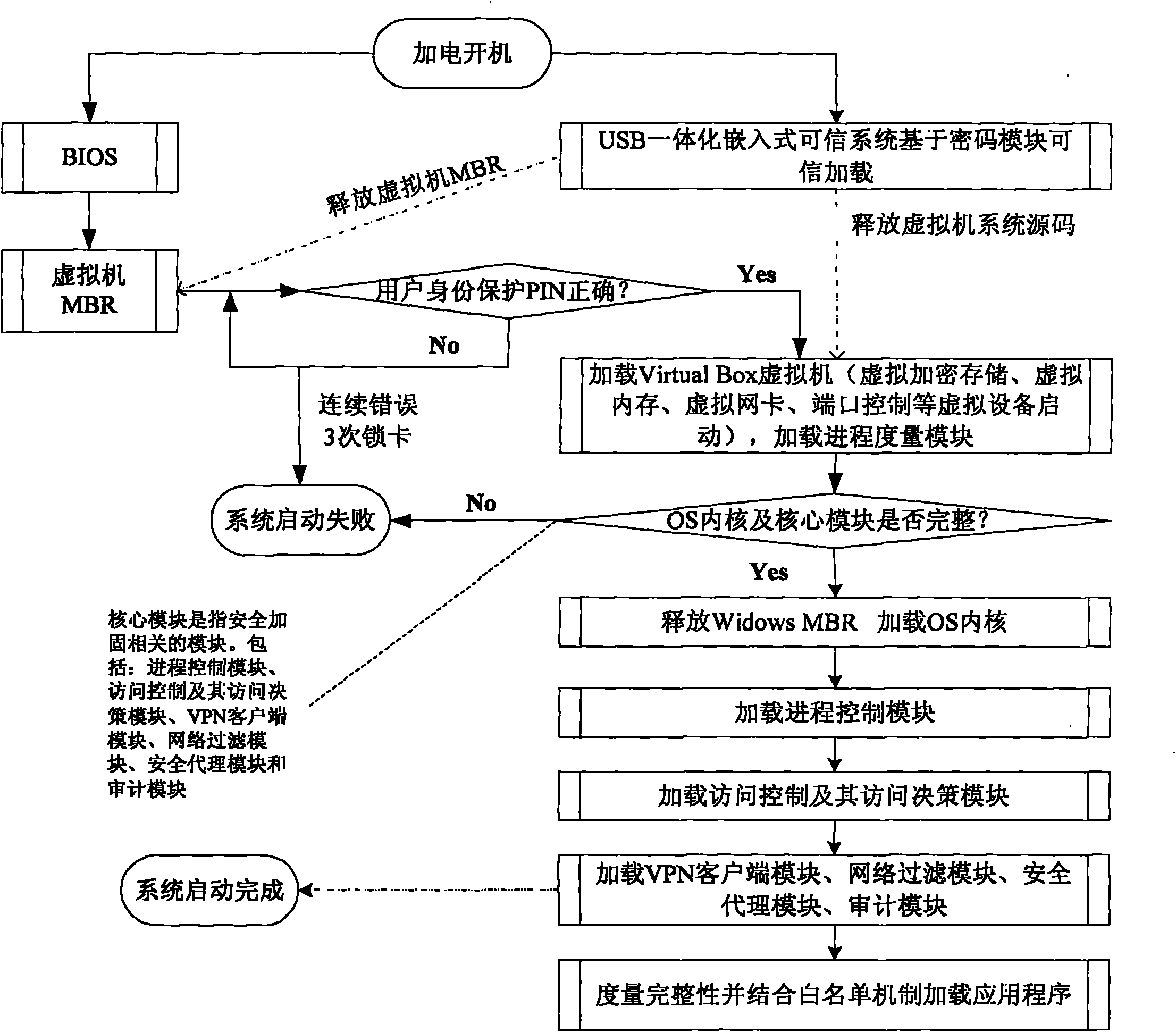
[0035] Such as figure 1 As shown in , the figure is a logical composition diagram of a secure terminal model that can tolerate untrusted components. This secure terminal hardening method is embodied as a secure terminal hardening model that can tolerate untrusted components. In this model, effective technical means are adopted in the links of information transmission channels (such as network, bluetooth, infrared and other communication means) and storage media (U disk, hard disk, readable and writable CD), and the existing trusted computing and other information security technologies to effectively prevent the occurrence of Trojan horses, viruses, system backdoors, hidden channels or malicious leaks, and construct a terminal trusted computing environment with predictable security results. The model includes hardware layer, virtualization layer, operating system layer and application layer.
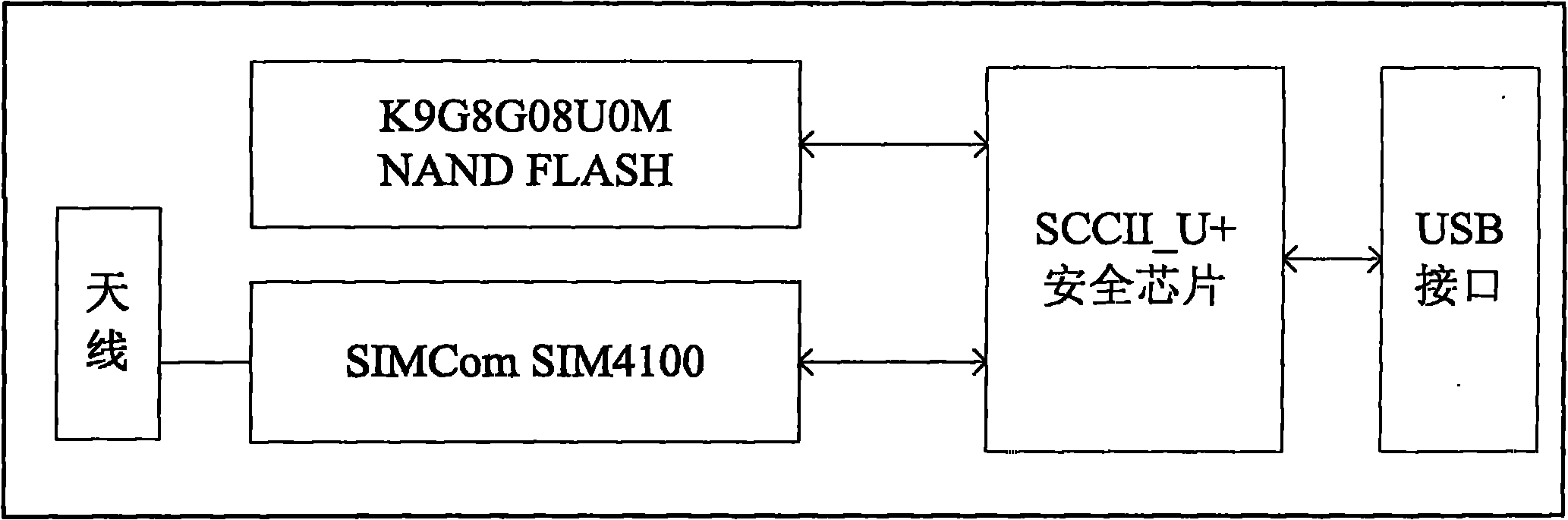
[0036] In addition to the basic computer hardware facilities, the terminal hardware...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com