Embedded terminal dependable starting method based on mobile dependable computing module
An embedded terminal, trusted computing technology, applied in computing, computer security devices, program loading/starting, etc., can solve the problems of slow startup, limited embedded terminal resources, poor stability, etc., to ensure safe operation, make up for The effect of limited computing power and faster startup
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
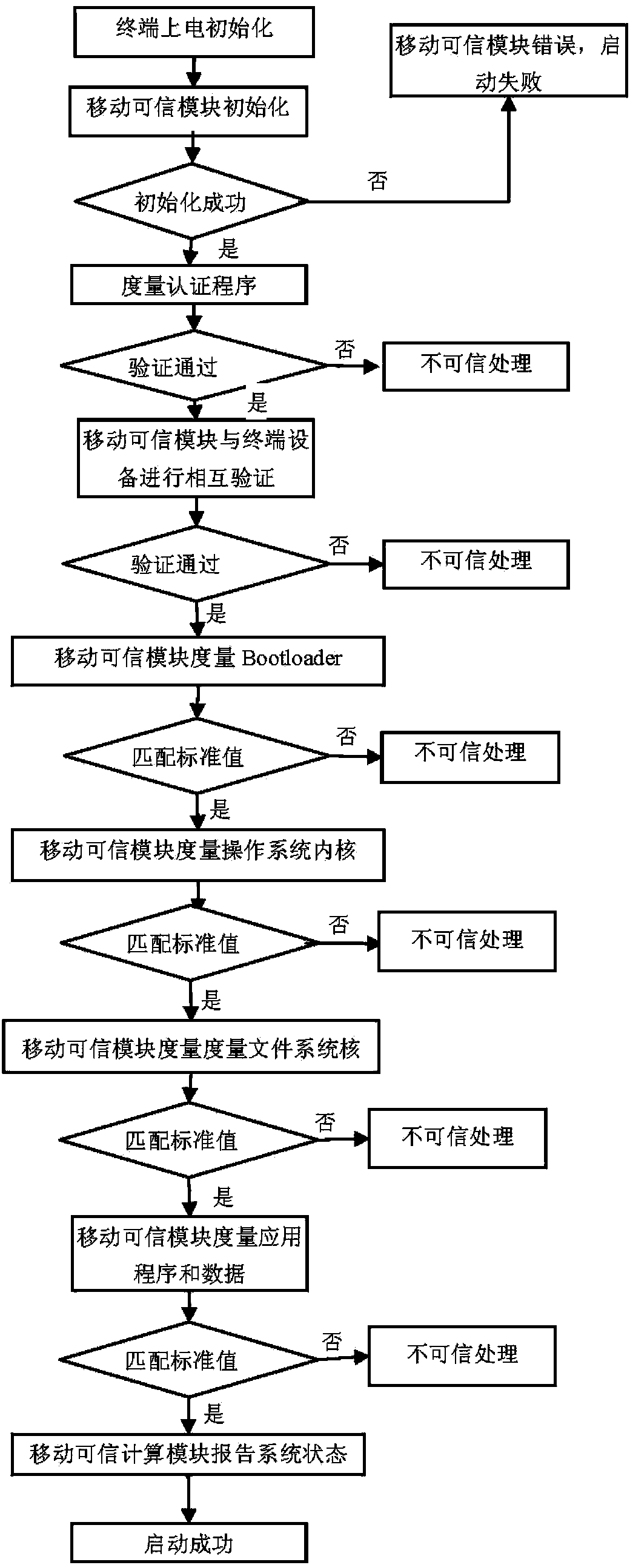
[0026] The implementation process of the present invention is described below with a specific example, but the present invention is not limited to this example. The content of the present invention covers any modification, equivalent and replacement of the core content of the present invention. The SD trusted computing module in this embodiment is a mobile trusted computing module packaged in the form of an SD card.
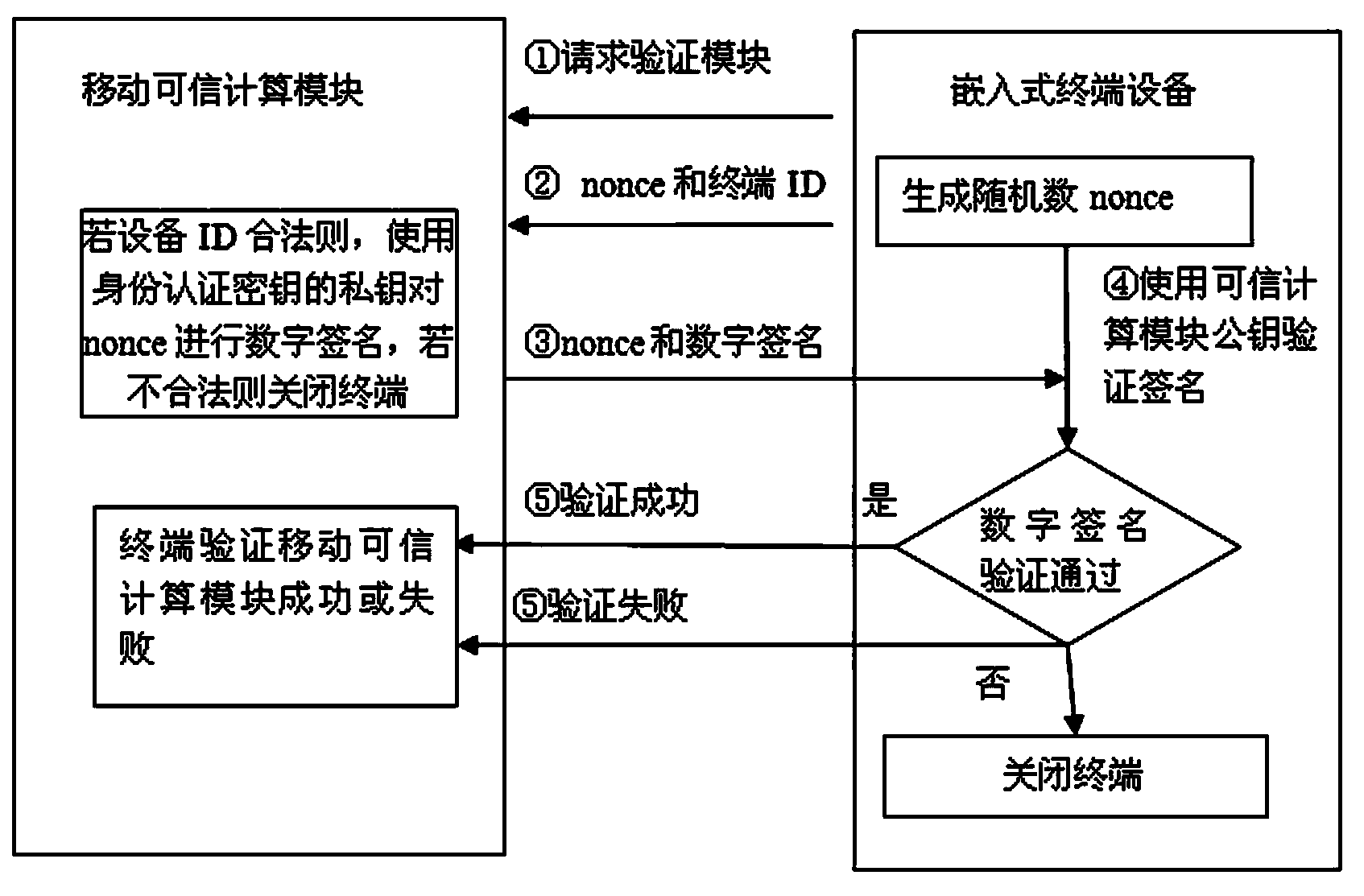
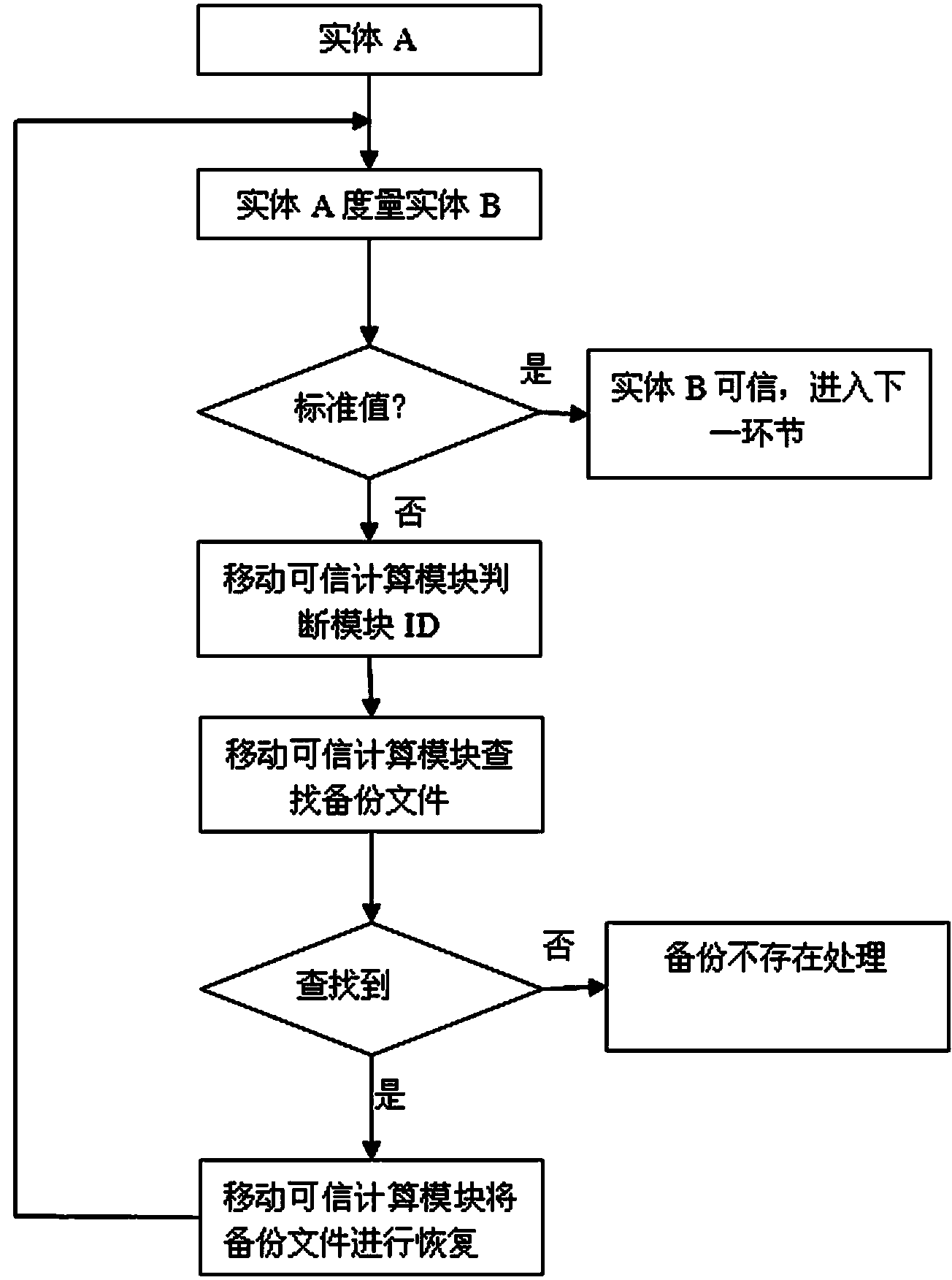
[0027] In the process of trusted booting, if the trusted computing module is illegal, then the security of the system becomes nonsense. The solution of the invention has a mobile trusted computing module authentication process, which can ensure the legitimacy of the mobile trusted computing module, thereby ensuring the safety of system startup. In addition, the system backup of the solution of the present invention is managed by a trusted computing module, which prevents the system backup from being maliciously tampered with and ensures the robustness of the emb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com