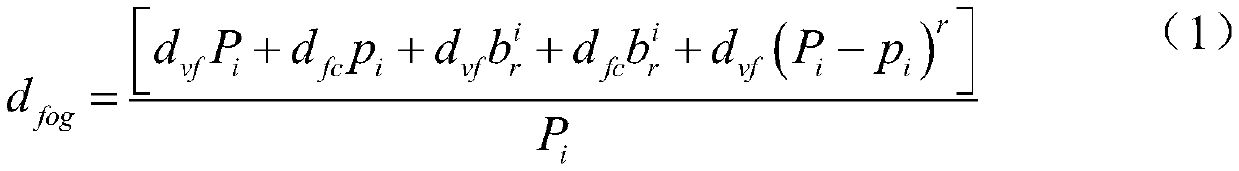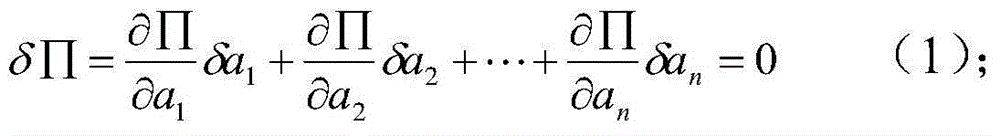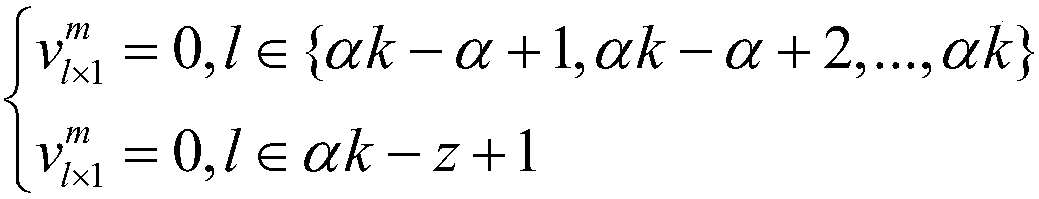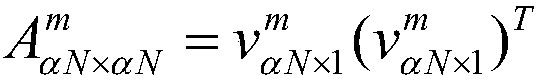Patents
Literature
65 results about "Reliable computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Reliable Computing is devoted to various aspects of interval mathematics and reliable numerical computations giving guaranteed properties of computed results. It includes various items in the fields of theoretical research, computer tools, applications, interdisciplinary research and other relevant areas.
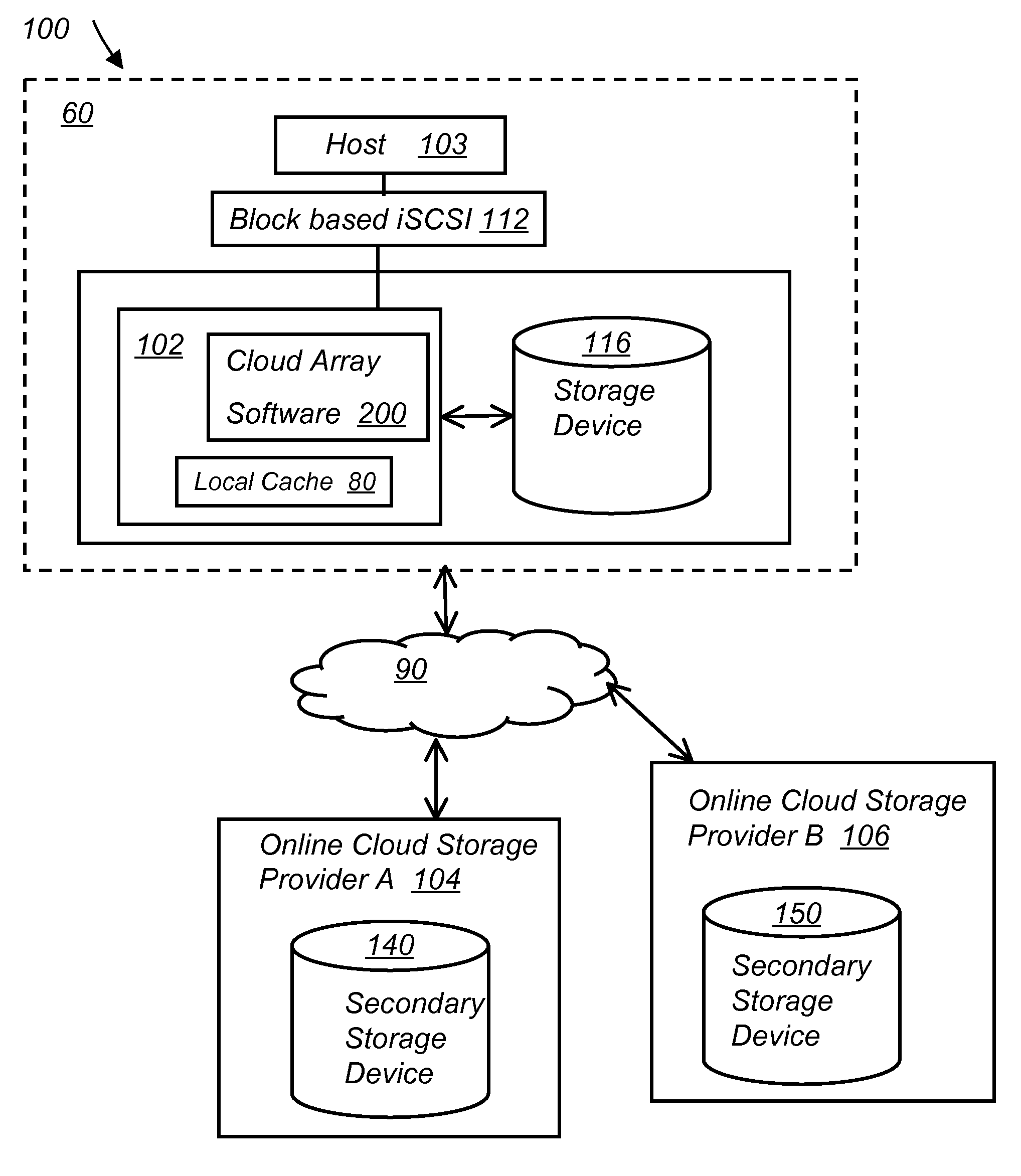
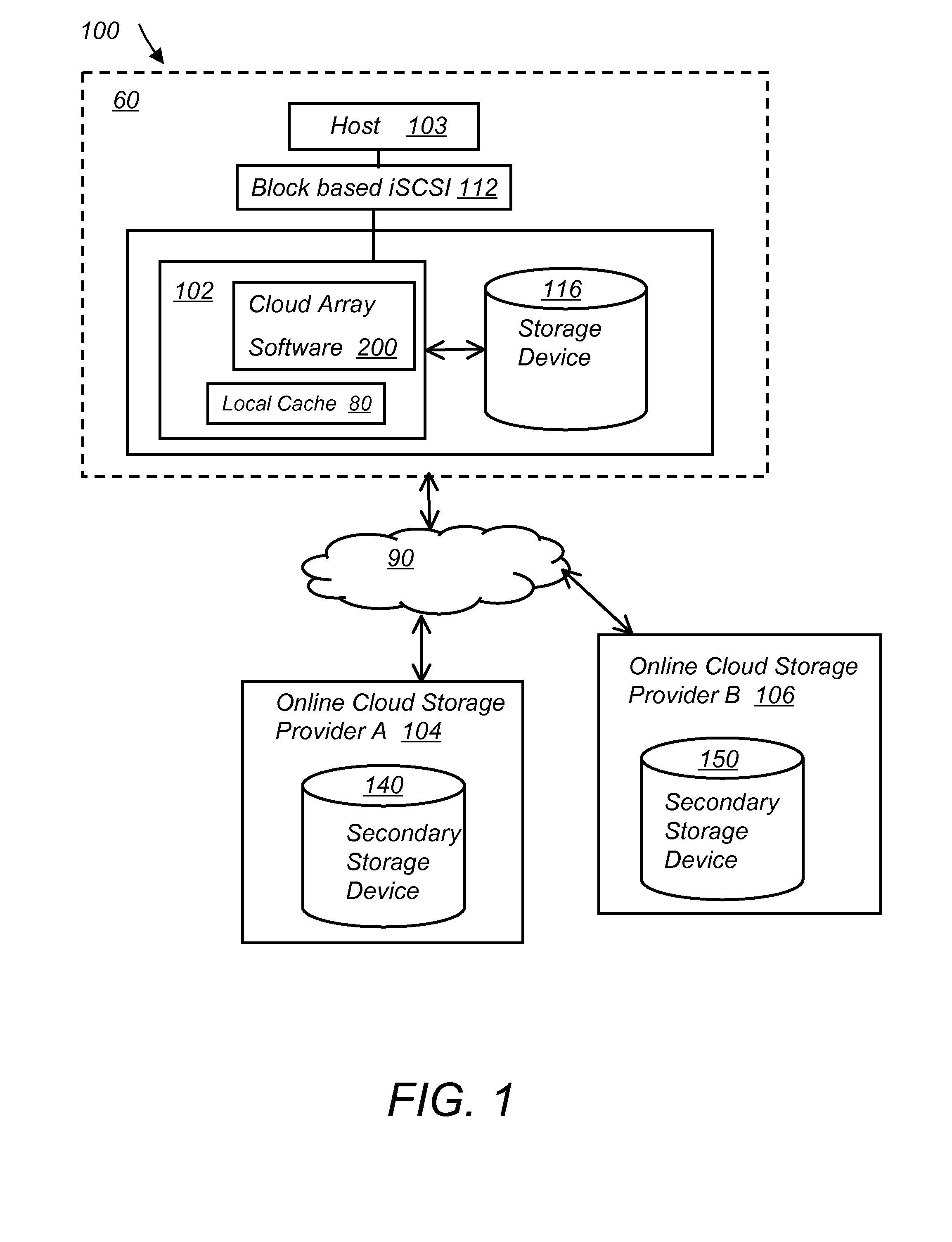
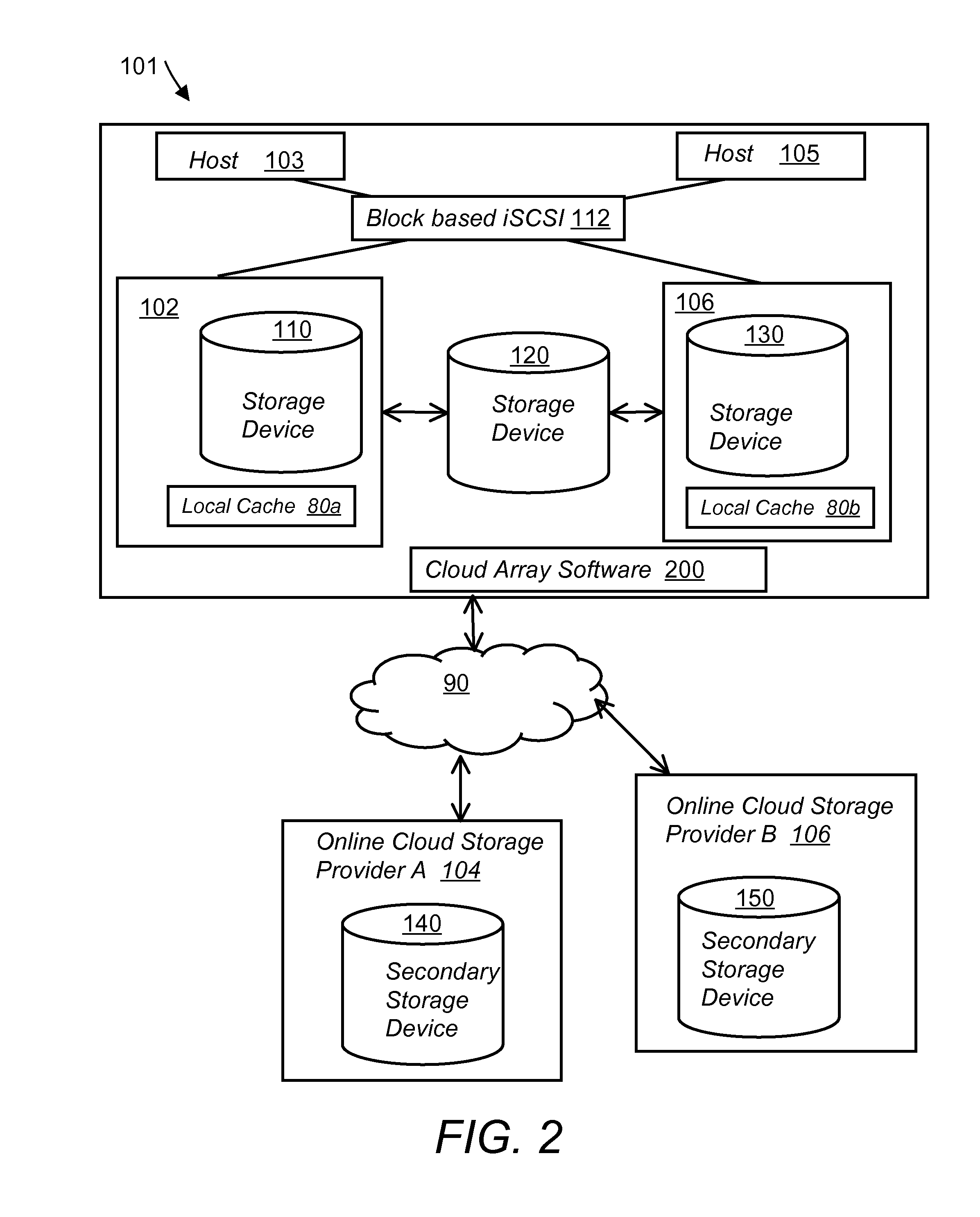
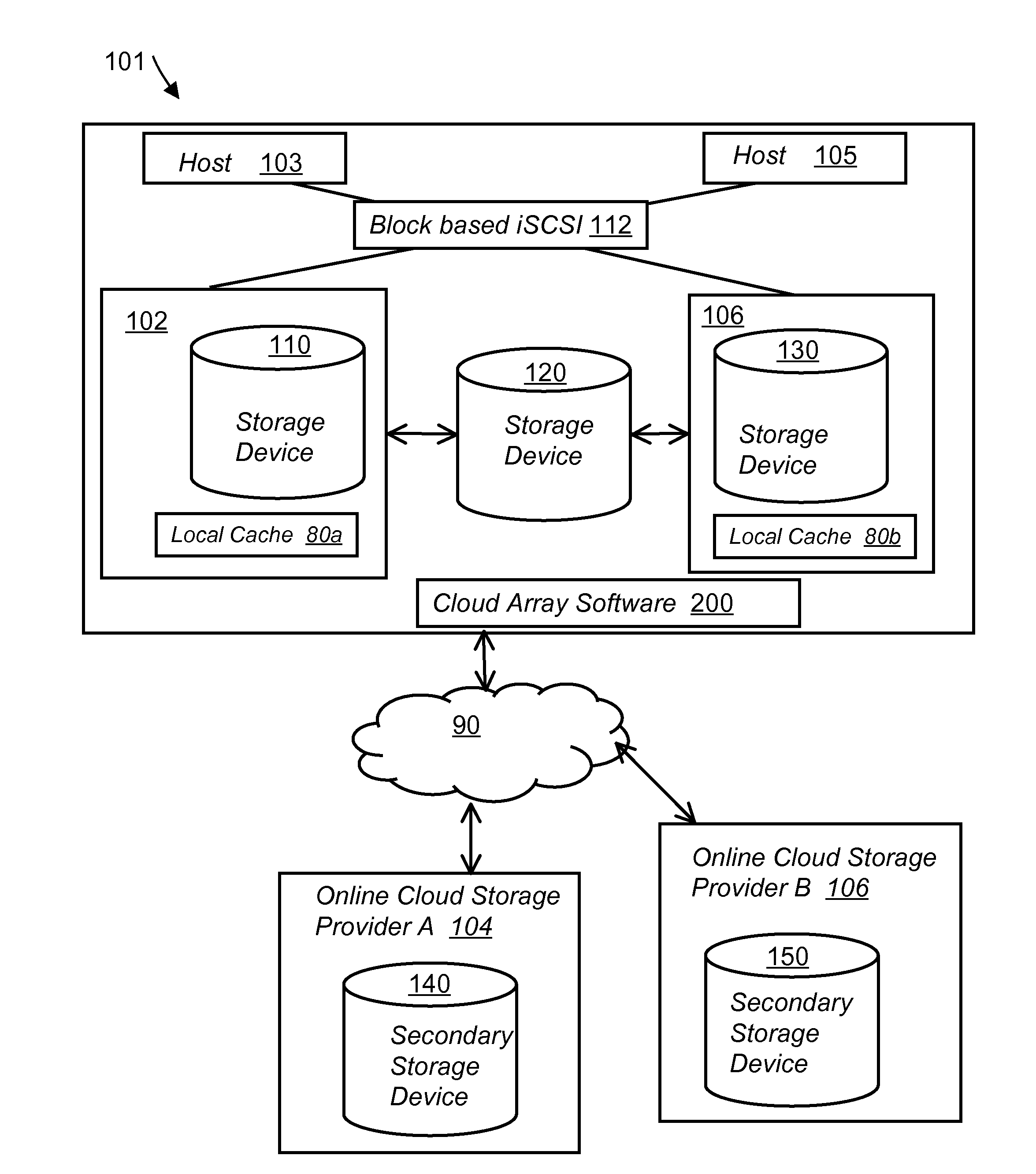
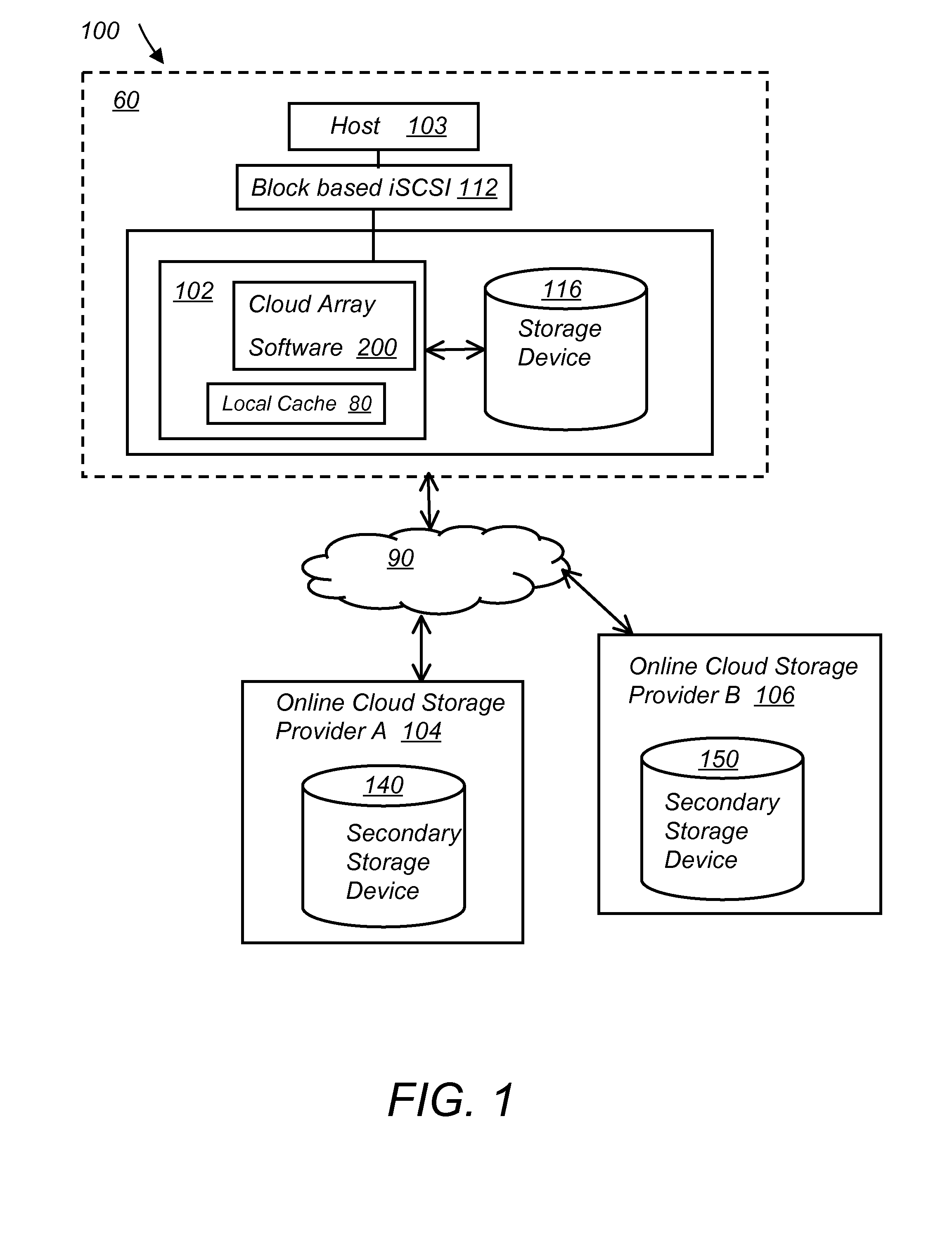
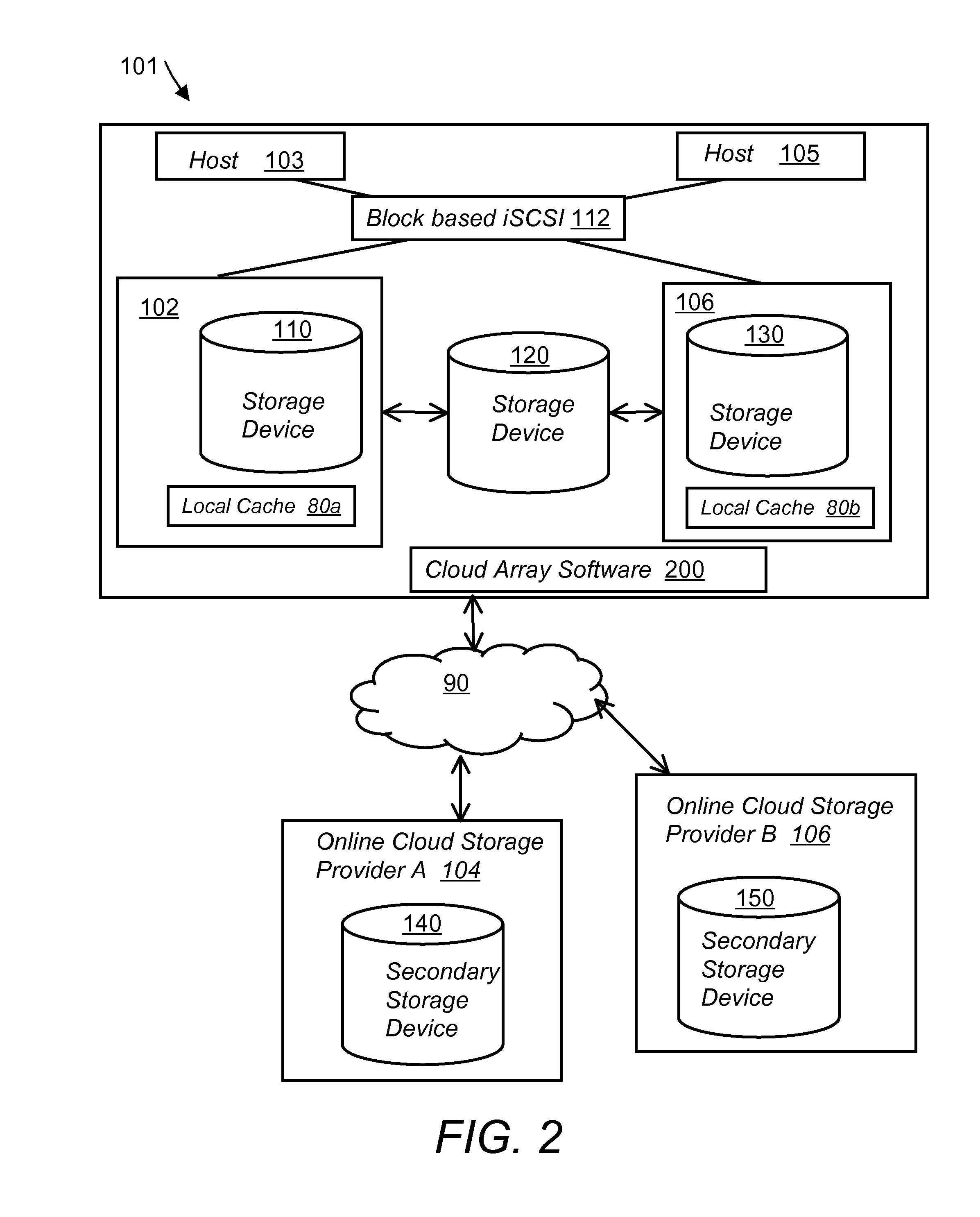
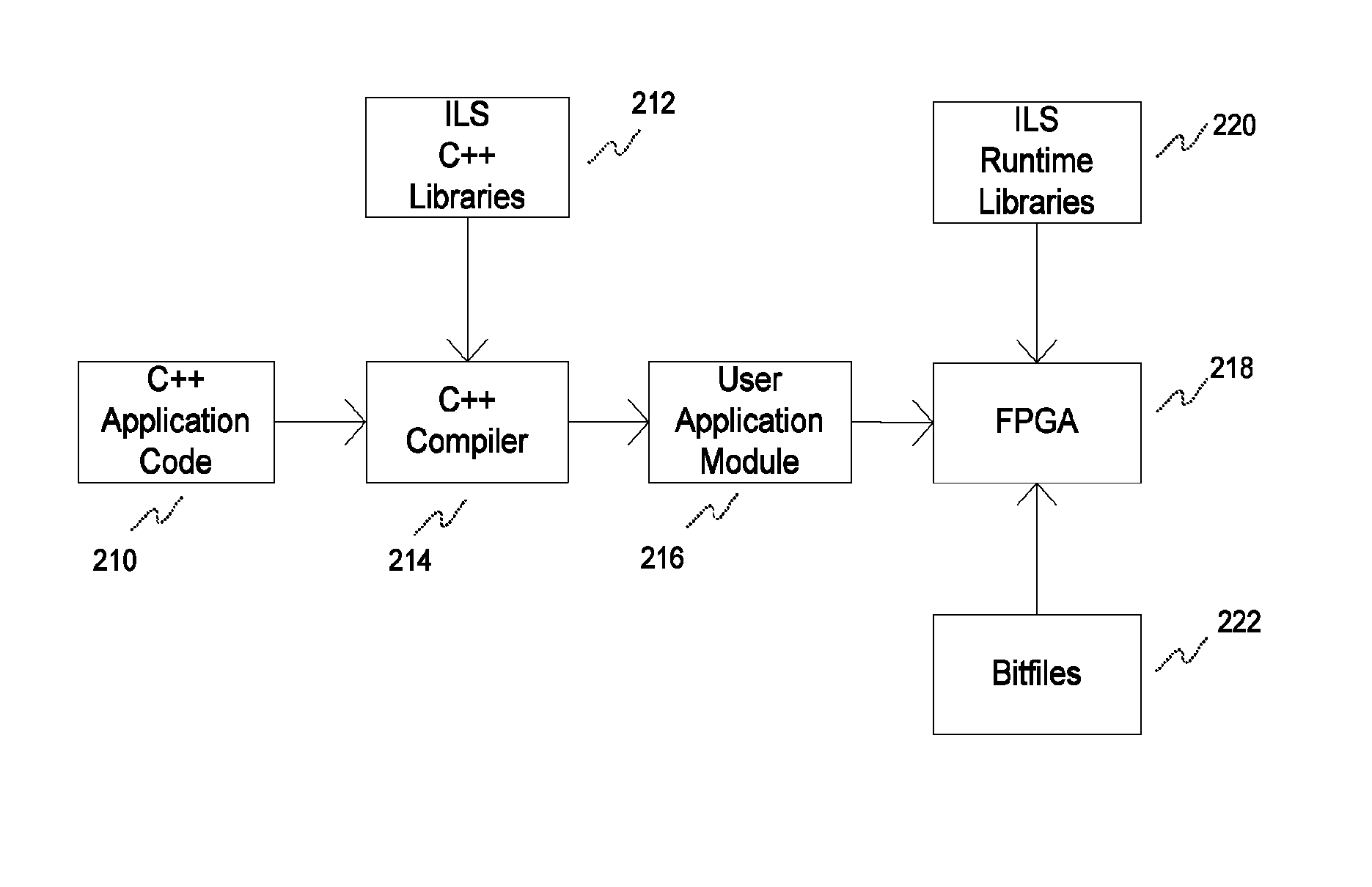
System and method for secure and reliable multi-cloud data replication
ActiveUS8762642B2Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationUnauthorized memory use protectionReliable computingNetwork connection
Owner:EMC IP HLDG CO LLC
System and method for secure and reliable multi-cloud data replication
ActiveUS20100199042A1Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationMemory loss protectionReliable computingReplication method
A multi-cloud data replication method includes providing a data replication cluster comprising at least a first host node and at least a first online storage cloud. The first host node is connected to the first online storage cloud via a network and comprises a server, a cloud array application and a local cache. The local cache comprises a buffer and a first storage volume comprising data cached in one or more buffer blocks of the local cache's buffer. Next, requesting authorization to perform cache flush of the cached first storage volume data to the first online storage cloud. Upon receiving approval of the authorization, encrypting the cached first storage volume data in each of the one or more buffer blocks with a data private key. Next, assigning metadata comprising at lest a unique identifier to each of the one or more buffer blocks and then encrypting the metadata with a metadata private key. Next, transmitting the one or more buffer blocks with the encrypted first storage volume data to the first online cloud storage. Next, creating a sequence of updates of the metadata, encrypting the sequence with the metadata private key and then transmitting the sequence of metadata updates to the first online storage cloud.
Owner:EMC IP HLDG CO LLC
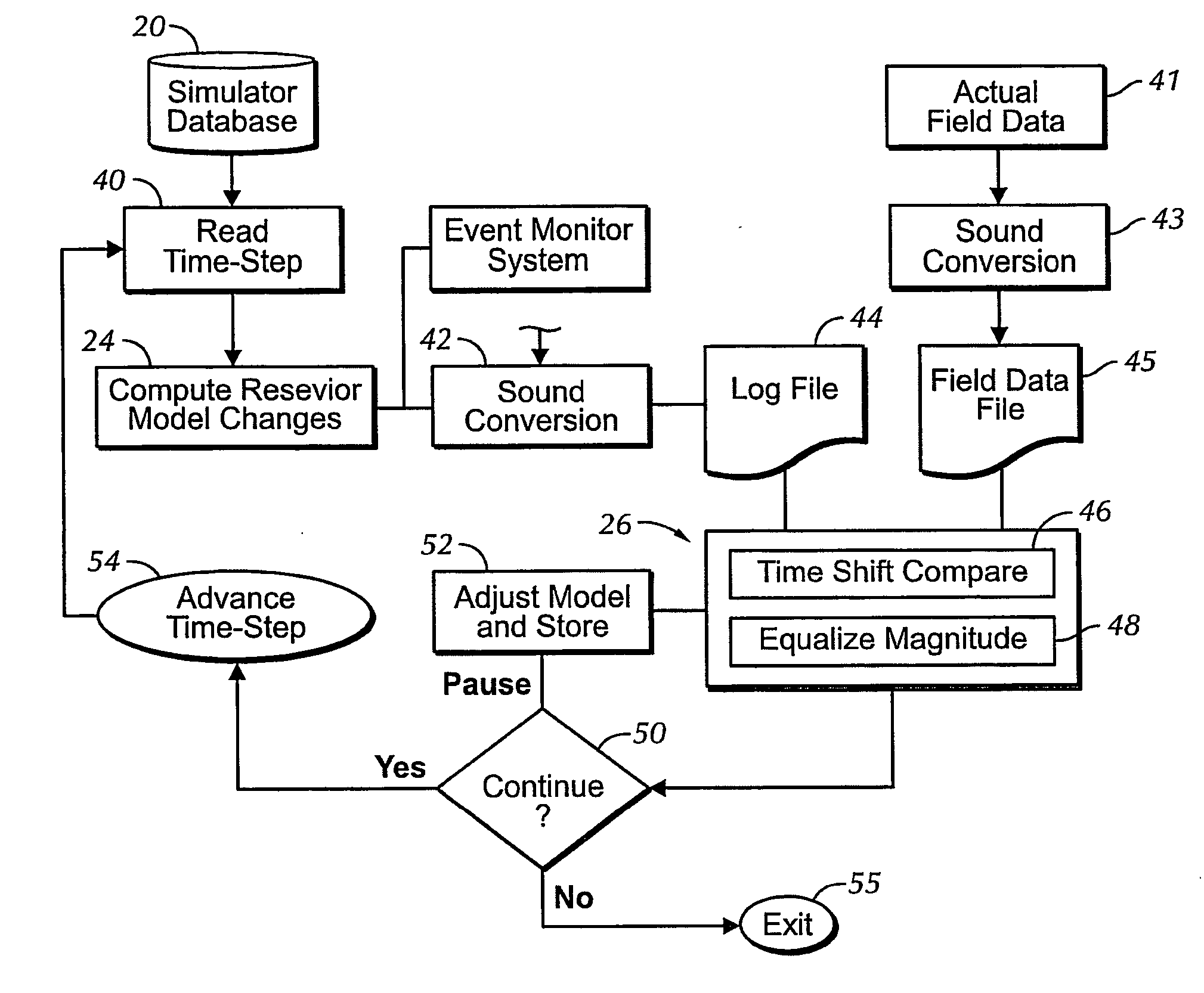
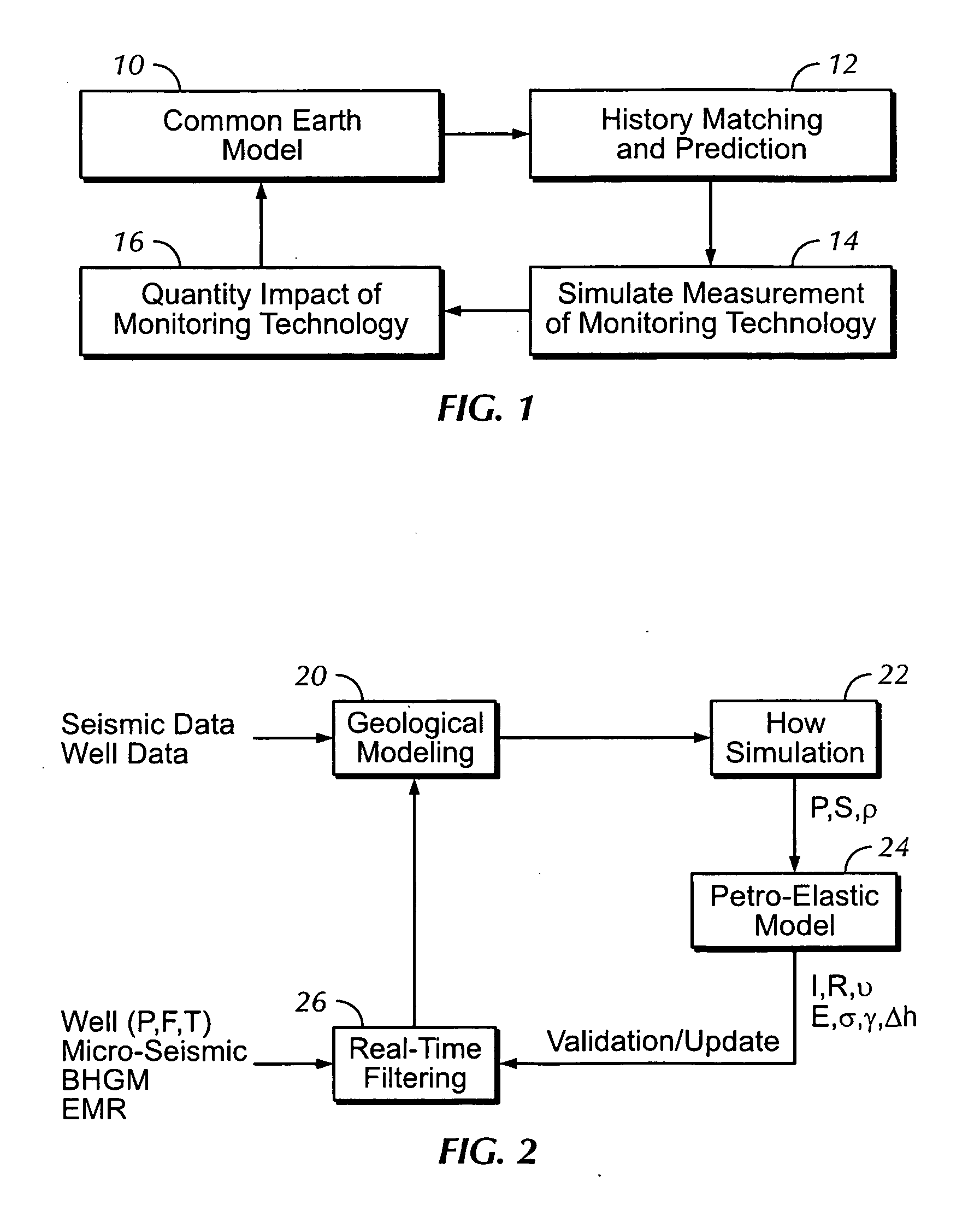
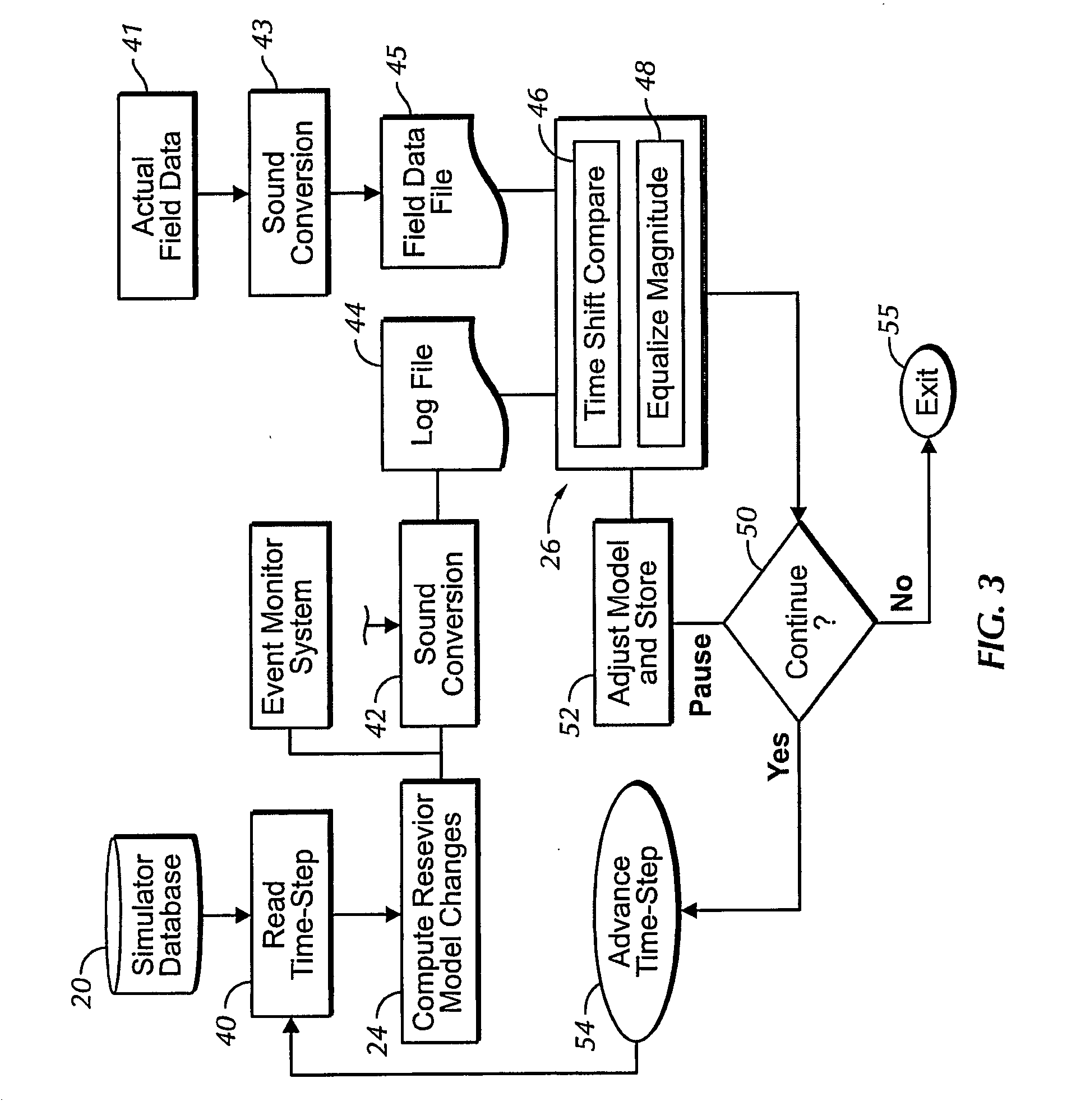
Sound enabling computerized system for real time reservoir model calibration using field surveillance data
ActiveUS20070255500A1Digital data processing detailsVolume/mass flow measurementReliable computingComputerized system
A computer-based system generates digital and audio responses to changes in fluid and rock properties of a producing hydrocarbon reservoir for surveillance analysis. The system calibrates observed changes against directly-measured field data in order to optimize the reservoir model. The changes may include, for example, stress changes in rock, impedance changes in rock, and fluid density changes.
Owner:ARAMCO SAUDI
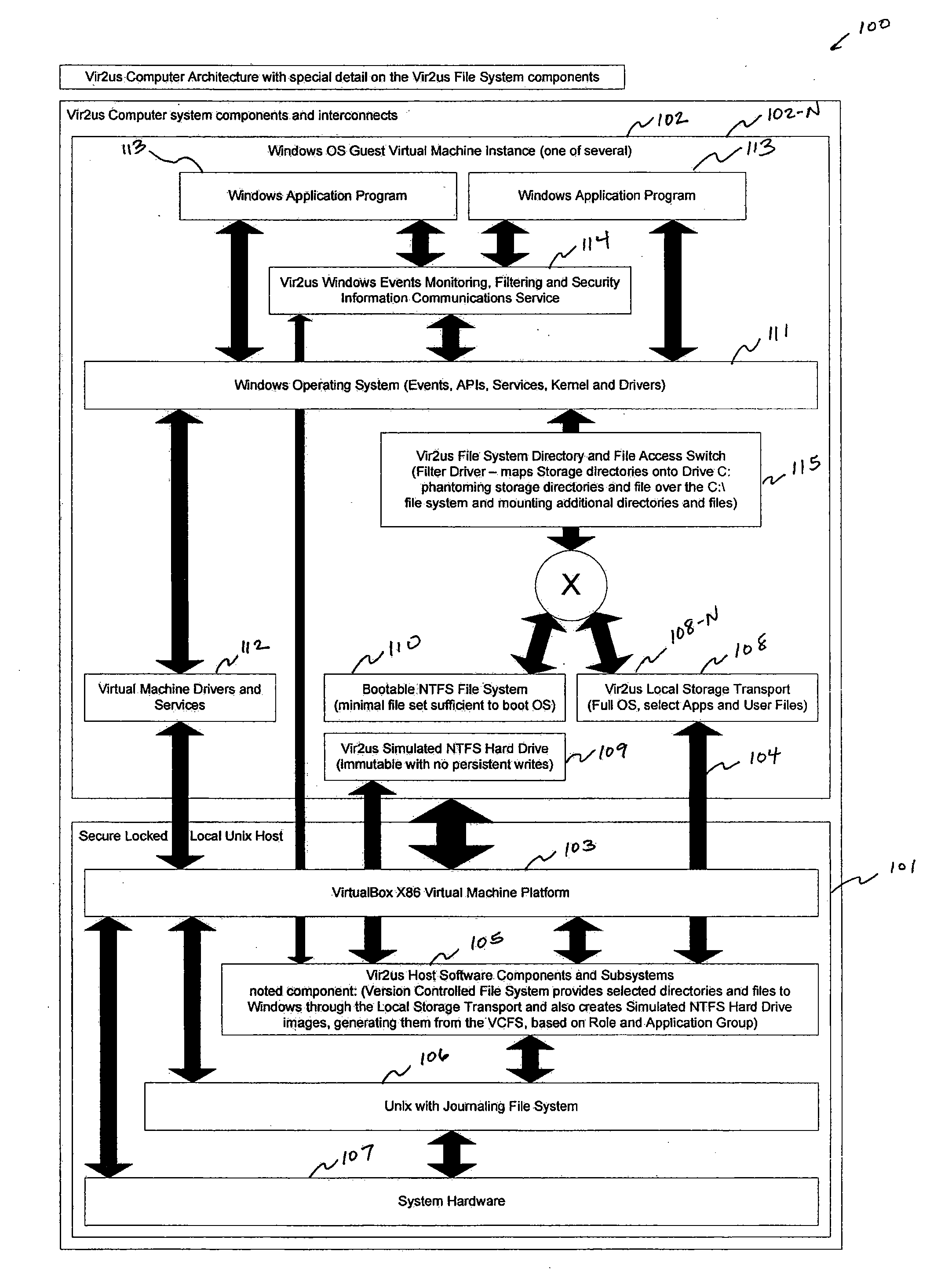
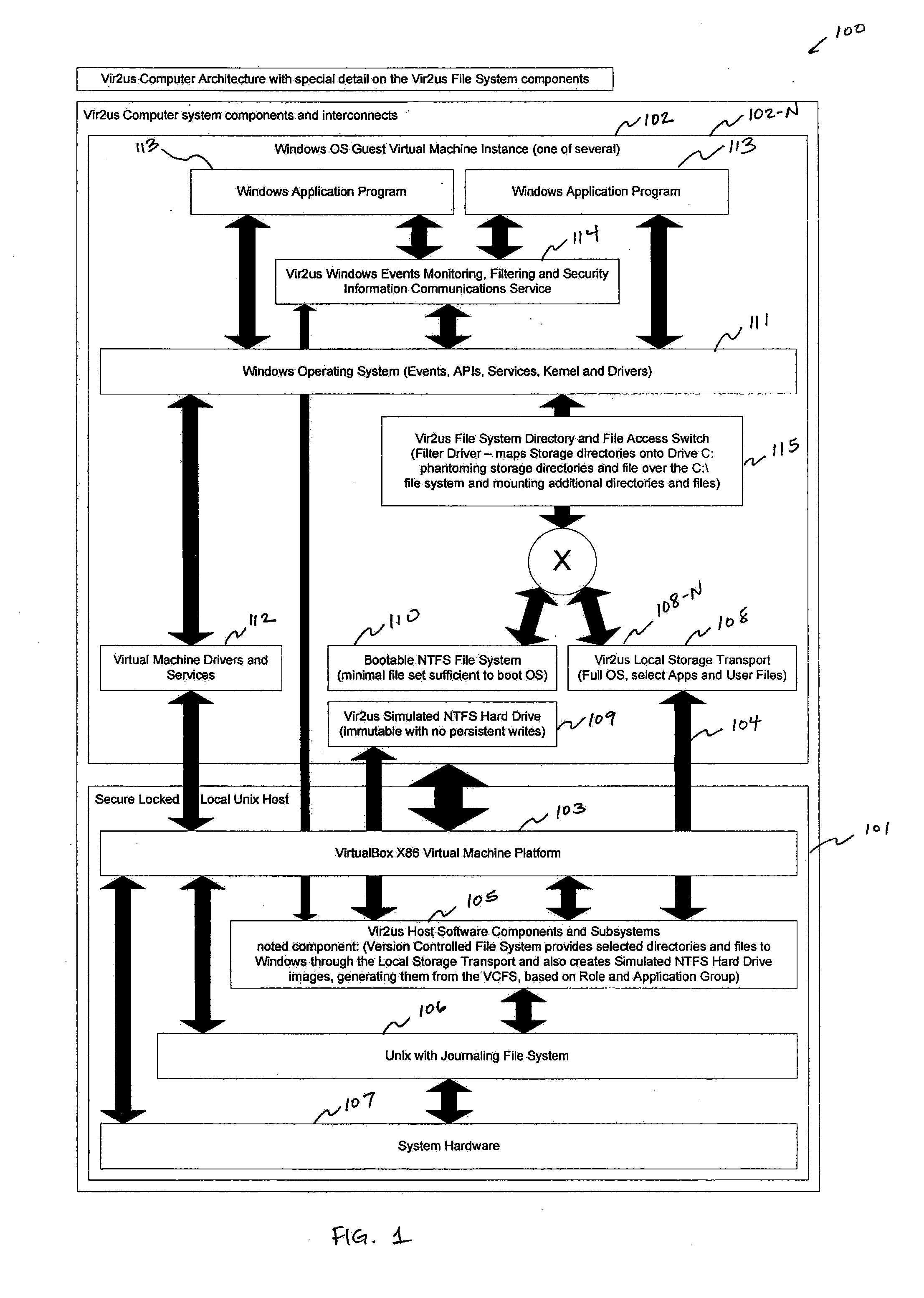
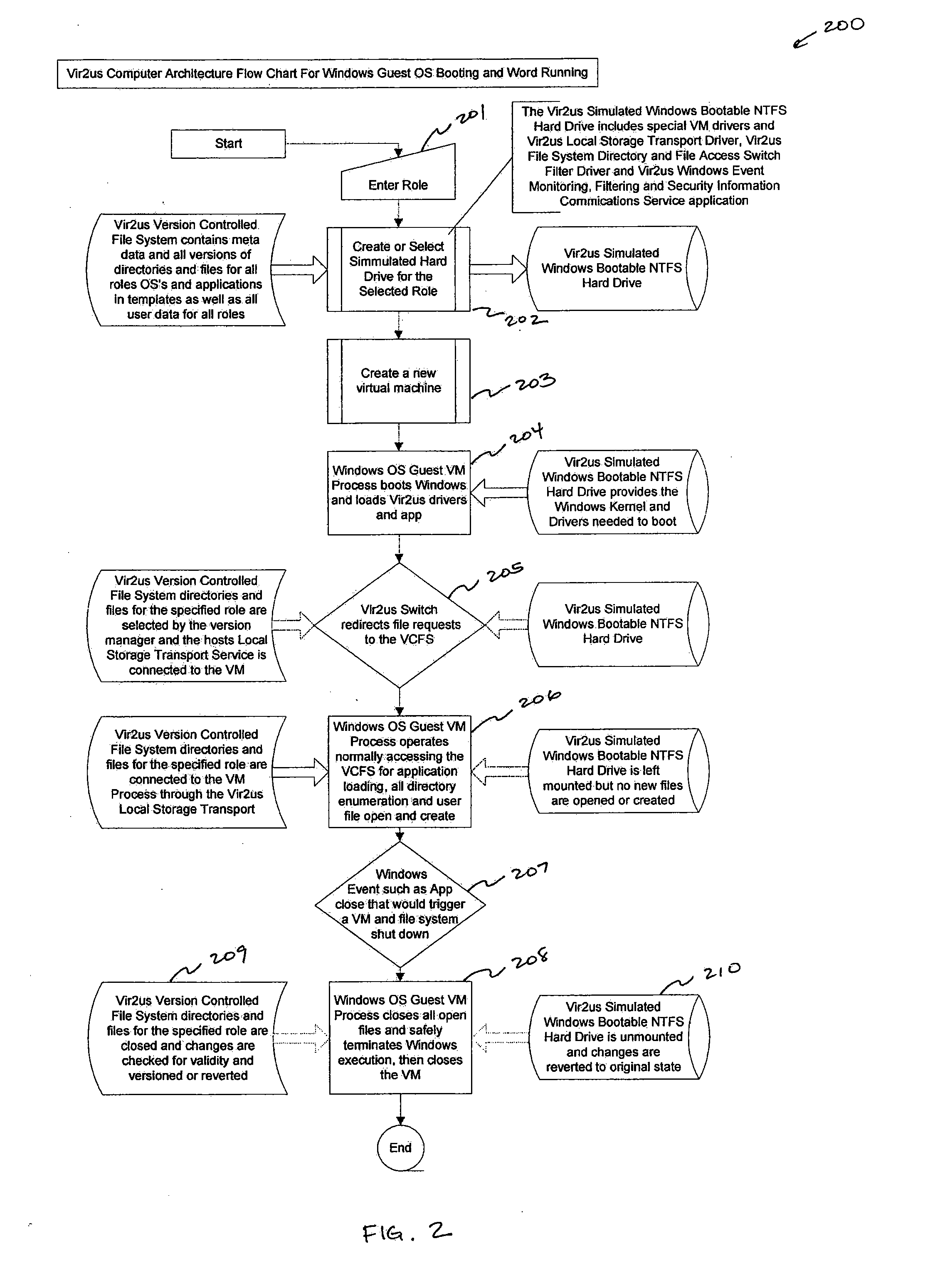
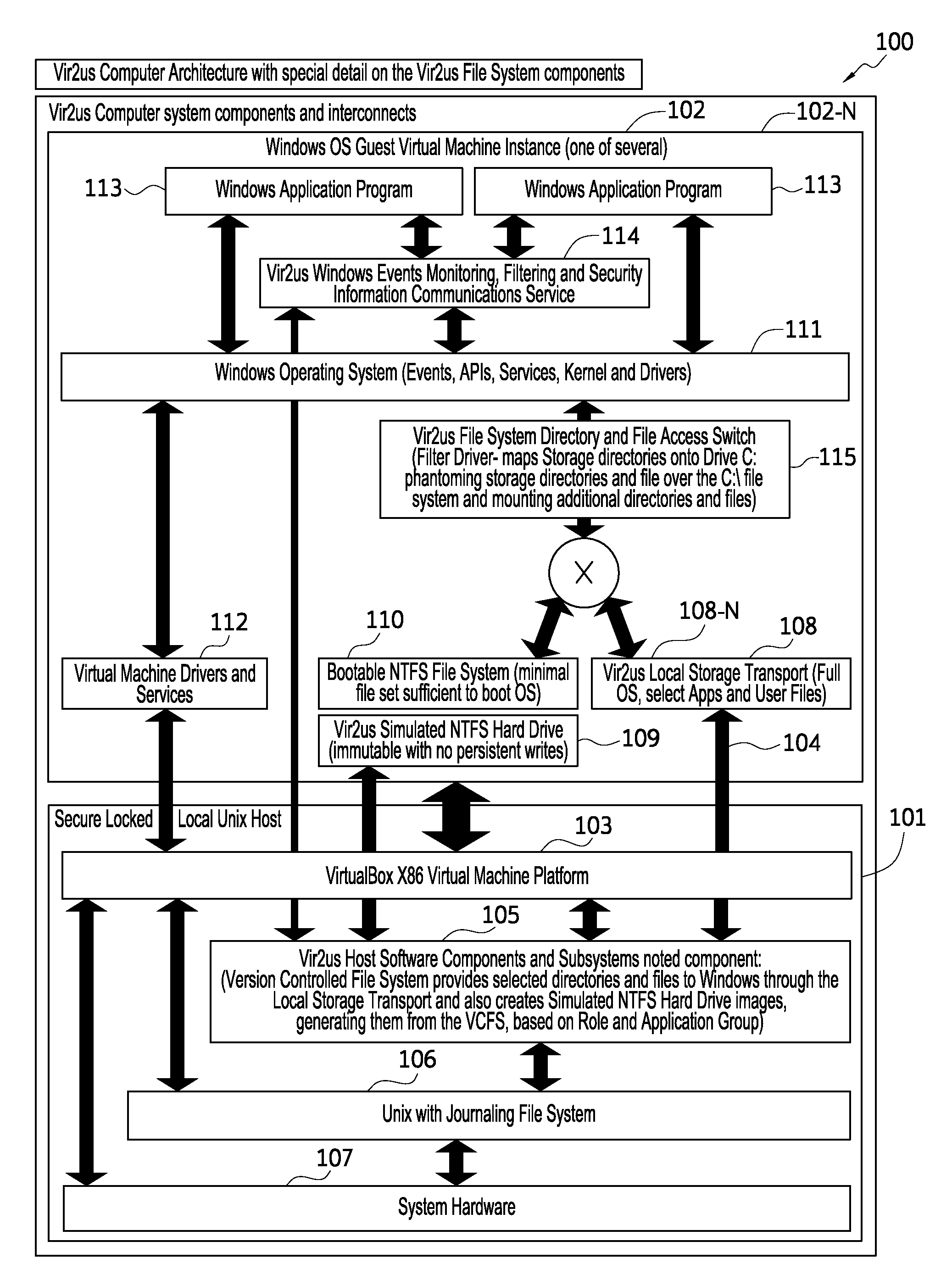
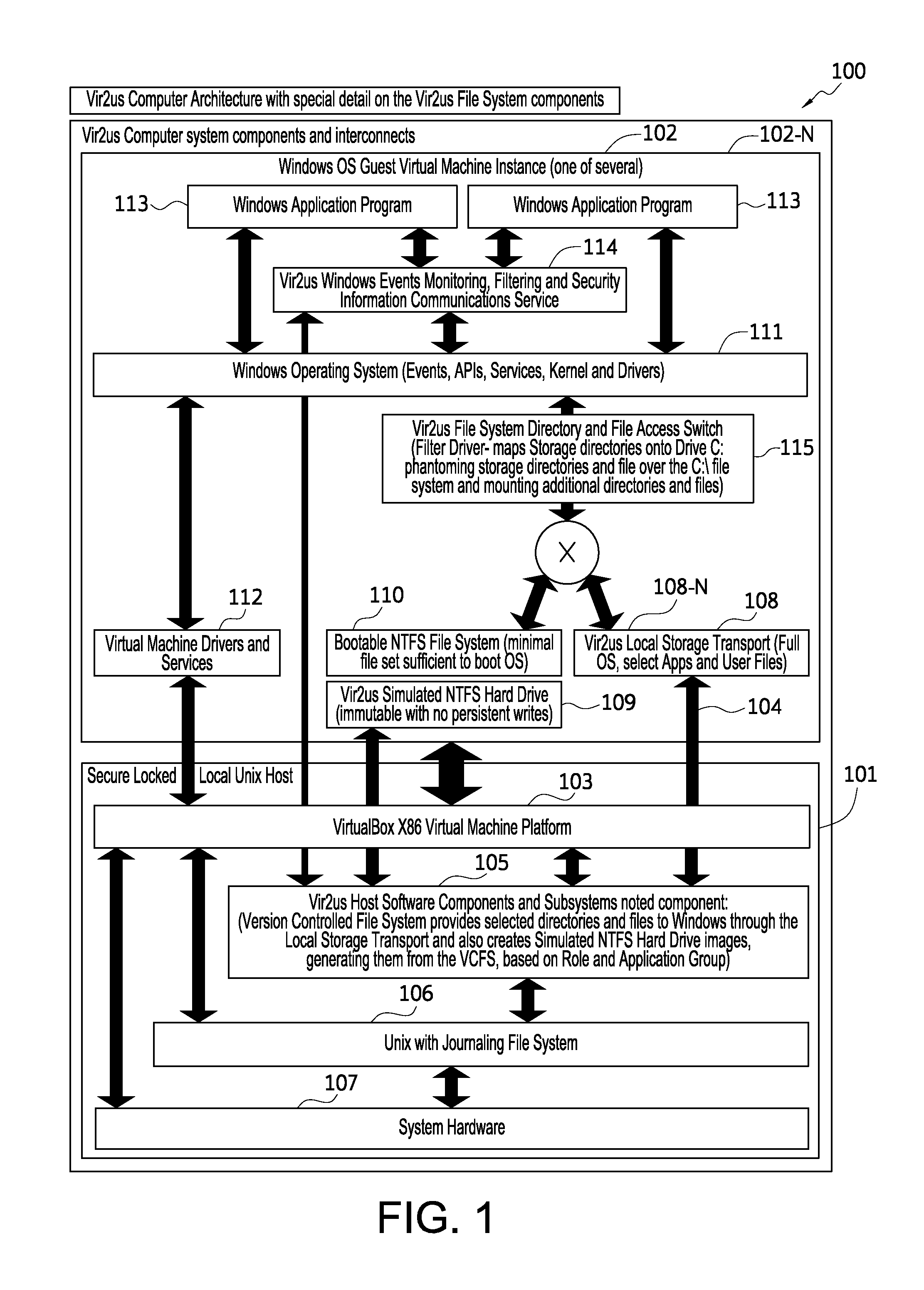
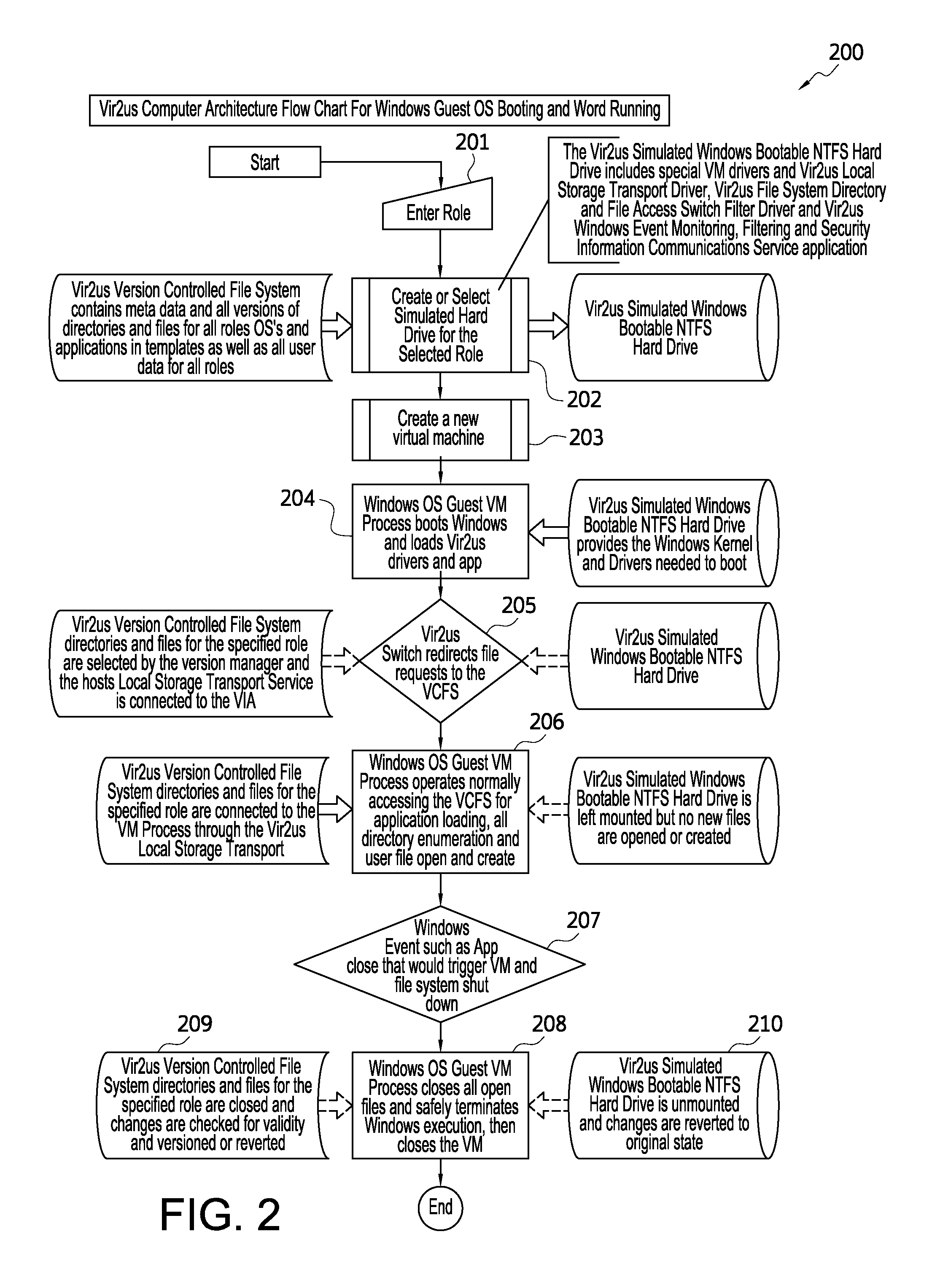
Computer system architecture and method having isolated file system management for secure and reliable data processing
ActiveUS20080184218A1Avoid lostComputer security arrangementsSpecific program execution arrangementsData processing systemReliable computing
System, method, computer, and computer program for secure data processing of potentially malicious code and documents or other data that may contain malicious code. System, method, computer for a secure and reliable computing environment to protect against data loss and / or corruption to provide secure and reliable data processing.
Owner:VIR2US
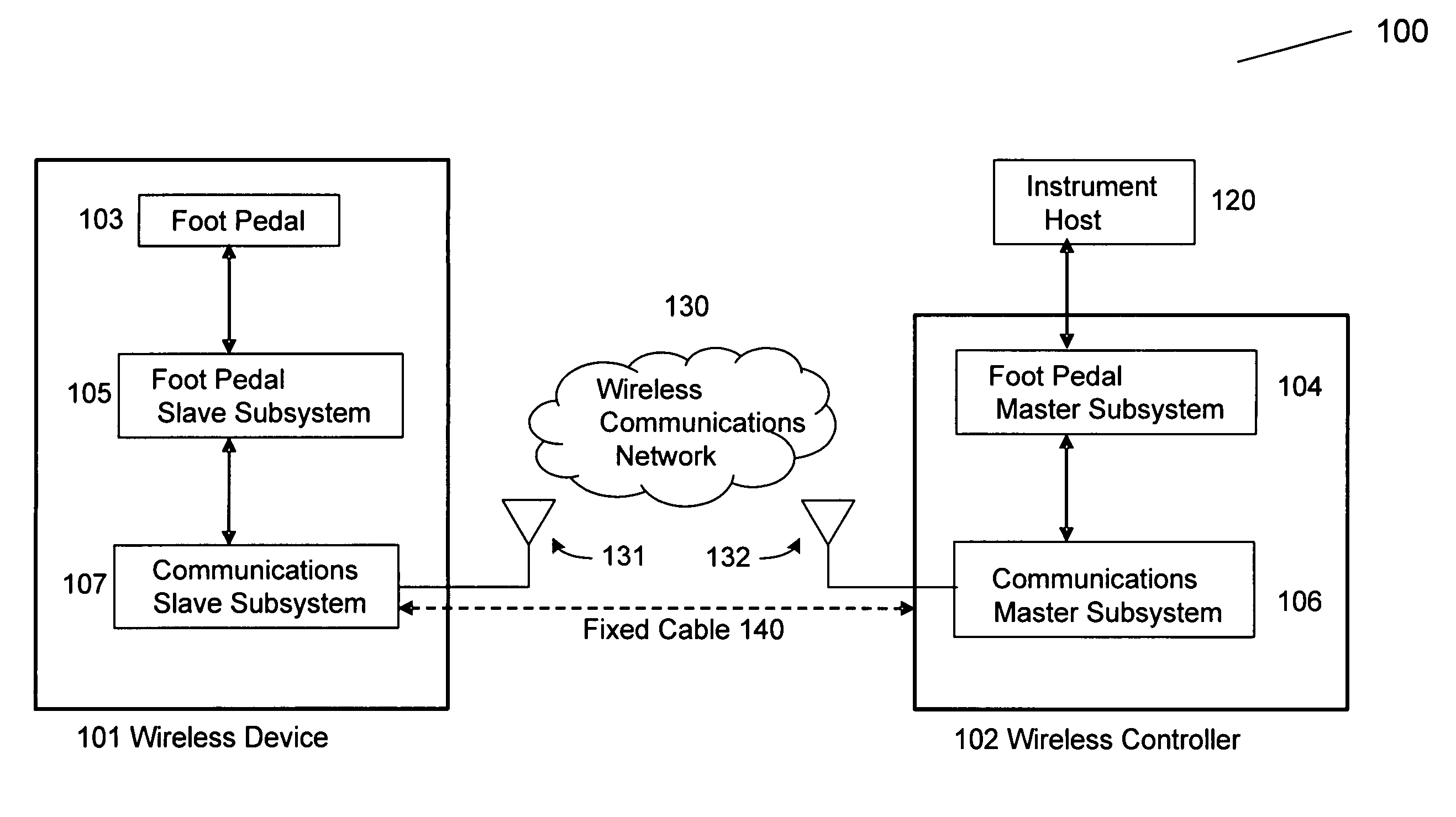
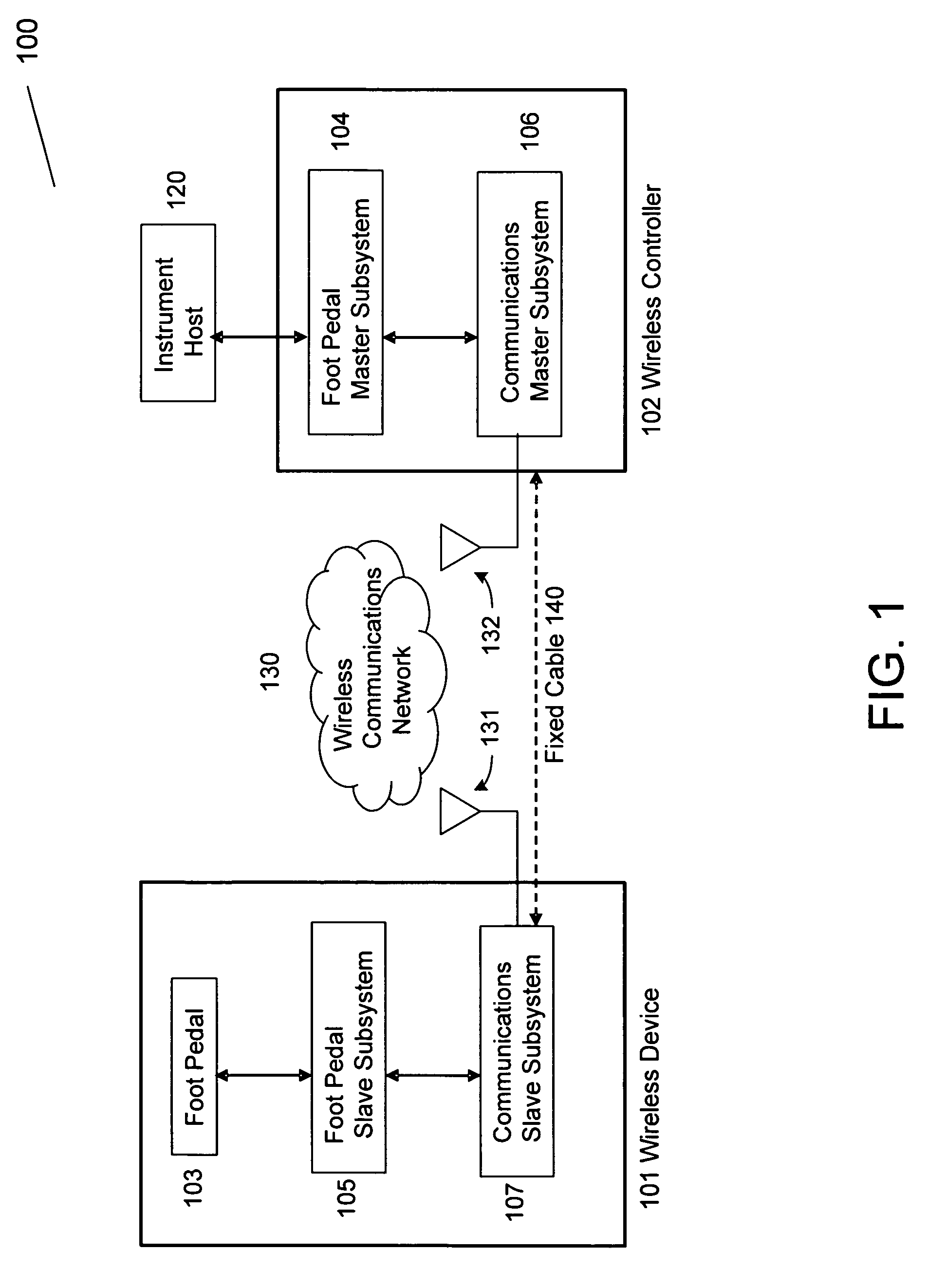
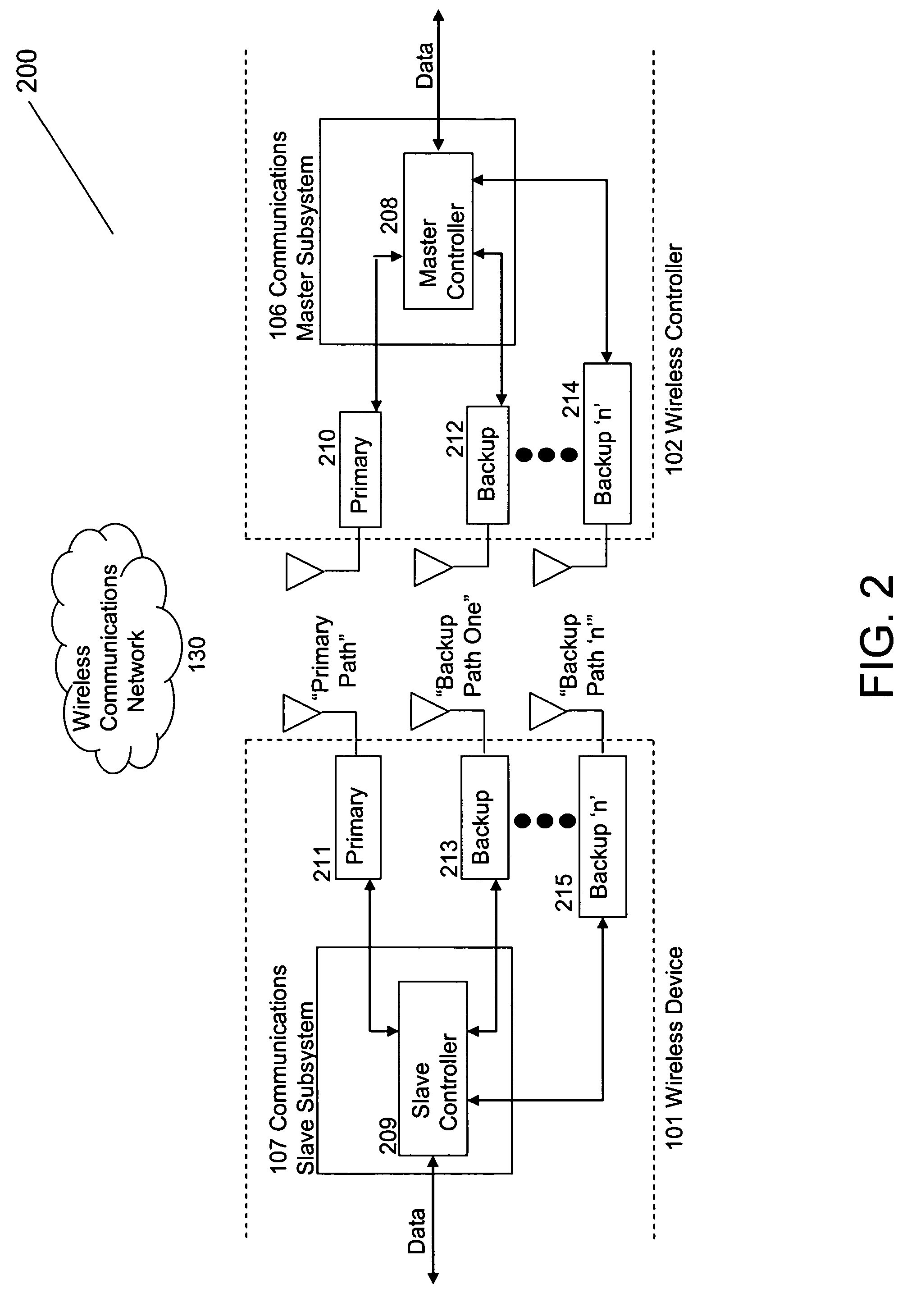
Reliable communications for wireless devices
A method and apparatus for connectivity management of a wireless device is provided, such as a wireless medical device. The method comprises providing a wireless connection between at least two medical devices, the at least two medical devices comprising a primary medical device and a secondary medical device, causing the primary medical device to transmit and the secondary medical device to receive state signals wirelessly across a plurality of communication data channels, and reporting a non-active state for one of the plurality of data channels from the primary medical device to the secondary medical device using the plurality of communication data channels.
Owner:ADVANCED OPTICS MEDICAL INC
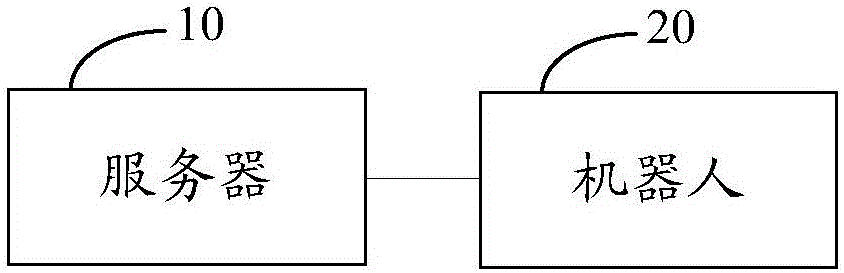
Robot system and method and server for controlling robot
InactiveCN106378780AImprove intelligenceExpand application service scenariosProgramme-controlled manipulatorRobotic systemsReliable computing
The embodiment of the invention discloses a robot system which comprises a server and at least one robot, wherein the server and the robot communicate with each other through a wireless link or a wire link; the robot is used for sending collected surrounding environmental information to the server; the server is used for receiving a task instruction, getting an action sequence and motion parameters of all actions in the action sequence according to the task instruction and the environmental information, and sending the motion parameters of the actions in the action sequence to the robot one by one according to the sequence of the actions in the action sequence; and the robot is used for performing corresponding actions according to the received motion parameters. The robot system provided by the embodiment of the invention separates a task planning step from the robot body, puts the task planning step in the charge of the server, can meet various concurrent highly real-time and highly reliable computation requirements in a task performing process of the robot, enables the robot to finish more tasks that are more complicated, improves intelligence of the robot, and enlarges the application service scene of the robot.
Owner:AUBO BEIJING ROBOTICS TECH CO LTD
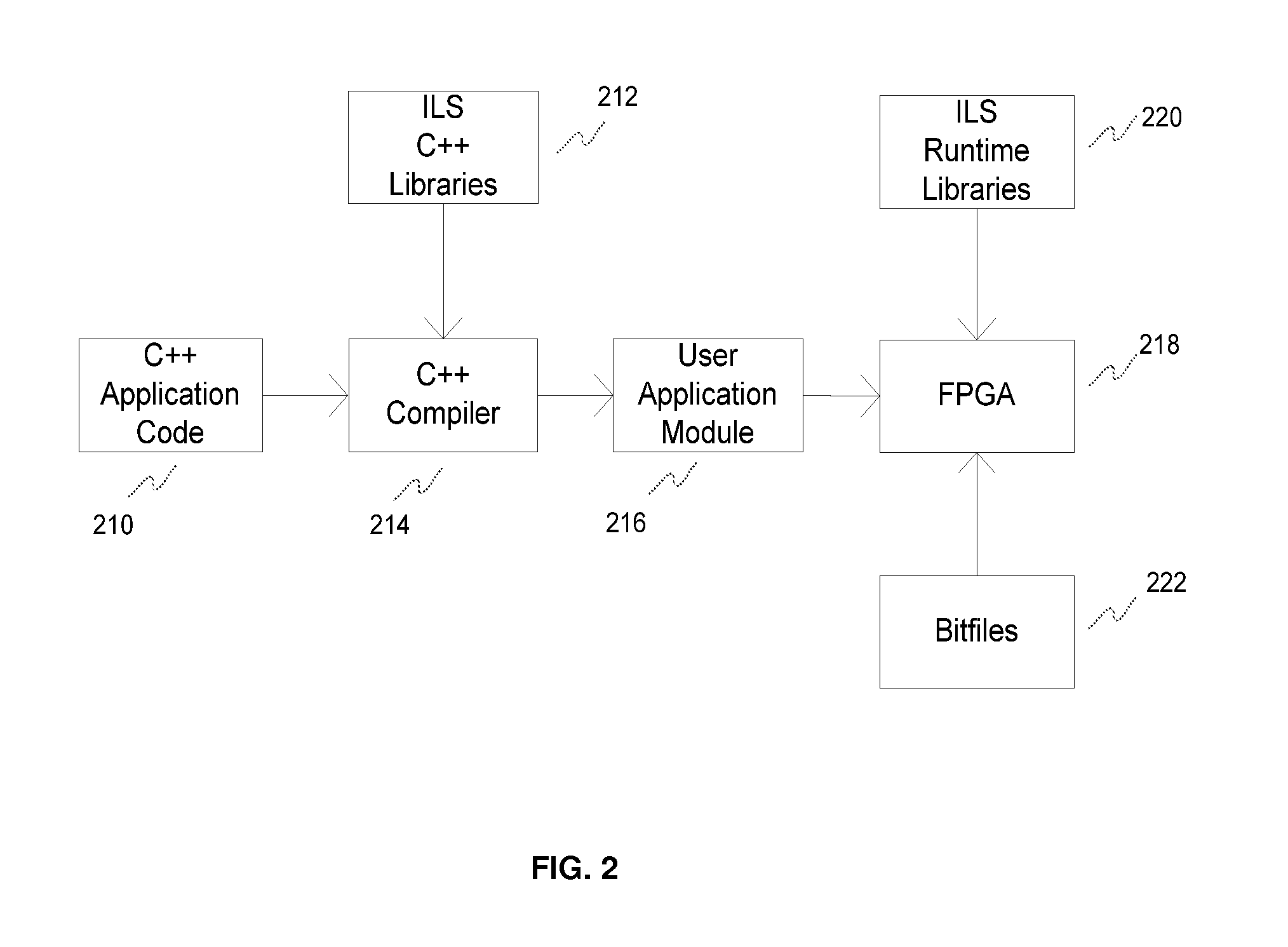
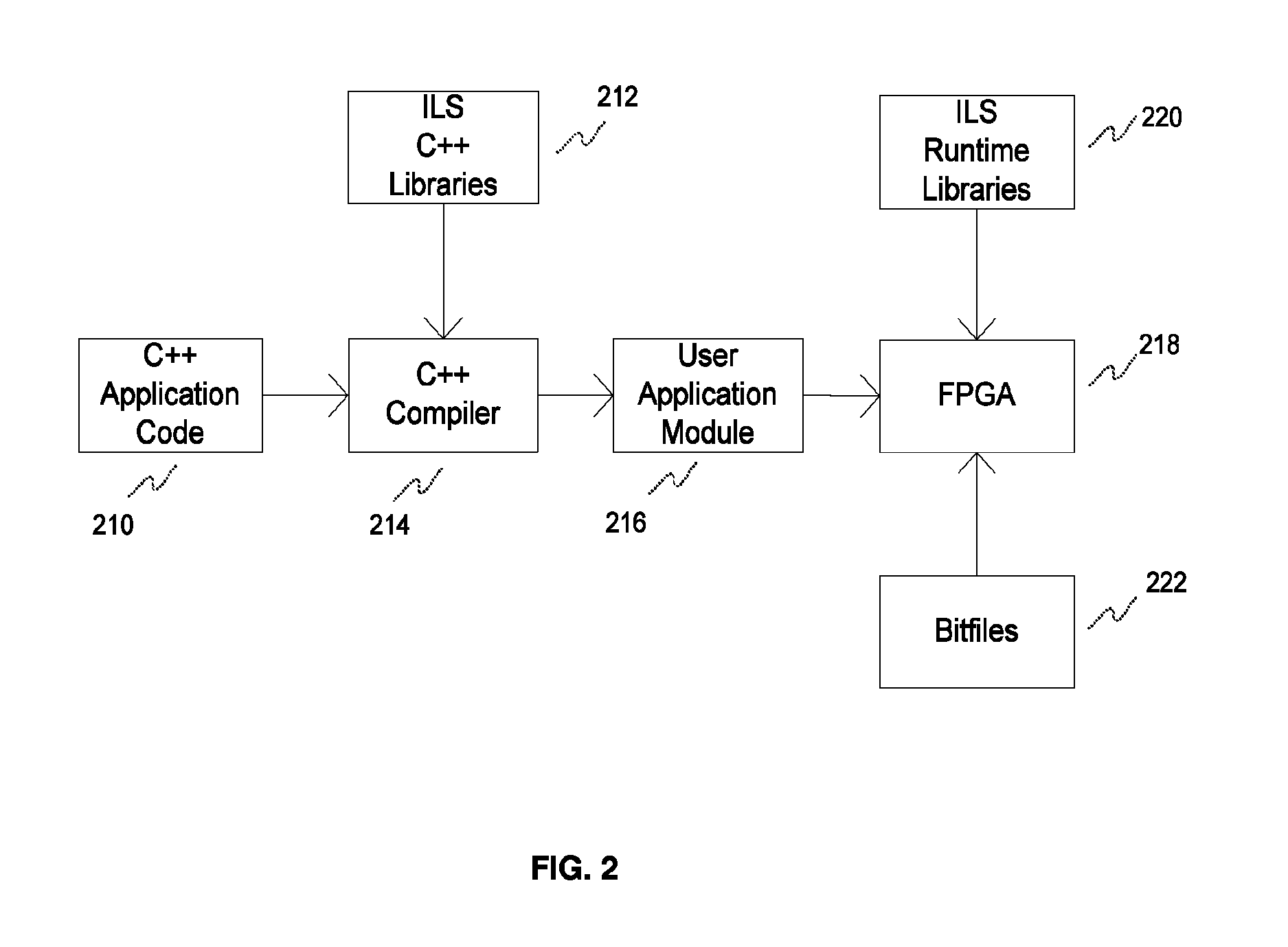
Reconfigurable computing system and method of developing application for deployment on the same
A method of developing an application for deployment on a computing system. The computing system includes a processor and a reconfigurable logic in communication with the processor for configuration thereby. The method includes programming the processor with hardware-neutral instructions in a high-level software programming language. The instructions are representative of an application configured to execute at least partially on the reconfigurable logic. The method further includes instantiating elements from a library of elements compatible with the high-level programming language; and constructing programmatically a generic data graph representative of the application to be mapped at least partially onto the reconfigurable logic. The generic data graph is expressed as streams of records flowing between operators. A computing system is also disclosed. By presenting an instruction level streaming data processing model that expresses an application as operators and data flows, the invention provide several advantages such as design portability.
Owner:ISHEBABI HAROLD
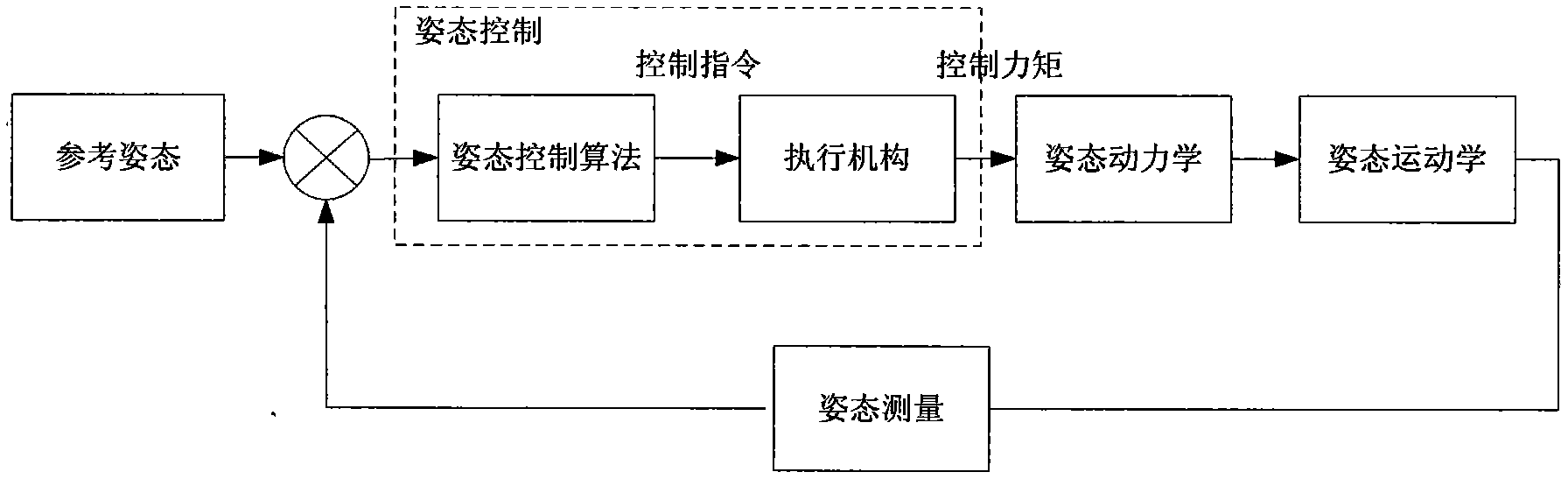
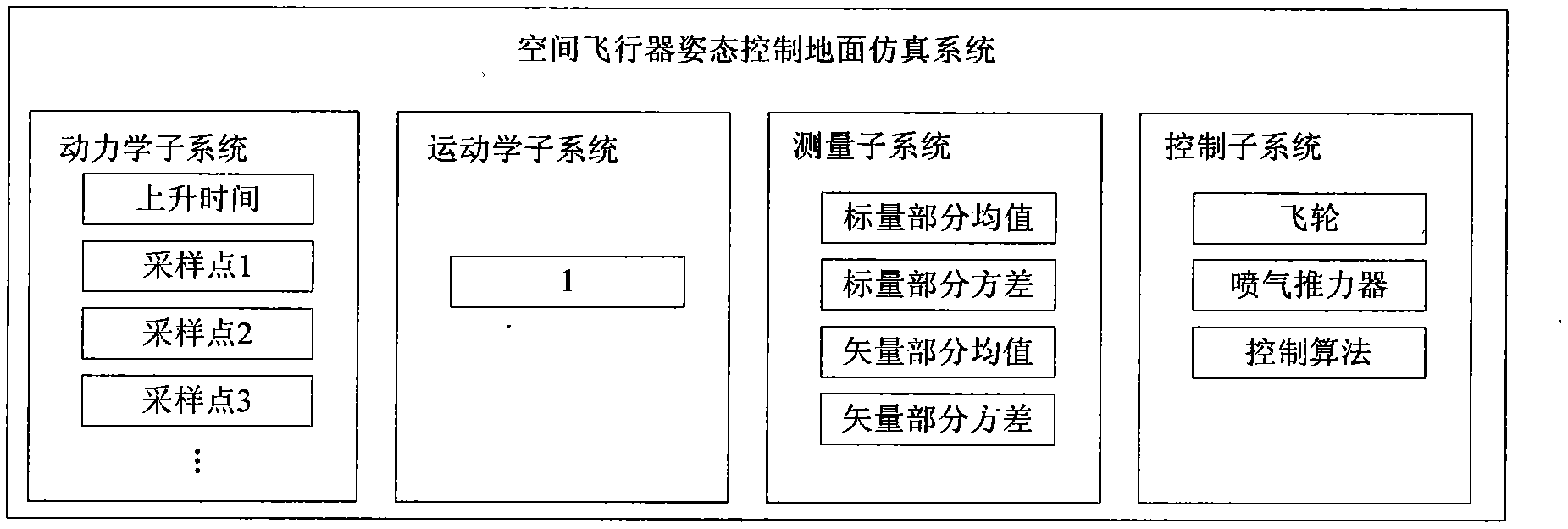
Method for performance evaluation of spacecraft attitude control ground simulation system
ActiveCN104077456ASimple calculationSpecial data processing applicationsKinematicsSpacecraft attitude control
The invention provides a method for performance evaluation of a spacecraft attitude control ground simulation system. According to the method, the credibility of a dynamic system, a kinematics system, a measurement system and a control system is studied based on the simulation system credibility theory, the overall credibility of the spacecraft attitude control ground simulation system is obtained through comprehensive calculation, and then the performance of the spacecraft attitude control ground simulation system is evaluated. According to the evaluation method, the credibility of the ground simulation system and an actual satellite attitude control system is considered from all aspects, simulation data are fully utilized, and the credibility of the ground simulation system is described objectively and quantitatively; the theoretical basis is reliable, the calculation process is simple, the application range is wide, and a new idea and reference are provided for performance evaluation study of other simulation systems.
Owner:HARBIN INST OF TECH
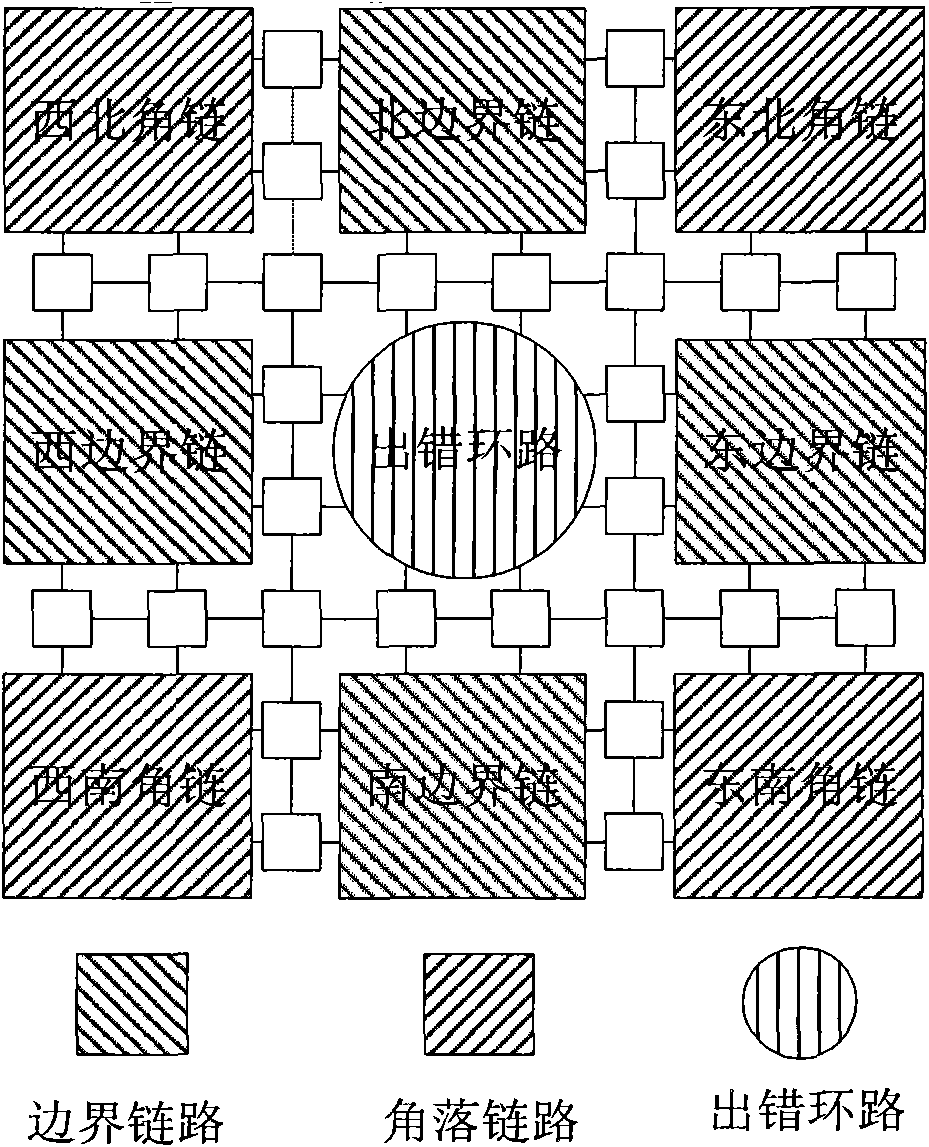
Low-complexity and extensible fault-tolerant routing algorithm specific to network on chip
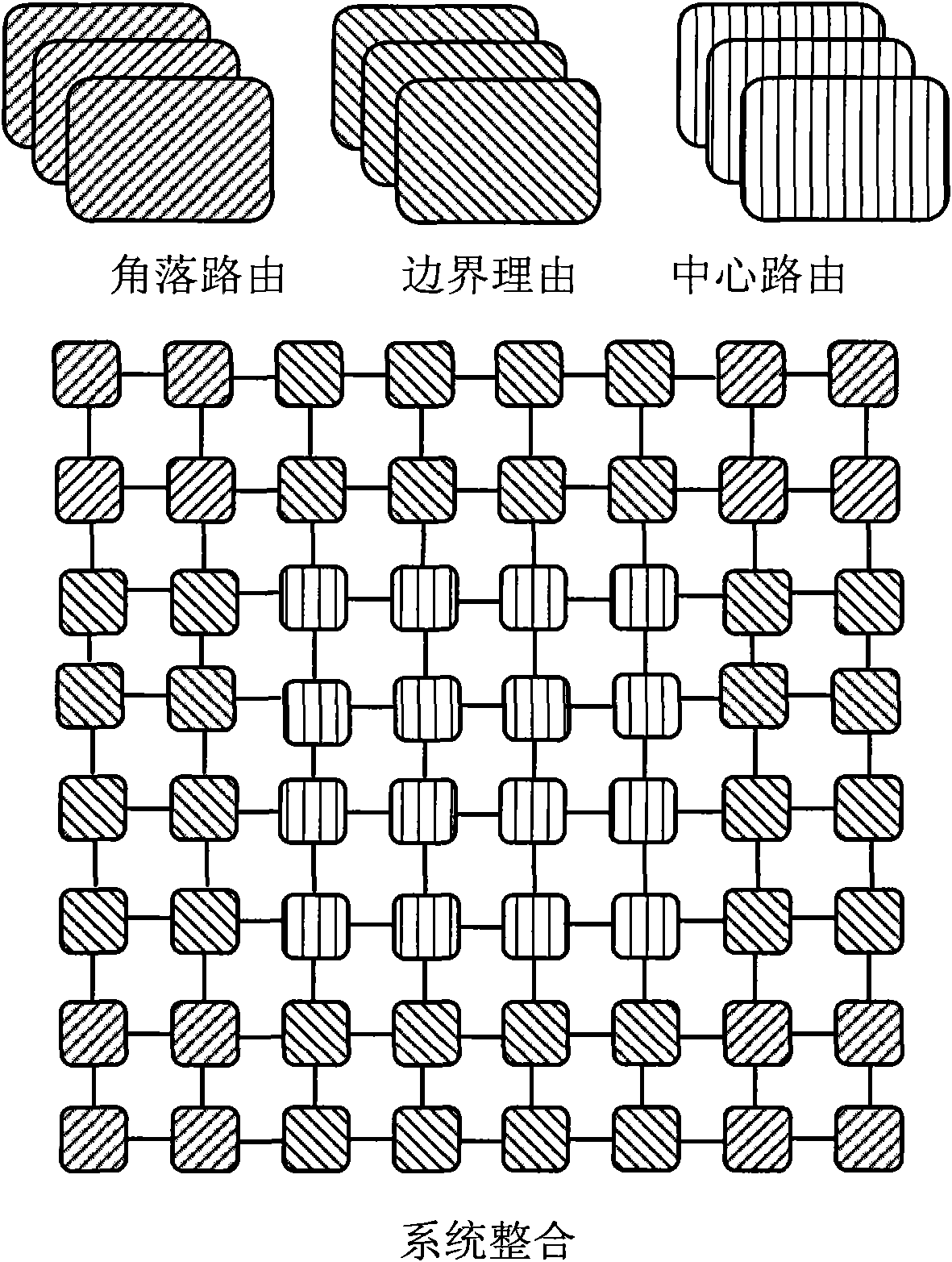
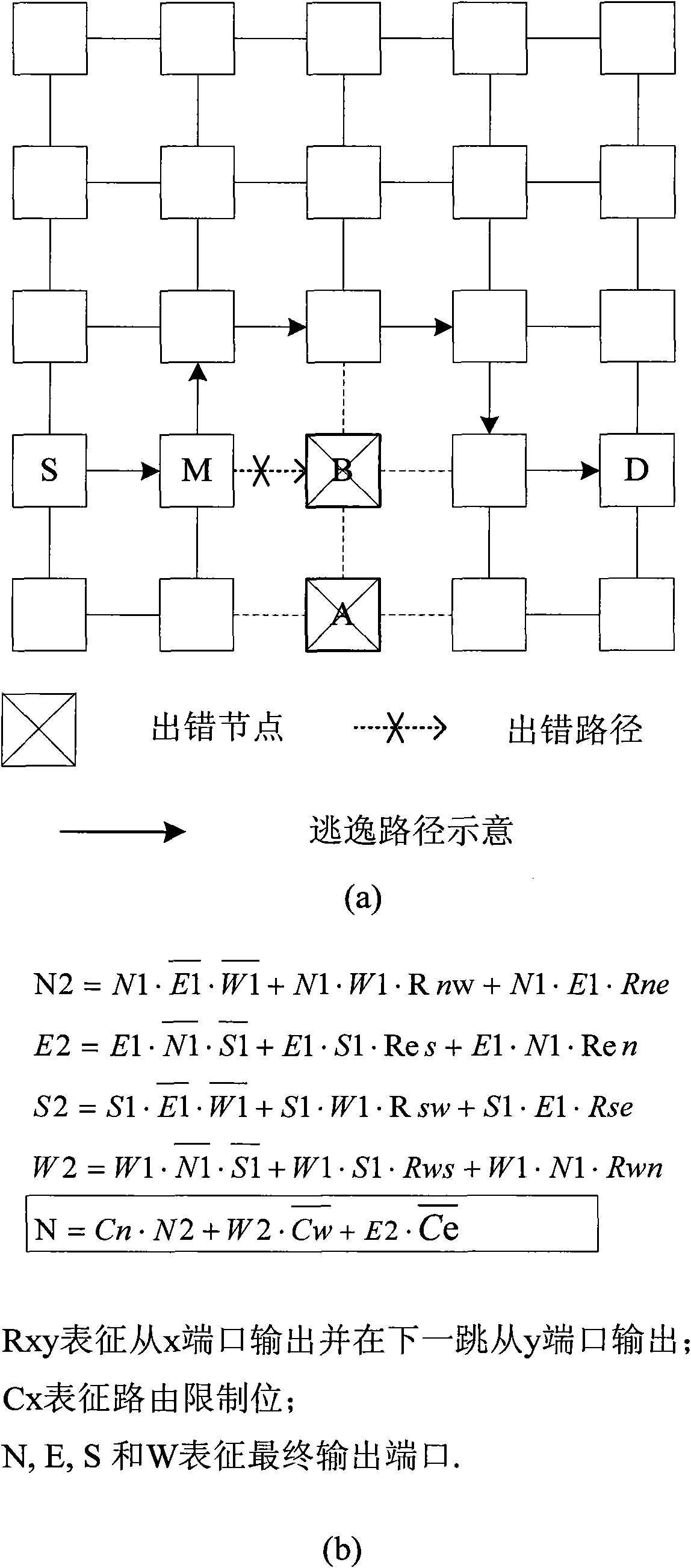
InactiveCN101834797AOverhead remains constantImprove scalabilityError preventionData switching networksRound complexityReliable computing
The invention belongs to the field of reliable computing technologies and particularly relates to a low-complexity and extensible fault-tolerant routing algorithm for a network on chip. The routing algorithm adopts strategies of system partition and divide-and-conquer, and can better tolerate faults occurred in different parts of a central zone, four boundaries and four corner parts. Under the circumstance of certain nodes fault, the entire system can still work, thereby the fault-tolerant capability and the continuous service capability of the system are greatly enhanced, the yield of chips and the service life of the system are improved in a disguised form, and the cost of the system is reduced. The routing algorithm is applicable to occasions having extremely high requirement on reliability, such as aerospace, military network, financial transactions, banks and other key fields as well as the fields, such as civilian use, consumer electronics, and the like.
Owner:FUDAN UNIV
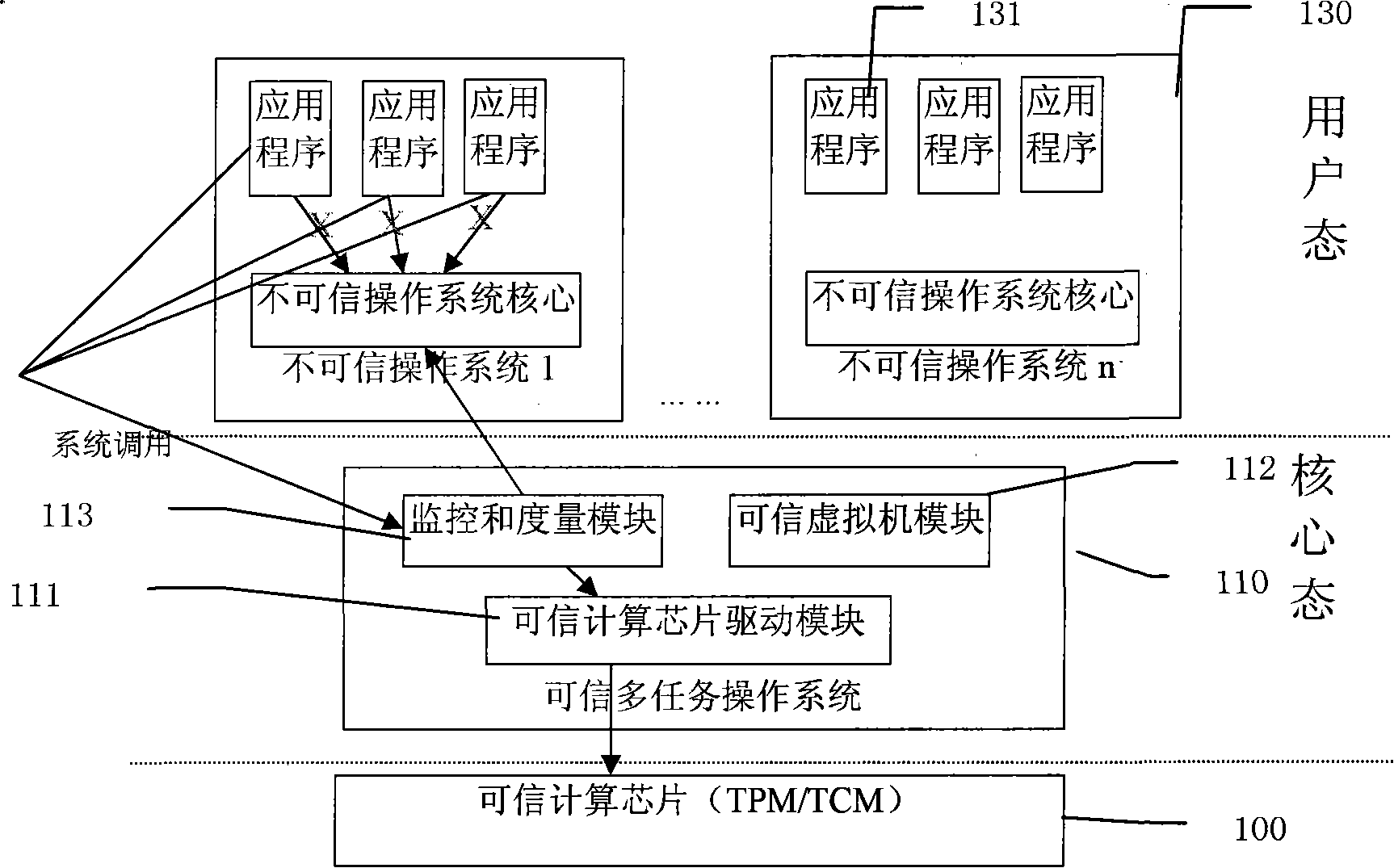
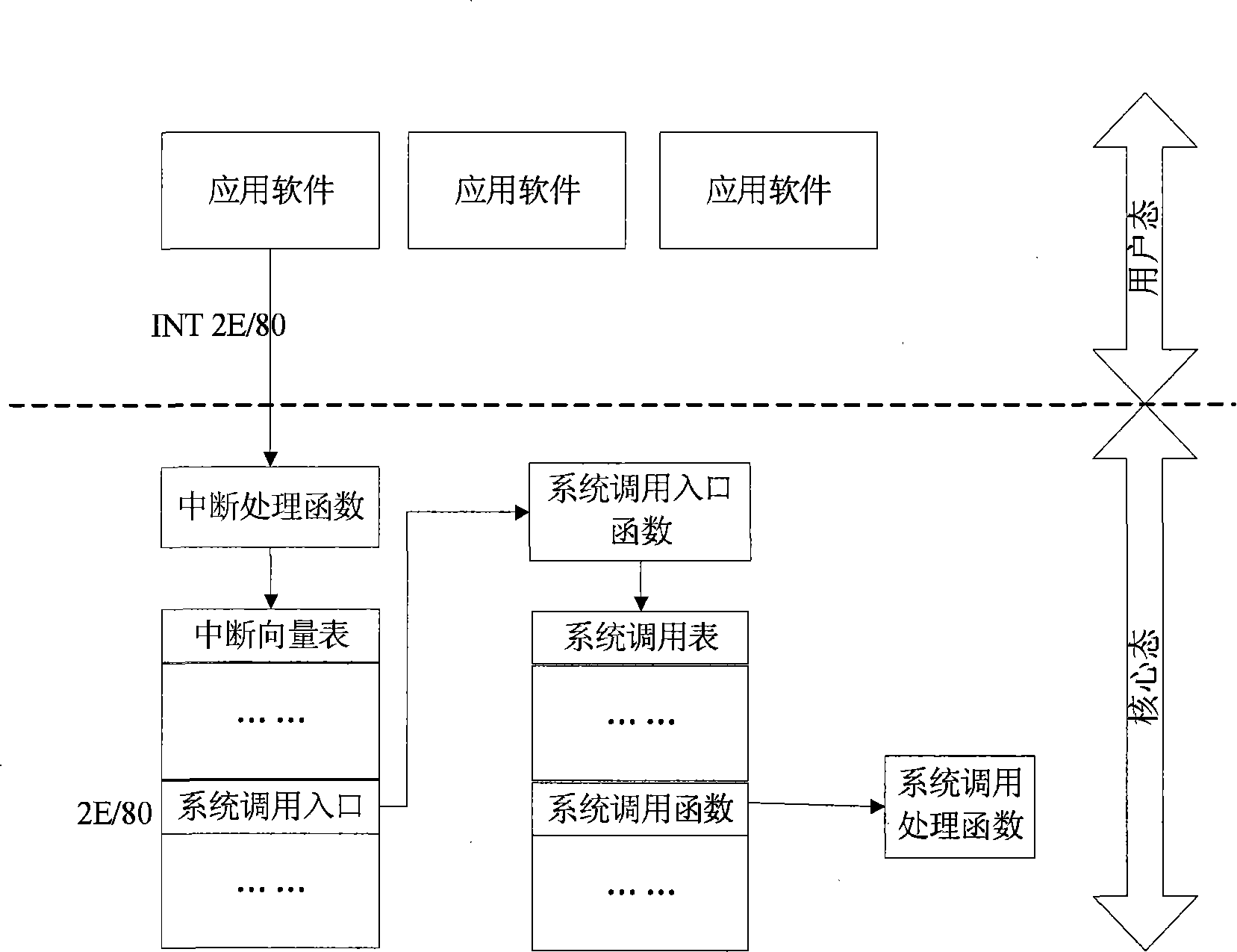
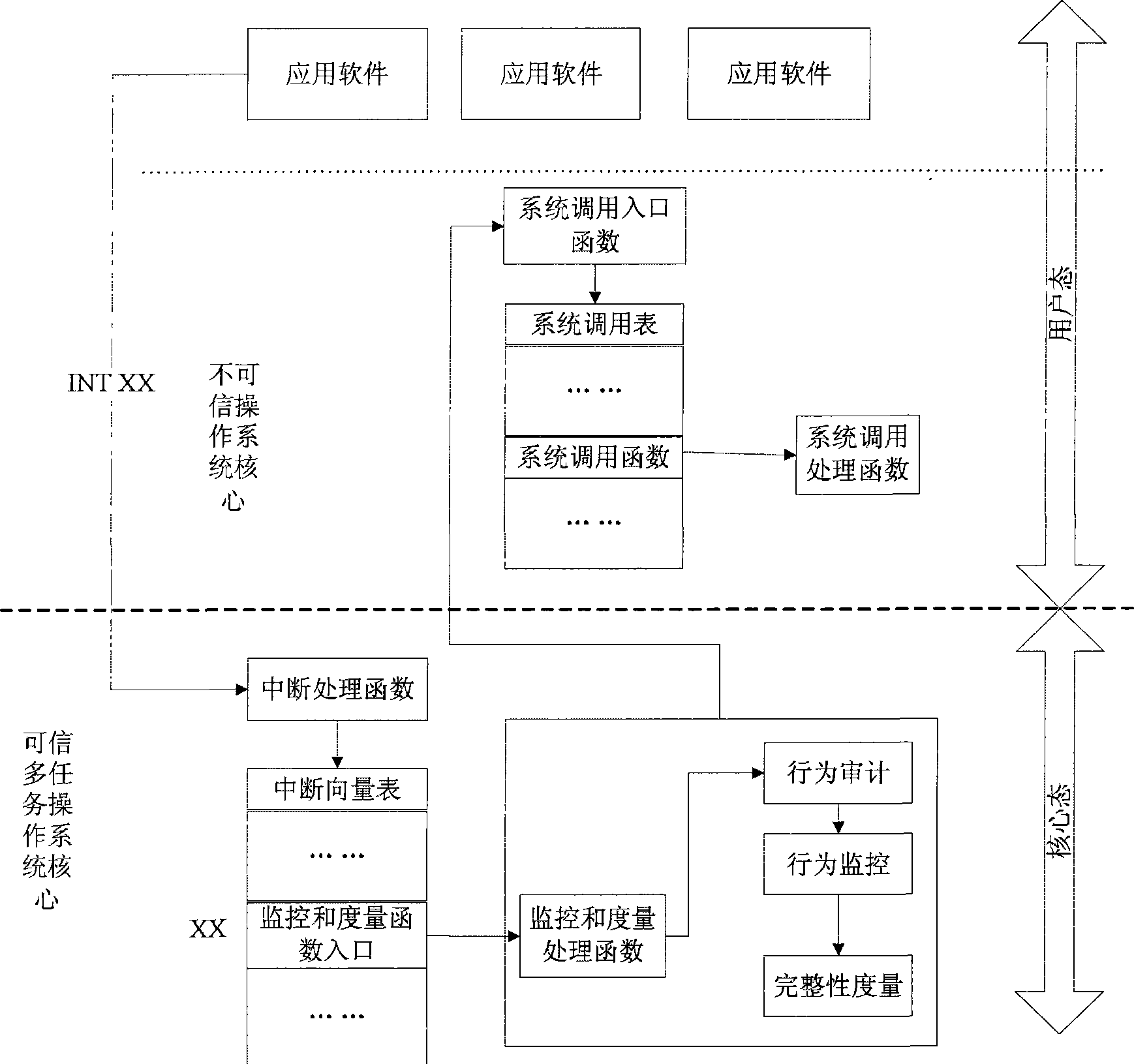
Method for implementing reliable computation based on reliable multi-task operating system
ActiveCN101246537AProtect Software PropertyLow costPlatform integrity maintainanceOperational systemReliable computing
The invention realizes a measuring and monitoring method for a credible multi-task operating system to an incredible operating system making use of a credible computing technology. The credible multi-task operating system is composed of a credible computing chip drive module ,a credible virtual machine module, and a measuring and monitoring module, the credible multi-task operating system runs one or more incredible operating systems making use of the credible virtual machine module, the actions such as all the system call of application program, etc. in the incredible operating system are redirected by modifying the vector terminal, etc. and then operated by the measuring and monitoring module of the credible multi-task operating system, so as to realize the measuring and monitoring to the actions of the incredible operating system. The incredible operating system includes various editions such as Windows or Linux operating system. The invention can be used in PC, meanwhile the users'previous operating interface is not changed, the security and credibility of the system can be effectively enhanced, and the users' habits can be better compatible.
Owner:CHINA STANDARD SOFTWARE
Computer system architecture and method having isolated file system management for secure and reliable data processing
ActiveUS8775369B2Avoid lostDigital data processing detailsComputer security arrangementsData processing systemSystems management
System, method, computer, and computer program for secure data processing of potentially malicious code and documents or other data that may contain malicious code. System, method, computer for a secure and reliable computing environment to protect against data loss and / or corruption to provide secure and reliable data processing.
Owner:VIR2US
Reconfigurable computing system and method of developing application for deployment on the same
A method of developing an application for deployment on a computing system. The computing system includes a processor and a reconfigurable logic in communication with the processor for configuration thereby. The method includes programming the processor with hardware-neutral instructions in a high-level software programming language. The instructions are representative of an application configured to execute at least partially on the reconfigurable logic. The method further includes instantiating elements from a library of elements compatible with the high-level programming language; and constructing programmatically a generic data graph representative of the application to be mapped at least partially onto the reconfigurable logic. The generic data graph is expressed as streams of records flowing between operators. A computing system is also disclosed. By presenting an instruction level streaming data processing model that expresses an application as operators and data flows, the invention provide several advantages such as design portability.
Owner:ISHEBABI HAROLD
Method and apparatus for sociable computing in ad-hoc and configured peer-to-peer networks
ActiveUS9262743B2Multiple digital computer combinationsOffice automationProgram instructionReliable computing
Executing a program structure for spanning a thread of control and a thread of execution across multiple peers in a peer-to-peer network comprises generating a program structure comprising a plurality of program instructions. A first of a plurality of network peers then executes a portion of the program instructions which initiates the execution of code hosted by said first network peer, where said portion comprising fewer than all program instructions. The first network peer then migrates one or more of the program instructions, including one or more controlling program instructions, together with any requisite data, some of which may include control data, to at least one other of the plurality of network peer. The at least one other network peer then continues execution of the program instructions in accordance with the controlling program instructions and control data until one or more of the objections of the program structure are achieved.
Owner:ZEROTOUCHDIGITAL
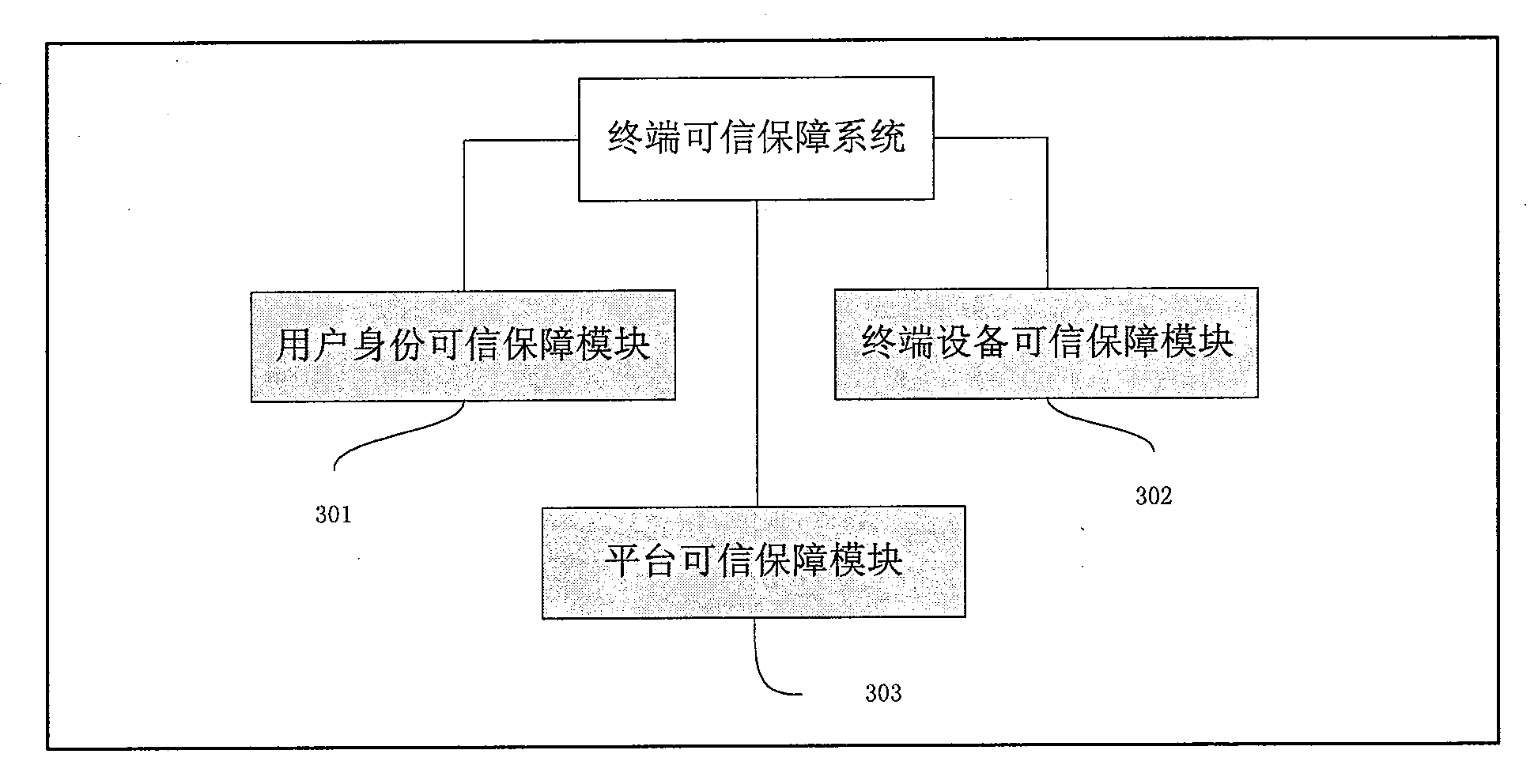
Terminal credible security system and method based on credible computing
ActiveCN101667232AGuaranteed confidentialityIntegrity guaranteedDigital data protectionReliable computingTerminal equipment
The invention relates to a terminal credible security system which comprises a user identity credible security module, a terminal device credible security module, a platform credible security module.The user identity credible security module is used for setting lists for storing important documents of users and utilizing a kernel protection mode to ensure that the lists of the important documentscan not be revised by non-authorized users; the terminal device credible security module is used for controlling the writing function of mobile devices of U disks, and the like; and the platform credible security module is used for preventing malicious programs from operating. The invention also relates to a terminal credible security method which comprises a user identity credible security step,a terminal device credible security step and a platform credible security step, wherein the user identity credible security step is used for setting the lists for storing the important documents andensuring that the lists of the important documents can not be revised; the terminal device credible security step is used for controlling the writing function of the mobile devices of U disks, and thelike; and the platform credible security step is used for preventing the malicious programs from operating.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
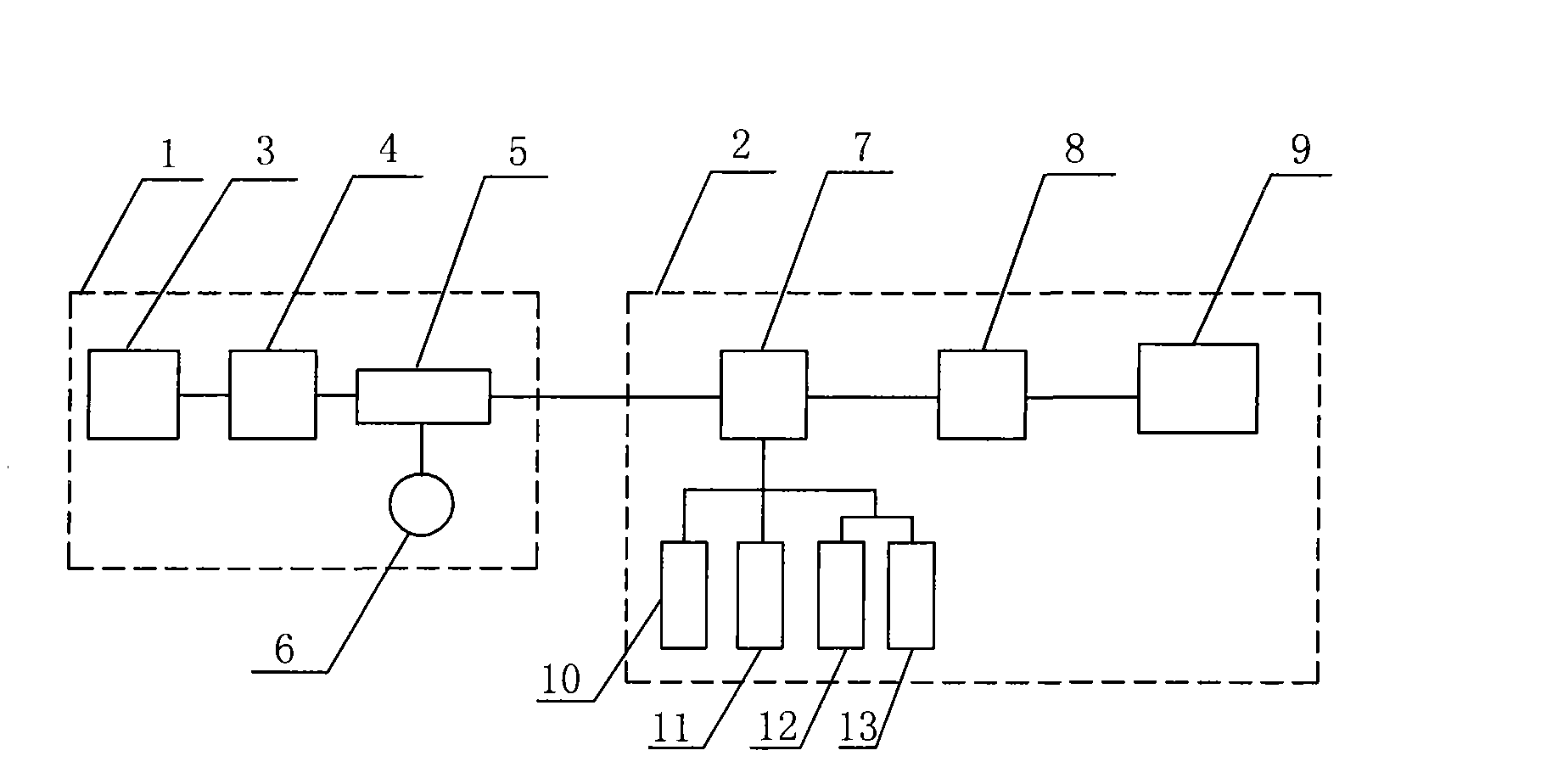
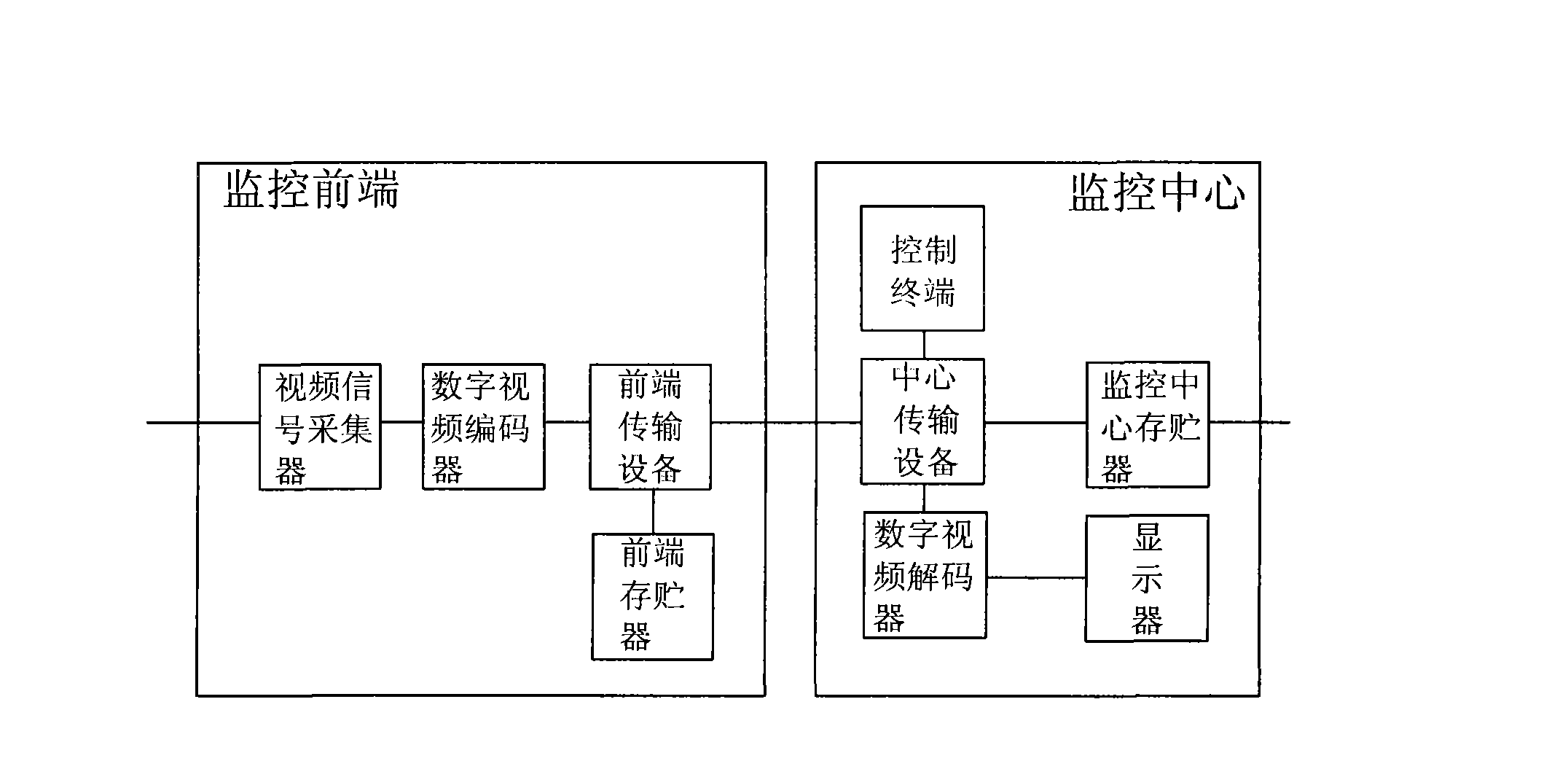
Reliable video system using digital signature technology
ActiveCN101516025AIncrease the difficultyGuaranteed credibilityPulse modulation television signal transmissionClosed circuit television systemsDigital videoCode module
The invention discloses a reliable video system using digital signature technology, comprising a video surveillance terminal and a surveillance center; wherein, the video surveillance terminal comprises a video signal collector which is connected with a reliable digital video encoder; the reliable digital video encoder is connected with front-end transmission equipment; the surveillance center comprises central transmission equipment connected with the digital video encoder which is connected with a monitor; the front-end transmission equipment is connected with a front-end memory; the central transmission equipment is connected with a central memory, a control terminal, a certificate management server and a reliability verification server; the reliable digital video encoder comprises an analog video input interface, a digital video coding module, a reliable computing module and a network interface; the reliable computing module is connected with a special security chip. The system can greatly increase the difficulty and cost of secretly tampering with data, thus achieving the effects of effectively preventing tampering and maintaining reliability of video data.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
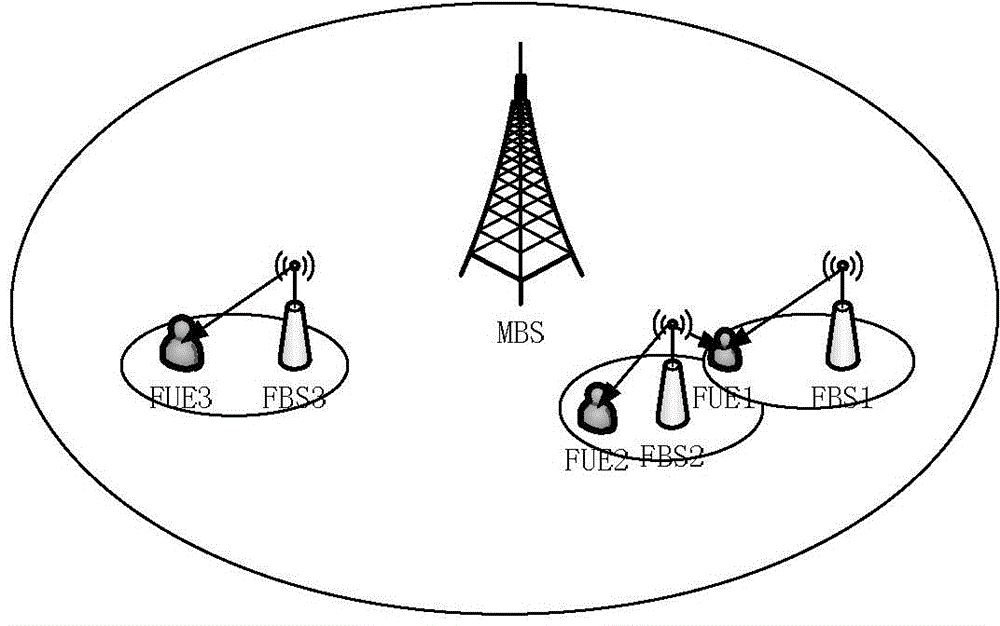
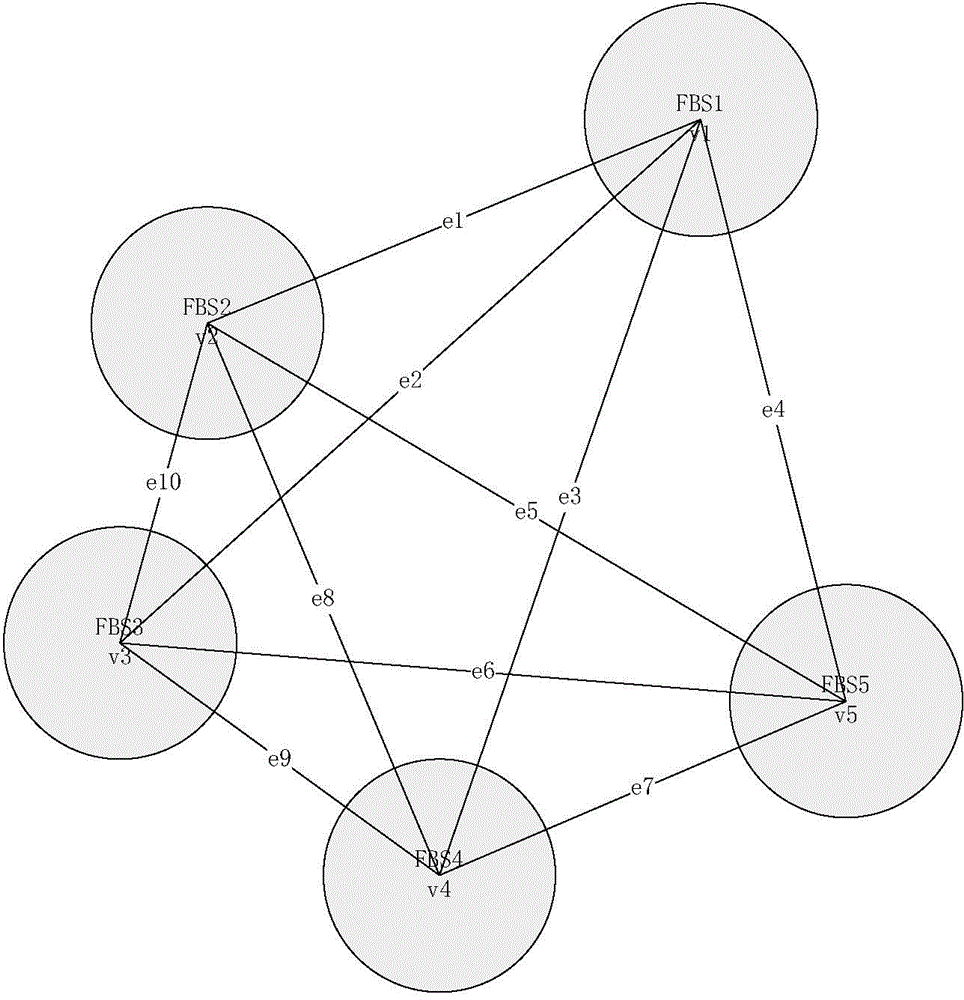
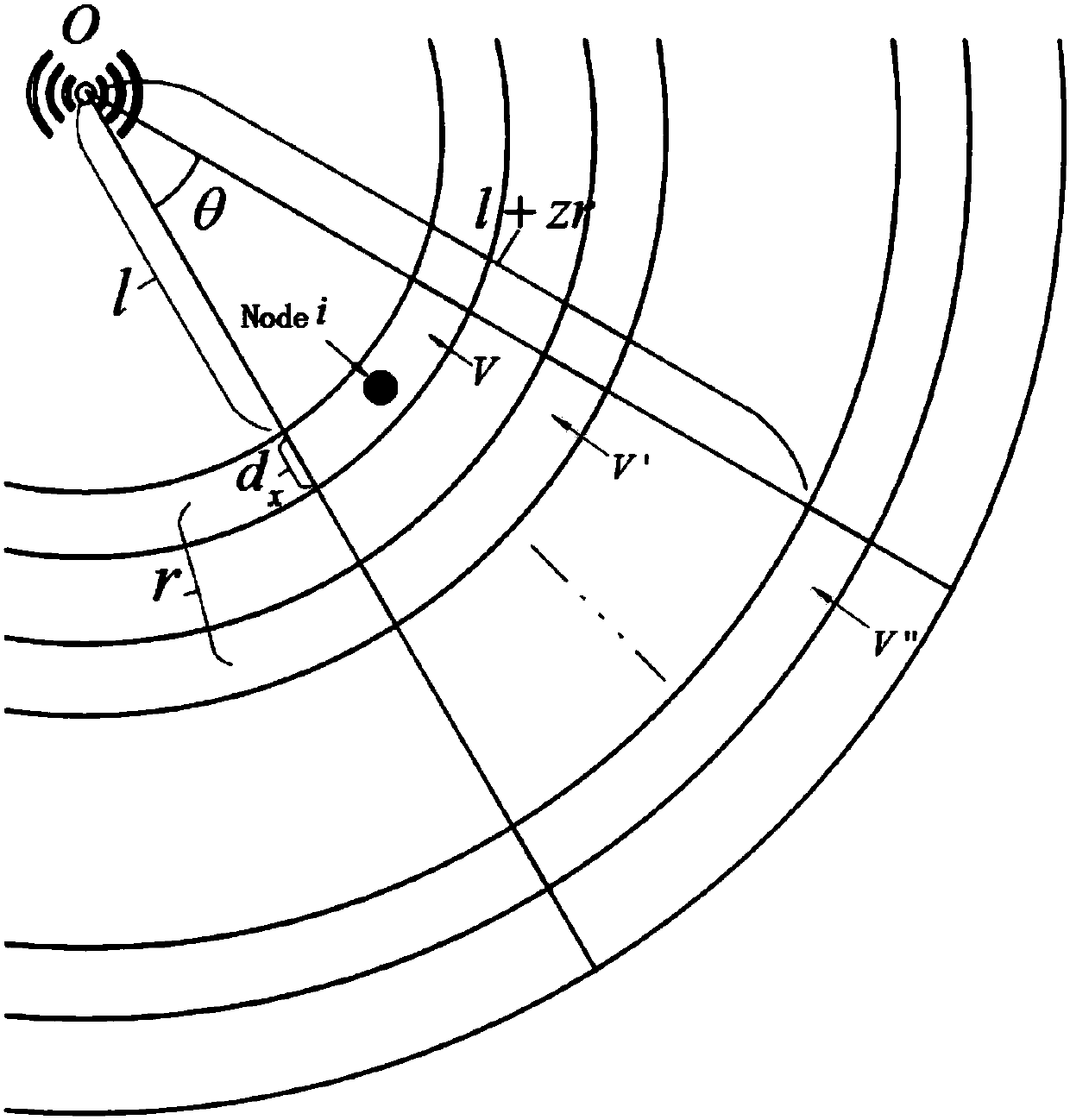
Reliable communication based femtocell user clustering method in cognition heterogenous network
ActiveCN104159313ASuppress mutual interferenceEnsure reliable communicationWireless communicationFrequency spectrumReliable computing
The invention discloses a reliable communication based femtocell user clustering method in a cognition heterogenous network. The clustering method comprises the following steps: at the initial moment of each time slot, acquiring position information of non-clustered femtocell base stations by perceiving available spectrum of the stations; under the management of an integrated controller, obtaining path loss information among all femtocell base stations with communication users to be regarded as interference among the femtocell users; randomly selecting one existing femtocell user cluster for the non-clustered femtocell users, calculating the interference subjected by each femtocell base station; if all the femtocell base stations in the cluster satisfy the interference limiting condition, enabling the femtocell users to join the cluster; if not, selecting other clusters, and judging whether the femtocell users satisfy the condition to join the other clusters or not. The clustering method improves stability and anti-interference performance of femtocell base station communication.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
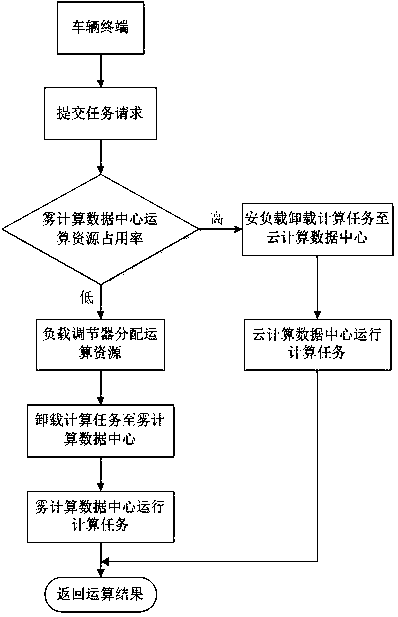
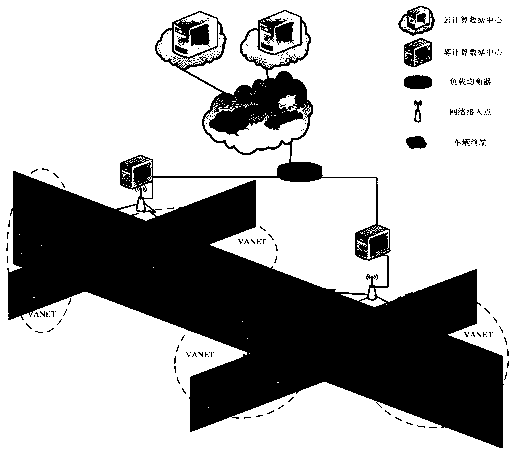
A vehicle big data computing and unloading method based on a fog network
ActiveCN109947574ALess number of task failuresLess number of failed tasksResource allocationParticular environment based servicesReliable computingFog computing
The invention discloses a vehicle big data computing and unloading method based on a fog computing network. According to the invention, a more efficient and reliable computing environment can be provided for analyzing vehicle big data. Firstly, a fog computing network system architecture is provided, a network delay model is further established, then a task generation model is established, a fog computing resource optimization model is established, and finally a load balancing computing resource effective task unloading algorithm is used. Efficient Task Offloading Algorithm with Load Balancing, CRETOA) is used for managing computing resources for load balancing of the fog computing network, and a road vehicle terminal request computing task is allocated to the optimal fog computing resources.
Owner:NANJING UNIV OF POSTS & TELECOMM
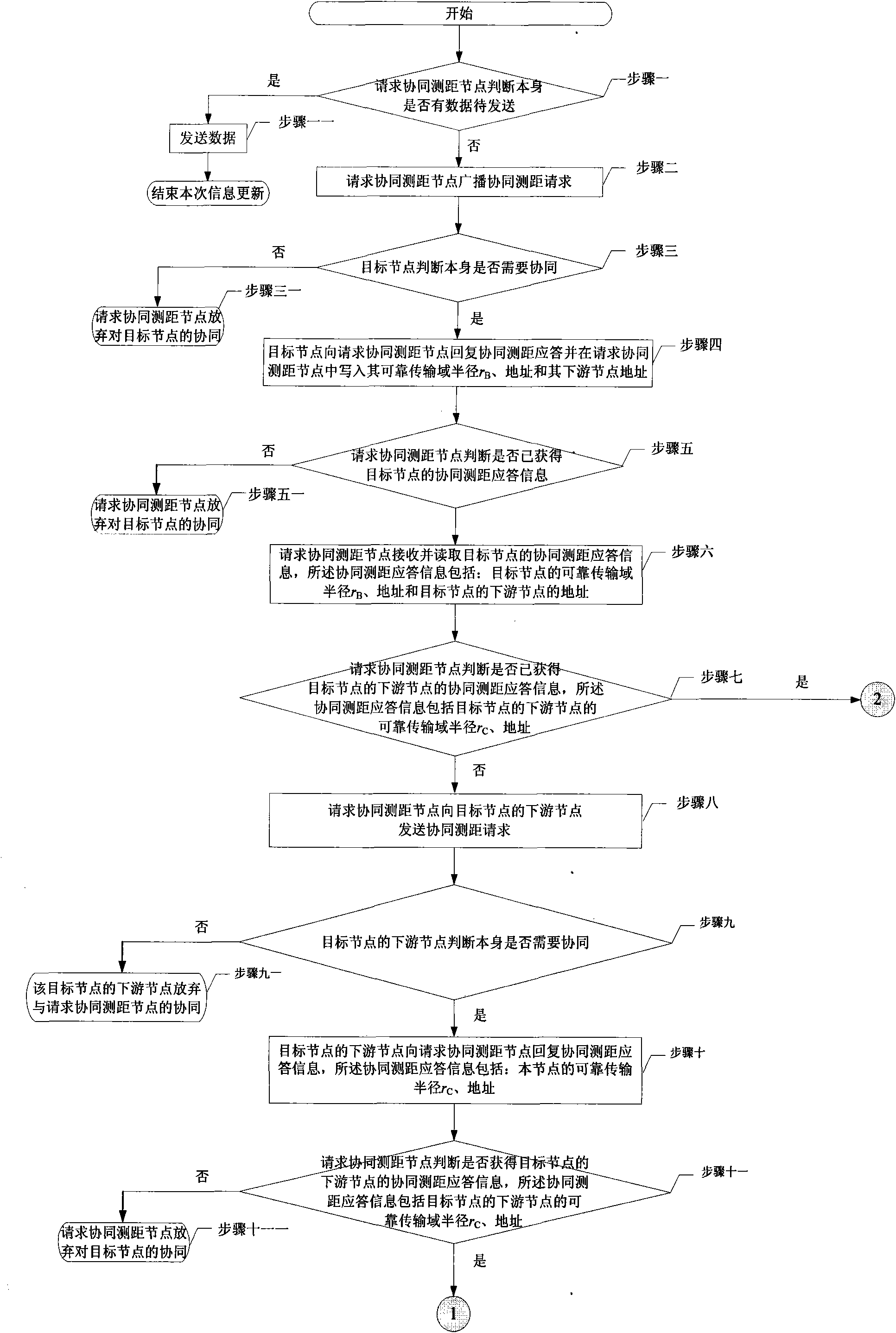
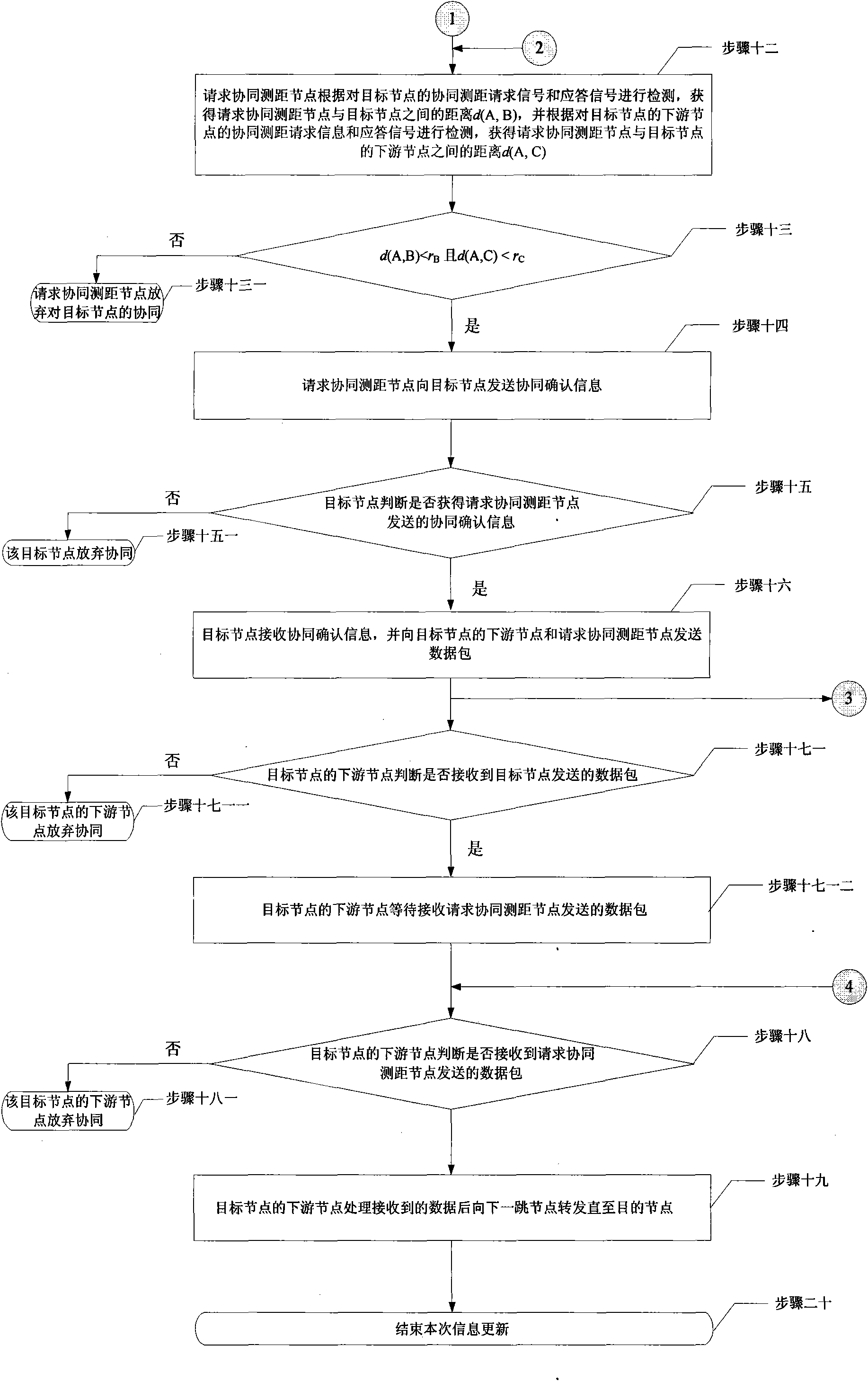
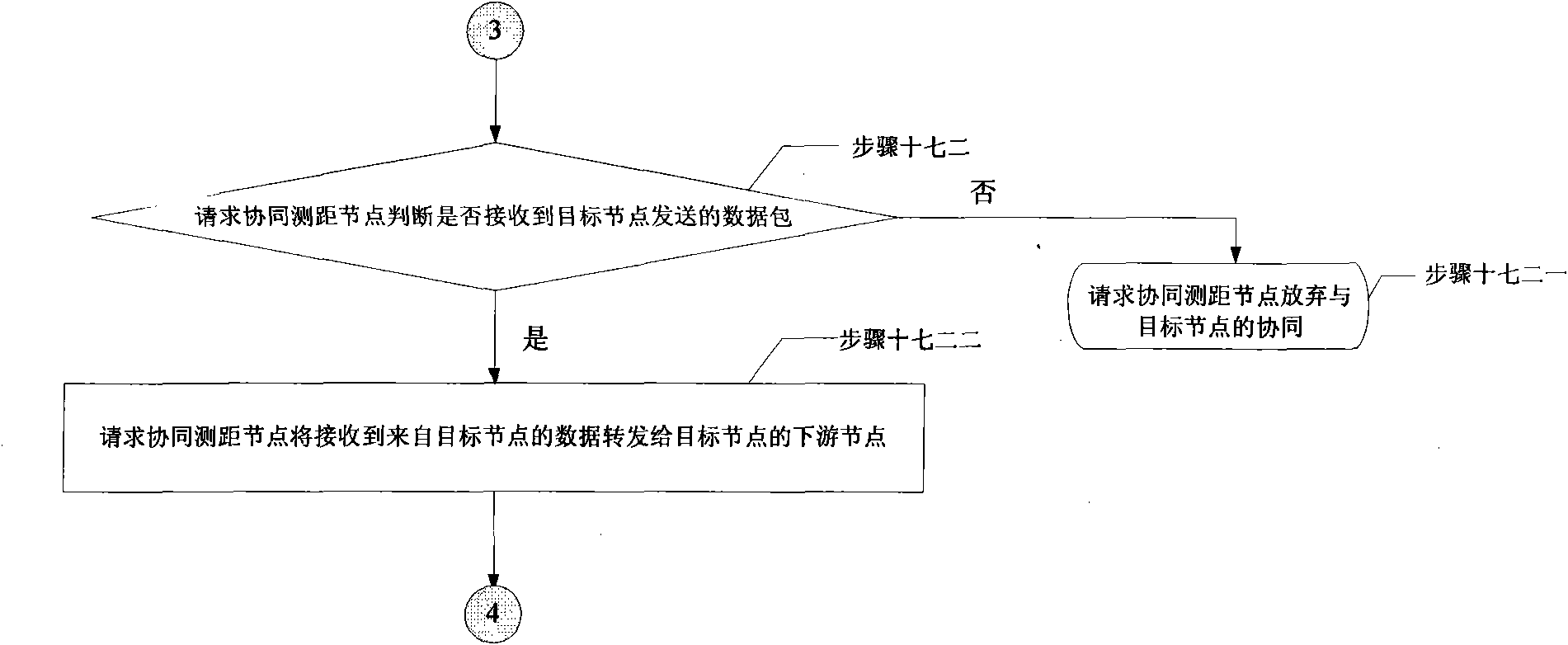
Multipoint cooperative working method for reliable communication in wireless Ad hoc network communication system
InactiveCN101600241AIncrease success rateStrong transmission reliabilityNetwork topologiesHigh level techniquesReliable transmissionReliable computing
A multipoint cooperative working method for reliable communication in a wireless Ad hoc network communication system relates to the wireless Ad hoc network technical field. The invention solves the problem that information transmission reliability is poor as only one route is used for information transmission in the existing wireless communication process. The method includes that: a node requesting cooperative distance measurement broadcasts a cooperative distance measurement request; a destination node writes in the address thereof and the address of a downriver node thereof if needing cooperation; after obtaining successful signal interaction with the destination node and the downriver node of the destination node, the node requesting cooperative distance measurement obtains the distance with the destination node and the distance with the downriver node of the destination node by detecting the cooperative distance measurement request message and acknowledgement signal of the destination node and those of the downriver node of the destination node; and if the two distance values meet the requirement of being less than the corresponding reliable transmission domain radius, the node requesting cooperative distance measurement sends an acknowledge message to the destination node. The invention is applicable to emergency response and communication recovery process after disaster.
Owner:HARBIN INST OF TECH
Wearable computing system
InactiveUS20170108892A1Convenient hot swappingImprove balanceGarmentsVolume/mass flow measurementMixed realityGraphic card
A wearable computer system which may be used in various applications including virtual reality, augmented reality and mixed reality applications. The system may be worn by a user while using such systems and applications. Power may be supplied by a battery which powers a computer, a graphics card, a head mounted display and other peripherals. The system may include a counterbalanced configuration of the power supply and computing components through strategic placement to achieve optimal weight balance between a front portion and a rear portion of the wearable computing system, and may include a frame that allows for protection and proper ventilation for standing, seated or lying (front or back) user positions. The system may also include one or more tracking markers and / or tracking devices built or placed on the system for tracking the spatial position and orientation of the user using optical, RF, or ultrasonic tracking technologies, for example.
Owner:ATOMIC VR INC
Modeling method of plate spring virtual model for force touch reappearance
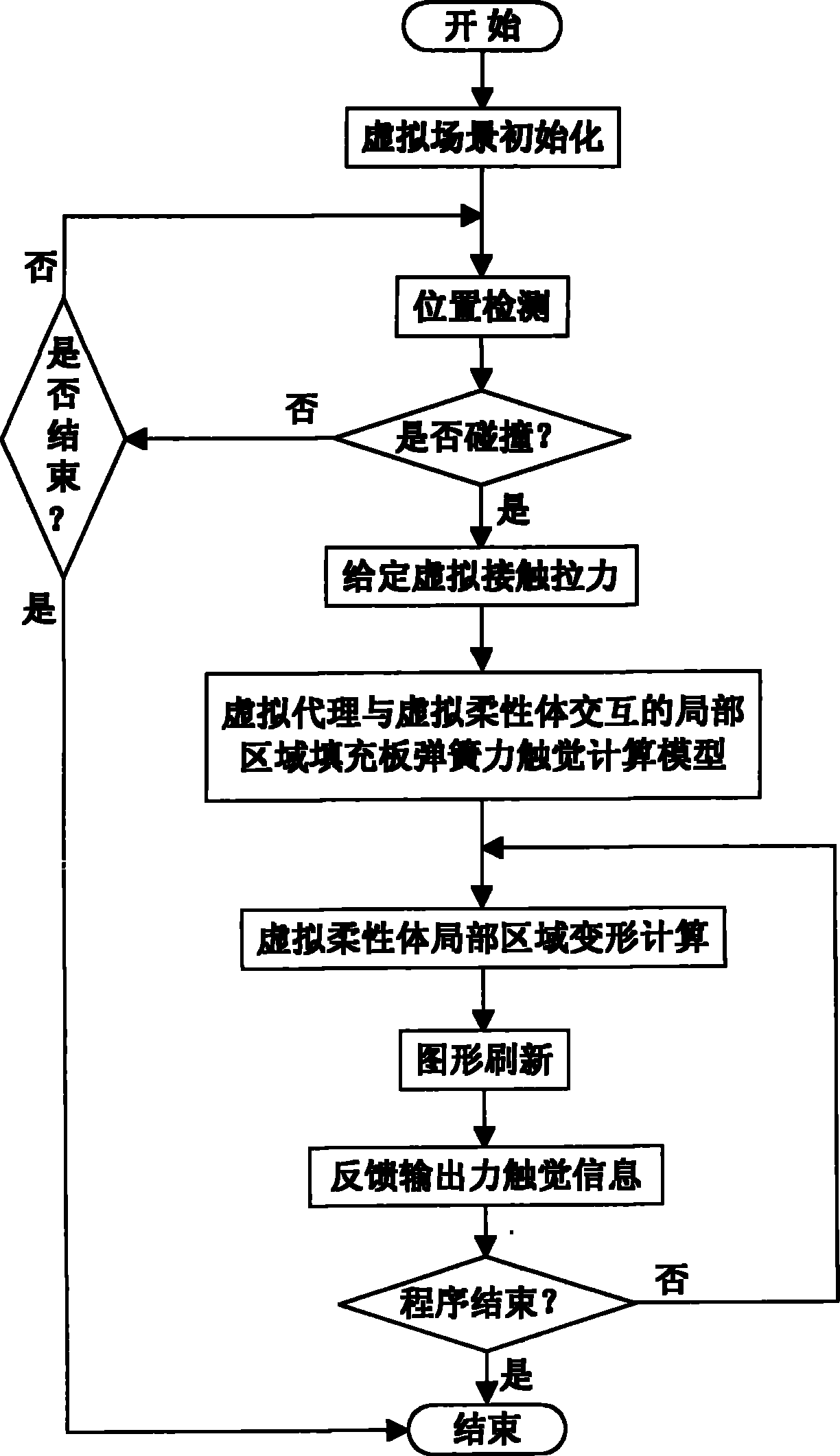
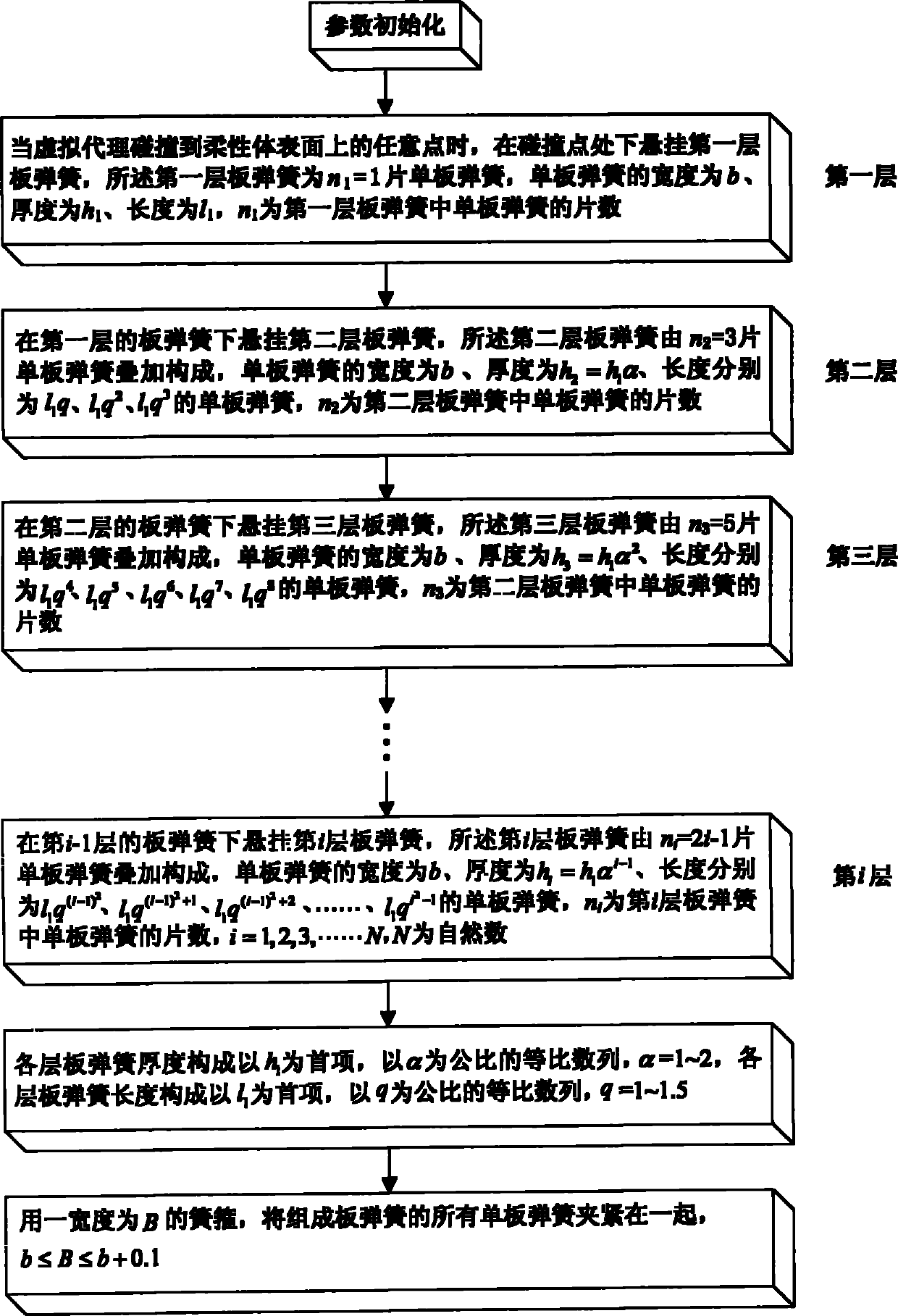
InactiveCN101996280AReduce the amount of deformation calculationFast operationSpecial data processing applicationsTouch sensationTouch Senses
The invention discloses a modeling method of a plate spring virtual model for force touch reappearance, which is characterized in that when the collision of a virtual agent to any one point on the surface of a virtual flexible body is detected, a plate spring virtual model is filled inside an interactive local region of the virtual agent and the virtual flexible body under the given virtual contact tension action, signals of force touch sensation information with the feedback reflected on real-time deformation simulation of the virtual flexible body under the pulling force effect and calculated by adopting the plate spring virtual model are output, the overlapping of the sum of all single plate spring deformation quantity in the plate spring virtual model for the force touch sensation reappearance is externally equivalent to the deformation on the surface of the virtual flexible body, and the sum of consumed tensions of all the single plate springs in the stretching process is equivalent to the given virtual contact tension. The modeling method has the advantages of accuracy, reliability, simple and convenient calculation, good practicability and good universality, can really feed back the force touch sensation information to operators, and realistically realizes the deformation simulation on the virtual flexible body at the real time.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
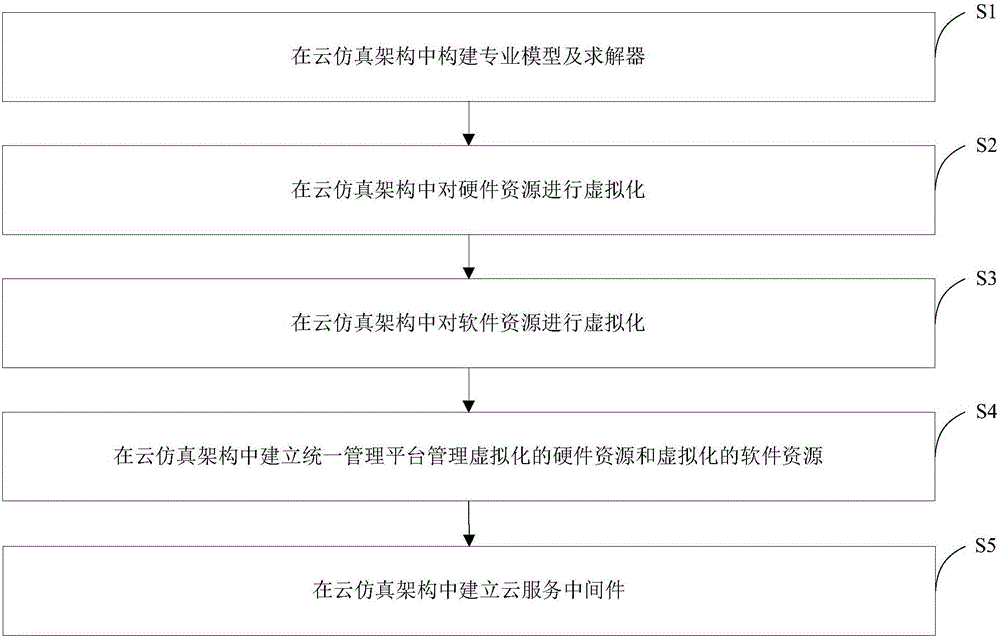
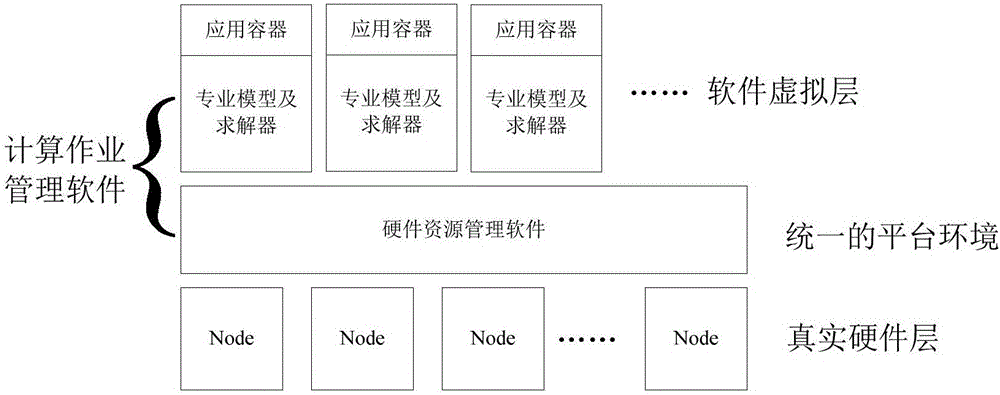
Cloud simulation service method
The invention discloses a cloud simulation service method comprising the steps of: virtualizing hardware resources in a cloud simulation architecture; virtualizing software resources in the cloud simulation architecture; establishing a unified management platform in the cloud simulation architecture to manage the virtualized hardware resources and the virtualized software resources; and constructing a the professional model and a solver in the cloud simulation architecture. The method has the following advantages of using model sharing service, resource flexible scheduling and solver parallel computing as a core, scheduling tasks and distributing computing resources on demand, providing the professional model and the solver for engineering staff in the form of services by using service middleware, configuring on demand, providing a flexible and reliable computing platform for enterprises; and achieving high data security and high data reliability.
Owner:BEIJING POWER MACHINERY INST
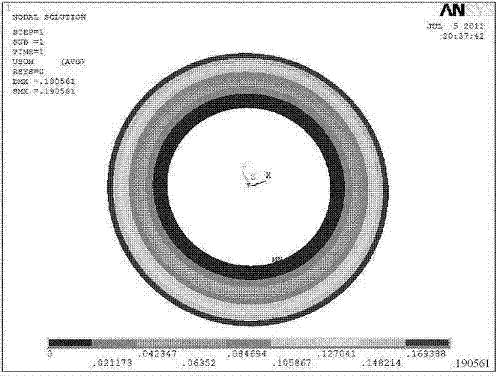
Computing method for circumferential stress of absorber annular valve sheet
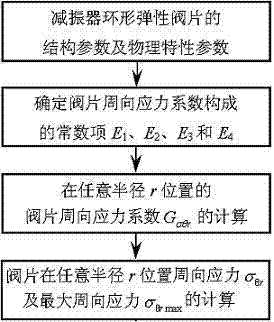
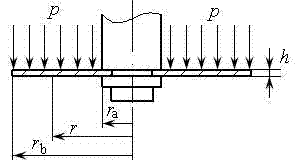
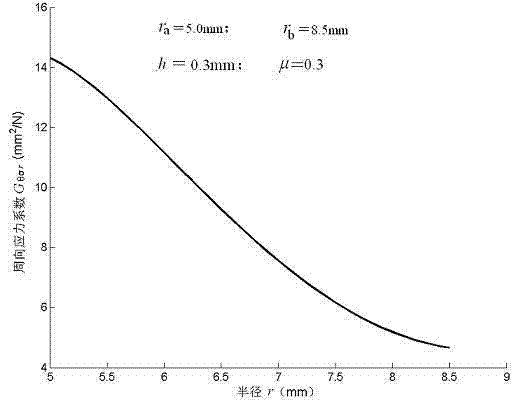
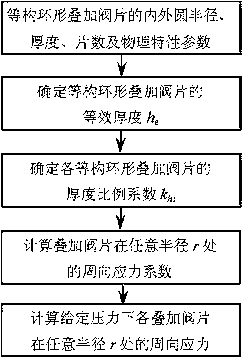
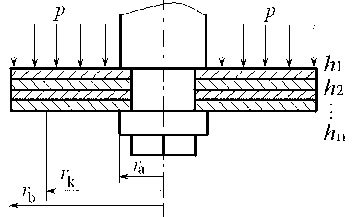
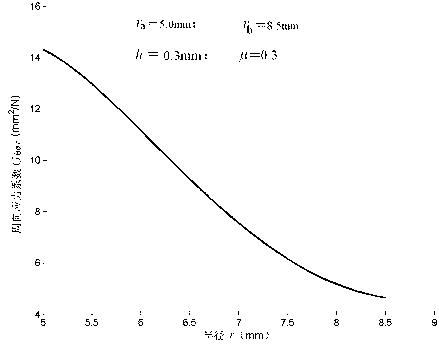
InactiveCN103116709ACan not meet the requirements of modern CAD designSpecial data processing applicationsReliable computingEngineering
The invention relates to a computing method for circumferential stress of an absorber annular valve sheet, and belongs to the technical field of absorbers. No reliable computing method is put forward for circumferential stress of the absorber annular valve sheet in the prior art. The computing method for circumferential stress of the absorber annular valve sheet is characterized in that the following steps are adopted: 1) each constant term composed of the circumferential stress coefficient of a valve sheet is confirmed; 2) the circumferential stress coefficient G sigma theta r at any position of radius r is computed; 3) the circumferential stress sigma theta r at any position of the radius r of the absorber annular valve sheet is computed. By means of the computing method for circumferential stress of the absorber annular valve sheet, the circumferential stress sigma theta r at any position of the radius and the maximum circumferential stress sigma theta r max at the position of the inner circle radius ra can be accurately computed. The result of the ANSYS emulation proof proves that the computing method for circumferential stress of the absorber annular valve sheet is accurate, so that the reliable circumferential stress computing method is provided for splitting design and stress intensity check of the absorber annular valve sheet.
Owner:SHANDONG UNIV OF TECH
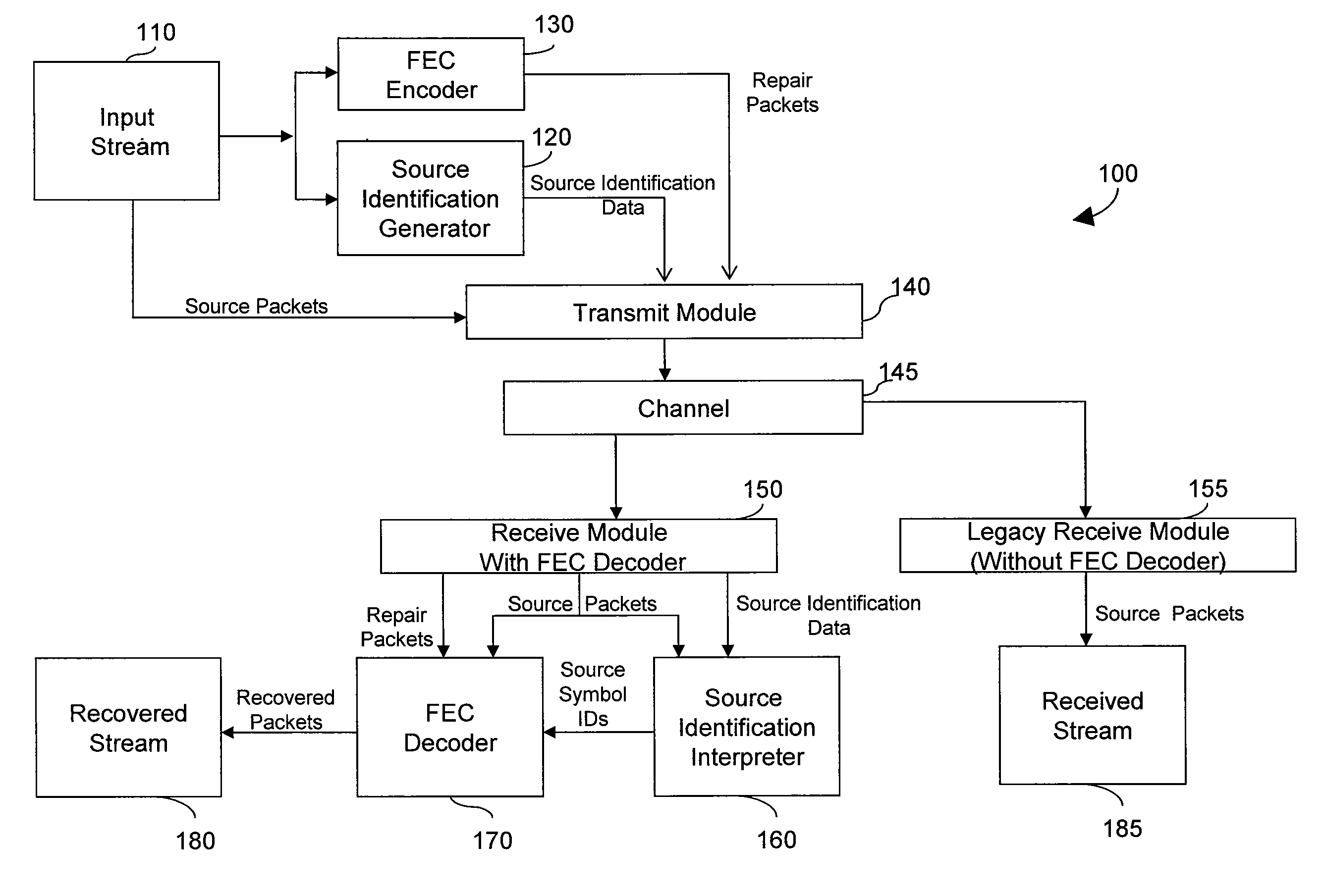
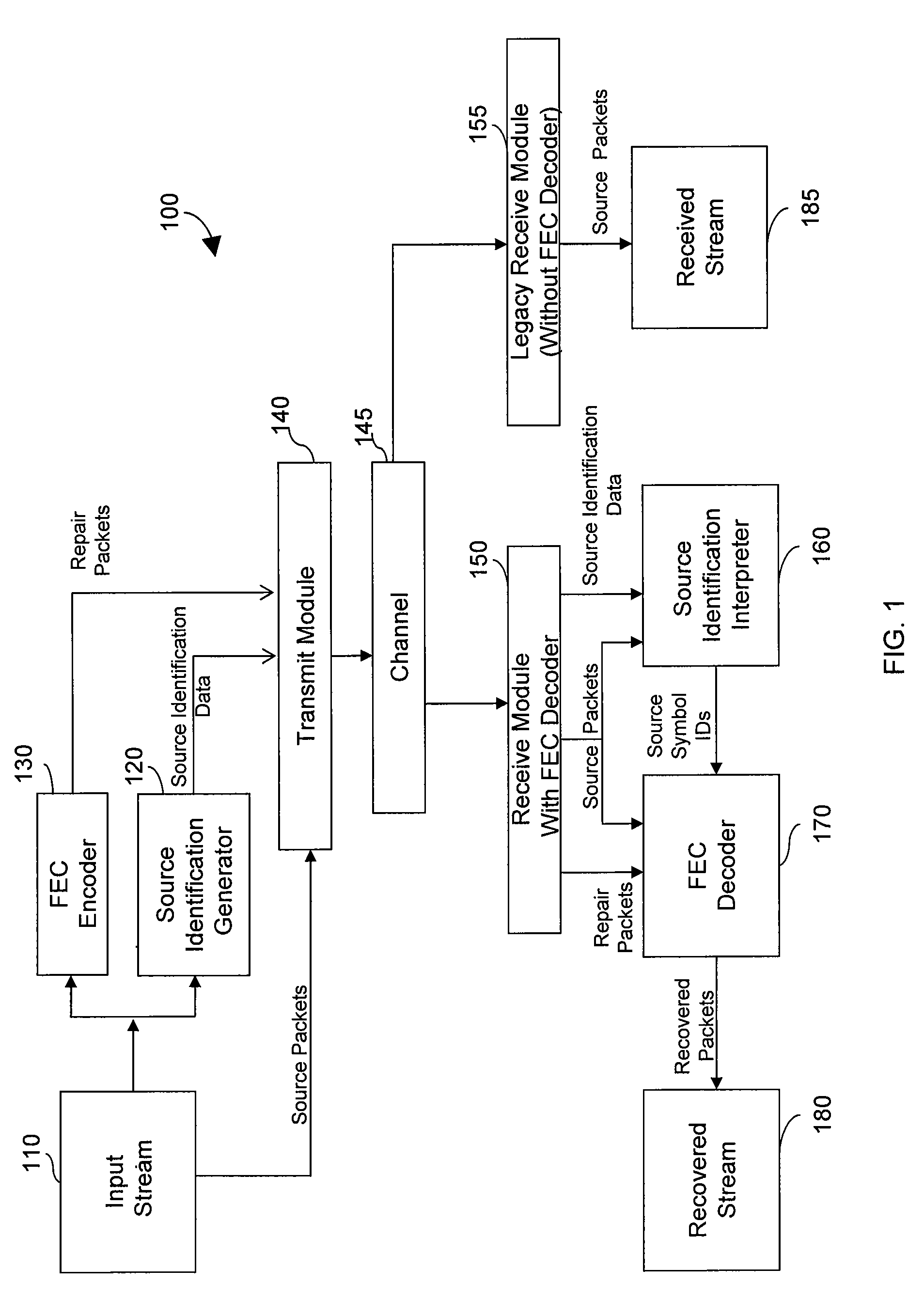
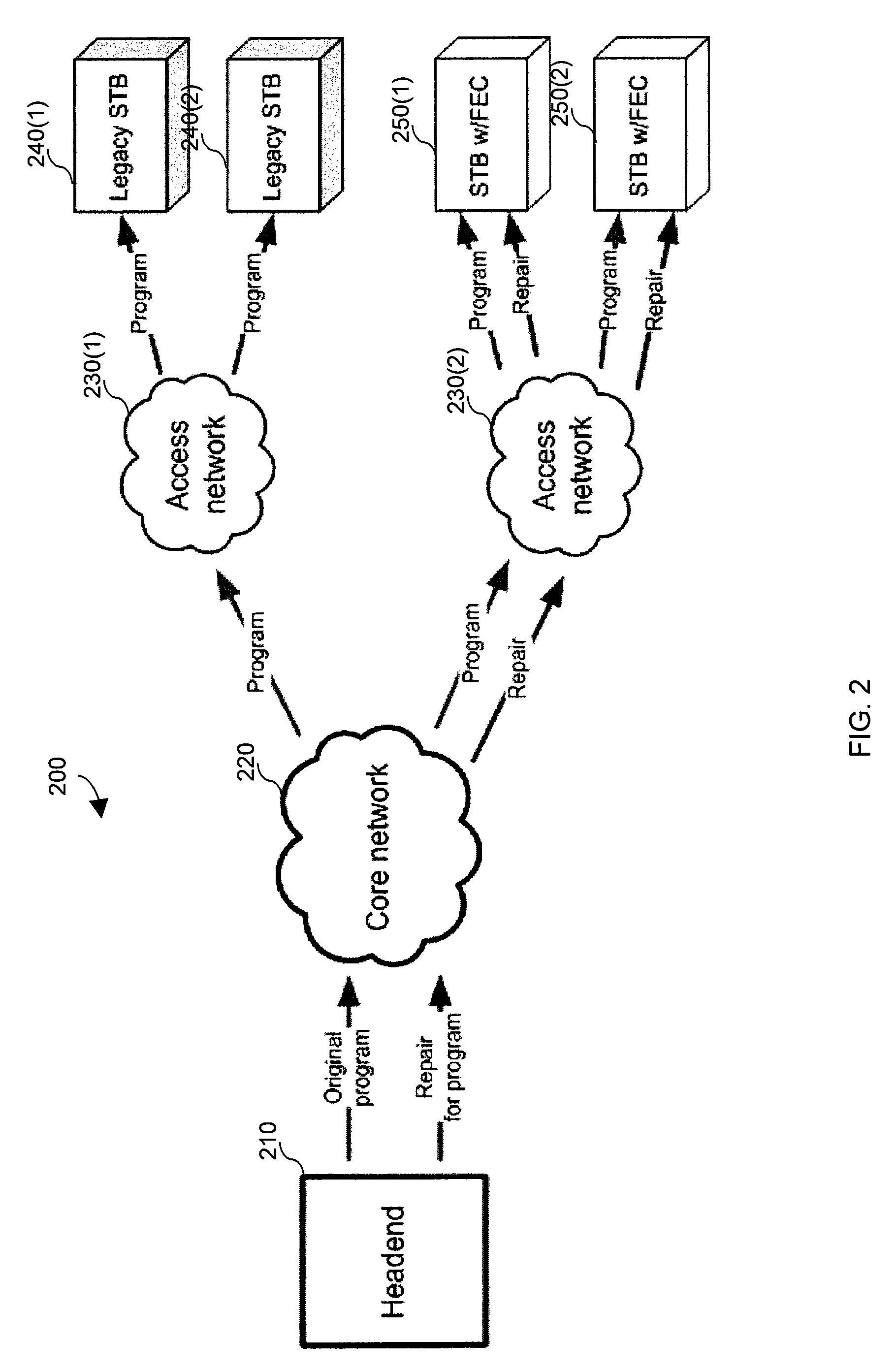
Generating and communicating source identification information to enable reliable communications
InactiveUS9237101B2Small amount of calculationCompact representationError prevention/detection by using return channelError detection/correctionComputer networkReliable computing
A method of generating Source Identification information from a source packet stream and reliably transmitting the Source Identification information from a source to a destination over a communications channel is provided. The method operates on a set of source packets, wherein Source Identification information for each source packet to be transmitted is derived and delivered with the Source Identification information of all or most other source packets of an associated source block. The method includes techniques to minimize the network bandwidth required to deliver Source Identification information and techniques to overcome network impairments. When combined with FEC techniques, retransmission techniques, or combinations of FEC techniques and retransmission techniques, the methods described herein allow receivers to recover lost source packets, while simultaneously ensuring that the original source packets are not modified and thereby ensuring backwards compatibility for legacy receivers.
Owner:QUALCOMM INC
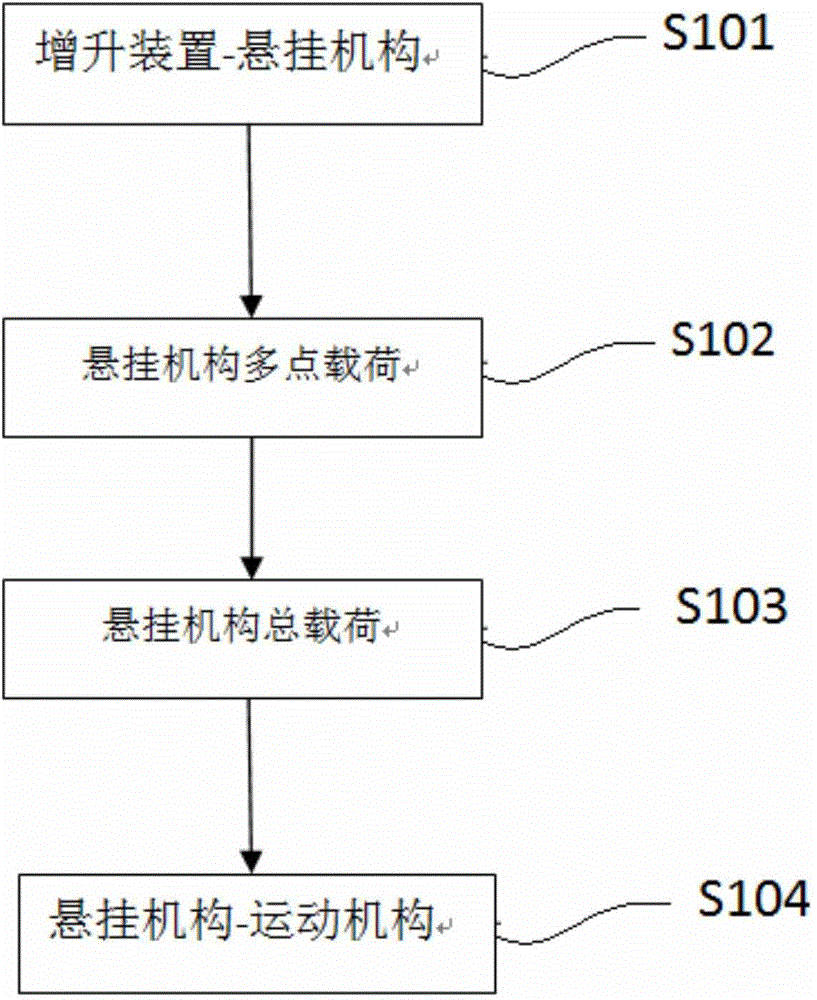
Method for load calculation of high lift system of aircraft
ActiveCN104933259ASolve force calculation problemsAvoid complexitySpecial data processing applicationsAviationSystems design
The invention relates to the field of design of aviation systems, in particular to a method for load calculation of a high lift system of an aircraft, to solve the problem of incapability of meeting the design requirements due to the low efficiency of the existing computing method. A high lift device in the high lift system is connected to a plurality of connecting points of a suspension mechanism; the suspension mechanism is in point contact with a plurality of movement mechanisms in the high lift system; according to the stress and constraint condition of each link on a force transfer path, the force transfer path can be decomposed into two sub-systems, namely high lift device-suspension mechanism and suspension mechanism-movement mechanisms, which are organically related, and then the force transfer computing problem of a complex system is solved step by step based on the design philosophy and the mechanical characteristics of each sub-system. The method has the advantages of quick computing speed and accurate and reliable computing result, and is capable of completely avoiding a complicated and tedious process needed by finite element software.
Owner:XIAN AIRCRAFT DESIGN INST OF AVIATION IND OF CHINA
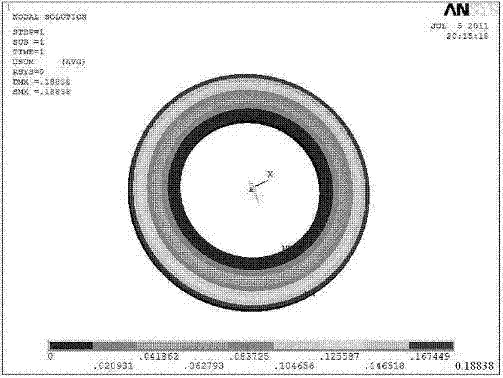
Computing method for circumferential stress of equivalent structure circular sandwich valve plate of absorber
The invention relates to a computing method for circumferential stress of an equivalent structure circular sandwich valve plate of an absorber, and belongs to the absorber technical field. A reliable computing method for the circumferential stress of the equivalent structure circular sandwich valve plate of the absorber does not exist previously, and therefore the requirements of absorber modernized computer aided design (CAD) design and stress intensity calculation can not be met. The computing method for circumferential stress of the equivalent structure circular sandwich valve plate of the absorber comprises the following steps: (1), ensuring equivalent thickness of the equivalent structure circular sandwich valve plate; (2), ensuring thickness proportionality coefficient of the equivalent structure circular sandwich valve plate; (3), calculating circumferential stress coefficient of the equivalent structure circular sandwich valve plate on any radius r; and (4), calculating circumferential stress and maximum circumferential stress of the equivalent structure circular sandwich valve plate on any radius r. The computing method for circumferential stress of the equivalent structure circular sandwich valve plate of the absorber can accurately calculate the circumferential stress and the maximum circumferential stress of the equivalent structure circular sandwich valve plate on any radius position, and provides a reliable computing method for circumferential stress for absorber equivalent structure sandwich valve plate designs and stress intensity calculation.
Owner:SHANDONG UNIV OF TECH
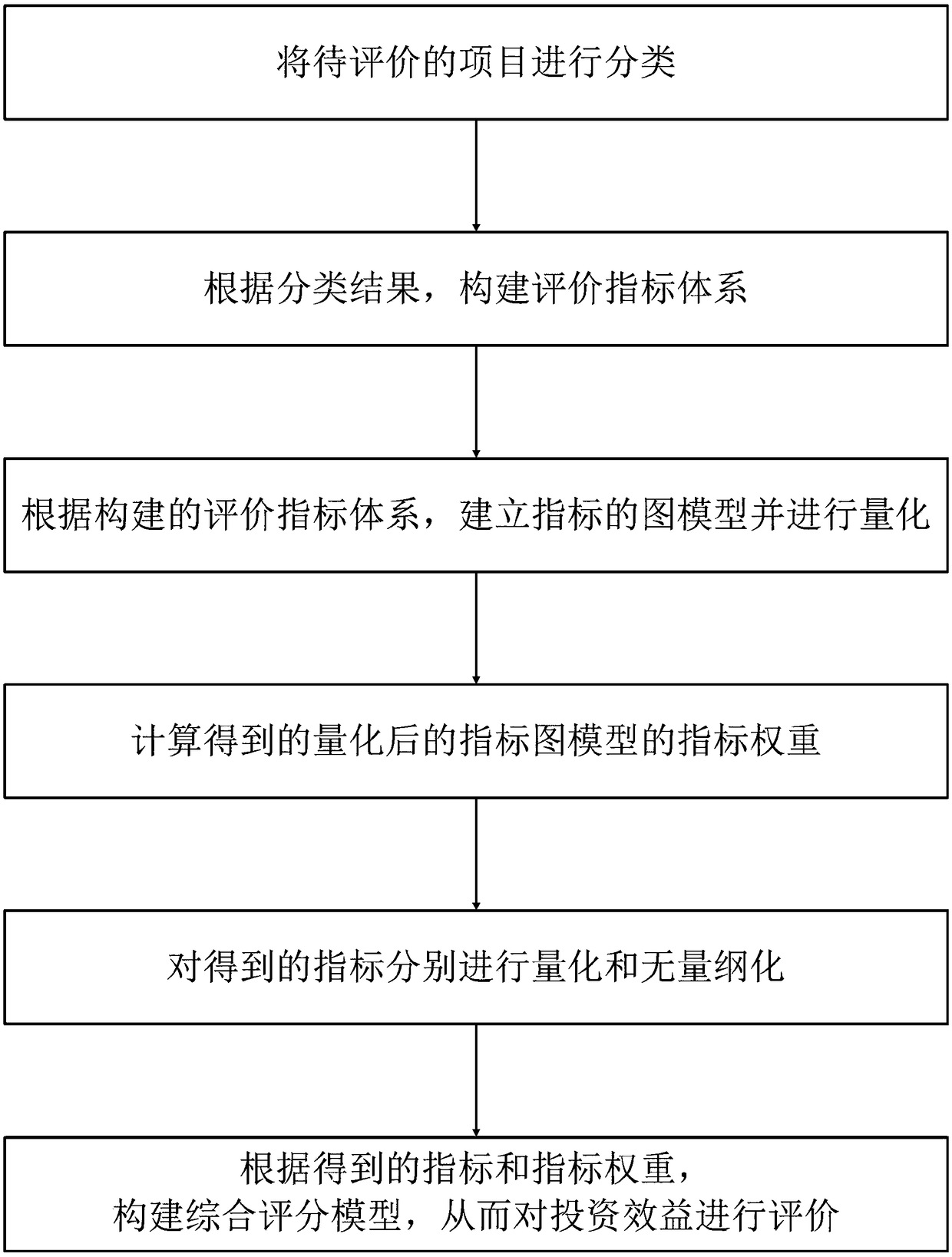
Evaluation method of investment benefit of power grid project
InactiveCN109003010AThe method is scientific and reliableSimple calculationResourcesInformation technology support systemComputation processPower grid
The invention discloses an evaluation method of investment benefit of a power grid project, which comprises the following steps of: classifying the items to be evaluated; constructing an evaluation index system; establishing the graph model of the index and quantifying it; calculating index weights of the quantized index graph model; performing quantification and dimensionlessness of the indexes;constructing a comprehensive scoring model to evaluate the investment benefit. The invention provides a method for evaluating the investment benefit of a power grid project, the evaluation index system considering the functional characteristics of the project is constructed, a graph model index weighting method is proposed and the differential evaluation results of power network projects based onfunction classificaiton can be obtained through a scoring module; the method of the invention can scientifically and reasonably evaluate the benefit of the investment of the power network project, andcan reflect the investment benefit of the different functional projects more accurately and quickly, and the method of the invention is scientific and reliable, and the calculation process is simpleand clear.
Owner:STATE GRID HUNAN ELECTRIC POWER +3
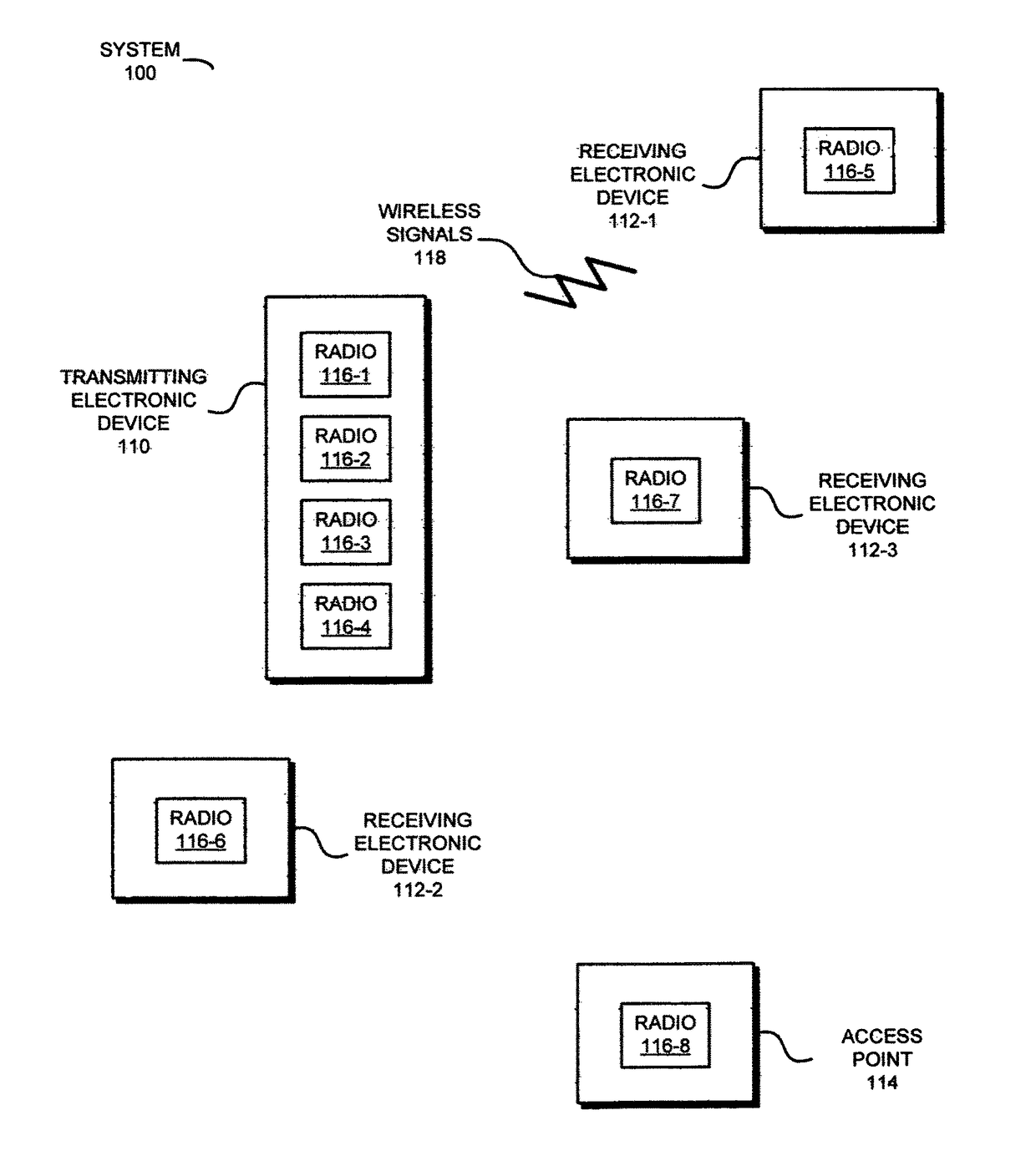
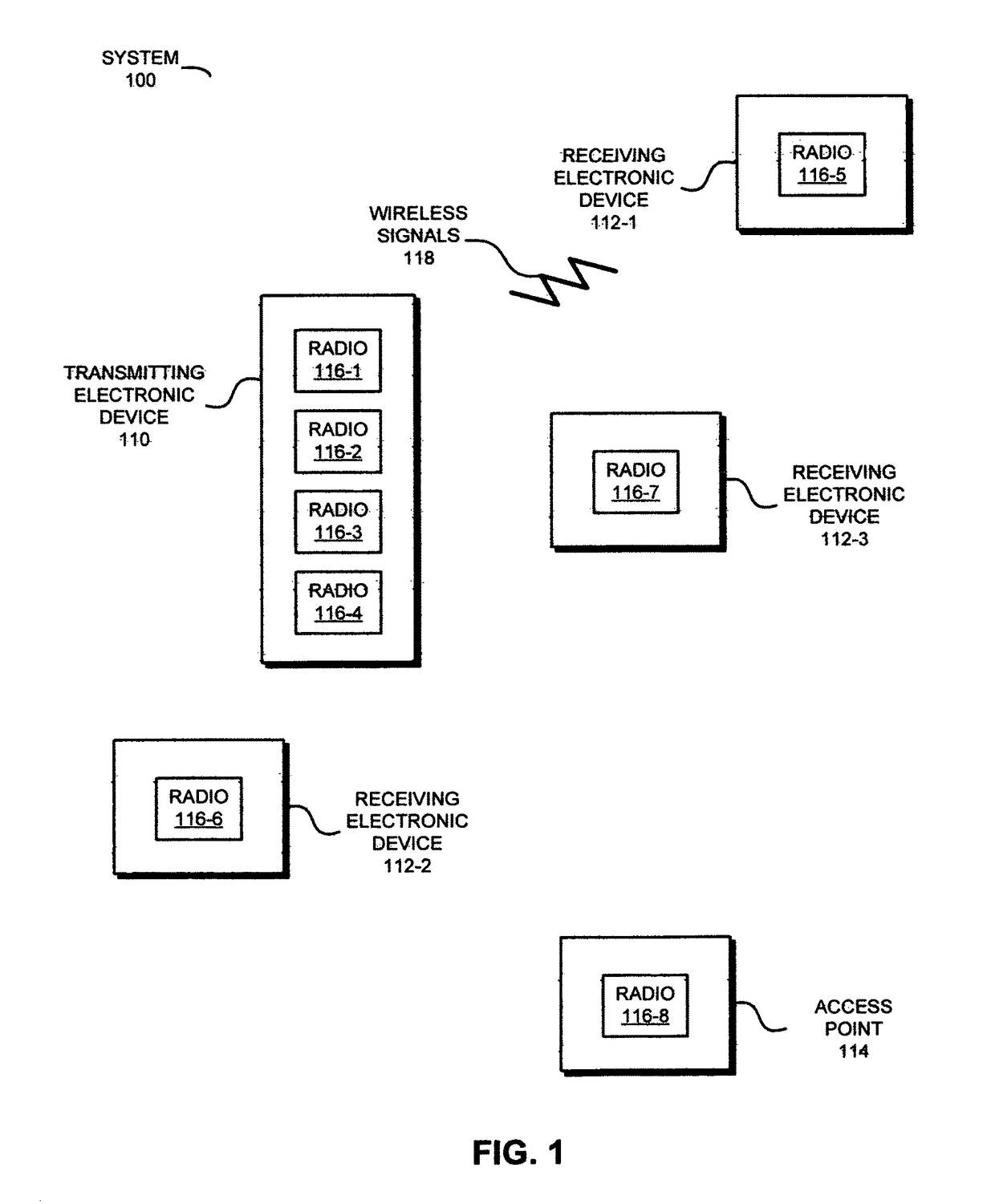
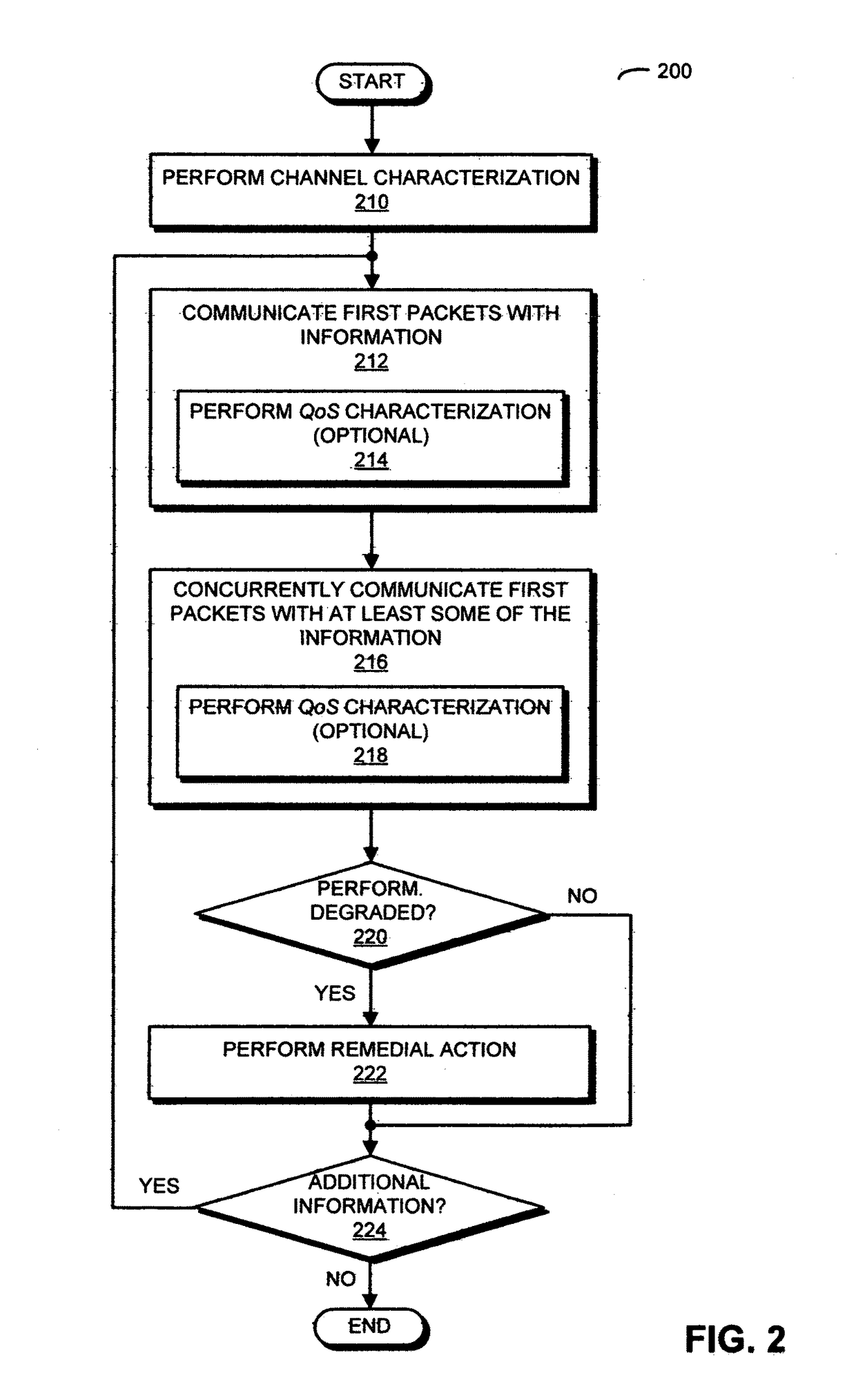
Redundant links for reliable communication
In order to maintain performance during wireless communication, a transmitting electronic device may concurrently and independently communicate redundant information to a receiving electronic device. In particular, information associated with a data stream may be communicated to the receiving electronic device using one or more channels by two radios using one or more wireless local area network communication protocols. The packets transmitted by the radios may preferentially include the same information. Moreover, the transmitting electronic device may attempt to maintain the redundant communication if a performance metric associated with the one or more channels degrades. For example, the transmitting electronic device may transfer communication to a different channel or may compress the information in the packets in the one or more channels if the throughput drops below a threshold value. Furthermore, the concurrent communication may allow the transmitting electronic device determine link quality without disrupting the communication of the information.
Owner:B & W GRP LTD
Reliable multi-path aggregation routing algorithm based on energy balance
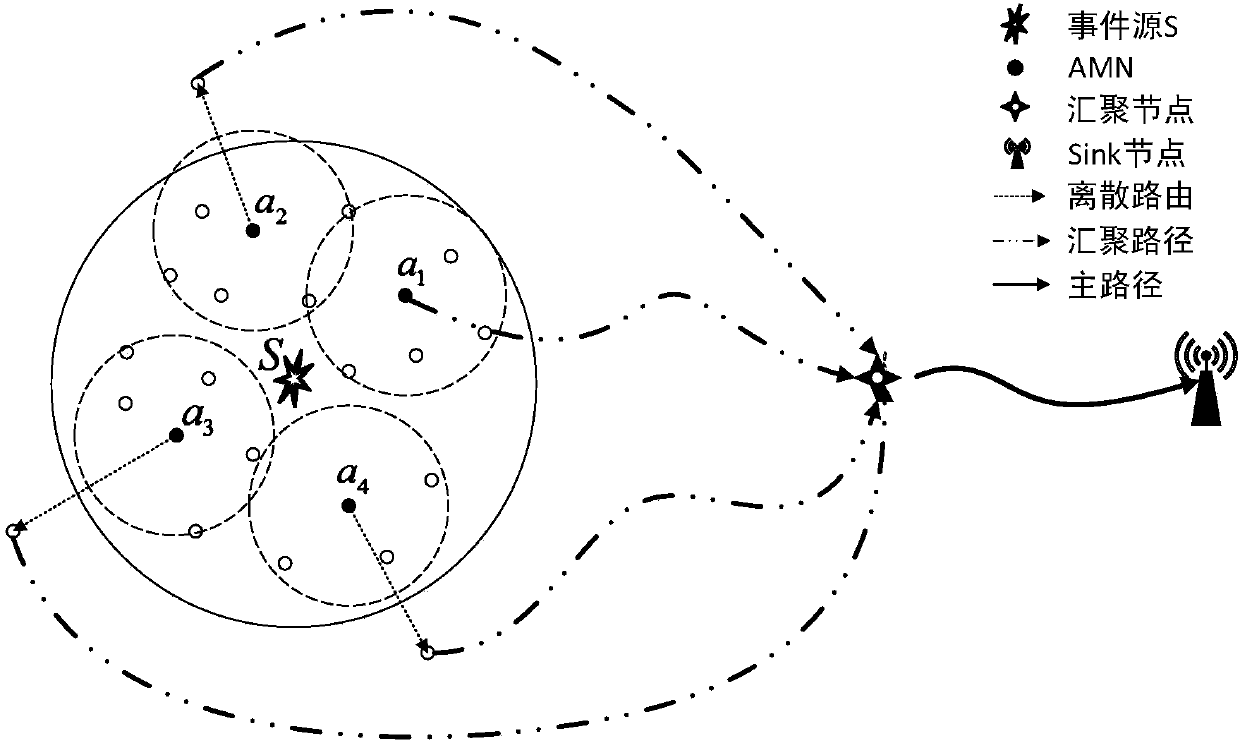
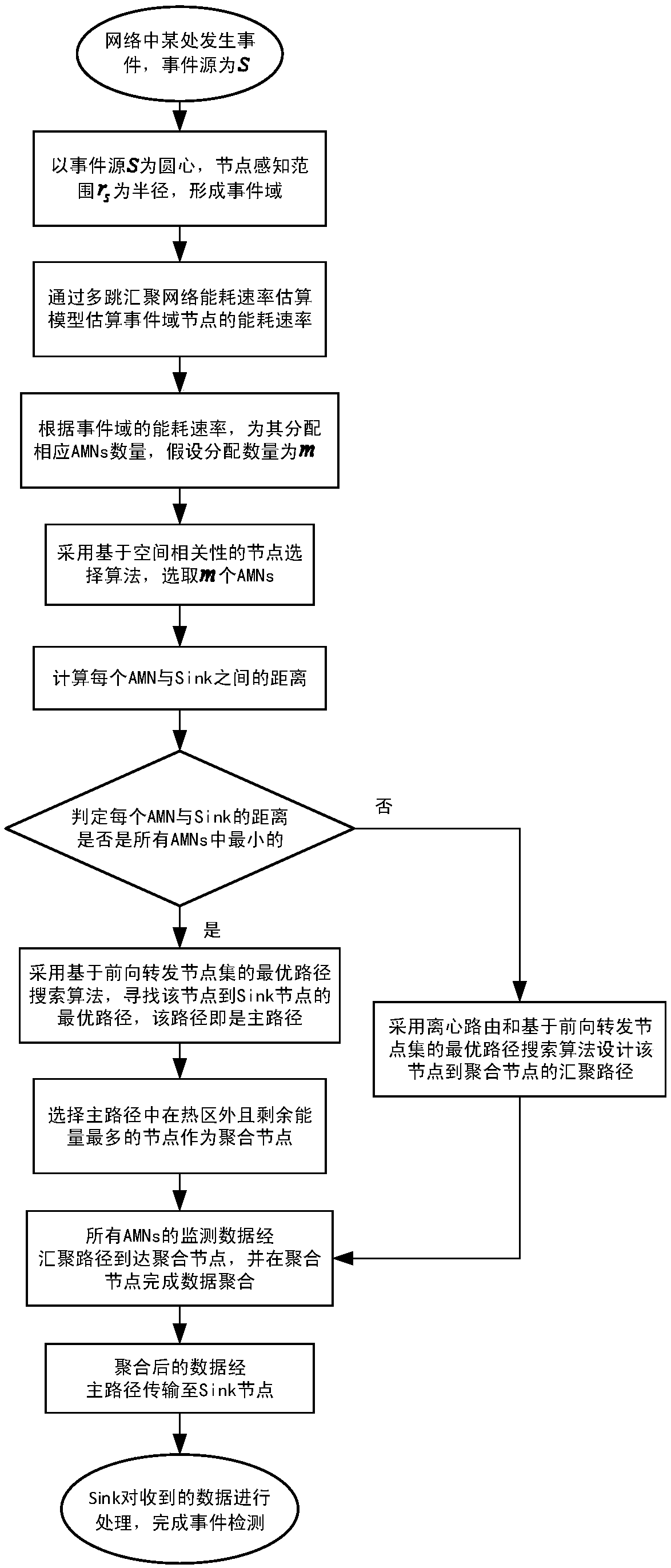
ActiveCN108366409AImprove detection reliabilityImprove energy efficiencyData switching networksHigh level techniquesEnergy balancingReliable computing
The invention relates to a reliable multi-path aggregation routing algorithm based on energy balance, and belongs to the technical field of a wireless sensor network. The algorithm comprises the following steps: analyzing a network data transmission feature, and establishing a multi-hop convergence network rate estimation model by combining the density and location information of the node; selecting more AMN and less AMNs at event regions with low energy consumption rate and high energy consumption rate by using a node selection algorithm based on the space relevancy; designing an optimal pathsearch algorithm based on a forwarding node set, and designing the multi-path convergence routing in energy balance by adopting the algorithm, wherein the multi-path convergence routing comprises anoptimal main path for data collection and an optimal convergence path for each AMN node, and all convergence paths are converged on an aggregation node on the main path; monitoring the data to arrivethe aggregation node through the convergence path, and enabling the data to arrive a Sink node through the main path after the aggregation node accomplishes the data aggregation. Through the algorithmdisclosed by the invention, the network energy consumption can be effectively balanced, the network life is prolonged, and the event detection reliability is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
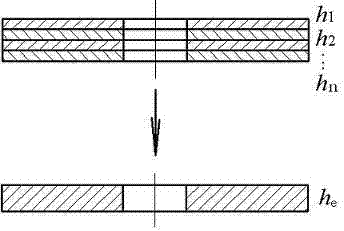
Computing method for equivalent thickness of hydraulic buffer isomorphic annular sandwich valve plates
InactiveCN103324824AThe calculation method is accurateSpecial data processing applicationsReliable computingEngineering
The invention relates to a computing method for equivalent thickness of hydraulic buffer isomorphic annular sandwich valve plates, and belongs to the technical field of buffers. In the prior art, the reliable computing method for the equivalent thickness of the hydraulic buffer isomorphic annular sandwich valve plates is not available, and thus the actual requirements for design, production and characteristic simulation modeling of the buffer can be not met. With adoption of the method, according to thickness and plate number of the annular sandwich valve plates with same material, equal inner diameter and equal outer diameter, the equivalent thickness h<e> of the sandwich valve plates, equivalent to that of a signal valve plate, can be computed accurately and quickly; through comparison with the ANSYS simulation result, the fact can be confirmed that the computing method for the equivalent thickness of the hydraulic buffer isomorphic annular sandwich valve plates is accurate and reliable, and further, the reliable computing method for the equivalent thickness of the isomorphic annular sandwich valve plates is provided for detachment design and stress intensity check of the buffer sandwich valve plates as well as characteristic simulation modeling of the buffer.
Owner:SHANDONG UNIV OF TECH
Method for extracting rolling bearing fault feature based on EEMD and K-GDE
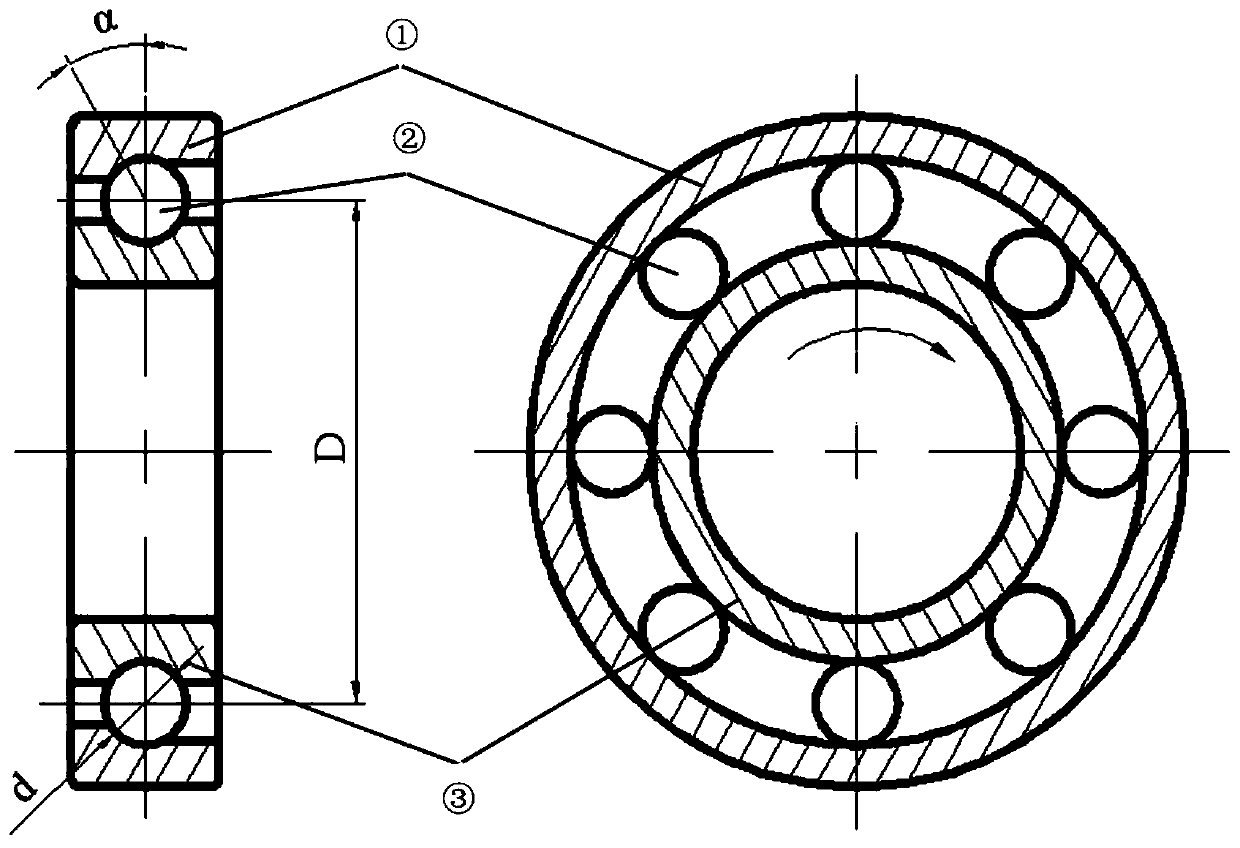
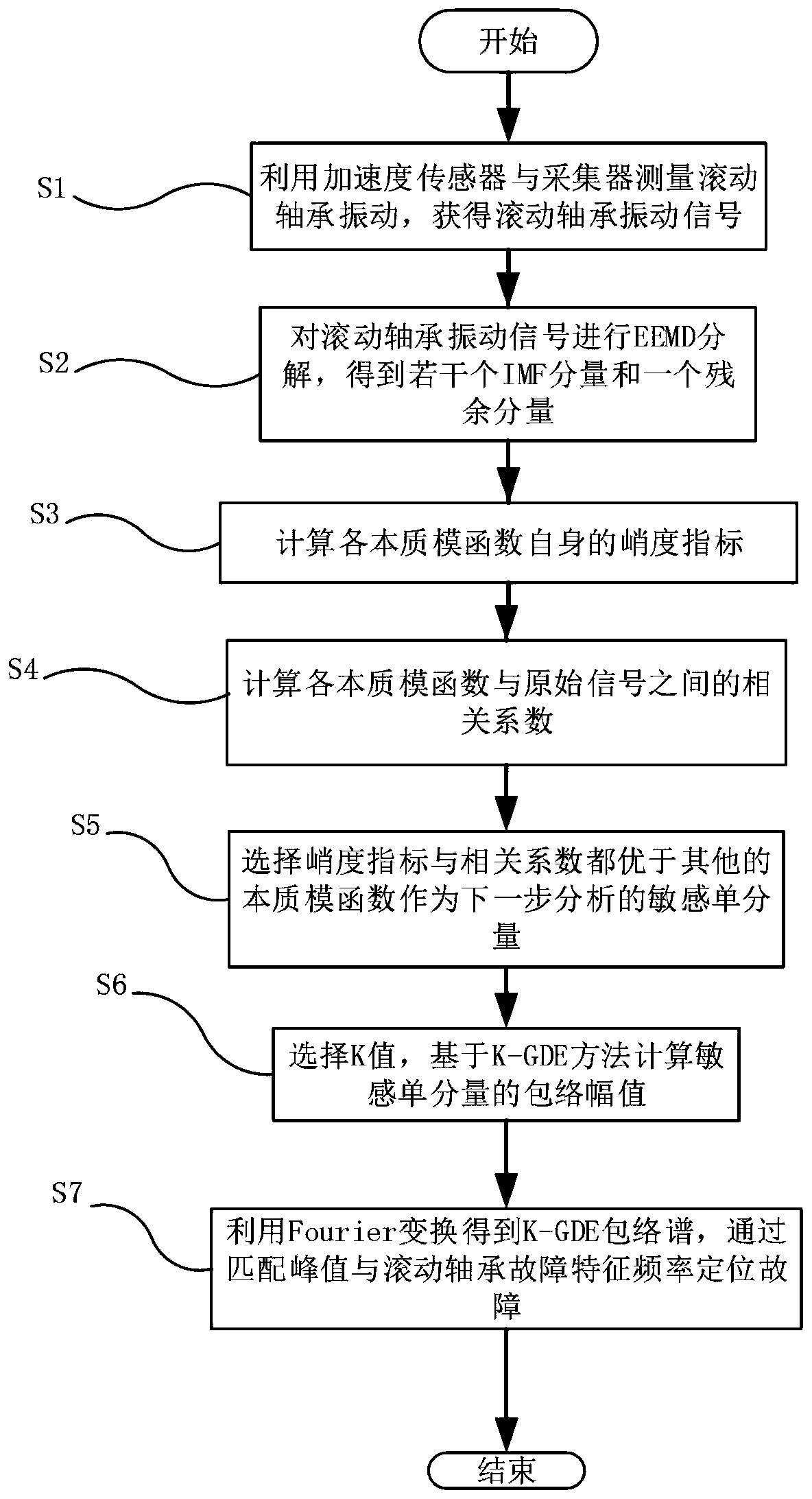
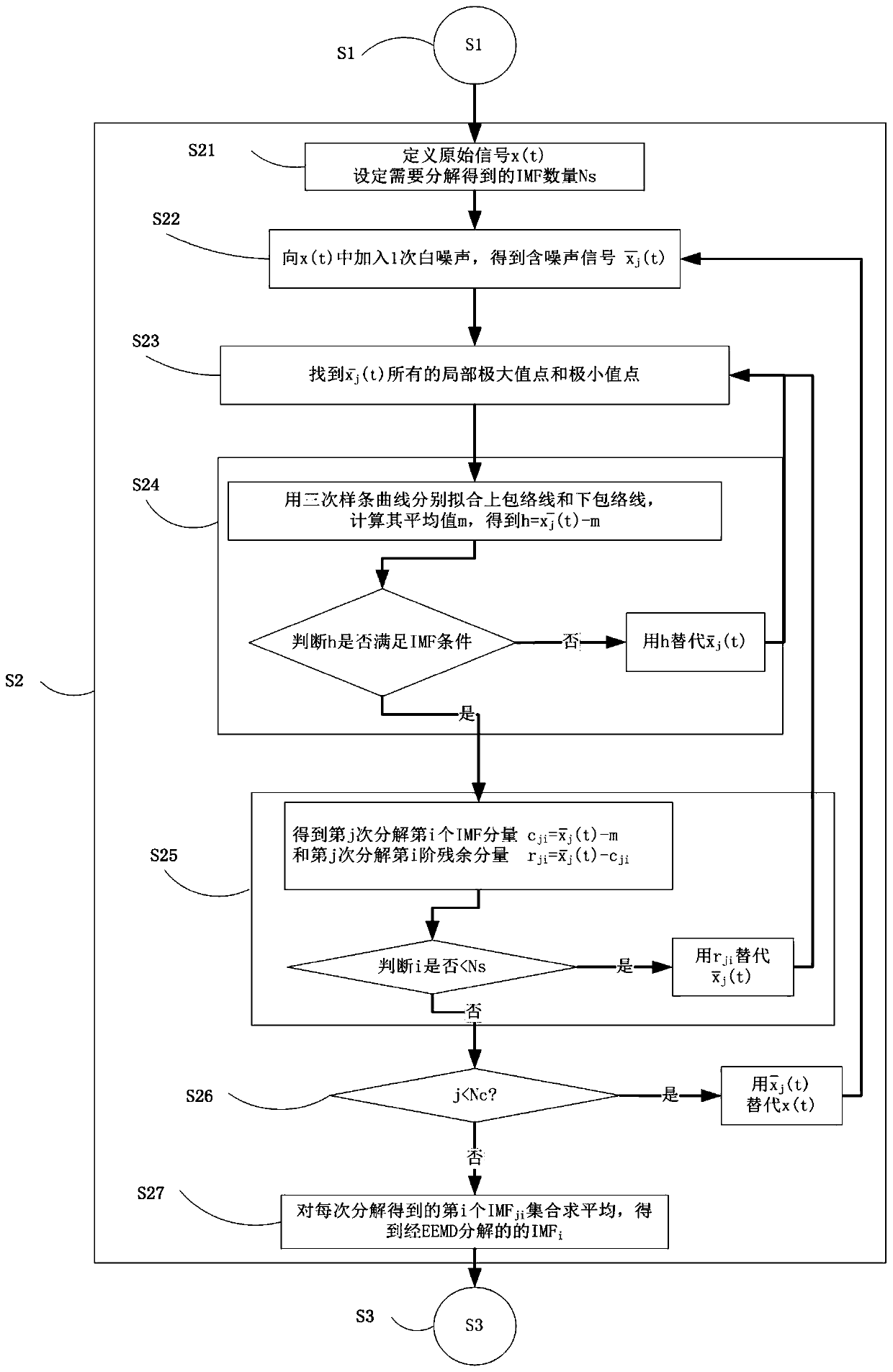
InactiveCN109883704ACalculation is simple and efficientMachine part testingCharacter and pattern recognitionCorrelation coefficientGDES
The invention discloses a method for extracting a rolling bearing fault feature based on EEMD and K-GDE. The method comprises the following steps: S1, measuring vibration of a rolling bear by using anacceleration sensor and a collector; S2, performing EEMD decomposition on a rolling bearing vibration signal; S3, calculating kurtosis indexes of essential modular functions; S4, calculating correlation coefficients between the essential modular functions and an original signal; S5, selecting an essential modular function with the largest kurtosis index and the largest correlation coefficient from all the essential modular functions to serve as a sensitive single component of next analysis; S6, selecting a value k from a value range, and calculating the envelop amplitude of the sensitive single component based on a k-GDE method; and S7, performing Fourier transform on the envelop amplitude to obtain a k-GDE envelop spectrum, and realizing fault diagnosis by matching a peak frequency and arolling bearing fault feature frequency. The method for extracting the rolling bearing fault feature based on the EEMD and the K-GDE has the effects of accurate and reliable algorithm, as well as simple, convenient and efficient calculation on the aspect of calculation of amplitude envelop.
Owner:LUDONG UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com