Terminal credible security system and method based on credible computing
A credible and terminal technology, applied in computing, computer security devices, digital data protection, etc., can solve problems such as unguaranteed, unguaranteed implementation of user behavior expectations, failure to form a credible system, etc., to eliminate operation and Effects of dissemination, ensuring confidentiality and integrity, and ensuring system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
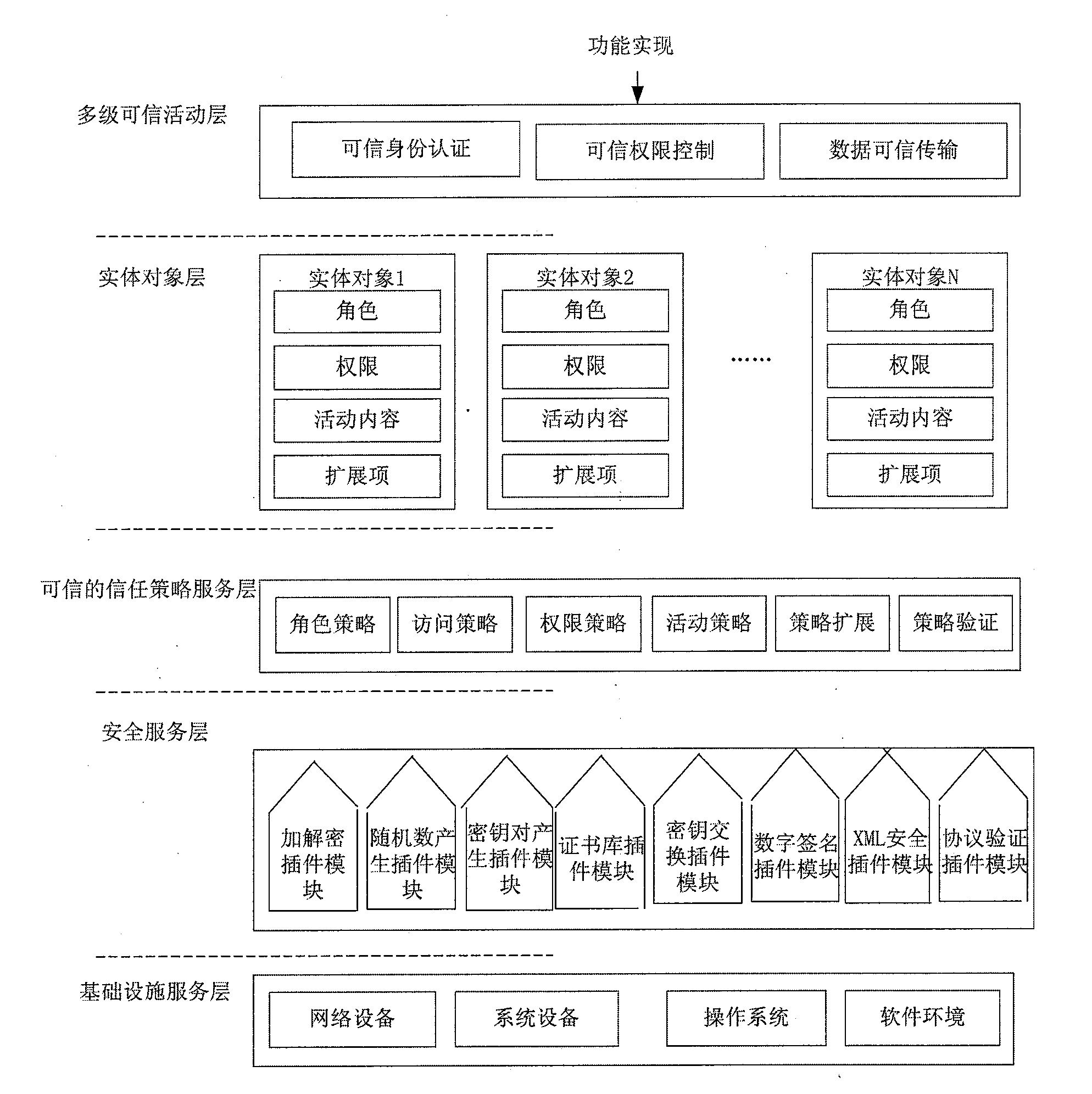
[0032] [32] figure 1 It is a structural diagram of the background technology of this application, which includes a multi-level trusted activity layer composed of trusted identity authentication, trusted authority control, and trusted data transmission. It can be known that this Chinese patent application only adds security management to identity authentication, authority control and data transmission, but it cannot guarantee that any process in the system is the process expected by the user, let alone that the user's behavior will be executed in the expected way.
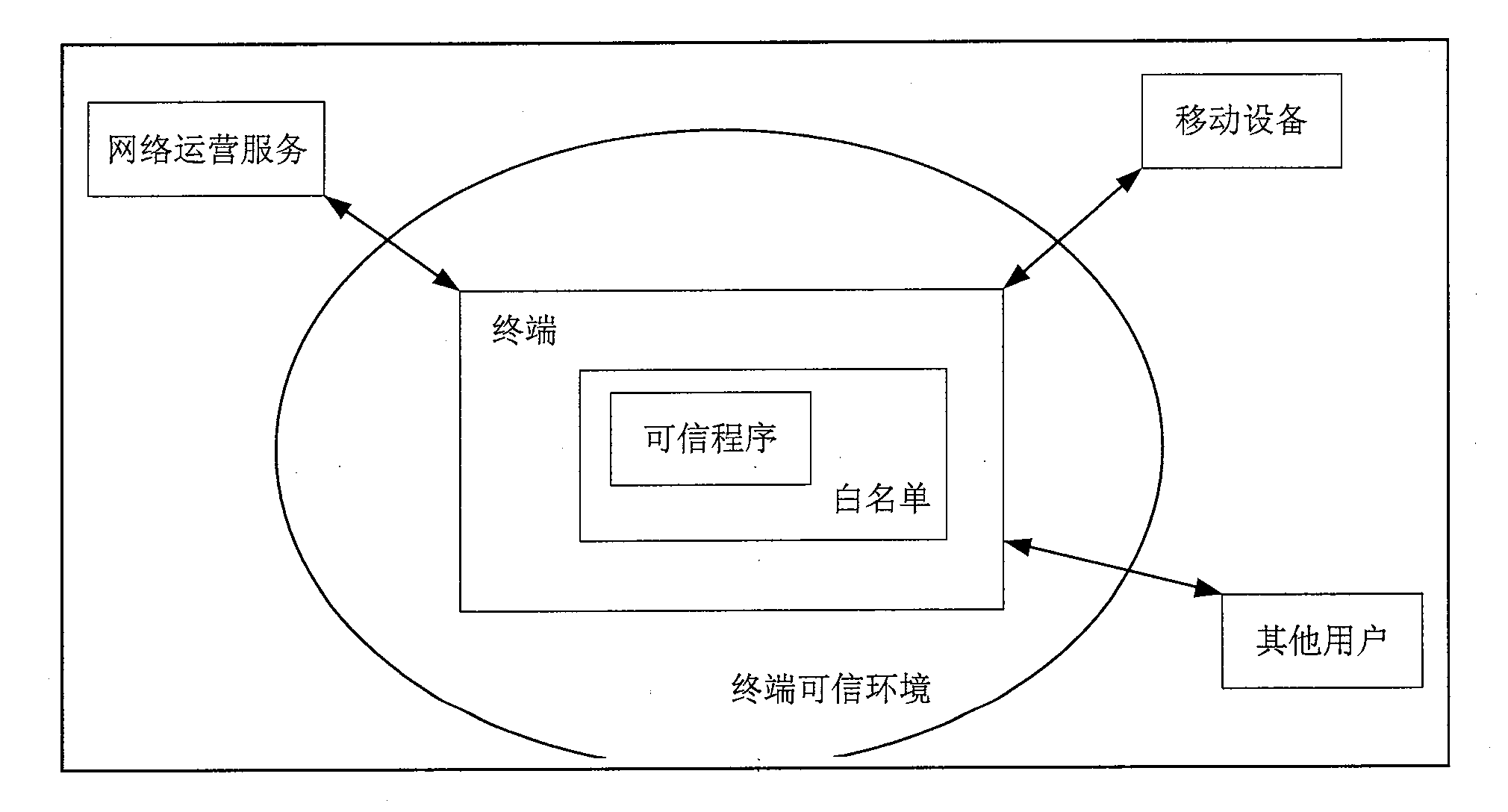
[0033] [33] figure 2 is the schematic diagram of this application, which is dedicated to obtaining a trusted environment for terminals interacting with network operation services, mobile devices, and other users. In the trusted environment of the terminal, the white list of files is obtained through a trusted program.
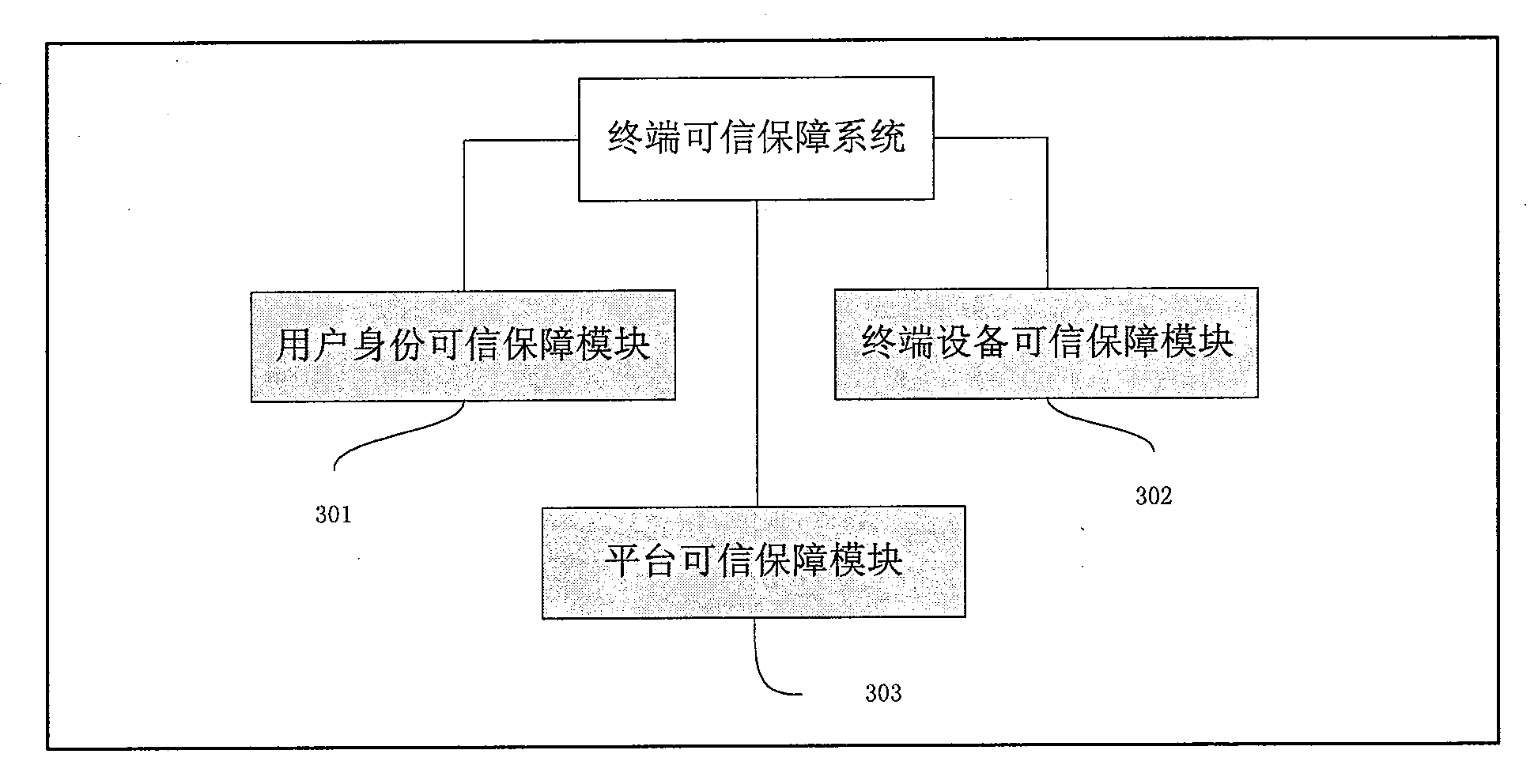
[0034] [34] image 3 It is a block diagram of the application. The terminal trust guarantee ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com