Method for implementing reliable computation based on reliable multi-task operating system
An operating system and trusted computing technology, applied in computing, computer security devices, instruments, etc., to save costs and protect existing software properties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
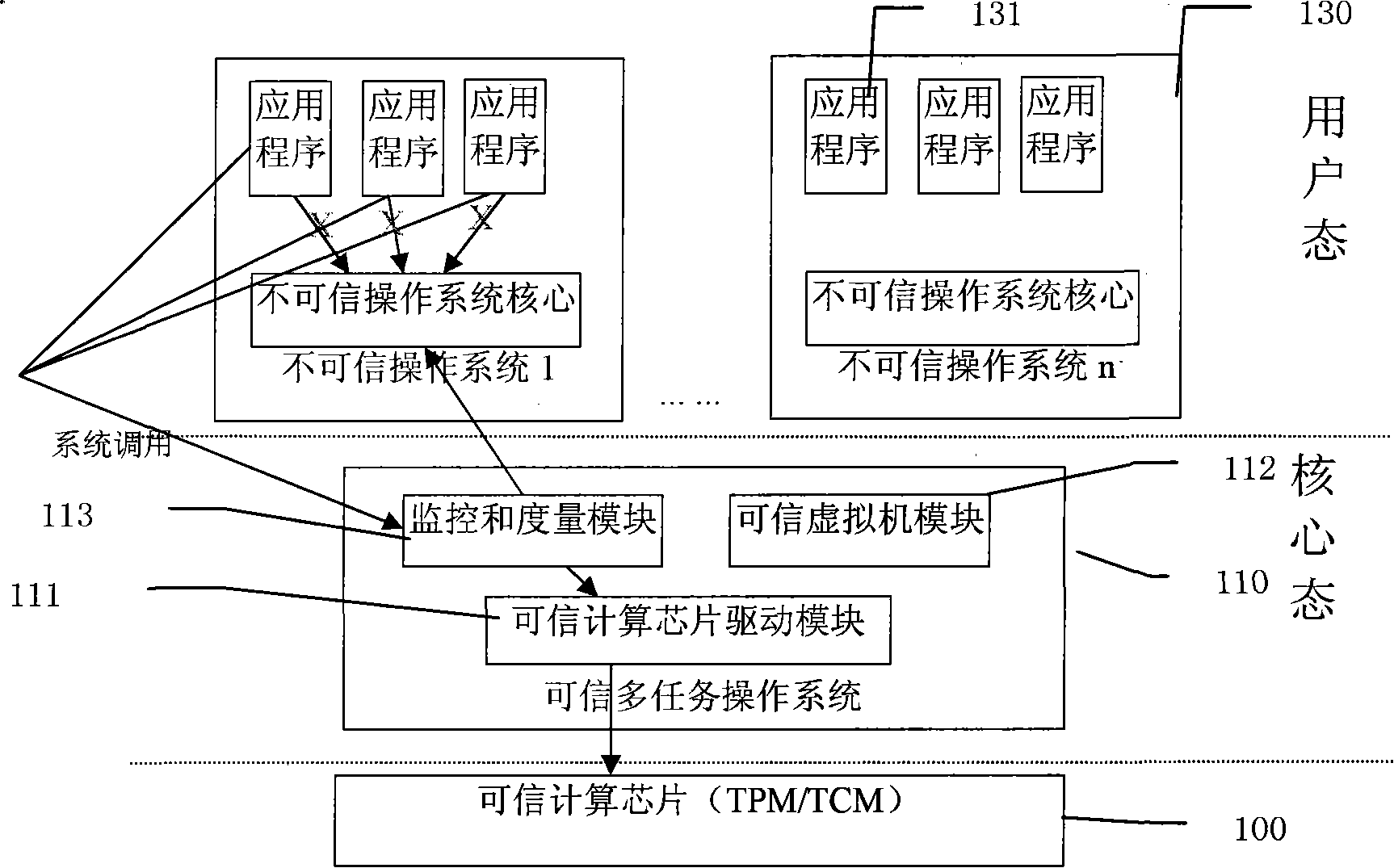
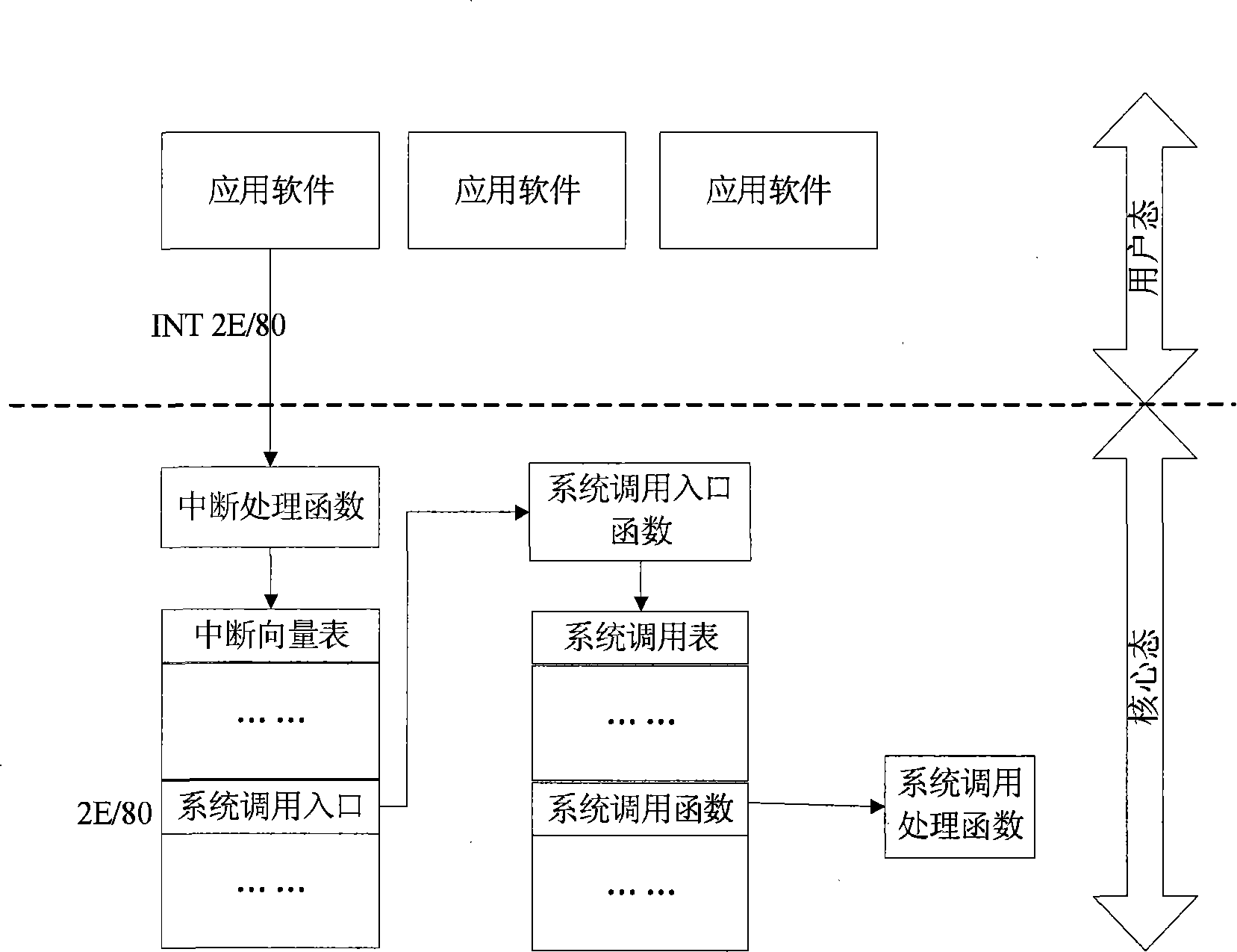
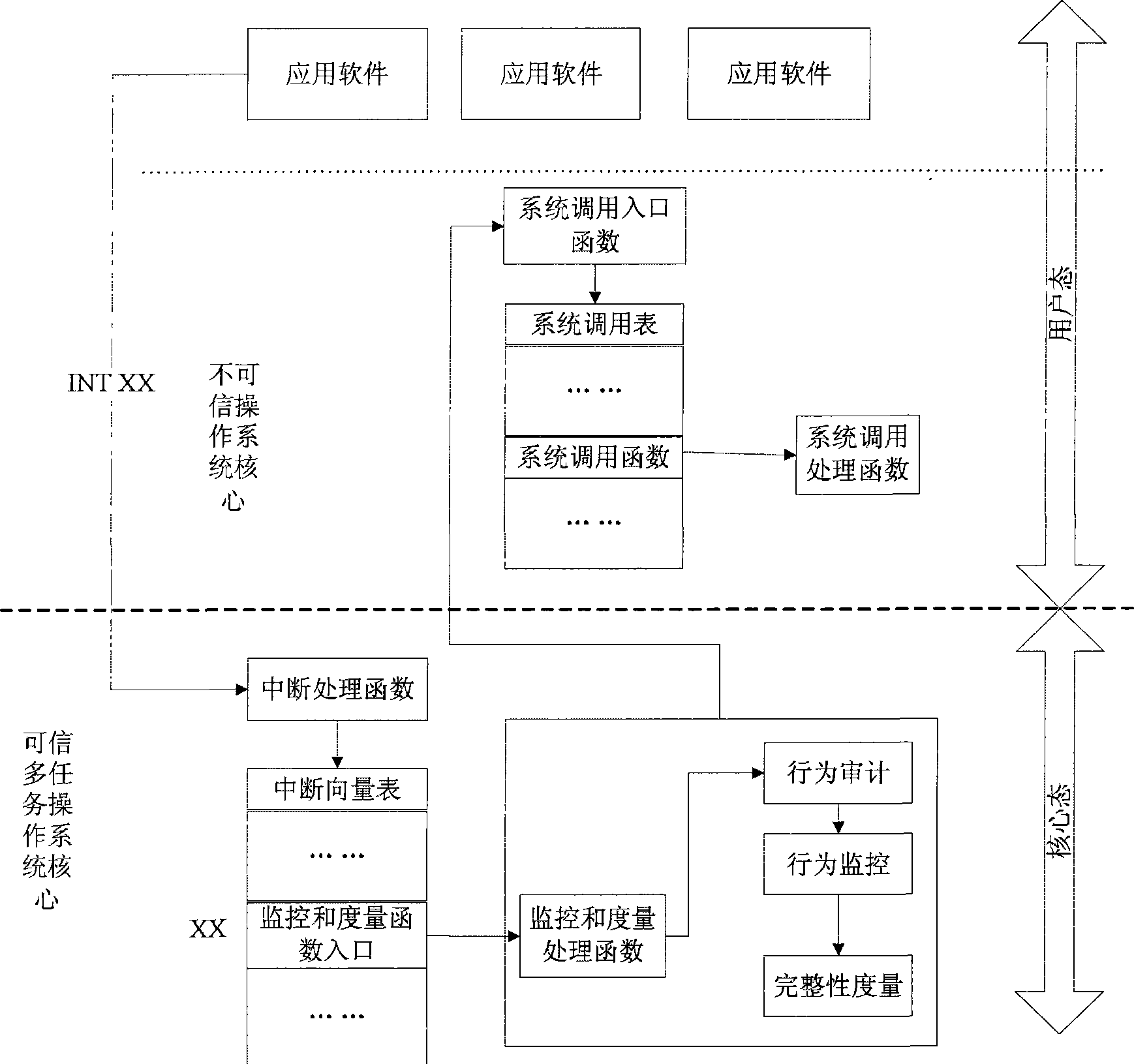
[0037] In order to make the features and advantages of the present invention more clearly understood, below in conjunction with accompanying drawing, describe in detail as follows: figure 1 As shown, it describes the structural diagram of the system architecture of the present invention, which is divided into three parts. The bottom layer 100 is a trusted computing chip, including TPM and TCM; the core state 110 is composed of a trusted computing chip driver module 111, a trusted virtual machine module 112. The monitoring and measurement module 113 is composed; the user mode 130 includes multiple untrusted operating systems, on which multiple application programs run. When the application program 131 in the user state requests information from the core state, the system will automatically switch from the user state to the core state, and enter the core of the trusted multitasking operating system for processing. The trusted multitasking operating system runs on the core state ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com