Method for upgrading function of creditable calculation modules
A technology of trusted computing and function upgrade, applied in the field of communication, can solve the problems of non-compliance, complicated use of commercial operations, and the fourth scheme does not have the conditions for implementation, and achieves the effect of realizing the upgrade and the method is simple and easy to implement.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
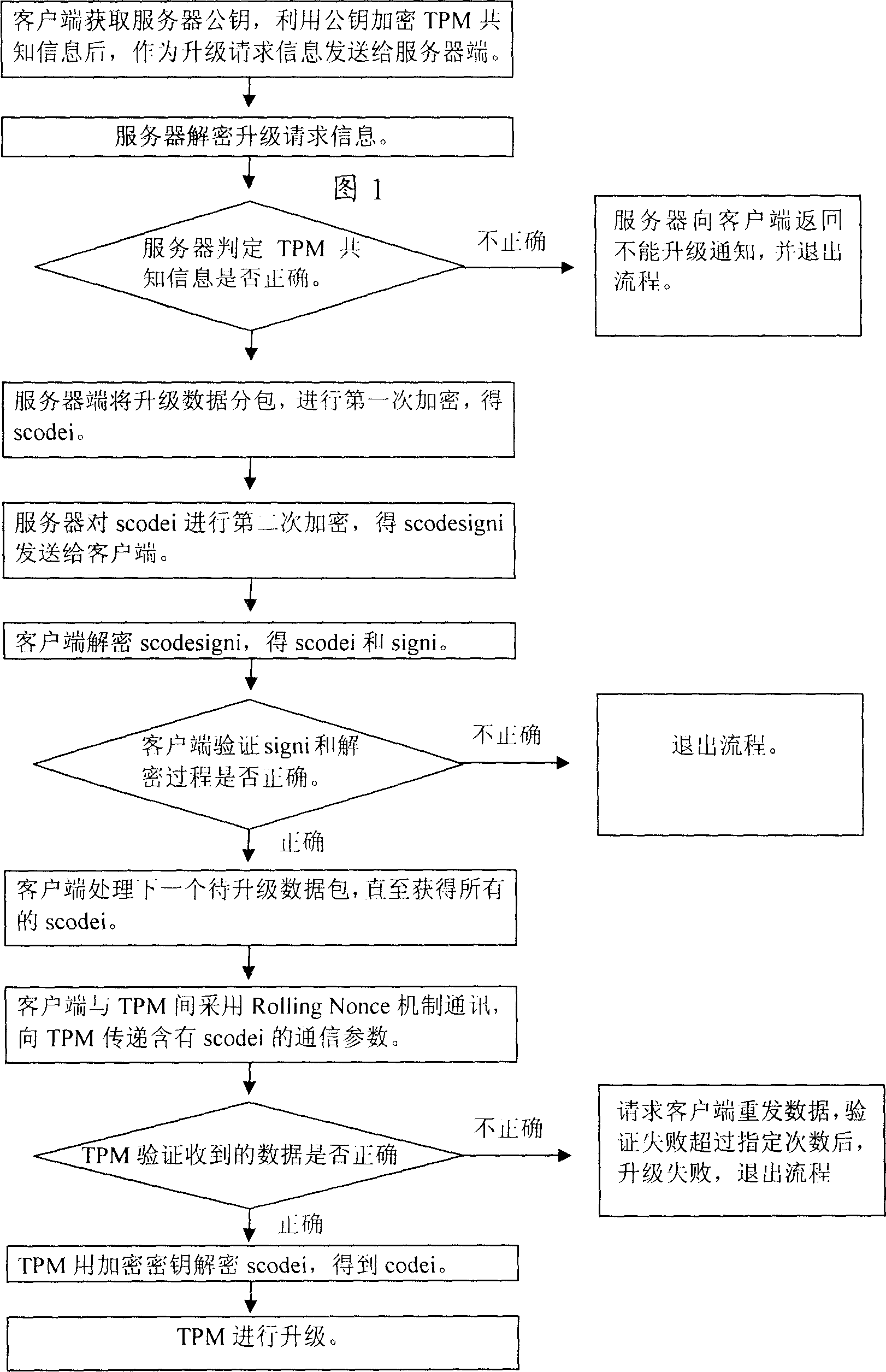
[0045] Below according to accompanying drawing and embodiment the present invention will be described in further detail:
[0046] The main idea of the present invention is: under the conditions of issuing AIK certificates have not been established at present, or do not rely on the establishment of conditions for issuing AIK certificates, the code of the trusted computing module is used as the common knowledge of the upgraded server and the trusted computing module secret information. The code of the trusted computing module is divided into the code before upgrading and the code to be upgraded, and both codes contain manufacturer information and version information (manufacture and version). The way to send commands to get this information. Generally, the manufacturer information of the code before the upgrade of the trusted computing module and the code after the upgrade of the protection function are the same, and the version information of the latter is greater than that ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com