Authentication system and method based on dependable computing
A technology of trusted computing and authentication system, which is applied in the field of authentication system based on trusted computing, can solve the problems that the authentication server cannot be guaranteed to be trusted, the certificate server cannot be guaranteed to be trusted, and the application server cannot be guaranteed to be trusted. Reliability, safety improvement, and safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
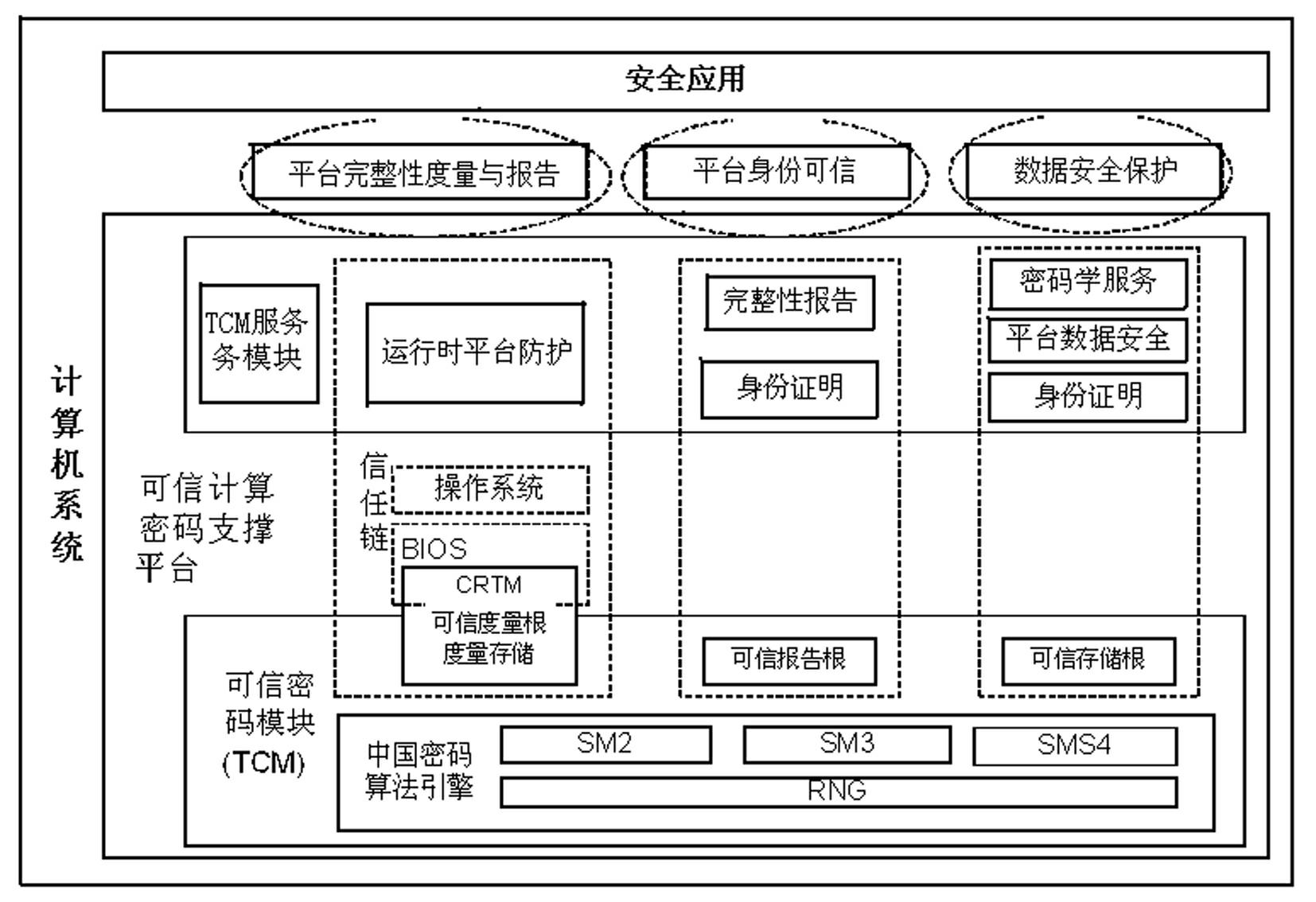
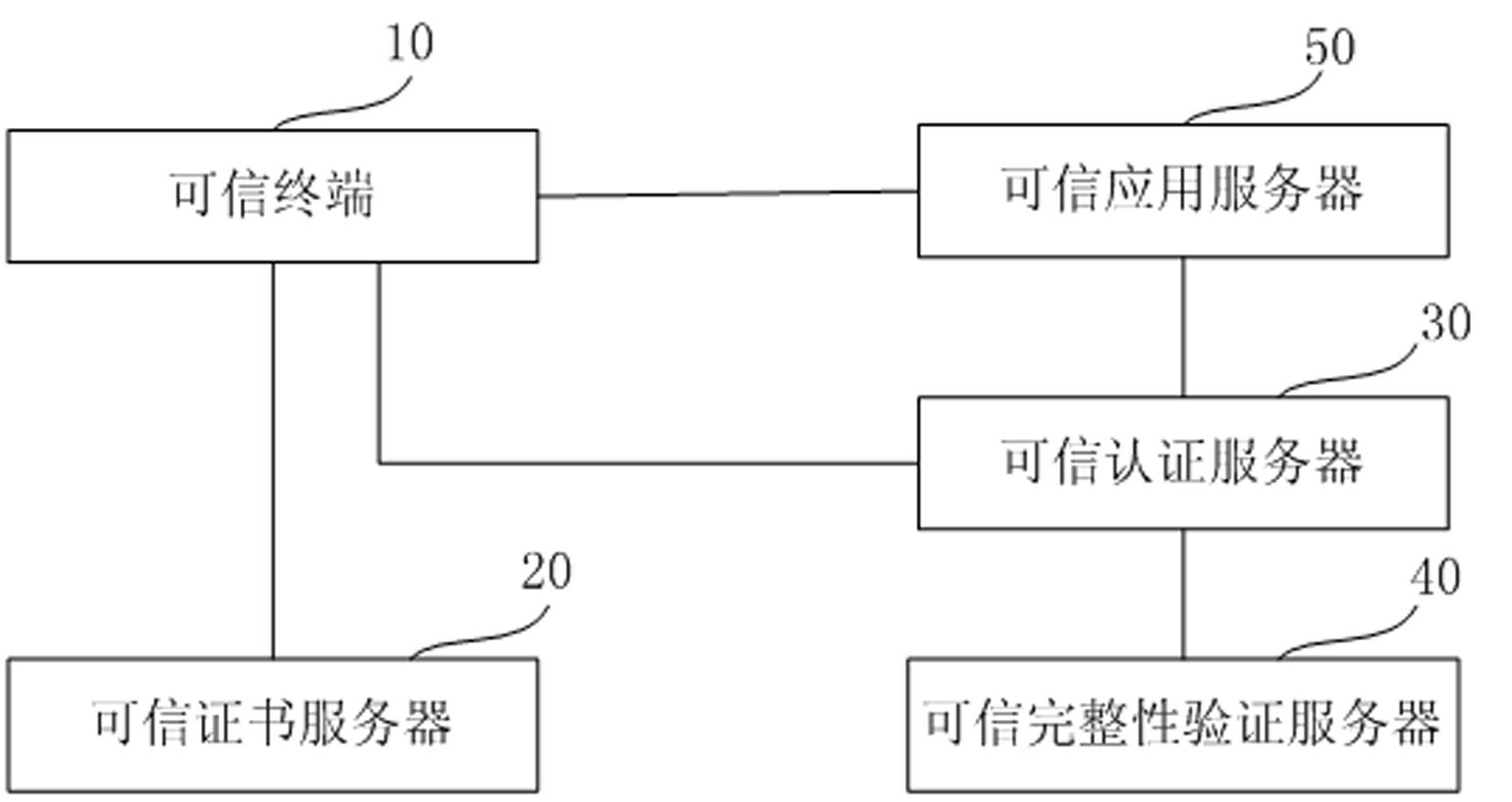
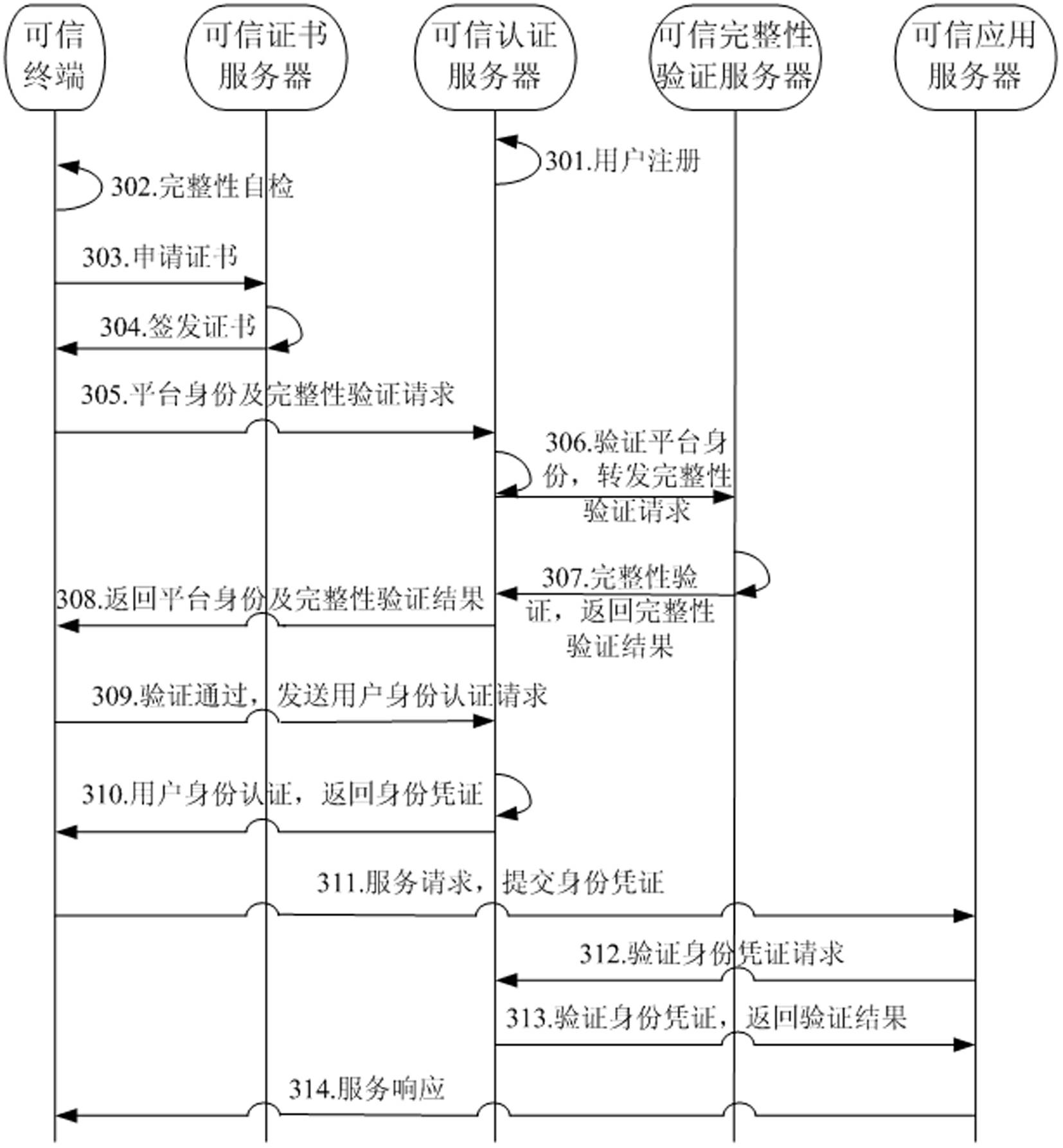
[0029] The main idea of the present invention is: using trusted computing technology, install a trusted computing module in the entity implementing authentication, to ensure the security of the computer network and server, and to ensure the credibility of the terminal, which can not only improve the security of the entity implementing authentication It can also improve the security of the entire computer network, thereby enhancing the credibility and security of authentication on the computer network.
[0030] In the present invention, the trusted computing module refers to a trusted computing security chip, which is a security chip on a computer motherboard. The chip performs a self-test on the local hardware platform when the computer is turned on, and compares the measurement value stored in the trusted computing security chip with the measurement value re-detected on the hardware when the computer is turned on. If the local hardware changes, the platform can Whether to c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com