Method of controlling security of terminal set top box applied under environment of living broadcast and broadcast on demand
A security control and terminal technology, applied in the field of information dissemination, can solve the problems of short and frequent decryption key deciphering period, unsafe communication channels between terminal set-top boxes and IC cards, and achieve the effect of avoiding frequent updates and ensuring effective execution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
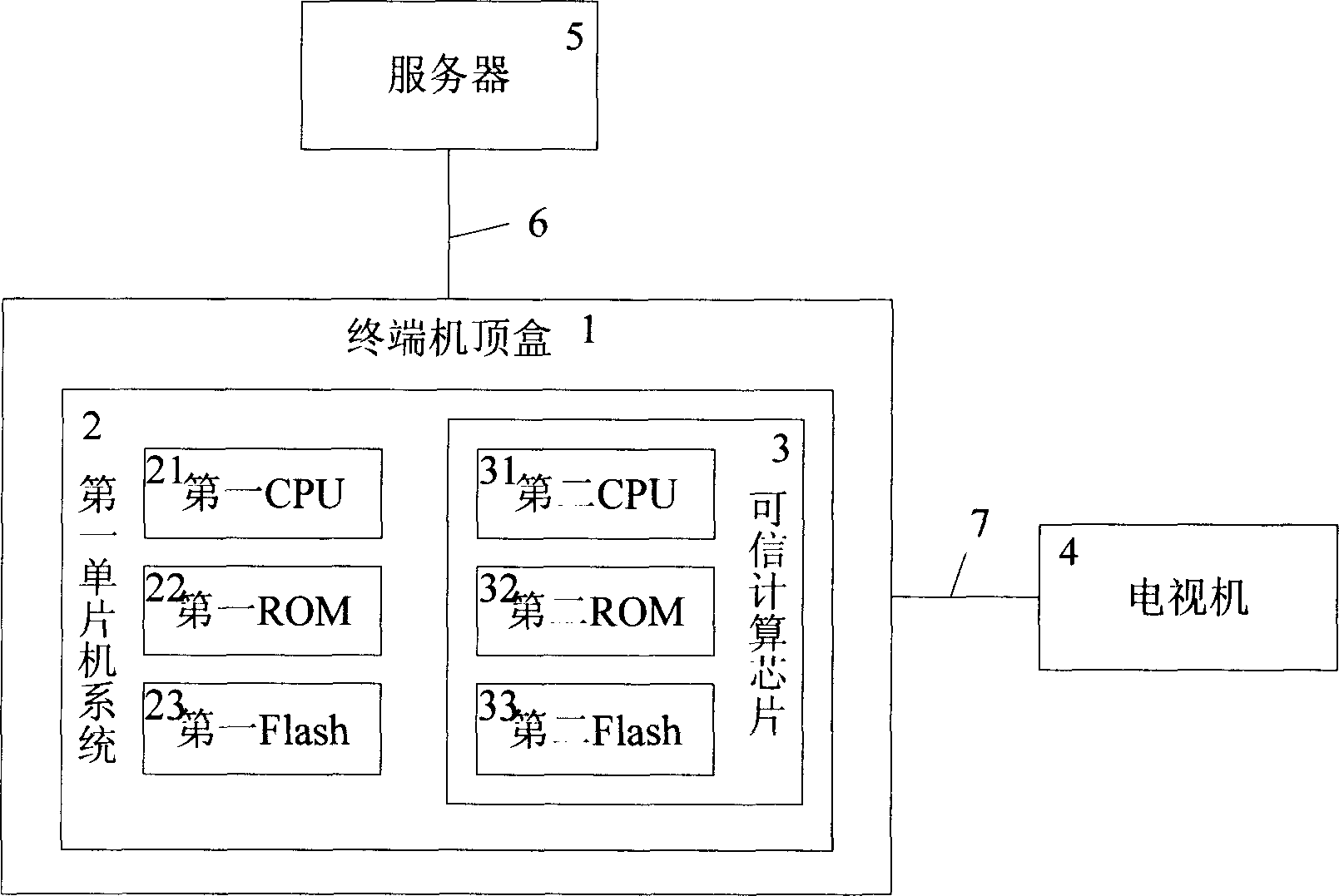
[0041]A terminal set-top box security control method applied in the live broadcast and on-demand environment, implemented in the Internet network system through the terminal set-top box 1, the terminal set-top box 1 is connected to the server 5 of the supplier through the Internet network 6, and the terminal set-top box 1 is connected to the TV through a cable 7 The machine 4 is online, the first single-chip microcomputer system 2 of the terminal set-top box 1 contains the first ROM22, the first CPU21 and the first Flash23. The program of the control, under the control and command of the program stored in the first ROM22 and the first Flash23, the first CPU21 performs the operation of managing and controlling the work of the following CPU31. It is characterized in that the first single-chip microcomputer system 2 Trusted computing chip 3 is also embedded in it, trusted computing chip 3 is a second single-chip microcomputer system that is sealed and contains the second ROM32, th...
Embodiment 2
[0070] Except for the prompt information in the eleventh step, the sixteenth step, the nineteenth step and the twenty-third step, the words of the prompt information are "update failed, please contact the supplier", "the user has no right to receive the program, please contact the supplier The supplier purchases the right to receive", "Update failed, please contact the supplier" and "Decoding failed, please contact the supplier", the rest is the same as that of Embodiment 1.
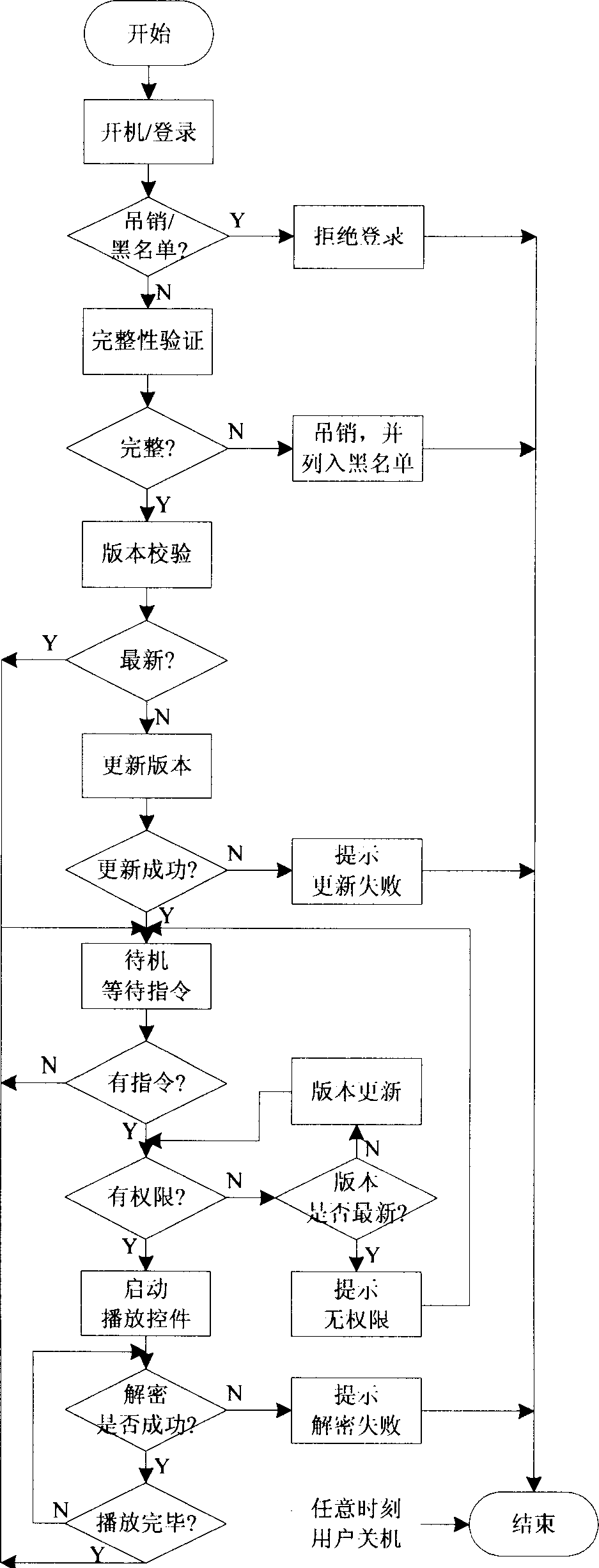
[0071] The above embodiment is implemented in the Internet network system, see figure 1 . The operation process of above embodiment, see figure 2 .
[0072] working principle. The trusted computing chip 3 obtains the digital media content from the playback control, and within the scope permitted by the right object in it, the decryption program decrypts the digital media content according to the decryption key in it, and then decrypts the The digital media content, that is, the audio-visual program ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com